Changing the Threshold in a Bivariate Polynomial Based Secret Image Sharing Scheme
Abstract
:1. Introduction
2. Related Works
2.1. Polynomial Based SIS
- 1
- A dealer encrypts a confidential image O into shadows .
- 2
- Each shadow is sent to participant through a secure channel.
- 1
- The dealer divides O into l-non-overlapping k-pixel groups, .
- 2
- For k pixels in each group , the dealer builds a degree polynomial .
- 3
- The dealer computes n sub-shadows, .
- 4
- The dealer outputs n shadows .
- 1
- Reconstructing from using Lagrange interpolation:then the block is recovered from all k coefficients in .
- 2
- Output: .
2.2. Results on TCSIS
- 1
- A dealer encrypts a confidential image O into initial shadows .
- 2
- Each initial shadow is sent to participant through secure channel.
- 1
- A threshold T is selected from the set of all possible thresholds .
- 2
- Each participant updates the shadow according to current threshold T.
- 3
- Any group of participants that satisfy the access structure can reconstruct the image O using updated shadows.
- 1
- The dealer divides an image O into l non-overlapping pixel blocks, .
- 2
- For pixels in each block , generates a degree polynomial .
- 3
- selects randomly integers , and generates a degree polynomials . In addition, randomly selects integers and generates a polynomial: .
- 3
- Let . computes n sub-shadows , and the initial shadow of is .
- 1
- If the threshold is k, k or more initial shadows can reconstruct l polynomials . pixel block is made up of the first coefficients in , and thus the image can be recovered.
- 2
- If the threshold is , publishes the information of to all participants. Each participant updates its shadow by: . Here the operation of is defined as:. Let . The threshold of all updated shadows in is decreased to from k.
- 3
- If the threshold is , publishes the information of . Each participant updates their shadow by . Here the operation of is defined as: . Let . The threshold of all updated shadows in is increased to from k.
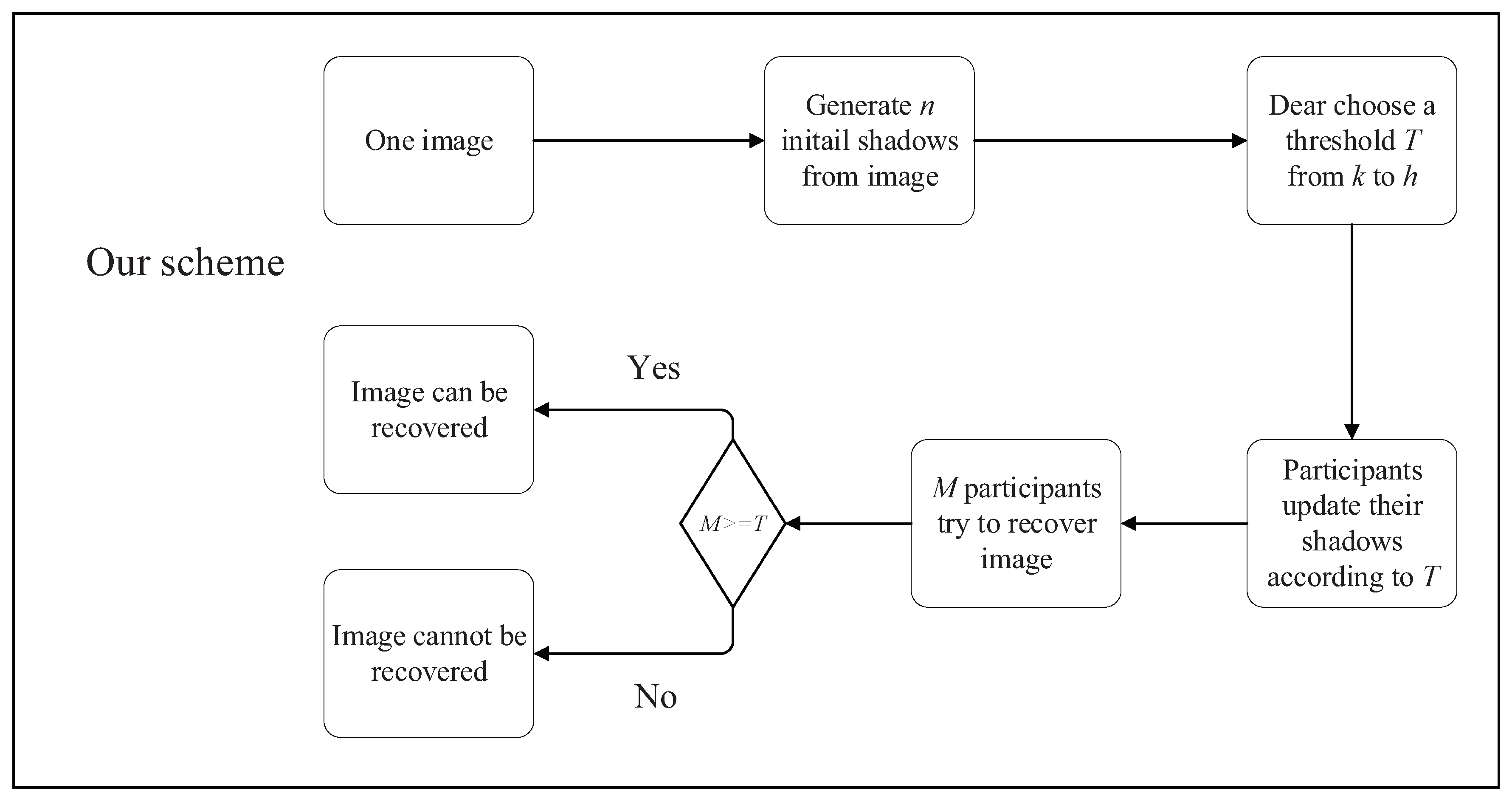
3. Proposed Scheme
3.1. Design Motivation
3.2. TCSIS Using a Bivariate Polynomial
- 1
- Suppose are pixels in G, builds a bivariate polynomial:
- 2
- computes . The initial shadow for is .
- 1
- Select a threshold T from the set .
- (a)
- If current threshold is , each participant updates their shadow by .
- (b)
- If the current threshold is , each participant updates its shadow by .
- (c)
- If the current threshold T satisfies , the participants select integers other than . Each participant computes , and the updated shadow is.
- 2
- Any group of T participants can reconstruct all pixels in G using Lagrange interpolation.
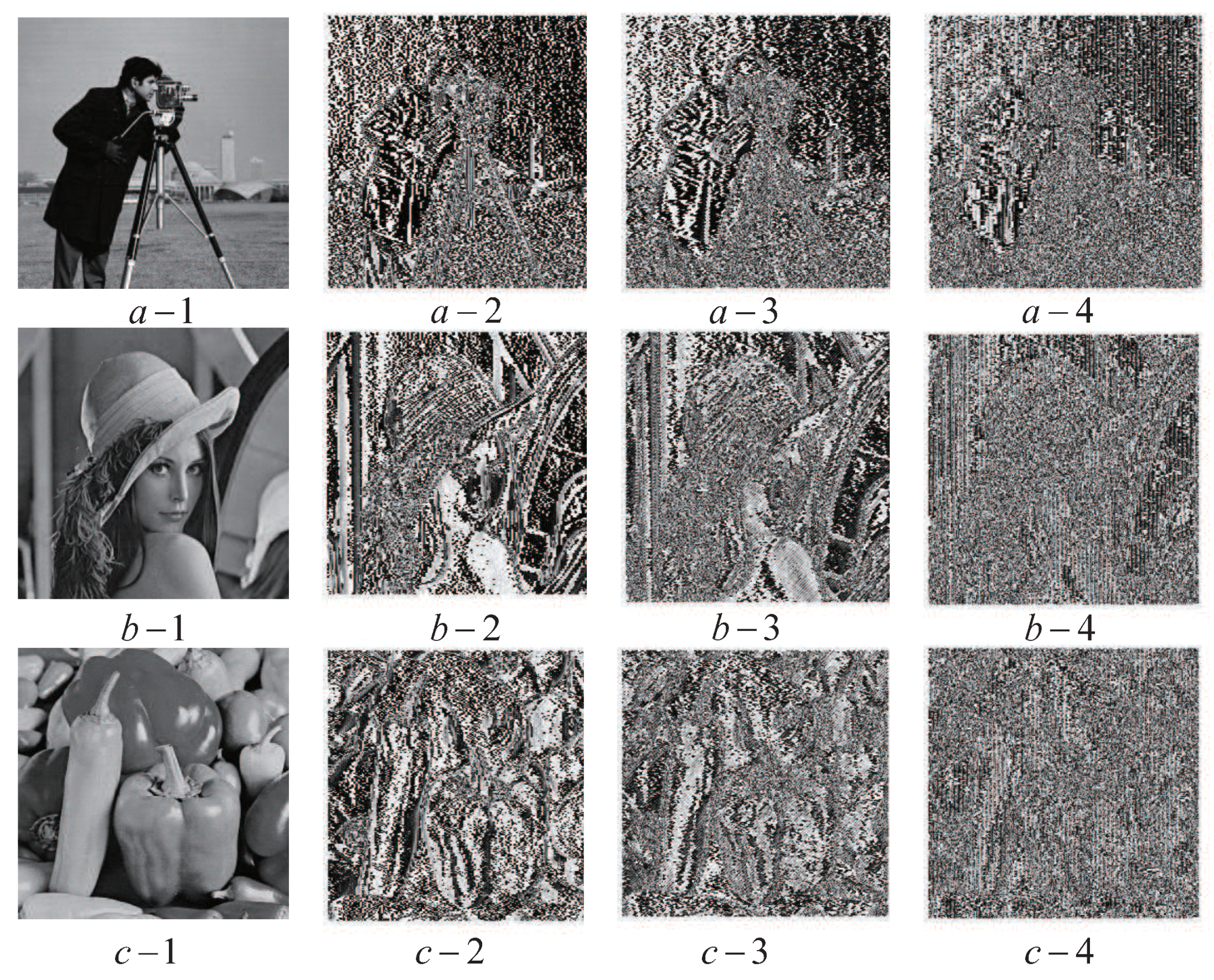
4. Results and Discussion
- If , publishes , all coefficients in can be computed using Lagrange interpolation according to Theorem 1. Then the image can be reconstructed.
- If , publish . Here . The interpolation polynomial on is for Example 1. Then, all coefficients in can be computed using the Lagrange interpolation according to Theorem 3. Then the image can be reconstructed.
- If , , publish . All coefficients in can be computed using Lagrange interpolation according to Theorem 1. Then the image can be reconstructed.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Zhou, Z.L.; Wu, Q.J.; Yang, Y.M.; Sun, X.M. Region-level visual consistency verification for large-scale partial-duplicate image search. ACM Trans. Multimed. Comput. Commun. Appl. 2020, 16, 1–25. [Google Scholar] [CrossRef]
- Wang, C.C.; Kuo, W.C.; Huang, Y.C.; Wuu, L.C. A high capacity data hiding scheme based on re-adjusted GEMD. Multimed. Tools Appl. 2018, 77, 6327–6341. [Google Scholar] [CrossRef]
- Zhou, Z.L.; Mu, Y.; Wu, Q.J. Coverless image steganography using partial-duplicate image retrieval. Soft Comput. 2019, 23, 4927–4938. [Google Scholar] [CrossRef]
- Naor, M.; Shamir, A. Visual cryptography. Lect. Notes Comput. Sci. 1994, 950, 1–12. [Google Scholar]
- Wang, R.Z. Region incrementing visual cryptography. IEEE Signal Process. Lett. 2009, 16, 659–662. [Google Scholar] [CrossRef]
- Yang, C.N.; Shih, H.W.; Wu, C.C.; Harn, L. k out of n region incrementing scheme in visual cryptography. IEEE Trans. Circuits Syst. Video Technol. 2012, 22, 799–809. [Google Scholar] [CrossRef]
- Thien, C.C.; Lin, J.C. Secret image sharing. Comput. Graph. 2002, 26, 765–770. [Google Scholar] [CrossRef]
- Wang, R.Z.; Shyu, S.J. Scalable secret image sharing. Signal Process. Image Commun. 2007, 22, 363–373. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.Y.; Yeh, P.H. Reducing shadow size in smooth scalable secret image sharing. Secur. Commun. Netw. 2014, 7, 2237–2244. [Google Scholar] [CrossRef]
- Wang, Z.H.; Di, Y.F.; Li, J.J.; Chang, C.C.; Liu, H. Progressive secret image sharing scheme using meaningful shadows. Secur. Commun. Netw. 2016, 9, 4075–4088. [Google Scholar] [CrossRef]
- Yan, X.H.; Wang, S.; Niu, X.M. Threshold progressive visual cryptography construction with unexpanded shares. Mutimedia Tools Appl. 2016, 75, 8657–8674. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N.; Wu, S.Y.; Chou, Y.S. Progressive (k, n) secret image sharing schemes based on Boolean operations and covering codes. Signal Process. Image Commun. 2018, 66, 77–86. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N. Scalable secret image sharing scheme with essential shadows. Signal Process. Image Commun. 2017, 58, 49–55. [Google Scholar] [CrossRef]
- Li, P.; Yang, C.N.; Wu, C.C.; Kong, Q.; Ma, Y. Essential secret image sharing scheme with different importance of shadows. J. Vis. Commun. Image Represent. 2013, 24, 1106–1114. [Google Scholar] [CrossRef]
- Yang, C.N.; Ouyang, J.F.; Harn, L. Steganography and authentication in image sharing without parity bits. Opt. Commun. 2012, 285, 1725–1735. [Google Scholar] [CrossRef]
- Ye, G.D.; Liu, M.; Wu, M.F. Double image encryption algorithm based on compressive sensing and elliptic curve. Alex. Eng. J. 2022, 61, 6785–6795. [Google Scholar] [CrossRef]
- Gong, L.H.; Qiu, K.D.; Deng, C.Z.; Zhou, N.R. An optical image compression and encryption scheme based on compressive sensing and RSA algorithm. Opt. Lasers Eng. 2019, 121, 169–180. [Google Scholar] [CrossRef]
- Zhang, Z.; Chee, Y.M.; Ling, S.; Liu, M.; Wang, H. Threshold changeable secret sharing schemes revisited. Theor. Comput. Sci. 2012, 418, 106–115. [Google Scholar] [CrossRef] [Green Version]
- Steinfeld, R.; Pieprzyk, J.; Wang, H.X. Lattice-based threshold-changeability for standard crt secret-sharing schemes. Finite Fields Their Appl. 2006, 12, 653–680. [Google Scholar] [CrossRef]
- Harn, L.; Hsu, C.F. Dynamic threshold secret reconstruction and its application to the threshold cryptography. Inf. Process. Lett. 2015, 115, 851–857. [Google Scholar] [CrossRef]
- Yuan, L.F.; Li, M.C.; Guo, C.; Hu, W.T.; Luo, X.J. Secret image sharing scheme with threshold changeable capability. Math. Probl. Eng. 2016, 2016, 9576074. [Google Scholar] [CrossRef] [Green Version]
- Liu, Y.X.; Yang, C.N.; Wu, C.M.; Sun, Q.D.; Bi, W. Threshold changeable secret image sharing scheme based on interpolation polynomial. Multimed. Tools Appl. 2019, 78, 18653–18667. [Google Scholar] [CrossRef]

| Schemes | Thresholds | Changing Threshold | Security Level | Main Computation | Shadow Size |
|---|---|---|---|---|---|
| Scheme [22] | Dealer involves | Unconditional | Polynomial interpolation | ||
| Scheme [21] | Dealer involves | Conditional | One way function | ||
| Proposed scheme | Without dealer | Unconditional | Polynomial interpolation |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, Q.; Cao, H.; Li, S.; Song, H.; Liu, Y. Changing the Threshold in a Bivariate Polynomial Based Secret Image Sharing Scheme. Mathematics 2022, 10, 710. https://doi.org/10.3390/math10050710
Sun Q, Cao H, Li S, Song H, Liu Y. Changing the Threshold in a Bivariate Polynomial Based Secret Image Sharing Scheme. Mathematics. 2022; 10(5):710. https://doi.org/10.3390/math10050710
Chicago/Turabian StyleSun, Qindong, Han Cao, Shancang Li, Houbing Song, and Yanxiao Liu. 2022. "Changing the Threshold in a Bivariate Polynomial Based Secret Image Sharing Scheme" Mathematics 10, no. 5: 710. https://doi.org/10.3390/math10050710
APA StyleSun, Q., Cao, H., Li, S., Song, H., & Liu, Y. (2022). Changing the Threshold in a Bivariate Polynomial Based Secret Image Sharing Scheme. Mathematics, 10(5), 710. https://doi.org/10.3390/math10050710








