Enhancement of Non-Permutation Binomial Power Functions to Construct Cryptographically Strong S-Boxes
Abstract
1. Introduction
1.1. Problem Statement
1.2. Contribution
1.3. Organisation
2. Security Requirement and S-Box Design Methods
2.1. S-Box Properties
2.1.1. Nonlinearity (NL)
2.1.2. Differential Uniformity (DU)
2.1.3. Algebraic Degree (AD)
2.1.4. Linear Approximation (LA)
2.1.5. Algebraic Complexity (AlC)
2.1.6. Fixed Points (Fp) and Opposite Fixed Points (OFp)
2.1.7. Balancedness
2.2. S-Box Design Methods
2.2.1. S-Boxes in Block Ciphers
Mathematical Function
Heuristic
Random Generation
Combination Method
2.2.2. Other S-Boxes Proposal
Random Generation
Heuristic
Mathematical Function
Combination Method
3. S-Box Construction
3.1. Preliminaries
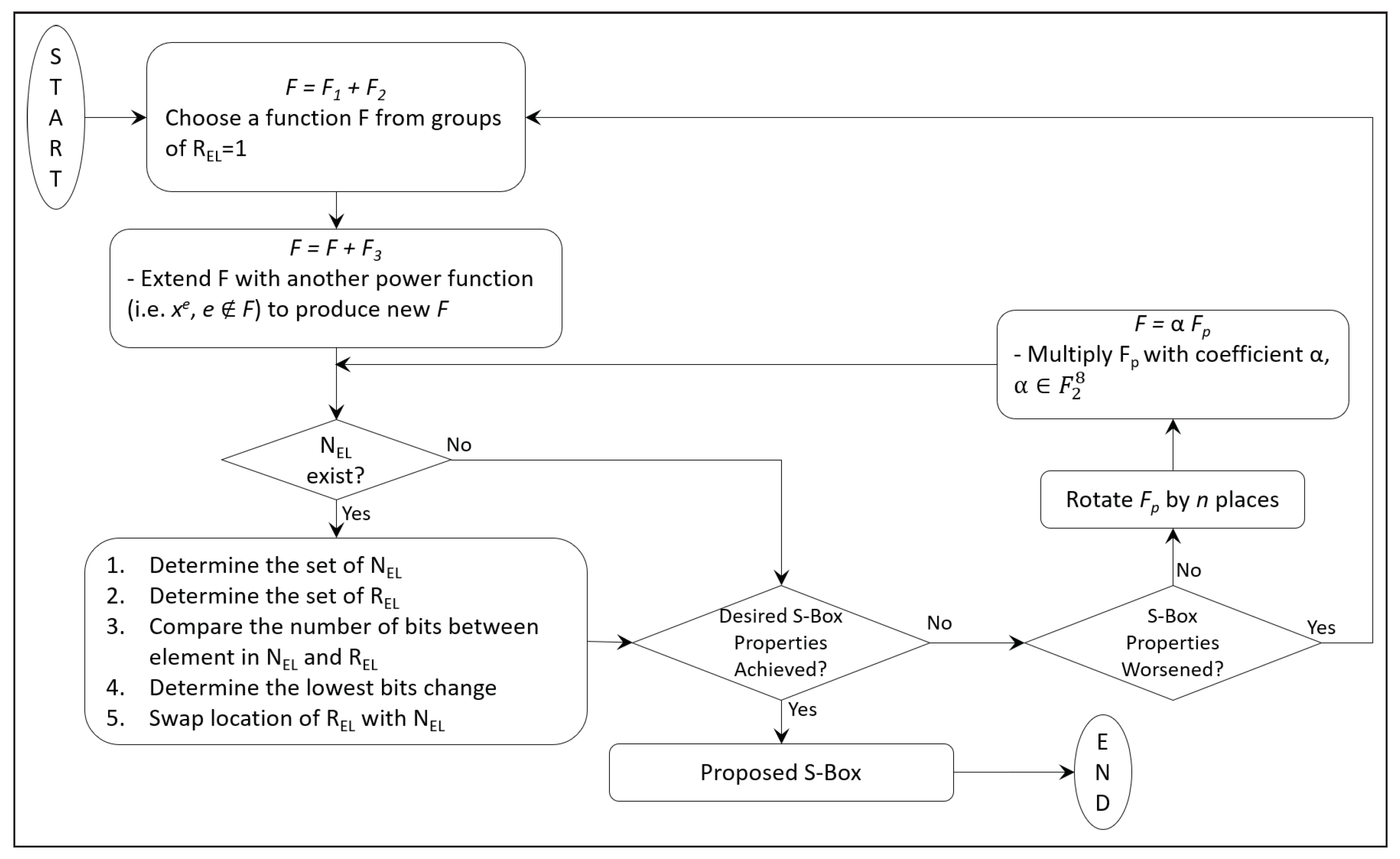
3.2. Our Proposed Construction
4. Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| SPNs | Substitution-Permutation Networks |
| S-box | Substitution box |
| NL | Nonlinearity |
| DU | Differential Uniformity |
| AD | Algebraic Degree |
| AES | Advanced Encryption Standard |
| LA | Linear Approximation |
| MDPI | Multidisciplinary Digital Publishing Institute |
| Desired Element | |
| Repeated Elements | |
| Non-Existent Elements |
Appendix A
Appendix A.1
| A | Linearly Equivalent Binomial Power Function to A |
|---|---|
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , | |
| , , | |
| , , | |
| , , | |
| , , | |
| , , | |
| , , | |
| , , | |
| , , | |
| , , | |
| , , | |
| , , | |
| , , | |
| , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , | |
| , , |
Appendix A.2
| B | Linearly Equivalent Binomial Power Function to B |
|---|---|
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , |
Appendix A.3
| D | Linearly Equivalent Binomial Power Function to D |
|---|---|
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , |
Appendix A.4
| C | Linearly Equivalent Binomial Power Function to C |
|---|---|
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , | |
| , , , , , , |
References
- Shannon, C.E. Communication Theory of Secrecy Systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Biham, E.; Shamir, A. Differential Cryptanalysis of DES-like Cryptosystems. In Advances in Cryptology—CRYPT0 ’90; Lecture Notes in Computer Science; Menezes, A.J., Vanstone, S.A., Eds.; Springer: Berlin/Heidelberg, Germany, 1991; Volume 537, pp. 2–21. [Google Scholar]
- Matsui, M. Linear Cryptanalysis Method for DES Cipher. In EUROCRYPT ’93; Lecture Notes in Computer Science; Helleseth, T., Ed.; Springer: Berlin/Heidelberg, Germany, 1994; Volume 765, pp. 386–397. [Google Scholar]
- Lai, X. Higher Order Derivatives and Differential Cryptanalysis. In Communications and Cryptography; The Springer International Series in Engineering and Computer Science; Blahut, R.E., Costello, D.J.J., Maurer, U., Mittelholzer, T., Eds.; Springer: New York, NY, USA, 1994; Volume 276, pp. 227–233. [Google Scholar]
- Knudsen, L.R. Truncated and Higher Order Differentials. In Fast Software Encryption; Lecture Notes in Computer Science; Preneel, B., Ed.; Springer: Berlin/Heidelberg, Germany, 1995; Volume 1008, pp. 196–211. [Google Scholar]
- Jakobsen, T.; Knudsen, L.R. The Interpolation Attack on Block Ciphers. In Fast Software Encryption; Lecture Notes in Computer Science; Biham, E., Ed.; Springer: Berlin/Heidelberg, Germany, 1997; Volume 1267, pp. 28–40. [Google Scholar]
- Courtois, N.T.; Pieprzyk, J. Cryptanalysis of Block Ciphers with Overdefined Systems of Equations. In ASIACRYPT 2002; Lecture Notes in Computer Science; Zheng, Y., Ed.; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2501, pp. 267–287. [Google Scholar] [CrossRef]
- Federal Information Processing Standard (FIPS) 197; Advanced Encryption Standard. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2001. [CrossRef]
- Dobbertin, H.; Daum, M.; Felke, P.; Lange, T.; Leander, G. S-Boxes and Filters. STORK Project, IST-2002-38273. 2002. Available online: http://www.stork.eu.org/papers/ (accessed on 20 July 2022).
- Carlet, C. Vectorial Boolean Functions for Cryptography; Cambridge University Press: Cambridge, UK, 2010; Chapter Boolean Models and Methods in Mathematics, Computer Science, and Engineering; pp. 398–470. [Google Scholar]
- Mamadolimov, A.; Isa, H.; Mohamad, M.S. Practical Bijective S-box Design. arXiv 2013, arXiv:1301.4723. [Google Scholar]
- Isa, H.; Jamil, N.; Z’aba, M.R. S-box Construction from Non-Permutation Power Functions. In Proceedings of the 6th International Conference on Security of Information and Networks, Aksaray, Turkey, 26–28 November 2013; ACM: New York, NY, USA, 2013; pp. 46–53. [Google Scholar]
- Roslan, M.F.; Seman, K.; Halim, A.; Sayuti, M. Current implementation of advance encryption standard (AES) S-Box. J. Fundam. Appl. Sci. 2017, 9, 518–542. [Google Scholar] [CrossRef]
- Carlet, C. On Known and New Differentially Uniform Functions. In Information Security and Privacy; Lecture Notes in Computer Science; Parampalli, U., Hawkes, P., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6812, pp. 1–15. [Google Scholar]
- Piret, G.; Roche, T.; Carlet, C. PICARO—A Block Cipher Allowing Efficient Higher-Order Side-Channel Resistance. In Applied Cryptography and Network Security; Lecture Notes in Computer Science; Bao, F., Samarati, P., Zhou, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7341, pp. 311–328. [Google Scholar]
- Daemen, J.; Knudsen, L.; Rijmen, V. The Block Cipher SQUARE. In Fast Software Encryption; Lecture Notes in Computer Science; Biham, E., Ed.; Springer: Berlin/Heidelberg, Germany, 1997; Volume 1267, pp. 149–165. [Google Scholar]
- Daemen, J.; Rijmen, V. The Block Cipher BKSQ. In Smart Card Research and Applications; Lecture Notes in Computer Science; Quisquater, J.J., Schneier, B., Eds.; Springer: Berlin/Heidelberg, Germany, 2000; Volume 1820, pp. 236–245. [Google Scholar]
- Daemen, J.; Rijmen, V. AES Proposal: Rijndael. NIST AES Proposal. 1999. Available online: https://csrc.nist.gov/projects/cryptographic-standards-and-guidelines/archived-crypto-projects/aes-development (accessed on 20 July 2022).
- Daemen, J.; Rijmen, V. The Block Cipher Rijndael. In Smart Card Research and Applications; Lecture Notes in Computer Science; Quisquater, J.J., Schneier, B., Eds.; Springer: Berlin/Heidelberg, Germany, 2000; Volume 1820, pp. 277–284. [Google Scholar]
- Nyberg, K. Differentially Uniform Mappings for Cryptography. In Advances in Cryptology—EUROCRYPT ’93; Lecture Notes in Computer Science; Helleseth, T., Ed.; Springer: Berlin/Heidelberg, Germany, 1994; Volume 765, pp. 55–64. [Google Scholar]
- Aoki, K.; Ichikawa, T.; Kanda, M.; Matsui, M.; Moriai, S.; Nakajima, J.; Tokita, T. Camellia: A 128-Bit Block Cipher Suitable for Multiple Platforms—Design and Analysis. In Selected Areas in Cryptography; Lecture Notes in Computer Science; Stinson, D.R., Tavares, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2012, pp. 39–56. [Google Scholar]
- Crowley, P. Mercy: A Fast Large Block Cipher for Disk Sector Encryption. In Fast Software Encryption; Lecture Notes in Computer Science; Goos, G., Hartmanis, J., van Leeuwen, J., Schneier, B., Eds.; Springer: Berlin/Heidelberg, Germany, 2001; Volume 1978, pp. 49–63. [Google Scholar]
- Kwon, D.; Kim, J.; Park, S.; Sung, S.; Sohn, Y.; Song, J.; Yeom, Y.; Yoon, E.J.; Lee, S.; Lee, J.; et al. New Block Cipher: ARIA. In Information Security and Cryptology—ICISC 2003; Lecture Notes in Computer Science; Lim, J.I., Lee, D.H., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; Volume 2971, pp. 432–445. [Google Scholar]
- Diffie, W.; Ledin, G. SMS4 Encryption Algorithm for Wireless Networks. Cryptology ePrint Archive, Report 2008/329. 2008. Available online: http://eprint.iacr.org/ (accessed on 25 July 2022).
- Kurniawan, Y.; Mardiyanto, M.S.; Supriana, I.; Sutikno, S. The New Block Cipher: BC2. Int. J. Netw. Secur. 2009, 8, 16–24. [Google Scholar]
- Hirata, K. The 128-bit Block Cipher HyRAL (Hybrid Randomization Algorithm): Common Key Block Cipher. In Proceedings of the International Symposium on Intelligence Information Processing and Trusted Computing (IPTC), Wuhan, China, 28–29 October 2010; pp. 9–14. [Google Scholar]
- Bucholc, K.; Chmiel, K.; Grocholewska-Czuryło, A.; Idzikowska, E.; Janicka-Lipska, I.; Stokłosa, J. Scalable PP-1 Block Cipher. Int. J. Appl. Math. Comput. Sci. 2010, 20, 401–411. [Google Scholar] [CrossRef]
- Fuller, J.; Millan, W. Linear Redundancy in S-boxes. In Fast Software Encryption; Lecture Notes in Computer Science; Johansson, T., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2887, pp. 74–86. [Google Scholar]
- Stern, J.; Vaudenay, S. CS-Cipher. In Fast Software Encryption; Lecture Notes in Computer Science; Vaudenay, S., Ed.; Springer: Berlin/Heidelberg, Germany, 1998; Volume 1372, pp. 189–204. [Google Scholar]
- Lim, C.H. A Revised Version of CRYPTON: CRYPTON V1.0. In Fast Software Encryption; Lecture Notes in Computer Science; Knudsen, L., Ed.; Springer: Berlin/Heidelberg, Germany, 1999; Volume 1636, pp. 31–45. [Google Scholar]
- Gérard, B.; Grosso, V.; Naya-Plasencia, M.; Standaert, F.X. Block Ciphers That Are Easier to Mask: How Far Can We Go? In Cryptographic Hardware and Embedded Systems—CHES 2013; Lecture Notes in Computer Science; Bertoni, G., Coron, J.S., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; Volume 8086, pp. 383–399. [Google Scholar]
- NIST. Skipjack and KEA Algorithm Specifications. 1998. Available online: https://csrc.nist.gov/Presentations/1998/Skipjack-and-KEA-Algorithm-Specifications/ (accessed on 20 July 2022).
- Junod, P.; Vaudenay, S. FOX: A New Family of Block Ciphers. In Selected Areas in Cryptography; Lecture Notes in Computer Science; Handschuh, H., Hasan, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3357, pp. 114–129. [Google Scholar]
- Biryukov, A.; Perrin, L. On Reverse-Engineering S-Boxes with Hidden Design Criteria or Structure. In Advances in Cryptology – CRYPTO 2015; Lecture Notes in Computer Science; Gennaro, R., Robshaw, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; Volume 9215, pp. 116–140. [Google Scholar]
- Peyravian, M.; Coppersmith, D. A Structured Symmetric-key Block Cipher. Comput. Secur. 1999, 18, 134–147. [Google Scholar] [CrossRef]
- Barreto, P.S.L.M.; Rijmen, V. The ANUBIS Block Cipher. 2000. Available online: https://www.cosic.esat.kuleuven.be/nessie/workshop/ (accessed on 20 July 2022).
- Barreto, P.S.L.M.; Rijmen, V. The KHAZAD Legacy-Level Block Cipher. 2000. Available online: https://www.cosic.esat.kuleuven.be/nessie/workshop/ (accessed on 20 July 2022).
- Standaertt, F.X.; Piret, G.; Rouvroy, G.; Quisquater, J.J.; Legat, J.D. ICEBERG: An Involutional Cipher Efficient for Block Encryption in Reconfigurable Hardware. In Fast Software Encryption; Lecture Notes in Computer Science; Roy, B., Meier, W., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3017, pp. 279–298. [Google Scholar]
- Elkamchouchi, H.M.; Makar, M.A. Kamkar Symmetric Block Cipher. In Proceedings of the Twenty-First National Radio Science Conference (NRSC), Cairo, Egypt, 18 March 2004; pp. C1–C18. [Google Scholar]
- Ohkuma, K.; Muratani, H.; Sano, F.; Kawamura, S. The Block Cipher Hierocrypt. In Selected Areas in Cryptography; Lecture Notes in Computer Science; Stinson, D., Tavares, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2012, pp. 72–88. [Google Scholar]
- Shirai, T.; Shibutani, K.; Akishita, T.; Moriai, S.; Iwata, T. The 128-Bit Blockcipher CLEFIA (Extended Abstract). In Fast Software Encryption: 14th International Workshop, FSE 2007, Luxembourg, Luxembourg, 26–28 March 2007; Revised Selected Papers; Springer: Berlin/Heidelberg, Germany, 2007; pp. 181–195. [Google Scholar]
- Oliynykov, R.; Gorbenko, I.; Kazymyrov, O.; Ruzhentsev, V.; Kuznetsov, O.; Gorbenko, Y.; Dyrda, O.; Dolgov, V.; Pushkaryov, A.; Mordvinov, R.; et al. A New Encryption Standard of Ukraine: The Kalyna Block Cipher; Cryptology ePrint Archive, Report 2015/650. 2015. Available online: https://eprint.iacr.org/2015/650 (accessed on 30 July 2022).
- Kazymyrov, O.; Kazymyrova, V.; Oliynykov, R. A Method for Generation of High-Nonlinear S-Boxes Based on Gradient Descent; Cryptology ePrint Archive, Report 2013/578. 2013. Available online: https://eprint.iacr.org/2013/578 (accessed on 30 July 2022).
- Gao, S.; Ma, W.; Feng, J.; Guo, N.; Yan, Y. Improved Hill-Climbing Methods in the Design of Bijective S-boxes. In Proceedings of the Sixth International Conference on Natural Computation (ICNC), Yantai, China, 10–12 August 2010; Volume 5, pp. 2378–2380. [Google Scholar]
- El-Ramly, S.H.; El-Garf, T.; Soliman, A.H. Dynamic Generation of S-boxes in Block Cipher Systems. In Proceedings of the Eighteenth National Radio Science Conference, Mansoura, Egypt, 27–29 March 2001; Volume 2, pp. 389–397. [Google Scholar]
- Kazlaukas, K.; Vaicekauskas, G.; Smaliukas, R. An Algorithm for Key-Dependent S-Box Generation in Block Cipher System. Informatica 2015, 26, 51–65. [Google Scholar] [CrossRef]
- Balajee, M.K.; Gnanasekar, J.M. Evaluation of Key Dependent S-Box based Data Security Algorithm using Hamming Distance and Balanced Output. TEM J. 2016, 5, 67–75. [Google Scholar]
- El-Latif, A.A.A.; Ramadoss, J.; Abd-El-Atty, B.; Khalifa, H.S.; Nazarimehr, F. A Novel Chaos-Based Cryptography Algorithm and Its Performance Analysis. Mathematics 2022, 10, 2434. [Google Scholar] [CrossRef]
- Gong, G.; Gupta, K.C.; Hell, M.; Nawaz, Y. Towards a General RC4-Like Keystream Generator. In Lecture Notes in Computer Science, Proceedings of Information Security and Cryptology: First SKLOIS Conference, CISC 2005, Beijing, China, 15–17 December 2005; Feng, D., Lin, D., Yung, M., Eds.; Springer: Berlin/ Heidelberg, Germany, 2005; Volume 3822, pp. 162–174. [Google Scholar]
- Mamadolimov, A.; Isa, H.; Ahmad, M.M.; Mohamad, M.S. Nonlinear Boolean Permutations. Pertanika J. Sci. Technol. 2011, 19, 1–9. [Google Scholar]
- Zhoua, Q.; Wong, K.; Liao, X.; Xiang, T.; Hu, Y. Parallel Image Encryption Algorithm based on Discretized Chaotic Map. Chaos 2008, 38, 1081–1092. [Google Scholar] [CrossRef]
- Xu, G.; Zhao, G.; Min, L. The Design of Dynamical S-boxes based on Discrete Chaos Map System. In Proceedings of the IEEE International Conference on Intelligent Computing and Intelligent Systems, Shanghai, China, 20–22 November 2009; Volume 2, pp. 473–478. [Google Scholar]
- Hung, P.A.; Klomkarn, K.; Sooraksa, P. Image Encryption based on Chaotic Map and Dynamic S-box. In Proceedings of the International Symposium on Intelligent Signal Processing and Communications Systems (ISPACS), Okinawa, Japan, 12–15 November 2013; pp. 435–439. [Google Scholar]
- Gondal, M.A.; Raheem, A.; Hussain, I. A Scheme for Obtaining Secure S-Boxes Based on Chaotic Baker’s Map. 3D Research 2014, 5, 17. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T.; Mahmood, H.; Gondal, M.A.; Hussain, I. A Novel Technique for the Construction of Strong S-boxes based on Chaotic Lorenz Systems. Nonlinear Dyn. 2012, 70, 2303–2311. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T.; Batool, S. A New Implementation of Chaotic S-boxes in CAPTCHA. Signal Image Video Process. 2015, 10, 293–300. [Google Scholar] [CrossRef]
- Hussain, I.; Shah, T.; Gondal, M.A.; Mahmood, H. An Efficient Approach for the Construction of LFT S-boxes using Chaotic Logistic Map. Nonlinear Dyn. 2013, 71, 133–140. [Google Scholar] [CrossRef]
- Ali, R.S.; Akif, O.Z.; Jassim, S.A.; Farhan, A.K.; El-Kenawy, E.S.M.; Ibrahim, A.; Ghoneim, M.E.; Abdelhamid, A.A. Enhancement of the CAST Block Algorithm Based on Novel S-Box for Image Encryption. Sensors 2022, 22, 8527. [Google Scholar] [CrossRef]
- Wang, Y.; Yang, L.; Li, M.; Song, S. A Method for Designing S-box based on Chaotic Neural Network. In Proceedings of the Sixth International Conference on Natural Computation (ICNC), Yantai, China, 10–12 August 2010; Volume 2, pp. 1033–1037. [Google Scholar]
- Noughabi, M.; Sadeghiyan, B. Design of S-boxes based on Neural Networks. In Proceedings of the International Conference on Electronics and Information Engineering (ICEIE), Kyoto, Japan, 1–3 August 2010; Volume 2, pp. V2-172–V2-178. [Google Scholar]
- Zaibi, G.; Kachouri, A.; Peyrard, F.; Fournier-Prunaret, D. On Dynamic Chaotic S-box. In Proceedings of the Global Information Infrastructure Symposium, Hammamet, Tunisia, 23–26 June 2009; pp. 1–5. [Google Scholar]
- Ahmad, M.; Rizvi, D.R.; Ahmad, Z. PWLCM-Based Random Search for Strong Substitution-Box Design. In Proceedings of the Second International Conference on Computer and Communication Technologies: IC3T 2015; Springer: New Delhi, India, 2016; Volume 1, pp. 471–478. [Google Scholar]
- Tang, G.; Liao, X. A Method for Designing Dynamical S-boxes based on Discretized Chaotic Map. Chaos Solitons Fractals 2005, 23, 1901–1909. [Google Scholar] [CrossRef]
- Rîncu, C.I.; Iana, V.G. S-box Design based on Chaotic Maps Combination. In Proceedings of the 10th International Conference on Communications (COMM), Bucharest, Romania, 29–31 May 2014; pp. 1–4. [Google Scholar]
- Anees, A.; Ahmed, Z. A Technique for Designing Substitution Box Based on Van der Pol Oscillator. Wirel. Pers. Commun. 2015, 82, 1497–1503. [Google Scholar] [CrossRef]
- Millan, W. How to Improve the Nonlinearity of Bijective S-boxes. In Information Security and Privacy; Lecture Notes in Computer Science; Boyd, C., Dawson, E., Eds.; Springer: Berlin/Heidelberg, Germany, 1998; Volume 1438, pp. 181–192. [Google Scholar]
- Wu, Y.; Noonan, J.P.; Agaian, S.S. Dynamic and Implicit Latin Square Doubly Stochastic S-boxes with Reversibility. In Proceedings of the IEEE International Conference on Systems, Man, and Cybernetics (SMC), Anchorage, AL, USA, 9–12 October 2011; pp. 3358–3364. [Google Scholar]
- Radhakrishnan, S.V.; Subramanian, S. An Analytical Approach to S-box Generation. Comput. Electr. Eng. 2013, 39, 1006–1015. [Google Scholar] [CrossRef]
- Picek, S.; Ege, B.; Batina, L.; Jakobovic, D.; Chmielewski, L.; Golub, M. On Using Genetic Algorithms for Intrinsic Side-channel Resistance: The Case of AES S-box. In Proceedings of the First Workshop on Cryptography and Security in Computing Systems, Vienna, Austria, 20 January 2014; ACM: New York, NY, USA, 2014; pp. 13–18. [Google Scholar]
- Ivanov, G.; Nikolov, N.; Nikova, S. Reversed Genetic Algorithms for Generation of Bijective S-Boxes with Good Cryptographic Properties. Cryptology ePrint Archive, Report 2014/801. 2014. Available online: https://eprint.iacr.org/2014/801 (accessed on 30 July 2022).
- Clark, J.A.; Jacob, J.L.; Stepney, S. The Design of S-boxes by Simulated Annealing. New Gen. Comput. 2005, 23, 219–231. [Google Scholar] [CrossRef]
- Kuznetsov, A.; Wieclaw, L.; Poluyanenko, N.; Hamera, L.; Kandiy, S.; Lohachova, Y. Optimization of a Simulated Annealing Algorithm for S-Boxes Generating. Sensors 2022, 22, 6073. [Google Scholar] [CrossRef]
- Szaban, M.; Seredynski, F. Cryptographically Strong S-Boxes based on Cellular Automata. In Cellular Automata; Lecture Notes in Computer Science; Umeo, H., Morishita, S., Nishinari, K., Komatsuzaki, T., Bandini, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5191, pp. 478–485. [Google Scholar]
- Szaban, M.; Seredynski, F. Designing Cryptographically Strong S-boxes with the use of Cellular Automata. Ann. UMCS Inf. 2009, 8, 27–41. [Google Scholar] [CrossRef]
- Ahmad, M.; Bhatia, D.; Hassan, Y. A Novel Ant Colony Optimization Based Scheme for Substitution Box Design. Procedia Comput. Sci. 2015, 57, 572–580. [Google Scholar] [CrossRef]
- Ivanov, G.; Nikolov, N.; Nikova, S. Cryptographically Strong S-Boxes Generated by Modified Immune Algorithm. In Cryptography and Information Security in the Balkans: Second International Conference, BalkanCryptSec 2015, Koper, Slovenia, 3–4 September 2015; Revised Selected Papers; Springer International Publishing: Cham, Switzerland, 2016; pp. 31–42. [Google Scholar]
- Isa, H.; Jamil, N.; Z’aba, M.R. Construction of Cryptographically Strong S-Boxes Inspired by Bee Waggle Dance. New Gen. Comput. 2016, 34, 221–238. [Google Scholar] [CrossRef]
- Sikdar, D. S-box Optimization Technique with a Primitive Irreducible Polynomial. Int. J. Emerg. Trends Technol. Comput. Sci. 2014, 3, 97–99. [Google Scholar]
- Khan, M.; Azam, N.A. S-Boxes based on Affine Mapping and Orbit of Power Function. 3D Research 2015, 6, 12. [Google Scholar] [CrossRef]
- Yang, M.; Wang, Z.; Meng, Q.; Han, L. Evolutionary Design of S-box with Cryptographic Properties. In Proceedings of the Ninth IEEE International Symposium on Parallel and Distributed Processing with Applications Workshops (ISPAW), Busan, Republic of Korea, 26–28 May 2011; pp. 12–15. [Google Scholar]
- Chun, Y.; Guo, Y. A Research and Improvement Based on Rijndael Algorithm. In Proceedings of the 1st International Conference on Information Science and Engineering (ICISE), Nanjing, China, 26–28 December 2009; pp. 1585–1588. [Google Scholar]
- Cui, J.; Huang, L.; Zhong, H.; Chang, C.; Yang, W. An Improved AES S-box and Its Performance Analysis. Int. J. Innov. Comput. Inf. Control 2011, 7, 2291–2302. [Google Scholar]
- Kumar, A.; Tiwari, N. AES Security Enhancement by Using Double S-Box. Int. J. Comput. Sci. Inf. Technol. 2012, 3, 3980–3984. [Google Scholar]
- Kapalova, N.; Sakan, K.; Algazy, K.; Dyusenbayev, D. Development and Study of an Encryption Algorithm. Computation 2022, 10, 198. [Google Scholar] [CrossRef]
- Hussain, I.; Shah, T.; Gondal, M.A.; Khan, M.; Khan, W.A. Construction of New S-box using a Linear Fractional Transformation. World Appl. Sci. J. 2011, 14, 1779–1785. [Google Scholar]
- Hussain, I.; Shah, T.; Gondal, M.A.; Khan, W.A.; Mahmood, H. A Group Theoretic Approach to Construct Cryptographically Strong Substitution Boxes. Neural Comput. Appl. 2013, 23, 97–104. [Google Scholar] [CrossRef]
- Hussain, I.; Shah, T.; Mahmood, H.; Gondal, M.A. A Projective General Linear Group based Algorithm for the Construction of Substitution Box for Block Ciphers. Neural Comput. 2013, 22, 1085–1093. [Google Scholar] [CrossRef]
- Jin, S.Y.; Baek, J.M.; Song, H.Y. Improved Rijndael-Like S-Box and Its Transform Domain Analysis. In Proceedings of the Sequences and Their Applications—SETA 2006: 4th International Conference, Beijing, China, 24–28 September 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 153–167. [Google Scholar]
- Tran, M.T.; Bui, D.K.; Duong, A.D. Gray S-box for Advanced Encryption Standard. In Proceedings of the International Conference on Computational Intelligence and Security (CIS’08), Suzhou, China, 13–17 December 2008; Volume 1, pp. 253–258. [Google Scholar]
- Dumas, J.G.; Orfila, J.B. Generating S-Boxes from Semi-fields Pseudo-Extensions. arXiv 2014, arXiv:1411.2503. [Google Scholar]
- Li, Y.; Wang, M. Constructing Differentially 4-Uniform Permutations over GF(22m) from Quadratic APN Permutations over GF(22m+1). Des. Codes Cryptogr. 2014, 72, 249–264. [Google Scholar] [CrossRef]
- Fuller, J.; Millan, W.; Dawson, E. Multi-Objective Optimisation of Bijective S-boxes. New Gen. Comput. 2005, 23, 201–218. [Google Scholar] [CrossRef]
- Isa, H.; Jamil, N.; Z’aba, M.R. Improved S-Box Construction from Binomial Power Functions. Malays. J. Math. Sci. 2015, 9, 21–35. [Google Scholar]
- Aslan, B.; Sakalli, M.T.; Bulus, E. Classifying 8-Bit to 8-Bit S-Boxes based on Power Mappings from the Point of DDT and LAT Distributions. In Arithmetic of Finite Fields; Lecture Notes in Computer Science; von zur Gathen, J., Imaña, J.L., Koç, c.K., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5130, pp. 123–133. [Google Scholar]
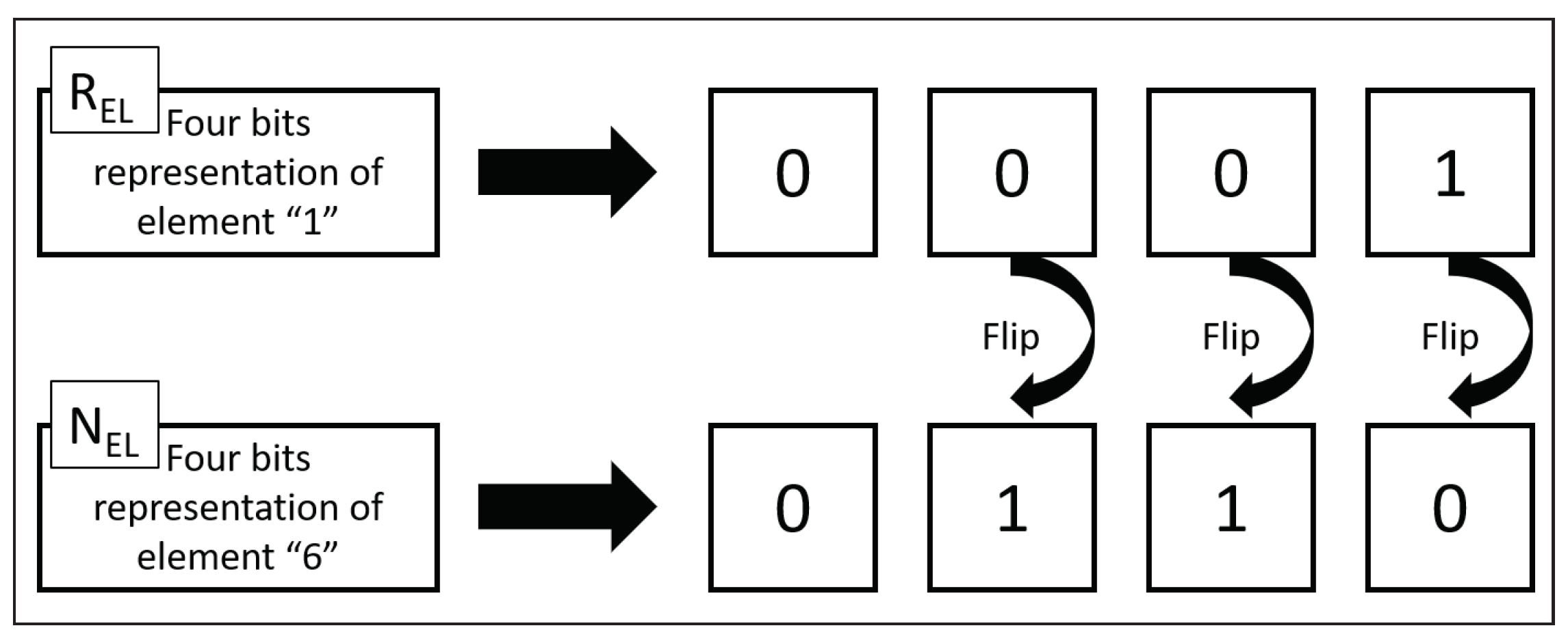
| Properties | Desired Value |
|---|---|
| High Nonlinearity | |
| Low Differential Uniformity | |
| High Algebraic Degree | |
| Low Linear Approximation | |
| Algebraic Complexity | Complex |
| Fixed Opposite Fixed Points | None/Low |
| Balanced Output | Permutation |
| x | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
| 0 | 1 | 8 | F | C | A | 1 | 1 | A | F | F | C | 8 | A | 8 | C |
| 2 | 3 | 4 | 5 | 6 | 7 | 9 | B | D | E | ||
|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 2 | 1 | 2 | 1 | 3 | 2 | 1 | 2 | 3 | 2 | |
| 8 | 2 | 3 | 2 | 3 | 3 | 4 | 1 | 2 | 1 | 2 | |
| A | 1 | 2 | 3 | 4 | 2 | 3 | 2 | 1 | 2 | 3 | |
| C | 3 | 4 | 1 | 2 | 2 | 3 | 2 | 3 | 0 | 1 | |
| F | 3 | 2 | 3 | 2 | 2 | 1 | 2 | 1 | 2 | 1 | |
| d | NL | DU | AD | LA | PERM | |||
|---|---|---|---|---|---|---|---|---|
| 127 | 254, 253, 251, 247, 239, 223, 191 | 112 | 4 | 7 | 16 | 0 | 0 | Y |
| 111 | 222, 246, 189, 123, 237, 219, 183 | 112 | 4 | 6 | 16 | 170 | 85 | N |
| 21 | 42, 84, 168, 162, 138, 81, 69 | 112 | 4 | 3 | 16 | 170 | 85 | N |
| 39 | 78, 156, 114, 228, 57, 201, 147 | 112 | 2 | 4 | 16 | 170 | 85 | N |
| 3 | 6, 12, 24, 48, 96, 192, 129 | 112 | 2 | 2 | 16 | 170 | 85 | N |
| 9 | 18, 36, 72, 144, 66, 132, 33 | 112 | 2 | 2 | 16 | 170 | 85 | N |
| 31 | 62, 124, 248, 241, 227, 199, 143 | 112 | 16 | 5 | 16 | 0 | 0 | Y |
| 91 | 182, 218, 214, 109, 181, 107, 173 | 112 | 16 | 5 | 16 | 0 | 0 | Y |
| 63 | 126, 252, 249, 243, 231, 207, 159 | 104 | 6 | 6 | 24 | 170 | 85 | N |
| 47 | 94, 188, 242, 121, 229, 203, 151 | 104 | 16 | 5 | 24 | 0 | 0 | Y |
| 19 | 38, 76, 152, 98, 196, 49, 137 | 104 | 16 | 3 | 24 | 0 | 0 | Y |
| 95 | 190, 250, 125, 245, 235, 215, 175 | 96 | 4 | 6 | 16 | 204 | 51 | N |
| 5 | 10, 20, 40, 80, 160, 130, 65 | 96 | 4 | 2 | 32 | 204 | 51 | N |
| 7 | 14, 28, 56, 112, 224, 193, 131 | 96 | 6 | 3 | 32 | 0 | 0 | Y |
| 37 | 74, 148, 82, 164, 146, 41, 73 | 96 | 6 | 3 | 32 | 0 | 0 | Y |
| 25 | 50, 100, 200, 70, 140, 145, 35 | 96 | 6 | 3 | 32 | 204 | 51 | N |
| 29 | 58, 116, 232, 142, 209, 163, 71 | 96 | 10 | 4 | 24 | 0 | 0 | Y |
| 11 | 22, 44, 88, 176, 194, 97, 133 | 96 | 10 | 3 | 24 | 0 | 0 | Y |
| 59 | 118, 236, 206, 217, 179, 103, 157 | 96 | 12 | 5 | 32 | 0 | 0 | Y |
| 55 | 110, 220, 230, 185, 115, 205, 155 | 96 | 12 | 5 | 32 | 204 | 51 | N |
| 13 | 26, 52, 104, 208, 134, 161, 67 | 96 | 12 | 3 | 32 | 0 | 0 | Y |
| 61 | 122, 244, 158, 233, 211, 167, 79 | 96 | 16 | 5 | 32 | 0 | 0 | Y |
| 23 | 46, 92, 184, 226, 113, 197, 139 | 96 | 16 | 4 | 32 | 0 | 0 | Y |
| 53 | 106, 212, 166, 154, 169, 83, 77 | 96 | 16 | 4 | 32 | 0 | 0 | Y |
| 27 | 54, 108, 216, 198, 177, 99, 141 | 80 | 26 | 4 | 48 | 170 | 85 | N |
| 87 | 174, 186, 234, 93, 117, 213, 171 | 80 | 30 | 5 | 48 | 170 | 85 | N |
| 43 | 86, 172, 178, 202, 89, 101, 149 | 80 | 30 | 4 | 48 | 0 | 0 | Y |
| 15 | 30, 60, 120, 240, 225, 195, 135 | 76 | 2 | 4 | 12 | 238 | 17 | N |
| 45 | 90, 180, 210, 150, 105, 165, 75 | 76 | 2 | 4 | 12 | 238 | 17 | N |
| 17 | 34, 68, 136 | 0 | 16 | 2 | 8 | 240 | 15 | N |
| 119 | 238, 221, 187 | 0 | 22 | 6 | 8 | 240 | 15 | N |
| 51 | 102, 204, 153 | 0 | 24 | 4 | 10 | 250 | 5 | N |
| 85 | 170 | 0 | 60 | 4 | 6 | 252 | 3 | N |
| 1 | 2, 4, 8, 16, 32, 64, 128 | 0 | 256 | 1 | 128 | 0 | 0 | Y |
| Total | Total | Total | Total | Total | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 15 | 1 | 1024 | 27 | 85 | 35 | 256 | 53 | 85 | 55 | 256 | 79 | 77 | 69 | 128 | 105 | 96 | 80 | 256 |
| 2 | 17 | 1 | 128 | 28 | 221 | 35 | 64 | 54 | 80 | 56 | 256 | 80 | 85 | 69 | 384 | 106 | 100 | 80 | 256 |
| 3 | 51 | 1 | 256 | 29 | 75 | 37 | 256 | 55 | 90 | 58 | 512 | 81 | 97 | 69 | 128 | 107 | 85 | 81 | 896 |
| 4 | 85 | 1 | 128 | 30 | 217 | 39 | 64 | 56 | 89 | 59 | 1024 | 82 | 187 | 69 | 192 | 108 | 125 | 81 | 256 |
| 5 | 16 | 2 | 128 | 31 | 45 | 41 | 128 | 57 | 88 | 60 | 256 | 83 | 78 | 70 | 128 | 109 | 175 | 81 | 512 |
| 6 | 254 | 2 | 1 | 32 | 81 | 41 | 512 | 58 | 92 | 60 | 384 | 84 | 92 | 70 | 768 | 110 | 104 | 82 | 256 |
| 7 | 253 | 3 | 2 | 33 | 85 | 41 | 256 | 59 | 75 | 61 | 256 | 85 | 94 | 70 | 128 | 111 | 105 | 83 | 256 |
| 8 | 252 | 4 | 4 | 34 | 214 | 42 | 64 | 60 | 99 | 61 | 768 | 86 | 96 | 70 | 128 | 112 | 97 | 85 | 256 |
| 9 | 251 | 5 | 4 | 35 | 85 | 43 | 512 | 61 | 195 | 61 | 64 | 87 | 93 | 71 | 256 | 113 | 105 | 85 | 128 |
| 10 | 40 | 6 | 128 | 36 | 213 | 43 | 256 | 62 | 84 | 62 | 128 | 88 | 185 | 71 | 64 | 114 | 171 | 85 | 256 |
| 11 | 250 | 6 | 4 | 37 | 50 | 46 | 128 | 63 | 85 | 63 | 256 | 89 | 84 | 72 | 128 | 115 | 90 | 86 | 128 |
| 12 | 248 | 8 | 12 | 38 | 82 | 46 | 256 | 64 | 89 | 63 | 768 | 90 | 92 | 72 | 256 | 116 | 102 | 86 | 128 |
| 13 | 247 | 9 | 8 | 39 | 90 | 46 | 512 | 65 | 193 | 63 | 64 | 91 | 75 | 73 | 640 | 117 | 120 | 86 | 128 |
| 14 | 246 | 10 | 8 | 40 | 210 | 46 | 64 | 66 | 84 | 64 | 128 | 92 | 93 | 73 | 256 | 118 | 170 | 86 | 64 |
| 15 | 245 | 11 | 32 | 41 | 209 | 47 | 64 | 67 | 88 | 64 | 384 | 93 | 97 | 73 | 256 | 119 | 96 | 88 | 256 |
| 16 | 244 | 12 | 8 | 42 | 75 | 49 | 128 | 68 | 96 | 64 | 256 | 94 | 99 | 73 | 640 | 120 | 104 | 88 | 256 |
| 17 | 243 | 13 | 32 | 43 | 99 | 49 | 256 | 69 | 192 | 64 | 128 | 95 | 123 | 73 | 256 | 121 | 102 | 90 | 256 |
| 18 | 80 | 16 | 128 | 44 | 207 | 49 | 256 | 70 | 89 | 65 | 640 | 96 | 183 | 73 | 320 | 122 | 160 | 96 | 64 |
| 19 | 240 | 16 | 96 | 45 | 206 | 50 | 128 | 71 | 191 | 65 | 128 | 97 | 92 | 74 | 256 | 123 | 99 | 97 | 128 |
| 20 | 239 | 17 | 112 | 46 | 85 | 51 | 256 | 72 | 94 | 66 | 256 | 98 | 93 | 75 | 128 | 124 | 100 | 98 | 128 |
| 21 | 68 | 18 | 128 | 47 | 125 | 51 | 128 | 73 | 85 | 67 | 256 | 99 | 181 | 75 | 320 | 125 | 108 | 100 | 128 |
| 22 | 238 | 18 | 16 | 48 | 205 | 51 | 224 | 74 | 93 | 67 | 256 | 100 | 84 | 76 | 256 | 126 | 144 | 112 | 64 |
| 23 | 64 | 22 | 256 | 49 | 72 | 52 | 256 | 75 | 97 | 67 | 256 | 101 | 108 | 76 | 256 | 127 | 113 | 113 | 128 |
| 24 | 51 | 25 | 512 | 50 | 84 | 52 | 640 | 76 | 189 | 67 | 64 | 102 | 179 | 77 | 1024 | 128 | 120 | 120 | 128 |
| 25 | 230 | 26 | 16 | 51 | 204 | 52 | 64 | 77 | 84 | 68 | 384 | 103 | 178 | 78 | 64 | 129 | 136 | 120 | 192 |
| 26 | 69 | 31 | 512 | 52 | 77 | 53 | 256 | 78 | 92 | 68 | 768 | 104 | 177 | 79 | 128 | 130 | 128 | 128 | 576 |
| Overall Total | 32,131 | ||||||||||||||||||
| Distinct Total | Linearly Non-Equivalent Total | |||
|---|---|---|---|---|
| 1 | 15 | 1 | 1024 | 136 |
| 2 | 17 | 1 | 128 | 16 |
| 3 | 51 | 1 | 256 | 32 |
| 4 | 85 | 1 | 128 | 16 |
| Overall Total | 1540 | 200 | ||
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 8B | C3 | 6E | 5E | 9B | E9 | 03 | 68 | BE | BD | 12 | 27 | 2C | F4 | BB | 41 |
| 1 | 31 | A3 | 8A | 86 | C8 | 38 | 94 | 3C | 08 | 32 | 3E | B5 | 56 | ED | 14 | 47 |
| 2 | 37 | 1B | 7B | DE | 35 | 99 | 1F | A0 | 81 | 65 | 8D | 5B | DC | E3 | 79 | 9C |
| 3 | 64 | E5 | 90 | 06 | D5 | 3A | AE | B4 | DF | 71 | 6D | 16 | A9 | 6C | 25 | BA |
| 4 | CF | 9D | 30 | D3 | EC | A5 | D8 | B0 | 05 | C1 | 6F | 0E | 7F | D4 | 91 | 62 |
| 5 | B9 | E1 | 61 | C9 | D6 | C6 | 43 | E2 | 88 | 52 | 0B | 87 | 4E | 17 | EF | CC |
| 6 | 60 | 2D | 3F | 78 | 2E | 24 | 45 | CB | D1 | C4 | FC | 1C | 22 | FE | 4D | 6B |
| 7 | B6 | CE | 07 | 6A | 66 | 58 | F8 | 0F | 70 | 67 | F5 | 98 | 74 | D0 | FD | 82 |
| 8 | 3B | FB | B3 | 9A | EE | 75 | F2 | 77 | 76 | 34 | 63 | E7 | 29 | 10 | 36 | 44 |
| 9 | 4A | 89 | BC | DB | 18 | 2F | DA | FA | 19 | AB | EB | 7A | 13 | 72 | 50 | D2 |
| A | 9F | 4F | 96 | F3 | 7C | CA | 7D | C0 | 09 | D7 | B1 | C5 | 57 | 73 | 48 | 04 |
| B | A6 | 5A | 11 | A7 | 93 | 97 | 1A | 0D | 26 | 0A | C7 | 69 | F0 | 3D | 39 | 8E |
| C | 00 | 20 | A4 | 95 | AC | E6 | 40 | 59 | 23 | 92 | A8 | 33 | 49 | 02 | F1 | AA |
| D | 15 | 8F | 5F | 1E | 80 | 53 | 4B | 42 | F6 | 7E | 2B | 01 | 9E | E4 | CD | AF |
| E | 5C | 2A | 55 | F7 | 8C | 28 | 0C | E8 | B8 | 5D | 4C | E0 | 84 | 21 | FF | A1 |
| F | B7 | A2 | B2 | BF | F9 | DD | 54 | 83 | 1D | EA | C2 | 85 | 51 | AD | 46 | D9 |
| NL = 108 | DU = 4 | AD = 7 | LA = 20 | |||||||||||||
| (Fp/OFp) = (1/0) | #term = 255 | AlC = Complex | PERM = Y | |||||||||||||
| Rank | S-Box | NL | DU | AD | LA | #Term | Design Method |
|---|---|---|---|---|---|---|---|
| 1 | AES [9] | 112 | 4 | 7 | 16 | 9 | Mathematical |
| Hierocrypt [40] | 112 | 4 | 7 | 16 | 255 | ||
| Camellia [21] | 112 | 4 | 7 | 16 | 254 | ||
| ARIA [23] | 112 | 4 | 7 | 16 | 9 | ||
| CLEFIA [41] | 112 | 4 | 7 | 16 | 254 | ||
| HyRAL [26] | 112 | 4 | 7 | 16 | 253 | ||
| Yang et al. [80] | 112 | 4 | 7 | 16 | 1 | ||
| Cui et al. [82] | 112 | 4 | 7 | 16 | 253 | ||
| Hussain et al. [57] | 112 | 4 | 7 | 16 | 254 | ||
| Dumas and Orfila [90] | 112 | 4 | 7 | 16 | 254 | ||
| Gondal et al. [54] | 112 | 4 | 7 | 16 | 251 | ||
| Khan and Azam [79] | 112 | 4 | 7 | 16 | 252 | ||
| Tran et al. [89] | 112 | 4 | 7 | 16 | 254 | ||
| Kapalova et al. [84] | 112 | 4 | 7 | 16 | 255 | ||
| 2 | Li et al. [91] | 112 | 4 | 5 | 16 | 217 | Mathematical + Heuristic |
| 3 | Yang et al. [80] | 112 | 6 | 7 | 16 | 250 | Mathematical |
| Ivanov et al. [70] | 112 | 6 | 7 | 16 | 253 | Mathematical + Heuristic | |
| 4 | Yang et al. [80] | 110 | 4 | 7 | 18 | 253 | Mathematical |
| 5 | Yang et al. [80] | 110 | 6 | 7 | 18 | 253 | Mathematical |
| Ivanov et al. [70] | 110 | 6 | 7 | 18 | 254 | Mathematical + Heuristic | |
| 6 | This Paper | 108 | 4 | 7 | 20 | 255 | Mathematical + Heuristic |
| Isa et al. [93] | 108 | 4 | 7 | 20 | 3 | Mathematical | |
| 7 | Ivanov et al. [70] | 108 | 6 | 7 | 20 | 253 | Mathematical + Heuristic |
| Isa et al. [77] | 108 | 6 | 7 | 20 | 253 | ||
| 8 | Isa et al. [93] | 108 | 6 | 4 | 20 | 3 | Mathematical |
| 9 | Ivanov et al. [70] | 106 | 6 | 7 | 22 | 252 | Mathematical + Heuristic |
| Fuller et al. [28,92] | 106 | 6 | 7 | 22 | 254 | ||
| Hierocrypt [40] | 106 | 6 | 7 | 22 | 253 | ||
| Isa et al. [93] | 106 | 6 | 7 | 22 | 3 | Mathematical | |
| 10 | Isa et al. [12] | 104 | 6 | 7 | 24 | 255 | Mathematical + Heuristic |
| Ivanov et al. [70] | 104 | 6 | 7 | 24 | 255 | ||
| 11 | KALYNA [42] | 104 | 8 | 7 | 24 | 254 | Heuristic |
| Kazymyrov et al. [43] | 104 | 8 | 7 | 24 | 254 | Random | |
| 12 | Mamadolimov et al. [11] | 102 | 8 | 7 | 26 | 254 | Mathematical + Heuristic |
| 13 | Kazymyrov et al. [43] | 100 | 8 | 7 | 28 | 254 | Random |
| 14 | Picek et al. [69] | 100 | 10 | 7 | 28 | 254 | Heuristic |
| 15 | CLEFIA [41] | 100 | 10 | 6 | 28 | 246 | Mathematical |
| 16 | Picek et al. [69] | 100 | 12 | 7 | 28 | 253 | Heuristic |
| SKIPJACK [32] | 100 | 12 | 7 | 28 | 255 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Isa, H.; Syed Junid, S.A.A.; Z’aba, M.R.; Endut, R.; Ammar, S.M.; Ali, N. Enhancement of Non-Permutation Binomial Power Functions to Construct Cryptographically Strong S-Boxes. Mathematics 2023, 11, 446. https://doi.org/10.3390/math11020446
Isa H, Syed Junid SAA, Z’aba MR, Endut R, Ammar SM, Ali N. Enhancement of Non-Permutation Binomial Power Functions to Construct Cryptographically Strong S-Boxes. Mathematics. 2023; 11(2):446. https://doi.org/10.3390/math11020446
Chicago/Turabian StyleIsa, Herman, Syed Alwee Aljunid Syed Junid, Muhammad Reza Z’aba, Rosdisham Endut, Syed Mohammad Ammar, and Norshamsuri Ali. 2023. "Enhancement of Non-Permutation Binomial Power Functions to Construct Cryptographically Strong S-Boxes" Mathematics 11, no. 2: 446. https://doi.org/10.3390/math11020446
APA StyleIsa, H., Syed Junid, S. A. A., Z’aba, M. R., Endut, R., Ammar, S. M., & Ali, N. (2023). Enhancement of Non-Permutation Binomial Power Functions to Construct Cryptographically Strong S-Boxes. Mathematics, 11(2), 446. https://doi.org/10.3390/math11020446








