1. Introduction
The Internet of Things (IoT for short) has rapidly evolved into a pervasive technological paradigm, characterized by the interconnection of a wide range of physical devices, such as sensors, computers, and software, for monitoring and control that facilitate data exchange and intelligent and autonomous decision making. The most important attributes that define IoT include its ability to collect real-time data from the physical world, enabling automation, enhanced efficiency, and improved quality of life. In this sense, IoT spans various domains, including Industry 4.0, smart homes, e-health, intelligent transport systems, and smart cities [
1,
2,
3,
4].
However, in this scenario of unprecedented and ubiquitous connectivity, we have to face great challenges, chief among them being the evolving cyber threats, with malware emerging as a significant concern [
5,
6,
7]. In this context, the different specimens of malware can infiltrate devices, compromise data integrity, disrupt operations and network functionalities, and even compromise personal privacy and security. Thus, it is very important to design tools that allow not only to detect the presence of malware on the network but also to predict its future behavior. As a consequence, to counteract the malicious activity of malware in IoT environments, it is crucial to distinguish between these two key aspects: malware detection algorithms and malware propagation models. Malware detection algorithms are focused on identifying and mitigating malware infections within devices and networks [
8,
9]. In contrast, malware propagation models are responsible for studying the dynamics of malware spreading through interconnected devices.
Mathematical epidemiology traditionally deals with the mathematical description and analysis of the dissemination of biological agents. Drawing inspiration from it, several models for malware propagation on different types of networks have appeared in recent years. Particularly interesting are those dedicated to study the propagation of malicious code on wireless sensor networks (WSNs), which constitute the foundation for the development and implementation of IoT networks. The vast majority of these models are of a global nature (see, for example, [
10,
11,
12,
13,
14] and the references therein), and their dynamics are described by continuous mathematical techniques, such as systems of ordinary differential equations. These are compartmental models (that is, the device population is divided into different classes or compartments: susceptible, infectious, recovered, etc.), and the main goal is to determine the temporal evolution of the size of these compartments. Consequently, the variables involved in the differential equations (that govern the dynamics of the system) represent the density at each step of time of susceptible devices, infectious devices, etc. Additionally, the epidemiological coefficients considered in these equations are inevitably of a general nature, making it impossible to distinguish between devices in a particular compartment. Moreover, it is not feasible to consider the local contact topology such that in the majority of models it is assumed that the communication topology is defined by means of a complete graph (all devices are in contact with all). Nevertheless, it is also true that it is possible to design models (networked models) where the degree distribution of the complex network defining the contact topology can be considered when defining the incidence term (see, for example, [
15,
16,
17]). Consequently, a critical analysis of global models reveals certain limitations that overlook the intricate topological structures of IoT networks and the heterogeneity of individual devices ([
18,
19]). This limitation necessitates a shift toward individual-based models, which consider the unique attributes of each network node [
20,
21].
The use of individual-based models for malware propagation presents a promising research line, offering a more detailed and realistic representation of malware dissemination on IoT networks. While this approach has gained traction, the state of the art concerning individual-based models for malware propagation, especially in the context of IoT networks, remains an area of active investigation. As far as we know, very few individual-based models for malware propagation have been proposed. In [
22], an individual-based, discrete, and stochastic SEIRS-F model is proposed. The authors aim to analyze malware propagation in a wireless sensor network and investigate the reliability of its components in this scenario. In [
23], an SITPS stochastic compartmental model is studied and analyzed, introducing—in addition to the classic compartments of susceptible and infected—the compartments of “tracked” (
T) and “repaired” (
P) devices. In [
24], an agent-based SEIRD model is described, providing a detailed analysis of all the characteristics of the agents involved in the propagation. In [
25], an individual-based model is proposed such that the dynamics of the malware outbreak is governed by means of a cellular automaton. In all these models, the variables involved in the transition functions correspond to the states of the particular devices, in contrast to what happens in global models, where the variables stand for the size of each compartment.
The use of mathematical models based on the individual paradigm is especially indicated when it is possible to have a deep knowledge of the interactions and specific characteristics of the potential hosts among which the agent (of whatever type) spreads. In the case of the propagation of biological agents, this type of model could be appropriate when, for example, the spread of a nosocomial infection is studied in an intensive care unit—note that patients are permanently monitored and it is possible to have a fairly approximate idea of their interactions. In other types of broader and more general scenarios in which a biological agent is spread, it would not be worthwhile to use individual models: global models would work perfectly well. In the case at hand, when the propagation is due to a “logical” agent (malicious code) on a network of computer devices (where it is possible to monitor the different devices in real time and know their activities, capabilities and objectives), it is reasonable to advocate for the use of individual models. Specifically, in the case of IoT device networks, different types of metrics can be applied to measure useful characteristics in the propagation process. For example, the communication capabilities and computational resources of the devices can give us an idea (both in terms of quality and performance) of how the devices can be used in the propagation process, how the specific task of a device will determine whether it is a target to attack or not, how the energy sources associated to a device will determine its lifetime, etc.
The main goal of this paper is to propose and analyze a novel individual-based model to predict the behavior of a specimen of malware on an IoT network. This is a compartmental SEA model, where the population of devices is classified into susceptible, exposed and attacked, and the dynamics refers to the variation of the states of devices at each step of time. These states are given by probability vectors such that the transition is ruled by a system of ordinary differential equations. This definition of the state for each device is what sets this model apart from the other individual models we previously mentioned. With it, it becomes possible to use differential equations as transition rules instead of cellular automata or other discrete tools.
The rest of the paper is organized as follows: in
Section 2, the fundamentals of individual-based modeling for malware propagation are stated; the proposed model is introduced and analyzed in
Section 3; and the conclusions are shown in
Section 4.
2. The Individual-Based Paradigm
Individual-based modeling is based on the study of the behavior of the individuals/agents that constitute the system, taking into account their particular characteristics. In the case at hand, these agents stand for the devices deployed within the IoT network and the specimen of malware. Therefore, as previously mentioned, the development of individual-based mathematical models for malware propagation on IoT networks necessitates a consideration of two key aspects: the specific attributes of devices and the specimen of malware pertaining to propagation and infection processes, and the unique contact topology, often leading to the consideration of a complex network structure.
In this context, the scenario can be succinctly characterized through a directed and weighted complex network denoted as . Here, the set of nodes symbolizes the population of devices, and the links stand for the communication connections among these devices. The dynamics of malware propagation is thus defined by the following components:
- (1)
The state of the i-th device at time t, which is denoted as . In this sense, time can flow both continuously or at discrete steps of time.
- (2)
The state set , within which the aforementioned individual states take their values: for and . This set can be finite, allowing devices to assume a finite number of possible states at each time step, or it can be infinite so that the states are continuous in nature: for example, .
- (3)
Device states evolve in discrete time steps, following local transition rules that are defined by means of continuous or discrete, deterministic or stochastic mathematical tools.
Consequently, several types of local transition functions can be used to describe the dynamics of the individual states. In our case, we will propose an individual-based model, where the states stand for stochastic vectors that take continuous values and the time flows also in a continuous way.
3. The Proposed Individual-Based Model
In this section, the novel individual-based model for malware propagation on an IoT network is introduced and analyzed. As is previously mentioned, it is a compartmental SEA model, where population is divided into susceptible
S, exposed
E, and attacked
A devices. It is assumed that a susceptible device becomes exposed when the specimen of malware reaches it and carries out the decision process to determine whether to attack the host device (making it “attacked”) or propagate to a neighbor device, returning the host to a state of susceptibility. Note that infectious devices are those which are exposed. Furthermore, attacked devices remain in this state indefinitely (see
Figure 1).
3.1. Mathematical Formulation of the Model
As is mentioned in
Section 2, the IoT network can be mathematically characterized as a directed and weighted complex network:
, where the set of nodes
represents the population of devices (the
i-th node is given by
), and the set of edges
stands for the direct communication links between two devices (if the
i-th node
can transmit information to the
j-th node
, then
).
Set
to the in-neighborhood of the
i-th node, that is, the set of adjacent nodes to
:
Moreover, the out-neighbor of
can be defined similarly as the set of adjacent nodes from
:
Note that is the set of devices with which the i-th device has a two-way communication.
Each link
of the network is endowed with a weight
representing the strength of infection from the
i-th device to the
j-th device: if
, then it is impossible for the specimen of malware hosted in
to reach the device
, whereas if
, then the malware spreads successfully from the
i-th node to the
j-th node at every step of time and contact. Specifically,
where
is the number of communication contacts from
to
per unit of time, and
is the probability that a communication contact leads to a “contagion”. Consequently, the adjacency matrix associated to
,
can be defined as follows:
As the proposed model follows the individual-based paradigm, the variables of the equations that describe the dynamics stand for the states of the devices at every time. In this sense, the state of the i-th device at time t is defined as , where represents the probability that the i-th device is susceptible at t, stands for the probability that the i-th device is exposed at t, and finally, is defined as the probability of the i-th device being attacked at t.
Let
be the set of in-neighbor devices to
such that its probability of being infectious at
t is greater than 0, and its probability of being attacked at
t is 0. Then, the dynamics of the system is described by means of the following system of ordinary differential equations:
or, equivalently, by the following initial value problem (IVP) expressed in terms of the adjacency matrix associated to
:
where
stands for the recovery coefficient (from exposed to susceptible), and
represents the attack coefficient (transition from exposed to attacked).
As the state of each device is a probabilistic vector (Equation (
11)), this IVP of
ordinary differential equations can be reduced to the following IVP formed by
ordinary differential equations:
If
and
, the systems (
12) and (
13) can be expressed in matrix form as follows:
where
, and
.
In
Table 1, the most important mathematical notations employed in the model are shown.
3.2. The Underlying Global Model
3.2.1. Mathematical Description and Analysis
Note that the IB model presented in the last subsection is based on the following global model with
:
where
. This system describes the evolution of the particular probabilities of each device in the particular case where the contact topology is defined by the complete graph
(that is, all devices are in contact with all devices at every
t), and the epidemiological coefficients are all equal:
for
, and
,
.
Since the sum of probabilities must equal to one,
for all
t, then the systems (
16)–(
18) can be reduced to the following:
with
and
.
Using simple arguments, the following results can be proved:
Proposition 1. The region is positively invariant and unique solutions of the systems (19) and (20) for all . Proposition 2. The basic reproductive number associated to the epidemiological model described by (19) and (20) is Furthermore, the effective reproductive number (also known as the replacement number) is given by . Note that for every .
Theorem 1. Set a solution of (19) and (20) in Ω. The following statements hold: - (1)
If , then the probability of being exposed decreases to zero, that is: where is the unique solution of the following equation: - (2)
If , then the probability of being exposed increases to a maximum valueand then it decreases to zero such that .
3.2.2. Numerical Simulations
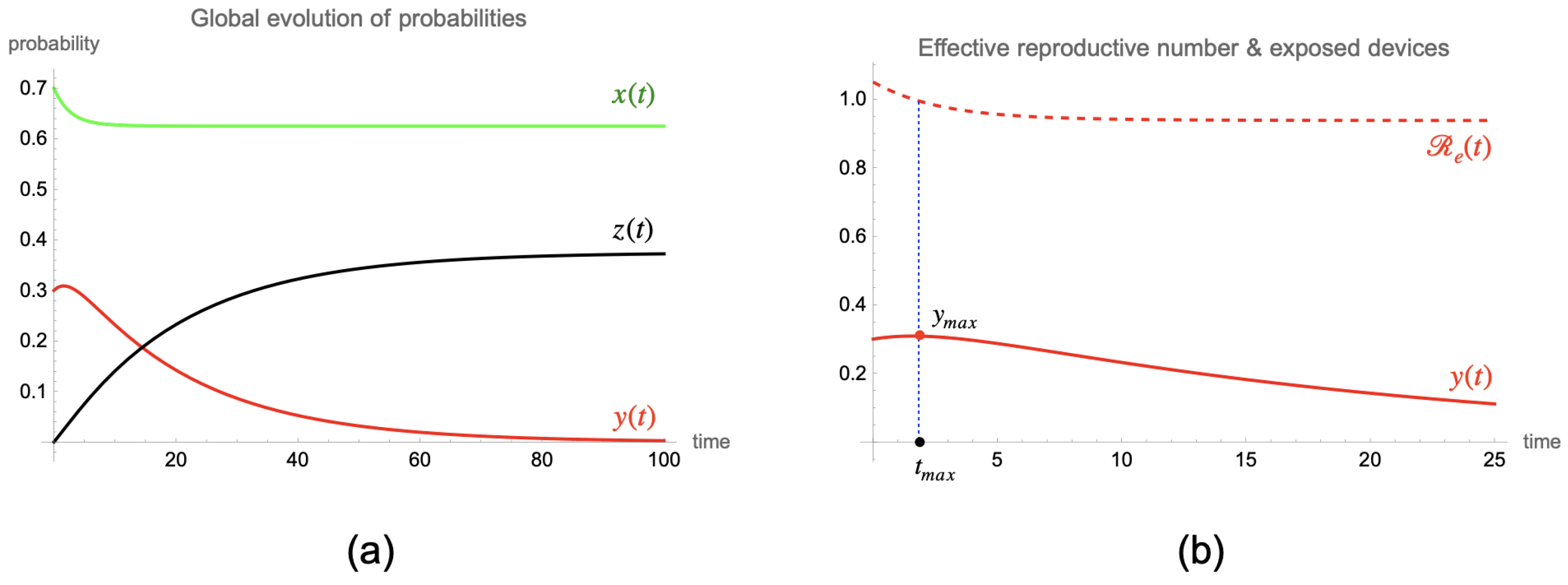
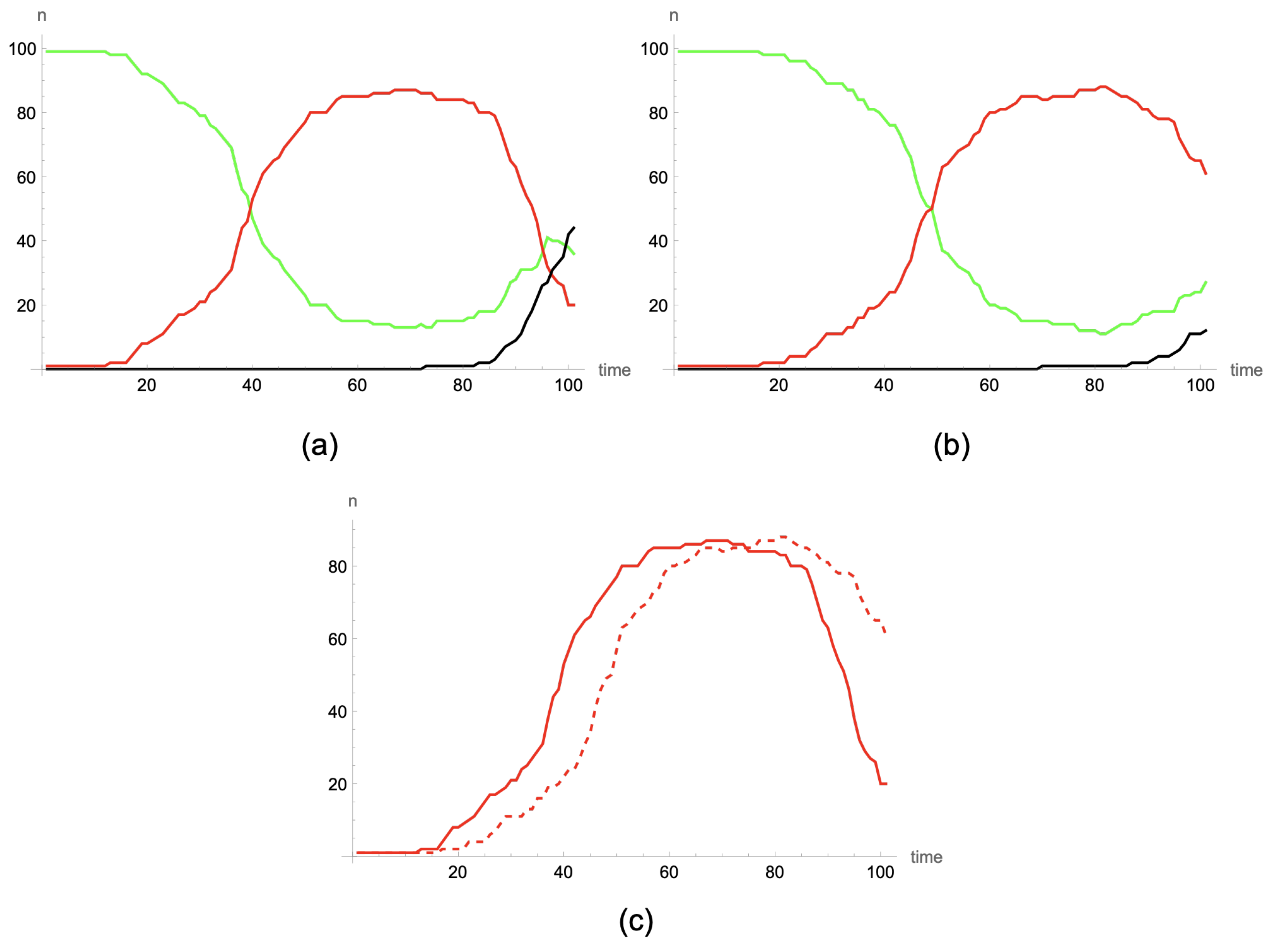
Let us suppose that the numerical values of the epidemiological coefficients are the following: , (consequently, ), and . Moreover, assume that at , there is a large fraction of infectious devices: and . In this case, the basic reproductive number is , whereas the replacement number at is . Moreover, the disease-free equilibrium point obtained is .
In
Figure 2a, the global evolution of the different probabilities of a (general) device state is shown (susceptible probability in green, exposed probability in red, and attacked probability in black). Note that as
, then the probability of being exposed initially increases to a maximum
, which is reached at
(obviously, as you can see in
Figure 2b, this occurs when the replacement number decreases to 1, that is,
), and then this probability decreases to
. On the other hand, the probability of being attacked monotonically increases to
, and the probability of being susceptible monotonically decreases to
.
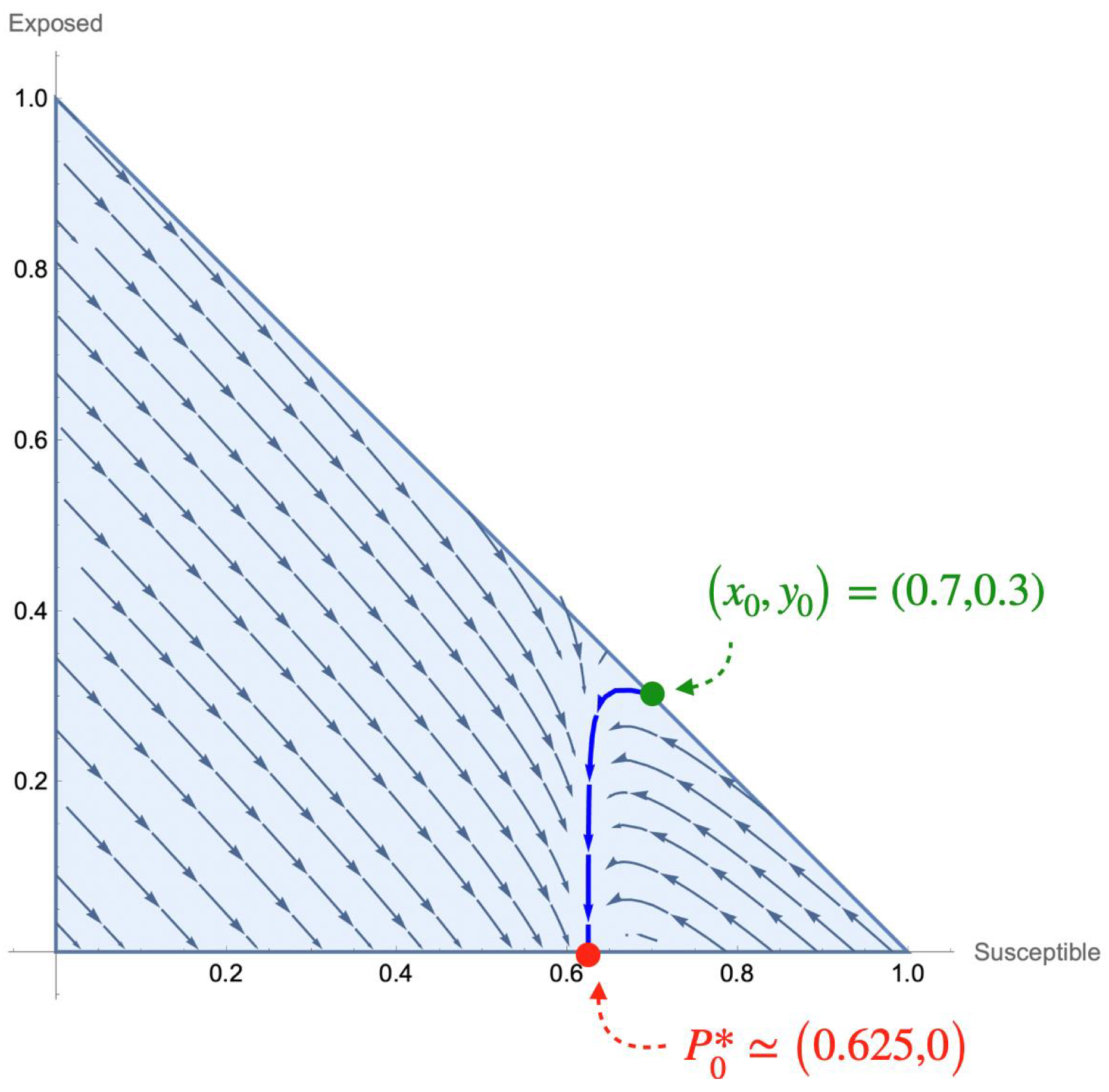
In
Figure 3, the phase plane on the feasible region
for susceptible and exposed probabilities is introduced. Note that, as it has been theoretically proven, all trajectories tend to a disease-free (
) equilibrium point. Specifically, in this figure, the trajectory corresponding to the solution curve defined by
of the last simulation is highlighted.
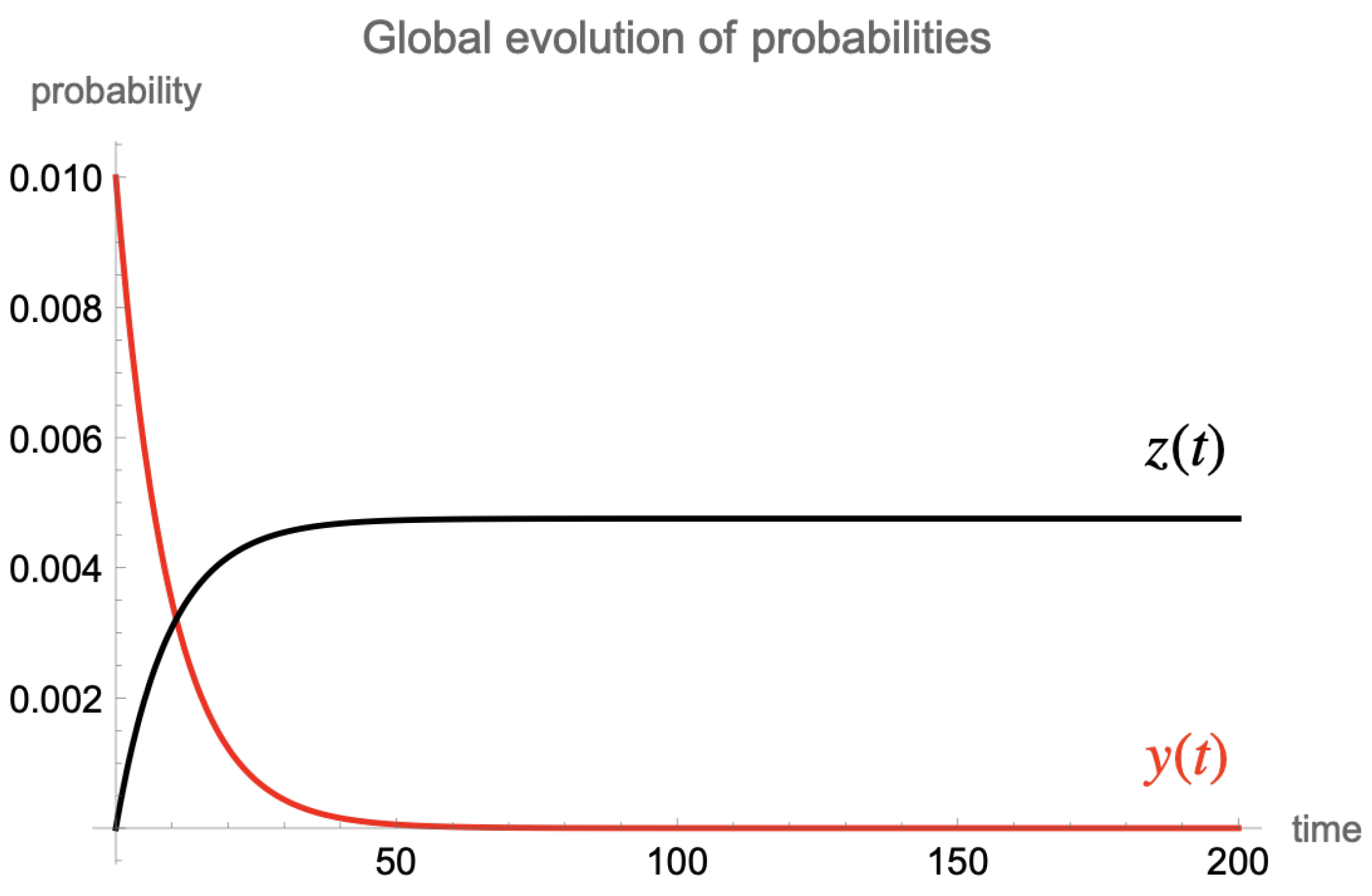
On the other hand, if it is supposed that at
the probability of being susceptible is
(and, consequently,
), and the contagion probability
q is varied to
, then
and
. In this situation, the probability of being exposed decreases directly to zero as is illustrated in
Figure 4, whereas the probability of being attacked tends to
and
.
3.2.3. Sensitive Analysis
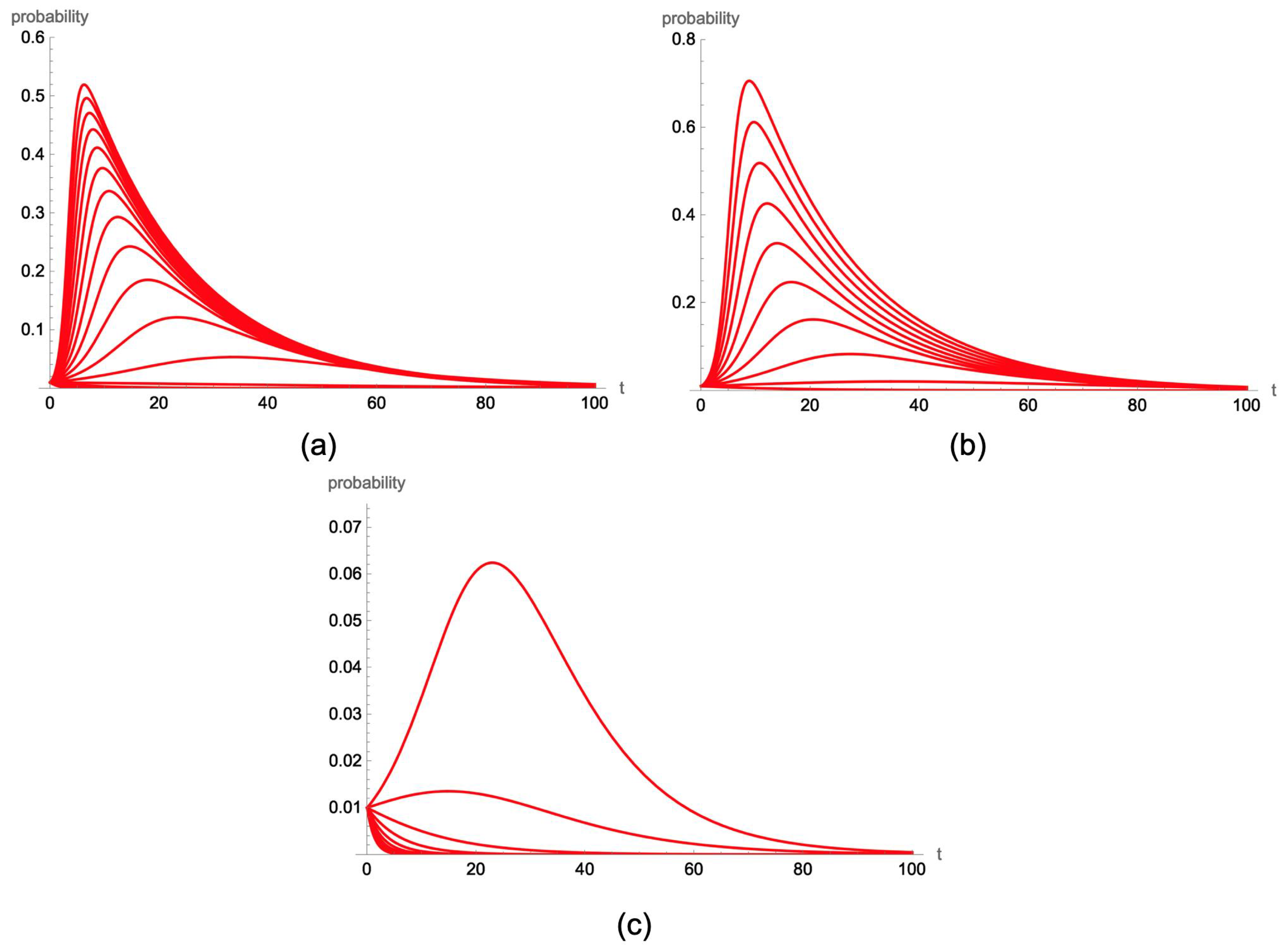
In this subsection, a brief sensitivity analysis of the model is introduced, where slight changes in the numerical value of the three epidemiological coefficients (the infection force w, the recovery coefficient , and the attack coefficient ) are made.
In
Figure 5a, some simulations are shown when the initial conditions are
and
, and the values of the epidemiological coefficients are
,
, and
. It can be observed that as the infection force increases, the peak of the probability of being exposed also increases. A simple calculation shows that if
, the basic reproductive number is
so that if
, this threshold coefficient is greater than 1, and obviously, the probability curve is monotonically increasing towards the maximum (it will later decrease). On the other hand, in
Figure 5b, a similar analysis is carried out, varying, in this case, the numerical value of the recovery coefficient
, and assuming
(the rest of the parameters are the same as in the previous case). It is shown that as the recovery coefficient increases, the basic reproductive number decreases: for
, it takes the value
; for
, it is
; and for
, it falls below one to
. This indicates that the curves corresponding to the probability of being in the exposed state tend to flatten as the recovery coefficient increases. Finally, in
Figure 5c, the simulations obtained when varying the attack coefficient
are shown. In this case, it is assumed that
and
. Here, as in the previous case, as the attack coefficient increases, the basic reproductive number decreases, finding (in this specific example) that the critical threshold appears at
.
3.3. Illustrative Simulations
In this subsection, some illustrative simulations of the proposed individual-based model are shown. Each of them will be characterized by different initial conditions, different contact topologies, and distinct numerical values of the particular epidemiological coefficients: , and for . More specifically, the simulations are divided into two types: those in which malware spreads on an homogeneous complex network, and those where malware propagates on heterogeneous complex networks.
The simulations are performed in a Mathematica environment using a normal processor (3 GHz Intel Xeon W 10-core). Once all the data related to the topological structure of the network and the epidemiological coefficients involved in the propagation process are processed, a system of ordinary differential equations must be solved numerically, where n is the number of nodes. Since the functions to be evaluated in the algorithm defining the numerical method are quite simple, it is known that the computational complexity is polynomial.
3.3.1. Propagation on Homogeneous Networks
In this case, the IoT network is described by means of a homogeneous network: complete network or grid network. With the aim of carrying out a simulation as similar as possible to that given in the case of the global underlying model, it is supposed that all epidemiological coefficients are the same: , , for all . Specifically, it is assumed that and , which are the same numerical values considered in the first simulation presented for the underlying global model. Moreover, it is supposed that devices form the networks, and there exists only one exposed device—the “patient zero”—at (that is, ), which is determined by the highest degree centrality.
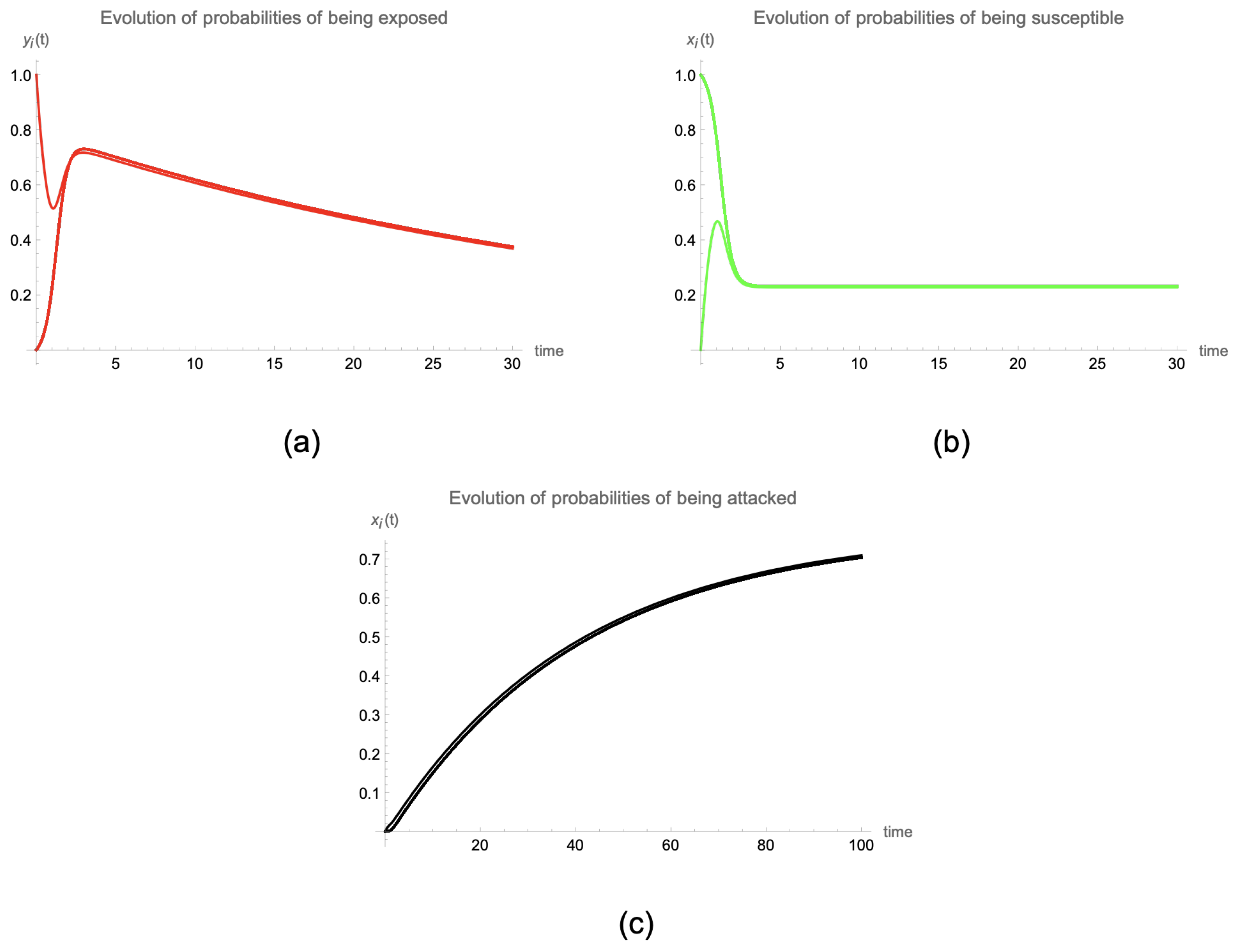
If the complete graph is considered, the evolutions of the probabilities of being susceptible (
) exposed (
), and attacked (
) are as shown in
Figure 6.
Note that, as it could not be otherwise, the disease-free steady state for all devices is the same: with . Moreover, the behavior of the probabilities of all nodes except the one that is initially exposed (say, the j-th node), , , are the same. However although the evolution of and (probabilities of the device initially exposed) differs from the probabilities of the rest of the devices during the initial period, they end up having similar behaviors. Another interesting fact is that it is observed that as the number of nodes n in the network increases, the maximum value that the probability of being exposed can reach also increases.
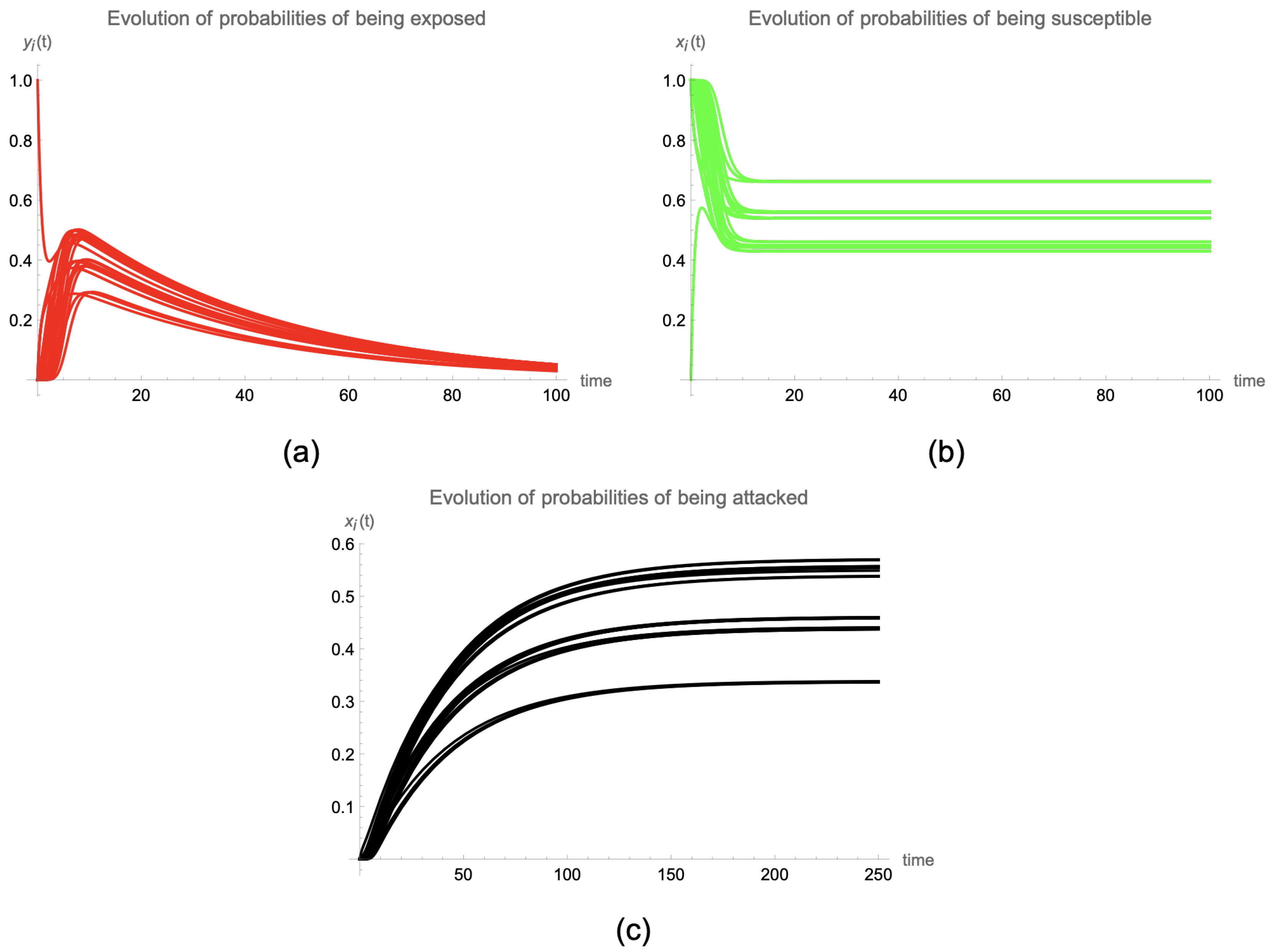
If the contact topology is described by means of a grid graph and, for the sake of simplicity (and visibility), only
devices are deployed, then the evolution of probabilities is shown in
Figure 7 when
for
, and
, and the joint evolution of the different probabilities is presented in
Figure 8. It can be seen how the population of devices are classified into several groups based on their evolution:
In the case of the probability of being exposed, initially, three groups are formed that are characterized by the maximum value that takes for , although later they all converge to the same value of , the disease-free equilibrium point.
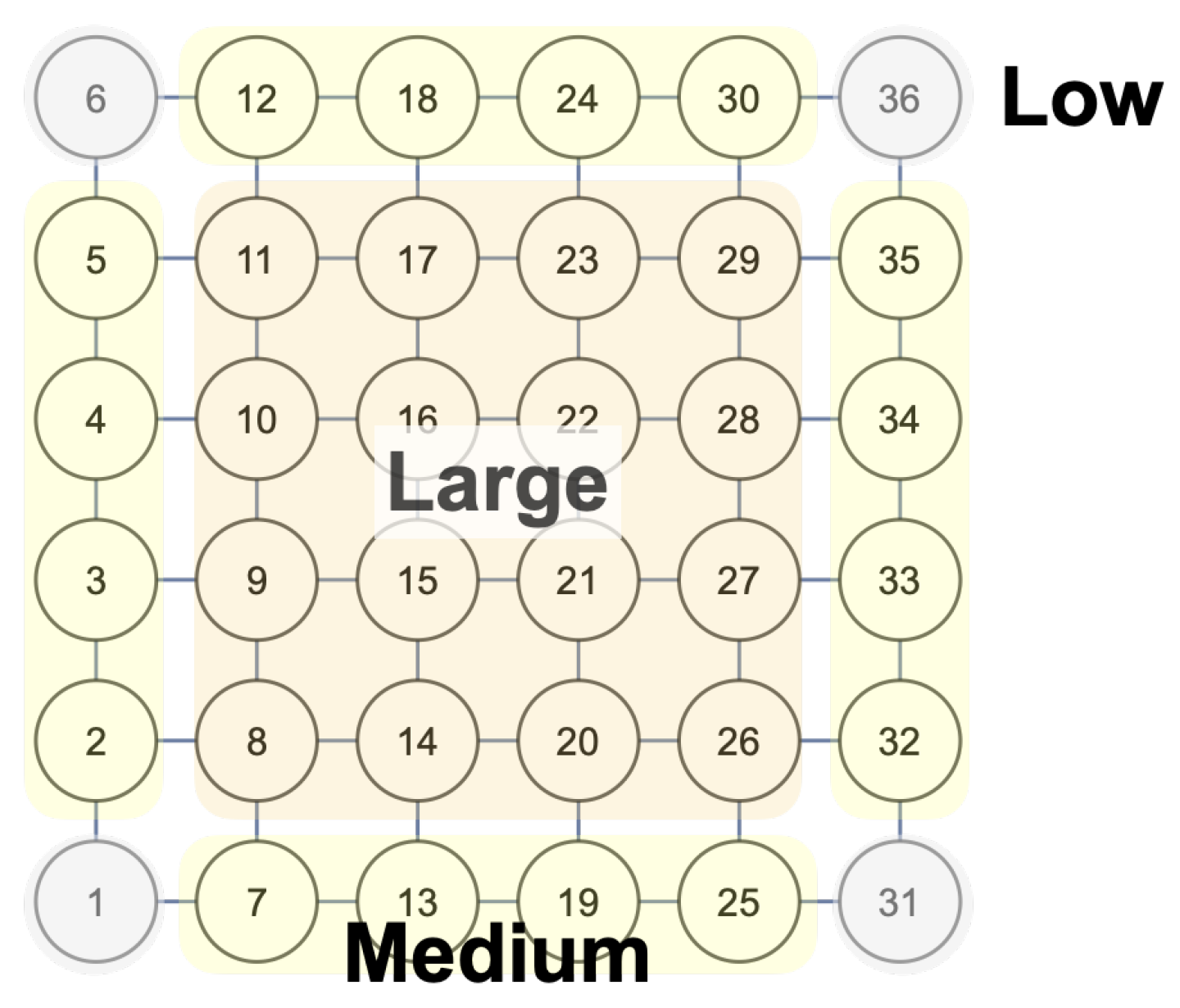
In the case of the probability of being susceptible, it can be shown that from , three groups of devices are created, depending on their positions within the complex network (degree and distance to the initially exposed node).
As
for all
, the behavior of the probabilities of being attacked is similar to that of the probabilities of being susceptible, that is, three types of devices can be derived from the evolution considering the value of
:
(low values),
(medium values), and
(large values). The spatial distribution of these three types of nodes within the network is shown in
Figure 9.
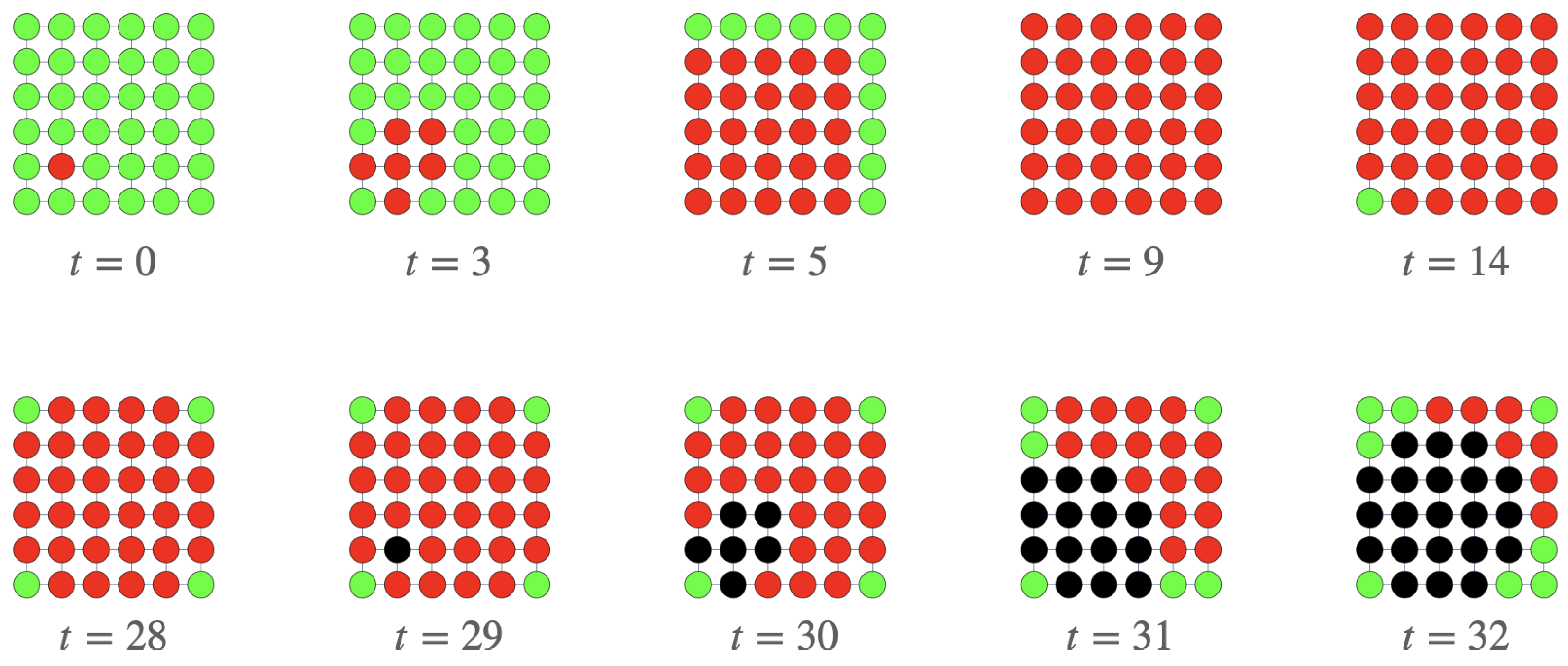
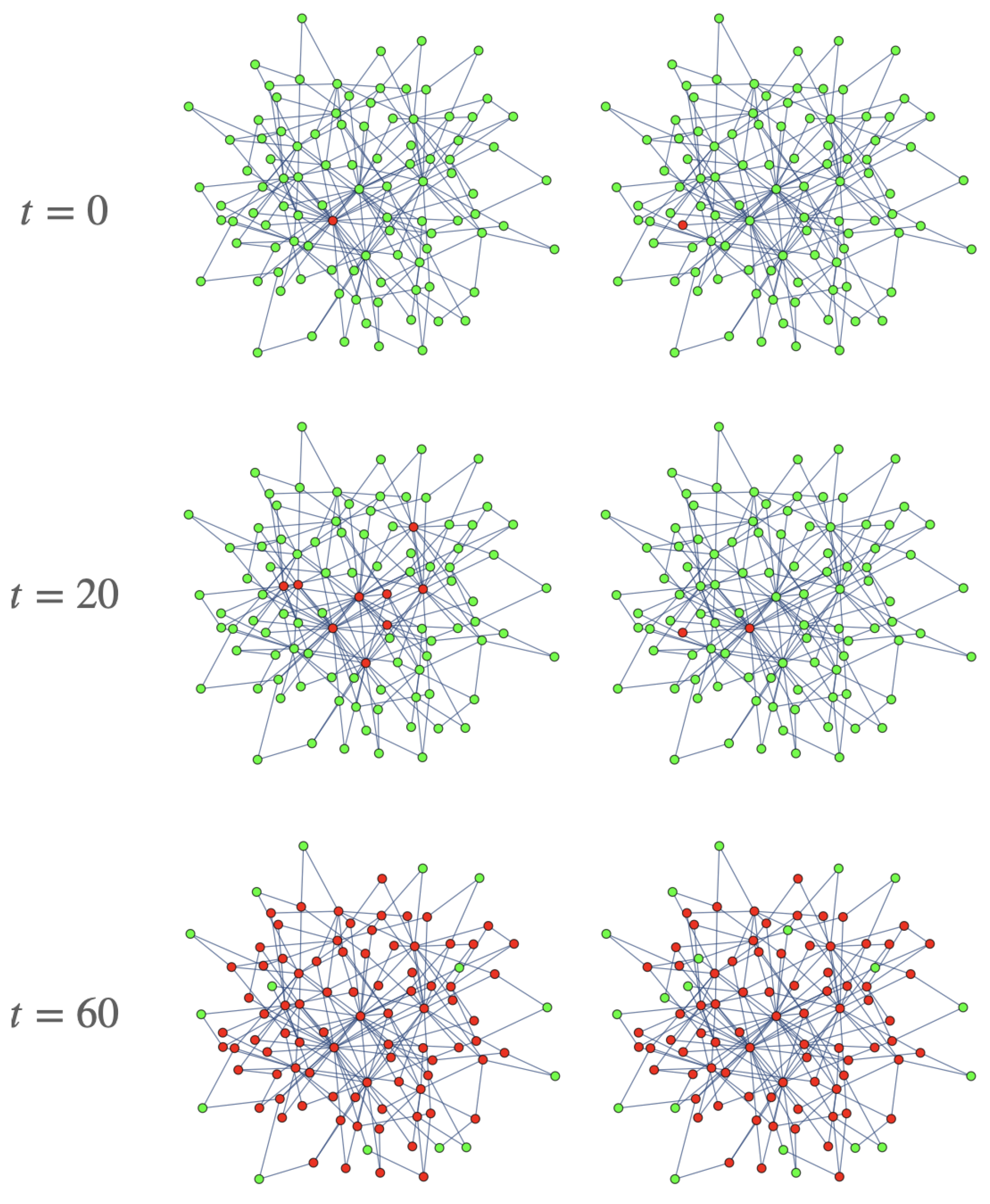
In
Figure 10, the spatio-temporal spreading of the specimen of malicious code on the
grid network is shown at different steps of time. In this simulation, the color of each node is assigned considering the greatest probability:
or
(that is, green, red and black for nodes whose highest probability is that of being susceptible, exposed and attacked, respectively).
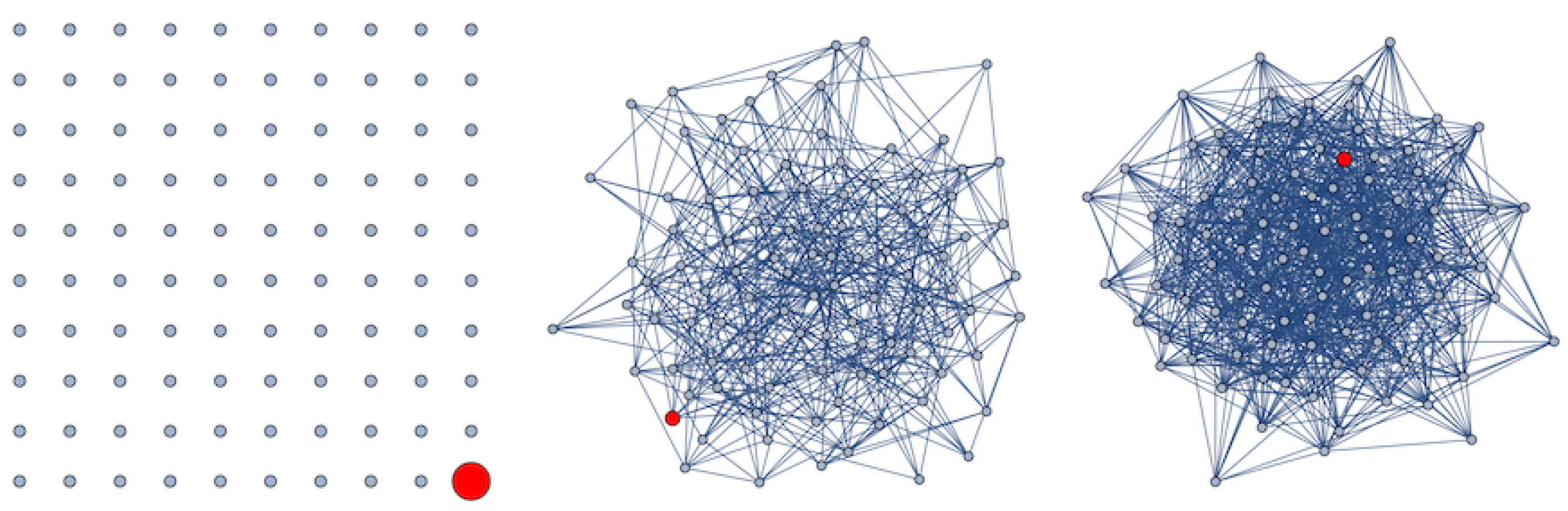
3.3.2. Propagation on Heterogeneous Networks
Initially, suppose that all epidemiological coefficients are the same for all network devices, specifically:
, and
. Moreover, assume that the IoT network is formed by
nodes/devices, and its contact topology is determined by a random complex network defined by the Erdös–Rényi algorithm with probability
p. Moreover, as in the previous simulations, it is assumed that at
, there is only one device with non-zero exposed probability: without loss of generality, we can suppose that it is the
i-th device. Consequently,
and
for all
. In
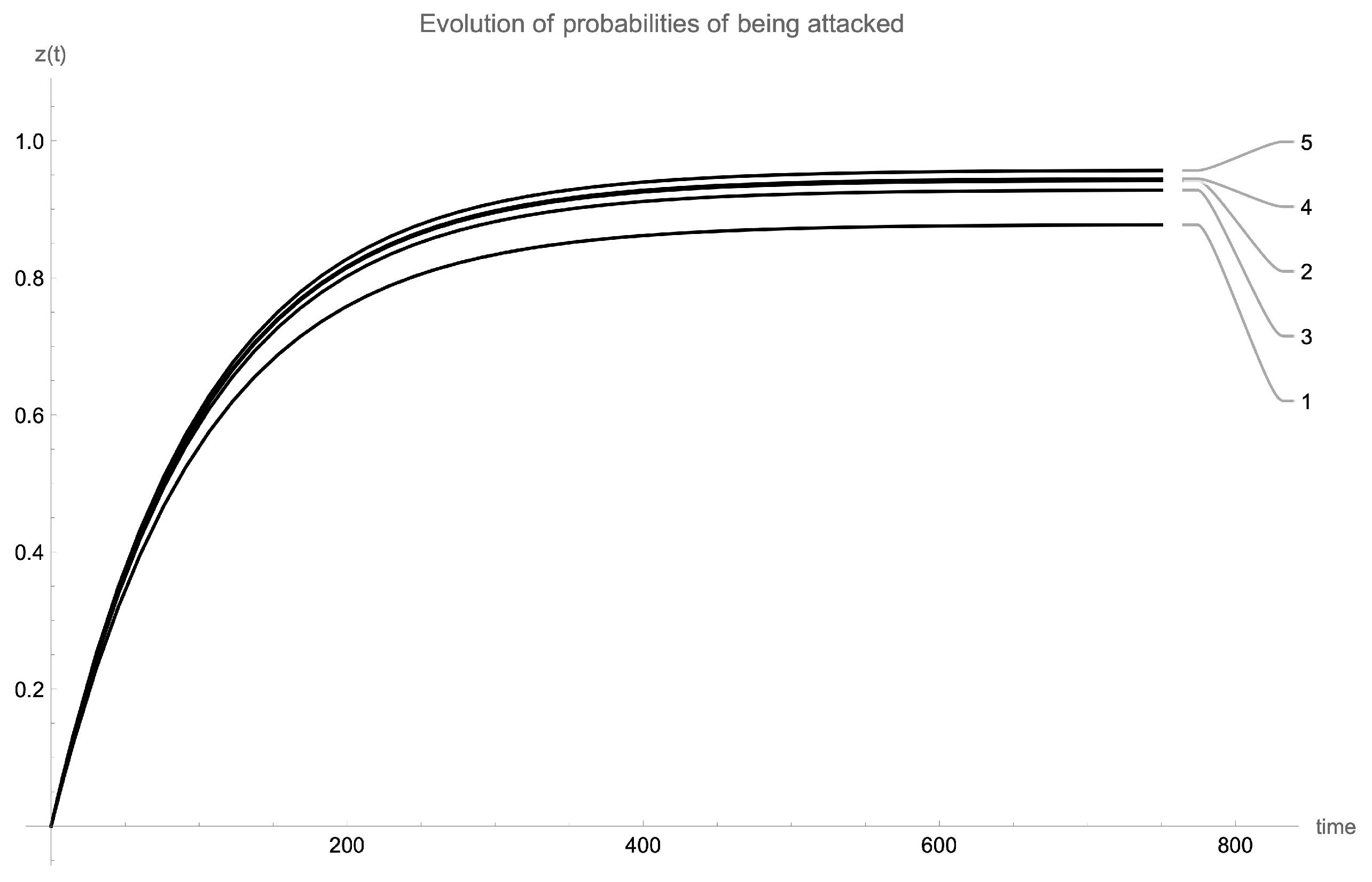
Figure 11, the evolution of the exposed probability
associated to the initially exposed device (the
i-th device) is shown for each ER random network, where the link probability
p takes the following values:
. In
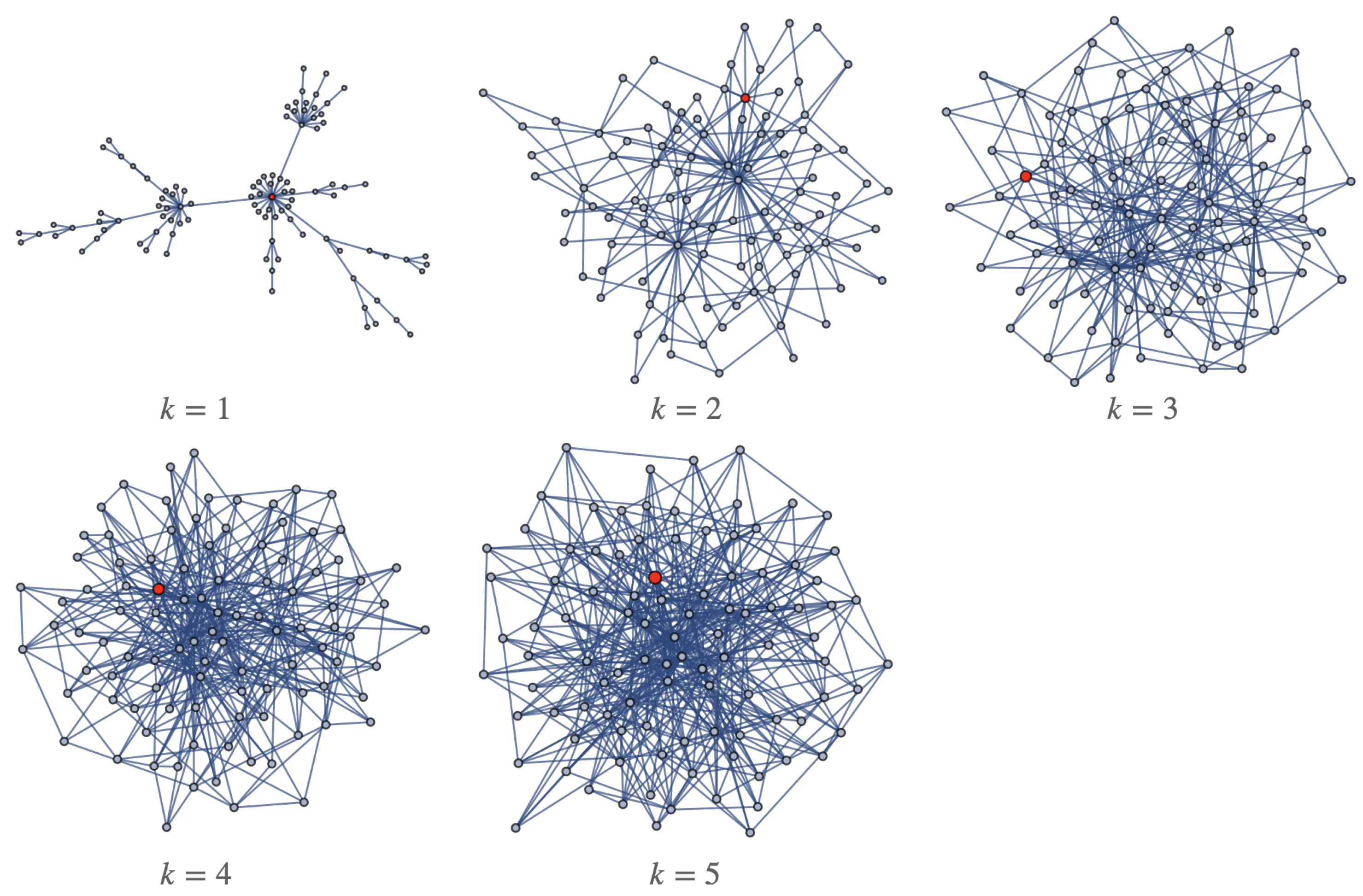
Figure 12, the explicit link structures of the ER random networks are shown (for
, the network consists of
n isolated nodes, and for
, the complete graph is obtained), and in
Table 2, the global structural characteristics of these networks are shown. Note that as the link probability
p increases, the higher the exposed probability values that are reached. The structural characteristics of the initially exposed devices are shown in
Table 3.
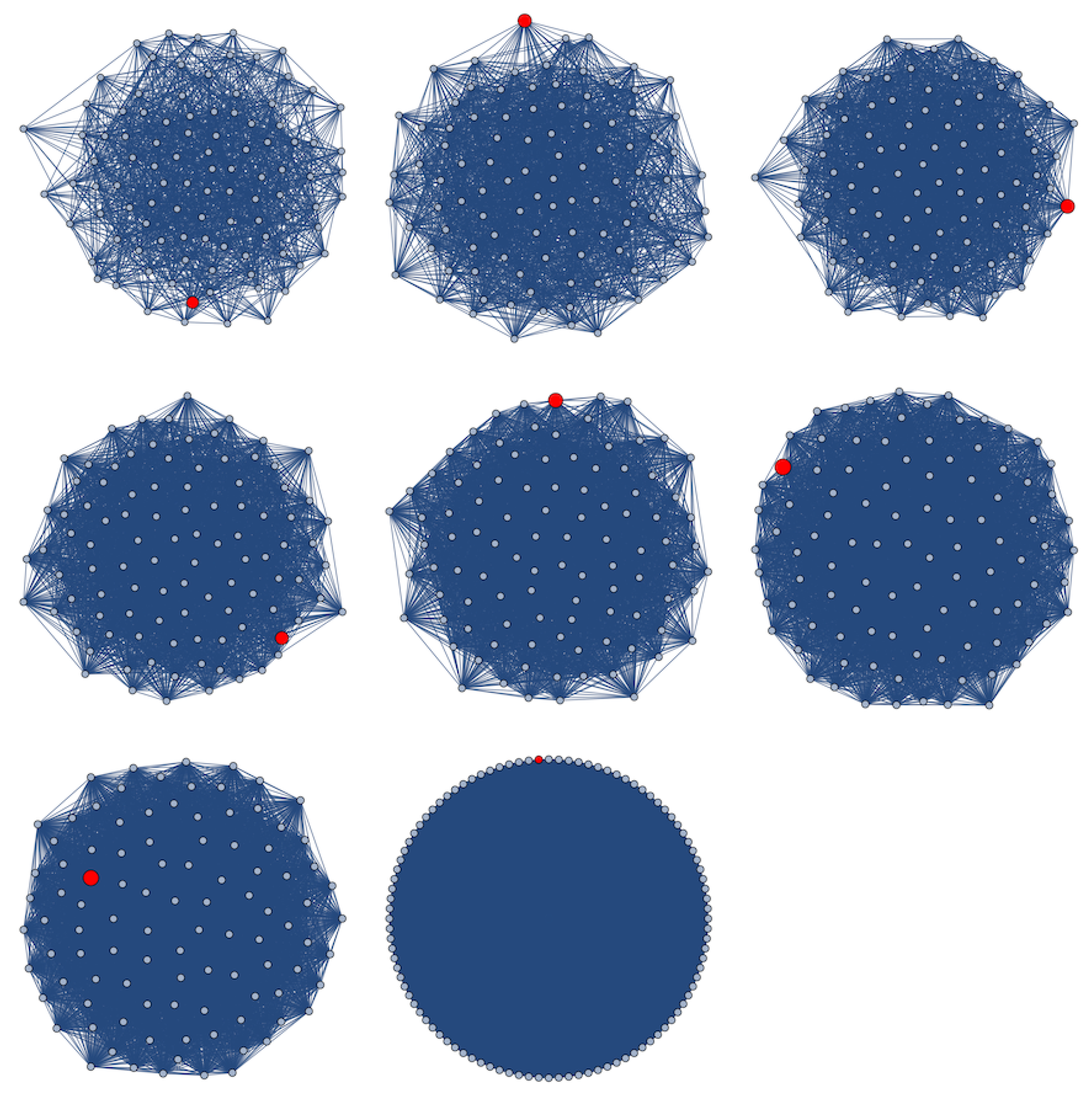
In
Figure 13, the evolution of the attacked probabilities when the specimen of malicious code spreads on an IoT network that follows a scale-free topology where
stand for the parameters of the Barabási–Albert algorithm (the explicit topologies of these networks are shown in
Figure 14). The initial conditions and epidemiological coefficients employed are the same than those used in the last simulation. As is shown, the larger
k is, the larger
is.
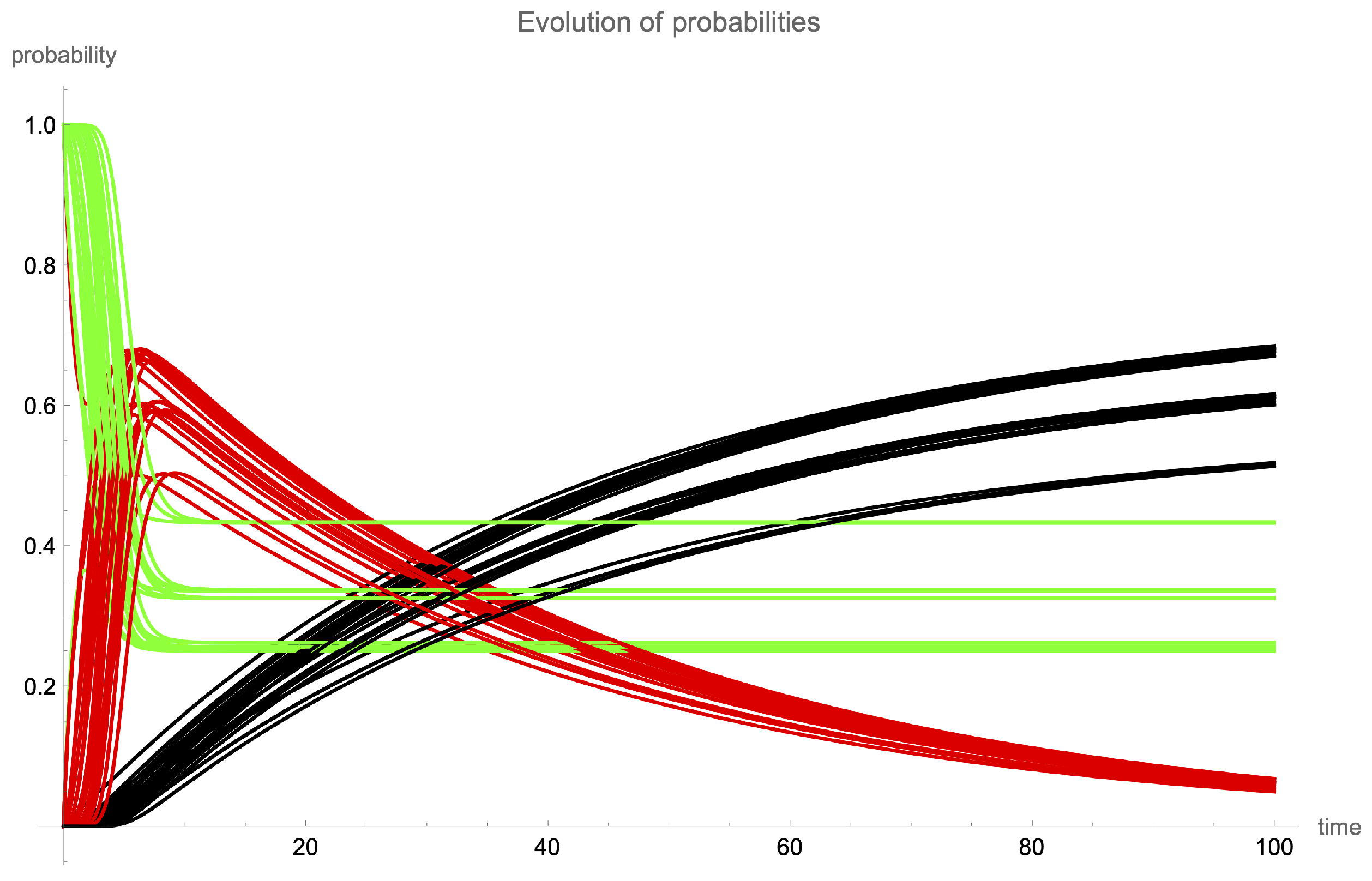
Finally, the behavior of spreading obviously depends on the structural characteristics of the initially exposed node. For example, in
Figure 15 and
Figure 16, the evolution of probabilities in each node of a scale-free network is shown, with
,
for
, and
, for
.
Specifically, in
Figure 15a, the evolution of the number of devices with large probability of being susceptible (green), exposed (red) and attacked (black) when the “zero patient” is determined by the node with highest degree centrality is shown. The same simulation but considering as “patient zero” the node with the minimum degree centrality is presented in
Figure 15b. Finally, in
Figure 15c, the comparison between the simulations when the temporal evolution of the number of exposed devices is only represented is shown (the red dashed line stands for the case with the minimum degree centrality). In
Figure 16, the spatial distribution of these nodes within the network is illustrated for three specific steps of time
, and
: the left column represents the evolution of the system when “patient zero” is the highest-degree node, whereas the right column stands for the evolution when “patient zero” is determined by the minimum degree centrality. Note that the growth of the number of devices with a higher probability of being exposed is faster in the first case (when the initially exposed node has the highest degree centrality) than in the second case, reaching its maximum earlier. However, in the end, both curves collapse to zero as the states of different nodes reach their equilibrium points.
It seems reasonable to think that the topology of the network over which malware spreads conditions that propagation. It is expected that certain structural (and global) indices associated to the network (such as its density, average degree, average betweenness coefficient, etc.) serve as indicators of this process. In this sense, it can be observed that higher values of these indices cause the number of devices with a probability of being in the exposed state above a certain threshold to grow. For example, in
Figure 17, some simulations are shown on ER random networks with
devices, defined by different probabilities:
. Additionally, for simplicity, the same epidemiological coefficients are assumed for all devices (
), and the node with the highest degree centrality is considered patient zero.
Figure 17a shows the temporal evolution of the number of devices whose highest probability is to be exposed, while
Figure 17b shows the evolution of the number of devices whose probability of being exposed is above
. It can be observed that as the reconnection probability
p increases, the number of nodes with these characteristics also increases, peaking before eventually dropping to zero. Note (see
Table 4) that higher probability
p corresponds to higher density, smaller diameter and radius, and more central values for different structural indices. Consequently, when the spread occurs on a network whose contact topology is defined by a complete graph, the malware propagates more “rapidly”.
4. Conclusions
In this work, a novel individual-based model for malware propagation on IoT networks is presented. One of the most important, and genuine, characteristics of the proposed model is the definition of the state of each node, which does not consist of its univocal determination at each step of time as is usual in the vast majority of models (susceptible device, exposed device, or attacked device), but rather is determined by a stochastic vector defined by the probabilities of being susceptible, exposed and attacked at this time. This is a deterministic model, where the local transition rules of the stochastic vector state of each device are described by means of a system of ordinary differential equations whose dependent variables represent the last three mentioned variables.
It is shown that the probability vector evolves to a steady state with for such that the values of the other two probabilities (the probability of remaining susceptible and the probability of being attacked ) and the maximum value taken by the probability of being exposed depend on the structural properties of the corresponding node within the complex network and the global structural characteristics of the complex network that describes the contact/communication topology of the IoT network.
The determination of security countermeasures is an important issue [
26,
27]. From the analysis of the model, and more specifically from the analysis of the basic reproductive number
, it is possible to obtain control strategies for the epidemic process (consisting of reducing the number of devices capable of transmitting the malware). Thus, the objective would be to reduce this threshold parameter to below 1. Taking into account the explicit expression of
, this could be achieved by decreasing
w or increasing both the recovery rate and the attack rate. Realistically, in this case, it would only be possible to decrease the number of contacts or increase the recovery rate.
In my opinion, such models that predict the spread of a particular specimen of malware in an IoT network, while they have not received as much attention as models for detecting the presence of malware, can offer solutions of the same level of importance. In this sense, I believe that their implementation in the security operation centers (SOCs) is particularly interesting and useful such that after the successful detection of malware, real-time predictions about the future evolution of malware (considering different types of initial conditions) could be given.
Future work will focus on carrying on a more in-depth theoretical study of the explicit expression of the “disease-free” steady state reached by the system that takes into account the particular characteristics of each node/device. It is also of great interest to study in depth the design of different metrics that allow to correctly analyze how fast a specific malware specimen spreads when the state of the devices is probabilistic.