1. Introduction
With the rapid spread of the Internet, the dissemination of information is easier than ever before, which has led to serious copyright infringement issues, such as unauthorized copying [
1], distribution [
2] and illegal tampering with digital works [
3]. Therefore, in order to improve the security of Internet information, copyright protection becomes very important. The most common infringement problem is mainly the infringement of images. Image infringement will have a serious impact on the copyright party, especially important medical or military-related images. If they are tampered with or illegally used by criminals, they will have very important consequences. Therefore, in order to ensure the safe development of the information society, the security protection of digital images is urgent. As one of the widely used protection technologies, the watermarking method has been applied in many fields of multimedia copyright protection. As a common information embedding technology, it plays an important role in protecting image, video and audio information.
The embedding methods of image watermarking can be divided into many different types. According to the embedding process of watermark, the watermark can be divided into spatial domain watermark [
4] and frequency domain watermark [
5]. Spatial domain watermark is mainly embedded by directly changing the pixels of the cover image, such as the least significant bit (LSB) algorithm. The spatial domain watermark has low computational complexity and high operation efficiency, but the robustness is poor. Frequency domain watermarking is mainly realized by some commonly used image transformations. The pixels of the image are transformed into frequency coefficients by transformation, and then the watermark information is embedded in the frequency coefficients. The frequency domain algorithm greatly improves the robustness of the watermark, but the computational complexity is usually higher and the operation time is longer. Fourier transform (DFT), discrete wavelet transform (DWT), discrete cosine transform (DCT), singular value decomposition (SVD) and so on are commonly used frequency domain watermarking schemes.
Robustness, imperceptibility, embedding capacity and security are the four core indicators to evaluate the performance of image watermarking algorithms. There is often a trade-off relationship between these indicators, that is, in practical applications, it is difficult to optimize these indicators at the same time. Alpha hybrid technology [
6] can be used to solve this problem. By finely adjusting the embedding strength, a relatively balanced state can be found between these four evaluation indicators, so as to ensure certain robustness and security while minimizing the imperceptibility of the watermark. By adaptively calculating the embedding strength, the robustness of the watermark image can be significantly enhanced. In contrast, a fixed embedding strength may cause the watermark to be more easily damaged. Therefore, adaptive computing provides a more effective way to improve the performance of watermarking [
7]. In the face of geometric attacks, the watermarking method based on wavelet transform shows a certain degree of vulnerability [
8], but the extraction of image geometric features by matrix decomposition can overcome this limitation. The combination of wavelet transform and matrix decomposition is often used for watermark embedding, which aims to prevent image tampering and resist geometric attacks. In addition, due to the concentration of DCT coefficients in the low-frequency part of the image, the image can still maintain good stability when experiencing compression, clipping, rotation and other operations [
9]. In addition, color space also plays an important role in image watermarking technology. In particular, the
YCbCr color space separates the brightness information (Y component) from the chromaticity information (Cb and Cr components). Among them, the
Y component expresses the brightness of the image, while the Cb and Cr components carry the color information of the image. This separation makes the watermark embedding process more targeted; in particular, the brightness information to hide the watermark is more effective so as to ensure that the watermark is embedded at the same time and as far as possible to reduce the overall image quality of the potential impact [
10].
Hajjaji et al. [
11] proposed an efficient hardware-based image watermarking scheme based on Haar discrete wavelet transform (DWT). The system uses DWT technology to subtly embed key information fragments into digital content with excellent robustness, and also designs an ultra-large-scale integrated architecture based on FPGA. This architecture is specifically optimized for watermarking algorithms to accelerate the media authentication process. Hamidi et al. [
12] proposed an innovative hybrid robust blind image watermarking technology, which combines the advantages of DFT-DCT and Arnold transform, and significantly enhances the imperceptibility and robustness of the watermark. In the embedding process, the technology makes specific adjustments to the DCT coefficients of the intermediate band through the key. In order to ensure the security of the watermark, Arnold transform is used to encrypt the watermark before embedding. This method enables the watermark to maintain a high degree of invisibility in the face of multiple attacks, thereby effectively protecting the image content.
Li et al. [
13] proposed a reversible watermarking scheme based on wavelet transform. The cover image is divided into blocks, each block is transformed by wavelet transform as the carrier signal, and two different chaotic maps are used for encryption, which improves the security of the watermark image. Hsu et al. [
14] proposed a new adaptive blind watermarking technique for deep forgery detection. This technique embeds the deep forgery detection information into the image, extracts the image without additional information and verifies the authenticity of the image. The scheme uses a combination of mixed modulation and partial symbol change mean to embed a set of coefficients. These coefficients not only maintain the image quality but also enhance the robustness against attacks. Dey et al. [
15] designed a blind watermarking method for medical image authentication. This method embeds the patient’s information into the computer’s scanned copy in digital form, and applies the SHA-512 hash algorithm to process the watermark. The generated hash value is embedded into the digital copy of the scanned image to ensure the authenticity and integrity of the scanned copy.
Bhinder et al. [
16] proposed an adaptive image watermarking technique that combines discrete wavelet transform (DWT) and fast Walsh–Hadamard transform (FWHT). In this method, the cover image is first divided into blocks, and then the entropy value of each block is calculated. The watermark embedding factor is determined by the statistical characteristics of the transform coefficients in the high entropy block (such as mean, standard deviation, entropy and kurtosis), so as to realize the effective embedding of the watermark. Hua et al. [
17] proposed an adaptive watermarking scheme for remote sensing images based on information complexity. The scheme first converts the remote sensing image from RGB color space to
YCbCr color space, and performs two-stage discrete wavelet transform (DWT) on the brightness component. Subsequently, the scheme selects the high-frequency coefficients of the low-frequency component as the embedding area of the watermark. At the same time, in order to determine the best watermark embedding position, the image is further divided into blocks, and the entropy value of each sub-block is calculated. Finally, the sub-block with the largest entropy value is selected as the watermark embedding target. Su et al. [
18] proposed a robust color image watermarking method combining spatial domain and LU decomposition depth fusion. This method embeds the color watermark image into the color cover image by adjusting the high-correlation elements in the matrix L, and can realize the correction function of the geometric attack. Yuan et al. [
19] designed a robust feature watermarking algorithm for encrypted medical images, which combines multi-level discrete wavelet transform (DWT), chrysanthemum descriptor and discrete cosine transform (DCT). In order to enhance the security of the image, logistic mapping is also used to encrypt the original medical image.
The main contributions of this paper are as follows:
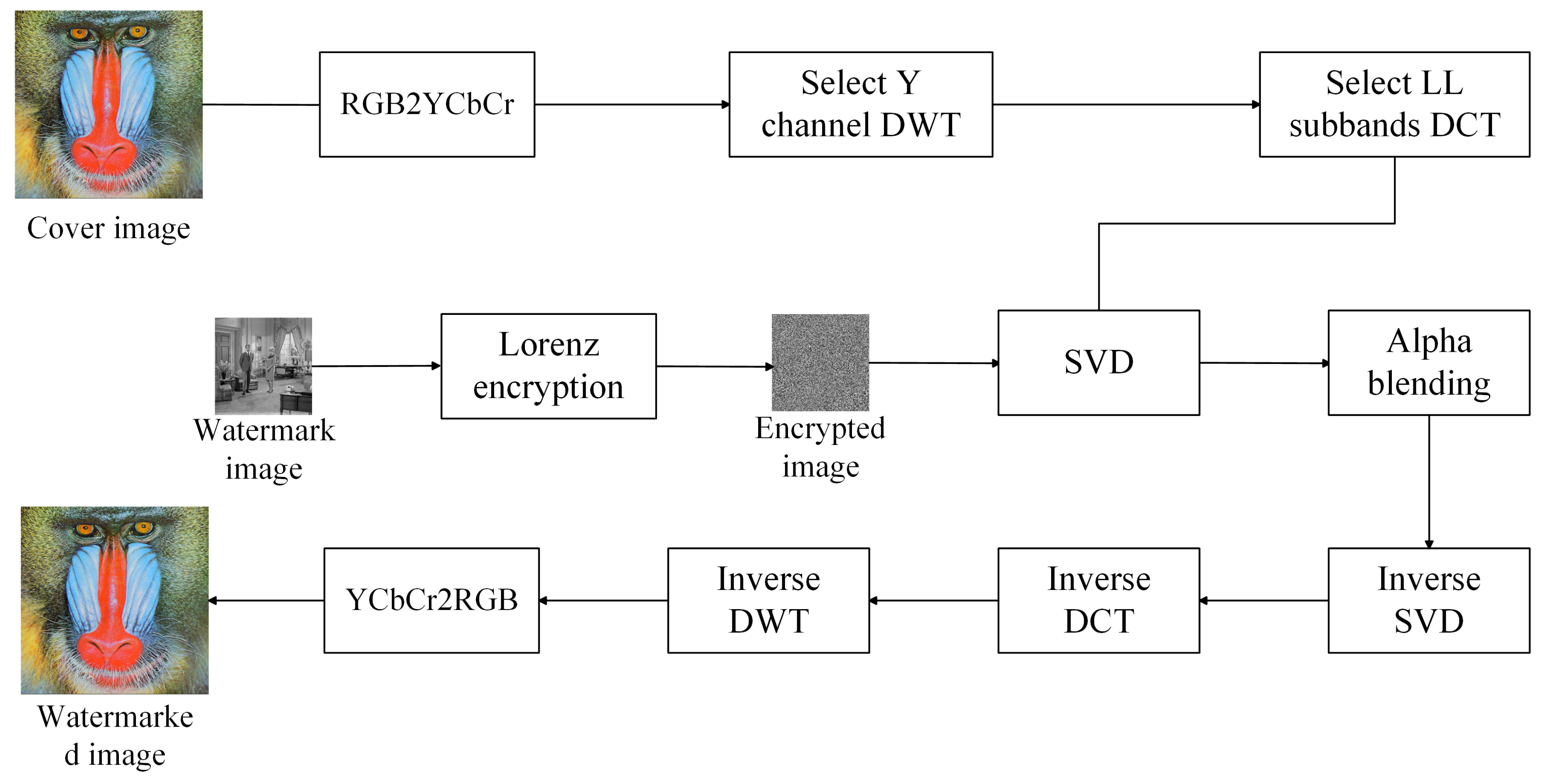
A large-capacity robust image watermarking scheme based on DWT-DCT-SVD is proposed;
The security of the watermarking algorithm is improved by encrypting Lorenz hyperchaotic map;
In the YCbCr color space, the Bhattacharyya distance between the cover image and the watermark image is used to adaptively calculate the embedding factor, which solves the balance between the robustness and imperceptibility of the watermark.
The rest of this article is structured as follows.
Section 2 introduces some techniques used in this paper, including Lorenz hyperchaotic system, discrete wavelet transform, discrete cosine transform and singular value decomposition.
Section 3 introduces the watermarking scheme proposed in this paper.
Section 4 is the experimental results of this scheme.
Section 5 summarizes the work of this paper.
4. Experimental Results and Analysis
In this section, six color cover images with a resolution of
and a gray watermark with a resolution of
are used to verify the performance of the proposed scheme.
Figure 6 shows the cover image and watermark image used in this paper. All the image data used in this paper are from USC-SIPI: Signal and Image Processing Institute, University of Southern California (
https://sipi.usc.edu/database/) (accessed on 1 June 2024). The experiment is carried out in MATLAB (R2020b) environment on Intel (R) Core (TM) i5-12400F CPU 2.50 GHz, 16.0 GB RAM computer. The peak signal-to-noise ratio (PSNR) and structural similarity (SSIM) are used to measure the imperceptibility of the proposed scheme, while the normalized correlation coefficient (NCC) and bit error rate (BER) are used to measure the robustness of the proposed scheme. The embedding factor is calculated by using Equation (
10). In this paper, the value of
is 0.1.
Table 1 shows the embedding factor of each cover image.
4.1. Invisibility Analysis
Invisibility means that the similarity between the watermarked image and the original cover image is difficult to identify. This slight change is almost invisible to the human eye. In this study, two key indicators, PSNR and SSIM, were selected to evaluate the watermarking methods applied on six different cover images. Among them, PSNR is used to measure the transparency of the watermark image and the original cover image in visual perception, while SSIM is responsible for evaluating the contrast, brightness and structural similarity of the image. When the PSNR value exceeds 30 dB, it means that the watermark image has an acceptable visual quality and maintains a high degree of similarity with the original image. When the SSIM value is close to 1, it indicates that the watermark image has reached a high level of perceptual quality [
26].
Figure 7 shows these cover images with watermarks and the successfully extracted watermarks.
The PSNR, MSE and SSIM of different cover images are shown in
Table 2. The average PSNR and SSIM of the scheme are 45.9382 dB and 0.9986, respectively. It can be seen that the scheme has good imperceptibility.
Image histogram is a tool similar to PSNR, which is widely used to measure the difference between the cover image and the watermarked image to evaluate the influence of the watermark on the original cover image. The image histogram intuitively shows the distribution of different pixel values in the image, thus revealing the core features of the image. By comparing the histograms of the two, we can more reliably judge the similarity between images, which also shows that the watermark embedding method does not significantly change the original characteristics of the cover image.
Figure 8 intuitively shows the histogram comparison between the original cover image and the watermarked image. It can be observed from the figure that there is almost no significant change in the histogram before and after watermark embedding, which fully shows the excellent performance of our scheme in imperceptibility.
4.2. Robustness Analysis
In this section, we focus on evaluating the robustness of the proposed scheme against various attacks. Based on this, we use three main metrics: PSNR, NCC and BER. These three indicators play a crucial role in evaluating the performance of the scheme. PSNR is used to show the perceptual transparency of the watermark image relative to the original cover image. The NCC value directly reflects the anti-attack ability of the scheme. The higher the value is, the stronger the resistance of the scheme to the attack is. The decrease in bit error rate means that the degree of watermark distortion is smaller, which is very important in maintaining the integrity of watermark information.
In this paper, various attacks are comprehensively tested. These attacks are mainly divided into four categories: noise attack, enhanced technology attack, geometric transformation attack and compression attack. In the experiment, we compare the attacked cover image and the successfully restored watermark. The comparison results are shown in
Figure 9 and
Figure 10, where [a–l] represent different types of attacks, respectively: no attack, salt and pepper noise (v = 0.05), Gaussian noise (m = 0, v = 0.05), speckle noise (v = 0.05), sharpening, Gaussian filtering, mean filtering, rotation 10°, vertical flipping, cropping 20%, JPEG compression (QF = 90), and JPEG 2000 compression (QF = 90). These attacks represent a variety of situations that may be encountered in the real world, and our scheme has been thoroughly tested to ensure robustness in all situations.
Through our experimental results, we can clearly see that our scheme can effectively resist other attacks, except rotation and cropping attacks, and the extracted watermark image has only slight distortion. This shows that our scheme has high robustness and can effectively deal with attacks in various situations in the real world, thus protecting the integrity and stability of watermark information.
Table 3 describes the PSNR of the attacked watermark cover image,
Table 4 describes the PSNR of the watermark image extracted from different attacks,
Table 5 describes the NCC of the watermark image extracted from different attacks, and
Table 6 describes the BER of the watermark image extracted from different attacks. Under the condition of no attack, the average PSNR of this method is 45.6849 dB, the average NCC of this method is 1, and the average bit error rate is 0. And under various attacks, the average NCC and average BER can maintain a good level.
Table 7 describes the robustness comparison results with other watermarking schemes. Taking the Baboon cover image as an example, it can be seen from
Table 7 that the watermarking scheme in this paper can effectively extract the watermark image in the face of various attacks.
It can be seen from
Table 3 that when the cover image is attacked by different attacks, there is a big difference between the PSNR of the attacked image and the original image, and the quality of the image is significantly reduced, but the watermark image extracted from it can still maintain high quality. The average PSNR of the extracted watermark can maintain 20 dB, indicating that the watermark scheme in this paper has good robustness. From the comparison with other schemes in
Table 7, it can also be seen that most of the NCC values of the schemes in this paper are higher than other schemes, indicating that the scheme in this paper has higher robustness.
4.3. Embedding Capacity Analysis
The embedding capacity is a measure of the number of bits of information that can be inserted into the cover image [
31]. In this scheme, a color cover image with a size of 512 × 512 is used, and a grayscale watermark image with a size of 256 × 256 is used. Therefore, the embedding capacity of the scheme is (256 × 256 × 8) / (512 × 512 × 3) = 0.6667 bpp. Most of the other watermarking schemes use 64 × 64 or 128 × 128 watermarks, and the embedding capacity is 0.0417 and 0.1667, respectively. The embedding capacity is low, and the scheme in this paper has high embedding capacity.
4.4. Security Analysis
The security of the image watermark is a key point that the watermark algorithm needs to consider. A robust algorithm needs to ensure that illegal personnel cannot extract the watermark image from the cover image. In this paper, we use Lorenz hyperchaotic map encryption to protect the watermark. Even if the attacker extracts the watermark, only the encrypted image is obtained. Lorenz chaotic map has good chaotic properties, including sensitivity dependence on initial conditions, long-term unpredictability, etc. A small change in initial conditions can cause a significant deviation from the system trajectory, making it form a complex trajectory in the phase space. These characteristics ensure that the generated chaotic sequence has a high degree of randomness and improve the strength of watermark encryption. In addition, the scheme has good robustness. In the face of some attacks, the watermark image can be completely extracted, which greatly improves the security of the watermark.
5. Conclusions
In watermarking technology, it is necessary to make a trade-off between imperceptibility, robustness and embedding capacity, but many watermarking schemes ignore this problem. In order to solve this problem, we propose an adaptive color image watermarking scheme based on DWT-DCT-SVD. The embedding factor is adaptively determined by calculating the Bhattacharyya distance between the cover image and the watermark image. At the same time, in order to enhance the security of the watermark, we use Lorenz hyperchaotic mapping to encrypt the watermark image. Experimental results show that our scheme achieves a balance between imperceptibility, robustness and embedding capacity. The digital watermarking of color images is widely used, including digital copyright protection, security authentication, information hiding, digital media traceability and other fields. Therefore, the research and application of digital color image watermarking technology has become a very important topic in the field of digital information security. The future research direction of this study to improve on our findings mainly combines image watermarking with intelligent optimization algorithm or deep learning, which can search for better embedding factors through intelligent optimization. At the same time, the combination of deep learning and image watermarking will greatly improve the performance and application potential of watermarking.