The Application of Directed Hyper-Graphs for Analysis of Models of Information Systems
Abstract
1. Introduction
“A system can be defined as a complex of interacting elements.” [1], p. 55.
- —
- Who are the stakeholders, end-users?
- —
- What are the stimuli, events when the system is used?
- —
- What are the entities, concepts, things that are specified in models within the system?
- —
- How could the system be used by the members of the ecosystem?
- —
- What is the goal of the system, motivation? Why the system is used?
2. Hyper-Graph Representation of Information Systems
- —
- Assemblages Sawyer et al. consider Information Systems as digital “assemblages” that are the interconnections among parties participating in the information exchange of business and information flows among institutions. The Information Technology underpins and yields models for these configurations [31,32,33]. Following this viewpoint, we may take into account the properties of both individuals and groups of some things.
- —
- Granules In the first cut, we can think of granules as equivalence classes. However, other structures of granules are well-known, e.g., within Soft Computing [34]. A granule as an entity may have properties that induce the clustering of various individuals into specific clusters considered to be similar to granules. However, it is allowed that the same element may occur in disparate granules depending on the actual perspective. Following this approach, both granules and the elements of the granules may have their own specific properties.
- —
- Connections There are several examples, e.g., most recently, social media where the avatars, the digital personas, and any defined communities possess a diverse set of properties. Similarly, the network of roads or rail tracks together with the gas and rail stations showcase similar structures. Thus, the links and essential entities of the system, the higher-level organization of elements, hold a distinct set of properties [35].
2.1. Graph Models of Systems
2.2. The Fundamentals of Hyper-Graphs
2.3. Operationalization and Implementation
2.4. Implementation Details in Graph Databases
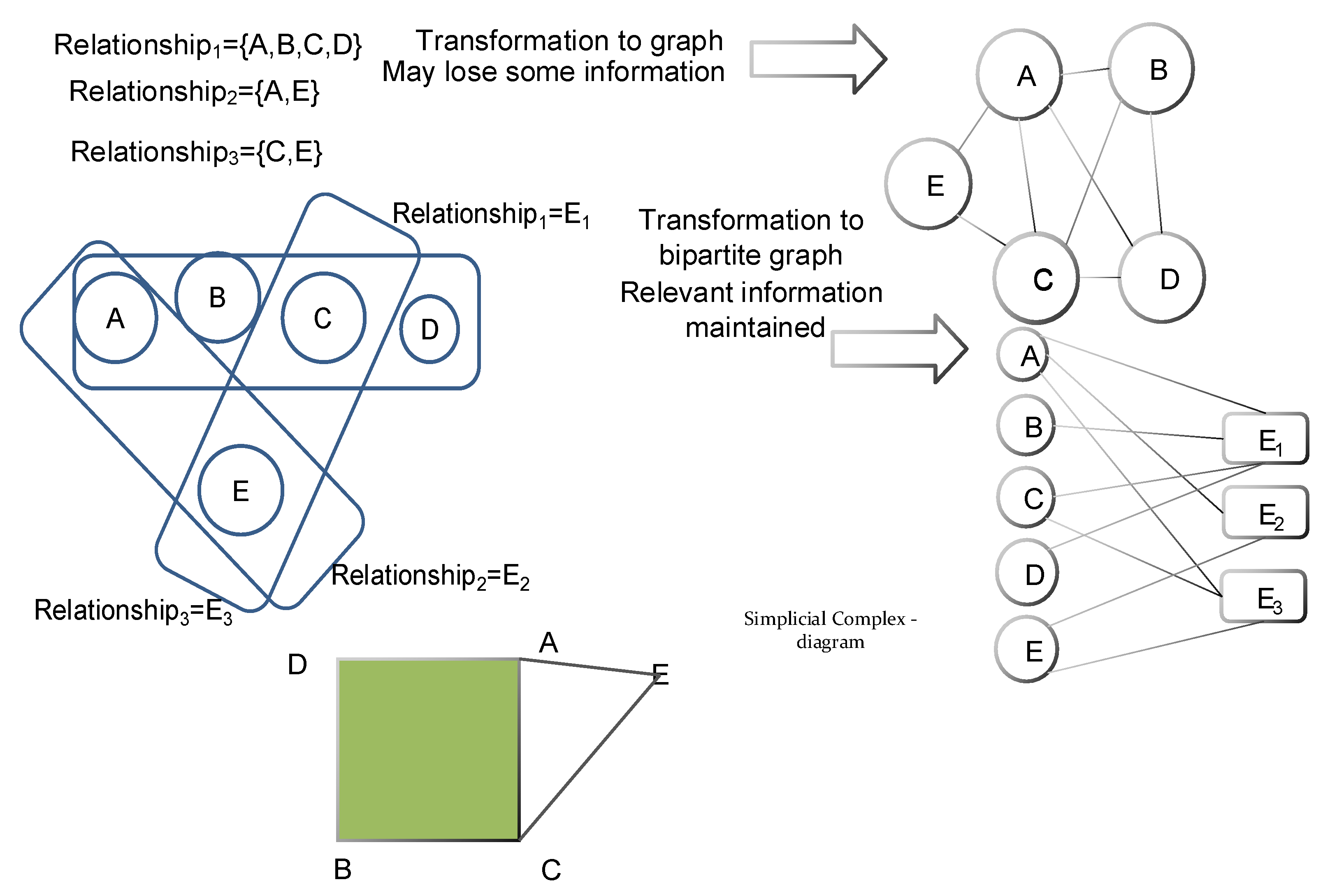
2.5. Hyper-Graph Representation by Simplicial Complexes
2.6. Homology and Similarities
2.7. Modeling and Verification of Information Systems
- —
- Information and Data: The integrity and consistency in the Information and Data collection is vital for the operation of Information Systems. The Information and Data collection can be implemented by various structuring approaches, namely, relational and NoSQL databases, XML (Document Object Model), JSON, etc. [29,40,42,43,58,59,60,61]. The data collections can be manipulated by the Data Manipulation Language of relational calculus and SQL. The documents described in XML can be handled by XPATH and XQuery. The data stored in other NoSQL databases can be managed by the native and system-specific languages. The Data Definition Language in Relational Database Management Systems (RDBMS) and the same brethren in other Data Base Management Systems offer the possibility to define integrity constraints. The normalization that was originally defined for relational databases has been extended to XML and object-oriented data collections [62,63,64,65]. Thereby, the entity (entity ↔ identity), referential, and business integrity can be interpretable for tuples of data collections and not only for relational databases.
- —
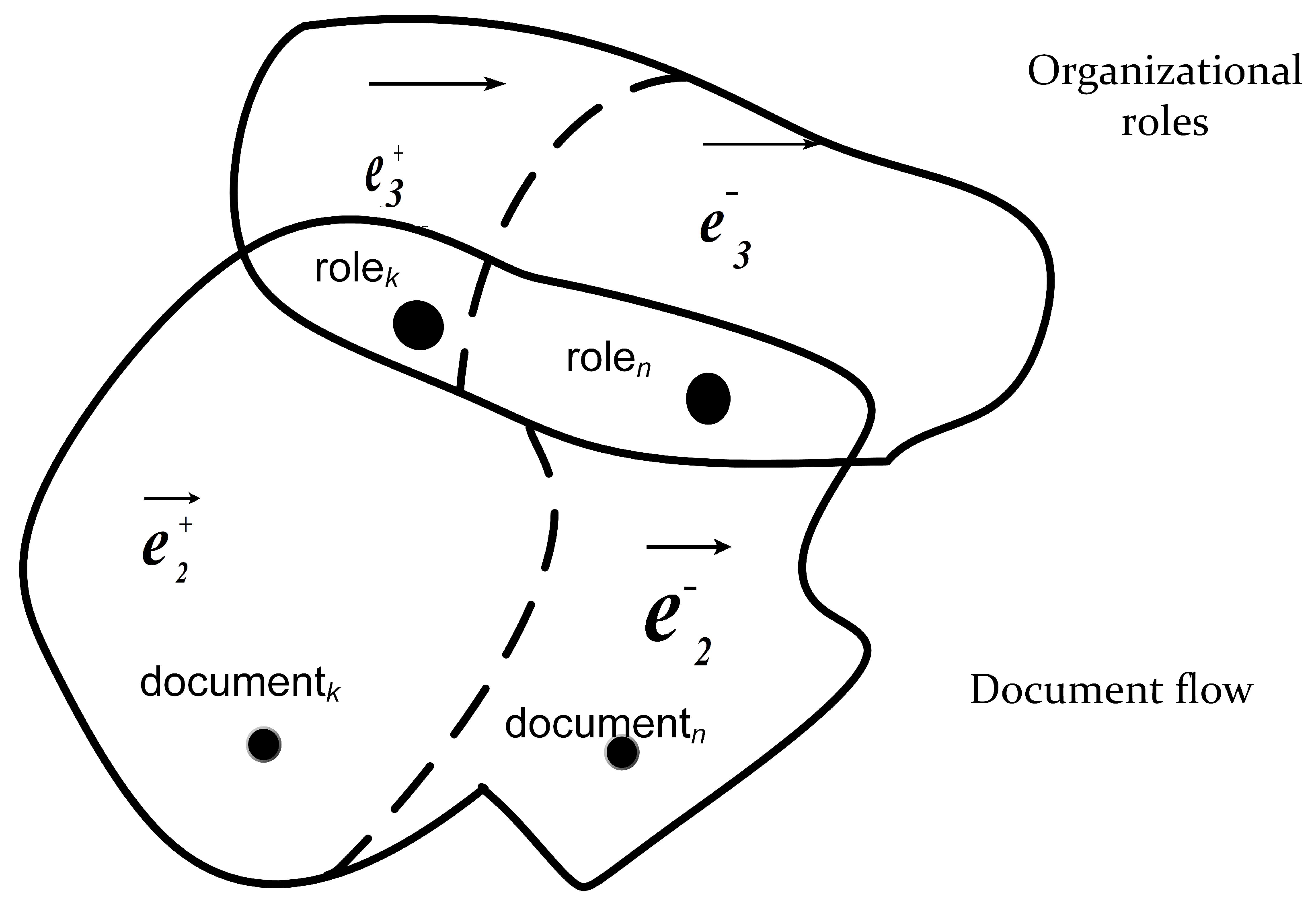
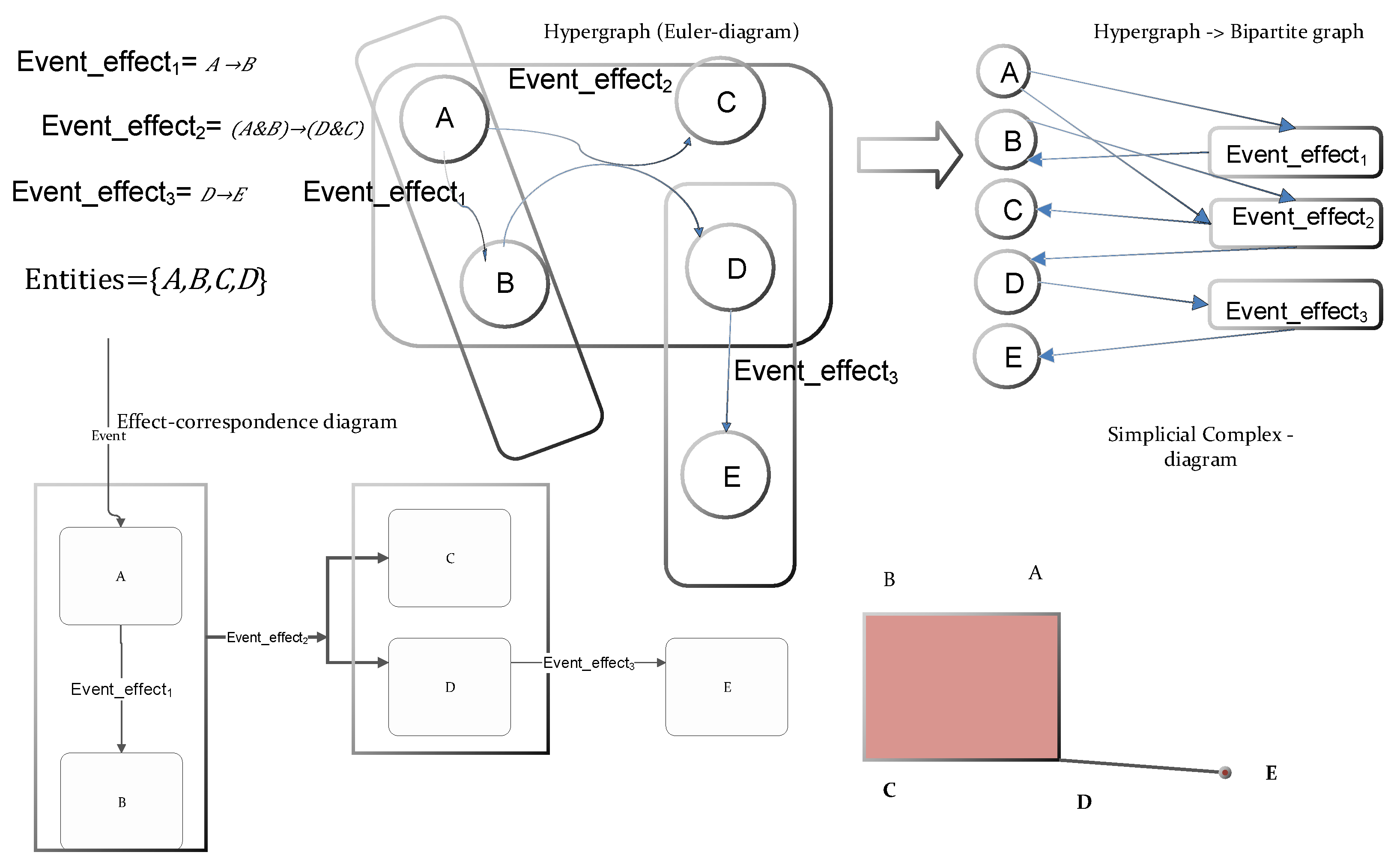
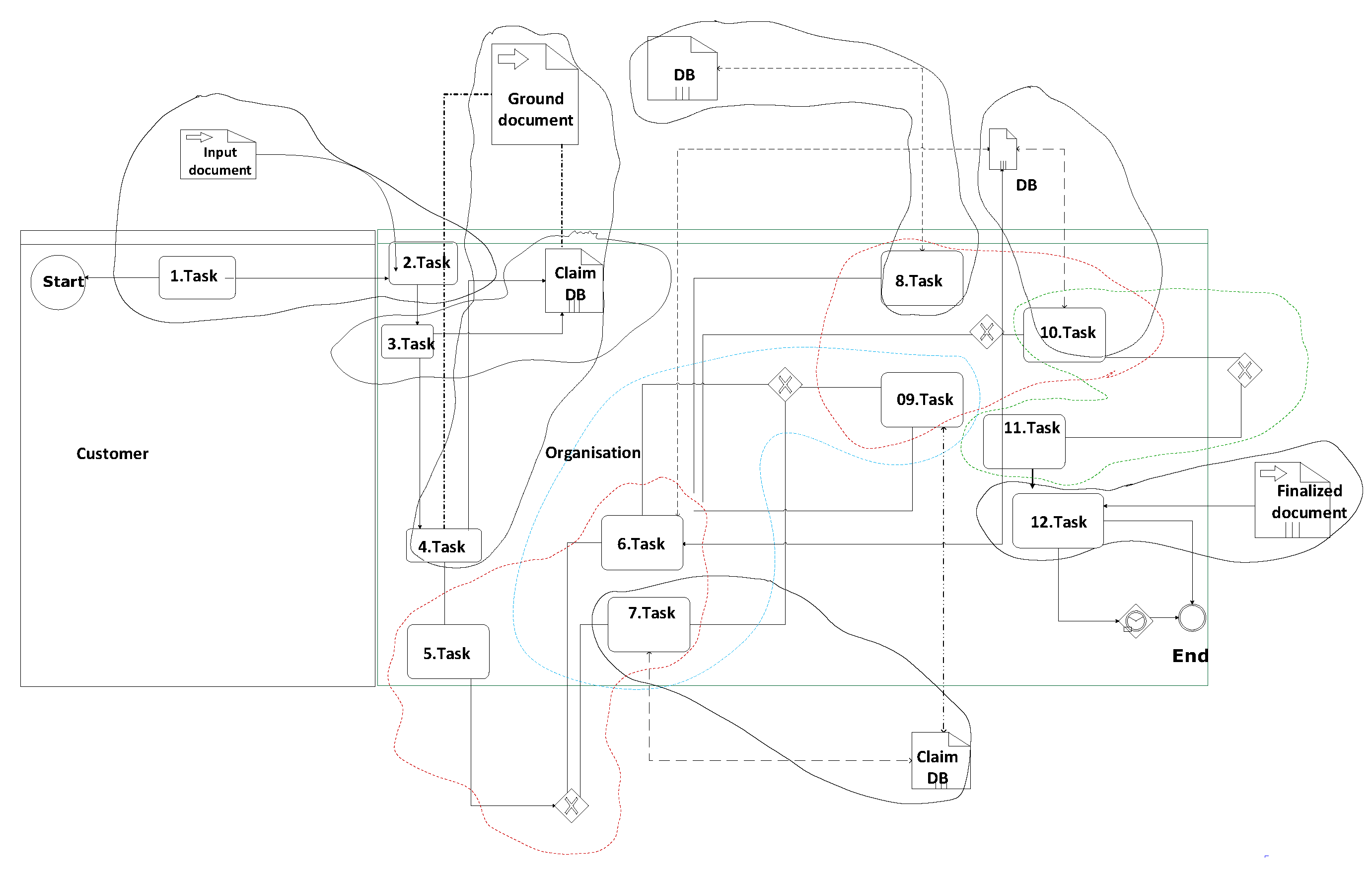
- Processes, Events and Entities: Events are intimately coupled to Business Processes and Workflows. Activities in Business Processes and Workflow are initiated by either external or internal events. The chain of activities and the state changes exerted by the event-triggered activities can be semi-formally represented in Business Process Modeling Notation (BPMN), Event Process Chain (EPC), or in Petri nets [66,67,68,69]. The formal ground are the process algebra and finite-state machines [70,71,72], respectively. The descriptive, syntactic representation of Business Processes, Workflow, Petri Nets, and their activities is realized in XML nowadays [73]. The behavior of the Information System and its dynamic constituents is described by processes and activities, which are represented typically in XML; therefore, they can be grasped as documents. The events represented within diagrams of BPMN, EPC, Petri net, or UML Activity cause state-transition of entities, objects, or “things” in the data collections [74]. The entity-relationship diagrams, or object class diagrams, which describe the relationships among entities of data collections, are inherently hierarchic so that some entities are subsumed into other entities. There are two aspects of effects that are exerted by events on entities. One aspect is when the chain of events is tracked through the life cycle of an entity in the form of the Entity Life History or UML State Chart [14,75]. The accurate and formal description can be specified by Finite State Machines. The other aspect is when the alteration of several entities and their attributes is traced through the elements of the data collection; this flow of actions incorporates a long transaction, i.e., the chain of consecutive transformations [14,76]. The model of exerted impacts of an event can be represented in Finite State Machines. The two sets of models of Finite State Machines—namely the life cycles of entities and the long transactions of events— are orthogonal to each other. One of them meticulously pursues the fate of an entity, the other follows how an event affects the entities and their attributes within a data collection. These two sets of models embody the various integrity constraints of business processes that describe the behavior of the system and the state transitions of the constituents of the system. Due to the hierarchical nature of the model of a data collection, the behavior of a “super-entity” and the interdependencies of its subsumed entities along with the event-coupled constraints emerges as integrity constraints, which should be consistent and reconciled. For the sake of unified and uniform representation and handling of constraints and distinct models of the system, a hyper-graph can incorporate the diverse models and their representation, including the Finite State Machines [77] (see Figure 7).
- —
- The system responds to a stimulus, i.e., an organizational-level event, that originates from the external environment of the organization and triggers the functions of the Information System through interfaces including User Interfaces (UI). The interfaces can be perceived as documents that are represented in document-describing languages (XML, XHTML, JSON, etc.).
- —
- Integrity rules The entity integrity rules that ensure identity are implemented in the various database management systems efficiently and effectively so that the enforcement of these integrity rules is straightforward in any representation, for instance, hyper-graph representation of data collections that are realized in any database management system. The entity integrity concentrates on the validity and correctness of the “tuples”, the data items, and the values of the attributes in the data-containing structure. The referential integrity depicts the data dependencies among tuples and entities in a hierarchy within data collections (Figure 8). The specification of business- or enterprise-level integrity constraints can be realized at the data-collection level as static rules or as business rules of activities of processes that are initiated by events.
- —
- The realization of integrity constraints happens finally in the Conceptual Model of the Systems (Figure 9). The consistency of the system can be achieved through the maintenance and enforcement of constraints. The hyper-graph makes it possible that the various models that contain the integrity constraints can be represented in a uniform theoretical environment. Furthermore, the hyper-graph representation offers the opportunity for the unified management of model-checking exercises.
3. Literature Review—Related Works
3.1. Hyper-Graph Application Domains
3.2. Documents and Information Systems
3.3. Enterprise Architecture and Information Systems
4. The Application of Graph-Theoretic Approaches in the Context of Information Systems
4.1. Model Checking for Dynamically Modified Business Processes
4.2. Hyper-Graphs for Modeling Information Systems from the Aspect of a Document-Centric Approach
4.2.1. Constituents of Information Systems
- Enterprise Architecture
- Business Unit An entity partly or wholly fulfills a business function to achieve strategic objectives.
- Business Unit Type Based on certain properties of business units, equivalence classes are defined as business units types, and the business units are placed into these types.
- Job is an elementary constituent of a Business Unit.
- Job description describes the access rights, responsibilities, tasks, and obligations of a Job.
- Job Type is a categorization of Jobs through certain properties into equivalence classes.
- Actor is an employee who is associated with a Business Unit.
- Actor Type is a categorization of Actors through some properties into equivalence classes.
- Group may consist of either Actors or Business Units that have a common objective to be achieved.
- Location This is a location in cyberspace or a geographical place where a business unit, actor, actor type, job, or group is situated.
- Business Process Management and Models
- Business Process is a set of activities or tasks that ingests various input items and then generates outcomes that are valuable for the human actors of stakeholders. The collection of activities and tasks are reconciled into the features of the Enterprise and Technology Architecture. The aim of the set of tasks and activities is to achieve business/organizational objectives. Every business process is initiated by a definite business function and may touch several other business processes and business units.
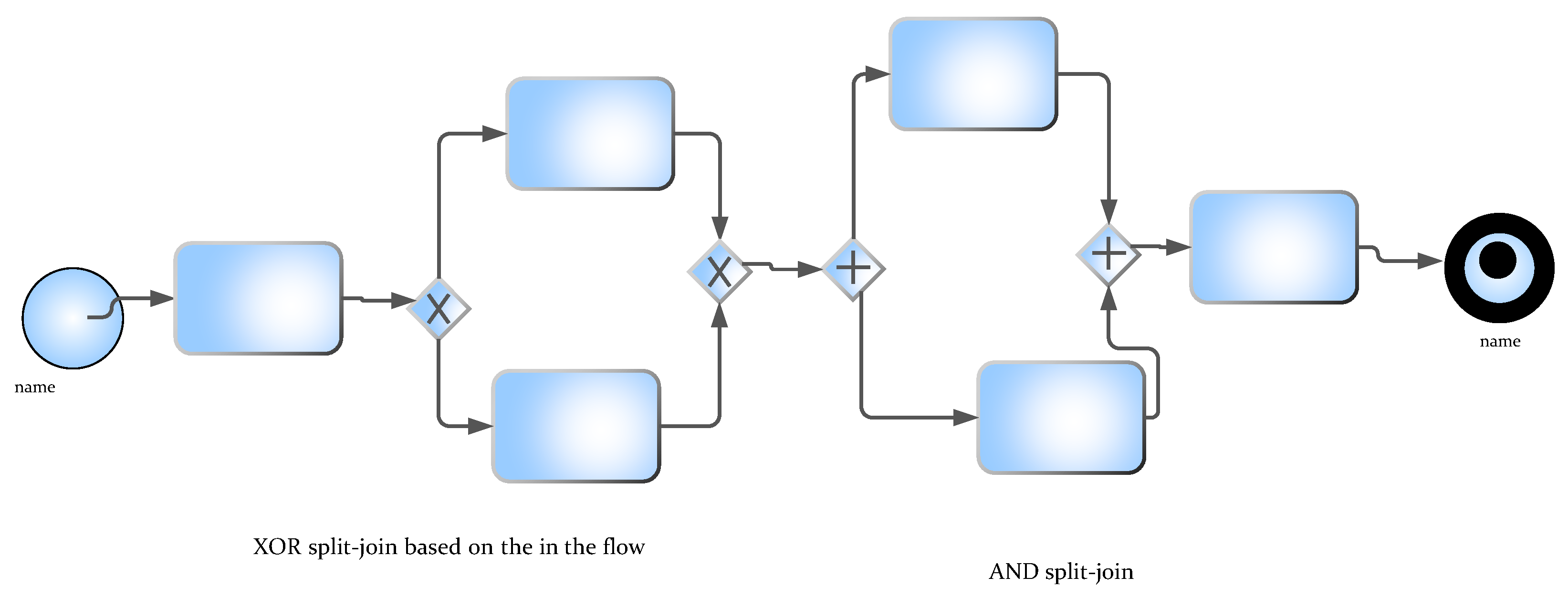
- Business Process Model is comprised of a set of models of activities and tasks, and it contains the specification of constraints for operationalization. An instance of a business process is composed out of instances of activities and tasks that expound the description of a particular case of the operation of the enterprise. A Business Process Model is a description and prescription for instances of a Business Process. A Business Process Model contains several models of tasks as sub-components. In the graph representation, a Business Process Model is composed of vertices and directed edges that represent the linkages among the vertices of the model. The vertices can represent tasks/activities, decisions, and the directed edges can represent information and control flows.
- Workflow A Workflow Management System (WfMS) is a software package designed to manage business process design and execution of the business processes represented in a format that the computer can interpret. A Workflow System (WfS) is based on a Workflow Management System. The workflow system enables the set of business processes that have computer-supported process models to be operationalized [110]. Hence, the Workflow can be considered to be the subset of the Business Process and the Activities. The activities and tasks are coded either by a visual language or a formal language that can be interpreted directly by a computer system. Thus, a workflow is a directed graph of activities and tasks that receive inputs in the form of data and documents and then transforms them into outcomes that appear as documents (and data).
- Activity/Task There could be human tasks to be carried out by an Actor through the utilization of computer-supported Activities. An activity can be grasped as a “black box” that embeds data transformation and business rules as its task, and the activity can be perceived as a triple that includes the task and a pair of information items that themselves represented documents. A task has a goal and execution steps of a well-defined algorithm.
- Event Events represent those intangible phenomena that initiate changes of state within the real-world system and their IT representations that are relevant to Business Processes and Workflows and exert alteration in the data collection.
- Logic gate/Decision In several Business Processes and Workflows, description language calls this component of the visual representation a “Gateway” that describes the control structure, checking mechanism, conditions, and flow of control.
- Document-centric approach and Models (Section 4.2.6)
- Document Model We consider all the constituents of an Information System to be components of a generic document. The overarching document incorporates all segments of the ingredients of Information Systems that are apt to be described in document representation languages, such as XML, JSON, etc.
- Document The activities accept documents, and, after processing, the activities produce outcome documents.
- Types of Documents We differentiate between generic, intensional, extensional, ground, and finalized documents.
- Variables/Placeholders/Information items In this perception, every document—general-template-like or instance—is comprised of variables that, during processing, become bound [111].
4.2.2. Constituents of Generalized Hyper-Graphs
4.2.3. Hyper-Graph Representation for Storing in Databases
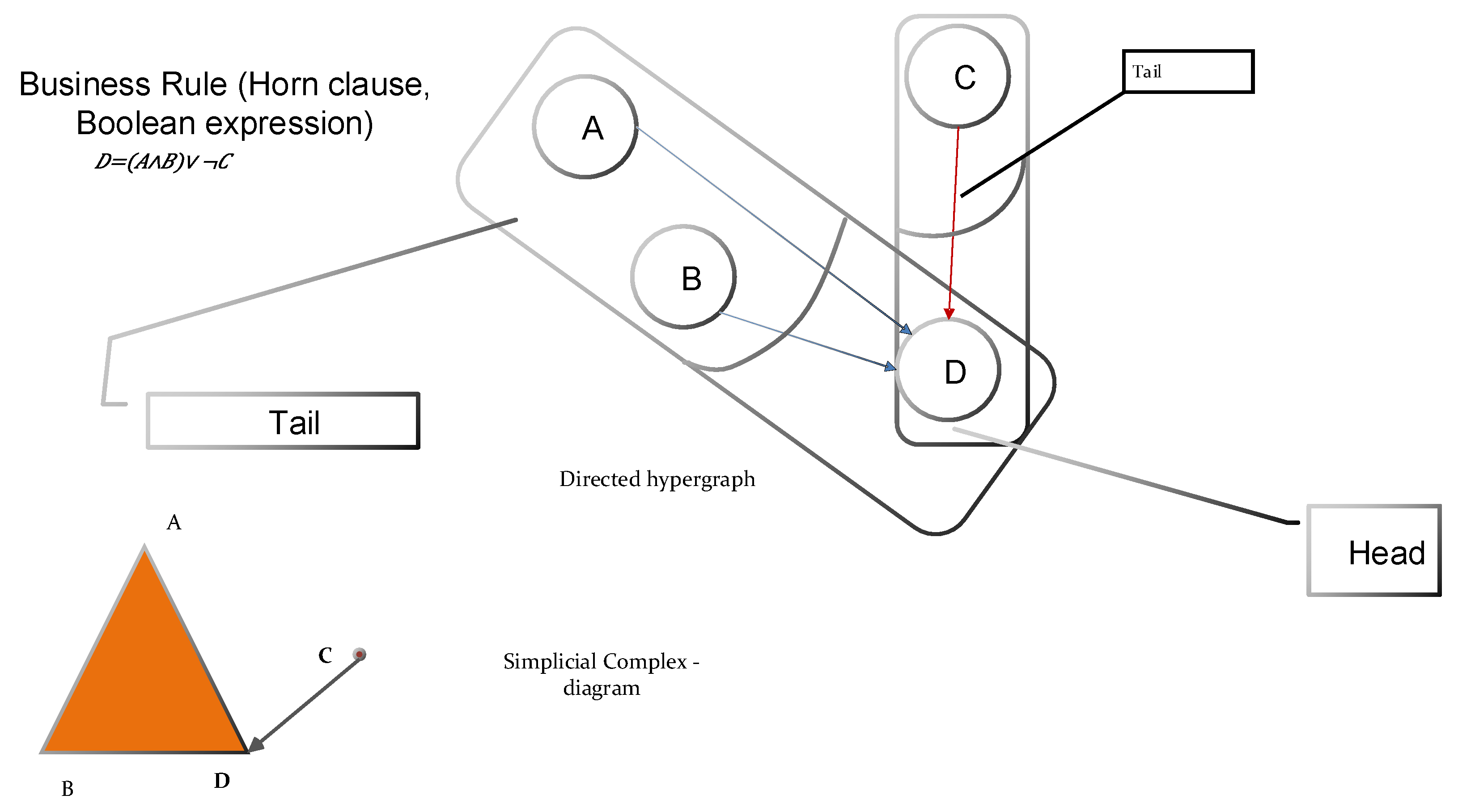
4.2.4. Business Rules and Logical Statements
4.2.5. Horn Clauses and the Hyper-Graph Representations
- 1
- ’In’ represents inputs that could be sub-documents or collections of data items.
- 2.
- ’Ou’ describes the outputs that could be sub-documents or collections of data items.
- 3.
- ’Constraint’ depicts behavioral constraints and goals to be achieved (see Equation (11)).
- 4.
- ’’ contains the actual valuation of the variable, and, moreover, whether it is free or has a value, it is denoted as well through the meta-attribute of the variable .
- 5.
- ’free-document’ is a document with free variables.
4.2.6. The Document Model in Hyper-Graphs
- (1)
- A finite set of variables (attributes) that are represented by vertices in a hyper-edge, ;
- (2)
- A finite set of documents that are represented by hyper-edges DOC = { doc1, …, docn};
- (3)
- The variables that are contained in documents belong to attribute types Attr = { T1, …, Tn};
- (4)
- The finite set of domains is DOMSET={ D1,…..Dk} that contains the domain of each single type, Ti, attribute type;
- (5)
- The relationship between an OGDT generic document type (overarching document of organization) and its constituents that are the document types that belong to a DTH (document type hierarchy) can be described by hyper-arcs representing is-a relationships; the hierarchy is a mapping of super-type—subtype relationships between document types. The relationships can be deduced from the variables, their attributes, and the types of attributes. A document type is realized either by a DTD or an XML Schema [130];
- (6)
- The relationship between a document, doci, and a document type, DT, can be described by a hyper-arc representing the instance-of relationship.
4.2.7. Exploring the Dependency Rules in the Hyper-Graph Model
- (i)
- for each variable, DOC, there is a vertex in the hyper-graph;
- (ii)
- for each dependency rule, there is a hyper-edge that contains the variables from both the left-hand side and right-hand side of the rule , where where each variable occur at least once in or B;
- (iii)
- The hyper-edges that contains the variables —either of the left-hand side or right-hand side of a rule or of a sub-document or a task —are labeled as composite hyper-edges (hyper-vertices);
- (iv)
- The hyper-edges that represent the dependencies are labelled by attribute functional dependency, and the content of the attribute is the dependency rule in Horn-clause format.
- Step 1
- For each task, locate the task or tasks that are indicated by the logical rule (Equation (19)).
- Step 2
- Then, identify the linked sub-documents and collection of data items.
- Step 3
- For each logical implication between tasks, create an incidence matrix for a directed graph . This directed graph is manifested as a directed hyper-edge (Equation (2)). A task is displayed as an embedded hyper-edge that represents the sub-document describing the task and contains the variables as vertices in the sub-document that are related to the said task and manipulated by this task. The tasks that are on the left-hand side of the implication will be embedded into the tail of hyper-edge, . The tasks that are on the right-hand side of the implication will be included in the head of the hyper-edge . This way, there is a hyper-arc between the hyper-edges that contains the variables of the left-hand and right-hand sides of the dependency rules and represents the dependency rule that is formulated in a Horn clause.
- Step 4
- For each document or collection of data items, create an incidence matrix for the representation of the related hyper-edges . The directed incidence matrix describes the directed relationships between tasks and documents (data items). When the document or collection of the data items is input for a task or for tasks, then the documents or the collection of data items is placed in the tail of the hyper-edge, and the related task or tasks are placed in the head of the hyper-edge: and . When the document or collection of the data items, , is output for a task or tasks, then the documents or the collection of data items are placed in the head of the hyper-edge, and the related task or tasks are placed in the tail of the hyper-edge: and . In an analog way, we can build up an incidence matrix, , for every variable contained in a document to track the fate of the variables.
- Step 6
- B-hyper-graph and L-path computation (see Equations (12) and (14)). We locate an end-state and the document that represents the attained state of a business process chain. Each variable in this document is represented as a vertex. We select one variable/vertex, then we identify the tasks that are related to that variable through the incidence matrix that describes the input/output variables and tasks (Step 4) and start building up an L-hyper-path through B-arcs. Then, we pursue the tasks and their input variables. These input variables are the output variables of antecedents tasks that can be determined again by the incidence matrix. Since an L-hyper-path is an alternating sequence of vertices and hyper-edges containing tasks and a set of variables, an L-hyper-path connects the variables in an end-state of a business process or chain to the variables of one of the start-states of another business process or the business process chain. The B-arcs are determined by the incidence matrix of the variables and the tasks, so that the matrix makes it possible to establish several continuations of the respected L-hyper-path. The collection of L-hyper-paths constitutes a B-hyper-graph. It is the set of domains of data types that cares for the values of variables. For every process chain and each of their end-states, the collection of L-hyper-paths and B-arcs that are encompassed by their related B-hyper-graphs should be constructed. This procedure should be repeated for each workflow and business process that is a constituents of a business process chain, then for every task within a business process.
- Step 7
- B-hyper-path computation. After identifying the B-hyper-graphs that are associated with business process chains, workflows, and business processes, we can calculate the B-hyper-path. In the case of B-hyper-paths, we start again with one variable in some end-state, then we create a B-hyper-path Equation (15). We repeat this procedure for all variables that can be found in documents representing end-states in business process chains, workflows, and business processes.
- Step 8
- Transversals and path computations from hyper-vertices [44], p. 37. After discovering the possible B-hyper-graphs that are associated with business process chains, workflows, and business processes, we can calculate the transversals for each identified B-hyper-graph. In the case of transversal computation, we start with the hyper-edge that represents the documents in some end-state and contains a set of variables. A minimal transversal T of B-hyper-graph / / is a collection of the tasks whose output variables can be used as input variables of , , (Equation (18)). We repeat this procedure for all documents that can be found in documents representing the end-state. We compute the L-hyper-paths repeatedly in such a way that the set of variables in a document within an end-state, which is enclosed in an adequate hyper-edge, is replaced in the representation by one vertex (hyper-vertex = hyper-edge identified with one compound vertex) that contains all variables with their properties. Thereby, we acquire another collection of L-hyper-paths.
- Step 9
- Consistency checking of generated dependency rules. Each minimal transversal, , is a representation of dependency rules that can be identified from the models. For every edge and the minimal transversal containing it, we check whether, when starting from the head part of some end-state, the associated attributes and logical statements are consistent (see Equation (9)). When a new workflow or new business process is inserted into the system, the attainable goals are formulated as variables of documents stored in some end-state, either of the business process chain, particular workflow, or the said business process. If transversals T, in a minimal transversal (that is associated with , , ) fulfills the behavior and other constraints, then the tail containing logical conjunctions of tasks and the head containing either variables of documents or a task represent a valid dependency rule (Equation (11)).
4.2.8. Model Improvement through Model Checking
- Option 1.
- , there is no hyper-edge representing a task that contains that variable in its head. It should be investigated whether this variable is necessary and, if yes, which business process and its task should produce it as an outcome.
- Option 2.
- , then the meta-attribute of this variable should be checked to see which task gives value to this variable. If there is at least one task that sets the meta-attribute of the variable to “valuated”, then the relevant business processes and tasks can be found through an L-hyper-path and a B-hyper-path. If there does not exist a task that valuates the variable, then it should again be investigated whether this variable is necessary and, if yes, which business process and its task should produce it as an outcome, i.e., it seems to be that a valid input does not exist, or it did not succeed in constructing a hyper-path that connects the resultant variable to any valid input variable or set of input variables. The causes should be investigated, and the possible solution should be identified.
- Option 3.
- If , then there is no hyper-edge representing a task that contains that document—and the set of variables in the document—in its head. Whether this document is necessary should be investigated and, if yes, which business process and its task should produce it as an outcome, if this situation occurred.
- Option 4.
- then the meta-attribute of these variables in the document should be checked to see which task gives value to these variable. If there is at least one task that sets the meta-attribute of the variable “valuated” to true, then the relevant business processes and tasks can be found through an L-hyper-path and a B-hyper-path. If a task that valuates one of the variables does not exist, then it should again be investigated whether this variable is necessary and, if yes, which business process and its task should produce it as an outcome, i.e., it seems to be that a valid input does not exist, or it did not succeed in constructing a hyper-path that connected the resultant variable to any valid input variable or set of input variables. The causes should be investigated, and the possible solution should be identified.
- Option 5.
- and the meta-attribute “valuated” of this variable is true, then at least one or more L-hyper-path and B-hyper-path exist that yield viable sequences of variables and tasks in business processes that lead back to valid start-states and associated input variables. If there are several allowed sequences, which path is worth retention should again be investigated. Other factors can be contemplated in the selection procedure: e.g., the length of the path of the alternating tasks and input variables; the complexity of the paths investigated; and, moreover, the reliability and trustability of tasks and contained business processes; furthermore, the cost factors in an IT sense should also be investigated.
- Option 6.
- and the meta-attribute “valuated” of all variables in the document is true, then at least one or more L-hyper-paths and B-hyper-paths exist that produce a feasible series of variables/documents and tasks in business processes that lead back to valid start-states and associated input variables. As in Option 5, we should investigate which path is viable, reasonable, and consistent with the intentions of the system.
- Option 7.
- If either or and the meta-attribute “valuated” of all variables in the document is true, however, neither L-hyper-path nor B-hyper-path exist that provide a feasible sequence of variables/documents and tasks in business processes that lead back to any valid start-states and associated input variables, the required input variables are not known or not reachable.
- 1.
- alpha (α) acyclicity:
- 1.1
- The hyper-graph H is α acyclic if it is conformal, where conformal means that a hyper-graph H is conformal if every clique of the hyper-graph is included in a hyper-edge, and free of cycles, i.e, cycle-free.
- 1.2
- The hyper-graph H is GYO reducible [138].
- 2.
- beta (β) acyclicity:
- 2.1
- The hyper-graph H is β acyclic if each subset of H (or each sub-hyper-graph of H) is α acyclic.
- 2.2
- The hyper-graph H can be reduced to an empty set by repeatedly removing nest points. A vertex v is a nest point if there is a linearly ordered sequence of hyper-edges that include each other consecutively and all contain v, , and [139].
- 3.
- gamma (γ) acyclicity:
- 3.1
- The hyper-graph H is γ acyclic, if H is β acyclic and there are no vertices so that , where is the induced sub-hyper-graph, e.g., , the vertices of H, .
- 3.2
- The hyper-graph H can be reduced to an empty set by repeatedly removing nest points.
- 3.3
- The hyper-graph is DM reducible [140].
5. Discussion
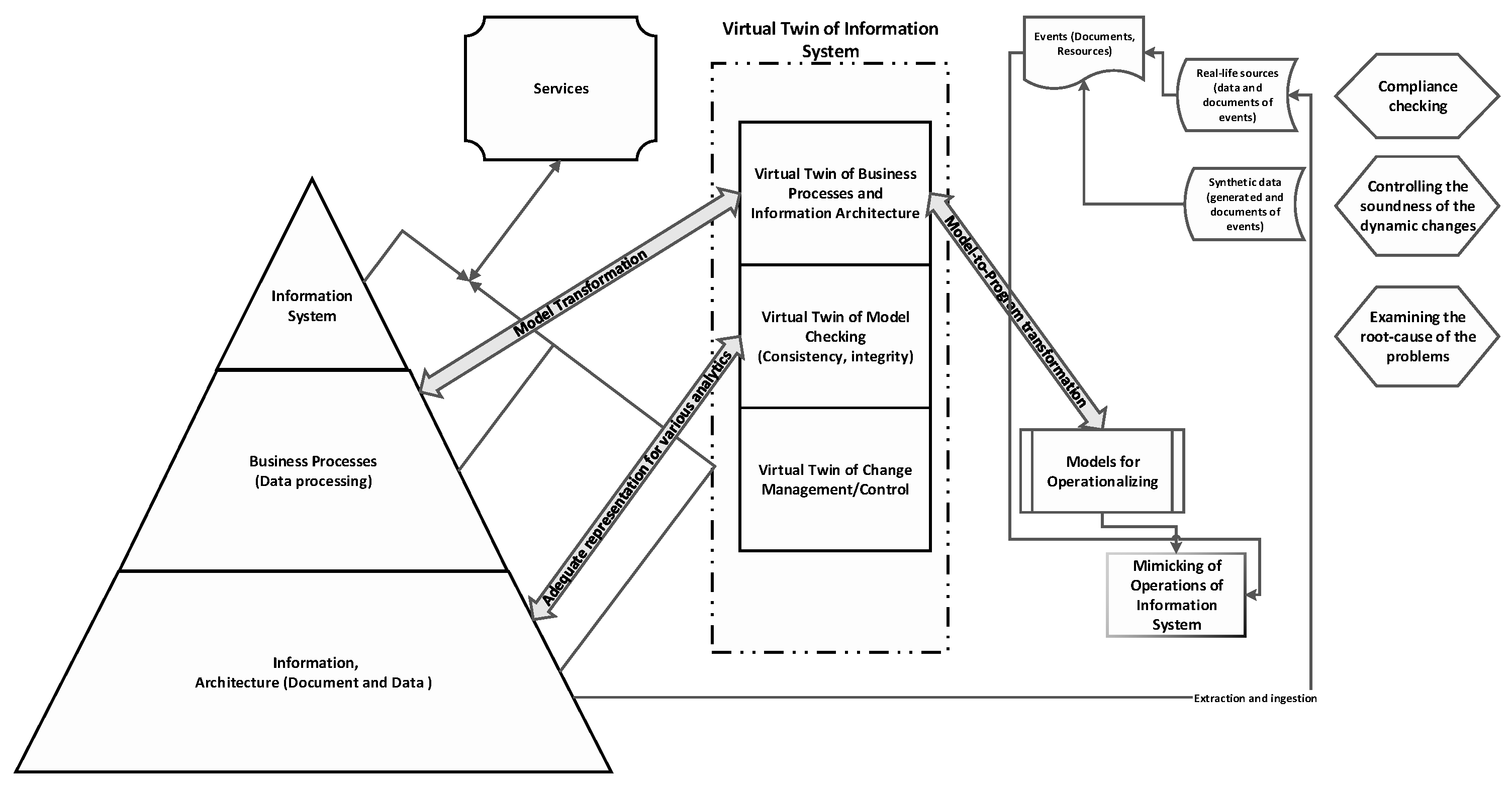
6. Future Directions of the Research
7. Materials and Methods
- —
- Hyper-graph visualization; source code of implementation:
- -
- https://github.com/stsoor/MScFinalProject (accessed on 30 Augest 2021).
- -
- https://github.com/stsoor/MScThesis(accessed on 30 Augest 2021).
- —
- Clustering Business Processes for Evaluation of Similarities and Dissimilarities:
- -
- https://github.com/KumundzhievMaxim/ELTE-EFOP-2020(accessed on 25 July 2021).
- —
- Operationalized transformation of UML AD into YAWL:
- -
- https://github.com/ahmadmukashaty/An-Operationalized-M2P-Transformation-for-Activity-Diagram-into-YAWL (accessed on 26 January 2022).
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| Article specific | |
| IS | Information System |
| IT | Information Technology |
| IT/IS | Information Technology and Information System |
| ERP | Enterprise Resource-Planning System |
| ITIL | Information Technology Infrastructure Library |
| TOGAF | The Open Group Architecture Framework |
| ASC | Abstract Simplicial Complex |
| XML | Extensible Markup Language |
| JSON | JavaScript Object Notation |
| DBMS | Database Management System |
| BPMN | Business Process modeling Notation standard version 2.0 |
| CNF | Conjunctive Normal Form |
| DNF | Disjunctive Normal Form |
| DTD | Document Type Definition |
| GYO | non-deterministic algorithm described by Graham, Yu, and Özsoyoglu |
| DM | DM-reduction algortihm originates from D’Atri and Moscarini |
| DOM | Document Object Model |
References
- Bertalanffy, L.V. General System Theory: Foundations, Development, Applications, revised ed.; George Braziller, Inc.: New York, NY, USA, 2015. [Google Scholar]
- Alter, S. Defining information systems as work systems: Implications for the IS field. Eur. J. Inf. Syst. 2008, 17, 448–469. [Google Scholar] [CrossRef]
- Cardoso, J.; Fromm, H.; Nickel, S.; Satzger, G.; Studer, R.; Weinhardt, C. Fundamentals of Service Systems; Springer: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Demirkan, H.; Spohrer, J.C.; Krishna, V. The Science of Service Systems; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Mattyasovszky-Philipp, D.; Molnár, B. Adaptive/cognitive Resonance and the Architecture Issues of Cognitive Information Systems. In Proceedings of the 2020 11th IEEE International Conference on Cognitive Infocommunications (CogInfoCom), Mariehamn, Finland, 23–25 September 2020; IEEE: New York, NY, USA, 2020; pp. 000479–000484. [Google Scholar]
- Molnár, B.; Mattyasovszky-Philipp, D. Cognitive Information Systems-artificial Intelligence & Management Decisions. In Proceedings of the 12th IADIS International Conference Information Systems, Vilnius, Lithuania, 10–12 October 2019; Volume 2019, pp. 290–294. [Google Scholar]
- Spohrer, J.; Maglio, P.P.; Bailey, J.; Gruhl, D. Steps toward a Science of Service Systems. Computer 2007, 40, 71–77. [Google Scholar] [CrossRef]
- Mattyasovszky-Philipp, D.; Molnár, B. Cognitive Resonance and the Architecture Issues of Cognitive Information Systems. In Accentuate Innovations in Cognitive Info-Communication in Series: Topics in Intelligent Engineering and Informatics Infocommunications and Human Centred Engineering (Working Title); Springer: Berlin/Heidelberg, Germany, 2021; in press. [Google Scholar]
- Molnár, B.; Mattyasovszky-Philipp, D.A. An Architectural Approach to Cognitive Information System. In Proceedings of the 10th IEEE International Conference on Cognitive Infocommunications, Naples, Italy, 23–25 October 2019; IEEE: Manhattan, NY, USA, 2019; pp. 459–462. [Google Scholar]
- Ogiela, L.D. Cognitive Information Systems in Management Sciences; Academic Press: Boston, MA, USA, 2017. [Google Scholar]
- Open Group. Togaf: The Open Group Architecture Framework, Version 9.2. 2010. Available online: http://www.opengroup.org/togaf/ (accessed on 26 January 2022).
- Zachman, J.A. A Framework for Information Systems Architecture. IBM Syst. J. 1987, 26, 276–292. [Google Scholar] [CrossRef]
- CCTA (Ed.) Ssadm Version 4 Reference Manuals (Volumes 1–4); NCC Blackwell: Oxford, UK, 1990. [Google Scholar]
- Skidmore, S.; Farmer, R.; Mills, G. Ssadm Models and Methods, Version 4; Blackwell Pub.: Oxford, UK, 1992. [Google Scholar]
- Duncan, J. Ssadm in Practice: A Version 4 Text; Macmillan International Higher Education: London, UK, 1995. [Google Scholar]
- Molnár, B.; Őri, D. Towards a Hypergraph-based Formalism for Enterprise Architecture Representation to Lead Digital Transformation. In European Conference on Advances in Databases and Information Systems; Springer: Berlin/Heidelberg, Germany, 2018; pp. 364–376. [Google Scholar]
- Őri, D.; Molnár, B. A Hypergraph Based Formal Description Technique for Enterprise Architecture Representation. In Proceedings of the 2018 7th International Congress on Advanced Applied Informatics (IIAI-AAI), Yonago, Japan, 8–13 July 2018; IEEE: New York, NY, USA, 2018; pp. 799–804. [Google Scholar]
- Kozák, M.; Stárka, J.; Mlýnková, I. Schematron Schema Inference. In Proceedings of the 16th International Database Engineering & Applications Sysmposium; Association for Computing Machinery (ACM): New York, NY, USA, 2012; pp. 42–50. [Google Scholar]
- Molnár, B.; Béleczki, A.; Sarkadi-Nagy, B. Storing Hypergraph-based Data Models in Non-hypergraph Data Storage and Applications for Information Systems. Vietnam. J. Comput. Sci. 2021, 8, 375–395. [Google Scholar] [CrossRef]
- Krogstie, J.; Opdahl, A.L.; Brinkkemper, S. Conceptual Modeling in Information Systems Engineering; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Evans, A.; Sammut, P.; Willans, J.S. Metamodeling for Mda; First International Workshop: York, UK, 2003. [Google Scholar]
- Zhang, Z. Big Data Mining for Climate Change; Elsevier: Amsterdam, The Netherlands, 2020. [Google Scholar]
- Aubin, J.P.; Désilles, A. Traffic Networks as Information Systems; Springer GmbH: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Blokdijk, A.; Blokdijk, P. Planning and Design of Information Systems; Academic Press: London, UK, 1994. [Google Scholar]
- Kipling, R. Just So Stories for Little Children; Oxford Paperbacks: Oxford, UK, 1998; Available online: https://amzn.to/34yuKka (accessed on 26 January 2022).
- Flood, R.L. I Keep Six Honest Serving Men: They Taught Me All I Knew. Syst. Dyn. Rev. 1994, 10, 231–243. [Google Scholar] [CrossRef]
- Molnár, B.; Benczúr, A. Issues of Modeling Web Information Systems Proposal for a Document-centric Approach. Procedia Technol. 2013, 9, 340–350. [Google Scholar] [CrossRef]
- Gewertz, M. Defining Enterprise: A Systems View of Capability Management. Marc H. Gewertz. 2016. Available online: https://www.eabooks.net/ (accessed on 26 January 2022).
- Olivier Curé, G.B. Rdf Database Systems: Triples Storage and Sparql Query Processing; MORGAN KAUFMANN PUBL INC.: Burlington, MA, USA, 2014. [Google Scholar]
- Molnár, B.; Béleczki, A.; Benczúr, A. Information Systems modeling Based on Graph-theoretic Background. J. Inf. Telecommun. 2017, 2, 68–90. [Google Scholar] [CrossRef]
- Sawyer, S.; Crowston, K.; Wigand, R.T. Digital assemblages: Evidence and theorising from the computerisation of the US residential real estate industry. New Technol. Work. Employ. 2014, 29, 40–56. [Google Scholar] [CrossRef]
- Sassen, S. Territory, Authority, Rights: From Medieval to Global Assemblages; PRINCETON UNIV PR: Princeton, NJ, USA, 2008. [Google Scholar]
- Latham, R. Digital formations: IT and New Architectures in the Global Realm; Princeton University Press: Princeton, NJ, USA, 2005. [Google Scholar]
- Shanahan, J. Soft Computing for Knowledge Discovery: Introducing Cartesian Granule Features; Springer: Boston, MA, USA, 2000. [Google Scholar]
- Savić, M.; Ivanović, M.; Jain, L.C. Complex Networks in Software, Knowledge, and Social Systems; Springer International Publishing: Berlin/Heidelberg, Germany, 2019. [Google Scholar] [CrossRef]
- Abiteboul, S.; Hull, R.; Vianu, V. Foundations of Databases; Addison-Wesley: Singapore, 1995. [Google Scholar]
- Cohrs, M. Ein Architekturmodel Für SAP®-Anwendungen (An Architecture Model for SAP® Applications); Vieweg + Teubner Verlag: Berlin, Germany, 2011. [Google Scholar]
- Fortnow, L. Fifty years of P vs. NP and the possibility of the impossible. Commun. ACM 2022, 65, 76–85. [Google Scholar] [CrossRef]
- Pearl, J. Probabilistic Reasoning in Intelligent Systems: Networks of Plausible Inference; Morgan Kaufmann Publishers: San Mateo, CA, USA, 1988. [Google Scholar]
- Maier, D. Theory Relational Databases; Computer Science Press: Rockville, MD, USA, 1983. [Google Scholar]
- Gottlob, G.; Pichler, R.; Wei, F. Tractable database design through bounded treewidth. In Proceedings of the Twenty-Fifth ACM SIGMOD-SIGACT-SIGART symposium on Principles of Database Systems—PODS, Chicago, IL, USA, 26–28 June 2006; ACM Press: New York, NY, USA, 2006. [Google Scholar] [CrossRef]
- Marini, J. Document Object Model; McGraw-Hill, Inc.: New York, NY, USA, 2002. [Google Scholar]
- Friesen, J. Java XML and JSON; Apress: Berlin/Heidelberg, Germany, 2019. [Google Scholar] [CrossRef]
- Bretto, A. Applications of Hypergraph Theory: A Brief Overview. In Hypergraph Theory; Springer: Berlin/Heidelberg, Germany, 2013; pp. 111–116. [Google Scholar]
- Iordanov, B. HyperGraphDB: A Generalized Graph Database. In Web-Age Information Management—WAIM 2010 International Workshops: IWGD 2010, XMLDM 2010, WCMT 2010, Jiuzhaigou Valley, China, 15–17 July 2010, Revised Selected Papers; Shen, H.T., Pei, J., Özsu, M.T., Zou, L., Lu, J., Ling, T.W., Yu, G., Zhuang, Y., Shao, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6185, pp. 25–36. [Google Scholar] [CrossRef]
- Kobrix Software. Hypergraphdb—A Graph Database. 2010. Available online: http://hypergraphdb.org (accessed on 30 January 2022).
- Michael, R.; Marcus, P.; Christof, B.; Wolfgang, L. The Graph Story of the SAP HANA Database. In Datenbanksysteme für Business, Technologie und Web (BTW), 15. Fachtagung des GI-Fachbereichs “Datenbanken und Informationssysteme” (DBIS), 11.-15.3.2013 in Magdeburg, Germany. Proceedings; Markl, V., Saake, G., Sattler, K., Hackenbroich, G., Mitschang, B., Härder, T., Köppen, V., Eds.; Gesellschaft für Informatik e.V.: Bonn, Germany, 2013; Volume P-214, pp. 403–420. [Google Scholar]
- Newman, M. The Smith normal form. Linear Algebra Its Appl. 1997, 254, 367–381. [Google Scholar] [CrossRef]
- Dummit, D.; Foote, R. Abstract Algebra, 3rd ed.; Wiley: New York, NY, USA, 2004; p. xii + 932. [Google Scholar]
- Scheinerman, E.R.; Ullman, D.H. Fractional Graph Theory; A Wiley-Interscience publication; Wiley: New York, NY, USA, 1997. [Google Scholar]
- Ferrario, D. A Simple Algorithm for Computing the Smith Normal Form of a Matrix in Z. 2016. Available online: https://www.dlfer.xyz/post/2016-10-27-smith-normal-form/ (accessed on 8 June 2021).
- Purvine, E.; Aksoy, S.; Joslyn, C.; Nowak, K.; Praggastis, B.; Robinson, M. A Topological Approach to Representational Data Models. In Human Interface and the Management of Information. Interaction, Visualization, and Analytics; Chapter A Topological 142 Approach to Representational Data Models; Yamamoto, S., Mori, H., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; Volume 10904, pp. 90–109. [Google Scholar] [CrossRef]
- Vick, J.W. Homology Theory: An Introduction to Algebraic Topology; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2012; Volume 145. [Google Scholar]
- Kahle, M. Topology of random clique complexes. Discret. Math. 2009, 309, 1658–1671. [Google Scholar] [CrossRef]
- Praggastis, B.; Arendt, D.; Joslyn, C.; Purvine, E.; Aksoy, S.; Monson, K. PNNL HyperNetX. 2020. Available online: https://pnnl.github.io/HyperNetX/build/index.html (accessed on 20 March 2021).
- Earl, J. Computing Homology of Hypergraphs. 2019. Available online: https://digitalcommons.calpoly.edu/star/561 (accessed on 30 January 2022).
- Dumas, J.G.; Heckenbach, F.; Saunders, D.; Welker, V. Computing Simplicial Homology Based on Efficient Smith Normal Form Algorithms. In Algebra, Geometry and Software Systems; Springer: Berlin/Heidelberg, Germany, 2003; pp. 177–206. [Google Scholar] [CrossRef]
- Robinson, I. Graph Databases; O’Reilly Media, Inc., O’Reilly Media: Sebastopol, CA, USA, 2013. [Google Scholar]
- Deka, G.C. (Ed.) NoSQL; Taylor & Francis Ltd.: Abingdon, UK, 2017. [Google Scholar]
- Brien, P.M.; Poulovassilis, A. A Semantic Approach to Integrating Xml and Structured Data Sources. In Advanced Information Systems Engineering; Springer: Berlin/Heidelberg, Germany, 2001; pp. 330–345. [Google Scholar]
- Meier, A.; Kaufmann, M. SQL & NoSQL Databases; Springer Fachmedien Wiesbaden: Berlin/Heidelberg, Germany, 2019. [Google Scholar] [CrossRef]
- Dietrich, S.W.; Urban, S.D. Fundamentals of Object Databases. Object-Oriented and Object-Relational Design; Morgan & Claypool Publishers: San Rafael, CA, USA, 2010; Volume 12, p. xxi + 151. [Google Scholar] [CrossRef][Green Version]
- Merunka, V.; Molhanec, M. Object Normalization as Contribution to the area of Formal Methods of Object-Oriented Database Design. In Advances in Computer and Information Sciences and Engineering; Springer: Berlin/Heidelberg, Germany, 2008; pp. 300–304. [Google Scholar] [CrossRef]
- Libkin, L. Normalization Theory for XML. In Database and XMLTechnologies; Springer: Berlin/Heidelberg, Germany, 2007; pp. 1–13. [Google Scholar] [CrossRef]
- Lv, T.; Yan, P. XML Normal Forms Based on Constraint-Tree-Based Functional Dependencies. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2007; pp. 348–357. [Google Scholar] [CrossRef]
- Fischer, L. BPMN 2.0 Handbook Second Edition: Methods, Concepts, Case Studies and Standards in Business Process Management Notation; Future Strategies: Lighthouse Point, FL, USA, 2012. [Google Scholar]
- White, S. BPMN Modeling and Reference Guide: Understanding and Using BPMN: Develop Rigorous Yet Understandable Graphical Representations of Business Processes; Future Strategies Inc.: Lighthouse Point, FL, USA, 2008. [Google Scholar]
- Reisig, W. Understanding Petri Nets; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar] [CrossRef]
- Davis, R. The Event-Driven Process Chain. In Business Process Modeling with ARIS: A Practical Guide; Springer: London, UK, 2001; pp. 111–139. [Google Scholar] [CrossRef]
- Singer, R.; Teller, M. Process Algebra and the Subject-Oriented Business Process Management Approach. In S-BPM ONE-Education and Industrial Developments; Springer: Berlin/Heidelberg, Germany, 2012; pp. 135–150. [Google Scholar] [CrossRef]
- Wong, P.Y.; Gibbons, J. Formalisations and applications of BPMN. Sci. Comput. Program. 2011, 76, 633–650. [Google Scholar] [CrossRef]
- Jensen, K.; Rozenberg, G. (Eds.) High-Level Petri Nets; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar] [CrossRef]
- Mutarraf, U.; Barkaoui, K.; Li, Z.; Wu, N.; Qu, T. Transformation of Business Process Model and Notation models onto Petri nets and their analysis. Adv. Mech. Eng. 2018, 10, 168781401880817. [Google Scholar] [CrossRef]
- Eshuis, R.; Wieringa, R. Verification support for workflow design with UML activity graphs. In Proceedings of the 24th International Conference on Software Engineering, Orlando, FL, USA , 19–25 May 2002; ACM Press: New York, NY, USA, 2002; pp. 166–176. [Google Scholar] [CrossRef]
- Larman, C. Applying Uml and Patterns: An Introduction to Object-Oriented Analysis and Design and Iterative Development, 3/e; Pearson Education India: New Delhi, India, 2012. [Google Scholar]
- Scheer, A.W.; Thomas, O.; Adam, O. Process Modeling using Event-Driven Process Chains. In Process-Aware Information Systems; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2005; pp. 119–145. [Google Scholar] [CrossRef]
- Bouafia, K.; Molnár, B. Formal Verification of Analysis Approach for Enterprise Information Systems Architecture Using Hypergraph Representation Based on Finite State Machines for Supporting Business Process Requirements. J. Appl. Bus. Econ. (JABE) 2020, 22, 265. [Google Scholar] [CrossRef]
- Saligny, L.; Bouillé, F. La Méthode Hbds: Hypergraph-based Data Structure; Information Spatiale Et Archéologie. 2011, pp. 62–65. Available online: https://halshs.archives-ouvertes.fr/halshs-00959477 (accessed on 26 January 2022).
- Sun, L.; Ji, S.; Ye, J. Hypergraph Spectral Learning for Multi-label Classification. In Proceedings of the Fourteenth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Las Vegas, NV, USA, 24–27 August 2008; pp. 668–676. [Google Scholar] [CrossRef]
- Ducournau, A. Hypergraphes: Clustering, Réduction Et Marches Aléatoires Orientées Pour La Segmentation D’images Et De Vidéo. Ph.D. Thesis, Ecole Nationale d’ingénieurs, Saint-Etienne, France, 2012. [Google Scholar]
- Rital, S. Hypergraphe De Voisinage Spatiocolorimétrique: Application En Traitement D’images. Ph.D. Thesis, Université de Bourgogne, Dijon, France, 2004. [Google Scholar]
- Tian, Z.; Hwang, T.; Kuang, R. A Hypergraph-Based Learning Algorithm for Classifying Gene Expression and arrayCGH Data with Prior Knowledge. Bioinformatics 2009, 25, 2831–2838. [Google Scholar] [CrossRef]
- Koppen, E.; Neumann, G. Active Hypertext for Distributed Web Applications. In Proceedings of the IEEE 8th International Workshops on Enabling Technologies: Infrastructure for Collaborative Enterprises (WET ICE’99), Stanford, CA, USA, 18 June 1999. [Google Scholar] [CrossRef]
- Atzeni, P.; Merialdo, P.; Mecca, G. Data-intensive Web Sites: Design and Maintenance. World Wide Web 2001, 4, 21–47. [Google Scholar] [CrossRef]
- Rossi, G.; Schwabe, D.; Lyardet, F. Web Application Models Are More Than Conceptual Models. In International Conference on Conceptual Modeling; Springer: Berlin/Heidelberg, Germany, 1999; pp. 239–252. [Google Scholar]
- Erl, T. Service-Oriented Architecture: Concepts, Technology, and Design; Pearson Education India: New Delhi, India, 2005. [Google Scholar]
- Erl, T. Service-Oriented Architecture; Pearson Education: London, UK, 2017. [Google Scholar]
- Wilde, E.; Pautasso, C. (Eds.) REST: From Research to Practice; Springer: New York, NY, USA, 2011. [Google Scholar] [CrossRef]
- Chinnici, R.; Moreau, J.J.; Ryman, A.; Weerawarana, S. Web Services Description Language (wsdl) Version 2.0 Part 1: Core Language. W3C Recomm. 2007, 26, 19. [Google Scholar]
- MacKenzie, C.M.; Laskey, K.; McCabe, F.; Brown, P.F.; Metz, R.; Hamilton, B.A. Reference Model for Service Oriented Architecture 1.0. Oasis Standard. 2006. Available online: http://angeldeacero.wdfiles.com/local–files/start/oasissoa.pdf (accessed on 26 January 2022).
- Bernauer, M.; Schrefl, M. Self-maintaining Web Pages: From Theory to Practice. Data Knowl. Eng. 2004, 48, 39–73. [Google Scholar] [CrossRef]
- Chiu, C.M.; Bieber, M. A Dynamically Mapped Open Hypermedia System Framework for Integrating Information Systems. Inf. Softw. Technol. 2001, 43, 75–86. [Google Scholar] [CrossRef]
- Nam, C.K.; Jang, G.S.; Bae, J.H.J. An Xml-based Active Document for Intelligent Web Applications. Expert Syst. Appl. 2003, 25, 165–176. [Google Scholar] [CrossRef]
- Molnár, B.; Benczúr, A.; Tarcsi, Á. Formal Approach to a Web Information System Based on Story Algebra. Singidunum J. Appl. Sci. 2012, 9, 63–73. [Google Scholar] [CrossRef]
- Suh, N.P. Axiomatic Design: Advantages and Applications; Oxford University Press: New York, NY, USA, 2001. [Google Scholar]
- Broekstra, J.; Kampman, A.; van Harmelen, F. Sesame: A Generic Architecture for Storing and Querying RDF and RDF Schema. In The Semantic Web — ISWC 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 54–68. [Google Scholar] [CrossRef]
- Šmite, D.; Moe, N.B.; Ågerfalk, P.J. (Eds.) Agility Across Time and Space; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar] [CrossRef]
- Lankhorst, M. (Ed.) Agile Service Development; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar] [CrossRef]
- Berliner BPM-Offensive. BPMN 2.0 Poster—Business Process Model and Notation. Available online: http://www.bpmb.de/index.php/BPMNPoster (accessed on 12 September 2021).
- Emam, K.E.; Mosquera, L.; Hoptroff, R. Practical Synthetic Data Generation; O’Reilly Media, Inc.: New York, NY, USA, 2020. [Google Scholar]
- Edwards, H.M. Linear Algebra; Birkhäuser: Boston, MA, USA, 2013. [Google Scholar]
- David, S.; Dummit, R.M.F. Abstract Algebra; WILEY: Hoboken, NJ, USA, 2003. [Google Scholar]
- A Tool for Computing the Smith Normal Forms over Arbitrary Principle Ideal Domains. Available online: https://pypi.org/project/smithnormalform/ (accessed on 26 September 2021).
- Peltier, S.; Alayrangues, S.; Fuchs, L.; Lachaud, J.O. Computation of homology groups and generators. Comput. Graph. 2005, 30, 62–69. [Google Scholar] [CrossRef]
- Agoston, M. Algebraic Topology: A First Course; M. Dekker: New York, NY, USA, 1976. [Google Scholar]
- Smith, H.J.S. Arithmetical notes. Proc. Lond. Math. Soc. 1976, 4, 236–253. [Google Scholar] [CrossRef]
- Bouafia, K.; Molnár, B. Hypergraph Application on Business Process Performance. Information 2021, 12, 370. [Google Scholar] [CrossRef]
- Geroimenko, V. Dictionary of XML Technologies and the Semantic Web; Springer: London, UK, 2013. [Google Scholar]
- van der Aalst, W.; ter Hofstede, A.; Kiepuszewski, B.; Barros, A. Workflow Patterns. Distrib. Parallel Databases 2003, 14, 5–51. [Google Scholar] [CrossRef]
- Fischer, L. Workflow Handbook, 2nd ed.; Future Strategies: Lighthouse Point, FL, USA, 2002. [Google Scholar]
- Molnár, B.; Benczúr, A. Facet of Modeling Web Information Systems from a Document-centric View. Int. J. Web Portals (IJWP) 2013, 5, 57–70. [Google Scholar] [CrossRef]
- Thompson, S. Type Theory and Functional Programming; Addison-Wesley: Wokingham, UK, 1991. [Google Scholar]
- Sharvit, Y. Data-Oriented Programming: Unlearning Objects; MANNING PUBN: New York, NY, USA, 2022. [Google Scholar]
- Perry, M.L. The Art of Immutable Architecture; Apress: New York, NY, USA, 2020. [Google Scholar] [CrossRef]
- Lazuashvili, N.; Norta, A.; Draheim, D. Integration of Blockchain Technology into a Land Registration System for Immutable Traceability: A Casestudy of Georgia. In Business Process Management: Blockchain and Central and Eastern Europe Forum; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; pp. 219–233. [Google Scholar] [CrossRef]
- Malone, T.W.; Crowston, K.; Herman, G.A. Organizing Business Knowledge: The MIT Process Handbook; The MIT Press: Cambridge, MA, USA, 2003. [Google Scholar]
- Russell, N.; van der Aalst, W.M.P.; ter Hofstede, A.H. Workflow Patterns; MIT Press Ltd.: Cambridge, MA, USA, 2016. [Google Scholar]
- Fischer, L. Workflow Handbook, 1st ed.; Future Strategies: Lighthouse Point, FL, USA, 2000. [Google Scholar]
- Kiepuszewski, B.; ter Hofstede, A.H.M.; Bussler, C.J. On Structured Workflow modeling. In Notes on Numerical Fluid Mechanics and Multidisciplinary Design; Springer International Publishing: Berlin/Heidelberg, Germany, 2000; pp. 431–445. [Google Scholar] [CrossRef]
- Dehnert, J.; Rittgen, P. Relaxed Soundness of Business Processes. In Notes on Numerical Fluid Mechanics and Multidisciplinary Design; Springer International Publishing: Berlin/Heidelberg, Germany, 2001; pp. 157–170. [Google Scholar] [CrossRef]
- Ye, Y.; Roy, K. Efficient synthesis of AND/XOR networks. In Proceedings of the ASP-DAC’97: Asia and South Pacific Design Automation Conference, Chiba, Japan, 28–31 January 1997; IEEE: New York, NY, USA, 1997. [Google Scholar]
- Thakur, M.; Tripathi, R. Linear connectivity problems in directed hypergraphs. Theor. Comput. Sci. 2009, 410, 2592–2618. [Google Scholar] [CrossRef]
- Chandra, A.K.; Harel, D. Horn clause queries and generalizations. J. Log. Program. 1985, 2, 1–15. [Google Scholar] [CrossRef]
- Kowalski, R.A. Predicate Logic as Programming Language. Information Processing. In Proceedings of the 6th IFIP Congress 1974, Stockholm, Sweden, 5–10 August 1974; Rosenfeld, J.L., Ed.; North-Holland: New York, NY, USA, 1974; pp. 569–574. [Google Scholar]
- Ligeza, A. Logical Foundations for Rule-Based Systems; Springer GmbH: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Gammaitoni, L.; Kelsen, P. F-Alloy: A relational model transformation language based on Alloy. Softw. Syst. Model. 2019, 18, 213–247. [Google Scholar] [CrossRef]
- Gammaitoni, L.; Kelsen, P. F-alloy: An alloy based model transformation language. In International Conference on Theory and Practice of Model Transformations; Springer: Berlin/Heidelberg, Germany, 2015; pp. 166–180. [Google Scholar] [CrossRef]
- Jackson, D. Alloy: A language and tool for exploring software designs. Commun. ACM 2019, 62, 66–76. [Google Scholar] [CrossRef]
- Armstrong, M. A Handbook of Human Resource Management Practice; Kogan Page: London, UK, 2006. [Google Scholar]
- Ullman, J.D. A First Course in Database Systems; Pearson Education India: Upper Saddle River, NJ, USA, 2007. [Google Scholar]
- Klug, A.; Price, R. Determining View dependencies using tableaux. ACM Trans. Database Syst. 1982, 7, 361–380. [Google Scholar] [CrossRef]
- Curran, T. SAP R/3 Business Blueprint: Understanding Enterprise Supply Chain Management; Prentice Hall PTR: Upper Saddle River, NJ, USA, 2000. [Google Scholar]
- Garcia-Molina, H.; Salem, K. Sagas. ACM SIGMOD Rec. 1987, 16, 249–259. [Google Scholar] [CrossRef]
- Liu, L.; Özsu, M.T. (Eds.) Web Services Business Process Execution Language; Encyclopedia of Database Systems; Springer: Boston, MA, USA, 2009. [Google Scholar] [CrossRef]
- Eiter, T.; Gottlob, G. Hypergraph Transversal Computation and Related Problems in Logic and AI. In Logics in Artificial Intelligence; Springer: Berlin/Heidelberg, Germany, 2002; pp. 549–564. [Google Scholar] [CrossRef]
- Bailey, J.; Manoukian, T.; Ramamohanarao, K. A fast algorithm for computing hypergraph transversals and its application in mining emerging patterns. Third IEEE International Conference on Data Mining. IEEE Comput. Soc. 2003. [Google Scholar] [CrossRef]
- Brault-Baron, J. Hypergraph Acyclicity Revisited. ACM Comput. Surv. 2016, 49, 1–26. [Google Scholar] [CrossRef]
- Marc, H.; Graham. On the Universal Relation; Technical report; University of Toronto: Toronto, ON, Canada, 1979. [Google Scholar]
- Brault-Baron, J.; Capelli, F.; Mengel, S. Understanding model counting for beta-acyclic CNF-formulas. arXiv 2014, arXiv:1405.6043. [Google Scholar]
- D’Atri, A.; Moscarini, M. On the recognition and design of acyclic databases. In Proceedings of the 3rd ACM SIGACT-SIGMOD Symposium on Principles of Database Systems-PODS; ACM Press: New York, NY, USA, 1984. [Google Scholar] [CrossRef]
- Tarjan, R.E.; Yannakakis, M. Simple Linear-Time Algorithms to Test Chordality of Graphs, Test Acyclicity of Hypergraphs, and Selectively Reduce Acyclic Hypergraphs. SIAM J. Comput. 1984, 13, 566–579. [Google Scholar] [CrossRef]
- Yu, C.; Ozsoyoglu, M. An algorithm for tree-query membership of a distributed query. In Proceedings of the COMPSAC 79 Computer Software and The IEEE Computer Society’s Third International Applications Conference, Chicago, IL, USA, 6–8 November 1979; IEEE: New York, NY, USA, 1979; pp. 306–312. [Google Scholar] [CrossRef]
- Ahituv, N.; Neumann, S.; Zviran, M. A System Development Methodology for ERP Systems. J. Comput. Inf. Syst. 2002, 42, 56–67. [Google Scholar] [CrossRef]
- Yamakawa, P.; Noriega, C.O.; Linares, A.N.; Ramírez, W.V. Improving ITIL compliance using change management practices: A finance sector case study. Bus. Process Manag. J. 2012, 18, 1020–1035. [Google Scholar] [CrossRef]
- Kherbouche, M.; Bouafia, K.; Molnár, B. Transformation of Uml State Machine to Yawl. In Proceedings of the Ninth IEEE International Conference on Intelligent Computing and Information Systems, Washington, DC, USA, 11–14 October 2009. [Google Scholar] [CrossRef]
- Kherbouche, M.; Mukashaty, A.A.; Molnár, B. An Operationalized Transformation for Activity Diagram into YAWL. In Developments in Computer Science, 17–19 June 2021, ELTE, Hungary; Csuhaj Varjú, E., Ed.; Eötvös Loránd University of Budapest, Faculty of Informatics, Eötvös Loránd University of Budapest, Faculty of Informatics: Budapest, Hungary, 2021; Available online: http://dcs.elte.hu/wp-content/uploads/2022/01/DCS_proceedings.pdf (accessed on 30 January 2022).
- Hofstede, A.H.M.; Aalst, W.M.P.; Adams, M.; Russell, N. (Eds.) Modern Business Process Automation; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar] [CrossRef]
- Kherbouche, M.; Molnár, B. Formal Model Checking and Transformations of Models Represented in UML with Alloy. In Modeling to Program; Thalheim, B., Ed.; Springer International Publishing: Berlin/Heidelberg, Germany, 2021; pp. 127–136. [Google Scholar] [CrossRef]
- Alrabbaa, C.; Baader, F.; Borgwardt, S.; Koopmann, P.; Kovtunova, A. Finding Good Proofs for Description Logic Entailments using Recursive Quality Measures. In Automated Deduction—CADE 28; Springer International Publishing: Berlin/Heidelberg, Germany, 2021; pp. 291–308. [Google Scholar] [CrossRef]
- Amit Basu, R.W.B. Metagraphs and Their Applications; Springer GmbH: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Tao, F. Digital Twin Driven Smart Manufacturing; Academic Press: London, UK, 2019. [Google Scholar]
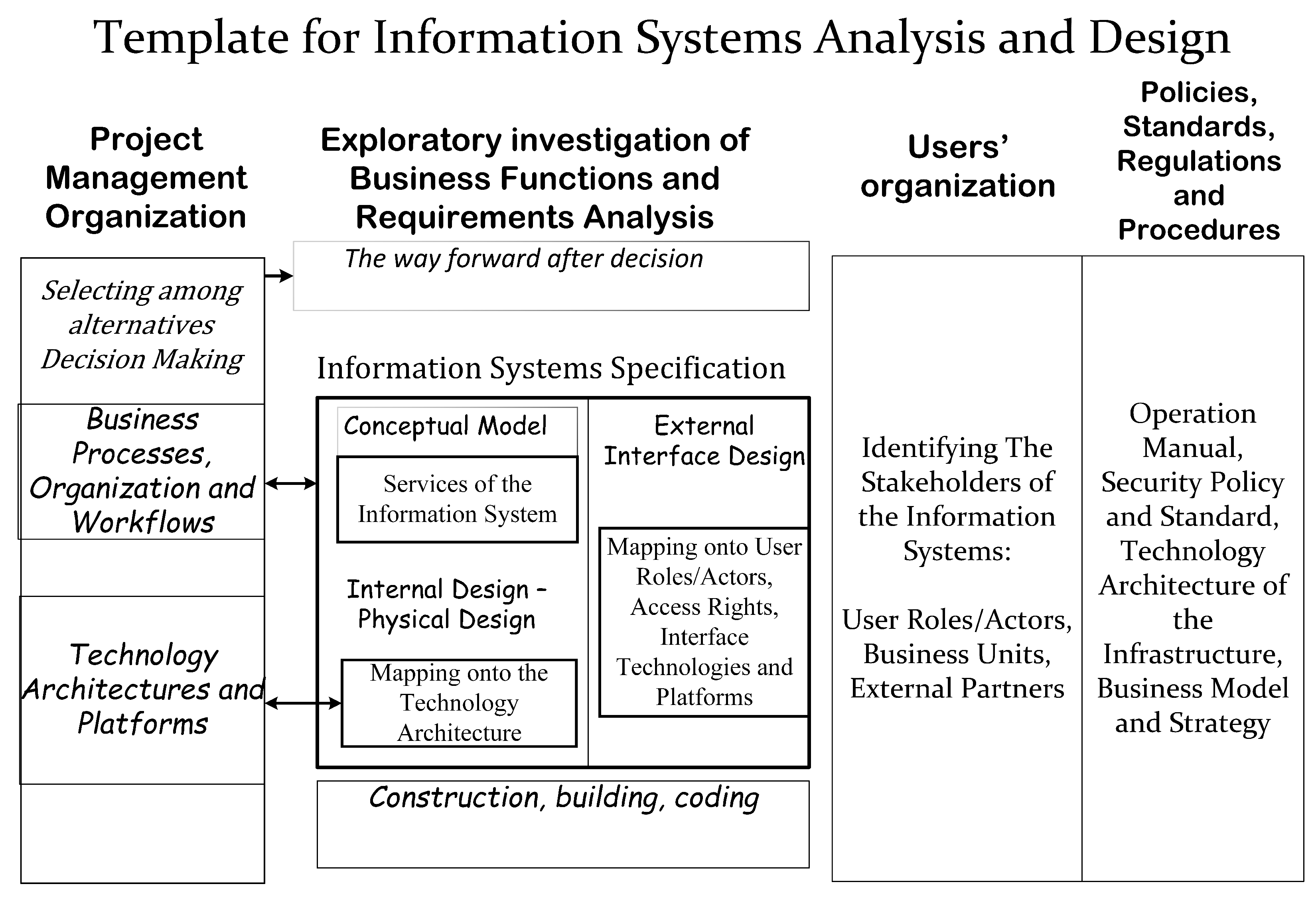








| Concept of Enterprise Architecture | Representation of Concept in the Domain of Hyper-Graph Theory |
|---|---|
| Information System (IS) | This consists of various models that depict the system from different aspects. The models and their constituents can be mapped onto a generalized hyper-graph to reflect the hierarchy of the models and their components. |
| A vertex in a hyper-graph | A vertex can represent a model element that can be characterized by constraints, pre- and post-conditions, and business rules formulated in logical statements. |
| Edge in a hyper-graph | An edge corresponds to a traditional edge in graphs, which connects two vertices in hyper-graphs. A simple edge designates the binary relationship between model components. |
| Hyperedge | A hyperedge represents a relationship among a specific group of vertices, e.g., models and their artifacts that are constituents of specific architecture layers. |
| System graph | This is a hyper-graph dedicated to describing the whole Information System; it contains hyperedges and their vertices, which represent models and their artifacts. It includes a disjointed node to denote the surrounding environment. |
| Sub-system | A specific module or well-defined part of an Information System. A set of hyperedges representing a sub-system composed of models and their artifacts belonging to this specific part of the system. |
| Aspects/Model Tier | What | How | Where | Who | When | Why | Viewpoints of Actors | Viewpoints of Roles |
|---|---|---|---|---|---|---|---|---|
| Extent of Business Domain | Facts, documents | Governance of Business Processes | Workflows for Business Processes | Organigram | Strategic Plan | Fundamental Objectives | Strategic Planner | Enterprise Architect |
| Notions of Business | Notional level data model of Data Collections (Directed Graph) | Process Model (Directed Graph) | Locations connected to Process Model (Graph) | Actor, Role coupled to Process Model (Graph) | Project Chart of Program (Directed Graph) | Association of Ideas and Objectives (Graph) | Business Analyst System Analyst | Business Architect and Process Architect |
| Logical Model of System | Logical Model for Data Collections (Directed Graph) | Logical model of Activities and Tasks (Directed Graph) | Logical Model of Components and Placement for Communication (Graph) | Actor, Role joined to Activity and Task Model (Graph) | Event and timing model (Directed Graph) | Business Rule (RDF/OWL Directed Graph) | System Designer | Insight Architect |
| Technology and Physical | Physical Data model (Graph) | Executable/ Interpretable Process/ Activity Model (Directed Graph) | Communication structure represented by deployed components (Graph) | Components for Access Rights and Roles (Directed Graph) | Choreography and Orchestration depicted by State Machines and Automaton (Directed Graph) | Executable/ Interpretable Rule Design (Directed Graph) | Program Designer and Developer | IT Architect |
| Assemblies of Constituents | Data in the physical implementation of DBMS | Code for Executable/ Interpretable Process/ Activity Model (Directed Graph) | Code for Communication structure represented by deployed components (Graph) | Code for Access Rights and Roles (Directed Graph) | Code for State Machines and Automaton (Directed Graph) | Code for Executable/ Interpretable Rule Design (Directed Graph) | System Builder and Implementer | System Architect |
| Functioning Enterprise | Data | Function | Network | Organization | Schedule | Strategy | Staff | Service Architect |
| 1 | 1 | 0 | 0 | 0 | 0 | |
| 0 | 1 | 1 | 1 | 0 | 0 | |
| 1 | 1 | 1 | 1 | 1 | 0 |
| 1 | 1 | 0 | 0 | 0 | |
| 1 | 1 | 1 | 0 | 0 | |
| 0 | 0 | 1 | 1 | 1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Molnár, B.; Benczúr, A. The Application of Directed Hyper-Graphs for Analysis of Models of Information Systems. Mathematics 2022, 10, 759. https://doi.org/10.3390/math10050759
Molnár B, Benczúr A. The Application of Directed Hyper-Graphs for Analysis of Models of Information Systems. Mathematics. 2022; 10(5):759. https://doi.org/10.3390/math10050759
Chicago/Turabian StyleMolnár, Bálint, and András Benczúr. 2022. "The Application of Directed Hyper-Graphs for Analysis of Models of Information Systems" Mathematics 10, no. 5: 759. https://doi.org/10.3390/math10050759
APA StyleMolnár, B., & Benczúr, A. (2022). The Application of Directed Hyper-Graphs for Analysis of Models of Information Systems. Mathematics, 10(5), 759. https://doi.org/10.3390/math10050759








