D-FAP: Dual-Factor Authentication Protocol for Mobile Cloud Connected Devices †
Abstract
:1. Introduction
2. An Overview of MCC Authentication Protocols
2.1. Cryptographic Based Methods
2.2. Biometrics Based Methods
2.3. Password Based Methods
2.4. Smart Card with Password Based Methods
- (a)
- An adversary with no knowledge of the user’s password, but who had full access to the user’s smart card and was able to extract the security information stored on the card, should not be able to extract the user’s password by performing an offline guessing attack;
- (b)
- An adversary with full knowledge of the user’s password, but who was not in possession of the user’s smart card, should not be able to attempt to impersonate the user to login to the cloud server.
3. D-FAP in Detail
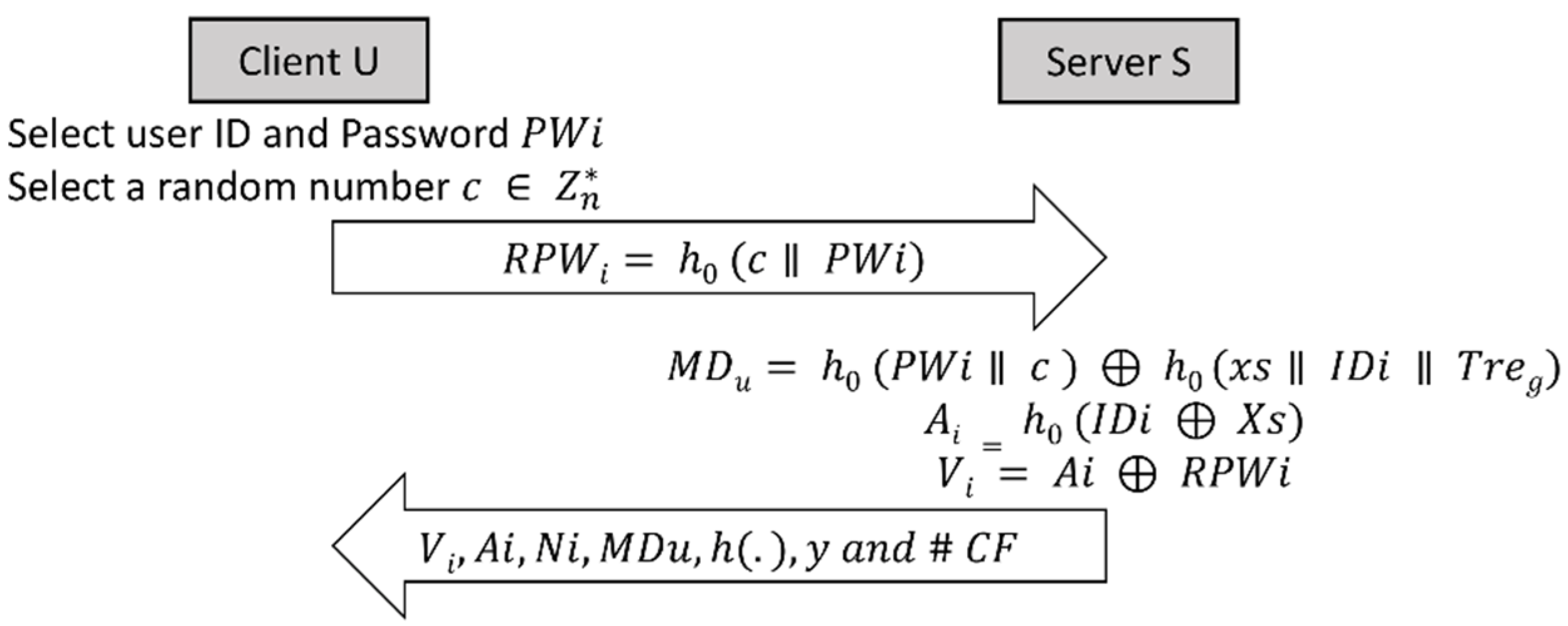
3.1. Registration Phase
3.1.1. User Registration
- 𝑈 signs up with a CSP a by accessing a secure registration URL;
- 𝑈 chooses a new User 𝐼𝐷 and password, at this point, the user is prompted to load their digital certificate (the user’s public key is encapsulated within the public digital certificate). The CSP will use the information provided by the certificate to identify the user, and the public key encapsulated within the certificate, to encrypt future communication with the user;
- To enhance the security of the user password, one of the most efficient ways is to employ ‘salting’ and ‘hashing’. Once the user enters their credentials, the server remotely:
- generates a random number 𝑐 on the mobile device side,
- concatenates the random number with the password (salting),
- hashes the outcome with a suitable one-way hash function (hashing), i.e.,: 𝑅𝑃𝑊𝑖 = ℎ0(𝑐ǁ𝑃𝑊𝑖),
- encrypts 𝑅𝑃𝑊𝑖 𝑎𝑛𝑑 𝐼𝐷𝑖 using the server’s public key;
- 𝑈 uploads {𝑅𝑃𝑊𝑖, 𝐼𝐷𝑖} to the server using a secure encrypted channel. This can be done by using an SSL protected URL. The main purpose of this is to protect the user credentials from being sniffed by an eavesdropper.
3.1.2. Server Registration
- Record the time of receipt of registration 𝑇𝑟𝑒𝑔. This is used to identify if the user is a registered user and, if so, when s/he was registered, and also to generate the nonce;
- Check if the user is a new user by checking its database of existing users. This is done to protect against user duplication;
- If the user is a new user, the server checks the validity of 𝑈’s digital certificate in order to guarantee its authenticity and it checks if the certificate belongs to the user being registered (if the user is already registered, then they will be rejected);
- Obtain 𝑈’s public key from the digital certificate, which is used to encrypt future communication with the client;
- 𝑈’s access policy file, including 𝑈’s usage policy and access level, is concatenated with 𝑈’s digital certificate, and the result is hashed using a suitable one-way function creating the message digest 𝑀𝐷𝑢 = ℎ0 (𝑈𝑠𝑒𝑟 𝑝𝑜𝑙𝑖𝑐𝑦 ǁ 𝑈𝑠𝑒𝑟 𝑐𝑒𝑟𝑡𝑖𝑓𝑖𝑐𝑎𝑡𝑒). 𝑀𝐷𝑢 is used for mutual authentication with the client, and it can also be used to identify the user;
- Generate the 𝑆 secret keys 𝑥𝑠 and 𝑦. 𝑥𝑠 is used by the remote server to generate security parameters for future communications with the smart card. 𝑦 is stored by the remote server in the smart card to be used by the smart card to generate security parameters for future communication with the server;
- Create a new user account in the user database with the following parameters stored on the database: 𝐼𝐷𝑖, 𝑇𝑟𝑒𝑔, 𝑀𝐷𝑢;
- Compute 𝐴𝑖 = ℎ0(𝐼𝐷𝑖 ⊕ 𝑥𝑠);
- Compute 𝑉𝑖 = 𝐴𝑖 ⊕ 𝑅𝑃𝑊𝑖;
- Create nonce 𝑁𝑖 = ℎ0(𝑃𝑊𝑖 ǁ 𝑐) ⊕ ℎ0(𝑥𝑠 ǁ 𝐼𝐷𝑖 ǁ 𝑇𝑟𝑒𝑔), where 𝑥𝑠 is 𝑆’s secret key;
- Personalize the smart card by storing 𝑉𝑖, 𝐴𝑖, 𝑁𝑖, 𝑀𝐷𝑢, ℎ(.), 𝑦, and #CF, where #CF is the column number in the database where 𝑈’s records are stored;
- Send the smart card with the reader securely to the client with instructions on how to:
- (a)
- use the smart card with the smart card reader,
- (b)
- keep the smart card secure,
- (c)
- change the password,
- (d)
- unlock the card,
- (e)
- report any loss or theft of the card.
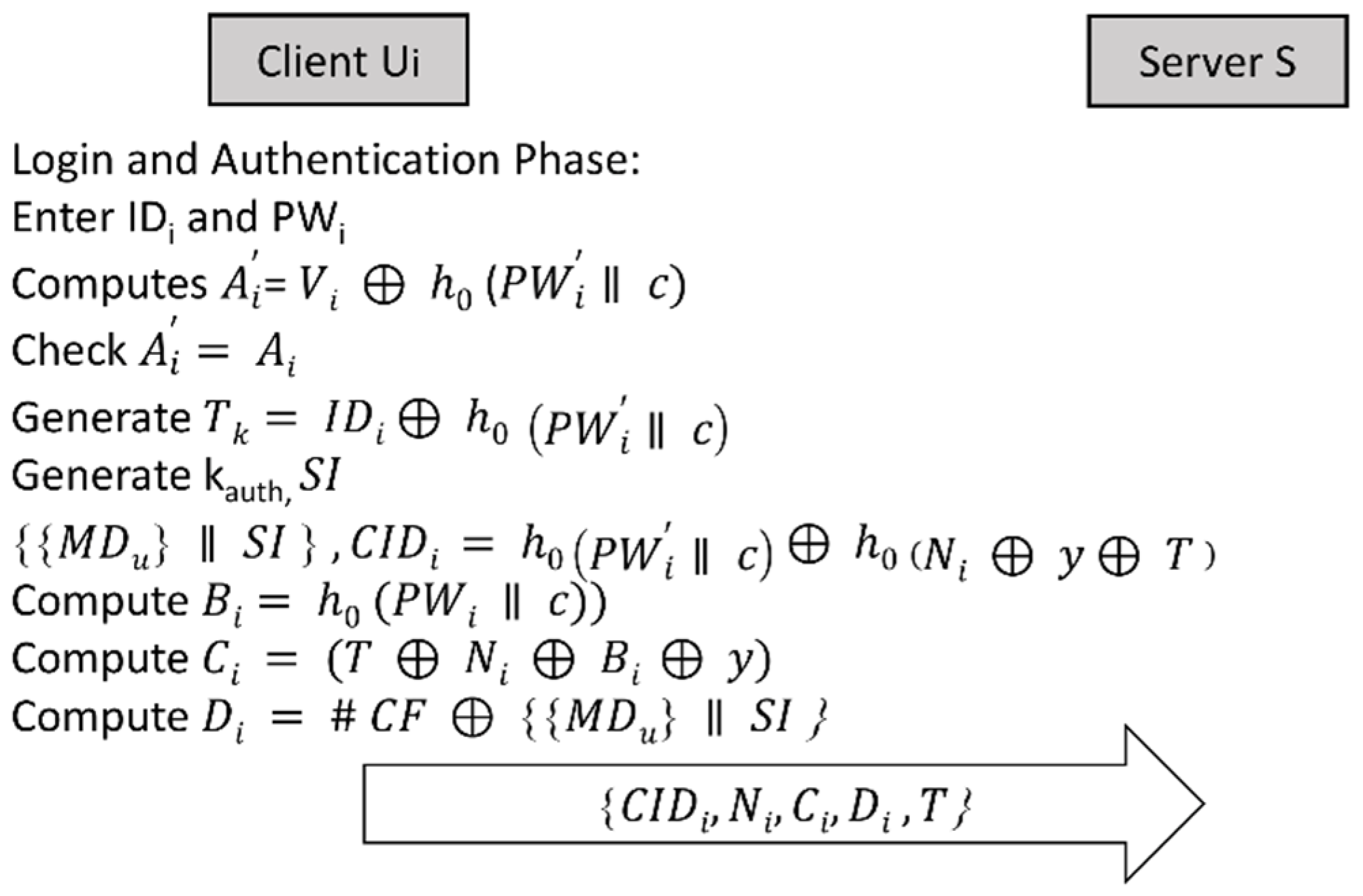
3.2. Login Phase
3.2.1. Local Authentication between the 𝑈 and 𝑆𝐶
- Concatenating the newly entered 𝑃𝑊′ with a random number 𝑐 and hashing them;
- Computing 𝐴′𝑖 = 𝑉𝑖 ⊕ ℎ0 (𝑃𝑊′𝑖 ǁ 𝑐);
- Comparing 𝐴′𝑖 with the 𝐴𝑖 stored in its memory. If 𝐴′𝑖 = 𝐴𝑖, then 𝑆𝐶 proceeds to the remote login operation, else the operation is terminated with the request for 𝑈 to re-enter the password.
3.2.2. Remote Login between 𝑆𝐶 and 𝑆
- 𝑆𝐶 generates 𝑇𝑘 = 𝐼𝐷𝑖 ⊕ ℎ0(𝑃𝑊𝑖 ǁ c);
- 𝑇𝑘 is used as a seed for Crypto Pseudo Random Number Generator (CPRNG) to generate 𝐾𝑎𝑢𝑡ℎ, which is used to encrypt 𝑀𝐷𝑢;
- 𝑇𝑘 is used to encrypt {{𝑀𝐷𝑢} ǁ 𝑆𝐼}, where 𝑆𝐼 is the State Identifier;
- To protect the anonymity of the user, 𝐶𝐼𝐷𝑖 is generated by creating a dynamic identifier, i.e., 𝐶𝐼𝐷𝑖 = ℎ0(𝑃𝑊𝑖 ǁ 𝑐) ⊕ ℎ0(𝑁𝑖 ⊕ 𝑦 ⊕ 𝑇);
- 𝑆𝐶 computes 𝐵𝑖 = ℎ0 (𝐼𝐷𝑖 ⊕ ℎ0(𝑃𝑊𝑖 ǁ 𝑐));
- 𝑆𝐶 computes 𝐶𝑖 = (𝑇 ⊕ 𝑁𝑖 ⊕ 𝐵𝑖 ⊕ 𝑦), where 𝑇 is the current time;
- 𝑆𝐶 computes 𝐷𝑖 = #𝐶𝐹 ⊕ {{𝑀𝐷𝑢} ⊕ 𝑆𝐼};
- 𝑆𝐶 encrypts the message using’s public key {𝐶𝐼𝐷𝑖, 𝑁𝑖, 𝐶𝑖, 𝐷𝑖, 𝑇};
- 𝑆𝐶 sends the encrypted message to the server 𝑆.
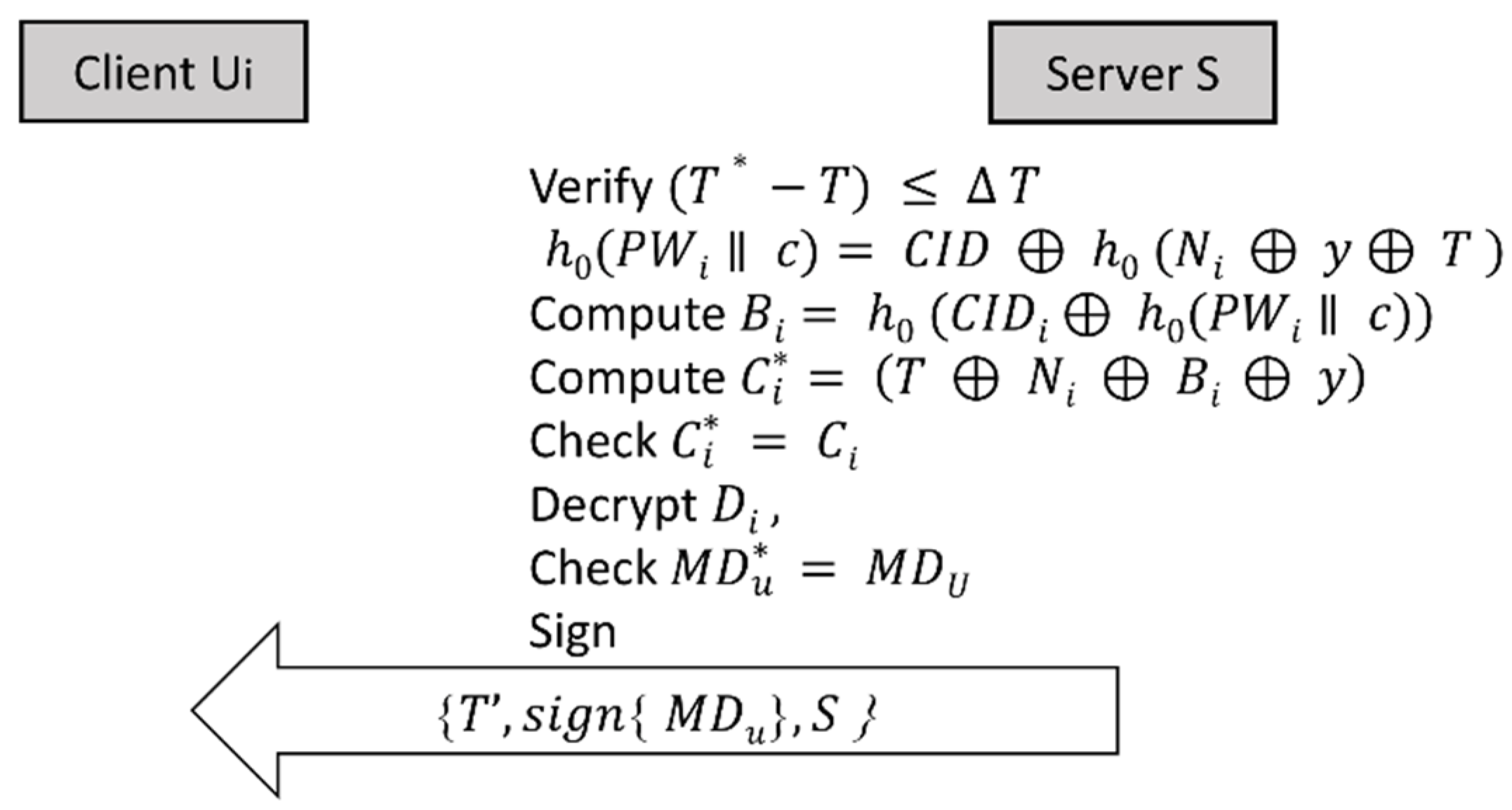
3.3. Verification Phase
3.3.1. Server Authentication
- Register the time of message arrival 𝑇∗;
- Calculate the time difference between arrival time 𝑇∗ and authentication message sent time 𝑇, extracted from the received authentication message, i.e., ∆𝑇 = 𝑇∗ − 𝑇. If the time window is acceptable, the message is accepted, else it is rejected. The time difference between the time of arrival of the message and the time the message sent is important to avoid replay attacks;
- Extract 𝑈’s password ℎ0(𝑃𝑊𝑖 ǁ 𝑐) = 𝐶𝐼𝐷 ⊕ ℎ0(𝑁𝑖 ⊕ 𝑦 ⊕ 𝑇);
- Compute 𝐵𝑖 = ℎ0(𝐶𝐼𝐷𝑖 ⊕ ℎ0(𝑃𝑊𝑖 ǁ 𝑐));
- Compute 𝐶𝑖 = (𝑇 ⊕ 𝑁𝑖 ⊕ 𝐵𝑖 ⊕ 𝑦);
- Check if 𝐶𝑖∗ = 𝐶𝑖. If so, then it proceeds to the next step, else, the user is rejected. This process is used to ensure the authenticity of the message received from 𝑈;
- Use the shared column reference #𝐶𝐹 to locate 𝑈’s record in the server database;
- Use 𝑇𝐾 to decrypt {{𝑀𝐷𝑢} ǁ 𝑆𝐼} in 𝐷𝑖 to obtain 𝑆𝐼 and {𝑀𝐷𝑢};
- 𝑇𝐾 is also used as a seed for 𝐶𝑃𝑅𝑁𝐺 to generate 𝐾𝑎𝑢𝑡ℎ, which is used to decrypt {𝑀𝐷𝑢};
- The decrypted 𝑀𝐷𝑢 is compared with the user 𝑀𝐷𝑢 stored in the server database. If they match, then the user is known to be a legitimate user, else the user authentication message is rejected;
- For mutual authentication, 𝑆 signs 𝑀𝐷𝑢 using the cloud’s private key;
- 𝑆 uses 𝑈’s public key to encrypt {𝑇′, 𝑠𝑖𝑔𝑛 {𝑀𝐷𝑢}, 𝑆} and sends to the user, where 𝑇′ is the current server time, and S is the server identity.
3.3.2. Mobile Mutual Authentication
- Using the 𝑆𝐶’s private key, 𝑆𝐶 decrypts {𝑇′, 𝑠𝑖𝑔𝑛{𝑀𝐷𝑢}, 𝑆};
- 𝑆𝐶 checks time ∆𝑇 = 𝑇″ − 𝑇′ where 𝑇″ is the time of message arrival. If the time window is acceptable, the message is accepted, else it is rejected;
- Using the cloud’s public key, 𝑆𝐶 decrypts the signed message 𝑠𝑖𝑔𝑛{𝑀𝐷𝑢};
- The decrypted 𝑀𝐷𝑢 is checked against the smart card’s stored 𝑀𝐷𝑢. If they match, then mutual authentication had been accomplished; otherwise, the message will be rejected.
3.3.3. Password Change Procedure
- The user inserts the smart card into the smart card reader, and submits the current 𝐼𝐷𝑖 and 𝑃𝑊𝑖, and requests to change the password
- The user is prompted twice for a new 𝑃𝑊𝑖∗;
- The Smart card computes ;
- The Smart card computes ;
- Then, once 𝑁𝑖 will be replaced with 𝑁𝑖∗ and 𝑉𝑖 will be replaced with 𝑉𝑖∗. The password has been changed with the new password and terminates the operation.
3.3.4. Lost Smart Card Revocation Procedure
4. D-FAP Security Analysis
4.1. Formal Verification by ProVerif
4.1.1. Simulation Processes
4.1.2. Simulation Results
4.2. Informal Security Analysis
4.3. D-FAP Security Comparisons
5. Conclusions
6. Future Work and Suggested Applications
Funding
Acknowledgments
Conflicts of Interest
References
- Srivastava, S. Smartphone Triggered Security Challenges—Issues, Case Studies and Prevention. In Cyber Security in Parallel and Distributed Computing; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2019; pp. 187–206. [Google Scholar] [CrossRef]
- Cui, Y.; Ma, X.; Wang, H.; Stojmenovic, I.; Liu, J. A Survey of Energy Efficient Wireless Transmission and Modeling in Mobile Cloud Computing. Mob. Netw. Appl. 2013, 18, 148–155. [Google Scholar] [CrossRef]
- Ateya, A.; Muthanna, A.; Gudkova, I.; Abuarqoub, A.; Vybornova, A.; Koucheryavy, A. Development of Intelligent Core Network for Tactile Internet and Future Smart Systems. J. Sens. Actuator Netw. 2018, 7, 1. [Google Scholar] [CrossRef] [Green Version]
- Ateya, A.; Muthanna, A.; Vybornova, A.; Gudkova, I.; Gaidamaka, Y.; Abuarqoub, A.; Algarni, A.; Koucheryavy, A. Model Mediation to Overcome Light Limitations—Toward a Secure Tactile Internet System. J. Sens. Actuator Netw. 2019, 8, 6. [Google Scholar] [CrossRef] [Green Version]
- Baker, T.; Asim, M.; Dermott, Á.M.; Iqbal, F.; Kamoun, F.; Shah, B.; Alfandi, O.; Hammoudeh, M. A secure fog-based platform for SCADA-based IoT critical infrastructure. Software 2019. [Google Scholar] [CrossRef]
- Muthanna, A.; Ateya, A.; Khakimov, A.; Gudkova, I.; Abuarqoub, A.; Samouylov, K.; Koucheryavy, A. Secure and Reliable IoT Networks Using Fog Computing with Software-Defined Networking and Blockchain. J. Sens. Actuator Netw. 2019, 8, 15. [Google Scholar] [CrossRef] [Green Version]
- Irshad, A.; Chaudhry, S.A.; Shafiq, M.; Usman, M.; Asif, M.; Ghani, A. A provable and secure mobile user authentication scheme for mobile cloud computing services. Int. J. Commun. Syst. 2019, 32, e3980. [Google Scholar] [CrossRef]
- Mo, J.; Hu, Z.; Chen, H.; Shen, W. An Efficient and Provably Secure Anonymous User Authentication and Key Agreement for Mobile Cloud Computing. Wirel. Commun. Mob. Comput. 2019, 2019. [Google Scholar] [CrossRef]
- Atwady, Y.; Hammoudeh, M. A Survey on Authentication Techniques for the Internet of Things. In Proceedings of the International Conference on Future Networks and Distributed Systems, Cambridge, UK, 19–20 July 2017. [Google Scholar]
- Wang, P.; Li, B.; Shi, H.; Shen, Y.; Wang, D. Revisiting Anonymous Two-Factor Authentication Schemes for IoT-Enabled Devices in Cloud Computing Environments. Secur. Commun. Netw. 2019, 2019. [Google Scholar] [CrossRef] [Green Version]
- Epiphaniou, G.; Walshe, M.; Al-Khateeb, H.; Hammoudeh, M.; Katos, V.; Dehghantanha, A. Non-Interactive Zero Knowledge Proofs for the Authentication of IoT Devices in Reduced Connectivity Environments. Ad Hoc Netw. 2019, 95, 101988. [Google Scholar]
- Balasubramanian, N.; Balasubramanian, A.; Venkataramani, A. Energy Consumption in Mobile Phones: A Measurement Study and Implications for Network Applications. In Proceedings of the 9th ACM SIGCOMM Conference on Internet Measurement 2009, Chicago, IL, USA, 4–6 November 2009; pp. 280–293. [Google Scholar] [CrossRef]
- Aloraini, A.; Hammoudeh, M. A Survey on Data Confidentiality and Privacy in Cloud Computing. In Proceedings of the International Conference on Future Networks and Distributed Systems, Cambridge, UK, 19–20 July 2017; pp. 1–7. [Google Scholar]
- Belguith, S.; Kaaniche, N.; Hammoudeh, M. Analysis of attribute-based cryptographic techniques and their application to protect cloud services. Trans. Emerg. Telecommun. Technol. 2019, e3667. [Google Scholar] [CrossRef]
- Fathi, R.; Salehi, M.A.; Leiss, E.L. User-Friendly and Secure Architecture (UFSA) for Authentication of Cloud Services. In Proceedings of the 2015 IEEE 8th International Conference on Cloud Computing, New York, NY, USA, 27 June–2 July 2015; pp. 516–523. [Google Scholar]
- Potlapally, N.R.; Ravi, S.; Raghunathan, A.; Jha, N.K. Analyzing the energy consumption of security protocols. In Proceedings of the 2003 International Symposium on Low Power Electronics and Design, New York, NY, USA, 27–27 August 2003; pp. 30–35. [Google Scholar]
- Forman, G.H.; Zahorjan, J. The challenges of mobile computing. Computer 1994, 27, 38–47. [Google Scholar] [CrossRef] [Green Version]
- Liao, I.E.; Cheng-Chi, L.; Min-Shiang, H. Security enhancement for a dynamic ID-based remote user authentication scheme. In Proceedings of the International Conference on Next Generation Web Services Practices (NWeSP’05), Seoul, Korea, 22–26 August 2005; p. 4. [Google Scholar]
- Abuarqoub, A. A Lightweight Two-Factor Authentication Scheme for Mobile Cloud Computing. In Proceedings of the 3rd International Conference on Future Networks and Distributed Systems, Paris, France, 1–2 July 2019; pp. 1–7. [Google Scholar]
- Carlin, A.; Hammoudeh, M.; Aldabbas, O. Intrusion Detection and Countermeasure of Virtual Cloud Systems—State of the Art and Current Challenges. Int. J. Adv. Comput. Sci. Appl. 2015, 6. [Google Scholar] [CrossRef] [Green Version]
- Ghafir, I.; Prenosil, V.; Svoboda, J.; Hammoudeh, M. A Survey on Network Security Monitoring Systems. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Vienna, Austria, 22–24 August 2016; pp. 77–82. [Google Scholar]
- Teing, Y.-Y.; Homayoun, S.; Dehghantanha, A.; Choo, K.-K.R.; Parizi, R.M.; Hammoudeh, M.; Epiphaniou, G. Private Cloud Storage Forensics: Seafile as a Case Study. In Handbook of Big Data and IoT Security; Dehghantanha, A., Choo, K.-K.R., Eds.; Springer International Publishing: Cham, UK, 2019; pp. 73–127. [Google Scholar] [CrossRef]
- Khan, M.S.A.; Mitchell, C.J. Trashing IMSI catchers in mobile networks. In Proceedings of the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Boston, MA, USA, 18–20 July 2017; pp. 207–218. [Google Scholar]
- Binu, S.; Mohan, A.; Deepak, K.T.; Manohar, S.; Misbahuddin, M.; Raj, P. A proof of concept implementation of a mobile based authentication scheme without password table for cloud environment. In Proceedings of the 2015 IEEE International Advance Computing Conference (IACC), Bangalore, India, 12–13 June 2015; pp. 1224–1229. [Google Scholar]
- Momeni, M. A Lightweight Authentication Scheme for Mobile Cloud Computing. Int. J. Comp. Sci. Bus. Inf. 2014, 14, 153–160. [Google Scholar]
- Schwab, D.; Yang, L. Entity authentication in a mobile-cloud environment. In Proceedings of the Eighth Annual Cyber Security and Information Intelligence Research Workshop, Oak Ridge, TN, USA, 8–10 January 2013; pp. 1–4. [Google Scholar]
- Moço, N.F.; Técnico, I.S.; Telecomunicações, I.D.; Correia, P.L. Smartphone-based palmprint recognition system. In Proceedings of the 2014 21st International Conference on Telecommunications (ICT), Lisbon, Portugal, 4–7 May 2014; pp. 457–461. [Google Scholar]
- Dey, S.; Sampalli, S.; Ye, Q. MDA: Message digest-based authentication for mobile cloud computing. J. Cloud Comput. 2016, 5, 18. [Google Scholar] [CrossRef] [Green Version]
- Camenisch, J.; Lehmann, A.; Neven, G. Optimal Distributed Password Verification. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 182–194. [Google Scholar]
- Moffat, S.; Hammoudeh, M.; Hegarty, R. A Survey on Ciphertext-Policy Attribute-based Encryption (CP-ABE) Approaches to Data Security on Mobile Devices and its Application to IoT. In Proceedings of the International Conference on Future Networks and Distributed Systems (ICFNDS’17), Cambridge, UK, 19–20 July 2017; p. 34. [Google Scholar] [CrossRef]
- Yang, G.; Wong, D.S.; Wang, H.; Deng, X. Two-factor mutual authentication based on smart cards and passwords. J. Comput. Syst. Sci. 2008, 74, 1160–1172. [Google Scholar] [CrossRef] [Green Version]
- Xie, T.; Liu, F.; Feng, D. Fast Collision Attack on MD5. IACR Cryptol. ePrint Arch. 2013, 2013, 170. [Google Scholar]
- Boone, G.; Huang, J.; Spiegeleire, S.D.; Sweijs, T. Future Issue Biometrics: The Uncertainty of Identification Authentication: 2010–2020; The Hague Centre for Strategic Studies: The Hague, The Netherlands, 2009. [Google Scholar]
- Ahmad, S.; Mohd Ali, B.; Wan Adnan, W.A. Technical issues and challenges of biometric applications as access control tools of information security. Int. J. Innov. Comput. Inf. Control 2012, 8, 7983–7999. [Google Scholar]
- Khan, S.H.; Akbar, M.A. Multi-Factor Authentication on Cloud. In Proceedings of the 2015 International Conference on Digital Image Computing: Techniques and Applications (DICTA), 23–25 November 2015; pp. 1–7. [Google Scholar]
- Han, Z.; Yang, L.; Wang, S.; Mu, S.; Liu, Q. Efficient Multifactor Two-Server Authenticated Scheme under Mobile Cloud Computing. Wirel. Commun. Mob. Comput. 2018, 2018. [Google Scholar] [CrossRef]
- Ghafir, I.; Saleem, J.; Hammoudeh, M.; Faour, H.; Prenosil, V.; Jaf, S.; Jabbar, S.; Baker, T. Security threats to critical infrastructure: The human factor. J. Supercomput. 2018, 74, 4986–5002. [Google Scholar] [CrossRef] [Green Version]
- Fiducia, K.J.; Thomas, J.F.; Schmerge, P.S. Mobile Enterprise Smartcard Authentication. U.S. Patent 9,083,703, 14 July 2015. [Google Scholar]
- Kard, P. Thursby Software. Available online: http://www.thursby.com/ (accessed on 12 December 2019).
- ACS. Advanced Card Systems Ltd. Available online: https://www.acs.com.hk/en/ (accessed on 12 December 2019).
- Chang, C.; Wu, T. Remote password authentication with smart cards. IEE Proc. 1991, 138, 165–168. [Google Scholar] [CrossRef] [Green Version]
- Radhakrishnan, N.; Karuppiah, M. An efficient and secure remote user mutual authentication scheme using smart cards for Telecare medical information systems. Inform. Med. Unlocked 2018. [Google Scholar] [CrossRef]
- Chen, C.-L.; Deng, Y.-Y.; Tang, Y.-W.; Chen, J.-H.; Lin, Y.-F. An Improvement on Remote User Authentication Schemes Using Smart Cards. In Proceedings of the second International Conference on Mobile Ad-Hoc and Sensor Networks, Hong Kong, China, 13–15 December 2006; pp. 416–423. [Google Scholar]
- Zhao, Y.; Li, S.; Jiang, L. Secure and Efficient User Authentication Scheme Based on Password and Smart Card for Multiserver Environment. Sec. Comm. Netw. 2018, 2018, 9178941. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C. Anonymous Two-Factor Authentication in Distributed Systems: Certain Goals Are Beyond Attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Das, M.L.; Saxena, A.; Gulati, V.P. A dynamic ID-based remote user authentication scheme. IEEE Trans. Consum. Electron. 2004, 50, 629–631. [Google Scholar] [CrossRef] [Green Version]
- Madhusudhan, R.; Mittal, R.C. Dynamic ID-based remote user password authentication schemes using smart cards: A review. J. Netw. Comput. Appl. 2012, 35, 1235–1248. [Google Scholar] [CrossRef]
- Yoon, E.-J.; Yoo, K.-Y. Improving the Dynamic ID-Based Remote Mutual Authentication Scheme. In Proceedings of the OTM Confederated International Conferences, On the Move to Meaningful Internet Systems 2006, Montpellier, France, 29 October–3 November 2006; pp. 499–507. [Google Scholar]
- Lee, C.-C.; Hwang, M.-S.; Yang, W.-P. A flexible remote user authentication scheme using smart cards. SIGOPS Oper. Syst. Rev. 2002, 36, 46–52. [Google Scholar] [CrossRef]
- Zhu, Y.; Ma, D.; Huang, D.; Hu, C. Enabling secure location-based services in mobile cloud computing. In Proceedings of the Second ACM SIGCOMM Workshop on Mobile Cloud Computing, Hong Kong, China, 16 August 2013; pp. 27–32. [Google Scholar]
- Chaudhry, S.A.; Farash, M.S.; Naqvi, H.; Kumari, S.; Khan, M.K. An enhanced privacy preserving remote user authentication scheme with provable security. Secur. Commun. Netw. 2015, 8, 3782–3795. [Google Scholar] [CrossRef]
- Chen, C.-T.; Lee, C.-C. A two-factor authentication scheme with anonymity for multi-server environments. Secur. Commun. Netw. 2015, 8, 1608–1625. [Google Scholar] [CrossRef]
- Chaudhry, S. Comment on Robust and Efficient Password Authenticated Key Agreement with User Anonymity for Session Initiation Protocol Based Communications. IET Commun. 2015, 9, 1034. [Google Scholar] [CrossRef]
- Wang, Y.-Y.; Liu, J.-Y.; Xiao, F.-X.; Dan, J. A more efficient and secure dynamic ID-based remote user authentication scheme. Comput. Commun. 2009, 32, 583–585. [Google Scholar] [CrossRef]
- Wen, F.; Li, X. An improved dynamic ID-based remote user authentication with key agreement scheme. Comput. Electr. Eng. 2012, 38, 381–387. [Google Scholar] [CrossRef]
- Tang, H.-B.; Liu, X.-S. Cryptanalysis of a dynamic ID-based remote user authentication with key agreement scheme. Int. J. Commun. Syst. 2012, 25, 1639–1644. [Google Scholar] [CrossRef]
- Tsai, J.; Lo, N. A Privacy-Aware Authentication Scheme for Distributed Mobile Cloud Computing Services. IEEE Syst. J. 2015, 9, 805–815. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Kim, I.L.; Rho, S.; Farash, M.S.; Shon, T. An improved anonymous authentication scheme for distributed mobile cloud computing services. Clust. Comput. 2019, 22, 1595–1609. [Google Scholar] [CrossRef]
- Blanchet, B.; Cheval, V.; Allamigeon, X.; Smyth, B.; Sylvestre, M. ProVerif: Cryptographic Protocol Verifier in the Formal Model. Available online: https://prosecco.gforge.inria.fr/personal/bblanche/proverif/manual.pdf (accessed on 12 December 2019).
- Wu, F.; Xu, L.; Kumari, S.; Li, X. An improved and provably secure three-factor user authentication scheme for wireless sensor networks. Peer-to-Peer Netw. Appl. 2018, 11, 1–20. [Google Scholar] [CrossRef]
- Lee, H.; Lee, D.; Moon, J.; Jung, J.; Kang, D.; Kim, H.; Won, D. An improved anonymous authentication scheme for roaming in ubiquitous networks. PLoS ONE 2018, 13. [Google Scholar] [CrossRef] [Green Version]
- Ryu, J.; Lee, H.; Kim, H.; Won, D. Secure and Efficient Three-Factor Protocol for Wireless Sensor Networks. Sensors 2018, 18, 4481. [Google Scholar] [CrossRef] [Green Version]
- Chen, Q.; Zhang, C.; Zhang, S. Overview of Security Protocol Analysis. In Secure Transaction Protocol Analysis: Models and Applications; Springer: Berlin/Heidelberg, Germany, 2008; pp. 17–71. [Google Scholar]
- Shieh, W.; Wang, M. A New Parallel Session Attack to Khan-Zhang’s Authentication Scheme. In Proceedings of the 2008 3rd International Conference on Innovative Computing Information and Control, DaLian, China, 18–20 June 2008; p. 154. [Google Scholar]
- Yeh, K.-H.; Su, C.; Lo, N.W.; Li, Y.; Hung, Y.-X. Two robust remote user authentication protocols using smart cards. J. Syst. Softw. 2010, 83, 2556–2565. [Google Scholar] [CrossRef]
- Ku, W.C.; Tsai, H.; Tsaur, M.J. Stolen-verifier attack on an efficient smartcard-based one-time password authentication scheme. IEICE Trans. Commun. 2004, 87, 2374–2376. [Google Scholar]
- Sumitra, B.; Pethuru, C.R.; Misbahuddin, M. A survey of cloud authentication attacks and solution approaches. Int. J. Innov. Res. Comput. Commun. Eng. 2014, 2, 6245–6253. [Google Scholar]
- Zhan, J.; Fan, X.; Han, J.; Gao, Y.; Xia, X.; Zhang, Q. CIADL: Cloud insider attack detector and locator on multi-tenant network isolation: An OpenStack case study. J. Ambient Intell. Humaniz. Comput. 2019. [Google Scholar] [CrossRef]
- Ding, Y.; Horster, P. Undetectable on-line password guessing attacks. SIGOPS Oper. Syst. Rev. 1995, 29, 77–86. [Google Scholar] [CrossRef]
| Notation | Description |
|---|---|
| Random number | |
| Column number where user information stored | |
| One-way hash function | |
| User’s ID | |
| User message digest | |
| Nonce | |
| User’s password | |
| Remote server identity | |
| Smart card | |
| State identifier | |
| Time stamp | |
| Expected valid time interval | |
| User | |
| Security parameters | |
| Secret value of server (to be stored on server) | |
| Secret value of server (to be stored in smart card) | |
| Bitwise XOR computation | |
| Concatenation operation |
| (* Channel *) | free pubCH: channel. free prCH: channel [Private]. |
| (*Constants *) | Const PWi: bitstring [Private]. |
| (* Events *) | event initiate_ Client (bitstring). event term_ Client (bitstring). event initiate_ RemS (bitstring). event term _ RemS (bitstring). |
| (* Functions *) | fun owh (bitstring): bitstring fun concat (bitstring, bitstring): bitstring fun Exr (bitstring, bitstring): bitstring fun SyEnc (bitstring, bitstring): bitstring fun pubk (seckey): secpubkey fun aenc (bitstring, privkey) fun sigpk (SSkey): sigpkey fun sig (bitsting, bitstring) |
| Parameter | ProVerif Output |
|---|---|
| Secure | |
| True | |
| True | |
| True |
| Attack | Tsai et al. [57] | Chaudhary et al. [58] | D-FAP |
|---|---|---|---|
| Resist offline password Guessing attack | yes | yes | yes |
| Prevent playback attack | yes | yes | yes |
| Minimize denial of service attack | yes | yes | yes |
| Prevent insider attack | no | no | yes |
| Prevent of masquerade attack | no | yes | yes |
| Prevent stolen verifier attacks | yes | yes | yes |
| Prevent reflection attack | yes | yes | yes |
| Prevent parallel session attack | no | yes | yes |
| Prevent smart card loss attack | no | no | yes |
© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abuarqoub, A. D-FAP: Dual-Factor Authentication Protocol for Mobile Cloud Connected Devices. J. Sens. Actuator Netw. 2020, 9, 1. https://doi.org/10.3390/jsan9010001
Abuarqoub A. D-FAP: Dual-Factor Authentication Protocol for Mobile Cloud Connected Devices. Journal of Sensor and Actuator Networks. 2020; 9(1):1. https://doi.org/10.3390/jsan9010001
Chicago/Turabian StyleAbuarqoub, Abdelrahman. 2020. "D-FAP: Dual-Factor Authentication Protocol for Mobile Cloud Connected Devices" Journal of Sensor and Actuator Networks 9, no. 1: 1. https://doi.org/10.3390/jsan9010001
APA StyleAbuarqoub, A. (2020). D-FAP: Dual-Factor Authentication Protocol for Mobile Cloud Connected Devices. Journal of Sensor and Actuator Networks, 9(1), 1. https://doi.org/10.3390/jsan9010001





