An Implementation of Image Secret Sharing Scheme Based on Matrix Operations
Abstract
:1. Introduction
2. Thien and Lin’s Secret Image Sharing Scheme
2.1. Secret Sharing Stage
| Algorithm 1 Thien and Lin’s secret image sharing scheme |
| Input: S, id1, id2, … , idn Output: S1, S2, … , Sn |
| Step1: Let j = 1 Step2: The k pixels from k(j−1) + 1 to k(j−1) + k are selected in S and assigned to a0, a1, …, ak−1 Step3: Construct the polynomial (1) where p > 0 Step4: Calculate Sij = f(idi), i = 1, … , n. Step5: If j < w/k, let j = j + 1 and skip to Step2; if j < w/k, skip to Step6. Step6: Using Sij, j = 1, … ,w/k as the pixel gray value of image Si and obtain the shadow image Si, i = 1, … , n. |
2.2. Secret Recovery Stage
| Algorithm 2 Thien and Lin’s secret image recovery scheme |
| Input: id1, id2, …, idk; S1, S2, …, Sk. Output: S |
| Step1: Denote the jth pixel gray value of Si as Sij and let j = 1. Step2: Substitute id1, id2, … , idk and S1j, S2j, … , Skj into the Lagrange’s interpolation polynomial (4). Step3: Take the coefficient a0, a1, … , ak−1 of f (x), let Sk(j−1) + 1 = a0, Sk(j−1) + 2 = a1, … , Sk(j−1) + k = ak−1. Step4: If j < w/k, let j = j + 1 and skip to Step2; if j = w/k, then skip to Step5. Step5: Get the secret image S |
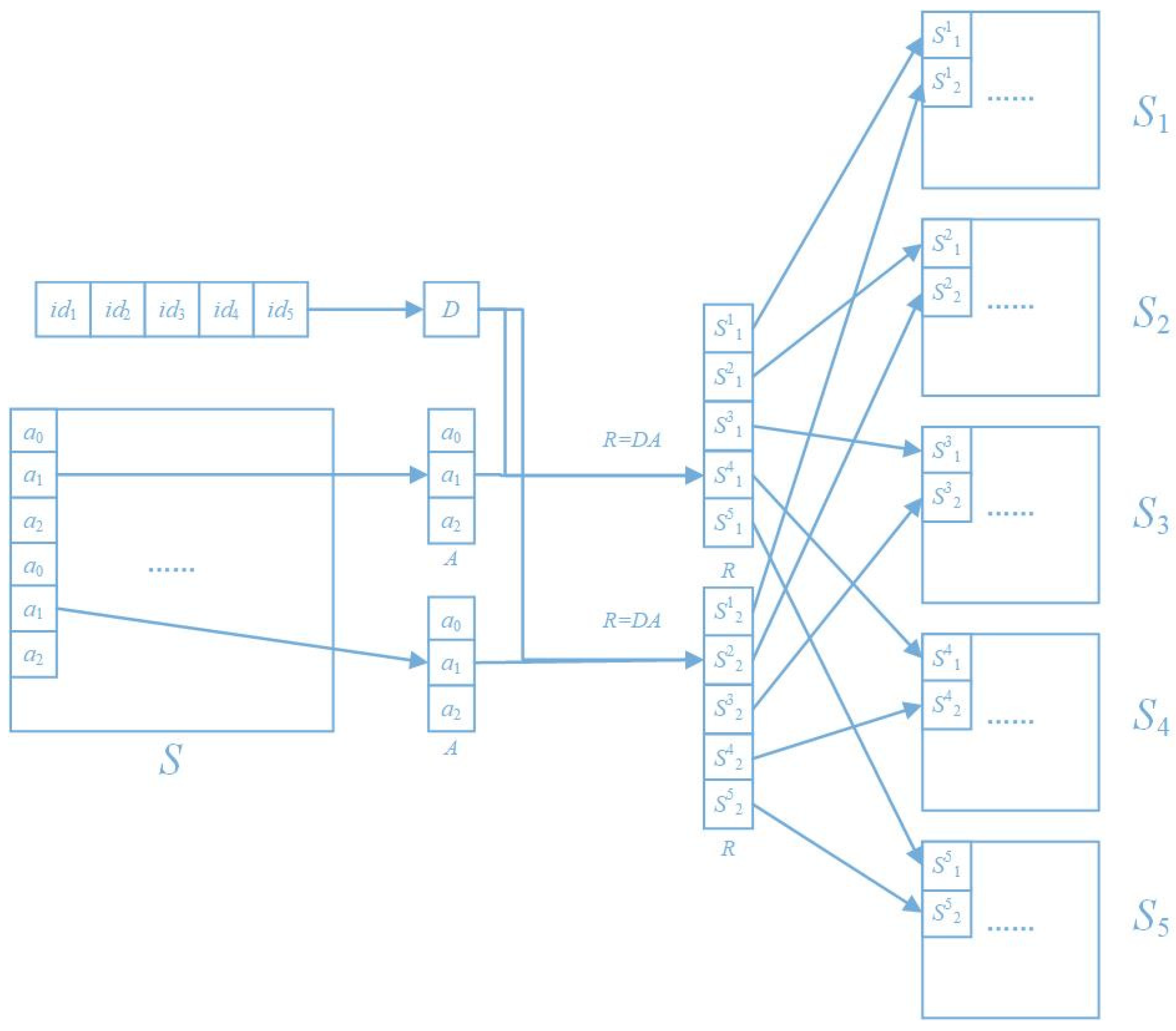
3. Implementation of SIS with Matrix Operation
3.1. Motivation
3.2. Agrithm of Secret Image Sharing Scheme with Matrix Operatio n
| Algorithm 3 Image secret sharing algorithm based on matrix operations |
| Input: S; id1, id2, … , idn Output: S1, S2, … , Sk |
| Step1: Construct matrix D from (8). Step2: Let j = 1 Step3: Select the k pixels from k(j−1) + 1 to k(j−1) + k in S and assign a0, a1, … , ak−1 to each pixel Step4: Construct the column vector A and calculate R = DA. Step5: Get S1j, S2j, … , Snj Step6: If j < w/k, let j = j + 1 and jump to Step3; if j = w/k, skip to Step7. Step7: The shadow image S1, S2, … , Sn is obtained by using Si1, Si2, … , Siw/k as the pixel grayscale value of image Si |
| Algorithm 4 Image secret recovery algorithm based on matrix operations |
| Input: id1, id2, …, idk, S1, S2, … , Sk Output: S |
| Step1: The matrix F is obtained by taking out the k rows corresponding to id1, id2, … , idk in the matrix D. Step2: Calculate the inverse matrix F−1 of F according to the method in Section 3.1. Motivation Step3: Denote the jth pixel gray value of Si as Sij and let j = 1. Step4: Construct G = (S1j, S2j, … , Skj)T and compute A = F−1G to obtain the column vector A. Step5: Get a0, a1, … , ak−1 from (9), let Sk(j−1) + 1 = a0, Sk(j−1) + 2 = a0, … , Sk(j−1) + k = ak−1 Step6: If j < w/k, then let j = j + 1 and skip to Step4; if j = w/k, skip to Step7. Step7: Obtain S by using S1, S2, … , Sw. as the pixel gray value of the image S. |
3.3. Example of (3, 3)-SIS
3.3.1. Example of (3, 3)-SIS Scheme in GF (28)
3.3.2. Example of (3, 3)-SIS Scheme in GF (251)
3.4. Computational Efficiency Analysis
3.4.1. Efficiency Analysis of Thien and Lin’s (k, n)-SIS Scheme
3.4.2. Efficiency Analysis of (k, n)-SIS Scheme Based on Matrix Operations
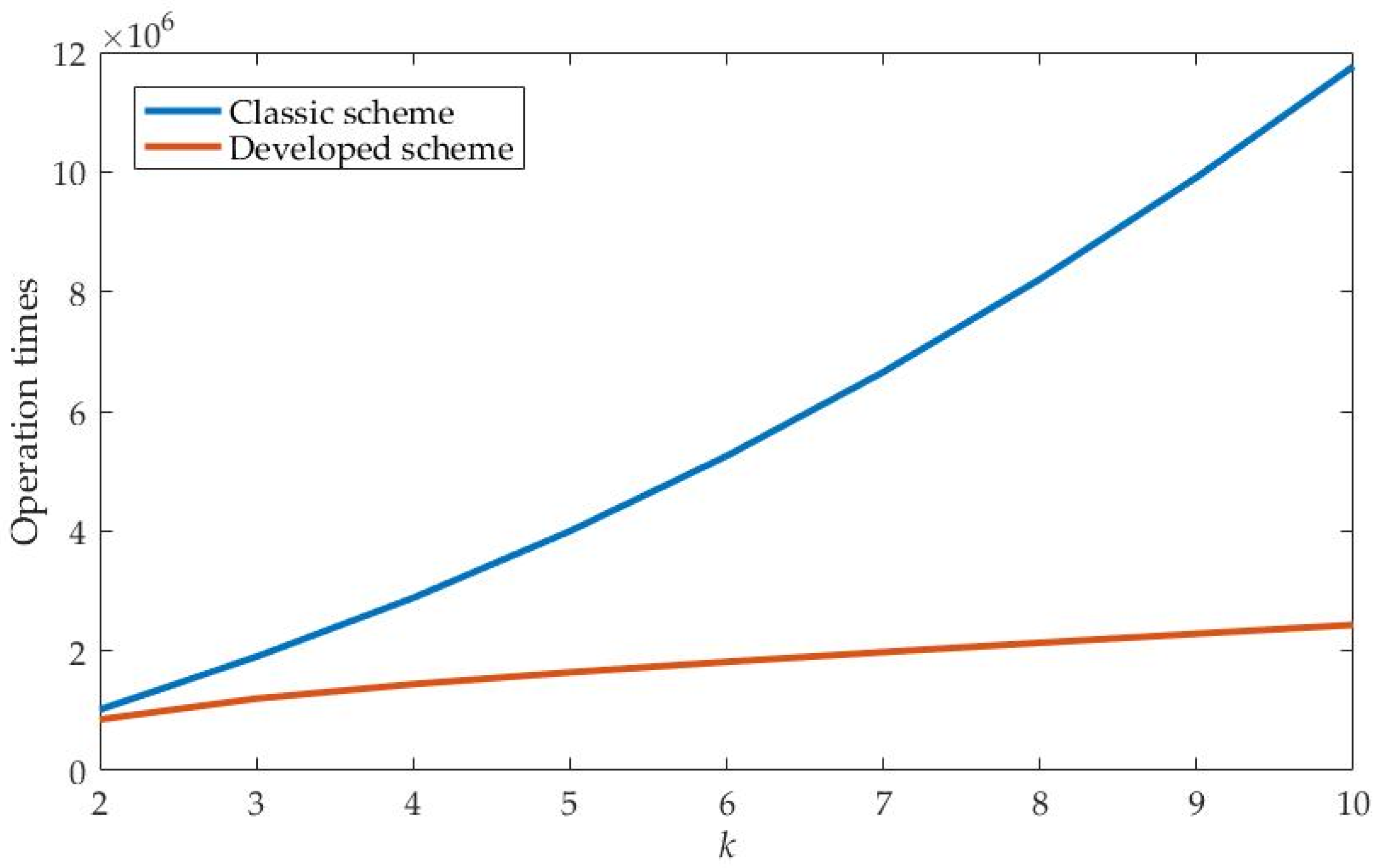
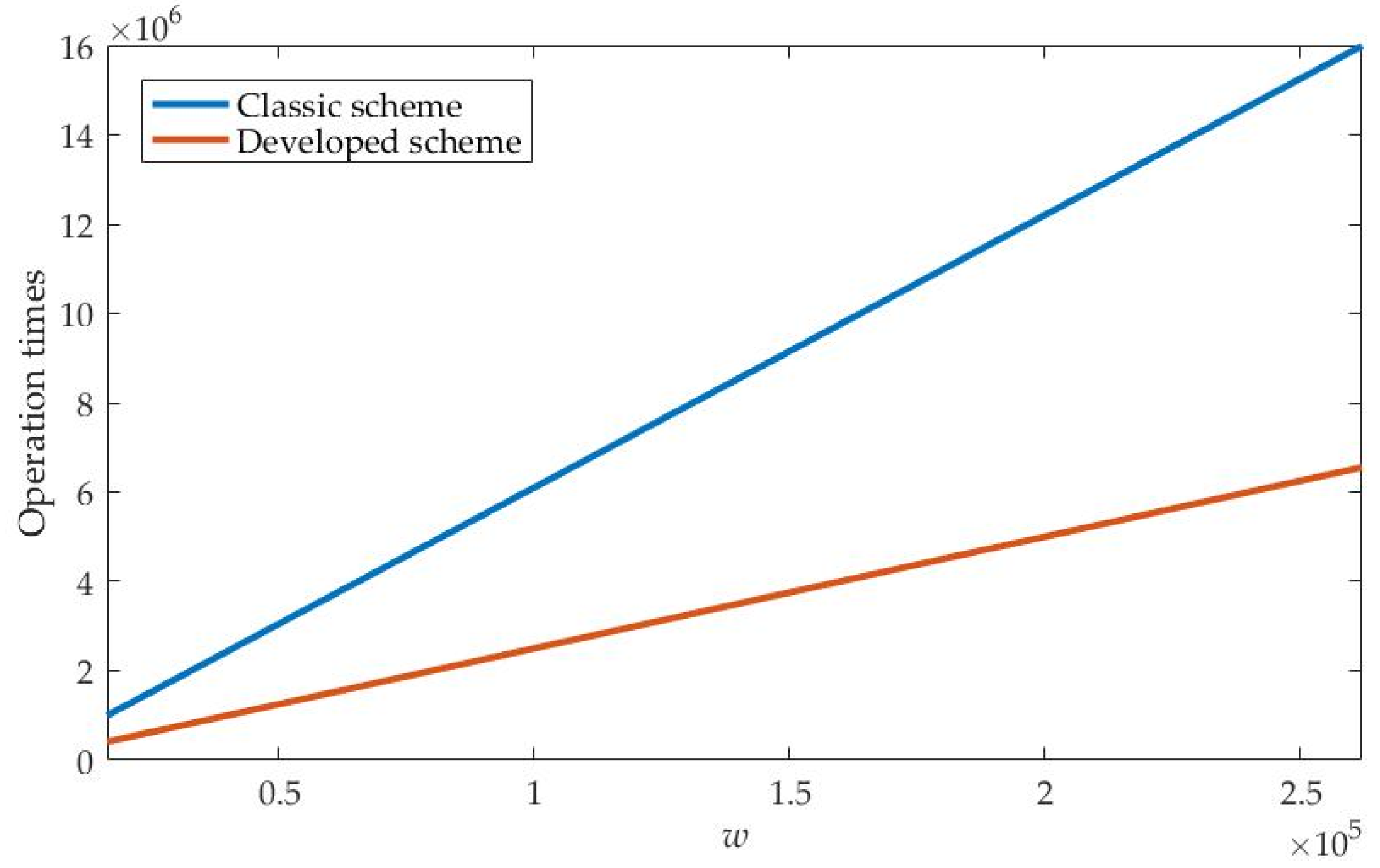
3.4.3. Operation Time Comparison
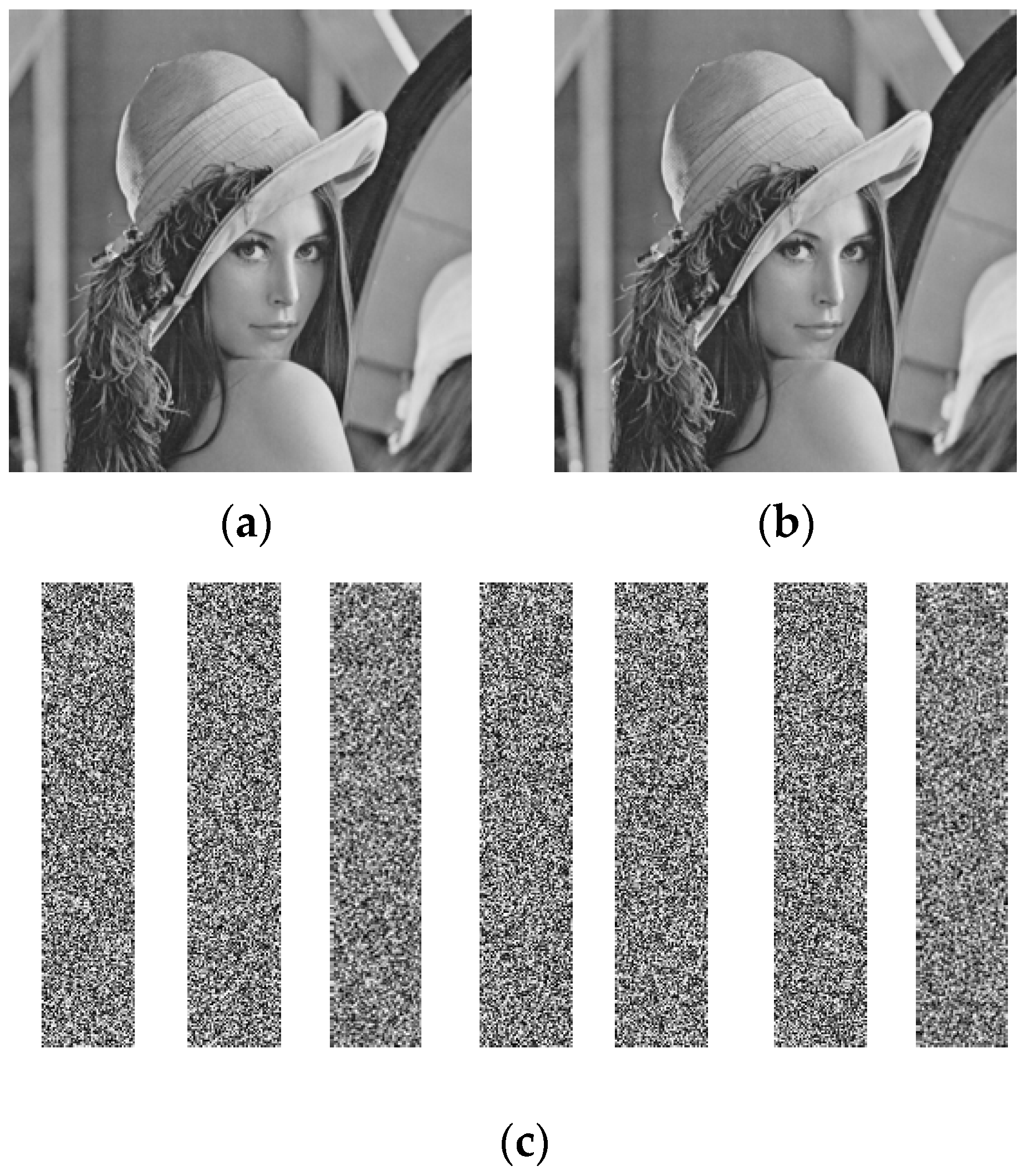
4. Experiments and Comparisons
4.1. Feasibility Experiment of the Implementation Proposed in This Paper
4.2. Comparison Experiment of Computing Efficiency under Different Thresholds
4.3. Comparison Experiments of Computing Efficiency under Secret Image Recovery of Different Sizes
4.4. Analysis of Experimental Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Lin, T. Secret image sharing. Comput. Graph. 2002, 26, 765–770. [Google Scholar]
- Lin, C.C.; Tsai, W.H. Secret image sharing with steganography and authentication. J. Syst. Softw. 2004, 73, 405–414. [Google Scholar] [CrossRef]
- Yang, C.N.; Chen, T.S.; Yu, K.H.; Wang, C.C. Improvements of image sharing with steganography and authentication. J. Syst. Softw. 2007, 80, 1070–1076. [Google Scholar] [CrossRef]
- Ma, K.Y. Essential secret image sharing scheme with different importance of shadows. J. Vis. Commun. Image Represent. 2013, 24, 1106–1114. [Google Scholar]
- Yan, X.; Wang, S.; Niu, X.; Yang, C.N. Essential Visual Cryptographic Scheme with Different Importance of Shares; Springer International Publishing: Berlin/Heidelberg, Germany, 2014. [Google Scholar]
- Chen, C.C. Essential Secret Image Sharing Scheme. In Proceedings of the CSCIST 2010, CrossStrait Conference on Information Science and Technology, Qinhuangdao, China, 9–13 July 2010; Department of Information Management, Hsuan Chuang University: Hsinchu, Taiwan, 2010. [Google Scholar]
- Li, P.; Liu, Z. An Improved Essential Secret Image Sharing Scheme with Smaller Shadow Size. Int. J. Digit. Crime Forensics 2018, 10, 78–94. [Google Scholar] [CrossRef] [Green Version]
- Li, P.; Yin, L.; Ma, J. Visual Cryptography Scheme with Essential Participants. Mathematics 2020, 8, 838. [Google Scholar] [CrossRef]
- Yadav, M.; Singh, R. Essential secret image sharing approach with same size of meaningful shares. Multimed. Tools Appl. 2021, 2021, 1–18. [Google Scholar] [CrossRef]
- Yuan, L.; Li, M.; Guo, C.; Hu, W.; Luo, X. Secret Image Sharing Scheme with Threshold Changeable Capability. Math. Probl. Eng. 2016, 2016, 9576074. [Google Scholar] [CrossRef] [Green Version]
- Liu, Y.X.; Yang, C.N.; Wu, C.M.; Sun, Q.D.; Bi, W. Threshold changeable secret image sharing scheme based on interpolation polynomial. Multimed. Tools Appl. 2019, 78, 18653–18667. [Google Scholar] [CrossRef]
- Deshmukh, M.; Nain, N.; Ahmed, M. An (n, n)-Multi Secret Image Sharing Scheme Using Boolean XOR and Modular Arithmetic. In Proceedings of the IEEE International Conference on Advanced Information Networking & Applications, Crans-Montana, Switzerland, 23–25 March 2016. [Google Scholar]
- Singh, N.; Tentu, A.N.; Basit, A.; Venkaiah, V.C. Sequential secret sharing scheme based on Chinese remainder theorem. In Proceedings of the 2016 IEEE International Conference on Computational Intelligence and Computing Research (ICCIC), Chennai, India, 15–17 December 2016. [Google Scholar]
- Rajput, M.; Deshmukh, M. Secure (n, n + 1)-Multi Secret Image Sharing Scheme Using Additive Modulo. Procedia Comput. Sci. 2016, 89, 677–683. [Google Scholar] [CrossRef] [Green Version]
- Deshmukh, M.; Nain, N.; Ahmed, M. A Novel Approach for Sharing Multiple Color Images by Employing Chinese Remainder Theorem. J. Vis. Commun. Image Represent. 2017, 49, 291–302. [Google Scholar] [CrossRef]
- Basit, A.; Kumar, N.C.; Venkaiah, V.C.; Moiz, S.A.; Tentu, A.N.; Naik, W. Multi-stage Multi-secret Sharing Scheme for Hierarchical Access Structure. In Proceedings of the International Conference on Computing, Communication and Automation (ICCCA2017), Greater Noida, India, 5–6 May 2017. [Google Scholar]
- Meng, K.; Miao, F.; Huang, W.; Xiong, Y. Tightly coupled multi-group threshold secret sharing based on Chinese Remainder Theorem. Discret. Appl. Math. 2019, 268, 152–163. [Google Scholar] [CrossRef]
- Bisht, K.; Deshmukh, M. A novel approach for multilevel multi-secret image sharing scheme. J. Supercomput. 2021, 77, 12157–12191. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, C.N. Scalable secret image sharing scheme with essential shadows. Signal Process. Image Commun. 2017, 58, 49–55. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, C.; Wang, Y.; Zhu, L.; Ji, W. Cheating Identifiable Secret Sharing Scheme Using Symmetric Bivariate Polynomial. Inf. Sci. 2018, 453, 21–29. [Google Scholar] [CrossRef]
- Liu, Y.; Sun, Q.; Yang, C.N. (k, n) secret image sharing scheme capable of cheating detection. Eurasip J. Wirel. Commun. Netw. 2018, 2018, 72. [Google Scholar] [CrossRef] [Green Version]
- Yan, X.; Gong, Q.; Li, L.; Yang, G.; Lu, Y.; Liu, J. Secret image sharing with separate shadow authentication ability. Signal Processing Image Commun. 2019, 82, 115721. [Google Scholar] [CrossRef]
- Gutub, A.; Al-Juaid, N.; Khan, E. Counting-based secret sharing technique for multimedia applications. Multimed. Tools Appl. 2019, 78, 5591–5619. [Google Scholar] [CrossRef]
- Strang, G. Matrices and Gaussian Elimination. In Linear Algebra and Its Applications, 4th ed.; Thomson Learning: Stamford, CT, USA, 2005; pp. 52–53. [Google Scholar]

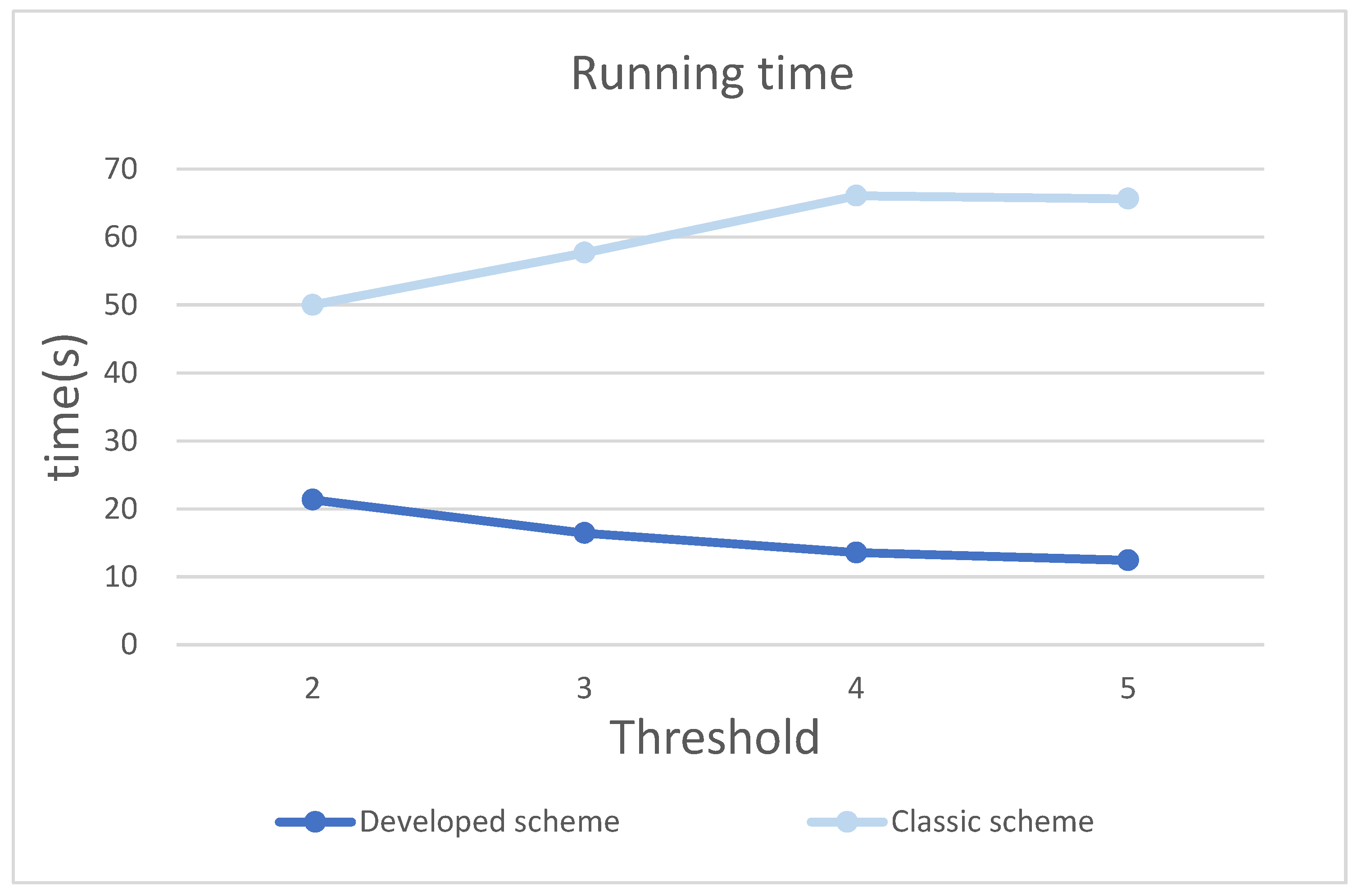


| Threshold k = 2 | Threshold k = 3 | Threshold k = 4 | Threshold k = 5 | |
|---|---|---|---|---|
| Developed scheme Running time (second) | 21.3185 | 16.4230 | 13.5538 | 12.4131 |
| Classic scheme Running time (second) | 50.0028 | 57.6745 | 66.0707 | 65.6301 |
| Threshold k = 2 | Threshold k = 3 | Threshold k = 4 | Threshold k = 5 | |
|---|---|---|---|---|
| Developed scheme Running time (second) | 0.3453 | 0.2960 | 0.2448 | 0.2524 |
| Classic scheme Running time (second) | 0.4062 | 0.3633 | 0.3287 | 0.3622 |
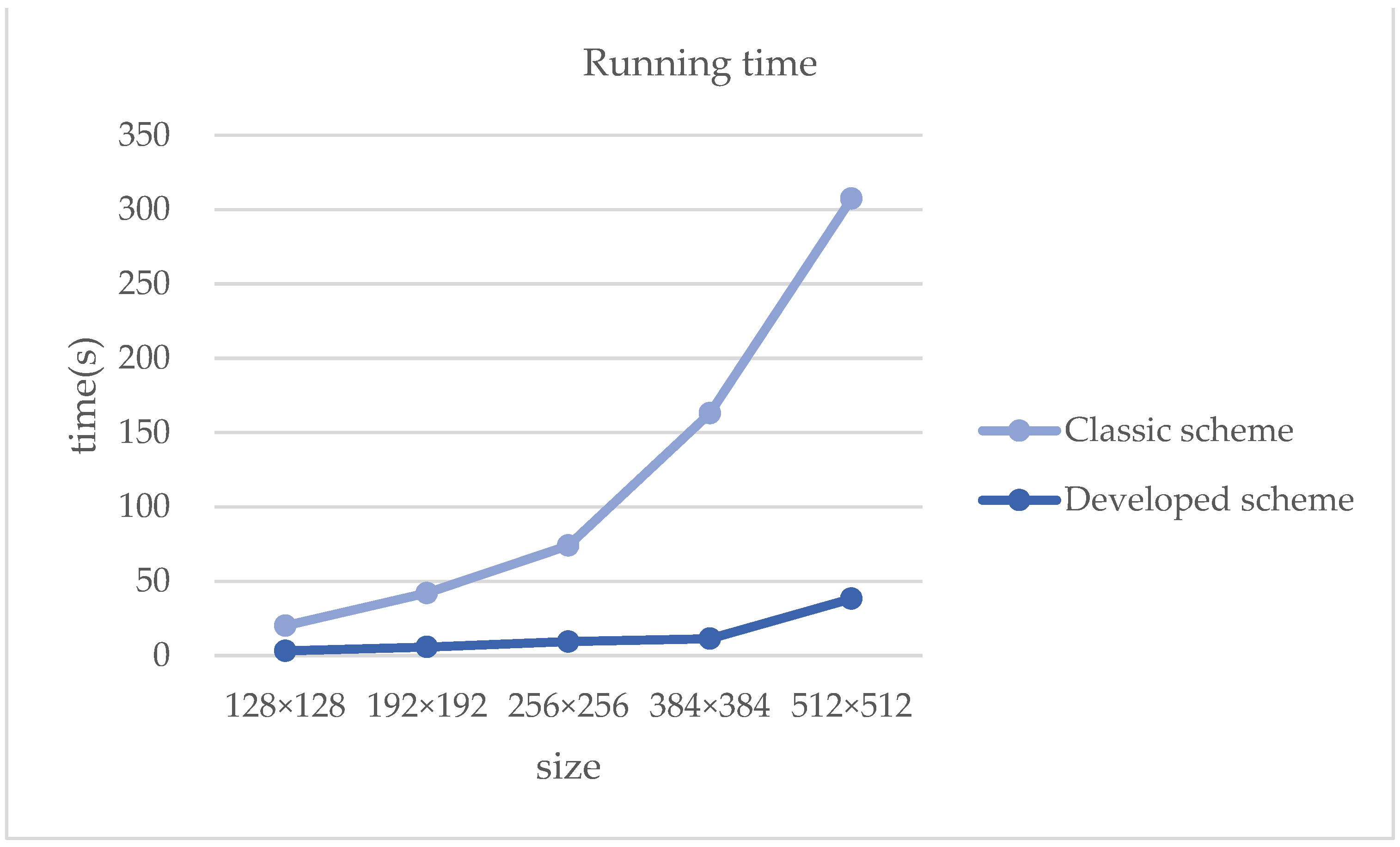
| Secret Image Size 128 × 128 | Secret Image Size 192 × 192 | Secret Image Size 256 × 256 | Secret Image Size 384 × 384 | Secret Image Size 512 × 512 | |
|---|---|---|---|---|---|
| Developed scheme Running time (second) | 3.1263 | 5.7193 | 9.3425 | 11.3432 | 38.2335 |
| Classic scheme Running time (second) | 16.9145 | 36.3079 | 64.6712 | 151.6507 | 269.1568 |
| Secret Image Size 128 × 128 | Secret Image Size 192 × 192 | Secret Image Size 256 × 256 | Secret Image Size 384 × 384 | Secret Image Size 512 × 512 | |
|---|---|---|---|---|---|
| Developed scheme Running time (second) | 0.1517 | 0.1778 | 0.2208 | 0.3558 | 0.5600 |
| Classic scheme Running time (second) | 0.2008 | 0.2203 | 0.4060 | 0.5803 | 0.9693 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ren, Z.; Li, P.; Wang, X. An Implementation of Image Secret Sharing Scheme Based on Matrix Operations. Mathematics 2022, 10, 864. https://doi.org/10.3390/math10060864
Ren Z, Li P, Wang X. An Implementation of Image Secret Sharing Scheme Based on Matrix Operations. Mathematics. 2022; 10(6):864. https://doi.org/10.3390/math10060864
Chicago/Turabian StyleRen, Zihan, Peng Li, and Xin Wang. 2022. "An Implementation of Image Secret Sharing Scheme Based on Matrix Operations" Mathematics 10, no. 6: 864. https://doi.org/10.3390/math10060864
APA StyleRen, Z., Li, P., & Wang, X. (2022). An Implementation of Image Secret Sharing Scheme Based on Matrix Operations. Mathematics, 10(6), 864. https://doi.org/10.3390/math10060864






