Anti-Recompression Video Watermarking Algorithm Based on H.264/AVC
Abstract
:1. Introduction
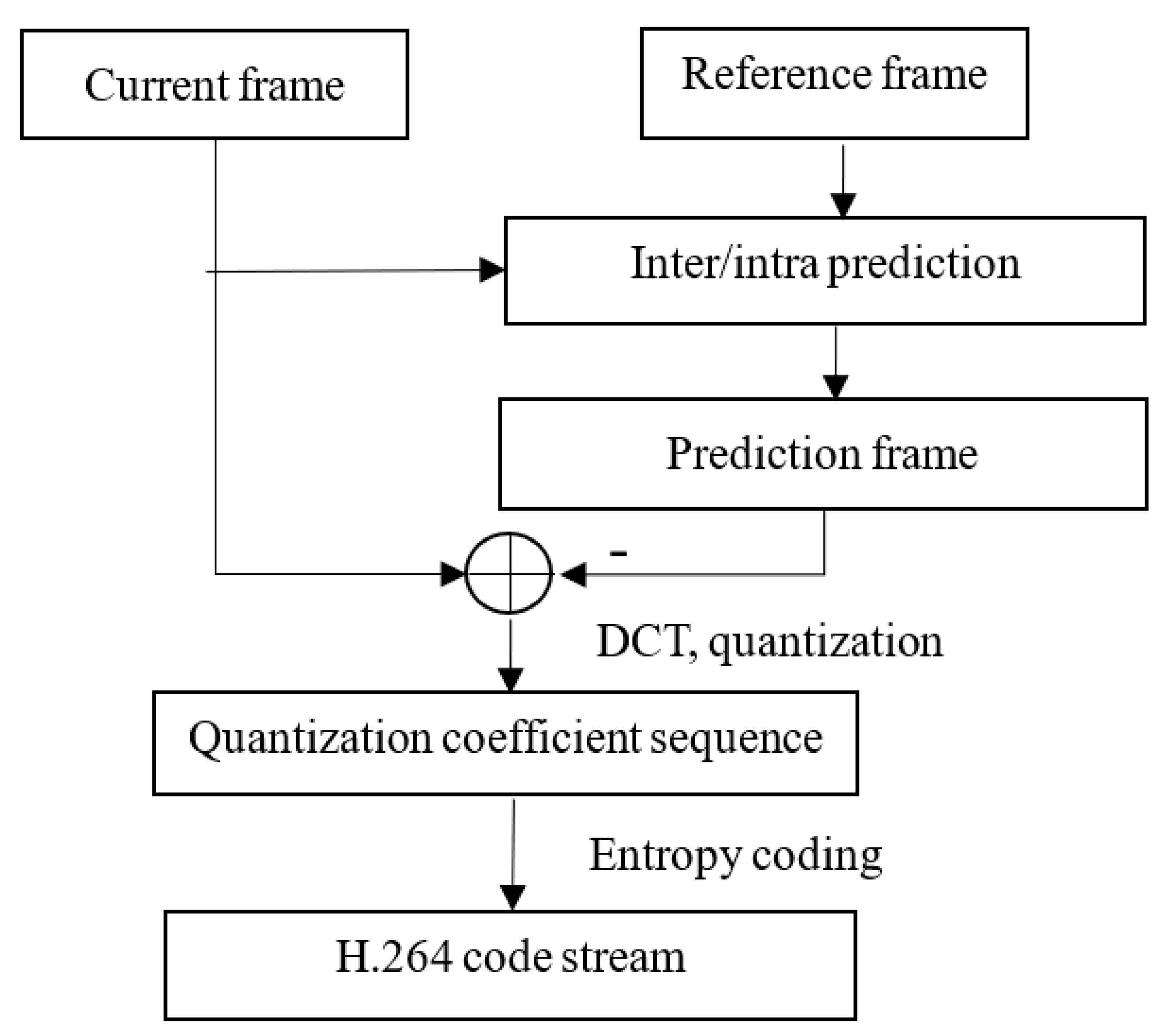
2. H.264 Compression Standard and Watermark Embedding Location Selection
2.1. H.264/AVC Video Compression Standard
2.2. Watermark Embedding Position Selection
3. Watermark Embedding and Extraction Algorithm
3.1. Video Watermark Embedding Algorithm
3.1.1. Modulation Mode of Watermark
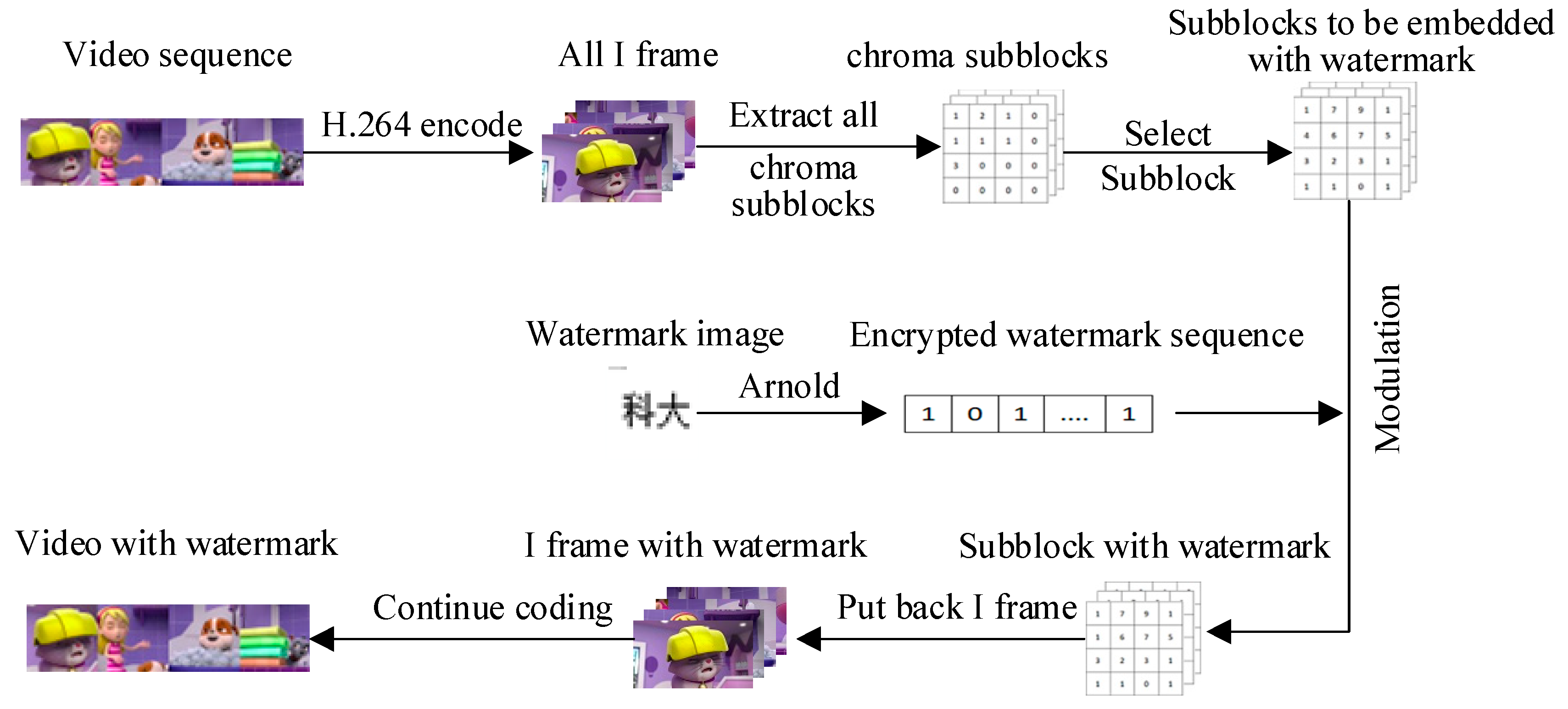
3.1.2. Watermark Embedding Process
- (1)
- The watermarked image of size is encrypted by Arnold scrambling, and then it is converted into a watermark sequence of size .
- (2)
- The H.264/AVC encoder is used to encode the video to the end of quantization, exclude the third I frame chroma subblock with non-zero quantization factor of 2 or −2, calculate the C value of the remaining chroma subblocks, select the 1024 subblocks with the largest C value as the watermark subblocks to be embedded, and record the position of the subblocks in the D array.
- (3)
- The of each subblock to be embedded is judged, to determine the modulation mode according to their minimum value and to modify the value of to achieve watermark embedding, and embed 1-bit watermark information in each subblock.
- (4)
- After embedding all the watermarks, the subblocks are put back to their original positions and video coding continued to obtain the H.264 video stream with watermarks.
| Algorithm 1: | Watermark embedding algorithm. |
| Input: | Video sequence V, Watermark image img |
| Initialize | W1 = zeros(32,32), W = zeros(1,1024) |
| Begin: | W1 = Arnold(img) |
| W = reshape(W1,1,1024) | |
| Encode V with H.264 encoding | |
| Extract chroma subblocks of all I frames in V | |
| Calculate the C of each subblock /*C = NNZ + Ef*/ | |
| Select 1024 subblocks with the largest C /*k = 1, 2, 3, ..., 1024*/ | |
| Store the position of in D | |
| Calculate of | |
| Select and record the modulation mode M corresponding to the minimum value in | |
| By modulating the third non-zero coefficient of to embed W(k), is obtained | |
| Put back to I frame | |
| Put I frame back in V | |
| Continue to encode V with H.264 encoding | |
| Output: | Video with watermark , Subblock location D, Modulation mode M |
3.2. Video Watermark Extraction Algorithm
| Algorithm 2: | Watermark extraction algorithm |
| Input: | Video to be detected v2, Subblock location D, Modulation mode M |
| Initialize: | w = zeros(1,1024), w1 = w2 = zeros(32,32) |
| Begin: | Decode v2 with H.264 decoding |
| Extract all I frames in v2 | |
| Extract subblocks to be detected in all I frames according to D /*l = 1, 2, 3, ..., 1024*/ | |
| Determine the demodulation algorithm according to the modulation mode M | |
| Demodulate and extract w(l) | |
| w1 = reshape(w,32,32) | |
| w2 = IArnold(w1)/*IArnold is the inverse transformation of Arnold*/ | |
| Output: | The extracted watermark image w2 |
4. Experimental Results and Analysis
4.1. Subblock Selection Rationality Experiments
4.2. Invisibility Experiment
4.3. Anti-Recompression and Anti-Requantization Test
4.3.1. Anti-Recompression Test
4.3.2. Anti-Requantization Attack
4.4. Bit Increase Rate Experiment
4.5. Complexity Experiment
4.6. Comparison Experiments with Similar Algorithms
4.6.1. Invisibility Comparison
4.6.2. Comparison of Recompression and Requantification
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wang, Y.F.; Zhou, Y.M.; Qian, Z.X.; Li, S.; Zhang, X.P. Review of robust video watermarking. J. Image Graph. 2022, 27, 27–42. [Google Scholar]
- Liby, J.J.; Jaya, T. HSV model based data hiding in video for watermark applications. J. Intell. Fuzzy Syst. 2021, 41, 2731–2742. [Google Scholar] [CrossRef]
- Amiri, M.D.; Amiri, A.; Meghdadi, M. HVS-based scalable video watermarking. Multimed. Syst. 2019, 25, 273–291. [Google Scholar] [CrossRef]
- Di, F.; Zhang, X.; Kang, W.; Zhao, H.; Lv, Y. Video watermarking algorithm based on NSCT, pseudo 3D-DCT and NMF. Sensors 2022, 22, 4752. [Google Scholar]
- Zhang, S.; Guo, X.; Xu, X.; Li, L.; Chang, C.-C. A video watermark algorithm based on tensor decomposition. Math. Biosci. Eng. 2019, 16, 3435–3449. [Google Scholar] [CrossRef] [PubMed]
- Sun, W.; Zhao, H.; Zhang, X.; Sun, Y.; Liu, X.; Lv, X.; Fan, D. Zero-watermarking algorithm for audio and video matching verification. Aims Math. 2022, 7, 8390–8407. [Google Scholar] [CrossRef]
- Asikuzzaman, M.; Mareen, H.; Moustafa, N.; Choo, K.K.R.; Pickering, M.R. Blind camcording-resistant video watermarking in the DTCWT and SVD domain. IEEE Access 2022, 10, 15681–15698. [Google Scholar] [CrossRef]
- Rajpal, A.; Mishra, A.; Bala, R. A novel fuzzy frame selection based watermarking scheme for MPEG-4 videos using Bi-directional extreme learning machine. Appl. Soft Comput. 2019, 74, 603–620. [Google Scholar] [CrossRef]
- Li, Y.; Wang, H. Robust H.264/AVC video watermarking without intra distortion drift. Multimed. Tools Appl. 2019, 78, 8535–8557. [Google Scholar] [CrossRef]
- Ghasempour, M.; Ghanbari, M. A low complexity system for multiple data embedding into H.264 Coded video bit-Stream. IEEE Trans. Circuits Syst. Video Technol. 2020, 30, 4009–4019. [Google Scholar] [CrossRef]
- Zhou, Y.; Wang, C.; Zhou, X. An Intra-Drift-Free robust watermarking algorithm in high efficiency video coding compressed domain. IEEE Access 2019, 7, 132991–133007. [Google Scholar] [CrossRef]
- Kaur, G.; Kasana, S.S.; Sharma, M.K. An efficient authentication scheme for high efficiency video coding/H.265. Multimed. Tools Appl. 2019, 78, 21245–21271. [Google Scholar] [CrossRef]
- El-Shafai, W.; El-Rabaie, S.; El-Halawany, M.M.; El-Samie, F.E.A. Security of 3D-HEVC transmission based on fusion and watermarking techniques. Multimed. Tools Appl. 2019, 78, 27211–27244. [Google Scholar] [CrossRef]
- Yi, Y.; Feng, G. A Video Zero-watermarking algorithm against recompression coding for 3D-HEVC. J. Signal Process. 2020, 36, 778–786. [Google Scholar]
- Yang, J.; Zheng, G. A fragile video watermarking algorithm based on motion vectors. Electron. Des. Eng. 2017, 25, 153–156. [Google Scholar]
- Sun, J.; Jiang, X.; Liu, J.; Zhang, F.; Li, C. An anti-Recompression video watermarking algorithm in bitstream domain. Tsinghua Sci. Technol. 2021, 26, 22–30. [Google Scholar] [CrossRef]
- Liu, K.; Li, C.; Tian, L.; Zhang, Y.; Song, H. A video watermarking algorithm against re-compression based on H.264/AVC. Comput. Appl. Softw. 2018, 35, 163–168. [Google Scholar]
- Li, C.; Yang, Y.; Liu, K.; Tian, L. A semi-Fragile video watermarking algorithm based on H.264/AVC. Wirel. Commun. Mob. Comput. 2020, 2020, 8848553. [Google Scholar] [CrossRef]
- Xue, Y.; Zhou, J.; Zeng, H.; Zhong, P.; Wen, J. An adaptive steganographic scheme for H.264/AVC video with distortion optimization. Signal Process. Image A Publ. Eur. Assoc. Signal Process. 2019, 76, 22–30. [Google Scholar] [CrossRef]
- Sun, Y.; Wang, J.; Huang, H.; Chen, Q. Research on scalable video watermarking algorithm based on H. 264 compressed domain. Optik 2021, 227, 165911. [Google Scholar] [CrossRef]
- Nguyen, T.S. Reversible Data Hiding Scheme Based on Coefficient Pair Mapping for Videos H. 264/AVC without Distortion Drift. Symmetry 2022, 14, 1768. [Google Scholar] [CrossRef]
- Tian, L.; Dai, H.; Li, C. A semi-fragile video watermarking algorithm based on chromatic Residual DCT. Multimed. Tools Appl. 2020, 79, 1759–1779. [Google Scholar] [CrossRef]
- Di, F.; Sun, W.; Zhao, H.; Kang, W. Audio and video matching zero-watermarking algorithm based on NSCT. Complexity 2022, 2022, 3445583. [Google Scholar]
- Ding, H.; Tao, R.; Sun, J.; Liu, J.; Zhang, F.; Jiang, X.; Li, J. A compressed-domain robust video watermarking against recompression attack. IEEE Access 2021, 9, 35324–35337. [Google Scholar] [CrossRef]
- Dai, H.; Tian, L.; Li, C. Video watermarking algorithm against recompression based on chromatic DCT. Comput. Eng. Des. 2019, 40, 1218–1224. [Google Scholar]








| Parameter Type | Parameter Value |
|---|---|
| Frame rate | 30 fps |
| GOP structure | IPPP |
| Coding grade | Baseline |
| Entropy coding type | CACVL |
| Quantitative parameters | 20 |
| Experiment Video | PSNR1 | PSNR2 | SSIM |
|---|---|---|---|
| Foreman | 35.6151 | 35.5184 | 0.9992 |
| News | 35.9164 | 35.7282 | 0.9974 |
| Mobile | 30.6107 | 30.5390 | 0.9991 |
| Hall | 36.0782 | 35.8611 | 0.9986 |
| Stefan | 34.6160 | 34.4690 | 0.9968 |
| Bus | 34.7719 | 34.7232 | 0.9993 |
| Experiment Video | Original Encoding | Watermarking Encoding | Difference | Original Decoding | Watermarking Decoding | Difference |
|---|---|---|---|---|---|---|
| Foreman | 340.237 | 345.499 | 5.262 | 123.944 | 125.172 | 1.228 |
| News | 299.304 | 302.826 | 3.522 | 118.118 | 120.398 | 2.28 |
| Mobile | 359.185 | 361.152 | 1.967 | 126.979 | 121.886 | 5.093 |
| Hall | 315.482 | 317.878 | 2.396 | 135.158 | 132.640 | 2.518 |
| Experiment Video | SSIM of Ref. [24] | SSIM of Ours |
|---|---|---|
| Mobile | 0.9951 | 0.9991 |
| Stefan | 0.9845 | 0.9968 |
| Foreman | 0.9941 | 0.9992 |
| Bus | 0.9901 | 0.9993 |
| Hall | 0.9763 | 0.9986 |
| Experiment Video | SSIM of Ref. [25] | SSIM of Ours |
|---|---|---|
| Mobile | 0.988 | 0.9967 |
| News | 0.970 | 0.997 |
| Tempete | 0.988 | 0.9962 |
| Flower | 0.972 | 0.9994 |
| Waterfall | 0.981 | 0.9979 |
| Experiment Video | NC Value under Recompression Attack | BER Value under Recompression Attack | BER Value under Requantification Attack | |||
|---|---|---|---|---|---|---|
| Ref. [25] | Ours | Ref. [25] | Ours | Ref. [25] | Ours | |
| Mobile | 0.98 | 0.9968 | 0.03 | 0.0029 | 0.14 | 0.0225 |
| News | 0.92 | 1 | - | - | - | - |
| Tempete | 0.94 | 0.98 | 0.1 | 0.0137 | 0.13 | 0.0205 |
| Flower | 0.97 | 0.9989 | - | - | 0.14 | 0.0225 |
| Waterfall | 0.91 | 0.9926 | 0.17 | 0.0078 | - | - |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fan, D.; Zhao, H.; Zhang, C.; Liu, H.; Wang, X. Anti-Recompression Video Watermarking Algorithm Based on H.264/AVC. Mathematics 2023, 11, 2913. https://doi.org/10.3390/math11132913
Fan D, Zhao H, Zhang C, Liu H, Wang X. Anti-Recompression Video Watermarking Algorithm Based on H.264/AVC. Mathematics. 2023; 11(13):2913. https://doi.org/10.3390/math11132913
Chicago/Turabian StyleFan, Di, Huiyuan Zhao, Changying Zhang, Hongyun Liu, and Xiaoming Wang. 2023. "Anti-Recompression Video Watermarking Algorithm Based on H.264/AVC" Mathematics 11, no. 13: 2913. https://doi.org/10.3390/math11132913
APA StyleFan, D., Zhao, H., Zhang, C., Liu, H., & Wang, X. (2023). Anti-Recompression Video Watermarking Algorithm Based on H.264/AVC. Mathematics, 11(13), 2913. https://doi.org/10.3390/math11132913








