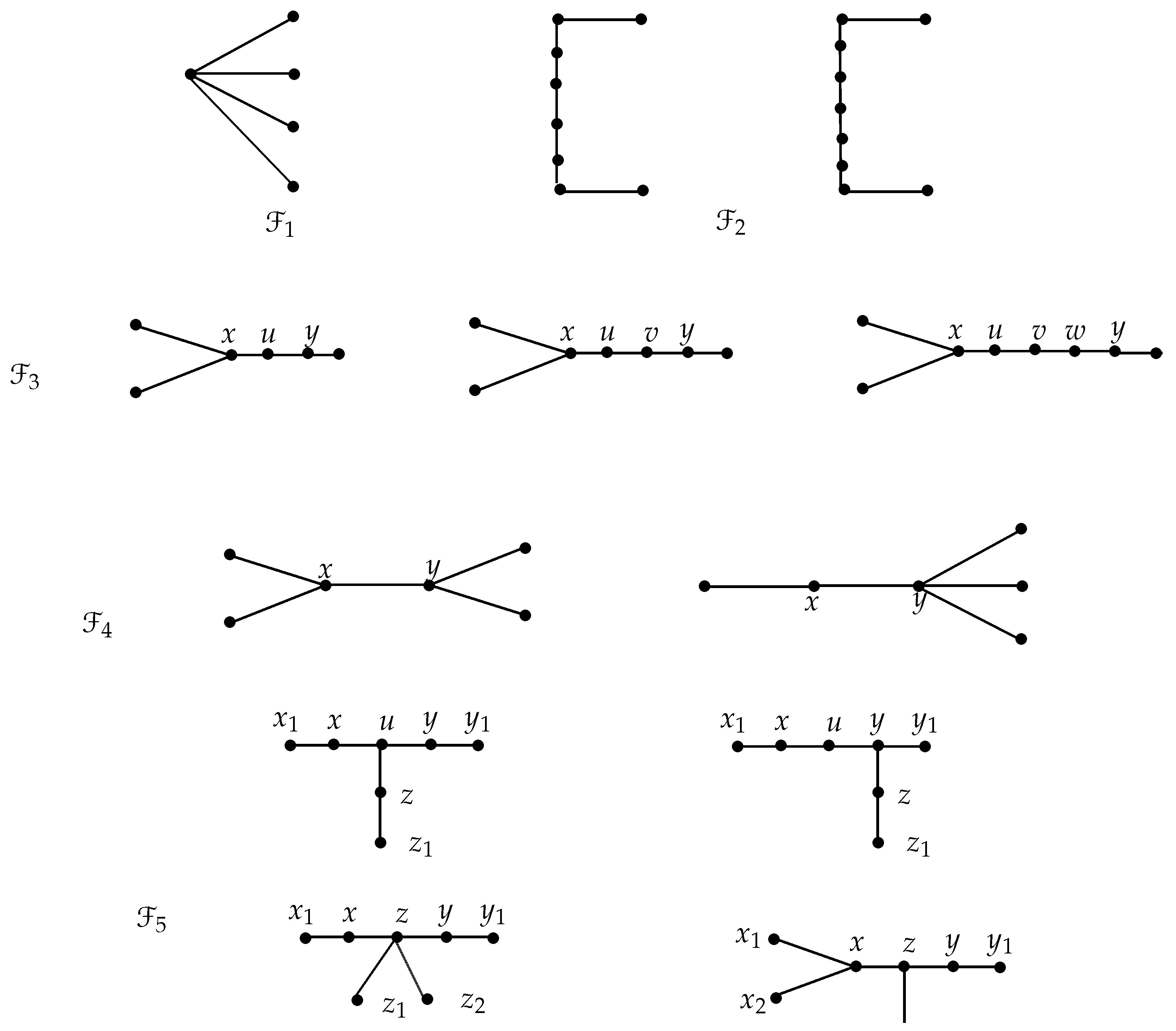1. Introduction
The graphs examined in this study are finite, simple, undirected, without loops, and with multiple edges. Let
be a graph and let
. The number of vertices adjacent to
v is called the
degree of
v and is denoted by
. The
open neighborhood of
v is defined as
. The
closed neighborhood of
v is defined as
. Let
and
. The
private neighborhood is defined by
. The
external private neighborhood of a vertex is defined as
\
X and
, also represented by
. A connected acyclic graph is called a
tree. A tree with a vertex of full degree is referred to as a
star and is denoted by
, where
k is the degree of the full-degree vertex. A vertex of degree one is known as a
pendant vertex. A neighboring vertex to a pendant vertex is referred to as its
support vertex. A
caterpillar is a tree in which the removal of all its pendant vertices results in a path. The graph obtained by removing an edge
e from a graph
G is denoted by
and this is called
edge deletion. A path on
n vertices and a cycle on
n vertices are denoted
and
, respectively. The reader may refer to [
1] for notation and terminology that is not defined here.
Let
If every vertex that is not in
D is adjacent to a vertex that is in
D, then
D is a
dominating set. The minimum cardinality of a dominating set in
G is its
domination number of
G. A well-researched graph parameter in the literature is domination, we refer the reader to the book [
2] and its references for more details.
Sampathkumar et al. [
3] introduced the strong domination number in 1996. If for every
\
D there is a vertex
with
and
, then a set
D of vertices in a graph
G is a
strong dominating set. The minimum cardinality of a strong dominating set in
G is its
strong domination number of
G. The results of a study on strong domination in graphs were presented in [
4,
5]. The concept of strong domination has, thus, been extensively studied in the literature. In [
6], Cockayne et al. introduced the concept of secure domination. A dominating set
D is called a
secure dominating set (sds) if for every
\
D there exists some
such that
u and
v are adjacent and
\
. Here,
u is called a
defender of
v. The secure domination number
of
G is the minimum cardinality of a secure dominating set in
G. Additional findings regarding this parameter can be found in [
7,
8,
9,
10].
Inspired by the ideas of secure and strong domination, it is logical to explore both of these concepts further, beginning with the idea of strong secure domination as put forth by Annaal Mercy et al. [
11]. A secure dominating set
D is called a
strong secure dominating set (ssds) if for every
\
D there exists
such that
u and
v are adjacent and
. The corresponding
u is called a
strong neighbor of
v. The minimum cardinality of an ssds is called a
strong secure domination number and is denoted by
. Note that
if and only if
G is a totally disconnected graph.
Why should such a domination in graphs be taken into consideration? This is the scenario: A computer network consists of a number of linked devices, each of which has connections to other devices. Consider a scenario where a network administrator must set up access control lists (ACLs) to manage network traffic flow. The following guidelines are what the administrator wishes to implement:
Each device not explicitly allowed access to certain network resources should have at least one connected device that is granted access, ensuring connectivity and efficient data transmission.
If a device is persistent about using a particular resource and applies pressure to be allowed access, it can be swapped out for a connected device that has already been given permission, as long as the new configuration keeps the connectivity requirement from the initial condition.
It is recommended that any device that is not explicitly granted access to specific network resources be connected directly to a device that has higher access privileges. In this way, a device with greater permissions will always be accessible for potential administrative or troubleshooting needs. This implies that devices with limited access are purposefully connected to devices with more expansive access capabilities. This makes network management easier and guarantees that troubleshooting tasks can be completed successfully, which improves the overall security and resilience of the network.
The goal of the network administrator is to reduce the size of the access control lists while optimizing resource allocation and network security. This strategy is consistent with the strong secure dominating theory, which maintains network connectivity while attending to the needs of individual device access. This idea is useful in a variety of contexts, including the setting up of ATMs in multiple locations, the distribution of secret keys in cryptography, military operations, and commercial endeavors.
3. Trees with Secure Domination Number at Most 4
In this section, we give a necessary and sufficient condition for a tree to have a secure domination number less than or equal to 4. A survey on the constructive characterization of trees using different types of domination numbers was recently provided by the authors in [
13].
Let us first review the results for the trees whose strong secure dominance number is either 2 or 3.
Proposition 3 ([
11])
. Let T be a tree. Then:- (i).
if and only if .
- (ii).
if and only if T is either or .
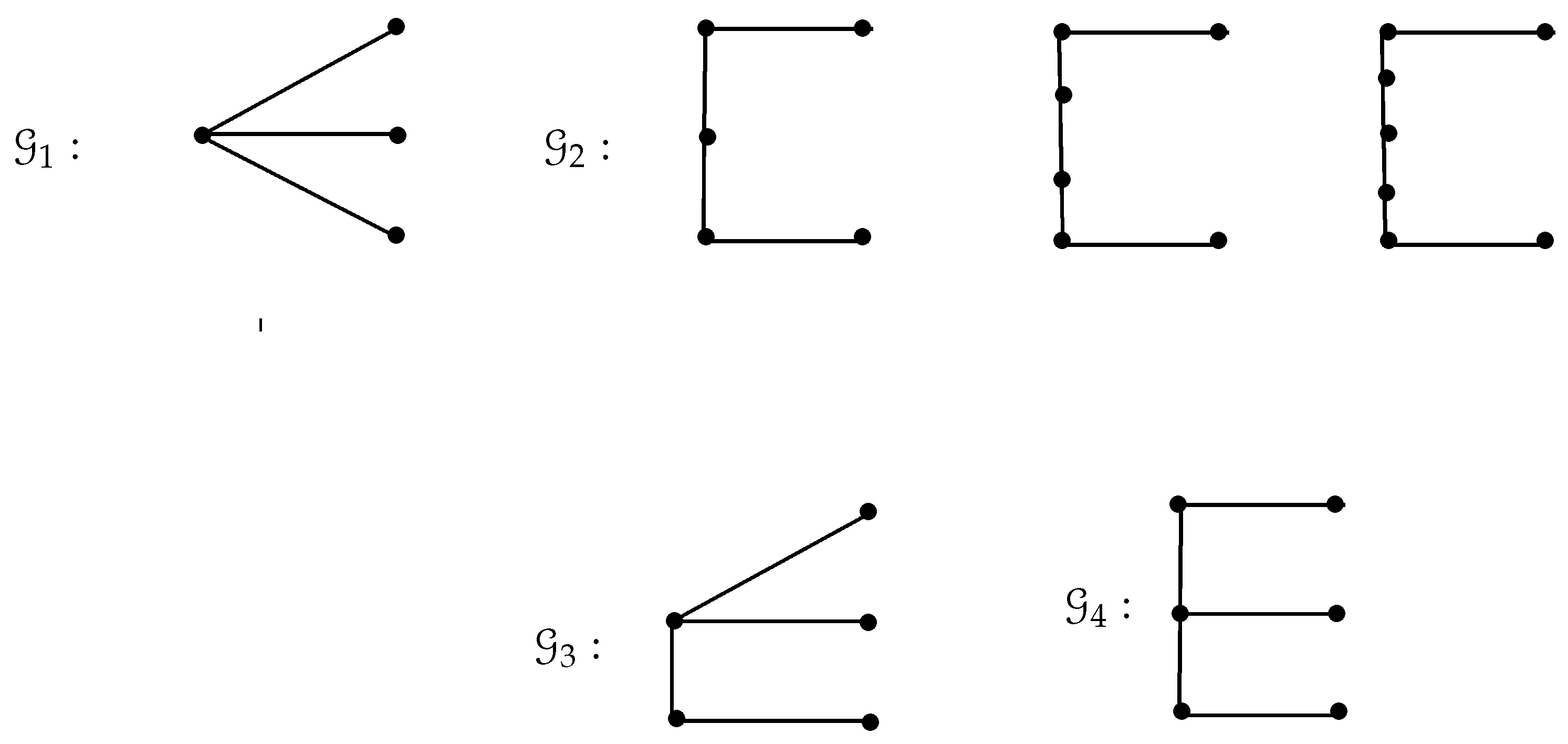
Let and be two stars. A path of length t connects the centers of and . The resulting graph is represented by .
The following theorem characterize all trees whose strong secure dominance number is 3. In what follows, the graphs’
s are given in
Figure 1.
Theorem 2. Let T be a tree. Then, if and only if .
Proof. Assume that . Then, by Proposition 2, T can have at most three support vertices. Suppose T has exactly one support vertex. Then, the support vertex must have 3 pendant neighbors and so . Assume that T has exactly two support vertices. Then, T is , where and . By Proposition 2, we have . If , then T is a path. Since , we obtain ; these graphs are listed in . If , without loss of generality, assume that and , then . When T has exactly three support vertices, T is isomorphic to the graph . The converse is obvious. □
The following theorem characterize all trees whose strong secure dominance number is 4. In what follows, the graphs’
s are given in
Figure 2 and
Figure 3.
Theorem 3. Let T be a tree. Then, if and only if .
Proof. Assume that . Let X be a minimum strong secure dominating set of T. Then, by Proposition 2, T has at most four support vertices. Suppose T has exactly one support vertex. Then, T is a star graph. Since , we have . Suppose T has exactly two support vertices. Obviously T becomes , where and . By Proposition 2, we have If , then T is a path. In this case, T is isomorphic to a graph in . Let . Without loss of generality, let and . Let x and y be the two support vertices of T. Since , x and y are connected by a path of length at most 4. In this case, T is isomorphic to a graph in . If , then and or and . In this case, T is isomorphic to a tree in . Next, we assume that T has exactly three support vertices, say, , and z. By Proposition 2, and the number of pendant vertices is at most 4. Without loss of generality, let us assume that the path between x and y is the longest. By Proposition 1, no vertex in the path has either x or y as defender, with respect to In fact, it cannot have z as a defender. Also, the length of the path between x and y is at most 4. Therefore, ; otherwise T becomes a tree with two support vertices, a contradiction. Let . In this case T is isomorphic to a graph in . When there exist two vertices u and v between x and y. In this case, T is isomorphic to a graph in . When T is isomorphic to a graph in . If T has exactly four support vertices, then . The converse is obvious. □
4. Bounds on the Strong Secure Domination Number of Graphs
In this section, we provide an upper and lower bound for the strong secure domination number of the rooted tree and the vertex gluing of two graphs.
A tree is said to be a rooted tree [
14] if one of the vertices is distinguished as the root from the remaining. In what follows, we consider a rooted tree
, where a root vertex is of degree
ℓ and all the other vertices except the support vertices are of degree
k, where
. Support vertices can be of any degree.
The following theorem gives bounds for the strong secure domination number of the rooted tree.
Theorem 4. For the rooted tree ,
Proof. Let X be a minimum secure dominating set of . Then, by Proposition 1 either all the pendant vertices belong to X or every support vertex and every pendant vertex, with the exception of one, belong to X. In other words, with respect to every support vertex, either the support vertex or one of its corresponding pendant vertices must be in .
If a pendant vertex is in , then its corresponding support vertex is the only defender as well a strong neighbor in X as X is the secure dominating set.
If a support vertex is in , then replacing a pendant vertex with its corresponding support vertex in X results in a strong secure dominating set. Also, note that the support vertex cannot be a defender for the root vertex as well as any internal vertex.
Suppose the root vertex belongs to , then it has a strong neighbor in X as X is a secure dominating set and its defender is an internal vertex whose degree is greater than or equal to l. In this case, .
If the root vertex belongs to X, then it can defend at most l neighbors which are internal vertices whose degree is greater than or equal to l. Let the internal vertices be , where . Since X is a secure dominating set, have another neighbor in X. If they are strong neighbors, then . Otherwise, remove the root vertex from X and add in X. Then, each vertex in has a strong neighbor. Thus, .
If there exist internal vertices which have strong neighbors in X and neighbors have no strong neighbors in X, then by adding those vertices in X, we obtain a strong secure dominating set. Therefore, we obtain . □
Let
and
be two connected graphs and let
,
. Then, a new graph obtained by merging
u and
v as a single vertex is called a
1-gluing (or vertex gluing) [
15] of
and
and is denoted by
. One can visualize any graph that has a cut vertex as a 1-gluing of two graphs. Clearly, all trees can be viewed as a 1-gluing of two trees.
The first result gives bounds on the secure domination number of the 1-gluing of two graphs.
Theorem 5. Let and be two connected graphs. Then, .
Proof. Let S and be sets of and , respectively. Let x be the merged vertex in . Clearly, is a dominating set of .
Case 1: Let
. Clearly,
. Let
. This implies that
or
or both. Without loss of generality, let
. Since
S is a secure dominating set, there exists a defender
. By Proposition 1, the subgraph induced by
forms a clique in
. Therefore,
If
and
, then
, where
. Thus,
So, the subgraph induced by forms a clique in . By Proposition 1, is a secure dominating set of . So, .
If either or , then or . In this case, is a clique in for every . Thus, by Proposition 1, t is a defender of and X is a secure dominating set of . Hence,
Case 2: When , or for every defender . So, for each either or . Since S and are secure dominating sets, there exists such that t is a defender of s. By Proposition 1, either or forms a clique in or for every . Therefore, forms a clique in for every . Hence, is a secure dominating set of , and so,
Now, we prove the lower bound. Let X be a set of . Let , where and . Suppose that ; clearly, and are dominating sets of and , respectively. Also, or for every . Note that . We prove that and are secure dominating sets of and , respectively. For . Since X is a secure dominating set of , s has a defender t in X, and so, by Proposition 1, is a clique in . So, forms a clique in . By proposition 1, is a secure dominating set of . Similarly is a secure dominating set of . Therefore, , and so, .
Assume that . Suppose x has two defenders with respect to X in , one in and another in . Since X is a secure dominating set, for every there exists such that is a clique in . By Proposition 1, is a secure dominating set of . Similarly is a secure dominating set of . So, .
Suppose x has a defender in exactly one of or , say in . Then, and are secure dominating sets in and , respectively. Therefore, . □
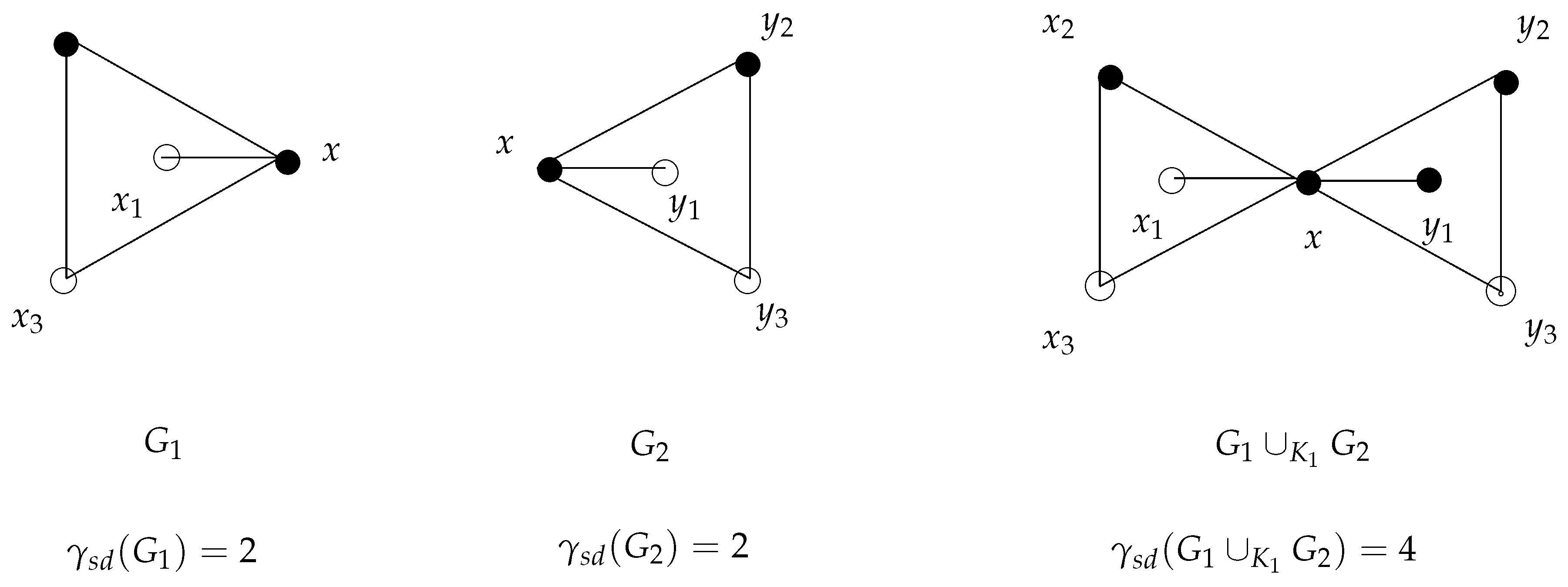
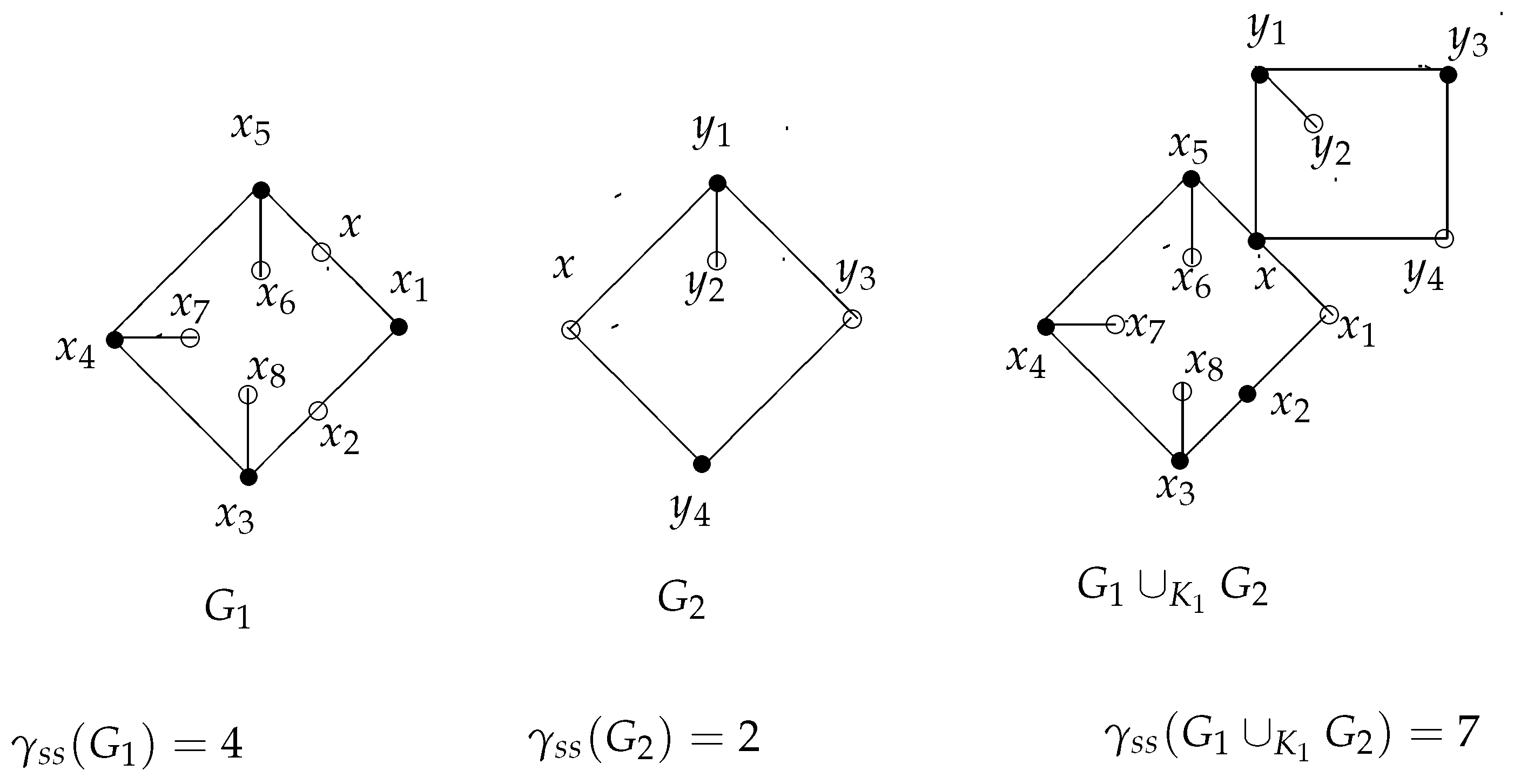
The bounds given in Theorem 5 are sharp. For instance, consider the graph
where
x is one of the pendant vertices of the path
and
. Here,
. Furthermore, take a look at the graph in
Figure 4 for the archiving upper bound in Theorem 5.
We are now in the position to prove the following result. A bound for the strong secure domination number of 1-gluing of two graphs is provided by the following theorem.
Theorem 6. Let and be two connected graphs. Then, .
Proof. Let S and be two sets of and , respectively, and let x be the common vertex of . Let . Clearly, is a strong dominating set of .
Case 1: Let . When and , as in case 1 of Theorem 5, one can prove that , where is a secure dominating set of . Therefore, is a strong secure dominating set of . When either or , we have that X is a secure dominating set of , refer to case 1 of Theorem 5. So, .
Case 2: Let . By case 2 of Theorem 5, X is a secure dominating set of and is a strong secure dominating set of . Hence, .
Let us prove the lower bound. Let X be a -set of and , where and . Let . As in the proof of Theorem 5, and are secure dominating sets. Moreover, and are strong secure dominating sets of and , respectively. Therefore, . Assume that . Suppose x has two defenders in X, one in and another in , then and are secure dominating sets. If x has no strong neighbor in but in , then and are strong secure dominating sets of and , respectively. Similarly, if x has no strong neighbor in but in , then and are strong secure dominating sets. Therefore, .
If x has no defender in but in , then and become strong secure dominating sets of and , respectively. Therefore, . Similarly, one can prove that x has no defender in but in . □
For the lower bound given in Theorem 5, consider the graph
where
x is one of the pendant vertices of the path
and
. Here,
,
, and
. Moreover, the upper bound provided in Theorem 5 is equal to the graph in
Figure 5.
Now, Theorem 5 gives us the following result.
Remark 2. For , we have
- (i).
.
- (ii).
.
- (iii).
Let us close this paper by comparing the strong secure domination number of a graph and the strong secure domination number of its edge removal graph.
Theorem 7. Let be a graph and be any edge of G. Then,
Proof. Let S be an ssds of G. Suppose both u and and u defends some vertices \S such that . Then, \ is an ssds for . Suppose neither u nor v belongs to S. Then, removing an edge does not make any changes. In this case, S is a -set for . If either or , say . In this case, by adding an edge which is incident with v to S gives an ssds for . Hence, .
Let S be an ssds for . If , then adding an edge e does not make any difference, so that S is a set for G. Suppose either or , say . Then, is an ssds for G. Therefore, . Suppose and . Without loss of generality, let . Then, gives an ssds for G. Therefore, . Hence, . □
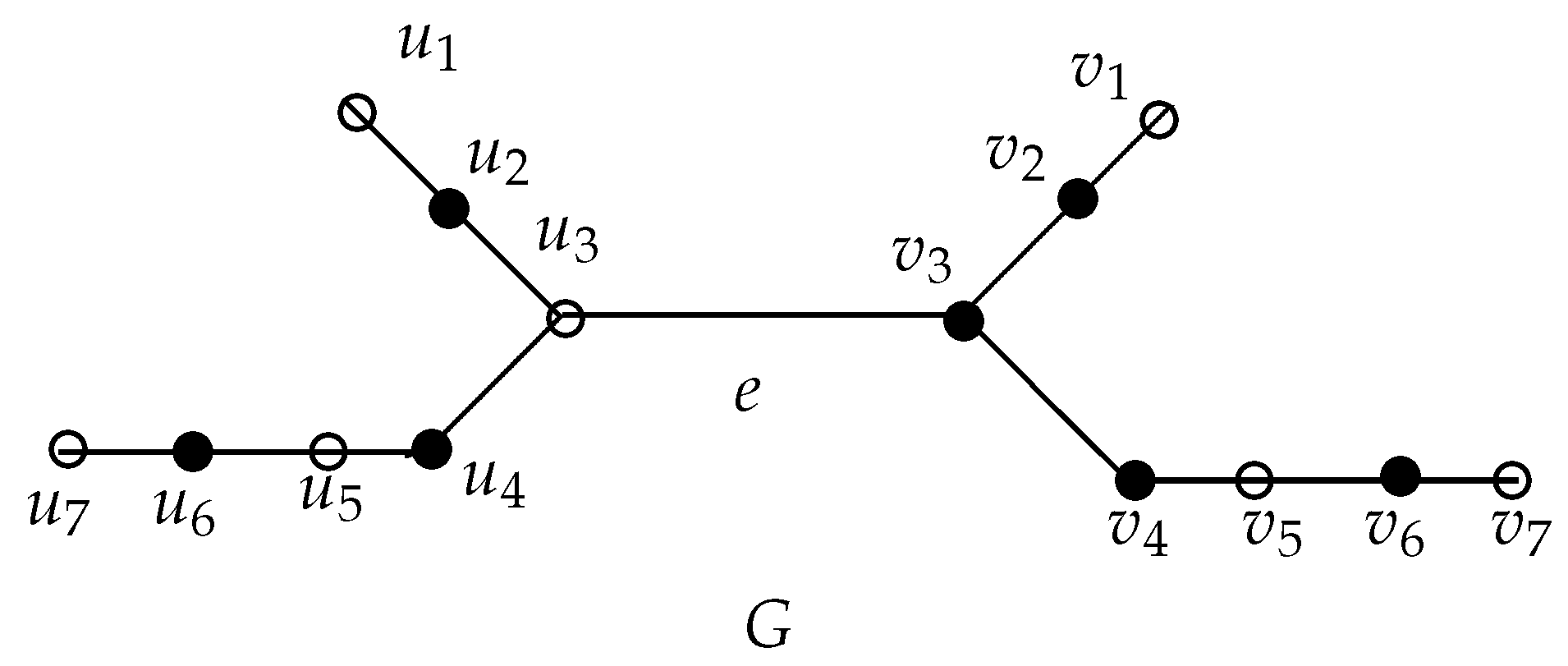
For the lower bound of Theorem 7, consider the graph
G given in
Figure 6. Note that
and
. For the upper bound, consider the graph
. Here,
, where
with
u being a pendant vertex and
v a vertex adjacent to
u in
.