Abstract
Telemedicine is the use of Information and Communication Technology (ICT) for clinical health care from a distance. The exchange of radiographic images and electronic patient health information/records (ePHI/R) for diagnostic purposes has the risk of confidentiality, ownership identity, and authenticity. In this paper, a data hiding technique for ePHI/R is proposed. The color information in the cover image is used for key generation, and stego-images are produced with ideal case. As a result, the whole stego-system is perfectly secure. This method includes the features of watermarking and steganography techniques. The method is applied to radiographic images. For the radiographic images, this method resembles watermarking, which is an ePHI/R data system. Experiments show promising results for the application of this method to radiographic images in ePHI/R for both transmission and storage purpose.
1. Introduction
Recently, rapid advances in information technology and telecommunication have enabled newer telemedicine facilities by supporting open network communication. The electronic Patient Health Information/Record (ePHI/R) and radiographic images sent to medical consultation centers/remote hospitals for speedy transmissions are examples. Telemedicine is the use of Information and Communication Technology (ICT) to provide clinical healthcare from a distance. However, the exchange of radiographic images and ePHI/R for diagnostic purposes has the risks of confidentiality, ownership identity, and authenticity. These medical minutes are exceedingly sensitive information about the patient and necessitate uncompromising security during both transmission and storage.
Information security and privacy in the healthcare sector is an issue of growing importance. Telemedicine and image security require methods and techniques that ensure the secure communication of radiographic images in ePHI/R systems. The main advantages of using steganography and watermarking in telemedicine are [1]: (i) These methods require no extra space for storage of data. The ePHI/R is embedded inside the cover radiographic images, so ePHI/R requires no extra storage space in memory. (ii) For transmission of data, the ePHI/R is embedded inside the cover radiographic image, and ePHI/R and radiographic images are transmitted together, so no additional bandwidth is required for transmission of ePHI/R. (iii) The ePHI/R is embedded in the radiographic image, so no one can perceive the existence of ePHI/R in radiographic images. These methods are secure and hold confidential information.
In this paper, an algorithm for data hiding in the radiographic images is introduced. This method can handle the security issues in ePHI/R and in other telemedicine application. The proposed method behaves like watermark methods and provides secure and protected transmitted of medical information. The rest of the paper is arranged as follows. Section 2 discusses related works from the literature. Our technique is discussed in Section 3. The simulation results and discussion are covered in Section 4. Conclusions and future work are described in Section 5.
2. Related Work
Various methods of steganography have been comprehensively reviewed in [2,3]. The steganography methods are classified based on data embedding Algorithms 1. The methods from these classes are discussed in [4,5,6,7,8,9,10,11,12,13]. The stago attacks and requirements of a steganographic system have been comprehensively discussed in [14,15,16]. The steganalysis methods [17,18,19,20,21,22,23] have also been projected to counter many advanced steganographic methods discussed in [2,3]. For telemedicine, such as tele-diagnosis and tele-consultancy services, radiographic images play a vital role. These images are used for instantaneous diagnosis, understanding of diseases, and to avoid the misdiagnosis [24].
Analysis of digital images shows that there are two important regions in the images, Region of Interest (ROI) and Region of Non-Interest (RONI) [25]. The region that contains most important information/data, mostly the diseased part in case of radiographic images, is called the ROI. This region, in case of radiographic images, does not allow any modification because this may result to misdiagnosis. The area other than the ROI is RONI [26]. Most of the steganographic methods use RONI for data embedding to avoid any kind of modification in the ROI [27,28,29]. For extraction of ROI and RONI in a radiographic image, both supervised and unsupervised methods are used. Supervised techniques may compromise the accuracy of segmentation, so automated techniques are implemented in many segmentation methods [30]. Some steganography and watermarking methods in radiographic images, which require classification into ROI and RONI, are discussed below.
Pandey et al. [31] presented a secure watermarking method by classifying image into ROI and RONI. This method uses manual segmentation method. For embedding data into RONI region, it uses Discrete Wavelet Transformation (DWT) decomposition. Jeya and Suganthi [32] presented the RONI-based secure and authenticated indexing of CT images of lungs. For classifying image into ROI and RONI, it applies the process of segmentation on the lung tissue of the CT scan image. Data is embedded into the RONI area after verifying that whether the RONI area is large enough to hold the embedded data. Aherrahrou and Tairi [33] presented the Partial Differential Equation, DWT, and Discrete Fourier Transformation (DFT)-based embedding and extraction algorithms. This algorithm reduces the computational complexity for classification, but PDE, DWT, and DFT transformation embedding algorithms increase the computational overhead. Al-Haj [34] presented the watermarking method for MRI, ultrasound, and X-ray images by classifying images into ROI and RONI. The authors assumed the segmented images and did not consider the segmentation problem. Both ROI and RONI are used for embedding data. The spatial domain method is implemented for embedding data into ROI, and a transformation domain method is used for the RONI.
Rayachotiand Edara [35] presented the block based algorithm for watermarking in medical images. This method divides the radiographic image into ROI, RONI, and boundary regions and embeds data in the LSBs of all three regions by using block-based technique. Classification of ROI and RONI is manual. Nyeemet al. [36] utilized the boundary pixels of the radiographic image as the RONI area. They did not apply any segmentation process to classify the image into ROI and RONI areas. For embedding in the RONI area of the images, the authors used the least significant bit plane method. Gunjaland Mali [37] presented an embedding algorithm that applies DWT on the RONI area of the radiographic image. For the classification of radiographic images into ROI and RONI areas, the author considered the manual segmentation method. All the stego-methods have limitations in terms of error types [14], active and passive attacks [15,16], statistical distortion transfer of domain and computational cost [2], and processing time [2,3]. Similarly, the stego systems in telemedicine face the problem of the segmentation of the image into ROI and RONI. The same segmentation algorithm cannot be implemented into the whole radiographic image domain. The segmentation of radiographic image into ROI and RONI creates computational overhead [30,31,32,33,34,35,36,37]. The methods discussed in [2,3,30,31,32,33,34,35,36,37] run the risk of data concealing.
To handle these issues, we propose a ε-secure stego-system where the segmentation is not required, data is embedded using the stego system, and a key is generated using the color information of the image.
3. Proposed Method
The radiographic images are multiple natures, and this depends on the application domain such as MR images, CT scan images, X-ray images, ultrasounds, etc. One single method does not cover the whole domain because of disease effects on the images. As a result, one single segmentation method does not work in every application. The EPHI/R minutes are also highly sensitive. This encourages us to propose a single method that is applicable in every application and has a high enough security level.
3.1. Challenges to Designing a New Method
General challenges are to design a new method that
- ➢
- Maximizes the probability of occurrence of Type II error;
- ➢
- Includes no transformation;
- ➢
- Processes the data byte by byte to reduce computational complexity.
Specific challenges are to design a new method that
- ➢
- Requires no classification of cover radiographic images into ROI and RONI;
- ➢
- Can be used for all types of radiographic images including MR images, CT scan images, X-ray images, ultrasounds, etc.;
- ➢
- Shows ε(θ) = ε(φ) even for the average and worst cases;
- ➢
- Should be ε-secure stego system.
3.2. Methodology
Figure 1 shows the overall work flow of our approach. Our methodology is to take the cover radiographic image and Patient Health Information/Record and apply the color analysis and attribute computation process on it. Distinct colors and attributes can be computed directly from the cover radiographic image. However, it is much easier by using the histogram of the image. These are actually named as statistical features of the image.
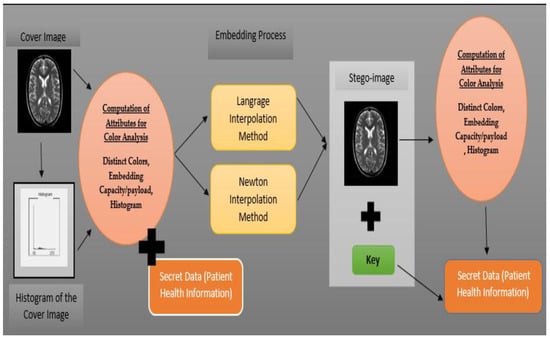
Figure 1.
Working model of the proposed steganographic approach.
For embedding phase, langrange interpolation [38,39,40] can also be used, but in this paper, Newton divided difference interpolation method [41,42,43] is used. as both of these method give the same polynomial, but the problem with using the langrage method is the large amount of computation. Given n + 1 distinct points, real number , and any real number , langrange interpolation and the Newton divided difference interpolation method give a unique polynomial p of degree, at most n satisfying . In the case of images, = Distinct Colors of the radiographic image and = Patient Health Information/Record. Unique polynomial created by this process will be used as a key in the extraction phase. This type of steganographic system falls into the private key steganography method, in which the key is shared between the sender and recipient.
Inputs of the extraction phase are the outputs of the embedding phase. The key with the combination of distinct colors of the stegoradiographic image will compute the Patient Health Information/Record.
Formal presentation of the proposed algorithm for embedding phase is
| Algorithms 1: The whole process of embedding data is divided into two algorithms. First algorithm is used at the sending end for embedding data and the second algorithm is for extraction process. |
| Key Generation Algorithm Inputs: Cover radiographic image (CRI), Patient Health information/Record (PHI/R) Output: Stego-radiographic image (Sri)
Formal presentation of the proposed algorithm for embeding phase with polynomial p is Inputs: Stego radiographic image Image Sri, lDePHI/R, p Output: Patient Health information/Record PHI/R
|
3.3. Evaluation Metrics
For the evaluation of these steganography techniques in terms of their efficiency, security, distortion, and diffusion of cover image analysis, the following metrics will be used (see [44,45,46,47,48]) For efficiency evaluation, the entropy matrix is used. Equation (1) describes the entropy measure.
where N is the number of pixels in an image and is the probability of occurrence of a pixel in an image with value . For security analysis, the Kullback-Leibler divergence method is used and defined in Equation (2).
where C is the total number of pixels in an image and and are the distribution of the stego and cover image, respectively, over C. If in a stego-system, the distribution of the stego and cover image cover image is identical, then by Equation (2),
Then, this type of stego system is called the “perfectly secure stego-system”. On the other hand, if
then the stego-system is called “-secure stego-system.”
Any change in the stego image, due to embedding of data in the cover image, is computationally called as distortion. For distortion analysis, Equation (5) defines the distortion function.
where is the Kronecker delta defined as
N is the total number of pixels in image and and are the stego and cover pixels at locations k.
For evaluating the ability of our method to diffuse the cover radiographic image, the Difference Number of Pixel Change Rate (NPCR) and Unified Average Changing Intensity (UACI) are computed. For the detail description of these matrices, we refer to [41,42,43].
The Difference Number of Pixel Change Rate (NPCR) is defined as
where is defined as
where N is the total number of pixels in an image, are the dimensions (width and height) of the image, is the kth pixel of the Stego image SI, and is the kth pixel of the Cover image CI.
Unified Average Changing Intensity (UACI) is defined as
where N is the total number of pixels in an image, are the dimensions (width and height) of the image, is the kth pixel of the Stego image SI, and is the kth pixel of the cover image CI.
4. Experimental Results and Discussion
This section covers the material and databases used for the experiments and the results against the different measures for to measure the security level, distortion, and statistical and change in perception.
4.1. The Material
We present experimental results of our method on various radiographic images. The parameters of the proposed algorithms were fixed to obtain overall optimal results in terms of image metrics. We analyze the results on 10 radiographic images taken from MedPix database. MedPix is a free online medical image database with over 53,000 indexed and curated images from over 13,000 patients. As shown in Figure 2, we number these images from 1 to 10 (according to the order from left-to-right and top-to-bottom.

Figure 2.
Set of testing images (referred to as 1 to 10, from left-to-right and top-to-bottom).
4.2. Histogram Computation
In the proposed algorithm, the key can be generated through two ways. First, we compute the histogram of an image and then use these histograms for a unique color. In this section, we showed the histogram for all the images. Figure 3 shows the histograms of the images represented in Figure 2. A histogram is the graphical representation of an image, which shows the frequency of intensity levels of the image pixels graphically. Computation of statistical attributes requires less computation time from the histogram of an image as compare to that from image directly.
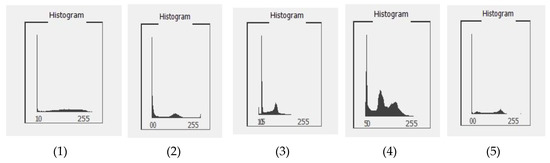
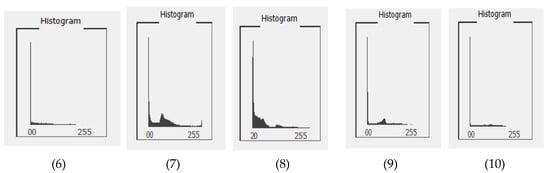
Figure 3.
Histograms of the images in Figure 2.
Computational results of the analysis of image in Figure 2(1) show that there are 48,221 pixels with same color in the image. These pixels are shown in Figure 3(1) with white region. Similarly, Figure 2(2) has 42,997 pixels having same color. Figure 2(3) has 37,863 pixels, Figure 2(4) has 19,256 pixels, Figure 2(5) has 134,993 pixels, Figure 2(6) has 83,749 pixels, Figure 2(7) has 17,890 pixels, Figure 2(8) has 24,892 pixels, Figure 2(9) has 74,785 pixels, and Figure 2(10) has 11,786 pixels with the same color.
4.3. Unique Color Computation
We first determine the unique colors in the image. Then, we count these colors. The pixels with these unique colors are used for the key generation. The white regions in the images of Figure 4 show the area of the image that contains these group of pixels with same color. The white regions show the parts of image that is the RONI area or the boundary pixels. From this analysis, all the unique colors of the image are computed, and the result are shown in Table 1.
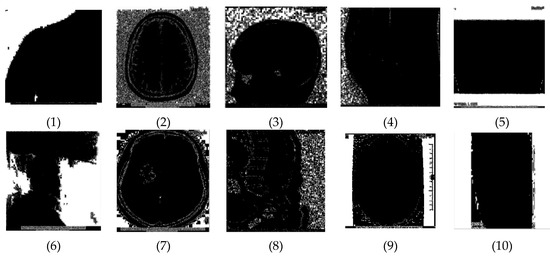
Figure 4.
Intensity based classification of images of Figure 2.

Table 1.
Computational results for unique colors and maximum capacity of images of Figure 2.
The maximum capacity for the embedding of data and the number of colors present in Figure 2 are shown in the Table 1.
These statistical features are used for the creation of the key for the steganography. At the next step, the data is embedded in the image with the different bit rate.
4.4. Results and Discussion
The statistical measures for detecting changes are the difference of entropies, Kullback-Leibler Divergence, Distortion Function, Difference Number of Pixel Change Rate (NPCR), and Unified Average Changing Intensity (UACI). These results are represented in the following tables. The objective of these measures is to check the security level and perceptual and statistical changes.
Table 2 shows computational results of entropy of the cover radiographic image, entropy of the stego radiographic image, change in entropies, Kullback-Leibler Divergence, Distortion Function, Difference Number of Pixel Change Rate (NPCR), and Unified Average Changing Intensity (UACI) for the cover and stego radiographic images after embedding a 100%, 75%, and 50% payload in the cover radiographic images. This shows that the embedding rate does not change the entropy of the image. The difference of entropies is also zero.

Table 2.
Computational results for entropy, Kullback Leibler divergence, distortion function, Difference Number of Pixel Change Rate (NPCR), and Unified Average Changing Intensity (UACI) after different embedding payload for each image.
Discussion
As mentioned in table 1, for maximum payload, the cover radiographic images 1, 2, 7, 8, and 9 require processing of only 256 pixels for the image. in radiographic image 3, the number of required pixels is 235. in radiographic image 4, this is 251. in radiographic image 6, this is 187. in radiographic image 10, this is 193.
The data in Table 2 represents the different measures. This shows that embedding payload does not affect the cover radiographic images in terms of efficiency, distortion, security, and other evaluation measures. This table shows that, for all the cases and embedding payloads, all the measures give their ideal results. Various image quality measures are used for measuring the image quality and performance of the steganographic and watermarking system. These measures detect changes in the image. The proposed method will obtain ideal results because the embedding phase does not create any changes in the cover image. The proposed approach uses the statistical feature—color information—to produce stego image. Hence, all the standard image quality measures [49] will produce ideal values.
5. Conclusions
The proposed method is a secure system for transforming medical minutes in telemedicine. The experimental results show that the method is secure and uses the color information for key generation. This algorithm has advantages over existing techniques in that it is a combination of watermarking and steganography, produces no statistical or visual changes in the images, and uses color information for key generation. This method does not use ROI and RONI, and it does not require any segmentation algorithm. This property of the algorithm is more effective and can be used for every sort of image. It is secure and easily extendable to color images. We hope to extend the method to protecting electrocardiography data. We also plan extend our approach to other interpolation techniques and optimize of our methodology and verification for different security levels.
Acknowledgement
The authors sincerely thank all the reviewers for their comments, which helped improve the overall quality and presentation of the paper.
Author Contributions
A.R., N.S., and V.B.S.P. conceived and designed the experiments; A.R. performed the experiments; A.R., N.S., and V.B.S.P. analyzed the data; A.R., N.S., and V.B.S.P. wrote the paper.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
| Acronym | Expended Form |
| CT | Computed Tomography |
| DFT | Discrete Fourier Transform |
| DKL | Divergence Kullback Leibler |
| DWT | Discrete Wavelet Transform |
| ePHI/R | Electronic Patient Health Information/Record |
| ICT | Information and Communication Technology |
| IQM | Image Quality Measure |
| MRI | Magnetic Resonance imaging |
| NPCR | Number of Pixel Change Rate |
| ROI | Region of Interest |
| RONI | Region of Non-Interest |
| UACI | Unified Average Change intensity |
References
- Singh, A.K.; Dave, M.; Anand, M. Hybrid technique for robust and imperceptible multiple watermarking using medical images. Multimedia Tools Appl. 2016, 75, 8381–8401. [Google Scholar] [CrossRef]
- Rashid, A.; Rahim, M.K. Critical Analysis of Steganography “An Art of Hidden Writing”. Int. J. Secur. Its Appl. 2016, 10, 259–281. [Google Scholar] [CrossRef]
- Subhedar, M.S.; Mankar, V.H. Current status and key issues in image steganography: A survey. Comput. Sci. Rev. 2014, 13, 95–113. [Google Scholar] [CrossRef]
- Silman, J. Steganography and steganalysis: An overview. Sans Inst. 2001, 3, 61–76. [Google Scholar]
- Lee, Y.K.; Chen, L.H. High capacity image steganographic model. IEE Proc. Vis. Image Signal Process. 2000, 147, 288–294. [Google Scholar] [CrossRef]
- Roque, J.J.; Minguet, J.M. SLSB: Improving the Steganographic Algorithm LSB. In Proceedings of the 7th International Workshop on Security in Information Systems (WOSIS 2009), In Conjunction with ICEIS 2009, Milan, Italy, 6–7 May 2009. [Google Scholar]
- Wu, D.C.; Tsai, W.H. A steganographic method for images by pixel-value differencing. Pattern Recognit. Lett. 2003, 24, 1613–1626. [Google Scholar] [CrossRef]
- Al-Momen, S.M.A.; George, L.E. Image hiding using magnitude modulation on the DCT coefficients. J. Appl. Comput. Sci. Math. 2010, 4, 9–14. [Google Scholar]
- Boney, L.; Tewfik, A.H.; Hamdy, K.N. Digital watermarks for audio signals. In Proceedings of the Third IEEE International Conference on Multimedia Computing and Systems, Hiroshima, Japan, 17–23 June 1996. [Google Scholar]
- Reddy, H.M.; Raja, K.B. High capacity and security steganography using discrete wavelet transform. Int. J. Comput. Sci. Secur. IJCSS 2009, 3, 462. [Google Scholar]
- Bender, W.; Gruhl, D.; Morimoto, N.; Lu, A. Techniques for data hiding. IBM Syst. J. 1996, 35, 313–336. [Google Scholar] [CrossRef]
- Johnson, N.; Jajodia, S. Steganalysis of Images Created Using Current Steganography Software. In Information Hiding; Springer: Berlin/Heidelberg, Germany, 1998. [Google Scholar]
- Marvel, L.M.; Boncelet, C.G.; Retter, C.T. Spread spectrum image steganography. IEEE Trans. Image Process. 1999, 8, 1075–1083. [Google Scholar] [CrossRef] [PubMed]
- Cachin, C. An information-theoretic model for steganography. In Information Hiding; Springer: Berlin/Heidelberg, Germany, 1998. [Google Scholar]
- Li, B.; He, J.; Huang, J.; Shi, Y.Q. A survey on image steganography and steganalysis. J. Inf. Hiding Multimedia Signal Process. 2011, 2, 142–172. [Google Scholar]
- Westfeld, A.; Pfitzmann, A. Attacks on steganographic systems. In International Workshop on Information Hiding; Springer: Berlin/Heidelberg, Germany, 1999. [Google Scholar]
- Fridrich, J.; Long, M. Steganalysis of LSB encoding in color images. In Proceedings of the 2000 IEEE International Conference on Multimedia and Expo, New York, NY, USA, 30 July–2 August 2000; Volume 3. [Google Scholar]
- Fridrich, J.; Goljan, M.; Du, R. Detecting LSB steganography in color, and gray-scale images. IEEE Multimedia 2001, 8, 22–28. [Google Scholar] [CrossRef]
- Dumitrescu, S.; Wu, X.; Wang, Z. Detection of LSB steganography via sample pair analysis. IEEE Trans. Signal Process. 2003, 51, 1995–2007. [Google Scholar] [CrossRef]
- Zhang, T.; Ping, X. Reliable detection of LSB steganography based on the difference image histogram. In Proceedings of the 2003 IEEE International Conference on Acoustics, Speech, and Signal Processing, Hong Kong, China, 6–10 April 2003. [Google Scholar]
- Lu, P.; Luo, X.; Tang, Q.; Li, S. An Improved Sample Pairs Method for Detection of LSB Embedding. In Information Hiding; Volume 3200, Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Ker, A.D. Improved detection of LSB steganography in grayscale images. In Proceedings of the International Workshop on Information Hiding, Toronto, ON, Canada, 23–25 May 2004; Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Ker, A.D. Derivation of error distribution in least squares steganalysis. IEEE Trans. Inf. Forensics Secur. 2007, 2, 140–148. [Google Scholar] [CrossRef]
- Rey, C.; Dugelay, J.L. A survey of watermarking algorithms for image authentication. EURASIP J. Adv. Signal Process. 2002, 6, 218932. [Google Scholar] [CrossRef]
- Singh, A.K.; Dave, M.; Mohan, A. Wavelet based image watermarking: Futuristic concepts in information security. Proc. Natl. Acad. Sci. USA 2014, 84, 345–359. [Google Scholar] [CrossRef]
- Zhang, L.; Zhou, P.P. Localized affine transform resistant watermarking in region-of-interest. Telecommun. Syst. 2010, 44, 205–220. [Google Scholar] [CrossRef]
- Memon, N.A.; Gilani, S.A.M. NROI watermarking of medical images for content authentication. In Proceedings of the 2008 IEEE International Multitopic Conference, Karachi, Pakistan, 23–24 December 2008. [Google Scholar]
- Zain, J.; Clarke, M. Security in telemedicine: Issues in watermarking medical images. In Proceedings of the 3rd International Conference: Sciences of Electronic, Technologies of Information and Telecommunications, Sousse, Tunisia, 27–31 March 2005. [Google Scholar]
- Yang, C.Y.; Hu, W.C. Reversible data hiding in the spatial and frequency domains. Int. J. Image Process. 2010, 3, 373–382. [Google Scholar]
- Rathi, S.C.; Inamdar, V.S. Analysis of watermarking techniques for medical Images preserving ROI. Comput. Sci. Inf. Technol. 2012, 287–308. [Google Scholar] [CrossRef]
- Pandey, R.; Singh, A.K.; Kumar, B.; Mohan, A. Iris based secure NROI multiple eye image watermarking for teleophthalmology. Multimedia Tools Appl. 2016, 75, 14381–14397. [Google Scholar] [CrossRef]
- Jasmine Selvakumari Jeya, I.; Suganthi, J. RONI based secured and authenticated indexing of lung CT images. In Computational and Mathematical Methods in Medicine; Hindawi Publishers: New York, NY, USA, 2015. [Google Scholar]
- Aherrahrou, N.; Tairi, H. PDE based scheme for multi-modal medical image watermarking. Biomed. Eng. Online 2015, 14, 108. [Google Scholar] [CrossRef] [PubMed]
- Al-Haj, A. Secured telemedicine using region-based watermarking with tamper localization. J. Digit. Imaging 2014, 27, 737–750. [Google Scholar] [CrossRef] [PubMed]
- Rayachoti, E.; Edara, S.R. Block Based Medical Image Watermarking Technique for Tamper Detection and Recovery. arXiv, 2014; arXiv:1412.6143. [Google Scholar]
- Nyeem, H.; Boles, W.; Boyd, C. Utilizing least significant bit-planes of RONI pixels for medical image watermarking. In Proceedings of the 2013 International Conference on Digital Image Computing: Techniques and Applications (DICTA), Hobart, Australia, 26–28 November 2013. [Google Scholar]
- Gunjal, B.L.; Mali, S.N. ROI based embedded watermarking of medical images for secured communication in telemedicine. Int. J. Comput. Commun. Eng. 2012, 6, 293–298. [Google Scholar]
- El-Samie, F.E.A.; Ahmed, H.E.H.; Elashry, I.F.; Shahieen, M.H.; Faragallah, O.S.; El-Rabaie, E.S.M.; Alshebeili, S.A. Image Encryption: A Communication Perspective; CRC Press: Boca Raton, FL, USA, 2013. [Google Scholar]
- El-Latif, A.A.A.; Li, L.; Zhang, T.; Wang, N.; Song, X.; Niu, X. Digital image encryption scheme based on multiple chaotic systems. Sens. Imaging Int. J. 2012, 13, 67–88. [Google Scholar] [CrossRef]
- Etemadi Borujeni, S.; Eshghi, M. Chaotic image encryption design using Tompkins-Paige algorithm. In Mathematical Problems in Engineering; Hindawi Publishers: New York, NY, USA, 2009. [Google Scholar]
- Stoer, J.; Bulirsch, R. Introduction to Numerical Analysis; Springer Science & Business Media: Berlin, Germany, 2013; Volume 12. [Google Scholar]
- Powell, M.J.D. Approximation Theory and Methods; Cambridge University Press: Cambridge, UK, 1981. [Google Scholar]
- Minoux, M. Mathematical Programming: Theory and Algorithms; John Wiley & Sons: Hoboken, NJ, USA, 1986. [Google Scholar]
- Rashid, A.; Rahim, M.K. Classification, Analysis and Comparison of Non-Blind Image Quality Measure. Int. J. Signal Process. Image Process. Pattern Recognit. 2016, 9, 347–360. [Google Scholar] [CrossRef]
- Eskicioglu, A.M.; Fisher, P.S. Image quality measures and their performance. IEEE Trans. Commun. 1995, 43, 2959–2965. [Google Scholar] [CrossRef]
- Sayood, K. Statistical evaluation of image quality measures. J. Electron. Imaging 2002, 11, 206–223. [Google Scholar]
- Wang, Z.; Bovik, A.C.; Sheikh, H.R.; Simoncelli, E.P. Image quality assessment: From error visibility to structural similarity. IEEE Trans. Image Process. 2004, 13, 600–612. [Google Scholar] [CrossRef] [PubMed]
- Snyder, H.L. Image Quality: Measures and Visual Performance. Flat-Panel Displays and CRTs; Springer: Houten, The Netherlands, 1985; pp. 70–90. [Google Scholar]
- Rashid, A. Experimental analysis and comparison of LSB substitution and LSB matching method of information security. Int. J. Comput. Sci. Issues IJCSI 2015, 12, 91. [Google Scholar]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).