1. Introduction
This paper aims to analyze the security of the Proof-of-Proof (PoP) protocol described in [
1]. The primary purpose of this protocol is to strengthen any “light” blockchain–blockchain, where blocks are created with small Proof-of-Work (PoW), but it may also be applied to blockchains with arbitrary consensus protocols to increase their security by binding to a blockchain, which is provably secure.
Note that block intensity generation may be relatively high for blockchains with “small” PoW, so transactions are processed quicker than in a classical “heavy” and secure blockchain. However, it is known that the security of blockchain (for example, against double-spend attacks) decreases when block intensity generation increases. According to various estimates, the number of transactions per second is expected to range from 3 to 7 for the secure BTC blockchain, with the desired speed of up to several thousand. We can say that such “light” blockchains increase throughput and lose out in security. This is the case when the PoP protocol can be used to provide a sufficient level of security for such “light” blockchains with high throughput (or even for blockDAG, but after some significant modification). In other words, it helps to solve one of the main problems of blockchains—the low network throughput.
In the available literature, we can find a plethora of different suggestions for increasing the throughput. These suggestions can be roughly divided into two types:
The first type includes papers [
2,
3,
4,
5,
6]. The authors of these papers announce improvements in both throughput and latency until the transaction is fully confirmed. However, none of these papers contains rigorous proofs of the stated results, semiempirical explanations are, at best, what they provide. Some of them also have serious mathematical errors (for example, refs. [
2,
3,
4,
5]).
Papers of the second type [
7,
8,
9,
10] contain more substantiated statements and more rigorous proofs. However, they solve only one of the existing problems—increasing the throughput. The second currently remains unresolved.
The main idea of the second type of papers is that, in addition to the classic “secure and stable” blockchain (with “slow” block generation, with liveness and consistence properties), which is called MainChain (MC), one can generate additional “separate” blocks or even blockchains that can be produced as quickly as you like (with minimal PoW or Proof-of-Stake (PoS)). Here, we will call such blockchains SideChains (SCs), though they may also have other names (parachain, fruitchain, and so on). SC blocks can refer to each other and to the MainChain. MC blocks (or some of them) may refer directly to SC blocks or may contain some information about a recent SC block, which can be considered as some type of reference.
The SC block B is considered stable (i.e., such that its transactions are irreversible with a probability close to 1) if it is referenced by any stable block of the MC blockchain. That is, the stabilization of a SC block is still a consequence of stabilizing the corresponding block from the MC. Therefore, the time until the block stabilizes remains long.
The PoP protocol suggested in [
1] can also be classified as a type 2 blockchain, but its main difference from the protocols indicated in [
7,
8,
9,
10,
11] is that it uses a “foreign” blockchain as an MC (for instance, BTC blockchain). In this case, there should be a “two-way” communication with the blockchains (i.e., references).
The Veriblock (VB) blockchain with PoP consensus refers to blocks from the MC, and the MC must, at certain limited intervals, refer to the VB. The blockchain that is the is called a security-provided blockchain (SP blockchain) and the VB blockchain is called a security-inherited blockchain (SI blockchain). This protocol increases the throughput (i.e., tps) significantly, but the transaction confirmation time is still fully determined by the “slow” SP blockchain. In addition to this, the VB blockchain itself can act as SP-blockchain for other, different blockchains.
In what follows, we give a short description of the main features of the PoP protocol and then analyze in more detail the procedure of achieving security in this protocol.
We also emphasize that it is essential to consider block synchronization time or time delay for block sharing in security analysis. The importance of this parameter was shown in many works, mainly [
12,
13,
14,
15]. Notably, it was shown that if the adversary is well synchronized and honest miners are not, the security threshold (the minimal ratio of adversary, which can attack the blockchain with probability 1 despite the number of confirmation blocks) decreases dramatically. For example, as it was shown in [
14], for Bitcoin, if the block synchronization time is 20 s and
, the security threshold is about
; if the block synchronization time is 60 s, the security threshold is about
. It means that if the ratio of an adversary is not less than
or
, respectively, his attack will be successful with probability 1 and it cannot be prevented with a large number of confirmation blocks. When the adversary’s ratio is smaller than this security threshold, we need to increase the number of confirmation blocks (in comparison with the case of zero synchronization time) to achieve the same security level.
Our security analysis in this work assumes that the synchronization time is non-zero and upperbound with some known value. For example, for the BTC blockchain, the most widely used assumption is that the synchronization time is up to 20 s. We obtain additional confirmation of the non-zero synchronization time in BTC from its regular “forks”, which occurs about 6 times in a month, on average. Thus, such forks (without a doublespend attack) occur when two different mining pools create blocks (of the same height) within a time delay interval.
Of course, we cannot state that time delay is essentially large all the time, but since we cannot define or predict the period when it really is essentially large, it is better to assume that the synchronization time is non-zero all the time in order to guarantee security in the worst case.
The main contribution of this work is the proving of explicit expressions, obtained for model with non-zero time delay, for the calculation of the number of confirmation blocks, which is enough for block stabilization in the SI blockchain. In particular, our results give the following possibilities:
To calculate the probability of double spend attack for given network parameters (block generation intensity, time delay for block sharing) and given number of blocks generated after the block with transaction (the number of so-called confirmation blocks);
Given the network parameters and preset (small) probability, to calculate the number of confirmation blocks which guarantees that the probability of double spend attack is not larger than the preset value.
This results are completely new to the realistic model with non-zero time delay. Some known results for synchronous model may be also derived from setting the time delay equal to zero.
2. Materials and Methods
In this section, we first explain the basic idea behind the PoP protocol, as well as some of the details and specifications of this protocol given in [
1]. Next, some of the auxiliary statements that are necessary for obtaining the key result are proved. The main result is Theorem 1, which gives the possibility to calculate the required number of confirmation blocks in the SI blockchain, guaranteeing (with overwhelming probability) the stability of a certain block in it.
2.1. PoP Consensus Protocol
The PoP protocol uses the properties of the SP blockchain (liveness, consistence) to provide similar properties to the SI blockchain. Hereinafter, we will assume that the SP blockchain is BTC, and the SI blockchain is VB.
In the SI blockchain, each subsequent block refers to several previous ones according to a specific rule, depending on the parameters of the network.
We introduce the concept of keystone block in order to set the link rule. In addition to this, two parameters related to the SI blockchain and one parameter related to the SP blockchain are set.
The keystone block is every ith block, where is the so-called keystone interval. Each new block in the SI blockchain refers to the previous block, and the r of the last keystone blocks, where is the number referenced keystones.
Therefore, each block contains a reference to r or of keystone blocks —if the block comes immediately after the keystone block).
The VB paper says that each block always refers to precisely i of keystone blocks (table on page 22). However, the second table on page 23 provides an example that contradicts the statement on page 22 but agrees with our statement (that refers to r or of keystone blocks).
We want to emphasize that two parameters i and r relate only to the SI blockchain.
The third parameter, d, relates to the SP blockchain. It shows that, to maintain the validity of the SI blockchain, the interval between references to new keystone blocks does not exceed d of blocks in the SP blockchain, i.e., if at some point, a block number l in the SP blockchain refers to a keystone block number k in the SI blockchain, then no later than in a block number in the SP blockchain, a link to th keystone block should appear.
2.2. Achieving Stability in the SI Blockchain
Informally speaking, the idea to achieve stability in the SI blockchain using stability in the SP blockchain can be described as follows: block B in the SI blockchain is stable if the block in the SP blockchain is stable, where is the first block in the SP blockchain that refers to the block B. In other words, in order to “cancel” block B in the SI blockchain, one needs to perform a long enough fork not only in the SI blockchain, but also in the SP blockchain, which is an arduous computational task. To provide some numerical characteristics to “stability”, the concepts of N-BTC-References and N-BTC-Finality are introduced. The first of them, N-BTC-References, means that after block in the SP blockchain, N blocks have already been created, and if an attacker begins to build an alternative branch in the SI blockchain, in which block B is absent, then a necessary condition for its validity is the appearance of reference to its blocks in the SP blockchain. In the paper, this is called an “early attack detection metric”. That is, if after block in the SP blockchain N blocks have already been released, and there are no references to the alternative chain in them, then this alternative chain does not exist (someone might have started building it, but now it has lost its validity).
The N-BTC-Finality term means that N blocks after block have already been created in the SP blockchain, and this amount is sufficient to guarantee the stability of block with a probability almost indistinguishable from 1. Please note that this probability depends on three parameters: the intensity of block generation (for BTC, it is ), the ratio of the attacker’s hash rate, and the network synchronization time (that is, the block propagation delay time).
That is, the main idea of achieving stability in the SI blockchain can be described as follows:
We wait until block appears in the SP blockchain with reference to block B from the SI blockchain;
After this moment, we wait for the creation of N blocks after block , where the value N is determined by the above parameters of the SP blockchain (block generation intensity, the ratio of the attacker’s hash rate, network synchronization time), as well as the desired probability value, which we choose ourselves.
At the same time, the N-BTC-References parameter is intermediate. It simply allows to detect an attack at an early stage but does not guarantee the impossibility of a fork in the SP blockchain with the required (set by us) probability.
The above idea of achieving stability in a “light” blockchain using some other ”heavy and stable” blockchain is proposed (by the authors of [
1]) to be generalized and developed further, with the possibility of using not only for the VeriBlock blockchain, but also for any existing altcoin. In this case, the VeriBlock blockchain already acts as an SP blockchain, and the altcoin blockchain, respectively, is an SI blockchain. In this case, to characterize the degree of stability achievement, by analogy, the following parameters are used:
N-BTC-References;
N-BTC-Finality;
N-VBK-References;
N-VBK-Finality.
2.3. Correlation of the Number of Blocks Created in Different (Independent) Blockchain
A measure of block stability in the blockchain is usually the number of blocks created after it, provided there is no visible fork in this interval. For a splitting attack, at the moment, no working (non-asymptotic) estimates of the attack probability have been obtained, depending on the block depth, for a model with continuous time. For a double spend attack, such estimates were obtained for various mathematical models (with continuous time [
12,
14,
15,
16] and with discrete [
15]; without taking into account the block synchronization time [
16] and taking it into account [
12,
13,
14,
15]). Although it is not completely clear from [
1], it can be reasonably assumed that the authors used the same quantitative characteristic to guarantee the stability of a block in the SI blockchain. Informally speaking, the reasoning is roughly as follows.
Let us assume that block is the first block in the SP blockchain that refers to a block B from the SI blockchain. Then, provided that there are no references to some alternative branch of the SI blockchain in the blocks following the block , to build this alternative branch of the SI blockchain, you need to fork the SP blockchain, that is, build its alternative branch in which there is no block . The greater the depth block is, the smaller the probability is to create such an alternative branch that will be longer than the existing one. Moreover, we ourselves can set the value of such a probability and, accordingly, choose the block depth in the SP blockchain, which guarantees that the probability of a fork will be no more than a given value. For example, for the probability of a fork to be no more than a certain small , we just need to build n blocks after the block . After these blocks are created, the probability of removing the B block from the SI blockchain also does not exceed . We do not want to look into the SP blockchain every time to check how many blocks there are, and we want to estimate the probability of a fork only by the number of blocks generated in the SI blockchain. Then, we set a small and determine value k such that the probability of the event {not less than the blocks that occur during the time when n SI blocks occur} is not less than . With the obtained value k, the probability of removing block B from the SI blockchain will not be larger than . That is, initially, we set the desired upper bound on the fork probability and then we determine values n and k in a such way that the corresponding sum is not larger than .
The paper provides formulas that are auxiliary for calculating the probability of event (page 11, 12, and on). These formulas correspond to the probabilities of exponential and inverse binomial distributions. They are correct if the following conditions are met with regard to the considered SP blockchain and SI blockchain:
The synchronization time in both blockchains is zero, that is, after creating a block, all nodes instantly see it;
Both blockchains use the PoW consensus protocol.
If at least one of these conditions is violated, then the basic formulae for calculating the probability of creation of exactly k blocks in one blockchain during the time until n blocks are created in another blockchain will be completely different.
In our analysis given below, we get rid of the first assumption and build correspondent probability estimations for the blockchains with non-zero synchronization time bounded with some arbitrary value.
2.4. Main Assumptions, Designations, and Some Auxiliary Statements
In this section, we describe the basic assumptions of our model and introduce the main designations. Sometimes, we will also refer to some statements proved in [
16].
We will use SP blockchain for “Security provided blockchain” and SI blockchain for “Security inherited blockchain”. Let us define the following random variables (RVs):
—the RV that is measuring the time it takes to mine a block in the SP blockchain,
—the RV that is measuring the time it takes to mine and share the block in the SP blockchain,
—the RV that is measuring the time it takes to mine a block in the SI blockchain,
—the RV that is measuring the time it takes to mine and share the block in the SI blockchain.
As shown in [
16], RVs
and
have exponential distributions:
for some
. The physical sense of these two parameters is that
and
are the mean rates of block generation in the SP blockchain and SI blockchain, correspondingly. Define
.
We also assume that denotes the time it takes in the SP blockchain to share a block (after it was generated) for all nodes in the network. The value is the corresponding time in the SI blockchain. In this very work, we assume that . The reasons for this assumption are as follows:
From a security consideration, it is critical that we can guarantee (with a probability close to 1) that during the time of the generation of a certain number of blocks in the SI blockchain, at least a certain number of blocks in the SP blockchain are created;
The most “terrible” thing that can happen from this assumption is that we will spend “extra” time waiting for a slightly larger number of confirmation blocks in the SI blockchain than is necessary to achieve the declared security, as a result of which, the obtained security will be somewhat higher than the declared one;
Under the assumption that in both blockchains the synchronization time is nonzero, the mathematical model becomes much more complicated, making it almost impossible to obtain the results we need.
Our assumption means that and .
We also should note that, for the sake of simplicity, we assume that the block delay time is the same for all blocks in the SP blockchain. Of course, this is a kind of simplification of the real model, but in an alternative case, it is impossible to take into account all particular time delays. On the other hand, we can consider the largest time delay in the SP blockchain and consider setting the problem “in the worst-case scenario”, that is, when all blocks in the SP blockchain are delivered with the maximum delay. As with the previous assumptions, this also leads to an increase in the blockchain security compared to the declared one.
In these designations, we have
Define
the probability that the next block in the SP blockchain will be generated before the next block in the SI blockchain (i.e., faster than in the SI blockchain), and
is the probability of the opposite event. Using considerations very similar to those in [
16], we obtain
Actually, in our case, we are interested in two other values that take into account the time delay . We introduce these values as follows:
—the probability that the next block in the SP blockchain will be generated and shared before the next block in the SI blockchain will be generated and shared for all nodes;
—the probability of the alternative event, .
According to their definitions,
and also
.
These two values in (4) are much more important than the values in (3) because they take into account time delay and describe the state of the network much more realistically. In what follows, we will show that the relation between the number of blocks in the SP blockchain and the SI blockchain depends on these very values in (4) rather than values in (3). Thus, if is rather large, the “real” hash rate in the SP blockchain is essentially smaller than .
Now we are going to find and .
Lemma 1. In our designations, the next equalities hold: Proof. Note that distribution functions for RVs
and
according to (2) and (4) are
The corresponding densities are
Then, according to the composite probability formula,
However,
, because from (2) we obtain
. So
Next, according to (4) and (6)–(8),
where
.
After integration, we obtain
and from
, we obtain
Respectively, , and the Formulas (5) and the lemma are proved. □
2.5. Main Results
In this section, we formulate our main results after some auxiliary lemmas.
Denote
as the time needed in the SP blockchain to form and share the
i-th block, i.e., the time from the event “
-th block is formed and available for all nodes” till the event ”
i-th block is formed and available for all nodes”. Similar to (2), we can also say that
where
is the time needed in the SP blockchain to generate the
i-th block, after the
-th block becomes available. Then,
, are independent, identically distributed RVs with distribution functions
where the last equality follows from (1).
Additionally, define RVs
, in the same way. Then their distribution functions are
In addition, for
, let us define RVs
, where
and RVs
, where
Then is the time needed to generate (without sharing) n (independent) blocks in the SP blockchain and is the time needed to generate and share n blocks in the SP blockchain, one after another.
From (10), we obtain that
where
has an Erlang distribution as the sum of independent identically distributed RVs with exponential distribution:
Additionally, define RVs
in the same way:
Note that
also has an Erlang distribution:
Let us also define the random process (RP) as the number of blocks generated in the SP blockchain during the time interval of the length t, if the time delay was equal to zero.
Lemma 2. The RP has Poisson distribution with parameter : Proof. The event
is the same as the event
, where
was defined in (11). We can write the subsequent chain of equalities:
Yet, according to the definition
, then, using (15),
The lemma is proved. □
Note that for RV
, defined in the same way, we also have the same statement:
Notation 1. From the properties of the Poison process (independent increments, absence of aftereffects), we get that for anythe distribution law ofis the same as the distribution law ofi.e., the number of events happening duringhas the same distribution law as the number of events happening during. Additionally, note that the number of events happening during the periodis the sum of the numbers of events happening duringand.
We will use this property in the lemma below.
Additionally, introduce RP
as the number of blocks generated and shared (one after another) in the SP blockchain during the time interval of the length
t. Then
Now we can define our purpose as to find, or at least to estimate, the probability
which is the probability of the following event
:
“Not less than
k blocks were generated and shared in the SP blockchain during the time when exactly
n blocks were generated in the SI blockchain (i.e., during the time
)”.
According to our purpose, we need to build lower estimation for
and then, for fixed
k (which corresponds to definite security level
in the SP blockchain) and fixed small
to define
We can also define
as
where
, according to
.
Now, we are ready to formulate our main result about the number of generated blocks.
Proof. Note that we can rewrite
as
because
.
Let us assume that holds. Then, we can define the full group of events as
exactly
blocks out of
blocks in SI blockchain were generated during the interval
,
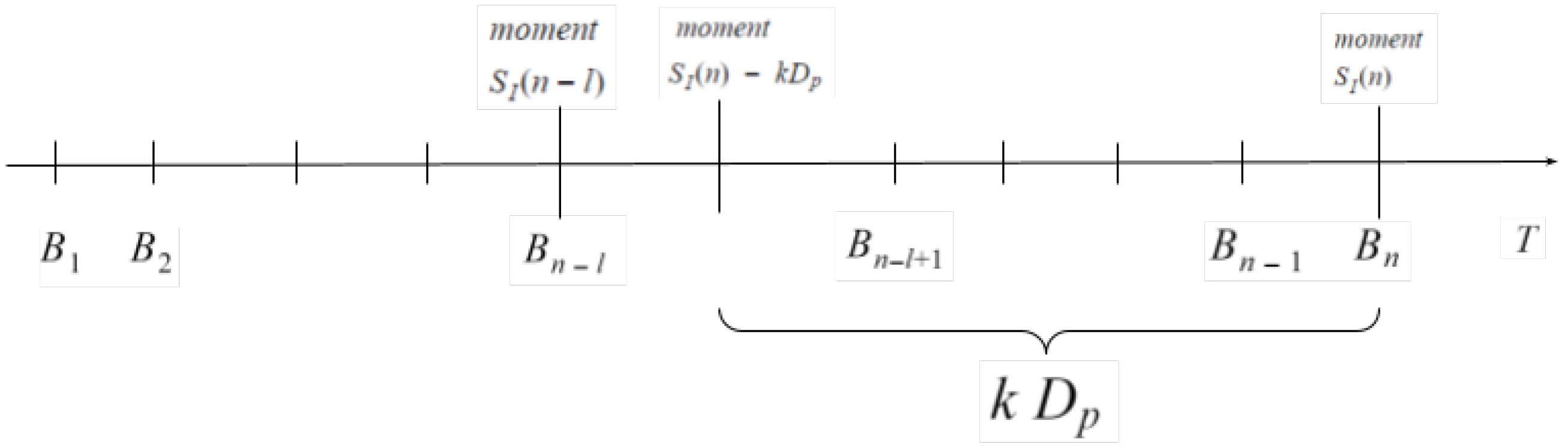
(see
Figure 1).
Note that n-th block was generated exactly at moment
, because of the definition of
. Then, under condition
,
If
doesn’t hold, then
.
Combining these two cases for according to (26) and using (24), we obtain the statement (25) and the theorem is proved.
Note that the expression (25) may also be used as an upper bound of
even in the case when
. Thus, in this case, the first sum of
has only one nonzero term when
. So we have
which is the probability
which is large than
.
Now we give some intuition for how we can use the result of Theorem 1.
Let the block of the deep k in the SP blockchain be considered stable with some overwhelming probability for some sufficiently small ε. Let for the value the next statement hold: □
Statement 1 (related to the number of blocks). “The probability, that during blocks were generated in the SI blockchain, not less than blocks were generated and shared in the SP blockchain, is not less than for some sufficiently small ”.
According to the PoP concept, to guarantee stability in the SI blockchain for some block B with an overwhelming probability for some given sufficiently small , we need to wait for such a number k of blocks in the SP blockchain after the first reference to B, for which Statement 1 is true, with values and such that . Thus, the stability may fail in only two cases: when Statement 1 fails (with probability ) or when stability in the SP blockchain fails (with probability ). Our main task is to find such that for a given sufficiently small and , Statement 1 holds. This is the same as to find such that .
4. Discussion
We analyzed the block stability in the SI blockchain with the PoP consensus protocol and obtained results in a realistic model, with nonzero synchronization time, which are strictly mathematically proved and allow us to build security estimations of the SI blockchain. Using these results, we also can set the desirable security level for the SI blockchain and calculate the necessary number of confirmation blocks in it, which guarantee this security level, based on the SP blockchain like BTC.
The numerical results obtained using the formulas that are in this paper are completely in line with the expectations and show that the probability of an attack in the SI blockchain increases with increasing the synchronization time in the SP blockchain and, accordingly, more confirmation blocks are required for protection against this attack. It should also be taken into consideration that when the block generation intensity in the SP blockchain increases, the probability of an attack will increase faster with increasing synchronization time.
These results may also be useful for building secure Altchains, which use VeriBlock blockchain as the SP blockchain, if both blockchains are based on a Proof-of-Work protocol.
Note that if at least one of these two blockchains—the SI blockchain or SP blockchain—is based on some other protocol, such as Proof-of-Stake, one must use a completely different approach to build security estimations of such blockchains.
The idea behind the PoP protocol, as well as similar ideas from earlier articles mentioned in the review, allows us not only to ensure the resilience of new blockchains that initially have a small PoW value in the block, but also to build security blockchains with high throughput using any of the existing blockchains with provable security. However, it does not solve the second significant problem of blockchains—reducing block confirmation time, i.e., the time until the moment when transactions in the block may be considered uninvertible with overwhelming probability. Maybe the described problem can be solved, at least partially, if we manage to generalize the PoP consensus to the case of SI DAGchain instead of the blockchain. This approach may be the next direction of further investigations.