3. Constrained Assignment Problem with Bounds and Penalties
In this section, we consider the constrained assignment problem with bounds and penalties (CA-BP). The objective is to minimize the total processing times of executed jobs as well as the penalties from rejected jobs. Without loss of generality, we assume that ; otherwise, there is no feasible solution to the CA-BP.
Given an instance
of the CA-BP, we use variables
and
simply as a scheme
, to represent an execution of
n jobs on
m machines, where a variable
indicates the job
to be executed on that machine
, and otherwise,
for any
and
. Then, we may obtain the linear integer programming (
IP) to determine the CA-BP as follows:
where the first constraint indicates that each job is assigned on at most one machine to be executed; i.e., no job can be executed on more than one machine. The second constraint indicates that each machine
must execute at least
and at most
jobs from
J.
In order to optimally solve the CA-BP, and equivalently the linear integer programming (
IP), we intend to transfer the CA-BP to the minimum-cost flow problem on a special network constructed in the following, where the flow value of each arc in such a problem must be between a lower bound and an upper bound.
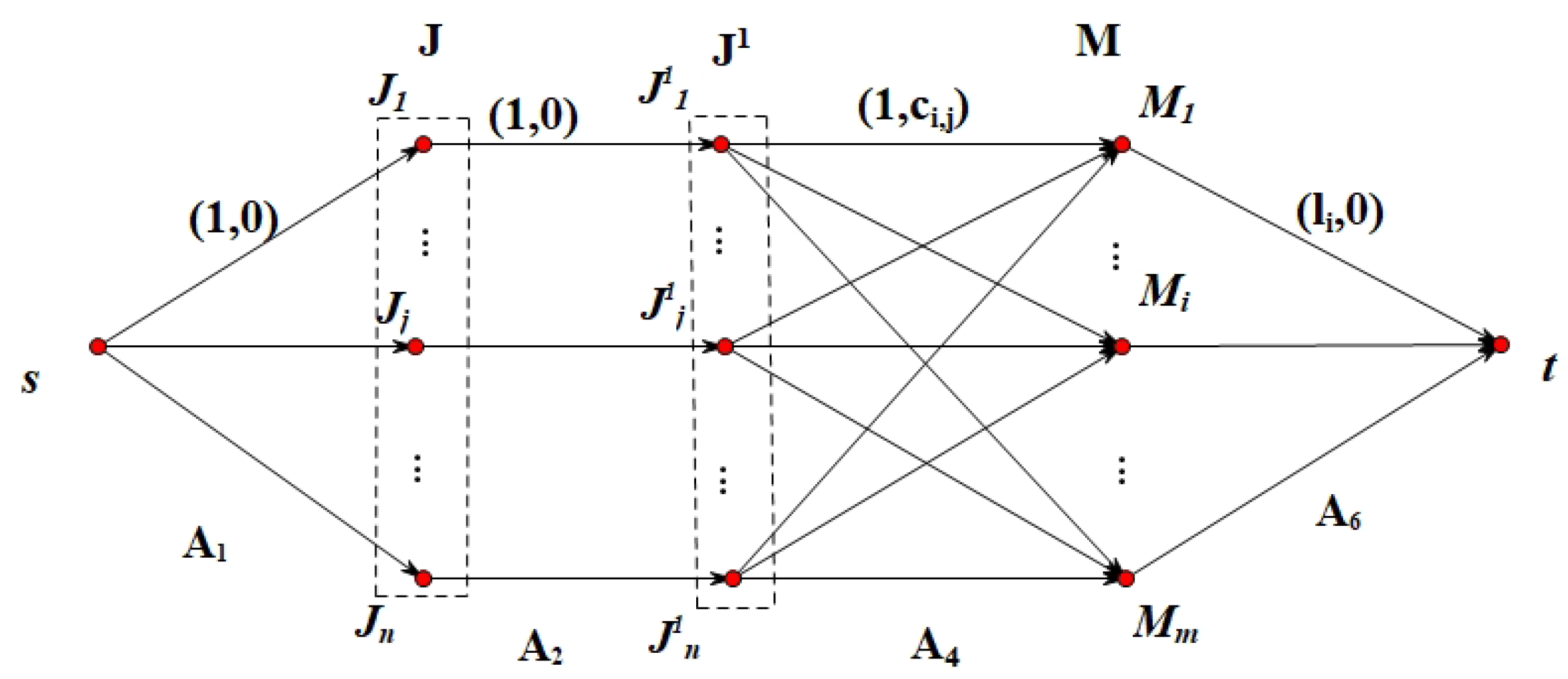
Figure 1 roughly illustrates the process of this transformation.
Given an instance of the CA-BP, we can construct a network in the following ways. Denote , where s and t are two special vertices; and are two sets of vertices copied from the set , respectively; and , where , , , }, , . We may define lower and upper capacities and unit costs on these arcs as follows. For each arc , let the lower capacity and the upper capacity . For each arc , let and . At the same time, let the unit cost for each arc , the unit cost for each arc , and for each arc . In addition, if there exists an -flow in this network , to satisfy for each arc , we call this flow f a bounded -flow in N.
Using the aforementioned construction, we obtain the following key lemma.
Lemma 1. Given an instance of the CA-BP, we can construct a network as mentioned above, such that there is a feasible solution with cost z on the instance I if and only if there is an integer-bounded -flow f of value in N, where the cost is .
Proof. (Necessity) Suppose that there is a feasible scheme with cost z for the linear integer programming (). We construct an integer -flow f in N as follows. For every in , if , let , , , , and ; otherwise, let , , , , and . For each , let , which implies that . Using this construction, we easily obtain that f is an integer-bounded -flow of value n in N, where the cost is .
(Sufficiency) Suppose that there exists an integer-bounded -flow f with value n and cost in N. It is easy to see that for each arc , implying that , and for each arc . We construct a scheme for the linear integer programming (IP) as follows. For each arc , if , denote ; otherwise, denote . Using this construction, for each , we have , implying that . This easily shows that the scheme is a feasible solution to the linear integer programming (), i.e., a feasible solution for the CA-BP, where the cost is .
This completes the proof of the lemma. □
Using Lemma 1, we easily obtain the following.
Corollary 1. The CA-BP has an optimal solution with cost z if and only if there exists a minimum-cost integer-bounded -flow f of value n in N (mentioned above), where the cost .
In order to find the minimum-cost integer-bounded -flow in N, we need the following definitions.
Definition 2 (The residual network). Suppose that f is a bounded -flow with value k in the network . The residual network of N, with respect to f, is constructed in the following way: (1) At the beginning, let . (2) For each arc , we add two residual arcs and to , where the residual capacities are and . (3) Then, we delete arcs in whose residual capacities are 0.
Definition 3 (The incremental network). Suppose that f is a bounded -flow with value k in the network . The incremental network of N, with respect to f, is constructed in the following way: (1) At the beginning, let . (2) For each arc , we add two incremental arcs and to , where the incremental capacities , and the unit incremental costs , . (3) Then, we delete all arcs in whose incremental capacities are 0.
Similarly, to solve the minimum-cost flow problem, we obtain a result for the bounded flow as follows. The method of proof is similar to Theorem 12.1 in [
10]; we present its proof in detail for completeness.
Lemma 2. Let f be an integer-bounded -flow with value n in the network mentioned above. Then, f is a minimum-cost integer-bounded -flow with value n if and only if the incremental network has no negative directed cycle with respect to the incremental cost function .
Proof. (Necessity) Suppose, to the contrary, that there is a directed cycle with a negative cost in the incremental network . We can augment the current flow f along by some value to obtain a new flow with value n. According to the construction of the incremental network, the augment process does not violate the lower and upper bound constraints, so is an integer-bounded -flow with value n. Since the cost of is negative, we have , which contradicts the fact that f is a minimum-cost integer-bounded -flow.
(Sufficiency) Assume that every directed cycle
in the incremental network
has a non-negative cost. For each arc
and
, we define
by the following:
Let
be another feasible integer-bounded
-flow. Then,
is a feasible circular flow, and we have
where
are directed cycles in the incremental network
, and
. That is, the flow
can be decomposed into flows on some circles. Therefore,
Since every directed cycle has a non-negative total cost , we have .
This completes the proof of the lemma. □
According to the aforementioned results, we can use the following strategies to find a minimum-cost integer-bounded -flow with value n in the network :
- (1)
Firstly, we determine an integer -flow with value in N to satisfy the lower bounds of arc capacities.
- (2)
Secondly, we augment the flow obtained in (1) to a minimum-cost integer-bounded -flow with value n in the network .
To solve stage (1), we construct another network
from the network
, where
,
, and the capacity is
for each
and
for each
. This process is shown in
Figure 2. In this network
, we can use the Edmonds–Karp algorithm [
27] in polynomial time to find an integer
-flow with value
.
Using Lemma 2 and the two aforementioned stages, we design a combinatorial algorithm, denoted by
(Algorithm 1), to solve the CA-BP.
| Algorithm 1: |
- Input:
An instance of the CA-BP. - Output:
A scheme of the linear integer programming (IP) with respect to I, or “no solution”. - Begin
- Step 1.
If (), then Output “no solution”, and STOP. - Step 2.
For the given instance of the CA-BP, as mentioned above, first construct a network , and then construct another network . - Step 3.
Use the Edmonds–Karp algorithm [ 27] in the network to produce an integer -flow with value . - Step 4.
From the -flow in , construct an integer -flow f with value in N as follows: (1) For each arc (), let . (2) For each arc (), let . - Step 5.
While () perform the following: 5.1 For the current integer -flow f in N, construct the corresponding residual network by Definition 2; 5.2 Find a directed path with the least arcs on the residual network , and augment the current integer-bounded -flow f along by the minimum augmentation capacity. - Step 6.
For the current integer-bounded -flow f with value n in N, construct the corresponding incremental network by Definition 3. Apply the minimum mean cycle algorithm [ 28] to produce a minimum mean cycle C in with respect to function . - Step 7.
If (), then Along this minimum mean cycle C, augment this integer-bounded -flow f to a new integer-bounded -flow f by the minimum augmentation capacity, and go to Step 6. - Step 8.
From the -flow f, construct a scheme as follows: for each and , if , choose ; otherwise, . - Step 9.
Output this scheme . - End
|
Using the algorithm , we obtain the following result.
Theorem 1. The algorithm is an optimal algorithm to solve the CA-BP, and it runs in time , where m and n are the numbers of machines and jobs, respectively.
Proof. By Lemma 2, it is easy to see that the algorithm
can optimally solve the CA-BP. In the first stage (Steps 1–5) of the algorithm
, we can use the Edmonds–Karp algorithm [
27] to find an integer
-flow with value
n in time
, where
m and
n are the numbers of machines and jobs, respectively. Furthermore, in the second stage (Steps 6–7) of the algorithm
, we can use the minimum mean cycle algorithm [
28] to find a minimum-cost
-flow with value
n in time
. To sum up, the total running time of the algorithm
is
.
This completes the proof of the theorem. □
To facilitate the understanding of the algorithm
, we give the following small example
:
m = 2,
n = 4. The penalty costs are
,
,
, and
, respectively. The processing time for each job is given in
Table 1, and the upper and lower bound constraints for each machine are given in
Table 2. Now, we consider the processes of applying algorithm
to this example.
Applying Steps 1–4 of the algorithm , an integer -flow f with value in N can be found as follows: (a) ; (b) for each remaining arc . Then, Steps 5–7 augment the current integer -flow f, and a new integer-bounded -flow f with value in N is produced as follows: (1) ; (2) ; (3) ; (4) ; (5) ; (6) for each remaining arc . According to the flow f, a scheme with the optimal value is found, where the optimal scheme is to reject job and to execute job on machine and jobs and on machine .
On the other hand, by further analyzing the construction of
N, we hope to reduce the complexity of the algorithm
to solve the CA-BP. Therefore, according to the other algorithms for solving the minimum-cost flow problem, we intend to design another algorithm to resolve the CA-BP. Using similar arguments as in [
26], we obtain the following result.
Lemma 3. Let f be a minimum-cost bounded -flow with value k in the network as mentioned above, where for each . Let be the shortest directed s–t path in with respect to the cost function ,and be an -flow obtained when augmenting f along by at most the minimum augmentation capacity θ on , that is, Then, is a minimum-cost bounded -flow with value .
Proof. It is easy to see that is a feasible bounded -flow with value in N. Considering the incremental network , the reverse of arc e must be in for any arc .
Suppose, on the contrary, that is not a minimum-cost bounded -flow. As we know from Lemma 2, there must be a negative cycle in . Since f is the minimum-cost bounded -flow with value k in the network N, we obtain that must contain some arcs , , ⋯, in , corresponding to arcs , , ⋯, in , where we denote the set of these arcs as . Let denote a network (which may have multiple arcs) formed by combining the vertices and arcs in and negative cycle . Obviously, in , there is one more arc leaving the vertex s than entering it, there is one more arc entering t than leaving it, and the numbers of leaving arcs and entering arcs of any other vertex are equal.
Let
, and update
by removing the isolated vertices in
. Then,
is the union of an
s–
t path and some cycles, denoted by
where
is an
s–
t path in
,
are the cycles in
, and
holds for each
. Since
,
,
, and
, we have
contradicting the choice of
. Hence,
is the minimum-cost bounded
-flow with value
in the network
N.
This completes the proof of the lemma. □
Using Lemma 3, we design a combinatorial algorithm, denoted by
(Algorithm 2), to resolve the CA-BP.
| Algorithm 2: |
- Input:
An instance of the CA-BP. - Output:
A scheme of the linear integer programming IP with respect to I, or “no solution”. - Begin
- Step 1.
If ( ) then Output “no solution”, and STOP. - Step 2.
For the given instance of the CA-BP, as mentioned above, first construct a network , and then construct another network . - Step 3.
Use the successive shortest path algorithm [ 10, 29] in the network to produce a minimum-cost integer -flow with value . - Step 4.
From the -flow in , construct an integer-bounded -flow f with value in N as follows: (1) For each arc , let . (2) For each arc , let . - Step 5.
While (), perform the following: 5.1 For the current integer-bounded -flow f in N, construct the corresponding incremental network ; ; ; by Definition 3. 5.2 Find a shortest directed path with respect to on the incremental network , and augment the current integer-bounded -flow f along by the minimum augmentation capacity. - Step 6.
For the integer -flow f in , construct a scheme as follows: for each and , if , we choose ; otherwise, . - Step 7.
Output this scheme . - End
|
Using algorithm , we obtain the following result.
Theorem 2. The algorithm can optimally solve the CA-BP, and it runs in time , where n is the number of jobs.
Proof. Using the successive shortest path algorithm [
10,
29], the first stage (Steps 1–4) of algorithm
produces a minimum-cost integer
-flow
in the network
, which can be transformed into a minimum-cost bounded
-flow with value
in
N. In subsequent steps, Lemma 3 guarantees the optimality of the algorithm
.
The complexity of the algorithm can be determined as follows: (1) Using the successive shortest path algorithm, Steps 1–4 need time to find a minimum-cost -flow with value , where n is the number of jobs. (2) Similarly, the other steps need at most time . Hence, the algorithm needs a total time .
This completes the proof of the theorem. □
As an illustration of the algorithm , we also apply the algorithm to the example mentioned above: a four-job example to be scheduled on two machines. Applying Steps 1–4 of the algorithm , a minimum-cost integer -flow with value in N can be found as follows: (1) ; (2) for each remaining arc . Then, executing Step 5 to augment the current minimum-cost integer -flow f along , a new integer-bounded -flow f in N is produced. According to the flow f, a scheme is found by the algorithm , where the scheme is to reject job and execute job on machine and jobs and on machine . It is easy to verify that the optimal value is , and is an optimal scheme.