A Privacy-Preserving Authentication Scheme for a Blockchain-Based Energy Trading System
Abstract
:1. Introduction
- We proposed a new blockchain-based energy trading scheme. We assumed that the energy broker is not a fully trusted entity. Therefore, energy brokers manage the blockchain and act as a middleman between energy traders but do not perform functions such as issuing an authentication token or matching energy traders.
- We adopted lightweight ABE-based access control for energy users. An energy request message of an energy user is encrypted and transmitted to the energy broker, and only energy sellers with the appropriate attributes can confirm the transaction details and respond to the energy buyer. The proposed model adopts ECC-based ABE, which has lower computational costs than pairing-based ABE and is more compatible with blockchain.
- We designed a mutual authentication scheme between energy purchasers and sellers. We analyzed the proposed scheme using informal methods and formal methods, such as the Burrows–Abadi–Needham (BAN) logic [28], the “Automated Validation of Internet Security Protocols and Applications (AVISPA)” tool [29], and the Real-or-Random (RoR) model [30] and proved that the proposed scheme is correct, has resistance to replay attacks, and guarantees semantic security.
Paper Organization
2. Related Works
2.1. Blockchain-Based Energy Trading Systems
2.2. Authentications in Smart Grids
3. Preliminary
3.1. Access Tree
3.2. Blockchain
3.3. Adversary Model
- A can obtain the messages transmitted through public channels. A can attempt to eavesdrop, modify, or forge the messages.
- A can guess the identity and password to log into the obtained smart card. We assume that A can try to guess the identity and password simultaneously.
- A can attempt diverse attacks such as impersonation, session key disclosure, replay, and Man-in-the-Middle (MITM) attacks.
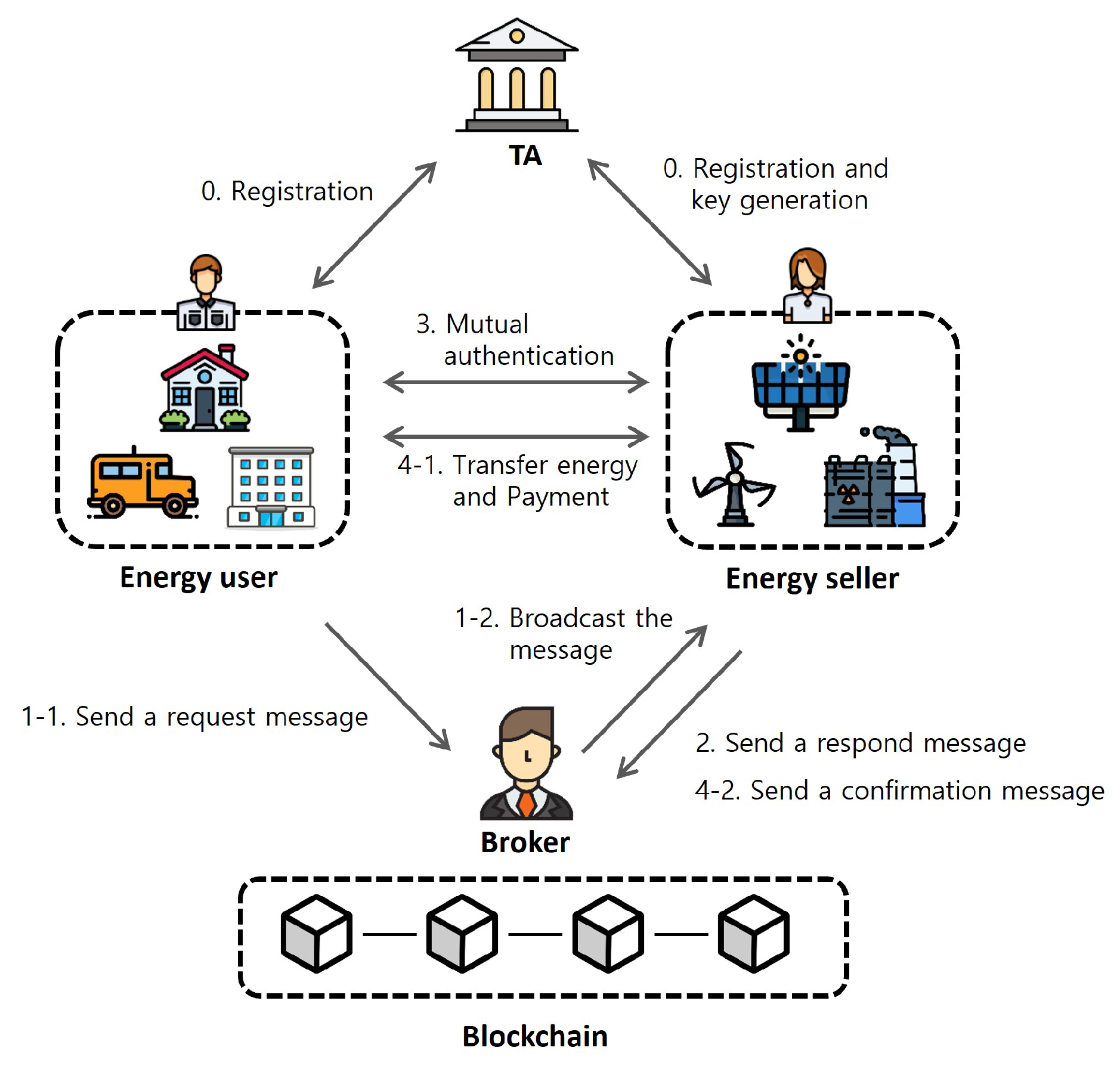
4. System Model
- TA: TA initializes the system, registers EBs and EUs, and issues attribute keys for ESs.
- EB: An EB acts as an intermediary between energy buyers and sellers and may be an individual or an institution [25]. An EB is not a fully trusted entity. After an EB receives an encrypted message from an EU, the EB verifies the signature of the message and then broadcasts the message to nearby ESs. When an ES receives a confirmation message, the EB verifies the message and uploads the transaction record to the blockchain.
- EU: EUs register with the TA to participate in the network. An EU generates an energy request message, which includes wallet address, energy type, demanding amount, price, location, and so on. After that, the encrypted message and the signature for the encrypted message are sent to the EB. The EB can only verify the signature without knowing the detailed information of the request message. Then, the EU mutually authenticates with an ES who has proper attribute keys and conducts energy trading with the ES.
- ES: ESs are issued attribute keys when registered with the TA. An ES receives an encrypted energy request message from the nearby EB and can decrypt the message if the ES has the proper attribute keys. After that, the ES conducts mutual authentication with the EU and transmits energy and receives payment. Then, the ES sends a confirmation message, including the EU and ES’s signatures, to the EB.
5. Proposed Scheme
5.1. Setup
5.2. Registration
- EB registration: chooses a unique identity and sends to . After receives the message, checks whether is registered, and, if not, generates a random number , computes , publishes , and sends to . Then, keeps secure and also writes permission for the blockchain.
- EU registration: For registration, chooses and and sends to . Then, checks whether is registered, and, if not, generates a fuzzy verifier and random numbers and stores in smart card . After that, computes for all x, which are wallet addresses of , and sends to . After receives , generates and computes , , , and . Then, stores in and deletes from . can guarantee anonymity for by using multiple wallet addresses.
- ES key generation: chooses , , and an access tree and sends to . Then, for root node of , generates a unique polynomial with order . sets and chooses other points of randomly. After that, defines other polynomials for other non-leaf nodes z with . Next, for leaf nodes l of , computes . Then, the attribute keys for are and are leaf nodes of ). This process is only executed the first time when generating attribute keys for . After that, randomly generates and and computes , which is a wallet address of . Furthermore, stores and in and sends to . generates and computes , , , and . deletes and stores in . After the ES key generation phase, is published, and maps to , which is a wallet address of .
5.3. Login
5.4. Requesting
- Step 1: randomly chooses and computes . If , chooses another and repeats the process. Then, is used as a symmetric key, and is used to generate message authentication code (MAC).
- Step 2: computes and . Furthermore, computes for each .
- Step 3: The encrypted message is . computes , generates a signature , and transmits to .
5.5. Responding
- Step 1: For each leaf node l of and , computes
- Step 2: For each non-leaf node z, let be a set of child nodes of z, be an arbitrary subset of with nodes, and be a set of indexes . Then, computes
5.6. Confirmation
6. Security Analysis
6.1. Informal Analysis
6.1.1. Smart Card Stolen Attack
6.1.2. Offline Guessing Attack
6.1.3. Impersonation Attack
6.1.4. Mutual Authentication
6.1.5. Anonymity and Untraceability
6.1.6. Denial of Services (DoS) Attack
6.1.7. Perfect Forward Secrecy
6.1.8. Ephemeral Session Random Number Leakage Attack
6.1.9. Privileged Insider Attack
6.1.10. Access Control
6.2. Formal Proof Using BAN-Logic Analysis
- Message meaning rule (MMR):
- Nonce verification rule (NVR):
- Jurisdiction rule (JR):
- Belief rule (BR):
- Freshness rule (FR):
6.2.1. Goals
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
6.2.2. Assumptions
- :
- :
- :
- :
- :
- :
6.2.3. Idealized Forms
- :
- :
6.2.4. BAN Logic Implementation
- Step 1:
- receives .
- Step 2:
- We can obtain by applying the MMR using and .
- Step 3:
- We can obtain by applying the FR using and .
- Step 4:
- We can obtain by applying the NVR using and .
- Step 5:
- We can obtain by applying the BR to .
- Step 6:
- receives .
- Step 7:
- We can obtain by applying the MMR using and .
- Step 8:
- We can obtain by applying the FR to .
- Step 9:
- We can obtain by applying the NVR using and .
- Step 10:
- We can obtain by applying the BR to .
- Step 11:
- can compute , and can compute using the obtained values. Therefore, we obtain and .and
- Step 12:
- We obtain and by applying the JR using and , and and , respectively. Then, the BAN logic’s implementation is complete.and,
6.3. RoR Model
- : In , we assume that A cannot perform any query. Let be a probability that A succeeds in guessing correctly when ends. Then, the advantage function can be defined as the following:
- : A performs the query in . In the proposed scheme, A can obtain and from a public channel. Then, A cannot guess any information about because the obtained values from the public channel are not used to calculate . Therefore, the probability that A guesses correctly when is not changed is as follows:
- : A can execute the and queries to guess . A can arbitrarily generate a message or re-use it. However, each message contains a timestamp and the message digest, and A cannot generate a legitimate message. In order for A to win the game, A has the only way to find a hash collision to compromise , and the following equation is induced:
- : A can execute the query and extracts the stored values of . In this scenario, A must guess the correct and to generate a legitimate message disguising itself as . Even if A succeeds in logging into , the probability that the guessed identity and password are correct is . If the generated message is not correct, revokes from the network. Next, A must succeed to guess and within attempts. Then, the following equation can be induced:
6.4. AVISPA Simulation
7. Performance Analysis
7.1. Computational Cost
- : Execution time for a bilinear pairing operation ≅ 5.811;
- : Execution time for a point scalar multiplication operation ≅ 2.226 ms;
- : Execution time for a point addition operation ≅ 0.0288 ms;
- : Execution time for a map-to-point hash function ≅ 12.418 ms;
- : Execution time for a modular exponentiation ≅ 3.85 ms.
7.2. Communication Cost
7.3. Security Features
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Fang, X.; Misra, S.; Xue, G.; Yang, D. Smart grid—The new and improved power grid: A survey. IEEE Commun. Surv. Tutor. 2011, 14, 944–980. [Google Scholar] [CrossRef]
- Gungor, V.C.; Sahin, D.; Kocak, T.; Ergut, S.; Buccella, C.; Cecati, C.; Hancke, G.P. Smart grid technologies: Communication technologies and standards. IEEE Trans. Ind. Inform. 2011, 7, 529–539. [Google Scholar] [CrossRef]
- Parag, Y.; Sovacool, B.K. Electricity market design for the prosumer era. Nat. Energy 2016, 1, 16032. [Google Scholar] [CrossRef]
- Fischer, D.; Madani, H. On heat pumps in smart grids: A review. Renew. Sustain. Energy Rev. 2017, 70, 342–357. [Google Scholar] [CrossRef]
- Hiremath, R.B.; Shikha, S.; Ravindranath, N.H. Decentralized energy planning; modeling and application—A review. Renew. Sustain. Energy Rev. 2007, 11, 729–752. [Google Scholar] [CrossRef]
- Abdallah, A.; Shen, X. Lightweight authentication and privacy-preserving scheme for V2G connections. IEEE Trans. Veh. Technol. 2017, 3, 2615–2629. [Google Scholar] [CrossRef]
- Saxena, N.; Choi, B.J. Authentication scheme for flexible charging and discharging of mobile vehicles in the V2G networks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1438–1452. [Google Scholar] [CrossRef]
- Wang, N.; Zhou, X.; Lu, X.; Guan, Z.; Wu, L.; Du, X.; Guizani, M. When energy trading meets blockchain in electrical power system: The state of the art. Appl. Sci. 2019, 9, 1561. [Google Scholar] [CrossRef]
- Al-Saif, N.; Ahmad, R.W.; Salah, K.; Yaqoob, I.; Jayaraman, R.; Omar, M.A. Blockchain for electric vehicles energy trading: Requirements, opportunities, and challenges. IEEE Access 2021, 9, 156947–156961. [Google Scholar] [CrossRef]
- Aloqaily, M.; Boukerche, A.; Bouachir, O.; Khalid, F.; Jangsher, S. An energy trade framework using smart contracts: Overview and challenges. IEEE Netw. 2020, 34, 119–125. [Google Scholar] [CrossRef]
- Kim, M.; Lee, J.; Oh, J.; Park, K.; Park, Y.; Park, K. Blockchain based energy trading scheme for vehicle-to-vehicle using decentralized identifiers. Appl. Energy 2022, 322, 119445. [Google Scholar] [CrossRef]
- Guo,, Y.; Zhang,, C.; Wang, C.; Jia, X. Towards Public Verifiable and Forward-Privacy Encrypted Search by Using Blockchain. IEEE Trans. Dependable Secur. Comput. 2023, 20, 2111–2126. [Google Scholar] [CrossRef]
- Hu, S.S.; Cai, C.J.; Wang, Q.; Wang, C.; Luo, X.; Ren, K. Searching an Encrypted Cloud Meets Blockchain: A Decentralized, Reliable and Fair Realization. In Proceedings of the IEEE Conference on Computer Communications (Infocom 2018), Honolulu, HI, USA, 16–19 April 2018. [Google Scholar]
- Cai, C.; Weng, J.; Yuan, X.; Wang, C. Enabling Reliable Keyword Search in Encrypted Decentralized Storage with Fairness. IEEE Trans. Dependable Secur. Comput. 2018, 18, 131–144. [Google Scholar] [CrossRef]
- Wang, M.; Guo, Y.; Zhang, C.; Wang, C.; Huang, H.; Jia, X. MedShare: A Privacy-Preserving Medical Data Sharing System by Using Blockchain. IEEE Trans. Serv. Comput. 2023, 16, 436–451. [Google Scholar] [CrossRef]
- Yu, S.; Park, Y. A robust authentication protocol for wireless medical sensor networks using blockchain and physically unclonable functions. IEEE Internet Things J. 2022, 9, 20214–20228. [Google Scholar] [CrossRef]
- Park, K.; Lee, J.; Das, A.K.; Park, Y. BPPS:Blockchain-enabled privacy-preserving scheme for demand response management in smart grid environments. IEEE Trans. Dependable Secur. Comput. 2023, 20, 1719–1729. [Google Scholar] [CrossRef]
- Wu, Y.; Wu, Y.; Cimen, H.; Vasquez, J.C.; Guerrero, J.M. Towards collective energy Community: Potential roles of microgrid and blockchain to go beyond P2P energy trading. Appl. Energy 2022, 314, 119003. [Google Scholar] [CrossRef]
- Wu, Y.; Wu, Y.; Cimen, H.; Vasquez, J.C.; Guerrero, J.M. P2P energy trading: Blockchain-enabled P2P energy society with multi-scale flexibility services. Energy Rep. 2022, 8, 3614–3628. [Google Scholar] [CrossRef]
- Faisal, J.; Naeem, I.; Shabir, A.; Dohyeun, K. Peer-to-peer energy trading mechanism based on blockchain and machine learning for sustainable electrical power supply in smart grid. IEEE Access 2021, 9, 39193–39217. [Google Scholar]
- Dong, J.; Song, C.; Liu, S.; Yin, H.; Zheng, H.; Li, Y. Decentralized peer-to-peer energy trading strategy in energy blockchain environment: A game-theoretic approach. Appl. Energy 2022, 325, 119852. [Google Scholar] [CrossRef]
- Chen, Y.; Li, Y.; Chen, Q.; Wang, X.; Li, T.; Tan, C. Energy trading scheme based on consortium blockchain and game theory. Comput. Stand. Interfaces 2023, 84, 103699. [Google Scholar] [CrossRef]
- Aitzhan, N.Z.; Svetinovic, D. Security and privacy in decentralized energy trading through multi-signatures, blockchain and anonymous messaging streams. IEEE Trans. Dependable Secur. Comput. 2016, 15, 840–852. [Google Scholar] [CrossRef]
- Zhang, X.; Jiang, S.; Liu, Y.; Jiang, T.; Zhou, Y. Privacy-preserving scheme with account-mapping and noise-adding for energy trading based on consortium blockchain. IEEE Trans. Netw. Serv. Manag. 2021, 19, 569–581. [Google Scholar] [CrossRef]
- Tesfamicael, A.D.; Liu, V.; Mckague, M.; Caelli, W.; Foo, E. A design for a secure energy market trading system in a national wholesale electricity market. IEEE Access 2020, 8, 132424–132445. [Google Scholar] [CrossRef]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October 2006; pp. 89–98. [Google Scholar]
- Yao, X.; Chen, Z.; Tian, Y. A lightweight attribute-based encryption scheme for the Internet of Things. Future Gener. Comput. Syst. 2015, 49, 104–112. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Vigano, L. Automated security protocol analysis with the AVISPA tool. Electron. Notes Theor. Comput. Sci. 2006, 155, 61–86. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the 8th International Workshop on Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Volume 3386, pp. 65–84. [Google Scholar]
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium blockchain for secure energy trading in industrial internet of things. IEEE Trans. Ind. Inform. 2017, 14, 3690–3700. [Google Scholar] [CrossRef]
- Gai, K.; Wu, Y.; Zhu, L.; Qiu, M.; Shen, M. Privacy-preserving energy trading using consortium blockchain in smart grid. IEEE Trans. Ind. Inform. 2019, 15, 3548–3558. [Google Scholar] [CrossRef]
- Li, M.; Hu, D.; Lal, C.; Conti, M.; Zhang, Z. Blockchain-enabled secure energy trading with verifiable fairness in industrial internet of things. IEEE Trans. Ind. Inform. 2020, 16, 6564–6574. [Google Scholar] [CrossRef]
- Guan, Z.; Lu, X.; Yang, W.; Wu, L.; Wang, N.; Zhang, Z. Achieving Efficient and Privacy-Preserving Energy Trading Based on Blockchain and ABE in Smart Grid. J. Parallel Distrib. Comput. 2021, 147, 34–45. [Google Scholar] [CrossRef]
- Li, X.; Wu, F.; Kumari, S.; Xu, L.; Sangaiah, A.K.; Choo, K.K.R. A provably secure and anonymous message authentication scheme for smart grids. J. Parallel Distrib. Comput. 2019, 132, 242–249. [Google Scholar] [CrossRef]
- Wu, L.B.; Wang, J.; Zeadally, S.; He, D.B. Anonymous and efficient message authentication scheme for smart grid. Secur. Commun. Netw. 2019, 2019, 4836016. [Google Scholar] [CrossRef]
- Mahmood, K.; Chaudhry, S.A.; Naqvi, H.; Kumari, S.; Li, X.; Sangaiah, A.K. An elliptic curve cryptography based lightweight authentication scheme for smart grid communication. Future Gener. Comput. Syst. 2018, 81, 557–565. [Google Scholar] [CrossRef]
- Abbasinezhad-Mood, D.; Nikooghadam, M. Design and hardware implementation of a security-enhanced elliptic curve cryptography based lightweight authentication scheme for smart grid communications. Futur. Gener. Comput. Syst. 2018, 84, 47–57. [Google Scholar] [CrossRef]
- Chen, Y.; Martínez, J.F.; Castillejo, P.; López, L. A bilinear map pairing based authentication scheme for smart grid communications: Pauth. IEEE Access 2019, 7, 22633–22643. [Google Scholar] [CrossRef]
- Wu, T.Y.; Lee, Y.Q.; Chen, C.M.; Tian, Y.; Al-Nabhan, N.A. An enhanced pairing-based authentication scheme for smart grid communications. J. Ambient Intell. Human. Comput. 2021, 1–13. [Google Scholar] [CrossRef]
- Wüst, K.; Gervais, A. Do you need a blockchain? In Proceedings of the 2018 Crypto Valley Conference on Blockchain Technology (CVCBT), Zug, Switzerland, 20–22 June 2018; pp. 45–54. [Google Scholar]
- Dolev, D.; Yao, A.C.-C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–207. [Google Scholar] [CrossRef]
- Chattaraj, D.; Bera, B.; Das, A.K.; Saha, S.; Lorenz, P.; Park, Y. Block-CLAP: Blockchain-assisted certificateless key agreement protocol for internet of vehicles in smart transportation. IEEE Trans. Veh. Technol. 2021, 70, 8092–8107. [Google Scholar] [CrossRef]
- Kim, M.; Yu, S.; Lee, J.; Park, Y.; Park, Y. Design of secure protocol for cloud-assisted electronic health record system using blockchain. Sensors 2020, 20, 2913. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Park, Y.; Park, Y.; Lee, S.; Chung, B. A secure and efficient three-factor authentication protocol in global mobility networks. Appl. Sci. 2020, 10, 3565. [Google Scholar] [CrossRef]
- Chattaraj, D.; Bera, B.; Das, A.K.; Rodrigues, J.J.; Park, Y. Designing fine-grained access control for software-defined networks using private blockchain. IEEE Internet Things J. 2021, 9, 1542–1559. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 1999; pp. 388–397. [Google Scholar]
- Canetti, R.; Krawczyk, H. Analysis of key-exchange protocols and their use for building secure channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Innsbruck, Austria, 6–10 May 2001; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2045, pp. 453–474. [Google Scholar]
- Son, S.; Park, Y.; Park, Y. A secure, lightweight, and anonymous user authentication protocol for IoT environments. Sustainability 2021, 13, 9241. [Google Scholar] [CrossRef]
- Ryu, J.; Oh, J.; Kwon, D.; Son, S.; Lee, J.; Park, Y.; Park, Y. Secure ECC-based three-factor mutual authentication protocol for telecare medical information system. IEEE Access 2022, 10, 11511–11526. [Google Scholar] [CrossRef]
- Oh, J.; Yu, S.; Lee, J.; Son, S.; Kim, M.; Park, Y. A secure and lightweight authentication protocol for IoT-based smart homes. Sensors 2021, 21, 1488. [Google Scholar] [CrossRef]
- Von Oheimb, D. The high-level protocol specification language HLPSL developed in the EU project AVISPA. In Proceedings of the 3rd APPSEM II (Applied Semantics II) Workshop (APPSEM’05), Frauenchiemsee, Germany, 12–15 September 2005; pp. 1–17. [Google Scholar]
- Basin, D.; Moedersheim, S.; Vigano, L. OFMC: A symbolic model checker for security protocols. Int. J. Inf. Secur. 2005, 4, 181–208. [Google Scholar] [CrossRef]
- Turuani, M. The CL-Atse protocol analyser. Term Rewrit. Appl. 2006, 277–286. [Google Scholar]
- Kilinc, H.H.; Yanik, T. A survey of SIP authentication and key agreement schemes. IEEE Commun. Surv. Tutor. 2014, 16, 1005–1023. [Google Scholar] [CrossRef]


| Notation | Meaning |
|---|---|
| j-th energy user | |
| k-th energy seller | |
| i-th energy broker | |
| identity and password of | |
| smart card of | |
| encrypted message of | |
| ’s K wallet addresses | |
| M is encrypted/decrypted with symmetric key k | |
| request message of | |
| M is signed using key s with ECDSA |
| Notation | Description |
|---|---|
| two principals | |
| two statements | |
| ≡ | believes |
| ∼ | once said |
| ⇒ | controls |
| ⊲ | receives |
| is fresh | |
| is encrypted with K | |
| and have shared key K |
| Query | Description |
|---|---|
| This query represents an eavesdropping attack carried out by A. A can obtain messages transmitted between and during execution of the mutual authentication protocol. | |
| This query represents A stealing the smart card of a legitimate user and extracting the stored value using a power analysis attack. | |
| This query represents active attacks, in which A can modify eavesdropped messages, send a message M to an instance p, and can receive a response message. | |
| This query represents A conducting a one-way hash operation using the eavesdropped or modified messages. | |
| We assume that there is an unbiased coin c. When A executes the query, c is flipped, and, if the result is the tail, then a random number is given to A. If the result is the head, then the session key is given to A. A guesses whether the given value is the session key or a random number. If the probability that A answers correctly is significantly higher than , the session key cannot guarantee the semantic security. |
| Scheme | Operations | Total Execution Time (ms) |
|---|---|---|
| Li et al. [35] | 35.252 | |
| Wu et al. [36] | 39.1308 | |
| Mahmood et al. [37] | 22.3752 | |
| Abbasinezhad et al. [38] | 17.9232 | |
| Chen et al. [39] | 52.0976 | |
| Wu et al. [40] | 61.0016 | |
| Proposed scheme | 38.0148 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Son, S.; Oh, J.; Kwon, D.; Kim, M.; Park, K.; Park, Y. A Privacy-Preserving Authentication Scheme for a Blockchain-Based Energy Trading System. Mathematics 2023, 11, 4653. https://doi.org/10.3390/math11224653
Son S, Oh J, Kwon D, Kim M, Park K, Park Y. A Privacy-Preserving Authentication Scheme for a Blockchain-Based Energy Trading System. Mathematics. 2023; 11(22):4653. https://doi.org/10.3390/math11224653
Chicago/Turabian StyleSon, Seunghwan, Jihyeon Oh, Deokkyu Kwon, Myeonghyun Kim, Kisung Park, and Youngho Park. 2023. "A Privacy-Preserving Authentication Scheme for a Blockchain-Based Energy Trading System" Mathematics 11, no. 22: 4653. https://doi.org/10.3390/math11224653
APA StyleSon, S., Oh, J., Kwon, D., Kim, M., Park, K., & Park, Y. (2023). A Privacy-Preserving Authentication Scheme for a Blockchain-Based Energy Trading System. Mathematics, 11(22), 4653. https://doi.org/10.3390/math11224653







