1. Introduction
In order to ensure the confidentiality of a request querying a complex database, techniques to authenticate the initiator and the answering entity and to encrypt the communication channel have been developed. Authentication based on the RSA-type digital signature—the Rivest, Shamir, and Adleman-based algorithm—was initially used ([
1]). However, the power required to compute the parameters involved in this process increased with an increase in the length of the encryption keys. For a fixed computing system (computers and servers), the required power is provided by the involved entities; therefore, in the event that a request is made from and to a fixed computing system, the required computing power for the authentication protocols and for the communication encryption is provided by the query requester(s) and by the systems that store these distributed databases. In contrast, for mobile systems, energy consumption becomes an essential limiting factor; to address this limitation, we adopted elliptic-curve cryptography (ECC) as the solution for processes that require user authentication (as in [
2], or quantum type on [
3]). In the particular case of querying complex databases consisting of structures that are stored on several heterogeneous systems, as well as on physical structures and software, existing studies have proposed implementable solutions for each subcategory of case studies. In this sense, new solutions or their optimizations have continuously been illustrated, and the vulnerabilities of existing solutions have been highlighted. For the queries mentioned above, in situations in which an intelligent answer is necessary, only data mining (
) techniques can be used. These intelligent answers are answers that actually provide an analysis of complex databases and algorithms and highlight certain aspects in their conclusions. More precisely, for situations where databases are heterogeneous complexes (that is, of different types and sizes), the data are stored heterogeneously (that is, on several types of computing systems, which can be personal computers, high-power computers, servers, and even mobile systems); we call these systems heterogeneous database systems (
). For HDBSs, an analysis does not yield only an individual answer—for example, finding not only some records that meet certain conditions but also some items with certain properties that are correlated with other items—and can provide a conclusion based on the correlation of several analyses comparing several databases. In situations where a query would be made from a mobile system to an
-type system, the use of an algorithm from the RSA–C category would require a computing power that consumes more energy than is available.
The solution proposed by the authors comes from their experience and expertise gained from research projects and government contracts. The proposed method addresses the case where a query, which involves , needs to be made from a mobile system with an -type structure. A variant of this method was implemented in a functional system and used within an institutional entity.
2. Existing Solutions for Related Problems
In this section, we briefly describe the existing solutions for problems related to authentication models between systems that involve multiple authentications. The difference between cases solved by other solutions and the case treated by our proposed solution is also described.
Starting from the basic advantage of ECC-type communication security systems, solutions that implement authentication models have been developed, such as the one in [
4,
5]; communication confidentiality systems, such as those developed in [
6,
7,
8]; and analysis models of their limits, also described in [
9,
10,
11,
12]. These models are based on an essential property of ECC systems, namely, the size difference of the cryptographic credentials used in the systems based on elliptic curves, compared with those of systems based on RSA-type models and their variants. This translates into the number of calculations required to create the cryptographic primitives as well as the transformation from plain text to encrypted text for messages that need to be protected against attacks in order to be transmitted on public communication channels.
Numerous studies on authentication and secure communication have been carried out, and more are underway, both within university research laboratories and within the research and development departments of large companies, to provide solutions regarding particular mathematical models that address concrete problems in applications of secure communication in the case of heterogeneous systems. The key models used can be classified into three categories, depending on the type of devices in which they are implemented:
- 1
Systems that are implemented for authentication and secured communications, in which the involved devices in the communication process are classified as servers and computers. In these cases, mathematical models and algorithms of the type described in [
13,
14] can be used. Particular variants of these solutions were implemented for this kind of model, by the authors, in such cases. For these models, the computing power required to compute the parameters involved in obtaining the cryptographic credentials can be assured by the devices in which they are implemented.
In the case studied by the authors, one of the restrictions is related to the computing power available for use in the process generating cryptographic credentials. Therefore, both the mathematical model used and the implemented algorithmic model must take this aspect into account.
- 2
Smart mobile system interconnections, in which unitary models are implemented to secure the communications. For this case, the computation of cryptographic credentials is ensured by a centralized system, and the mobile device uses the cryptographic primitives provided by a trusted party that manages the solution in a centralized way. Then, the mobile device has to use these parameters. Such models are described in [
15,
16]. The solution from [
15] was proposed by a team that included one of the authors from the present study. This solution was implemented and is still being used.
In our studied case, the system is heterogeneous both from the point of view of the devices that are involved in the communication process and from the point of view of the security model for each of the groups of devices, with a solution being proposed for the case where the authentication will be carried out based on the parameters computed also by the mobile systems, with these devices generating their own cryptographic primitives.
- 3
Security models in which mobile devices are involved in the correlation with fixed systems, included in
(Secure Online Transaction Algorithm)-type models. In these cases, three parties are involved: consumer, retailer, and financial credit company. Solutions in this sense can be studied in [
17].
The solution proposed by the authors is for the case where the volume of data transmitted is much higher than that in the case described above and where it is necessary to reduce the risk of malicious users, which in the above case does not need to be treated.
3. Description of The Parameters from Our Proposed Solution
This section describes the elements that define the treated case, the limitations imposed by the problem that needs to be solved, and the method of hierarchization for all the entities of the treated system.
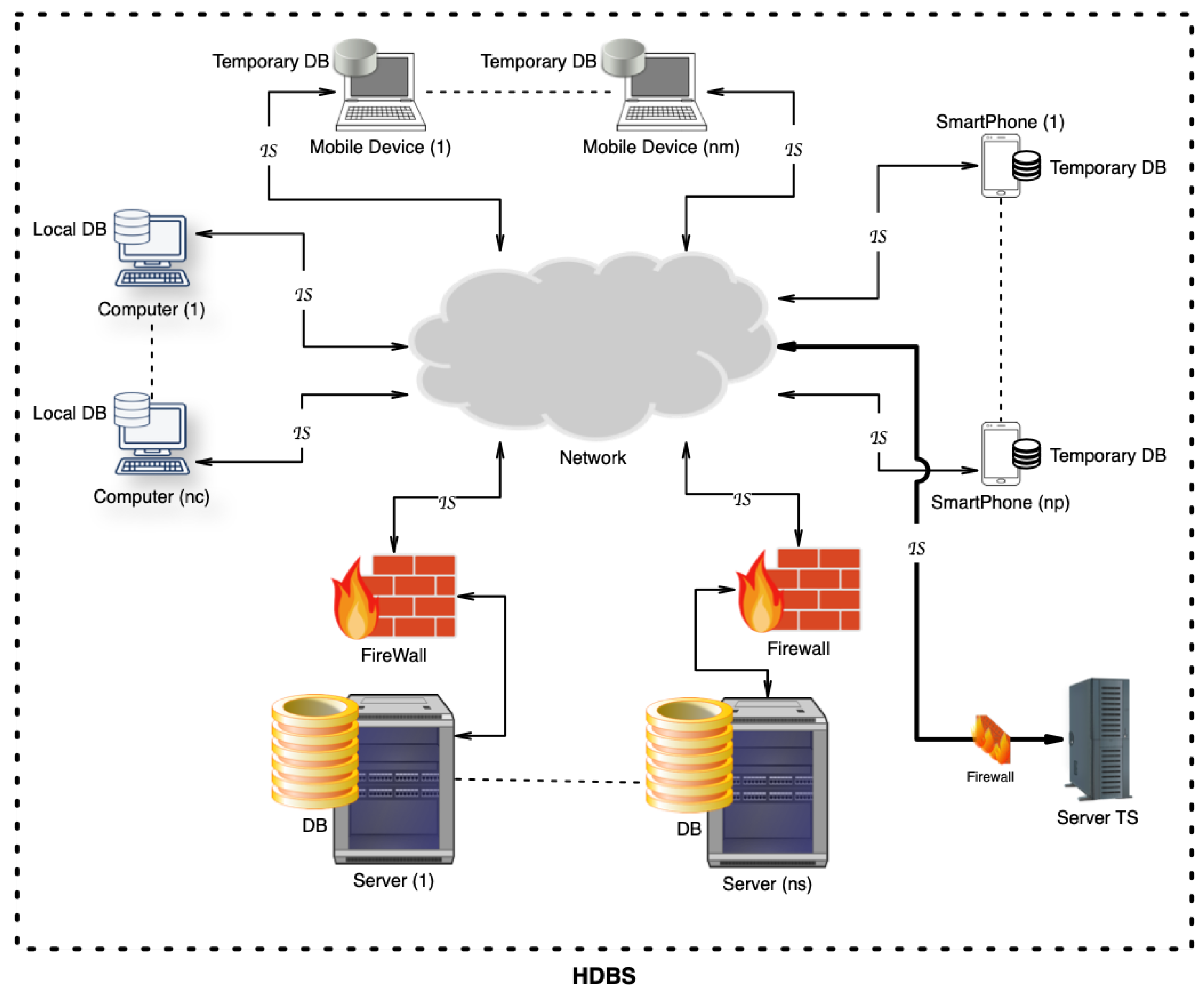
This study was carried out on an actual case in which an entity required a high degree of data security and communication confidentiality. We describe this case, first, by illustrating the components of this system. Let us take a heterogeneous set of computing systems, denoted as follows:
A set of
server-type computing systems, denoted by ;
computers, denoted by ;
mobile devices, denoted by ;
smart mobile phones, denoted by .
The aforementioned devices contain databases, with temporary databases stored in
and
, which means that the data will occasionally be transferred to specialized servers. The credentials required for the authentication and secure communications assurance systems are managed by a specialized device, called a trusted server (
). The presented system is described in
Figure 1.
All the above systems have ensured interconnections, but our proposed system involves different communication protocols, different types of physical communication, and different uptimes—the time during which they can be accessed. Let us denote the sets of communication types throughall systems as .
Let . Then, represents an .
Let be a smart mobile phone that makes a query in , where the result that will be provided involves an analysis of the whole using DM algorithms. The data that pass between and within the query request, as well as the result that provides to , represent a communication that requires double authentication and confidentiality of the communicated data; this is the treated case.
4. Our Solution to Ensure Authorized Access
This section presents the logical scheme of the studied system, the types of involved devices, the abstraction of the proposed model, and the proposed mathematical model for the generation of subspaces that are used in cryptographic processes.
In order to access ’s query service, a complete security process is required, through which proves its identity and the system identifies itself as the one to which wants to connect. This is the process of a double authentication: towards and towards .
For the double-authentication technique, classic RSA-type algorithms can be used; such implementations require key lengths of 2048 bits for the involved security requests and the generation of keys on all computer systems within for the treated case. For , and , this requirement can be fulfilled, but in the case of , the computing power required to generate the asymmetric keys of RSA involves the consumption of energy that is not available on such systems. To solve this requirement, which represents a class of data and communication security subproblems in which the confidentiality requirement is of a high degree and computing systems with low energy resources are involved, an ECC-based system can be used. First, we determine the cases of communication requests, and, depending on the type of devices involved, the mutual authentication method (double authentication) of the systems starts a data transfer process.
Involved devices:
Case 1: sets from and ;
Case 2: , where represents any other device type, including and .
For Case 1, the solution for the authentication was described in [
15] and implemented, and it is still functional within a governmental entity. Let us describe the solution for Case 2.
4.1. Involved Device Authentication
In order to construct various types of quantiles of subspaces over which elliptic curves with cryptographic properties are defined, several studies have been carried out, among which we recommend [
18,
19,
20,
21,
22,
23]. From the authors’ previous studies for cases in which such subspaces were created for communication between devices with low computing power, i.e., smartphones, among those that demonstrated, in practice, superior results using models based on nonsupersingular elliptic curves, we recommend references [
15,
24] to interested readers. In order to define the number of subspaces required to obtain credentials in the double-authentication process for devices within
, we build a model necessary for the particular case studied.
4.2. Mathematical Model for the Proposed Solution
Starting from the general space described in [
24], let the values be generated by a series of integrals based on the partitions defining subspaces
, as follows:
where
represents the quantile considered from the curves series,
is a partition of integer values, and
is the variable defined over the subspace
and
constants and represents the credential parameters of the series.
For each partition, we define its inverse as an elliptic curve from which points that have cryptographic properties in the sense of defining the credentials needed in the process of computing the keys involved in double authentication can be selected. To build this credential system, two constants,
and
, as well as a periodic function defined over a set of real numbers, are selected. In the case considered in the current study, the Weierstrass equation for each
-partition is given by the following formula:
where
and
are constants, and
.
The two values
define a point of this curve:
for which the possibility of being considered as a point with cryptographic properties is computed. These subsets are defined for each partition
of the above described system, thus obtaining a series of elliptic curves from which the points that will be part of the cryptographic algorithm are chosen.
6. Implementation of the Proposed Model
This section illustrates the formulas used to compute the parameters of the subspaces over which the elliptic curves are defined, the graphic representation of these subspaces, and the computation algorithm proposed to compute these parameters.
For the implementations considered in the present case, we consider the optimal method of the type
,
, where
These operations are used to compute the intermediate points Q of coordinates , using points of coordinates and of coordinates . In the case of this type of computation, it is necessary to consider compliance with the restrictions established for each partition defined by .
For each partition , the number of points on the elliptic subcurve, defined over the corresponding space of this partition, can be computed by computing the trace of Frobenius for the particular studied case. Let be a subset of , where represents the corresponding subsets for partition . Thus, we have this value defined as in the form , so for a space of size n, meaning , it becomes , where represents a prime integer for partition and represents the number of points from partition .
Starting from the form described in [
15], for the case of partitioning the parameter space with cryptographic properties for each partition, an endomorphism of the following form is defined:
For each partition
, with
, we have
for each device involved in the double-authentication process.
There is the possibility to compute the number of points with cryptographic properties from the total set of points on these subspaces, according to the size of the partition and the chosen starting point in the process of computing a pair of primary credentials.
6.1. Graphic Representation
In this section, we provide graphic representations of the series of elliptic curves from which the subspaces are chosen and a representation of a point model with cryptographic properties resulting from the ESG algorithm.
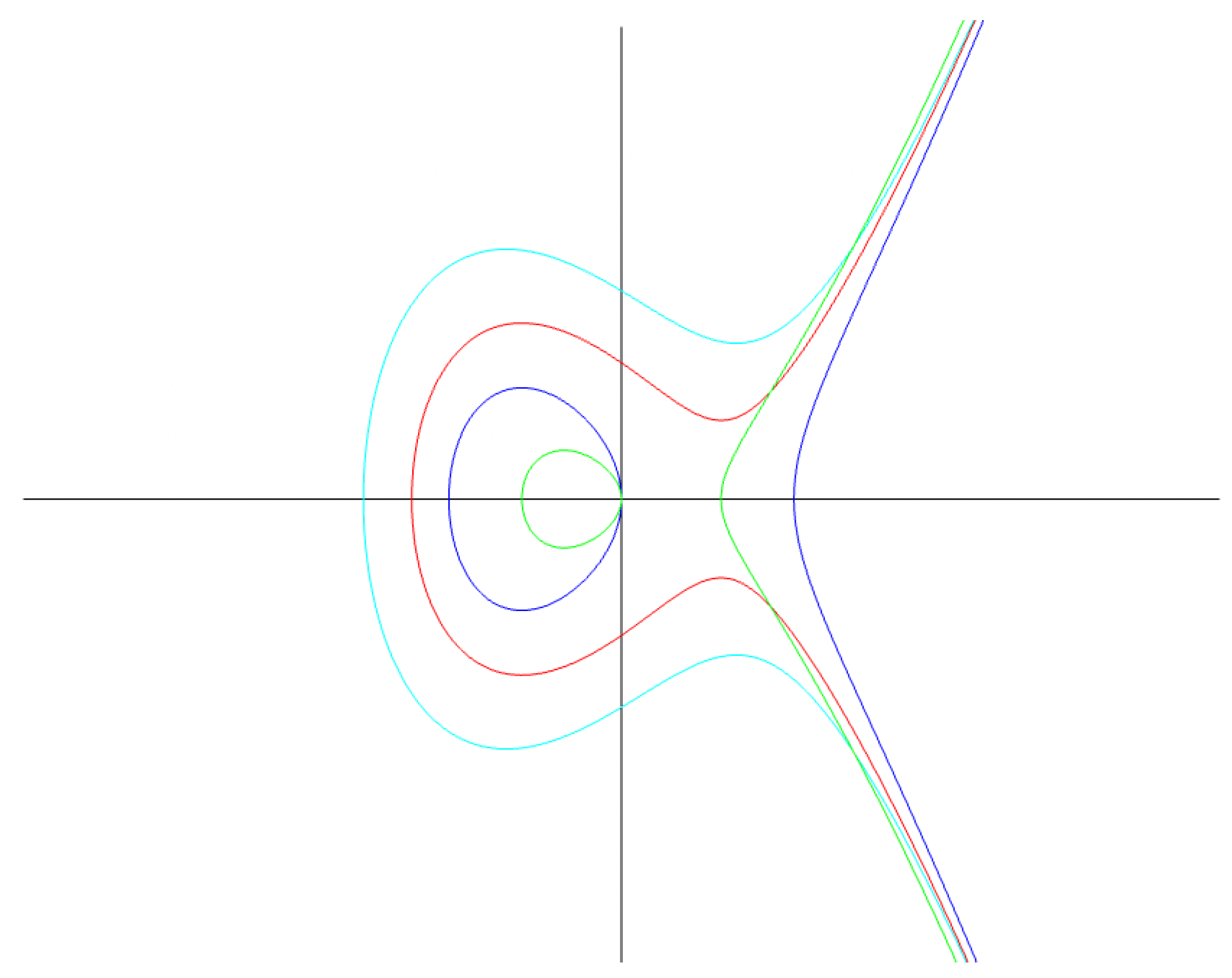
In this regards, in
Figure 2, a series of curves generated according to predefined
subspaces is represented and the choice of subspaces is made in compliance with the conditions from Theorem 1.
In
Figure 3, three types of points are presented: green, representing those that passed the ESG algorithm test, from step 4, and that have cryptographic properties; gray, those that passed the test at the returned step according to the minimum standard
value imposed by the security policies; and red, those that did not pass the test at step 5. They represent a limited number from possible sets and are computed for an interval within the subspaces within
;
defines their credentials within the algorithm.
6.2. ESG Algorithm. Cryptographic Parameter Computation
In this section, we describe our proposed method to compute the cryptographic parameters for each partition using an -type device.
Each of the devices involved in the communication process initially select optimal parameters that will be used in the double authentication.
6.3. Double-Authentication Method
In this section, the proposed algorithm for the cryptographic parameter computation necessary for double authentication and for agreement with the communication security credentials is presented.
Algorithm 1 is the method by which two devices authenticate each other in the case where at least one device is from
.
| Algorithm 1: Subspace generation. |
Initializations: is initialized at . 1. A partition is chosen for a value l generated pseudorandomly, and is initialized at . 2. is built based on coefficients. 3. An approximation of the number of points with cryptographic properties is computed, according to Equation ( 8), and is created accordingly. 4. The degree of correlation between the parameters of the points on the elliptic curve is checked to verify the degree of resistance to cryptographic attacks, according to the methodology of [ 29, 30]. In case this degree is greater than , certified according to the security policies established for , is retained in , and it returns to step 1. In other case, the current parameters are retained, in 5. The simulation of the cryptographic computation of the primary parameters is carried out according to Equation ( 6). If the value is exceeded, the maximum accepted value for devices in , then it returns to step 1. Otherwise, the current parameters are retained in 6. If the system returns a failure after testing the entire allocated partition, is returned together with a risk parameter allocated to this device. If the algorithm ends successfully, is returned.
|
All the communication processes that can be performed within an can be reduced to several communications, including this particular type, because any multiple communication required in multiple query processes within data mining operations can be divided into a certain number of such dual communication processes, with the application of the protocol described by the algorithm in the following part.
Let
be a device from
, and let
be another device from
. Let it be the case where the
device initiates the connection (the same procedure is followed in the opposite case). Device
is checked to determineif it is in Case 1 or Case 2 according to the description of the possible cases in
Section 4. For Case 1, the protocols described in [
15] are applied.
In Case 2, the procedure is as follows: device
uses in the double-authentication process its own pair of keys:
obtained from
, and
uses the key pair
obtained from
.
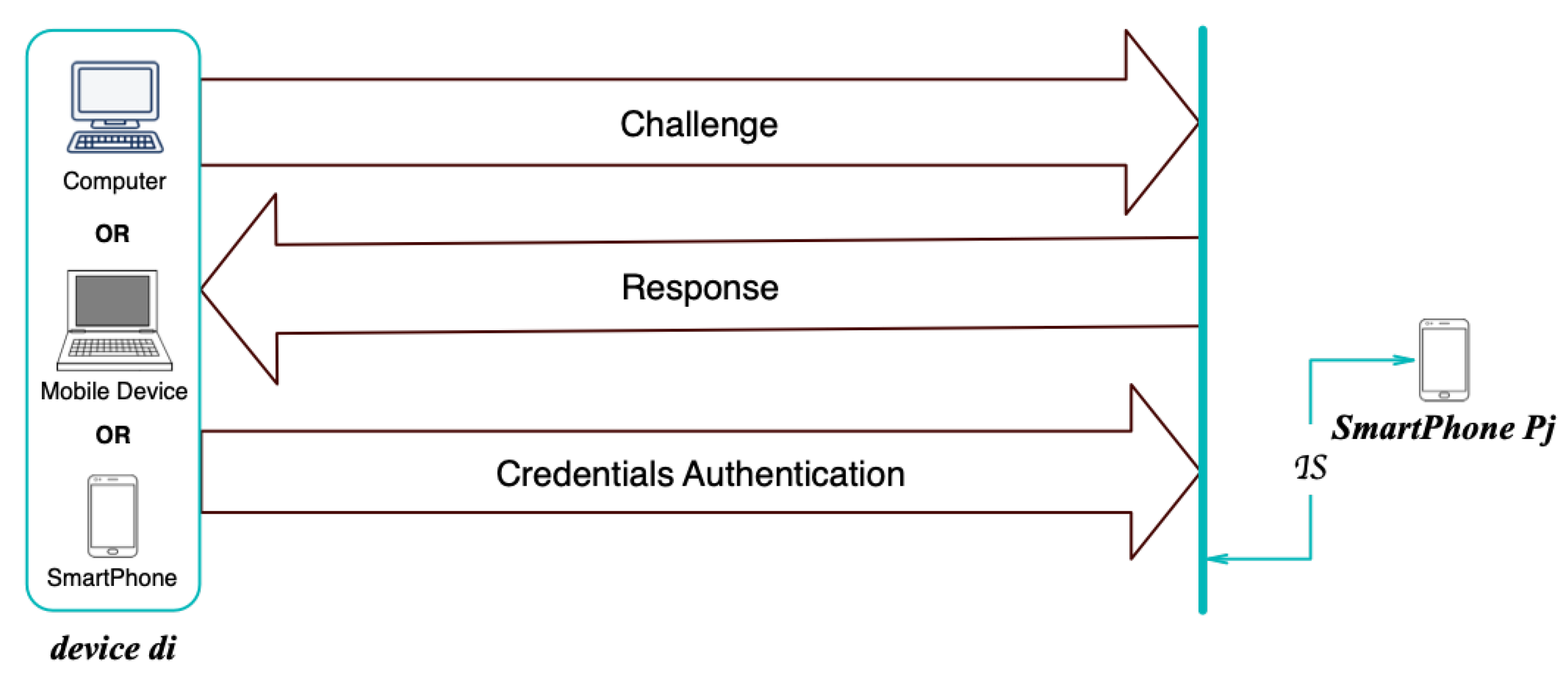
The initiator of the process generates a pair of pseudorandom values, which are used in the combination process according to its partition and will initiate the connection . Upon such a request, the mobile device generates a pair of pseudorandom values that are combined according to the composition algorithm for mobile devices.
After this, the mobile device initiates the process, through which it transmits the primary credentials necessary in the intermediate process required in the authentication of by .
In order to perform a double authentication, a new round of communications is initiated from to , called , through which the parameters computed in the previous rounds by each of the participants are used as primary input data.
On this basis, at the end of the three rounds of communication, the two devices involved in the protocol will have completed the double-authentication process, through which each proved to the other its identity within the
system. A representation of this process is briefly shown in
Figure 4.
6.4. DWA Authentication Algorithm
In this section, in accordance with the steps presented in
Section 6.3, we describe the proposed protocol, presented as the following Algorithm 2:
During the creation of the credentials used to secure the communication, participates in the process using the data created by itself, namely, , and participates in the construction of the credentials to secure the communication with the data generated independently of , namely, . On this basis, the final credentials are computed according to the combination of the data independently generated by each device involved in this process, which results in agreement with the credential protocol, not imposed credentials. Through this process of creating these credentials, there are also ensured authentications of by , as well as of by , which means that the man-in-the-middle attack is not possible.
Furthermore, the algorithm creates authenticated credentials for secure communication processes that take place between devices within a repeated query used to create a final answer given by a data mining action on . This procedure creates the credentials and takes into consideration a method of ensuring that cryptographic parameters are generated according to the parameters specific to each category of devices within . In this whole set of procedures initiated by elements from , it will be necessary for to manage the certificates of each device from . Within the information stored about devices from and , it is necessary to have descriptive data about each device from each class of devices and at each connection; for a device that contains an empty , it is first transferred to the database servers within , and only then will the query continue.
The security level of the algorithm presented is in accordance with the attack resistance of a model based on
, with the difference being that, for a possible attacker, the analysis must be conducted on
, which represents the composition of all the parts stored by the models from each device, and not on
, a fact that increases the difficulty of processing the parameters and therefore increases the security level of the system in the case of a real attack on the protection model described for mobile devices within
.
| Algorithm 2: DWA. |
- ♢
initiates the process. - 1.
are generated, and is called. is returned. - 2.
The parameter is computed. - 3.
is computed as the hash of the composition . - 4.
is computed as the asymmetric encryption of the message using the secret key . - 5.
The values are communicated to (the process). - ♢
Upon receiving the message, the device initiates the process; generates two pseudorandom values ; then calls the function, which respects the entropy principles from ([ 31, 32]); computes as the hash of the result given by the function; and computes to be the encryption of using ’s public key. If the two computed parameters are not identical, the authentication of by ends in failure. Otherwise, the construction of the cryptographic parameters continues. - 6.
computes . - 7.
computes as the hash of . - 8.
is computed as the asymmetric encryption of the message using the secret key . - ♢
The process consists of sending values. Upon receiving the message from , the device verifies the identity of in the same way as verified the identity of . If the verification fails, the protocol ends with a failure. Otherwise, the protocol initiates the process for the phase. - 9.
computes as the hash of the result returned by the function. - 10.
computes to be ’s encryption using ’s public key. If the two calculated parameters do not have the same value, the credential authentication step fails. If the two parameters have the same value, the process ends successfully by authenticating the credentials approved by the two parameters and proceeds to calculate the final credentials of secure communication: computes a parameter as the hash applied to the first three calculated parameters, encrypted with its public key, and transmits the result to .
|
6.5. Performance Analysis
In this section, the performance of the implemented model (
) is described in comparison with two models previously implemented by the beneficiary, namely,
(a variant based on solution presented in [
15]) and
(a variant based on solution presented in [
33]), which were solutions that contributed to the dual authentication system, with the common feature being the space over which elliptic curves are defined, for an environment which contains 3 server centers, 87 users from the
category, and 212 users from the class
, with heterogeneous systems.
The presented model was analyzed according to the computation time required to generate
-type subspaces for the presented solution, and the time generation and communication time of the results for previous solutions (in
Table 1).
Below are descriptions of the properties represented in the table, as well as some remarks on the results.
Generation time–the time (in seconds) required to compute the parameters for elliptic curves. The time to compute the parameters is correlated with power consumption.
Assignment time–the time (in seconds) required to transfer data to other devices that are involved in the communication. The assignment time is correlated with power consumption.
Recomputations–the number of parameter recalculations (at each 1000 calls) according to the security policies established by the beneficiary. It should be noted here that they change over time depending on the problems found during the periodic security audit. The recomputation time is correlated with power consumption.
Generation errors–the number of failures (at each 1000 calls) in the process of generating a subspace in a space.
Moreover, a performance analysis with the required computation time was performed every 6 months to establish the cryptographic credentials and the number of detected attacks on the system (the last analysis is presented in
Table 2).
The data from this table are explained and interpreted below.
Cryptographic credential generation time–the time required to generate the cryptographic credentials used in double authentication and to secure the communication. The cryptographic credential generation time is correlated with power consumption.
Detected attacks–the number of detected attacks (at each 1000 calls).
As a general statement, the method of computing the cryptographic parameters, from the point of view of the allocated times/power consumption, depends on the initial generation method of the involved parameters and the security policy established by the beneficiary, which influences the number of recomputations and the generation time of the cryptographic parameters. This decision is made depending on the degree of security that is requested to be implemented.
6.6. Limitations of the Proposed Model
The proposed model ensures the creation of the necessary credentials in the cryptographic processes involved in securing communications and double authentication; otherwise, communications will be disallowed. This main limitation of the model is due to step 5 of Algorithm 1, where a value is exceeded only if it meets the maximum conditions for this parameter, established as the maximum value accepted for the devices in , according to the security policies, so the establishment of the security policies determines the number of repetitions of the process in certain cases. This practically translates into longer creation times for cryptographic credentials.
The second limitation involves the way in which double authentication is performed and the protection against man-in-the-middle attacks. This is present in all systems that respect this principle, namely, the creation of common cryptographic credentials is ensured, and in the case of an attack of the type mentioned above, communication is not allowed; the presence of such an attack can thus be signaled, but communication is not allowed.