Risk Assessment Edge Contract for Efficient Resource Allocation
Abstract
1. Introduction
- 1.
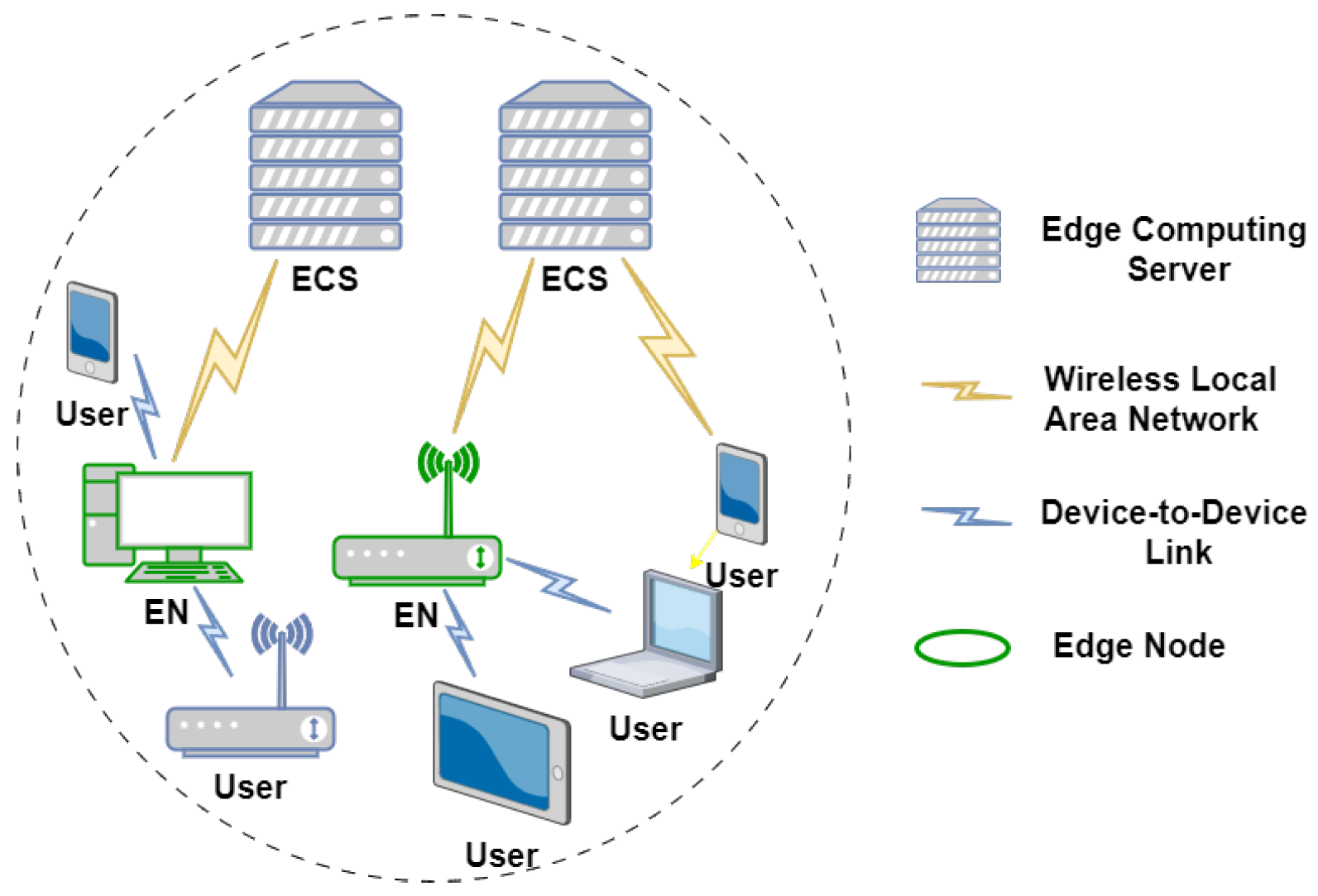
- In a resource pool composed of multiple ECSs and ENs, when an EN receives requests from edge devices, it sometimes needs to request computing resources from an ECS to complete the tasks according to its computing capabilities and the demands of edge devices. It is important to learn how to determine whether an EN should request computing resources from the ECS and how to determine the appropriate amount of requested resources to maximize the service quality for the edge devices in the region.
- 2.
- Edge devices are often different with heterogeneity in terms of location, specifications, reliability, and the reputation of edge devices and/or ENs. The allocation of computing resources is profoundly influenced. For instance, from a reputation perspective, within a resource pool, certain edge devices and ENs might frequently engage in resource monopolization, excessively occupying computing resources or requesting computing resources from an ECS at a high frequency. In such cases, the ECS tends to allocate resources to the edge devices with lower risk profiles or might raise the resource prices for high-demand ENs, while the ECS itself possesses specific resource preferences. For instance, in an edge hospital setting, online clinics often prioritize image data and tend to allocate more computing resources to image-related tasks compared to audio data. The heterogeneity of computational demands and the preferences of the ECS constitute significant challenges in edge resource allocation.
- 3.
- Since the usage of user data is increasing day by day, the data usage of users can be enormous. In some environments that are highly sensitive to computational latency and have strong requirements for real-time information, known as high-workload resource scheduling environments, the computing resources of an ECS could be fully occupied for extended periods. In such cases, the scheduling algorithms often lead to issues like energy waste and scheduling delays. Designing more efficient allocation schemes to reduce energy waste, scheduling delays, and edge service failure rates in high-workload resource scheduling environments is crucial.
- 4.
- The computing resource allocation for edge devices needs to consider a joint optimization model of resource allocation and task offloading, which often involves NP-hard optimization problems. If the algorithms cannot meet the required time complexity for optimization problems, facing an exponential growth trend in data volume, significant delays may occur. Therefore, the algorithms must be capable of fast convergence.
- 1.
- We develop a resource trading model based on the Stackelberg game for solving task offloading problems in a resource pool composed of ECSs and ENs. The model allocates computing resources according to the proportion of EN requests determined by the game, while the existence of Nash equilibrium in the game is proved by using fixed-point theory.
- 2.
- By incorporating risk assessment theory, we introduce the concept of edge risk to evaluate the profits and benefits based on the contracts with edge devices. The data usage follows a generalized Wiener process, and the ECS predicts the future edge risk value that edge devices will possess based on their current data volume. It provides a unified standard for heterogeneous edge devices. A novel edge contract based on the edge risk assessment is proposed, aiming to reduce transaction delays and energy losses in high-workload environments for resource allocation and task offloading. The contract allows edge devices to autonomously update two contract elements: the limit of local computation resource request and the computation resource price, in real time.
- 3.
- To address the resource allocation problem between the ECSs and the ENs, we design a low-complexity risk assessment contract algorithm (RACA). Furthermore, we prove the strict convexity of the subgame problem and solve it using the Lagrange multiplier method to find the equilibrium point in the game model. The heuristic algorithm demonstrates the capability of swift convergence, guided by the proportion of user-requested resources to the overall requested resources, allocating the computing resources acquired by the ENs to their respective edge devices.
- 4.
- We conduct simulation experiments to validate the convergence efficiency of the designed algorithm under high-workload conditions. Furthermore, we evaluate the performance of the ECS, utilizing the proposed RACA algorithm, which demonstrates its superiority compared to other similar algorithms. Additionally, the simulation results show the advantages of the proposed request ratio allocation scheme when the ENs receive specific requested resources. The performance of the RACA algorithm in terms of game convergence is demonstrated, too.
2. Related Work
3. System Model
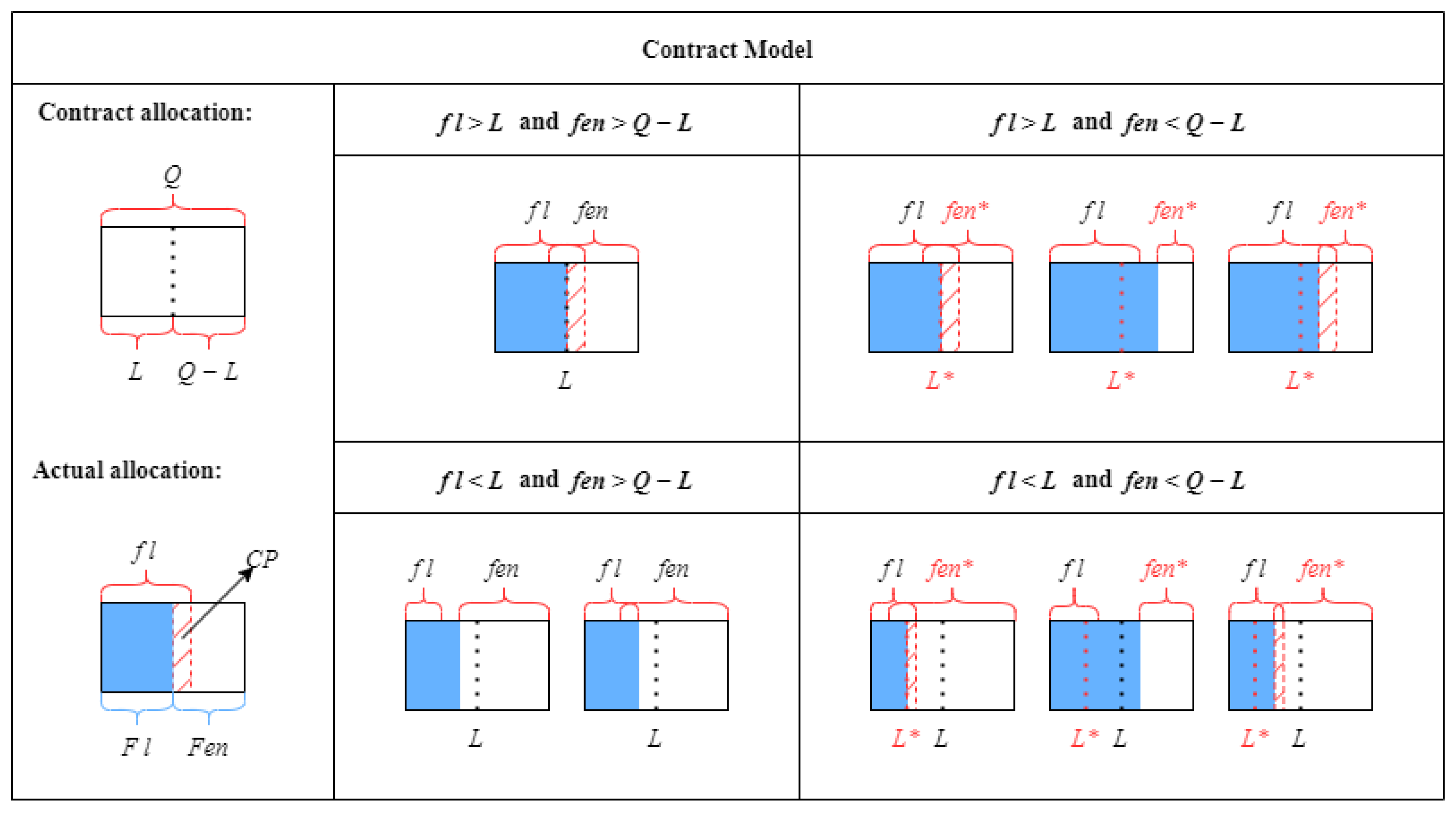
3.1. Problem Overview and Contract Model
| Notations | Descriptions |
|---|---|
| Sets of users, ECSs, and ENs | |
| Indices for users, ECSs, and ENs | |
| Subscription of to | |
| Subscription of to | |
| Subscription of to | |
| Data generated by | |
| Wiener process drift and volatility of | |
| Task request rate of | |
| Task request amount of | |
| Task request amount from to | |
| Expected task completion time of | |
| Unit gain for handling local tasks by | |
| Unit price of computing resources | |
| Unit price of compensatory resources | |
| Local/EN computing resource requests to | |
| Final resource allocation by to local/EN | |
| Final revenue of | |
| Local task volume of | |
| Computing resources held by | |
| Unit gain after saves time | |
| Channel bandwidth between and | |
| Transmission power between and | |
| Channel gain between and | |
| Loss weight between and | |
| Energy loss between and | |
| Revenue contribution of to | |
| Threshold for acceptable contribution increase | |
| Risk of for | |
| Threshold for acceptable risk for |
3.2. User Model
3.3. ECS Revenue Model
3.4. EN Revenue Model
3.5. Contract Risk Assessment
4. Problem Description
4.1. Stackelberg Game Model
4.2. Subgame Model Solution
4.3. Nash Equilibrium Proof
5. Algorithm Analysis
| Algorithm 1 Risk Assessment Contract Algorithm (RACA). |
|
| Algorithm 2 Finding Nash equilibrium between ECS and ENs based on convex optimization. |
|
6. Simulation Results
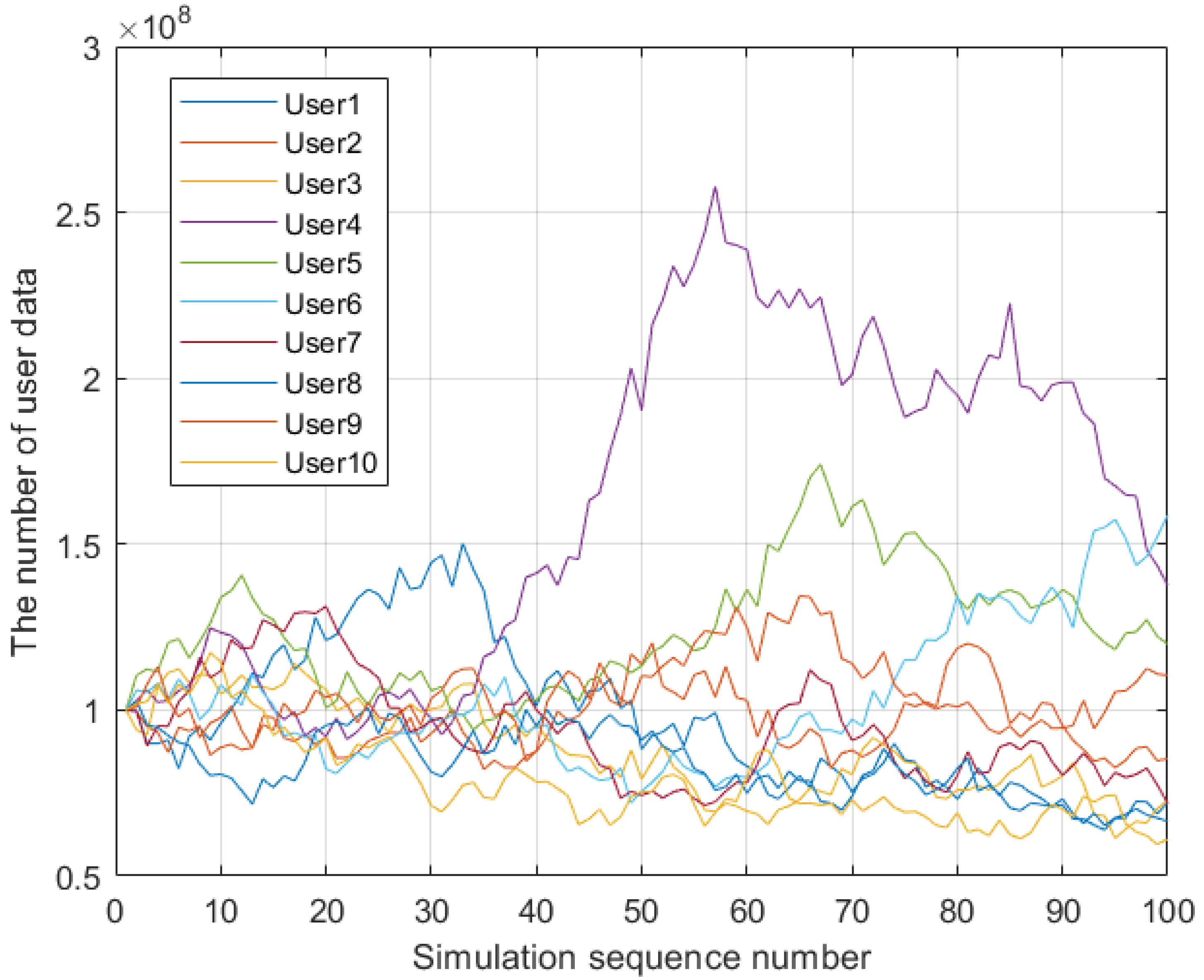
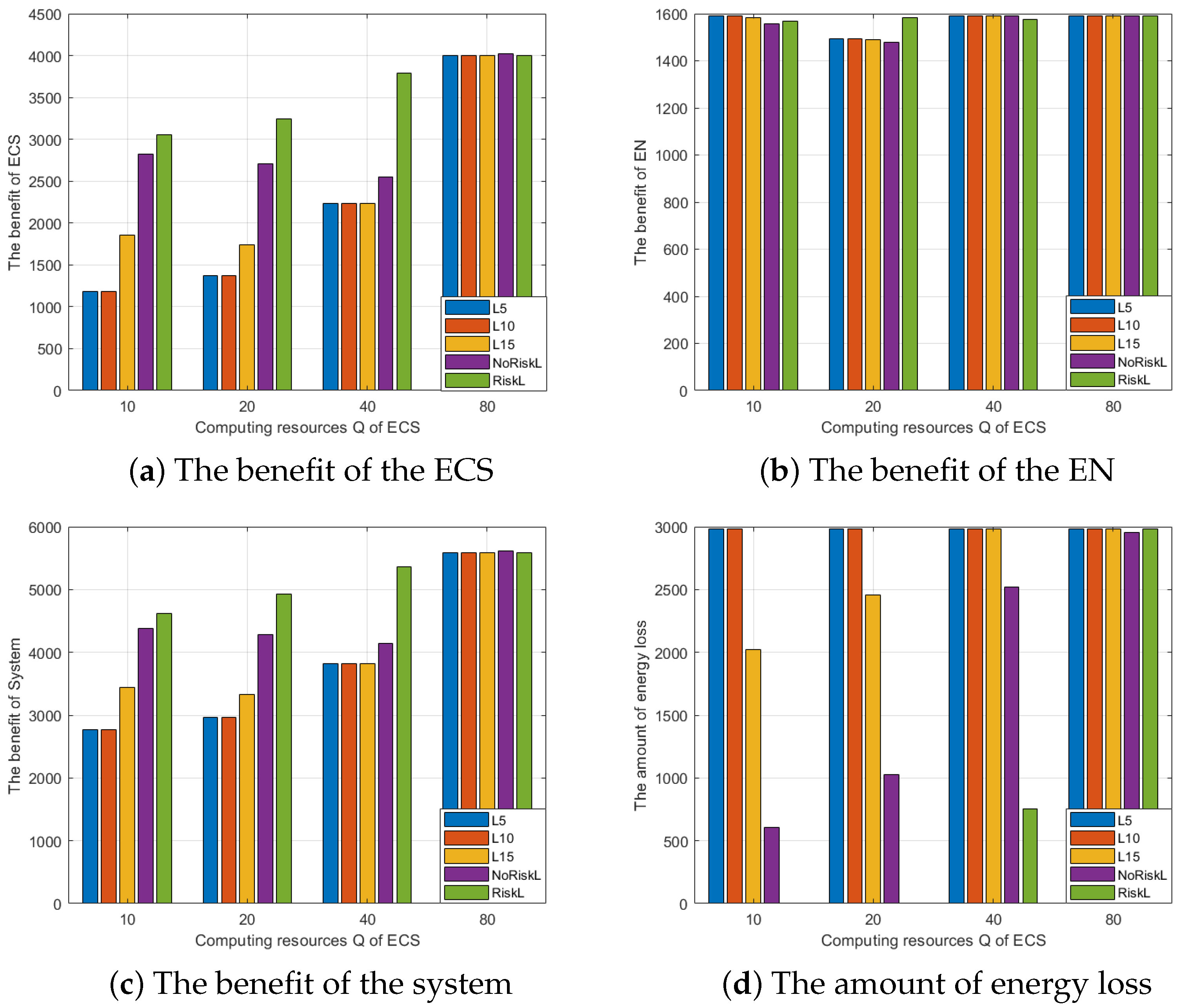
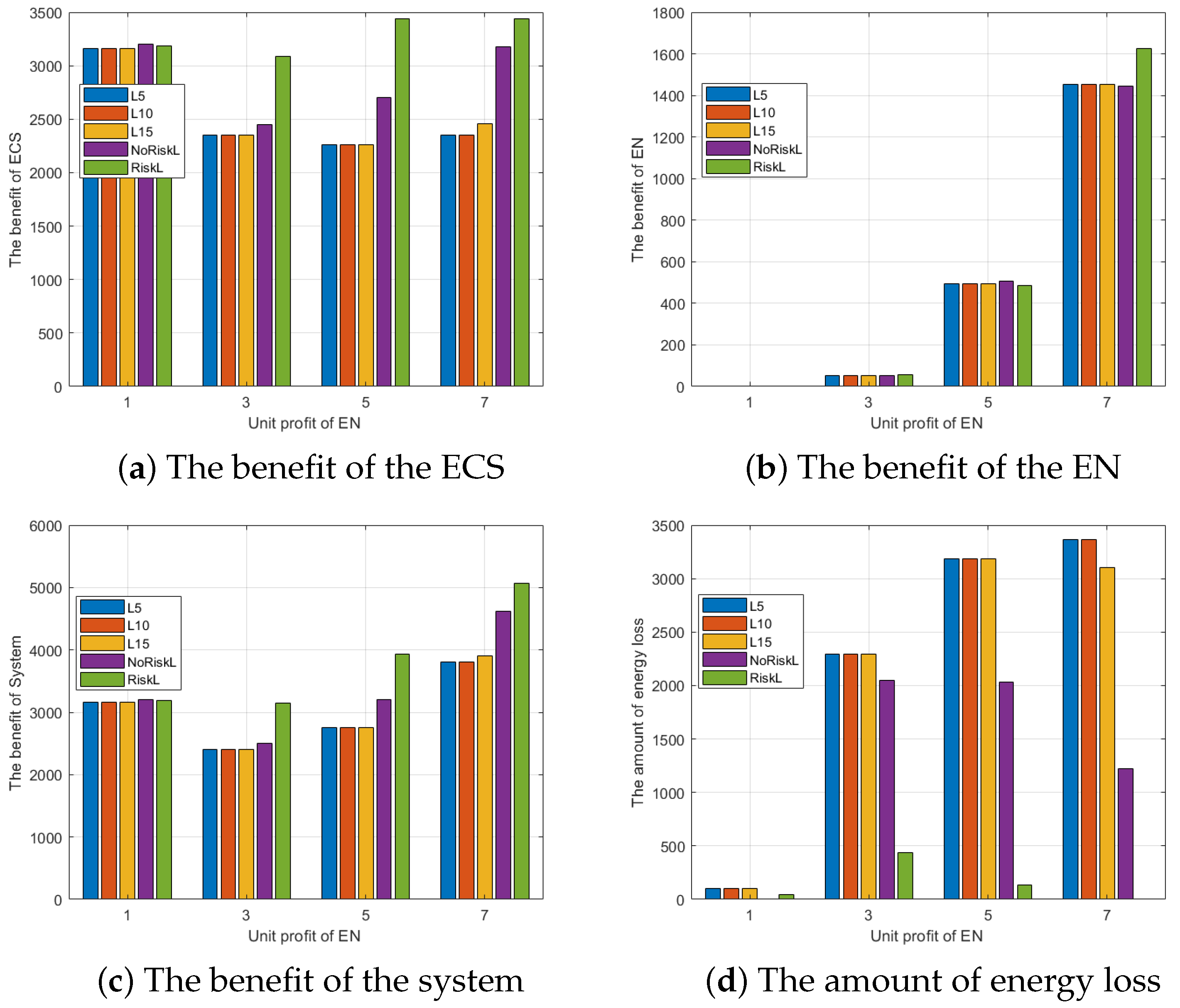
6.1. Performance Evaluation of Risk Assessment
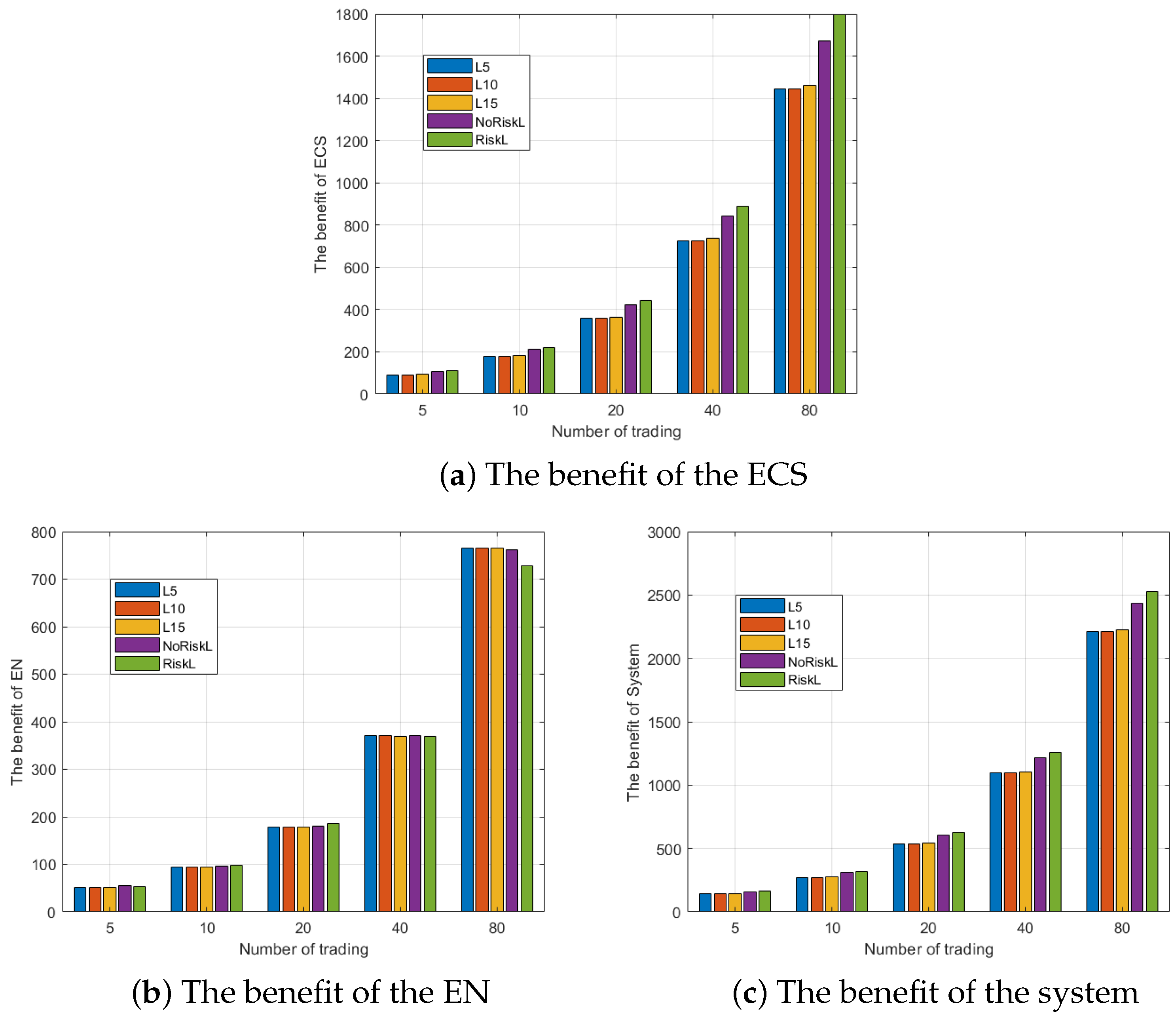
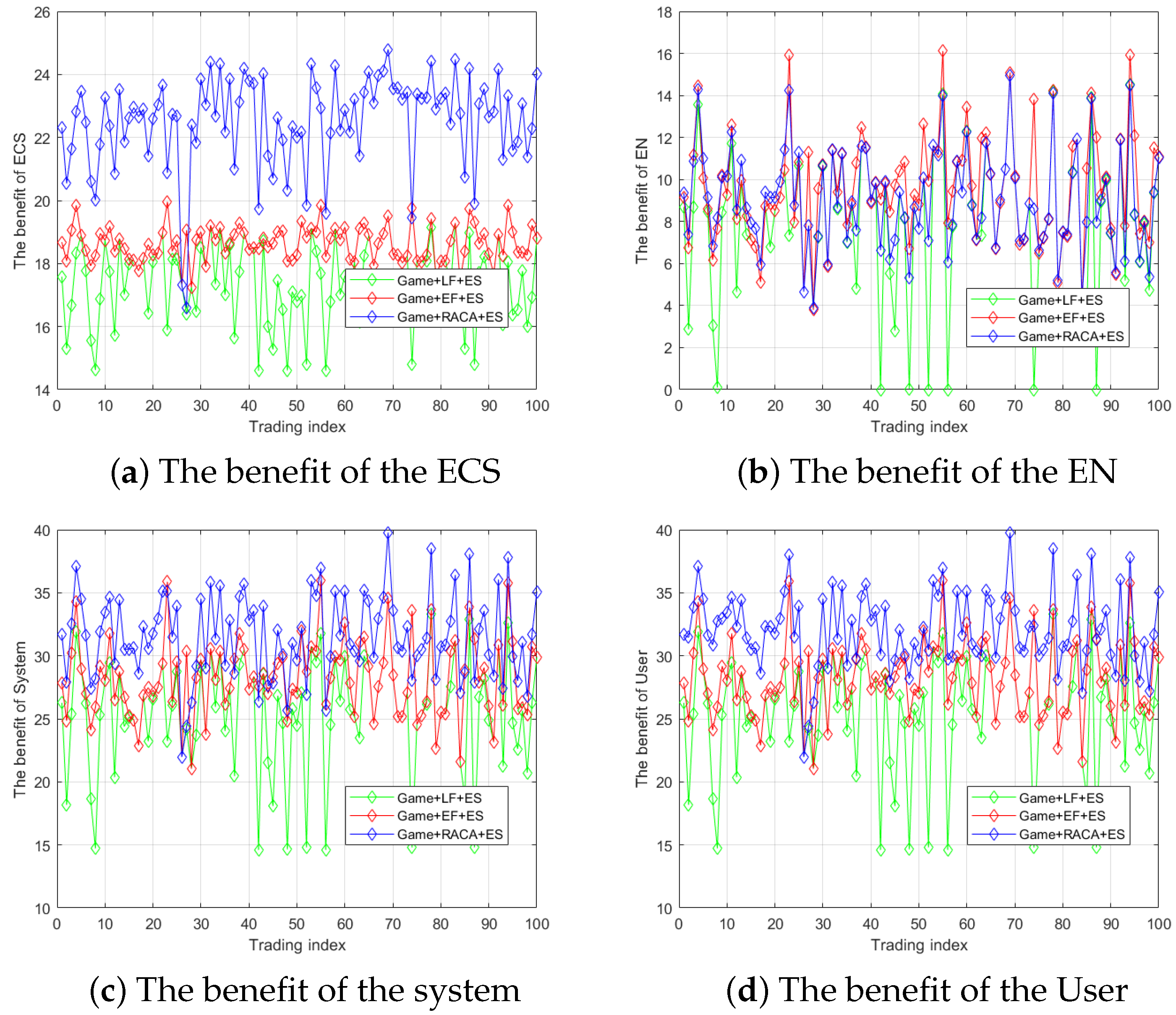
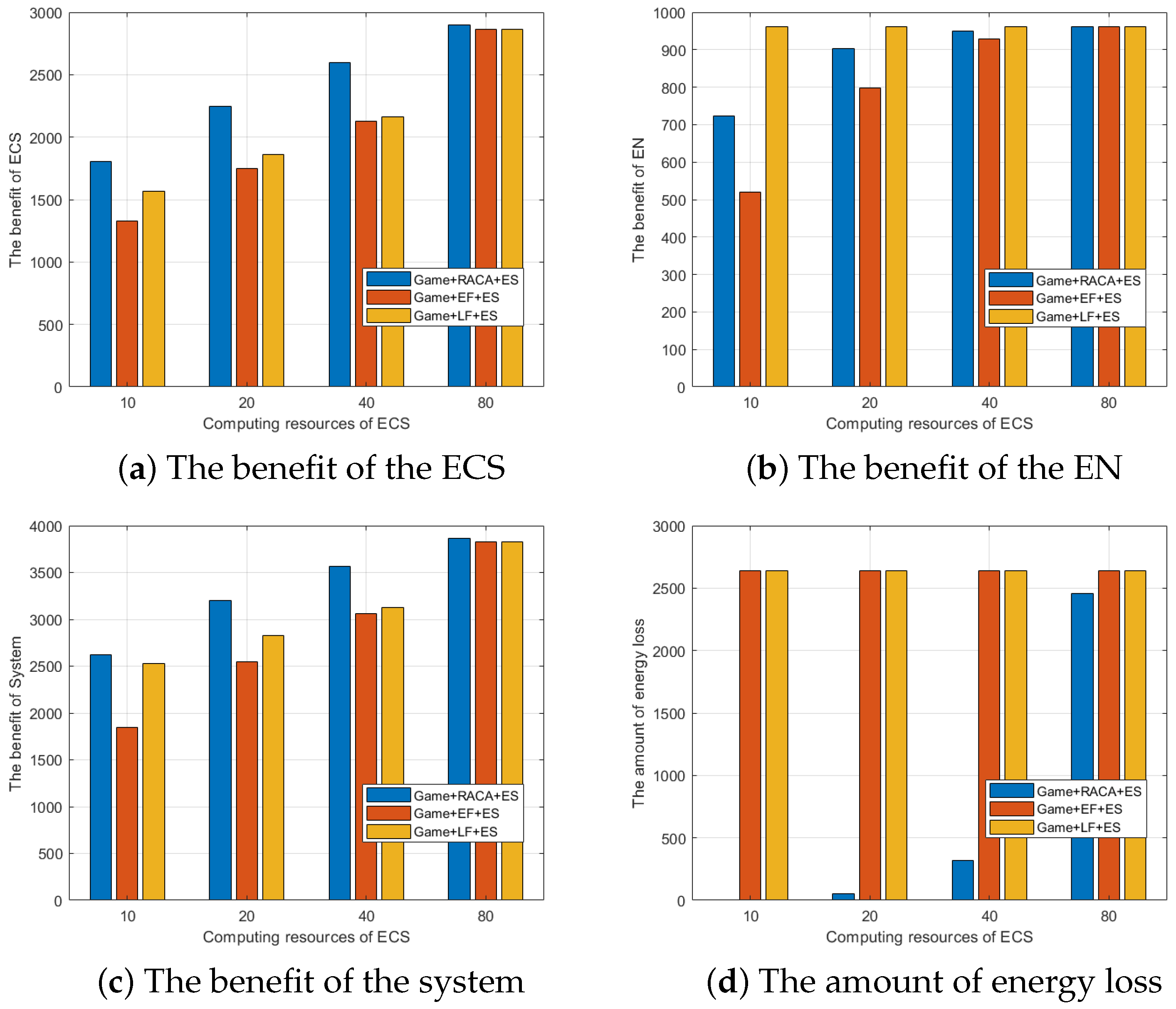
6.2. Performance Evaluation of RACA
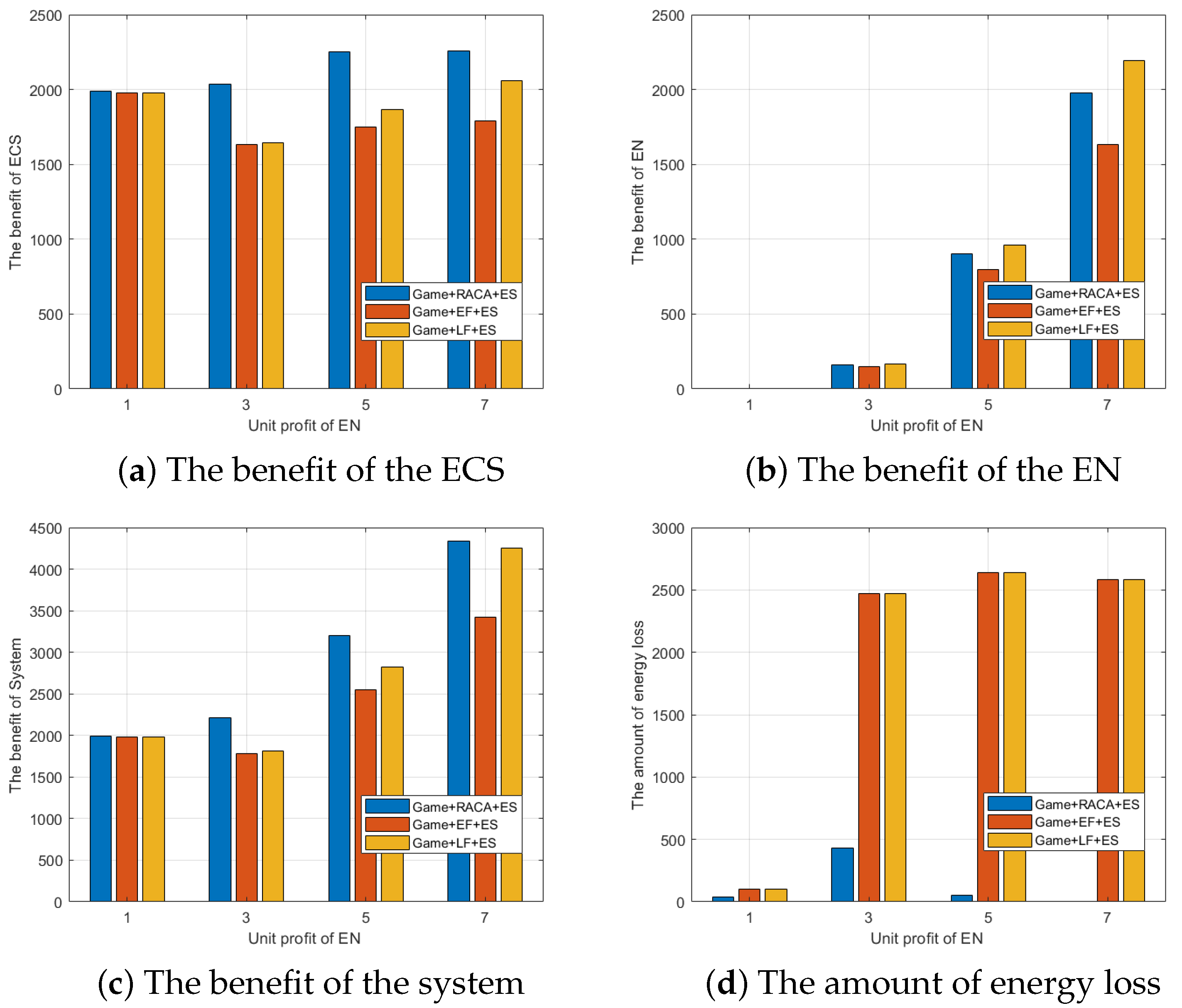
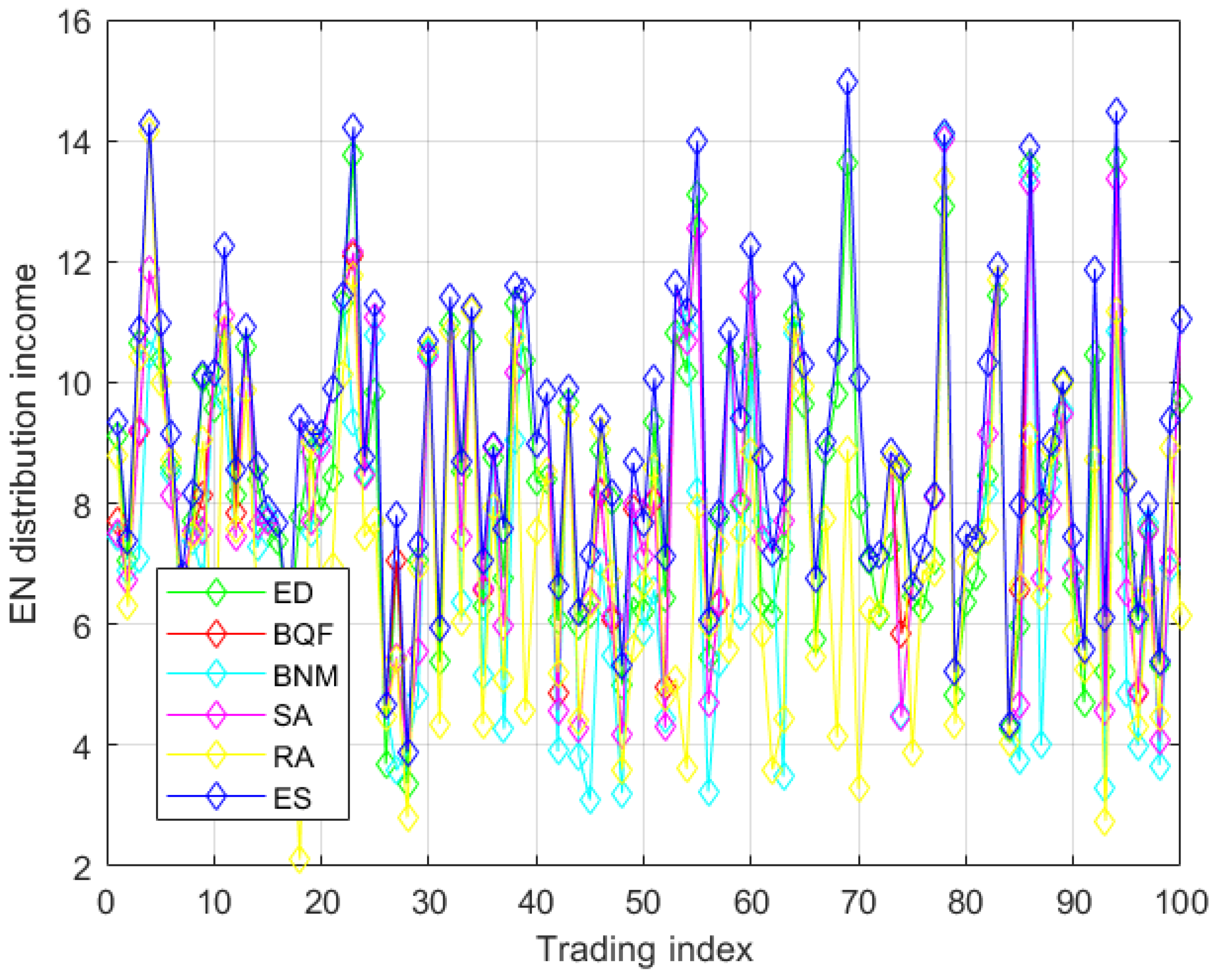
6.3. Comparison of EN Resource Allocation
7. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Correction Statement
Appendix A. The Derivation of dDl Using the Ito Process
References
- Chen, X.; Jiao, L.; Li, W.; Fu, X. Efficient Multi-User Computation Offloading for Mobile-Edge Cloud Computing. IEEE/ACM Trans. Netw. 2016, 24, 2795–2808. [Google Scholar] [CrossRef]
- Yi, C.; Cai, J.; Su, Z. A multi-user mobile computation offloading and transmission scheduling mechanism for delay-sensitive applications. IEEE Trans. Mob. Comput. 2019, 19, 29–43. [Google Scholar] [CrossRef]
- Chiang, M.; Zhang, T. Fog and IoT: An overview of research opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A survey on mobile edge computing: The communication perspective. IEEE Commun. Surv. Tutorials 2017, 19, 2322–2358. [Google Scholar] [CrossRef]
- Bozkaya, E. A Digital Twin Framework for Edge Server Placement in Mobile Edge Computing. In Proceedings of the International Informatics and Software Engineering Conference (IISEC), Ankara, Turkey, 21–22 December 2023; Volume 4, pp. 1–6. [Google Scholar]
- Luo, R.; Jin, H.; He, Q.; Wu, S.; Xia, X. Enabling Balanced Data Deduplication in Mobile Edge Computing. IEEE Trans. Parallel Distrib. Syst. 2023, 34, 1420–1431. [Google Scholar] [CrossRef]
- Yuan, L.; He, Q.; Tan, S.; Li, B.; Yu, J.; Chen, F.; Yang, Y. CoopEdge+: Enabling Decentralized, Secure and Cooperative Multi-Access Edge Computing Based on Blockchain. IEEE Trans. Parallel Distrib. Syst. 2023, 34, 894–908. [Google Scholar] [CrossRef]
- Dai, P.; Hu, K.; Wu, X.; Xing, H.; Teng, F.; Yu, Z. A probabilistic approach for cooperative computation offloading in MEC-assisted vehicular networks. IEEE Trans. Intell. Transp. Syst. 2020, 23, 899–911. [Google Scholar] [CrossRef]
- Jamil, M.N.; Hossain, M.S.; Islam, R.U.; Andersson, K. Workload Orchestration in Multi-Access Edge Computing Using Belief Rule-Based Approach. IEEE Access 2023, 11, 118002–118023. [Google Scholar] [CrossRef]
- Khazali, A.; Bozorgchenani, A.; Tarchi, D.; Shayesteh, M.G.; Kalbkhani, H. Joint Task Assignment, Power Allocation and Node Grouping for Cooperative Computing in NOMA-mmWave Mobile Edge Computing. IEEE Access 2023, 11, 93664–93678. [Google Scholar] [CrossRef]
- Hu, B.; Gao, Y.; Zhang, W.; Jia, D.; Liu, H. Computation Offloading and Resource Allocation in IoT-Based Mobile Edge Computing Systems. In Proceedings of the 2023 IEEE International Conference on Smart Internet of Things (SmartIoT), Xining, China, 25–27 August 2023; pp. 119–123. [Google Scholar]
- Song, C.; Xu, W.; Wu, T.; Yu, S.; Zeng, P.; Zhang, N. QoE-driven edge caching in vehicle networks based on deep reinforcement learning. IEEE Trans. Veh. Technol. 2021, 70, 5286–5295. [Google Scholar] [CrossRef]
- Cheng, Y.; Liang, C.; Chen, Q.; Yu, F.R. Energy-efficient D2D-assisted computation offloading in NOMA-enabled cognitive networks. IEEE Trans. Veh. Technol. 2021, 70, 13441–13446. [Google Scholar] [CrossRef]
- Hu, X.; Tang, X.; Yu, Y.; Qiu, S.; Chen, S. Joint load balancing and offloading optimization in multiple parked vehicle-assisted edge computing. Wirel. Commun. Mob. Comput. 2021, 2021, 1–13. [Google Scholar] [CrossRef]
- Wang, J.; Liu, K.; Li, B.; Liu, T.; Li, R.; Han, Z. Delay-sensitive multi-period computation offloading with reliability guarantees in fog networks. IEEE Trans. Mob. Comput. 2020, 19, 2062–2075. [Google Scholar] [CrossRef]
- Chen, R.; Li, L.; Hou, R.; Yang, T.; Wang, L.; Pan, M. Data-driven optimization for resource provision in non-cooperative edge computing market. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Virtually, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Iyer, G.N.; Raman, V.; Aswin, K.; Veeravalli, B. On the strategies for risk aware cloud and fog broker arbitrage mechanisms. In Proceedings of the 2020 Fourth International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 11–13 March 2020; Volume 4, pp. 794–799. [Google Scholar]
- Peng, K.; Huang, H.; Liu, P.; Xu, X.; Leung, V.C. Joint optimization of energy conservation and privacy preservation for intelligent task offloading in mec-enabled smart cities. IEEE Trans. Green Commun. Netw. 2022, 6, 1671–1682. [Google Scholar] [CrossRef]
- Du, J.; Cheng, W.; Lu, G.; Cao, H.; Chu, X.; Zhang, Z.; Wang, J. Resource pricing and allocation in MEC enabled blockchain systems: An A3C deep reinforcement learning approach. IEEE Trans. Netw. Sci. Eng. 2021, 9, 33–44. [Google Scholar] [CrossRef]
- Liwang, M.; Gao, Z.; Wang, X. Let’s trade in the future! A futures-enabled fast resource trading mechanism in edge computing-assisted UAV networks. IEEE J. Sel. Areas Commun. 2021, 39, 3252–3270. [Google Scholar] [CrossRef]
- Marbukh, V. Towards Robust Fog/Edge Computing Infrastructure with Risk Adjusted Multi-Connectivity. In Proceedings of the 2022 9th International Conference on Future Internet of Things and Cloud (FiCloud), Rome, Italy, 22–24 August 2022; Volume 9, pp. 161–166. [Google Scholar]
- Yi, C.; Huang, S.; Cai, J. Joint resource allocation for device-to-device communication assisted fog computing. IEEE Trans. Mob. Comput. 2019, 20, 1076–1091. [Google Scholar] [CrossRef]
- Dai, P.; Hu, K.; Wu, X.; Xing, H.; Yu, Z. Asynchronous deep reinforcement learning for data-driven task offloading in MEC-empowered vehicular networks. In Proceedings of the IEEE INFOCOM 2021-IEEE Conference on Computer Communications, Vancouver, BC, Canada, 10–13 May 2021; pp. 1–10. [Google Scholar]
- Wu, S.; Shi, Z. Itôwave: Itô stochastic differential equation is all you need for wave generation. In Proceedings of the ICASSP 2022—2022 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Singapore, 22–27 May 2022; pp. 8422–8426. [Google Scholar]
- Fujiwara, K.; Okamoto, Y.; Kameari, A.; Ahagon, A. The Newton-Raphson method accelerated by using a line search-comparison between energy functional and residual minimization. IEEE Trans. Magn. 2005, 41, 1724–1727. [Google Scholar] [CrossRef]
- Mawi Archive. 2004. Available online: http://mawi.wide.ad.jp/ (accessed on 20 November 2023).
- Alasmar, M.; Parisis, G.; Clegg, R.G.; Zakhleniuk, N. On the Distribution of Traffic Volumes in the Internet and its Implications. In Proceedings of the IEEE INFOCOM 2019—IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; pp. 955–963. [Google Scholar]
- Alasmar, M.; Clegg, R.; Zakhleniuk, N.; Parisis, G. Internet Traffic Volumes Are Not Gaussian—They Are Log-Normal: An 18-Year Longitudinal Study With Implications for Modelling and Prediction. IEEE/ACM Trans. Netw. 2021, 29, 1266–1279. [Google Scholar] [CrossRef]
- Dai, Y.; Xu, D.; Maharjan, S.; Zhang, Y. Joint load balancing and offloading in vehicular edge computing and networks. IEEE Internet Things J. 2018, 6, 4377–4387. [Google Scholar] [CrossRef]
- You, C.; Huang, K.; Chae, H.; Kim, B.H. Energy-efficient resource allocation for mobile-edge computation offloading. IEEE Trans. Wirel. Commun. 2016, 16, 1397–1411. [Google Scholar] [CrossRef]
- Du, J.; Yu, F.R.; Chu, X.; Feng, J.; Lu, G. Computation offloading and resource allocation in vehicular networks based on dual-side cost minimization. IEEE Trans. Veh. Technol. 2018, 68, 1079–1092. [Google Scholar] [CrossRef]
- Chen, M.; Hao, Y. Task offloading for mobile edge computing in software defined ultra-dense network. IEEE J. Sel. Areas Commun. 2018, 36, 587–597. [Google Scholar] [CrossRef]
- Liu, Y.; Yu, H.; Xie, S.; Zhang, Y. Deep reinforcement learning for offloading and resource allocation in vehicle edge computing and networks. IEEE Trans. Veh. Technol. 2019, 68, 11158–11168. [Google Scholar] [CrossRef]
- Qi, Q.; Wang, J.; Ma, Z.; Sun, H.; Cao, Y.; Zhang, L.; Liao, J. Knowledge-driven service offloading decision for vehicular edge computing: A deep reinforcement learning approach. IEEE Trans. Veh. Technol. 2019, 68, 4192–4203. [Google Scholar] [CrossRef]
- Ning, Z.; Dong, P.; Wang, X.; Obaidat, M.S.; Hu, X.; Guo, L.; Guo, Y.; Huang, J.; Hu, B.; Li, Y. When deep reinforcement learning meets 5G-enabled vehicular networks: A distributed offloading framework for traffic big data. IEEE Trans. Ind. Informatics 2019, 16, 1352–1361. [Google Scholar] [CrossRef]
| Paper | Edge-Cloud | D2D | Economic | Delay | Energy | Prediction | High Workload |
|---|---|---|---|---|---|---|---|
| [5,6,10] | ✓ | ✓ | ✓ | ||||
| [7] | ✓ | ✓ | ✓ | ✓ | |||
| [8,9] | ✓ | ✓ | ✓ | ||||
| [11] | ✓ | ✓ | |||||
| [12] | ✓ | ✓ | |||||
| [13] | ✓ | ✓ | ✓ | ✓ | |||
| [14] | ✓ | ✓ | ✓ | ||||
| [15] | ✓ | ✓ | ✓ | ✓ | |||
| [16] | ✓ | ✓ | ✓ | ||||
| [17] | ✓ | ✓ | ✓ | ✓ | |||
| [18] | ✓ | ✓ | ✓ | ✓ | |||
| [19] | ✓ | ✓ | ✓ | ✓ | |||
| [20] | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [21] | ✓ | ✓ | ✓ | ✓ | |||
| Ours | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Parameter | Value |
|---|---|
| Expected task completion time | 1 s |
| Transmission bandwidth | 30 Mhz |
| Transmit power | 150 mW |
| Channel gain | 5 DB |
| ECS computing resource | 20G CPU cycles/s |
| ECS compensation price | 1 |
| ECS local task unit value | 1 |
| Acceptable risk threshold | 0.5 |
| EN computing resource | 4G CPU cycles/s |
| EN task value per second | 5 |
| Delay loss value | 1 |
| Resource purchase and pricing upper limits fmax, pmax | [99 G CPU cycles/s, 50 ] |
| Task request rate limits A, B | [0.2; 0.6] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sheng, M.; Wang, H.; Ma, M.; Sun, Y.; Zhou, R. Risk Assessment Edge Contract for Efficient Resource Allocation. Mathematics 2024, 12, 983. https://doi.org/10.3390/math12070983
Sheng M, Wang H, Ma M, Sun Y, Zhou R. Risk Assessment Edge Contract for Efficient Resource Allocation. Mathematics. 2024; 12(7):983. https://doi.org/10.3390/math12070983
Chicago/Turabian StyleSheng, Minghui, Hui Wang, Maode Ma, Yiying Sun, and Run Zhou. 2024. "Risk Assessment Edge Contract for Efficient Resource Allocation" Mathematics 12, no. 7: 983. https://doi.org/10.3390/math12070983
APA StyleSheng, M., Wang, H., Ma, M., Sun, Y., & Zhou, R. (2024). Risk Assessment Edge Contract for Efficient Resource Allocation. Mathematics, 12(7), 983. https://doi.org/10.3390/math12070983






