Computer Science beyond Coding: Partnering to Create Teacher Cybersecurity Microcredentials
Abstract
:1. Challenge in Science Teacher Education
2. The Framework
3. Study and Research Questions
4. Methods and Analysis
5. Findings and Participant Learning
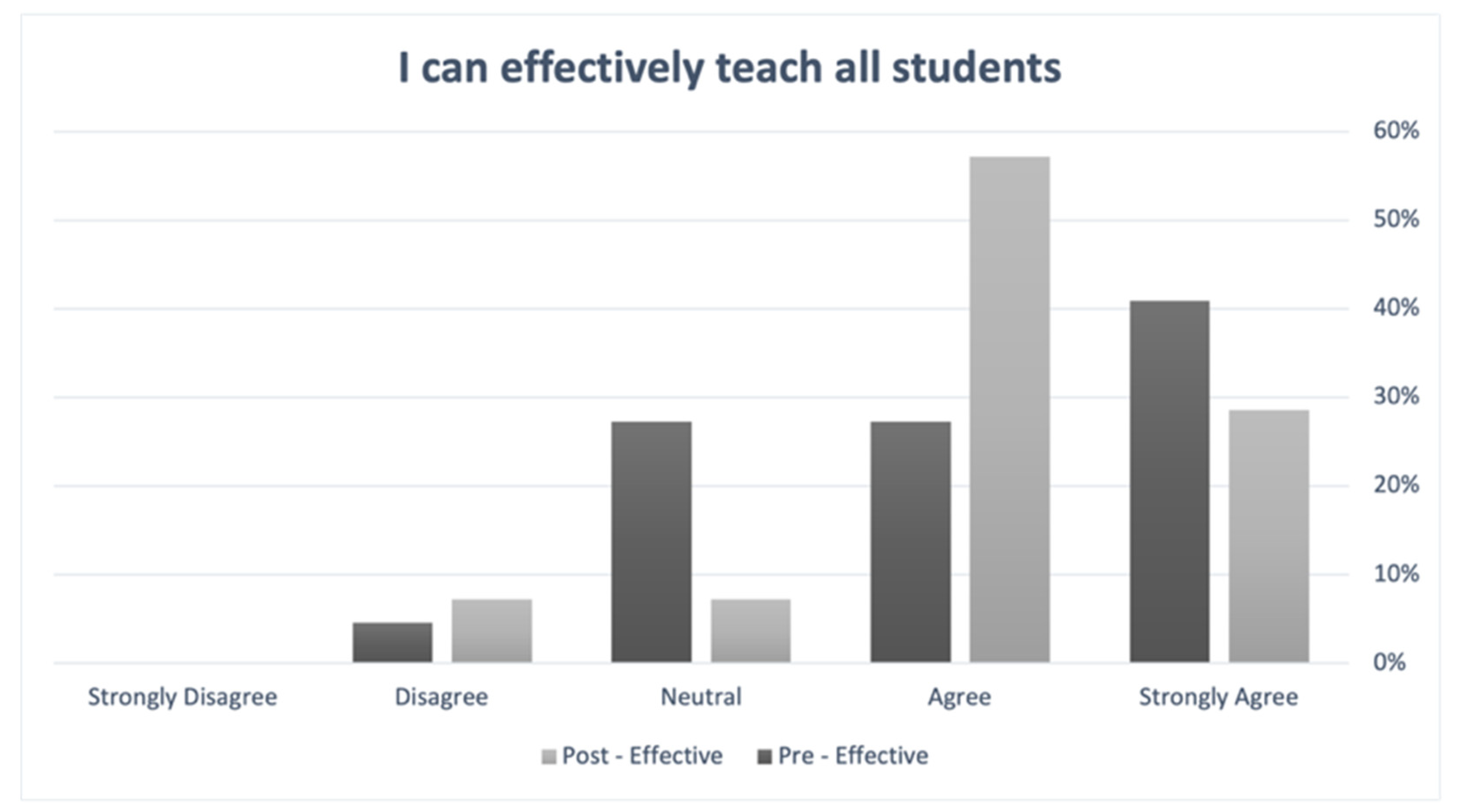
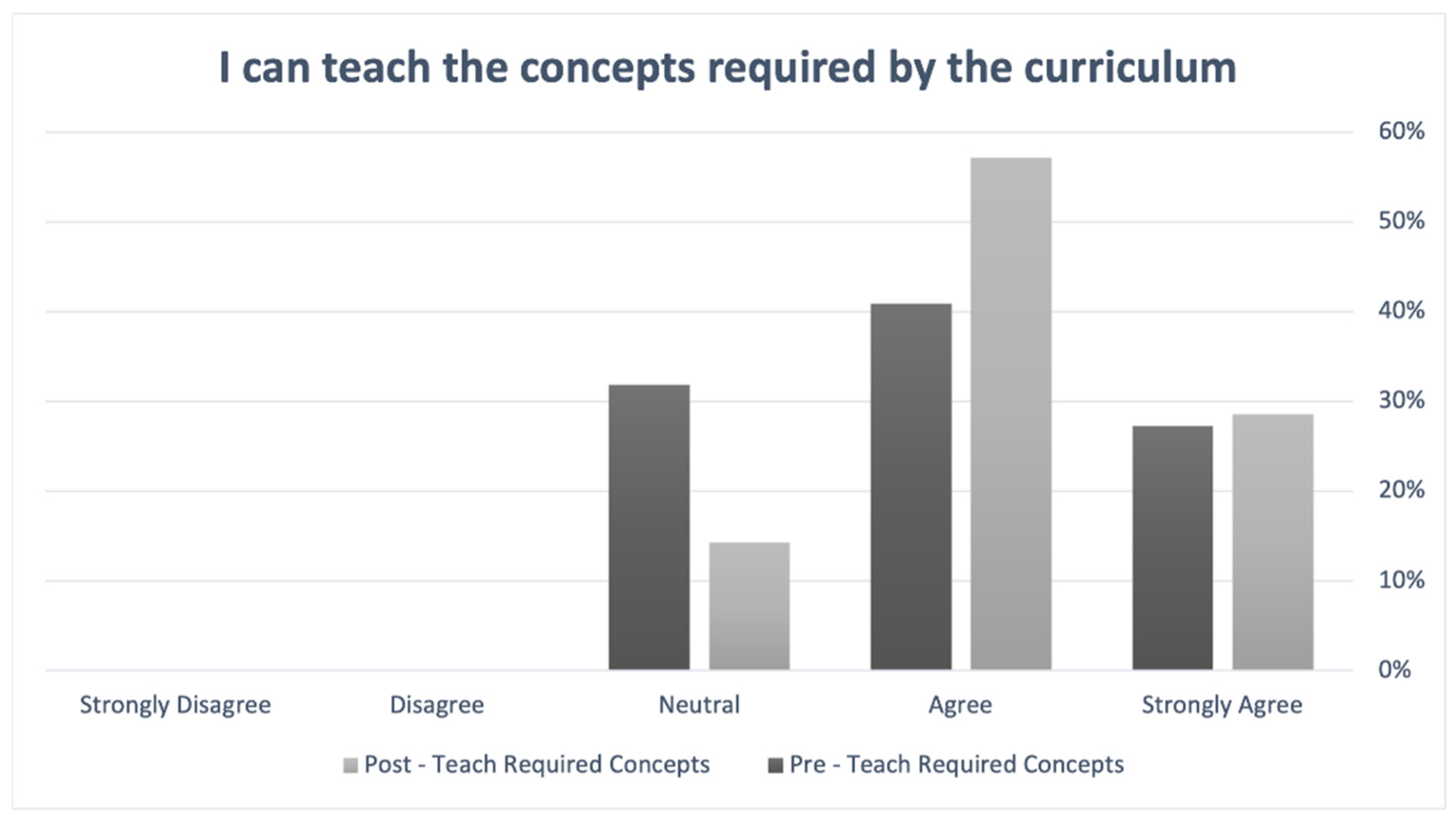
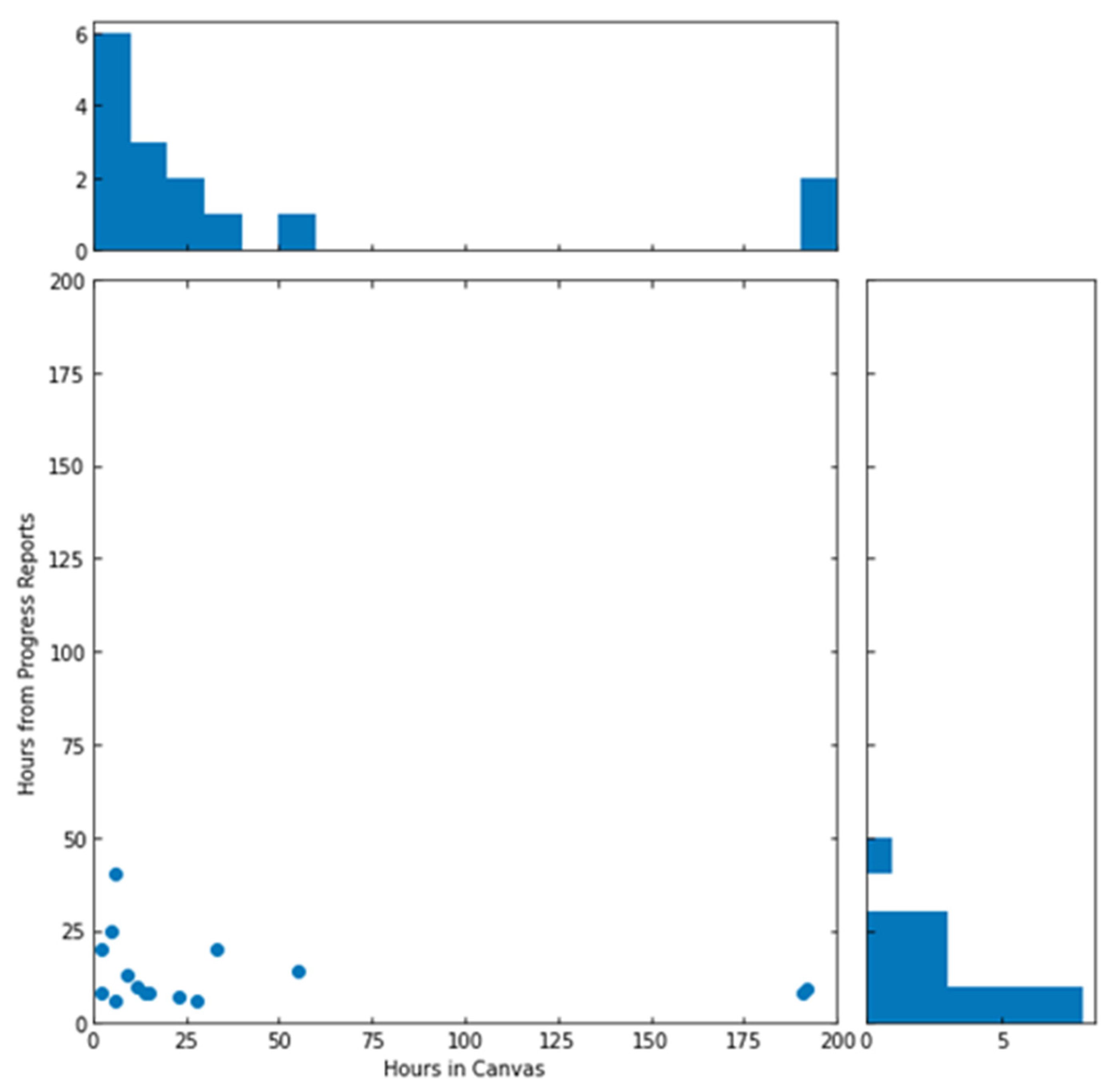
5.1. Quantitative Findings
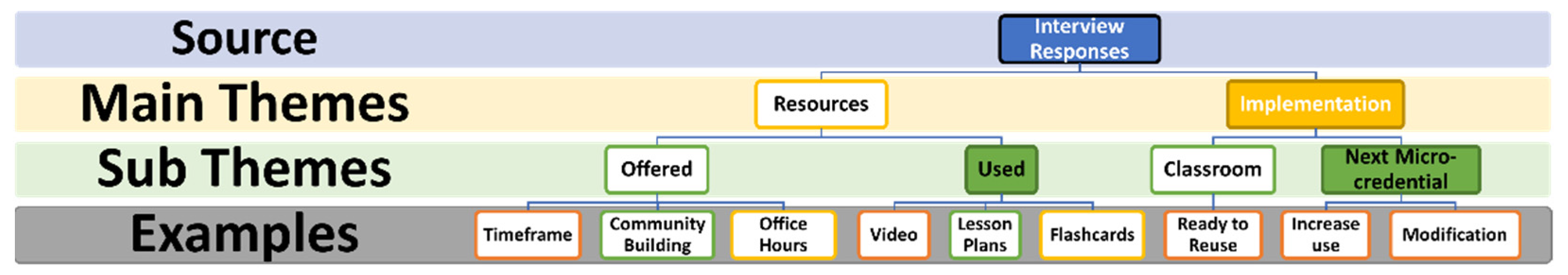
5.2. Qualitative Findings
6. Conclusions and Contributions to STEM Education
- Follow prior recommendations in the literature for online PDs and microcredentials, such as matching PDs to teachers’ backgrounds, aligning the PD with curricula, and using motivational design to enhance teacher engagement [20].
- Focus on creating teacher resources that could be offered to a middle or high school STEM or CS classroom audience, so that the teachers have to make less modifications for use. This includes novice, intermediate, and advanced resources.
- Use resources (such as journal articles and flashcards) that include sample computer-science- or cybersecurity-related unplugged and plugged activities, showing that computer science is more than coding and involves problem-solving. Use shorter readings and videos when possible.
- Identify for the teachers where classroom implementation could be beneficial for students to make disciplinary connections in and beyond STEM.
- Offer support to teachers for classroom implementation, beyond asynchronous support such as email. If traveling to the location is not feasible, then synchronous engagement offers a stronger assistance for sustainable use.
7. Limitations, Future Research, and Implications
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Aefsky, F. COVID19 Pandemic Impact on Education in the United States. Interdisciplinary Insights. J. St. Leo Univ. Coll. Educ. Soc. Serv. 2021, 3, 3–13. [Google Scholar]
- National Academies of Sciences, Engineering, and Medicine. Reopening K-12 Schools during the COVID-19 Pandemic: Prioritizing Health, Equity, and Communities; National Academy Press: Washington, DC, USA, 2020. [Google Scholar]
- Black, E.; Ferdig, R.; Thompson, L.A. Pre-collegiate virtual schooling, COVID-19, and student success. JAMA Pediatrics 2021, 175, 119–120. [Google Scholar] [CrossRef] [PubMed]
- Barnett, B.; Airhart, K.M.; Byrd, P.A. Microcredentials: Teacher learning transformed. Phi Delta Kappan 2016, 98, 34–40. [Google Scholar]
- Bartz, D.E.; Kritsonis, W.A. Micro-Credentialing and the individualized professional development approach to learning for teachers. Natl. Forum Teach. Educ. J. 2019, 29, 1–11. [Google Scholar]
- Brown, D. Research and Educator Micro-Credentials; Digital Promise; 2019; Available online: https://digitalpromise.dspacedirect.org/bitstream/handle/20.500.12265/46/Researcher-And-Educator-Microcredentials-2019.pdf?sequence=1 (accessed on 8 December 2021).
- Lawless, C. Synchronous vs Asynchronous Learning: Which Is Right for Your Learners? LearnUpon. 2020, p. 23. Available online: https://www.learnupon.com/blog/synchronous-learning-asynchronous-learning/ (accessed on 8 December 2021).
- Nieuwoudt, J.E. Investigating synchronous and asynchronous class attendance as predictors of academic success in online education. Australas. J. Educ. Technol. 2020, 36, 15–25. [Google Scholar] [CrossRef]
- Burrows, A.C.; Borowczak, M.; Slater, T.F.; Haynes, C.J. Teaching computer science & engineering through robotics: Science & art form. Probl. Educ. 21st Century 2012, 47, 6–15. [Google Scholar]
- Mugayitoglu, B.; Borowczak, M.; Burrows, A.C. A university’s developmental framework: Creating, implementing, and evaluating a K-12 teacher cybersecurity microcredential course. J. Syst. Cybern. Inform. 2021, 19, 13–22, ISSN: 1690-4524. [Google Scholar]
- Wing, J.M. Computational thinking. Commun. ACM 2006, 49, 33–35. [Google Scholar] [CrossRef]
- Wolf, S.; Burrows, A.C.; Borowczak, M.; Johnson, M.; Cooley, R.; Mogensen, K. Integrated outreach: Increasing engagement in computer science and cybersecurity. Educ. Sci. 2020, 10, 353. [Google Scholar] [CrossRef]
- Burrows, A.C.; Borowczak, M.; Myers, A.; Schwortz, A.C.; McKim, C. Integrated STEM for teacher professional learning and development: “I Need Time for Practice”. Educ. Sci. 2021, 11, 21. [Google Scholar] [CrossRef]
- Johnson, C.C.; Mohr-Schroeder, M.J.; Moore, T.J.; English, L.D. (Eds.) Handbook of Research on STEM Education; Routledge: London, UK, 2020. [Google Scholar]
- Coyne, J.; Hollas, T.; Lane, M.; Ellis, C. Microcredentials: A Promising Professional Development Model for Teacher Leaders. Int. J. Innov. Res. Educ. Sci. 2019, 6, 647–654. [Google Scholar]
- Borowczak, M.; Burrows, A.C. Ants go marching—Integrating computer science into teacher professional development with NetLogo. Educ. Sci. 2019, 9, 66. [Google Scholar] [CrossRef] [Green Version]
- Bers, M.U. Coding as another language: A pedagogical approach for teaching computer science in early childhood. J. Comput. Educ. 2019, 6, 499–528. [Google Scholar] [CrossRef]
- Saxena, A.; Lo, C.K.; Hew, K.F.; Wong, G.K.W. Designing unplugged and plugged activities to cultivate computational thinking: An exploratory study in early childhood education. Asia-Pac. Educ. Res. 2019, 29, 55–66. [Google Scholar] [CrossRef]
- Sun, L.; Hu, L.; Zhou, D. Improving 7th graders’ computational thinking skills through unplugged programming activities: A study on the influence of multiple factors. Think. Ski. Creat. 2021, 42, 100926. [Google Scholar] [CrossRef]
- Gonzalez-Manzano, L.; de Fuentes, J.M. Design recommendations for online cybersecurity courses. Comput. Secur. 2019, 80, 238–256. [Google Scholar] [CrossRef]
- Bhuyan, J.; Wu, F.; Thomas, C.; Koong, K.; Hur, J.W.; Wang, C. Aerial drone: An effective tool to teach information technology and cybersecurity through project based learning to minority high school students in the U.S. TechTrends 2020, 64, 899–910. [Google Scholar] [CrossRef] [PubMed]
- Cavelty, M.D.; Wenger, A. Cyber security meets security politics: Complex technology, fragmented politics, and networked science. Contemp. Secur. Policy 2020, 41, 5–32. [Google Scholar] [CrossRef] [Green Version]
- Kilty, T.; Burrows, A.C.; Welsh, K.; Kilty, K.; McBride, S.; Bergmaier, P. Transcending disciplines: Engaging college students in interdisciplinary research, integrated STEM, and partnerships. J. Tech. Sci. Educ. 2021, 11, 146–166. [Google Scholar] [CrossRef]
- Lambert, J.; Cioc, C.; Cioc, S.; Sandt, D. Making connections: Evaluation of a professional development program for teachers focused on STEM integration. J. STEM Teach. Educ. 2018, 53, 2. [Google Scholar] [CrossRef]
- Kelley, T.R.; Geoffery Knowles, J.; Holland, J.D.; Han, J. Increasing high school teachers self-efficacy for integrated STEM instruction through a collaborative community of practice. Int. J. STEM Educ. 2020, 7, 1–13. [Google Scholar] [CrossRef]
- Qian, Y.; Hambrusch, S.; Yadav, A.; Gretter, S. Who needs what: Recommendations for designing effective online professional development for computer science teachers. J. Res. Technol. Educ. 2018, 50, 164–181. [Google Scholar] [CrossRef]
- Chen, S.; Venkatesh, A. An investigation of how design-oriented organizations implement design thinking. J. Mark. Manag. 2013, 29, 1680–1700. [Google Scholar] [CrossRef]
- Sweeney, L.B.; Meadows, D. The Systems Thinking Playbook: Exercises to Stretch and Build Learning and Systems Thinking Capabilities; Chelsea Green Publishing: White River Junction, VT, USA, 2010. [Google Scholar]
- York, S.; Lavi, R.; Dori, Y.J.; Orgill, M. Applications of systems thinking in STEM education. J. Chem. Ed. 2019, 14, 2742–2751. [Google Scholar] [CrossRef]
- Astaíza-Martínez, A.F.; Mazorco-Salas, J.E.; Castillo-Bohórquez, M.I. Teacher-researcher training in higher education: A systems thinking approach. Syst. Pract. Action Res. 2021, 34, 187–201. [Google Scholar] [CrossRef]
- Patrick, S.; Worthen, M.; Frost, D.; Truong, N. Current to Future State: Issues and Action Steps for State Policy to Support Personalized, Competency-Based Learning; iNACOL: Vienna, VA, USA, 2018. [Google Scholar]
- Ravitz, J.; Stephenson, C.; Parker, K.; Blazevski, J. Lessons from evaluation of computer science teacher professional development in Google’s CS4HS program. ACM Trans. Comput. Educ. 2017, 17, 21. [Google Scholar] [CrossRef] [Green Version]
- Kruger, J.; Dunning, D. Unskilled and unaware of it: How difficulties in recognizing one’s own incompetence lead to inflated self-assessments. J. Personal. Soc. Psychol. 1999, 77, 1121–1134. [Google Scholar] [CrossRef]

| Gender (n = 30) | |||||
|---|---|---|---|---|---|
| Female | 73% | Male | 27% | ||
| Subjects Taught (n = 30) | |||||
| Mathematics | 53% | Science | 47% | Computer Science | 30% |
| Literacy/English | 27% | STEM | 20% | Other | 10% |
| Levels Taught (n = 30) | |||||
| PreK–2 | 27% | 3–5 | 37% | 6–8 | 47% |
| 9–12 | 37% | HE | 3% | ||
| Taken prior Cybersecurity Class/Course (n = 30) | |||||
| Yes | 63% | No | 37% | ||
| Years Teaching (Overall) (n = 30) | |||||
| 0–3 years | 7% | 4–6 years | 17% | 7–10 years | 10% |
| 11–15 years | 7% | 16+ years | 59% | ||
| Years Teaching (CS) (n = 25) | |||||
| 0–3 years | 88% | 4–6 years | 12% | 7–10 years | 0% |
| 11-15 years | 0% | 16+ years | 0% | ||
| Component | Pilot 1 | Pilot 2 | Pilot 3 |
|---|---|---|---|
| Modules | 2 | 5 | 12 |
| Required Modules: Details | 2: Modules 0 and 1 | 3: Module 0 + Choose 2 | 3: Module 0 + Choose 2 |
| Housed/Located | LMS/Canvas | LMS/Canvas | LMS/Canvas |
| Virtual Office Hours | 2x/week—1hr slot | 2x/week—1hr slot | By Request |
| Content Knowledge Quest. | No | Yes | Yes |
| Attitude Survey | No | Yes | Yes |
| Focus group & interviews | Yes | Yes | Yes |
| Bi-weekly progress reports | Yes | Yes | Yes |
| Duration | 28 days | 42 days | 49 days |
| Participants | 5 | 16 | 9 |
| Resources | Custom resources and research materials. | More resources and research materials. Added sample lesson plans & computational thinking flashcards. | More resources, research materials, and sample lesson plans. Added design thinking flashcards and videos. |
| Module | Pilot 1 | Pilot 2 | Pilot 3 |
|---|---|---|---|
| 0 | Intro to Cybersecurity | Intro to Cybersecurity | Intro to Cybersecurity |
| 1 | CIA Triad | CIA Triad | CIA Triad |
| 2 | Abstraction | Abstraction | |
| 3 | Modularity | Data Hiding | |
| 4 | Least Privilege | Simplicity | |
| 5 | Minimization | ||
| 6 | Modularity | ||
| 7 | Domain Separation | ||
| 8 | Least Privilege | ||
| 9 | Layering | ||
| 10 | Resource Encapsulation | ||
| 11 | Process Isolation |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Burrows, A.C.; Borowczak, M.; Mugayitoglu, B. Computer Science beyond Coding: Partnering to Create Teacher Cybersecurity Microcredentials. Educ. Sci. 2022, 12, 4. https://doi.org/10.3390/educsci12010004
Burrows AC, Borowczak M, Mugayitoglu B. Computer Science beyond Coding: Partnering to Create Teacher Cybersecurity Microcredentials. Education Sciences. 2022; 12(1):4. https://doi.org/10.3390/educsci12010004
Chicago/Turabian StyleBurrows, Andrea C., Mike Borowczak, and Bekir Mugayitoglu. 2022. "Computer Science beyond Coding: Partnering to Create Teacher Cybersecurity Microcredentials" Education Sciences 12, no. 1: 4. https://doi.org/10.3390/educsci12010004
APA StyleBurrows, A. C., Borowczak, M., & Mugayitoglu, B. (2022). Computer Science beyond Coding: Partnering to Create Teacher Cybersecurity Microcredentials. Education Sciences, 12(1), 4. https://doi.org/10.3390/educsci12010004








