A Lightweight and Privacy-Preserving Authentication Protocol for Healthcare in an IoT Environment
Abstract
:1. Introduction
- Design goals
- Motivations
- Contributions
2. System Model and Attack Model
2.1. System Model
2.2. Attack Model
- The attacker can eavesdrop on the open channels.
- The attacker can modify, insert, replay, and reroute the captured messages.
- The attacker can obtain the stored data if he/she captures a sensor node.
- If an attacker obtains the device of the user, he/she can get all the data kept on the device.
- The attacker may be an insider user, but the gateway is trustworthy, and the registration channels are secure.
3. Our Proposed Scheme
3.1. Initialization Phase
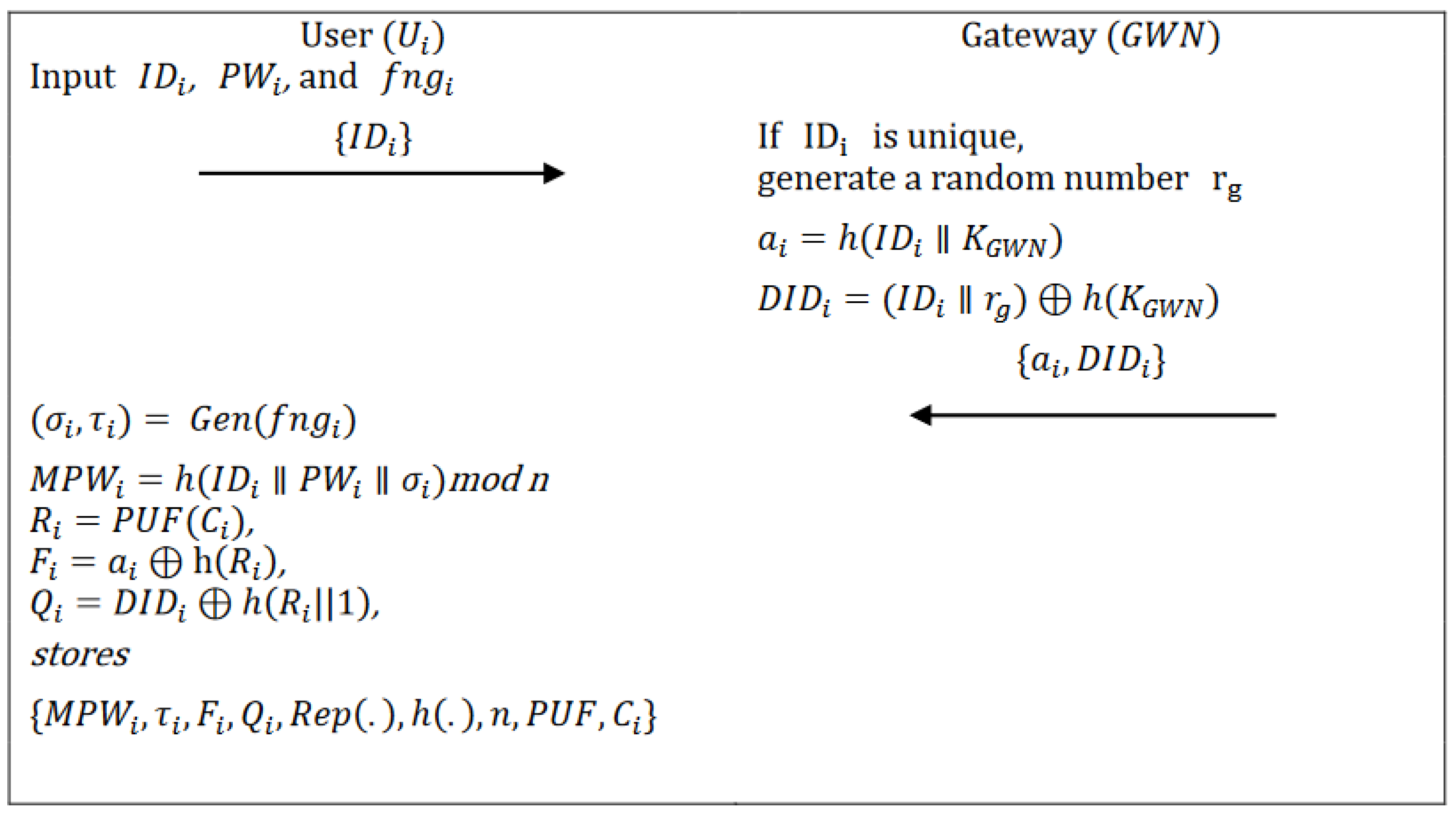
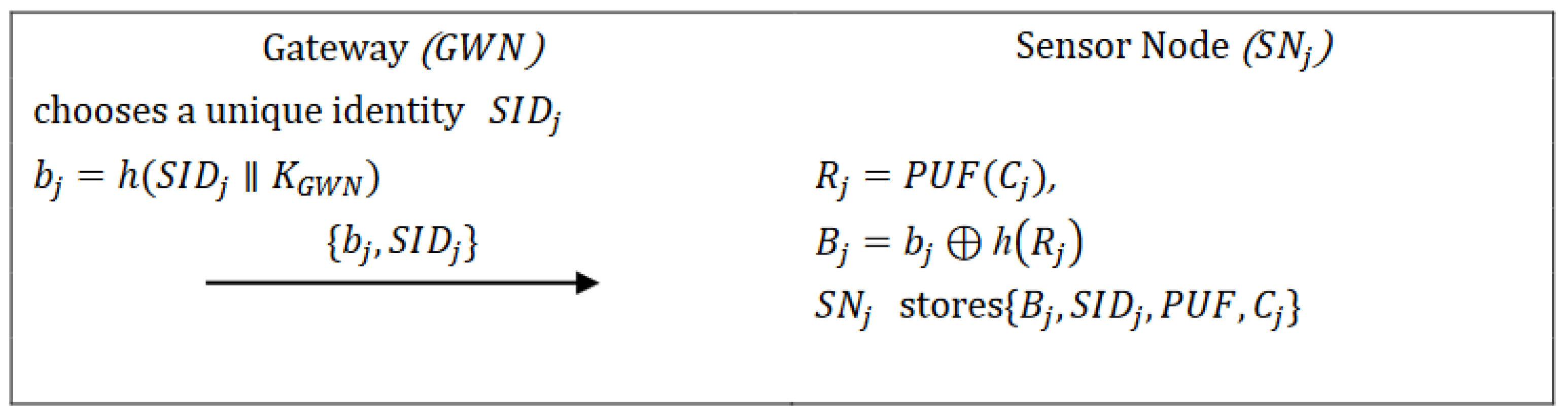
3.2. Registration Phase
3.3. Mutual Authentication and Key Agreement Phase
3.4. Password Update Phase
4. Formal Security Analysis
4.1. Random Oracle Model
4.2. Formal Proof
5. Informal Security Analysis
5.1. Off-Line Password Guessing Attack
5.2. Three-Factor Secrecy
5.3. Forgergery Attack and Impersonation Attack
5.4. Update Asynchronous Attack
5.5. Replay Attack
5.6. Sensor Node Captured Attack
5.7. Anonymity and Unlinkability
5.8. Known Session Key Security
5.9. Perfect Forward Secrecy
5.10. Mutual Authentication
6. Performance Comparison
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wu, Z.Y.; Lee, Y.C.; Lai, F.; Lee, H.C.; Chung, Y. A Secure Authentication Scheme for Telecare Medicine Iinformation Systems. J. Med. Syst. 2010, 36, 1529–1535. [Google Scholar] [CrossRef]
- Lansky, J.; Rahmani, A.M.; Ali, S.; Bagheri, N.; Safkhani, M.; Hassan Ahmed, O.; Hosseinzadeh, M. BCmECC: A Lightweight Blockchain-based Authentication and Key Agreement Protocol for Internet of Things. Mathematics 2021, 9, 3241. [Google Scholar] [CrossRef]
- Zhong, J.; Zhao, T.; Xiong, L.; Lin, R.; Wang, Z. An Anonymous Authentication Scheme Based on Chinese Residue Theorem in Wireless Body Area Networks. Mathematics 2023, 11, 2951. [Google Scholar] [CrossRef]
- Xie, Q.; Liu, W.; Wang, S.; Han, L.; Hu, B.; Wu, T. Improvement of a Uniqueness-and-Anonymity Preserving User Authentication Scheme for Connected Health Care. J. Med. Syst. 2014, 38, 91–101. [Google Scholar] [CrossRef] [PubMed]
- Xie, Q.; Zhang, J.; Dong, N. Robust Anonymous Authentication Scheme for Telecare Medical Information Systems. J. Med. Syst. 2013, 7, 9911. [Google Scholar] [CrossRef]
- Meshram, C.; Lee, C.-C.; Bahkali, I.; Imoize, A.L. An Efficient Fractional Chebyshev Chaotic Map-Based Three-Factor Session Initiation Protocol for the Human-Centered IoT Architecture. Mathematics 2023, 11, 2085. [Google Scholar] [CrossRef]
- Xie, Q.; Li, K.; Tan, X.; Han, L.; Tang, W.; Hu, B. A Secure and Privacy-preserving Authentication Protocol for Wireless Sensor Networks in Smart City. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 119. [Google Scholar] [CrossRef]
- Jia, X.; He, D.; Li, L.; Choo, K.R. Signature-based Three-factor Authenticated Key Exchange for Internet of Things Applications. Multimed. Tools Appl. 2018, 77, 18355–18382. [Google Scholar] [CrossRef]
- Challa, S.; Wazid, M.; Das, A.K.; Kumar, N.; Reddy, A.G.; Yoon, E.; Yoo, K. Secure Signature-based Authenticated Key Establishment Scheme for Future IoT Applications. IEEE Access 2017, 5, 3028–3043. [Google Scholar] [CrossRef]
- Hou, J.L.; Yeh, K.H. Novel Authentication Schemes for IoT based Healthcare Systems. Int. J. Distrib. Sens. Netw. 2015, 11, 183659. [Google Scholar] [CrossRef]
- Chen, R.; Peng, D. Analysis and Improvement of a Mutual Authentication Scheme for Wireless Body Area Networks. J. Med. Syst. 2019, 43, 19. [Google Scholar] [CrossRef] [PubMed]
- Al-Turjman, F.; Alturjman, S. Context-sensitive Access in Industrial Internet of Things (IIoT) Healthcare Applications. IEEE Trans. Ind. Inform. 2018, 14, 2736–2744. [Google Scholar] [CrossRef]
- Kumar, M.; Chand, S. A Lightweight Cloud-assisted Identity-based Anonymous Authentication and Key Agreement Protocol for Secure Wireless Body Area Network. IEEE Syst. J. 2020, 15, 2779–2786. [Google Scholar] [CrossRef]
- Huang, Y.; Wang, W.; Wang, H.; Jiang, T.; Zhang, Q. Authenticating On-body IoT Devices: An Adversarial Learning Approach. IEEE Trans. Wirel. Commun. 2020, 19, 5234–5245. [Google Scholar] [CrossRef]
- Adeli, M.; Bagheri, N.; Meimani, H.R. On the Designing a Secure Biometric-based Remote Patient Authentication Scheme for Mobile Healthcare Environments. J. Ambient Intell. Humaniz. Comput. 2021, 12, 3075–3089. [Google Scholar] [CrossRef]
- Yang, X.; Yi, X.; Nepal, S.; Khalil, I.; Huang, X.; Shen, J. Efficient and Anonymous Authentication for Healthcare Service with Cloud based WBANs. IEEE Trans. Serv. Comput. 2022, 15, 2728–2741. [Google Scholar] [CrossRef]
- Poongodi, M.; Sharma, A.; Hamdi, M.; Maode, M.; Chilamkurti, N. Smart Healthcare in Smart Cities: Wireless Patient Monitoring System using IoT. J. Supercomput. 2021, 77, 12230–12255. [Google Scholar] [CrossRef]
- Ibrahim, M.H.; Kumari, S.; Das, A.K.; Wazid, M.; Odelu, V. Secure Anonymous Mutual Authentication for Star Two-tier Wireless Body Area Networks. Comput. Methods Programs Biomed. 2016, 135, 37–50. [Google Scholar] [CrossRef]
- Xu, Z.; Xu, C.; Liang, W.; Xu, J.; Chen, H. A Lightweight Mutual Authentication and Key Agreement Scheme for Medical Internet of Things. IEEE Access 2019, 7, 53922–53931. [Google Scholar] [CrossRef]
- Liu, C.; Chung, Y. Secure User Authentication Scheme for Wireless Healthcare Sensor Networks. Comput. Electr. Eng. 2017, 2017. 59, 250–261. [Google Scholar] [CrossRef]
- Li, C.; Wu, T.Y.; Chen, C.L.; Lee, C.C.; Chen, C.M. An Efficient User Authentication and User Anonymity Scheme with Provably Security for IoT-based Medical Care System. Sensors 2017, 17, 1482. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Obaidat, M.S.; Wu, F.; Khan, M.K.; Chen, C. A Secure Three-factor User Authentication Protocol with Forward Secrecy for Wireless Medical Sensor Network Systems. IEEE Syst. J. 2020, 14, 39–50. [Google Scholar] [CrossRef]
- Shuai, M.; Liu, B.; Yu, N.; Xiong, L. Lightweight and Secure Three-factor Authentication Scheme for Remote Patient Monitoring using On-body Wireless Networks. Secur. Commun. Netw. 2019, 2019, 8145087. [Google Scholar] [CrossRef]
- Sharma, G.; Kalra, S. A Lightweight User Authentication Scheme for Cloud-IoT based Healthcare Services. Iran. J. Sci. Technol. Trans. Electr. Eng. 2019, 43, 619–636. [Google Scholar] [CrossRef]
- Gupta, D.S.; Islam, S.H.; Obaidat, M.S.; Karati, A.; Sadoun, B. LAAC: Lightweight Lattice-Based Authentication and Access Control Protocol for E-Health Systems in IoT Environments. IEEE Syst. J. 2021, 15, 3620–3627. [Google Scholar] [CrossRef]
- Fotouhi, M.; Bayat, M.; Das, A.K.; Far, H.A.N.; Pournaghi, S.M.; Doostari, M.A. A Lightweight and Secure Two-factor Authentication Scheme for Wireless Body Area Networks in Health-care IoT. Comput. Netw. 2020, 177, 107333. [Google Scholar] [CrossRef]
- Rangwani, D.; Om, H. Four-factor Mutual Authentication Scheme for Health-care based on Wireless Body Area Network. J. Supercomput. 2021, 78, 5744–5778. [Google Scholar] [CrossRef]
- Shamshad, S.; Ayub, M.F.; Mahmood, K.; Rana, M.; Shafiq, A.; Rodrigues, J.J.P.C. An Identity-Based Authentication Protocol for the Telecare Medical Information System (TMIS) Using a Physically Unclonable Function. IEEE Syst. J. 2022, 15, 4831–4838. [Google Scholar] [CrossRef]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L.; Li, Y. A Lightweight Three-factor Anonymous Authentication Scheme with Privacy Protection for Personalized Healthcare Applications. J. Organ. End User Comput. 2021, 33, 1–18. [Google Scholar] [CrossRef]
- Xie, Q.; Ding, Z.; Hu, B. A Secure and Privacy-Preserving Three-Factor Anonymous Authentication Scheme for Wireless Sensor Networks in Internet of Things. Secur. Commun. Netw. 2021, 2021, 4799223. [Google Scholar] [CrossRef]
- Hu, B.; Tang, W.; Xie, Q. A Two-factor Security Authentication Scheme for Wireless Sensor Networks in IoT Environments. Neurocomputing 2022, 500, 741–749. [Google Scholar] [CrossRef]
- Masud, M.; Gaba, G.S.; Choudhary, K.; Hossain, M.S.; Alhamid, M.F.; Muhammad, G. Lightweight and Anonymity-preserving User Authentication Scheme for IoT-based Healthcare. IEEE Internet Things J. 2022, 9, 2649–2656. [Google Scholar] [CrossRef]
- Wang, S.; Zhou, X.; Wen, K.; Weng, B.; Zeng, P. Security Analysis of a User Authentication Scheme for IoT-Based Healthcare. IEEE Internet Things J. 2023, 10, 6527–6530. [Google Scholar] [CrossRef]
- Kim, K.; Ryu, J.; Lee, Y.; Won, D. An Improved Lightweight User Authentication Scheme for the Internet of Medical Things. Sensors 2023, 23, 1122. [Google Scholar] [CrossRef]
- Wang, C.; Wang, D.; Tu, Y.; Xu, G.; Wang, H. Understanding Node Capture Attacks in User Authentication Schemes for Wireless Sensor Networks. IEEE Trans. Dependable Secur. Comput. 2022, 19, 507–523. [Google Scholar] [CrossRef]
- Maiti, A.; Kim, I.; Schaumont, P. A Robust Physical Unclonable Function with Enhanced Challenge-Response Set. IEEE Trans. Inf. Forensics Secur. 2011, 7, 333–345. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the Security of Public Key Protocols. IEEE Trans. Inform. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Rahman, A.; Hossain, M.S.; Alrajeh, N.A.; Alsolami, F. Adversarial Examples—Security Threats to COVID-19 Deep Learning Systems in Medical IoT Devices. IEEE Internet Things J. 2021, 8, 9603–9610. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s Law in Passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Two Birds with One Stone: Two-factor Authentication with Security Beyond Conventional Bound. IEEE Trans. Dependable Secur. Comput. 2018, 15, 708–722. [Google Scholar] [CrossRef]
- Koshy, J.; Wirjawan, I.; Pandey, R.; Ramin, Y. Balancing Computation and Communication Costs: The Case for Hybrid Execution in Sensor Networks. Ad Hoc Netw. 2008, 6, 1185–1200. [Google Scholar] [CrossRef]


| Notations | Descriptions |
|---|---|
| User (Doctor) | |
| Adversary | |
| sensor node | |
| Password of | |
| Personal identity of | |
| Unique identity of | |
| The bioinformatics (fingerprint) of | |
| Session key | |
| Temporary identity of | |
| Hash function | |
| Concatenation | |
| XOR operation | |
| The reproduction function of Fuzzy Extractor algorithm | |
| The generation function of Fuzzy Extractor algorithm | |
| PUF | Physical unclonable function |
| The gateway | |
| Public parameter of Fuzzy Extractor algorithm | |
| Biometric key of Fuzzy Extractor algorithm | |
| Timestamps | |
| The maximum transmission delay time | |
| The generator point of the elliptic curve | |
| The secret parameter of | |
| The challenge and corresponding response of PUF |
| Attacks/Properties | [23] | [24] | [26] | [27] | [29] | [30] | [32] | [34] | Ours |
|---|---|---|---|---|---|---|---|---|---|
| Privileged-Insider Attack | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ |
| Off-line Password Guessing Attack | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ |
| Impersonation Attack | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ |
| Replay Attack | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Man-in-Middle Attack | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Smart Card (Device) Loss Attack | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ |
| Sensor Node Captured Attack | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ |
| Stolen-Verifier Attack | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ |
| Update Asynchronous Attack | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ |
| Identity Anonymity | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ |
| Mutual Authentication | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Session Key Secrecy | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ |
| Known Session Key Attack | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ |
| Perfect Forward Secrecy | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ |
| Unlinkability | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ |
| n-Factor Security | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xie, Q.; Ding, Z.; Xie, Q. A Lightweight and Privacy-Preserving Authentication Protocol for Healthcare in an IoT Environment. Mathematics 2023, 11, 3857. https://doi.org/10.3390/math11183857
Xie Q, Ding Z, Xie Q. A Lightweight and Privacy-Preserving Authentication Protocol for Healthcare in an IoT Environment. Mathematics. 2023; 11(18):3857. https://doi.org/10.3390/math11183857
Chicago/Turabian StyleXie, Qingyun, Zixuan Ding, and Qi Xie. 2023. "A Lightweight and Privacy-Preserving Authentication Protocol for Healthcare in an IoT Environment" Mathematics 11, no. 18: 3857. https://doi.org/10.3390/math11183857
APA StyleXie, Q., Ding, Z., & Xie, Q. (2023). A Lightweight and Privacy-Preserving Authentication Protocol for Healthcare in an IoT Environment. Mathematics, 11(18), 3857. https://doi.org/10.3390/math11183857







