A Blockchain-Based Secure Sharing Scheme for Electrical Impedance Tomography Data
Abstract
1. Introduction
1.1. Our Contributions
- The EIT remote imaging system utilizes an anonymous and traceable authentication protocol. By employing pseudo-identity to safeguard user privacy, it has the capability to expose the identity of malicious nodes under certain circumstances and enhance verification efficiency through batch verification. Furthermore, this protocol enables easy implementation of the key recovery function.
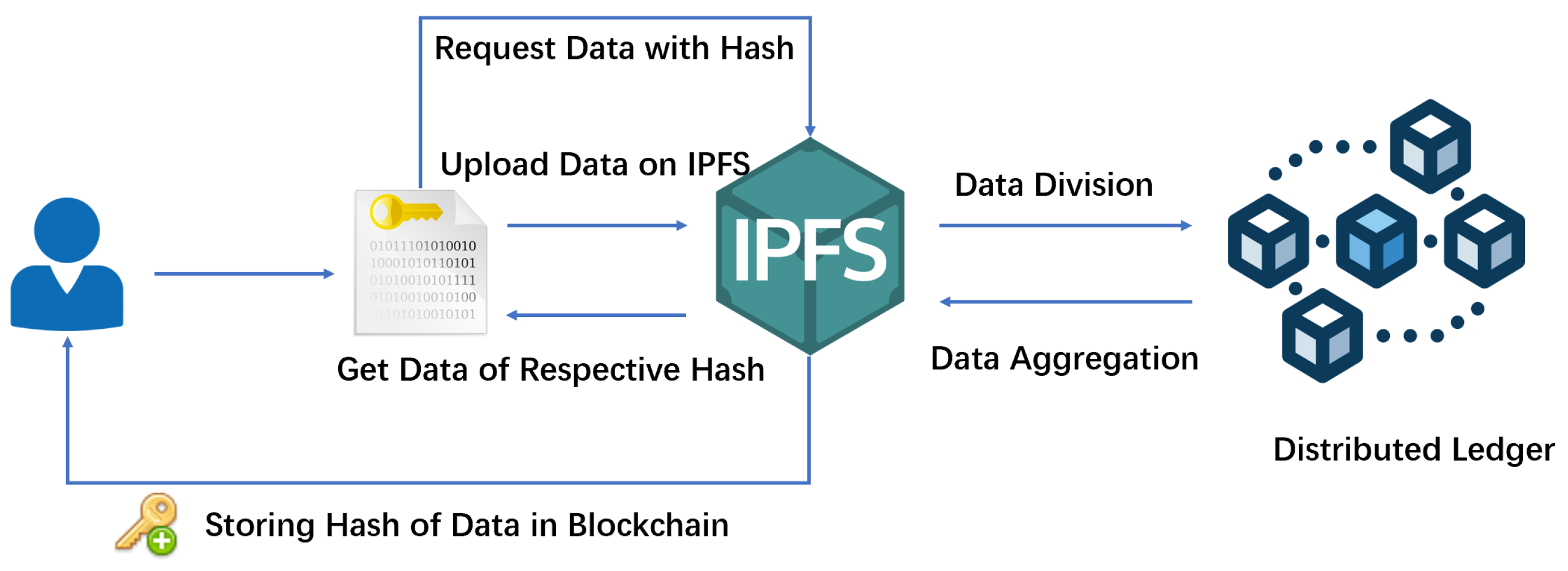
- A decentralized architecture inspired by MedRec was developed to establish a trustworthy platform for sharing and collaborating on EIT data. This system integrates the consortium chain with the IPFS to enable both on-chain and off-chain collaborative storage of EIT data. The chain only stores the IPFS hash of the EIT data, while the complete dataset is transferred to IPFS. This approach helps alleviate storage constraints on the chain and ensures secure storage of EIT data.
- The EIT data sharing system employs proxy re-encryption (PRE) technology to enforce stringent access control measures, thereby enhancing data privacy and security, to mitigate the risks of unauthorized disclosure and exploitation. A verifiable random function (VRF) is employed to generate random numbers for selecting the leader (proxy node), with the design ensuring that the random numbers generated for encryption and data access requests thwart potential collusion between semi-trusted agents and data requesters, thus preventing unauthorized access to secret information.
1.2. Related Work
1.3. Organization
2. Preliminaries
2.1. Consortium Blockchain
- (1)
- Permission-based node management: Not everyone can participate in the maintenance of the blockchain. Only authorized nodes can perform transaction verification and other related operations.
- (2)
- Higher efficiency and scalability: due to the limited number of participants, the network is able to handle higher transaction volumes, while maintaining fast processing speeds.
- (3)
- Privacy: Although transaction data are open to alliance members, they are not public to the outside world, which provides the possibility for sensitive business operations and data protection.
- (4)
- Co-governance: all alliance members jointly determine the rules, protocols, and standards of the blockchain, making the governance of the entire system more democratic and transparent.
2.2. InterPlanetary File System
2.3. Proxy Re-Encryption
3. System Architecture and Security Requirements
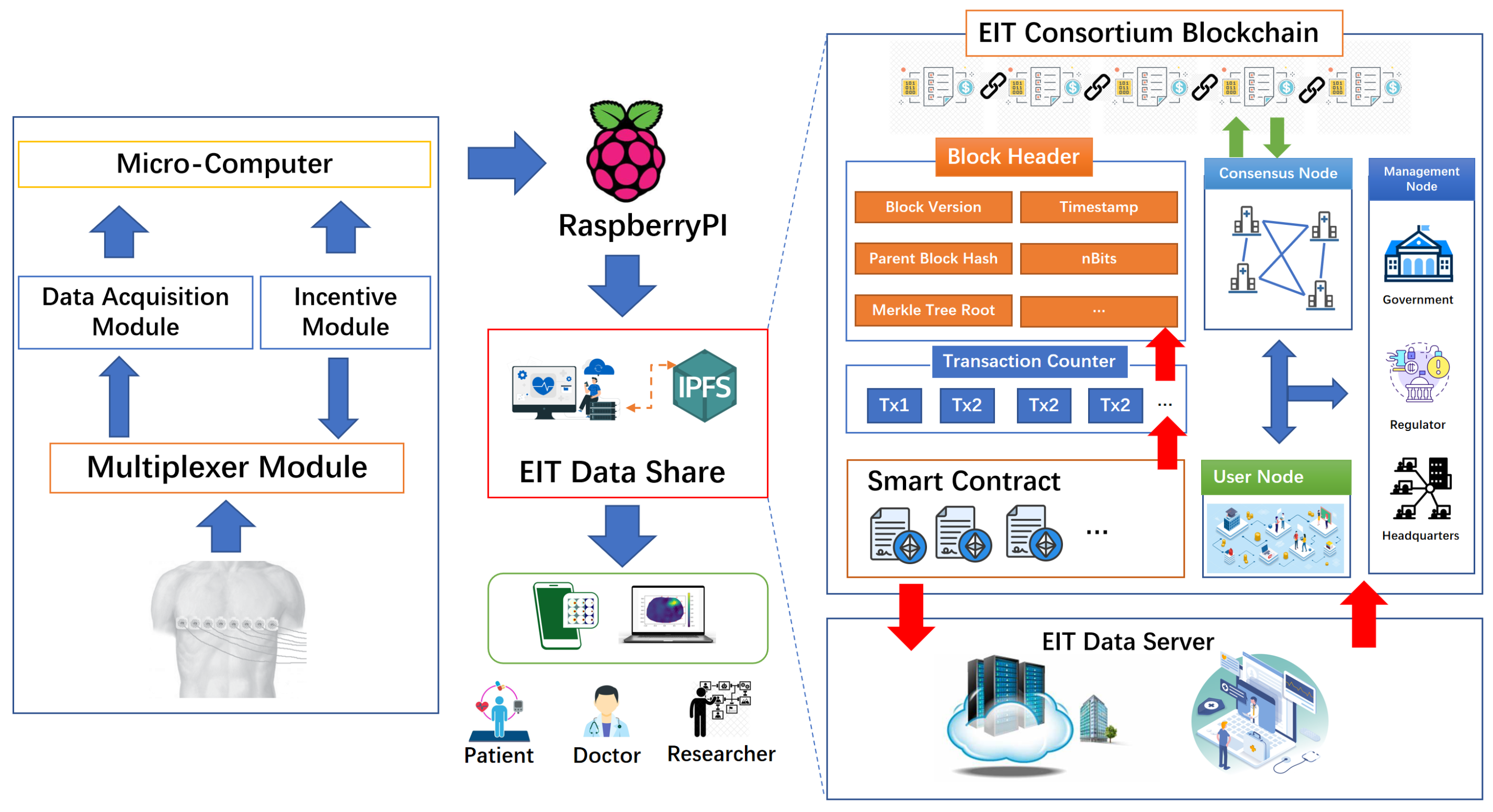
3.1. Blockchain-Based Remote EIT System Architecture
3.2. Security Requirements
- (1)
- Protection of identity privacy: EIT data often contain sensitive personal information, and users prefer to keep their identities confidential. Hence, the solution should safeguard the privacy of users’ identities.
- (2)
- Conditional identity tracking: In case of security incidents like unauthorized access, the system may need to track and identify the culprits to prevent further threats. Hence, the proposed solution should incorporate a method for selectively monitoring the genuine identities of malicious users.
- (3)
- Collusion attack prevention: As a proxy node, the consensus group leader is a semi-trusted entity who can collaborate with data requesters and potentially access EIT data without authorization. As a result, any solution implemented should be specifically crafted to prevent collusion between proxy nodes and requesters.
- (4)
- Recovery of user keys: User key recovery is a crucial aspect of EITDS, as the loss of private keys can occur for diverse reasons, such as a lost device, malware, or a forgotten password. In emergency situations where keys are lost, users should have mechanisms in place to promptly recover their keys through trusted channels, to minimize the impact on imaging. Furthermore, the finite storage capacity of blockchain systems presents a challenge as the EIT data volume grows. Insufficient storage capacity may lead to incomplete or lost data, jeopardizing data security. To tackle this issue and ensure secure storage of EIT data, it is essential to address the limitations of blockchain storage capacity.
4. EIT Data Storage and Sharing Solution
4.1. EIT Hardware Design
4.2. Initialization
- (1)
- Initialization
- (2)
- Encryption
- (3)
- Storage Phase
- (4)
- Requests, authorizations, and visits
- (5)
- Proxy Re-encryption
- (6)
- Decryption
- (7)
- Traceability
| Algorithm 1 The algorithm for tracking the malicious nodes. |
| Input: |
| , , |
| Output: |
|
| temporary = |
|
5. Theoretical Analysis
5.1. Correctness Analysis of the Scheme
5.2. Security Analysis of the Scheme
6. Complexity and Experimental Analysis
6.1. Complexity Analysis
6.2. Performance Analysis
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Li, Z.; Zhang, J.; Liu, D.; Du, J. CT Image-Guided Electrical Impedance Tomography for Medical Imaging. IEEE Trans. Med. Imaging 2020, 39, 1822–1832. [Google Scholar] [CrossRef] [PubMed]
- Adler, A.; Boyle, A. Electrical impedance tomography: Tissue Properties to image measures. IEEE Trans. Biomed. Eng. 2017, 64, 2494–2504. [Google Scholar] [PubMed]
- Newell, J.; Isaacson, D.; Mueller, J. Electrical Impedance Tomography. IEEE Trans. Med. Imaging 2002, 21, 553–554. [Google Scholar] [CrossRef]
- Brown, B. Electrical impedance tomography (EIT): A review. J. Med. Eng. Technol. 2003, 27, 97–108. [Google Scholar] [CrossRef] [PubMed]
- Adler, A.; Arnold, J.H.; Bayford, R.; Borsic, A.; Brown, B.; Dixon, P.; Faes, T.J.; Frerichs, I.; Gagnon, H.; Gärber, Y.; et al. GREIT: A unified approach to 2D linear EIT reconstruction of lung images. Physiol. Meas. 2009, 30, S35. [Google Scholar] [CrossRef]
- Kłosowski, G.; Hoła, A.; Rymarczyk, T.; Mazurek, M.; Niderla, K.; Rzemieniak, M. Using Machine Learning in Electrical Tomography for Building Energy Efficiency through Moisture Detection. Energies 2023, 16, 1818. [Google Scholar] [CrossRef]
- Enaizan, O.; Zaidan, A.A.; Alwi, N.; Zaidan, B.B.; Alsalem, M.A.; Albahri, O.; Albahri, A. Electronic medical record systems: Decision support examination framework for individual, security and privacy concerns using multi-perspective analysis. Health Technol. 2020, 10, 795–822. [Google Scholar] [CrossRef]
- Adamu, J.; Hamzah, R.; Rosli, M.M. Security issues and framework of electronic medical record: A review. Bull. Electr. Eng. Inform. 2020, 9, 565–572. [Google Scholar] [CrossRef]
- Stanfill, M.H.; Marc, D.T. Health information management: Implications of artificial intelligence on healthcare data and information management. Yearb. Med. Inform. 2019, 28, 056–064. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.B.; Smahi, A.; Amofa, S.; Zhang, X. BBDS: Blockchain-Based Data Sharing for Electronic Medical Records in Cloud Environments. Information 2017, 8, 44. [Google Scholar] [CrossRef]
- Chen, Y.; Ding, S.; Xu, Z.; Zheng, H.; Yang, S. Blockchain-Based Medical Records Secure Storage and Medical Service Framework. J. Med. Syst. 2018, 43, 1–9. [Google Scholar] [CrossRef]
- Sivan, R.; Zukarnain, Z. Security and Privacy in Cloud-Based E-Health System. Symmetry 2021, 13, 742. [Google Scholar] [CrossRef]
- Amiri, M.J.; Agrawal, D.; El Abbadi, A. Permissioned blockchains: Properties, techniques and applications. In Proceedings of the 2021 International Conference on Management of Data, Virtual Event, 20–25 June 2021; pp. 2813–2820. [Google Scholar]
- Chen, Y.; Xie, H.; Lv, K.; Wei, S.; Hu, C. DEPLEST: A blockchain-based privacy-preserving distributed database toward user behaviors in social networks. Inf. Sci. 2019, 501, 100–117. [Google Scholar] [CrossRef]
- Ren, Y.; Leng, Y.; Qi, J.; Sharma, P.K.; Tolba, A. Multiple cloud storage mechanism based on blockchain in smart homes. Future Gener. Comput. Syst. 2021, 115, 304–313. [Google Scholar] [CrossRef]
- Qiao, R.; Luo, X.Y.; Zhu, S.F.; Liu, A.D.; Wang, Q.X. Dynamic Autonomous Cross Consortium Chain Mechanism in e-Healthcare. IEEE J. Biomed. Health Inform. 2020, 24, 2157–2168. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, J.; Chen, X. Secure searchable encryption: A survey. J. Commun. Inf. Netw. 2016, 1, 52–65. [Google Scholar] [CrossRef]
- Xu, M.; Liu, S.; Yu, D.; Cheng, X.; Guo, S.; Yu, J. Cloudchain: A cloud blockchain using shared memory consensus and rdma. IEEE Trans. Comput. 2022, 71, 3242–3253. [Google Scholar] [CrossRef]
- Wu, Y.; Cegielski, C.G.; Hazen, B.T.; Hall, D.J. Cloud computing in support of supply chain information system infrastructure: Understanding when to go to the cloud. J. Supply Chain Manag. 2013, 49, 25–41. [Google Scholar] [CrossRef]
- Liu, X.; Wang, Z.; Jin, C.; Li, F.; Li, G. A blockchain-based medical data sharing and protection scheme. IEEE Access 2019, 7, 118943–118953. [Google Scholar] [CrossRef]
- Tanwar, S.; Parekh, K.; Evans, R. Blockchain-based electronic healthcare record system for healthcare 4.0 applications. J. Inf. Secur. Appl. 2020, 50, 102407. [Google Scholar] [CrossRef]
- Du, M.; Chen, Q.; Chen, J.; Ma, X. An optimized consortium blockchain for medical information sharing. IEEE Trans. Eng. Manag. 2020, 68, 1677–1689. [Google Scholar] [CrossRef]
- Liu, J.; Jiang, W.; Sun, R.; Bashir, A.K.; Alshehri, M.D.; Hua, Q.; Yu, K. Conditional Anonymous Remote Healthcare Data Sharing Over Blockchain. IEEE J. Biomed. Health Inform. 2023, 27, 2231–2242. [Google Scholar] [CrossRef] [PubMed]
- Tandon, A.; Dhir, A.; Islam, A.N.; Mäntymäki, M. Blockchain in healthcare: A systematic literature review, synthesizing framework and future research agenda. Comput. Ind. 2020, 122, 103290. [Google Scholar] [CrossRef]
- Xi, P.; Zhang, X.; Wang, L.; Liu, W.; Peng, S. A review of Blockchain-based secure sharing of healthcare data. Appl. Sci. 2022, 12, 7912. [Google Scholar] [CrossRef]
- Eluubek kyzy, I.; Song, H.; Vajdi, A.; Wang, Y.; Zhou, J. Blockchain for consortium: A practical paradigm in agricultural supply chain system. Expert Syst. Appl. 2021, 184, 115425. [Google Scholar] [CrossRef]
- Triulzi, I.; Antonel, A.; Rossi, E.; Turchetti, G. Public Hospital Supply Chain: Current View And Critical Issues In Italy. Value Health 2017, 20, A515–A516. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017. [Google Scholar]
- Sagirlar, G.; Carminati, B.; Ferrari, E.; Sheehan, J.D.; Ragnoli, E. Hybrid-iot: Hybrid blockchain architecture for internet of things-pow sub-blockchains. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1007–1016. [Google Scholar]
- Nyaletey, E.; Parizi, R.M.; Zhang, Q.; Choo, K.K.R. BlockIPFS-blockchain-enabled interplanetary file system for forensic and trusted data traceability. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 18–25. [Google Scholar]
- Muralidharan, S.; Ko, H. An InterPlanetary file system (IPFS) based IoT framework. In Proceedings of the 2019 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 11–13 January 2019; pp. 1–2. [Google Scholar]
- Batchu, S.; Henry, O.S.; Hakim, A.A. A novel decentralized model for storing and sharing neuroimaging data using ethereum blockchain and the interplanetary file system. Int. J. Inf. Technol. 2021, 13, 2145–2151. [Google Scholar] [CrossRef]
- Dunphy, P.; Petitcolas, F.A. A first look at identity management schemes on the blockchain. IEEE Secur. Priv. 2018, 16, 20–29. [Google Scholar] [CrossRef]
- Ateniese, G.; Fu, K.; Green, M.; Hohenberger, S. Improved Proxy Re-Encryption Schemes with Applications to Secure Distributed Storage. ACM Trans. Inf. Syst. Secur. (TISSEC) 2006, 9, 1–30. [Google Scholar] [CrossRef]
- Liang, K.; Au, M.H.; Liu, J.K.; Susilo, W.; Wong, D.S.; Yang, G.; Yu, Y.; Yang, A. A secure and efficient Ciphertext-Policy Attribute-Based Proxy Re-Encryption for cloud data sharing. Future Gener. Comput. Syst. 2015, 52, 95–108. [Google Scholar] [CrossRef]
- Shabtai, A.; Menahem, E.; Elovici, Y. F-Sign: Automatic, Function-Based Signature Generation for Malware. Trans. Syst. Man Cybern. Part C 2011, 41, 494–508. [Google Scholar] [CrossRef]
- Wang, Y.; Ding, Y.; Wu, Q.; Wei, Y.; Qin, B.; Wang, H. Privacy-Preserving Cloud-Based Road Condition Monitoring With Source Authentication in VANETs. IEEE Trans. Inf. Forensics Secur. 2019, 14, 1779–1790. [Google Scholar] [CrossRef]
- Zeng, P.; Choo, K.K.R. A New Kind of Conditional Proxy Re-Encryption for Secure Cloud Storage. IEEE Access 2018, 6, 70017–70024. [Google Scholar] [CrossRef]
- Ge, C.; Liu, Z.; Xia, J.; Fang, L. Revocable identity-based broadcast proxy re-encryption for data sharing in clouds. IEEE Trans. Dependable Secur. Comput. 2019, 18, 1214–1226. [Google Scholar] [CrossRef]
- Agyekum, K.O.B.O.; Xia, Q.; Sifah, E.B.; Cobblah, C.N.A.; Xia, H.; Gao, J. A proxy re-encryption approach to secure data sharing in the internet of things based on blockchain. IEEE Syst. J. 2021, 16, 1685–1696. [Google Scholar] [CrossRef]
- Zheng, X.; Zhou, Y.; Ye, Y.; Li, F. A cloud data deduplication scheme based on certificateless proxy re-encryption. J. Syst. Archit. 2020, 102, 101666. [Google Scholar] [CrossRef]



| Decentralization | Throughput | Cost | Scalability | |
|---|---|---|---|---|
| Consortium Chain | medium | medium | medium | Great |
| Public chain | high | low | high | Poor |
| Private chain | low | high | low | Great |
| Hybrid chain | - | - | low | Great |
| Scheme | [38] | [39] | [40] | [41] | Ours |
|---|---|---|---|---|---|
| Encrypt | 2Exp + 2Pair | 8Exp | 4Exp | 3Exp + 1Pair | 3Exp + 1Pair |
| ReKeyGen | 2Exp | 2Exp | 2Exp | 5Exp | 4Exp |
| ReEncrypt | 1Exp + 1Pair | 2Exp + 5Pair | 1Exp + 2Pair | 2Exp + 4Pair | 4Exp + 1Pair |
| Self-Decrypt | 1Pair | 3Exp + 3Pair | – | – | 4Exp + 1Pair |
| ReDecrypt | 1Exp + 2Pair | 2Exp + 2Pair | 1Exp + 3Pair | 2Exp + 4Pair | 8Exp |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, R.; Xu, C.; Zhu, Z.; Mo, W. A Blockchain-Based Secure Sharing Scheme for Electrical Impedance Tomography Data. Mathematics 2024, 12, 1120. https://doi.org/10.3390/math12071120
Zhao R, Xu C, Zhu Z, Mo W. A Blockchain-Based Secure Sharing Scheme for Electrical Impedance Tomography Data. Mathematics. 2024; 12(7):1120. https://doi.org/10.3390/math12071120
Chicago/Turabian StyleZhao, Ruwen, Chuanpei Xu, Zhibin Zhu, and Wei Mo. 2024. "A Blockchain-Based Secure Sharing Scheme for Electrical Impedance Tomography Data" Mathematics 12, no. 7: 1120. https://doi.org/10.3390/math12071120
APA StyleZhao, R., Xu, C., Zhu, Z., & Mo, W. (2024). A Blockchain-Based Secure Sharing Scheme for Electrical Impedance Tomography Data. Mathematics, 12(7), 1120. https://doi.org/10.3390/math12071120







