Priority-Based Machine-To-Machine Overlay Network over LTE for a Smart City
Abstract
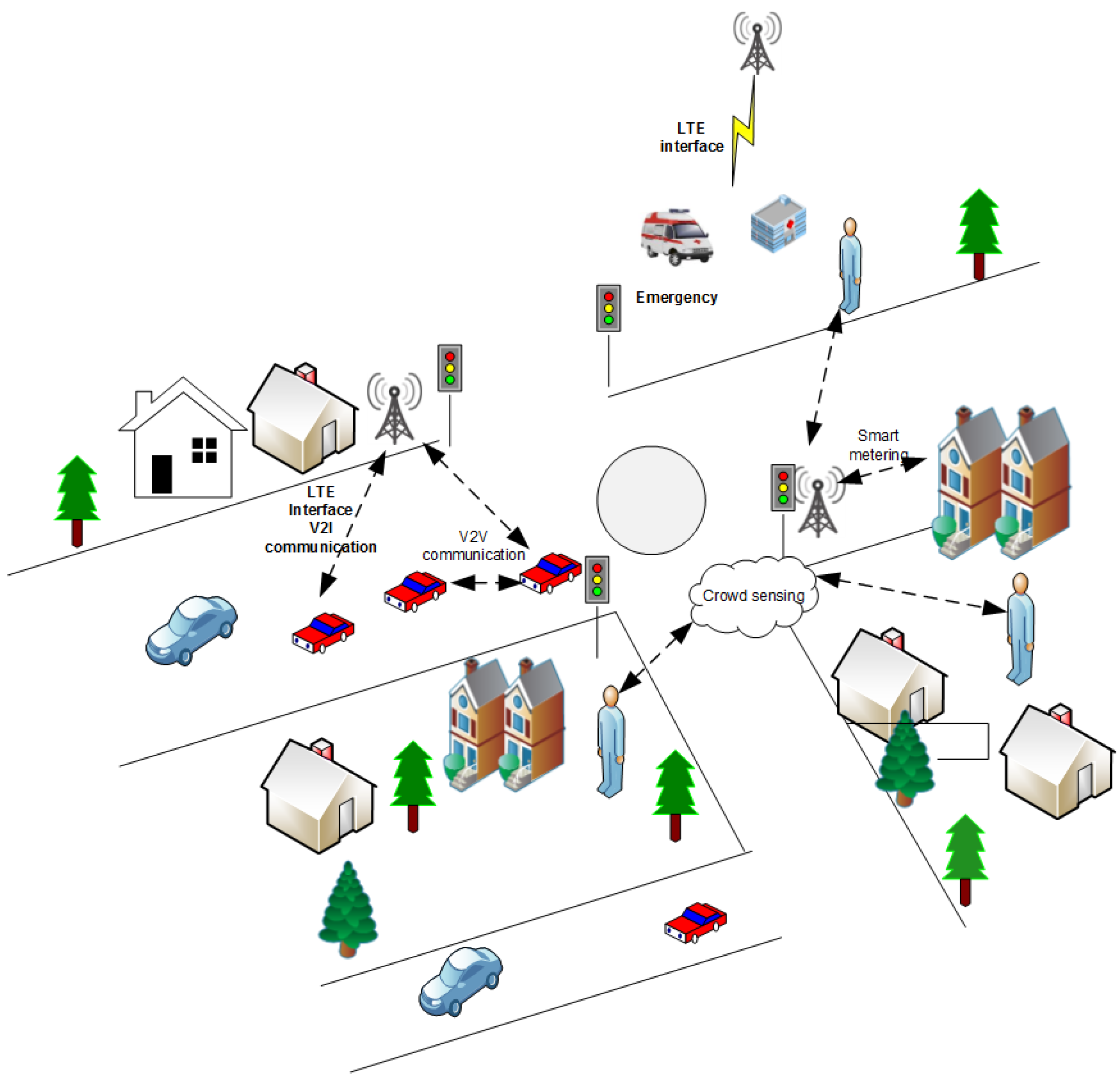
1. Introduction
- UEs may be grouped into traffic classes for which random access may be delayed or temporarily blocked. This technique is known as access class barring (which is already supported for H2H calls) and extended access class barring [3].
- Differentiation among traffic classes can be achieved by allowing different backoff windows for different classes of UEs [4].
- Further differentiation among the classes can be achieved by allowing members of the traffic class to attempt access only in predefined time slots within specific LTE frames, using base station scheduling [5].
- The base station can apply a suitable polling scheme (also known as pull-based scheme) to differentiate between UEs. In this scheme, M2M terminals initiate random access only after being paged by the eNodeB [6].
- PRACH resource separation and dynamic PRACH resource allocation schemes allocate different PRACH resources such as preamble sequences and random access slots to different types of traffic (i.e., H2H and M2M) in a dynamic manner [7].
- Traffic classes can be differentiated by using different power levels rather than using power ramping based on the age of the attempt [8].
- Failed calls may be allocated a specific set of preambles to use for repeated access attempts [9].
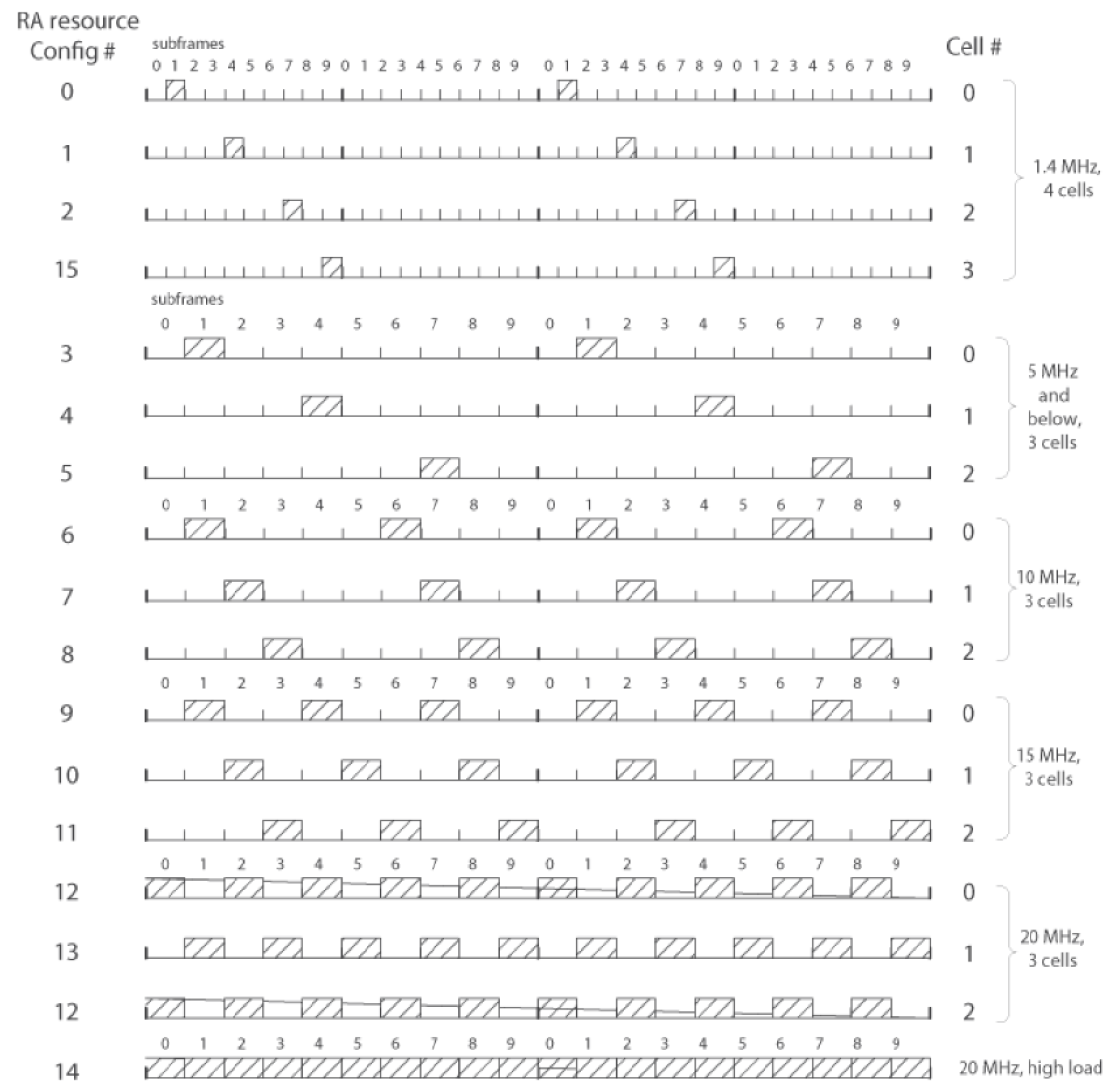
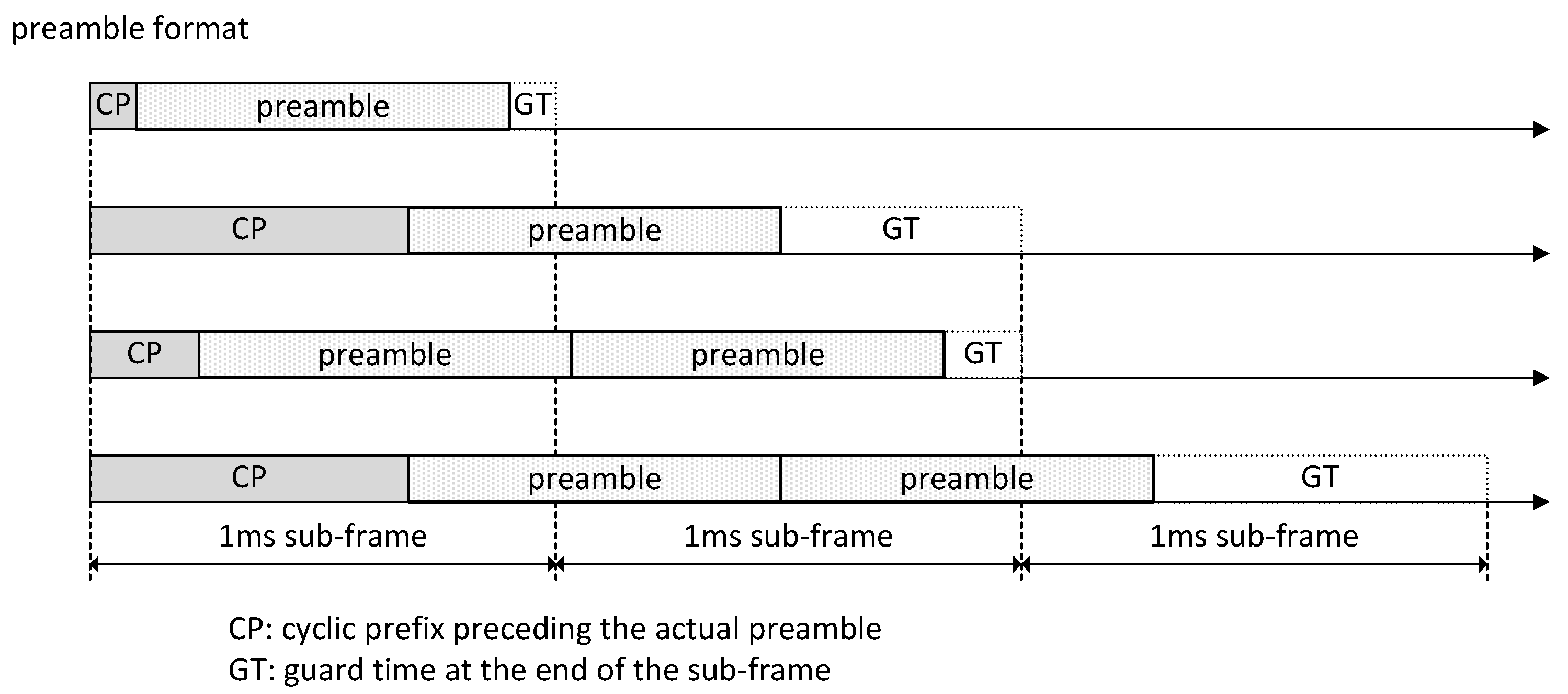
2. PRACH Architecture and Random Access Procedure
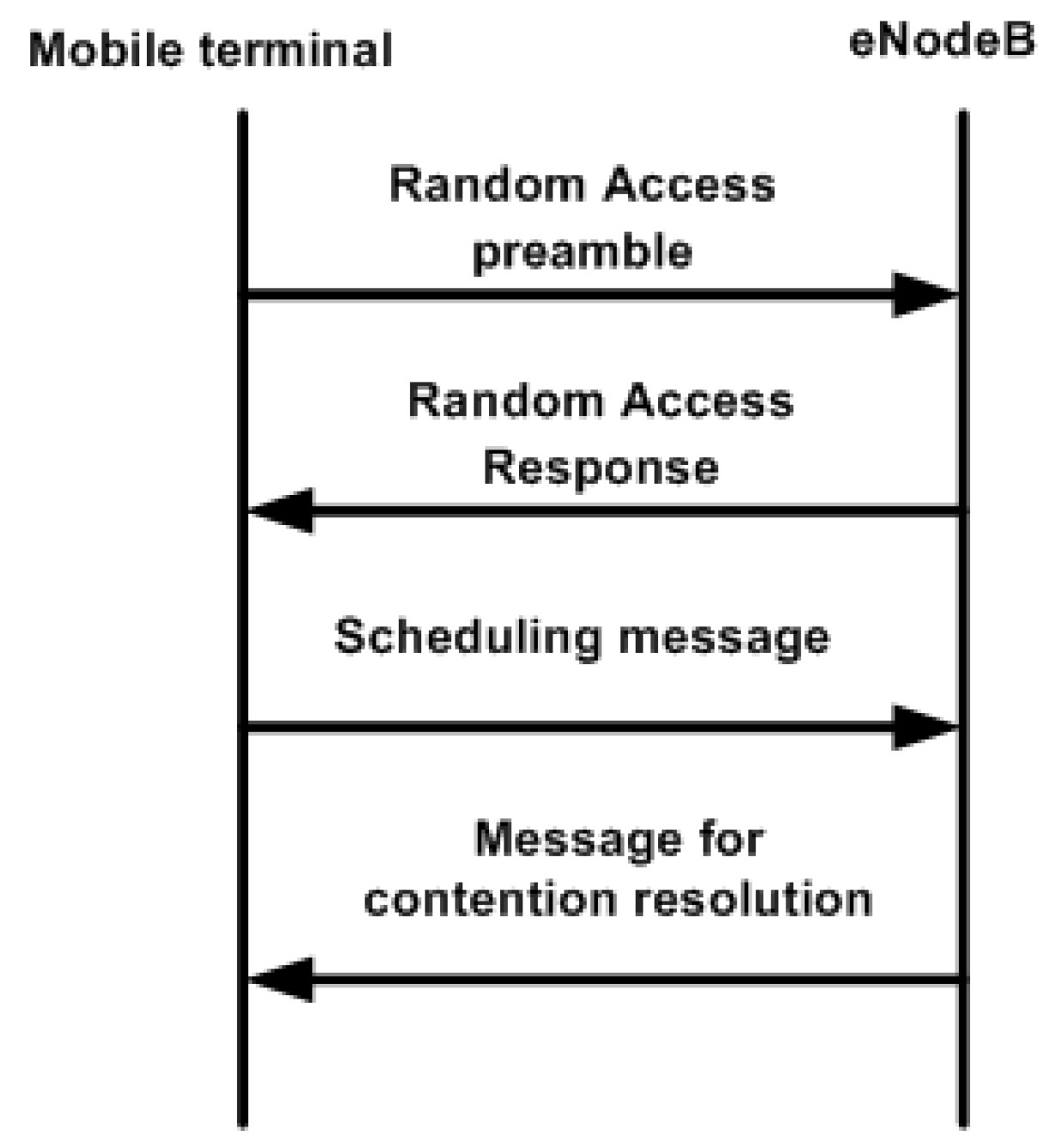
Steps of the Random Access Procedure
- Step 1:
- The terminal randomly selects the preamble from the available 54 preamble sequences and transmits it over PRACH to eNodeB.
- Step 2:
- The eNodeB transmits an RA Response (RAR) to the terminal through the physical downlink shared channel (PDSCH). RAR contains temporary Cell Radio Network Temporary Identifier (CRNTI) identity information. It also contains scheduling information for the third step.
- Step 3:
- Then, the terminal sends its CRNTI and scheduling information to eNodeB through the Physical Uplink Shared Channel (PUSCH) radio resources assigned in Step 2.
- Step 4:
- Finally, the eNodeB responds with the confirmation of the identity of the terminal and finishes the contention procedure.
3. PM2M Overlay Network over PRACH
3.1. Earlier Work on Overlays in LTE
3.2. Superframe Structure of PM2M
3.3. Physical and MAC Layer
3.4. Priority Mapping
4. Modelling PRACH for H2H and PM2M Traffic
- is the preamble sequence length in bits;
- W is the LTE PRACH bandwidth;
- R is the LTE PRACH preamble data rate;
- is the received signal power;
- is the power of external (Gaussian) interference;
- is the spectral density of white noise; and
- is the number of preambles that are always active for the PM2M overlay.
4.1. H2H PRACH Overload/Outage during Preamble Collision
4.2. PM2M Overload Calculation
- is the number of preamble elements;
- W is the LTE bandwidth;
- R is the LTE PRACH preamble data rate;
- is the received signal power;
- is the outer cell interference power; is the spectral density of white noise; and
- is the number of PM2M preamble codes that are always active.
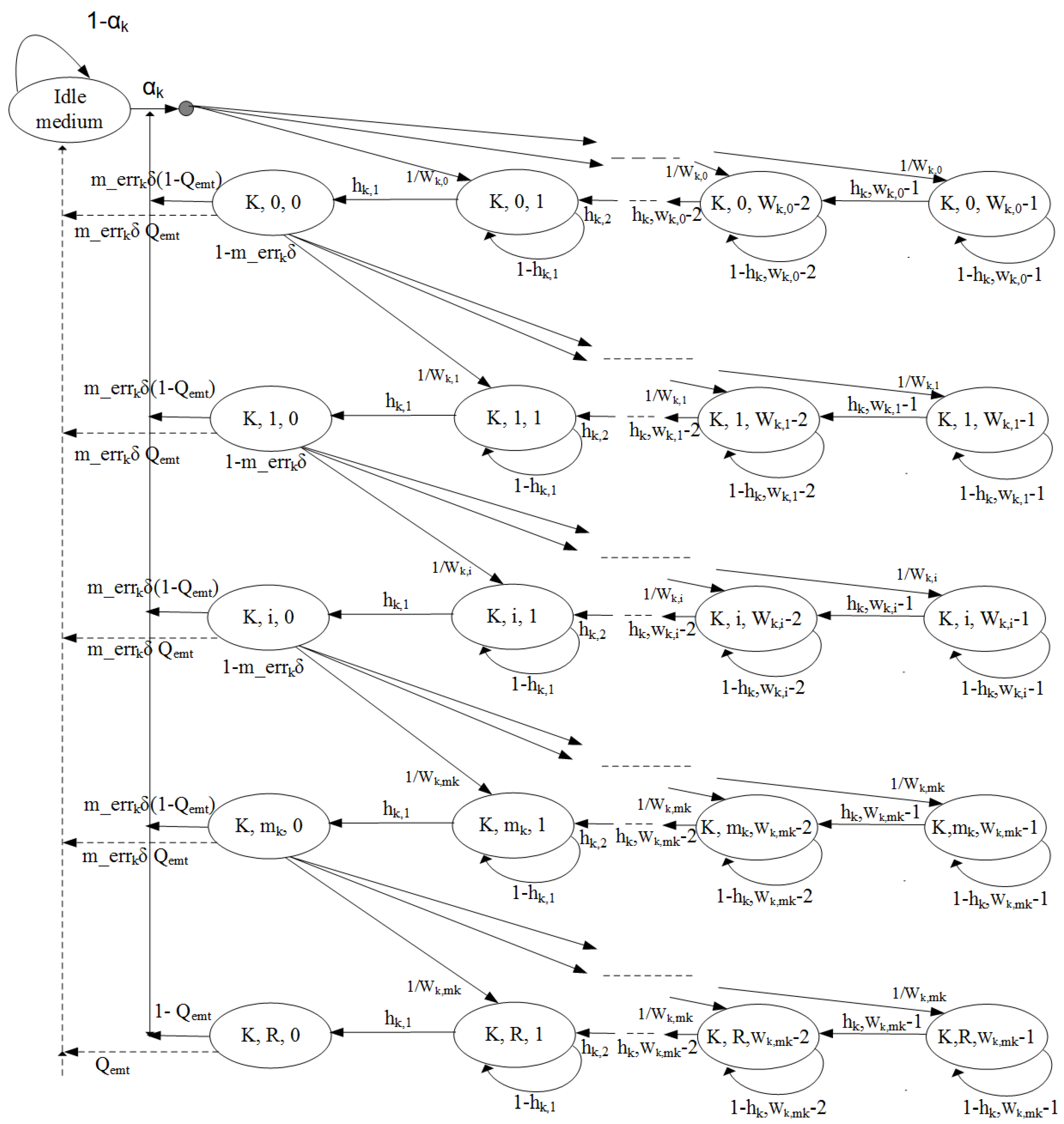
5. Modelling the PM2M Backoff Procedure with Backoff Error
- Initially, , where .
- The contention window value doubles when, , for , if i is an even number
- The contention window value increases uniformly when, , for , if i is an odd number.
- = is the successful transmission time in slots;
- = is the approximate mean backoff counter value; and
- = is the unsuccessful transmission time.
- , the time period between the locking and unlocking of the backoff counter due to successful transmission by another node.
- , the duration of unsuccessful transmission.
- , the time between locking and unlocking when there is not enough time for completing a packet transmission.
- is the probability that there is not enough time to complete a frame transaction in the current RAP;
- is the successful transmission time in slots;
- is the unsuccessful transmission time in slots;
- is the probability of locking the backoff counter due to successful transmission by others;
- is the probability of locking the backoff counter due to unsuccessful transmission by others; and
- is the number of CSMA slots when the backoff counter must be locked due to insufficient time for completing the transaction.
6. Performance Evaluation
6.1. Performance of H2H Traffic in the Presence of the Overlay Network
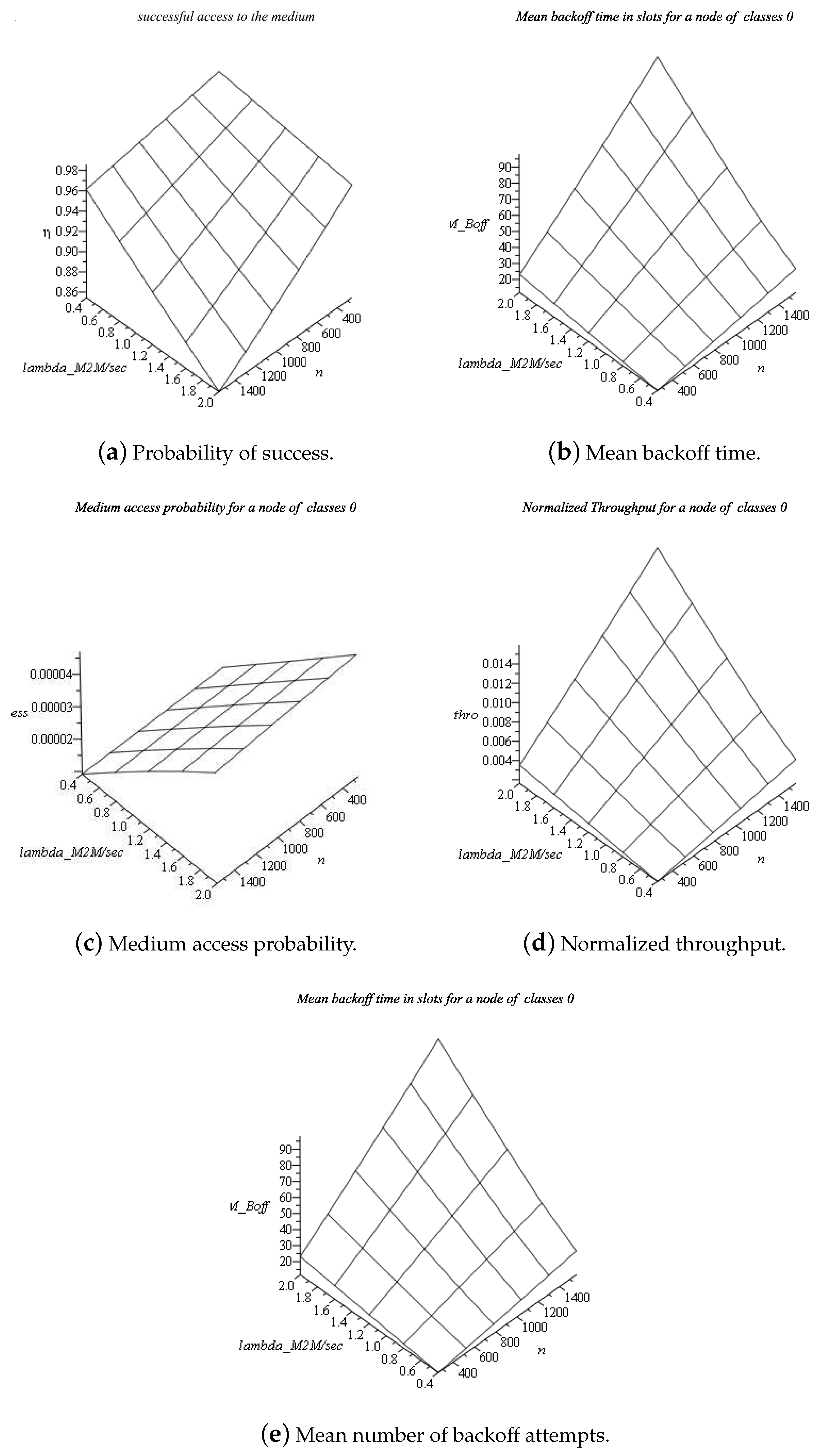
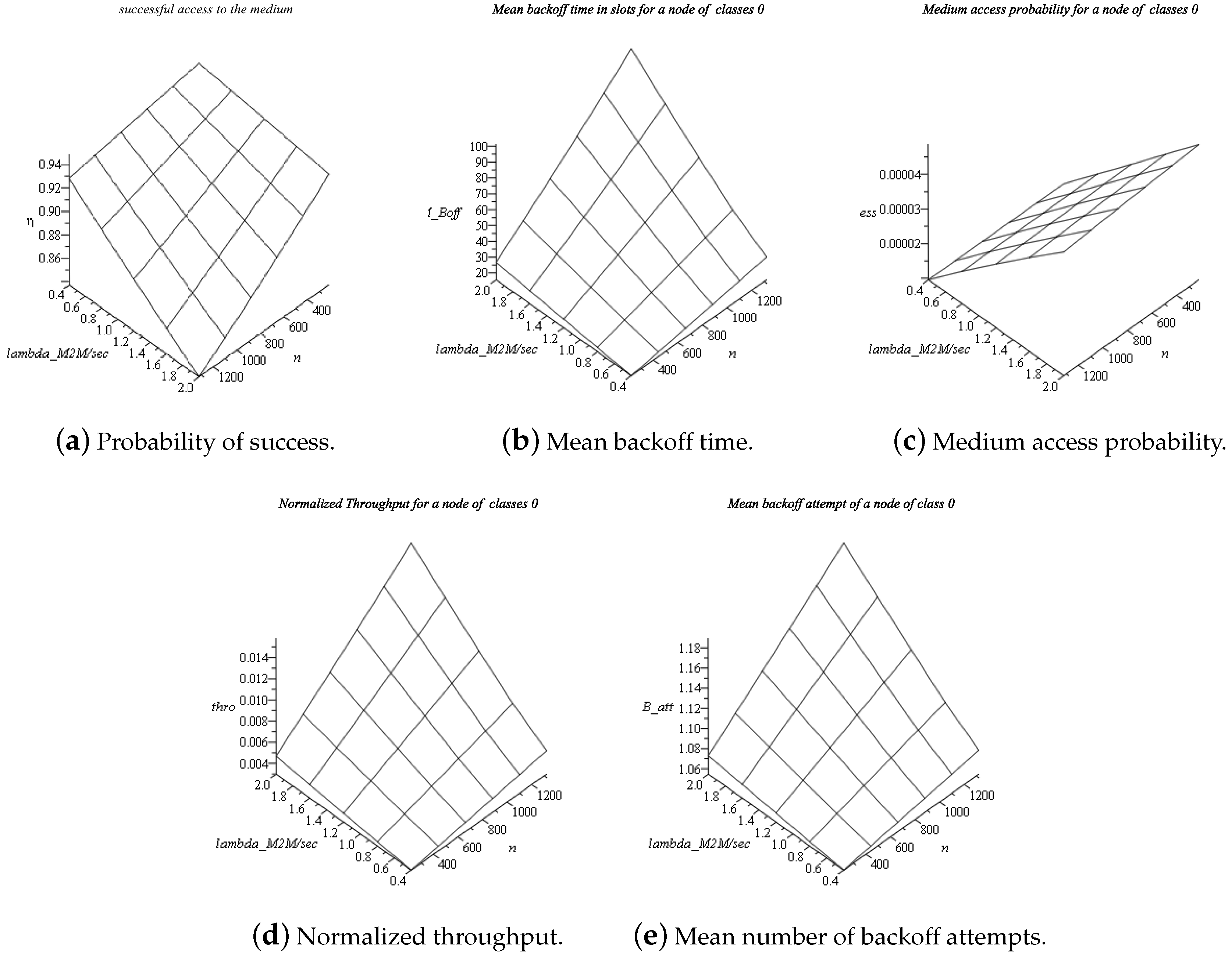
6.2. Performance of the PM2M Overlay Network without Backoff Error
6.3. Performance of the PM2M Overlay with Backoff Error
6.4. Discussion
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Mišić, V.B.; Mišić, J. (Eds.) Machine-to-Machine Communications—Architectures, Technology, Standards, and Applications; CRC Press: Boca Raton, FL, USA, 2014. [Google Scholar]
- Sesia, S.; Toufik, I.; Baker, M. LTE, the UMTS Long Term Evolution: From Theory to Practice; John Wiley & Sons: Hoboken, NJ, USA, 2009. [Google Scholar]
- Lien, S.Y.; Liau, T.H.; Kao, C.Y.; Chen, K.C. Cooperative access class barring for machine-to-machine communications. IEEE Trans. Wirel. Commun. 2012, 11, 27–32. [Google Scholar] [CrossRef]
- Cheng, J.P.; Lee, C.; Lin, T. Prioritized Random Access with Dynamic Access Barring for RAN Overload in 3GPP LTE-A Networks. In Proceedings of the 2011 IEEE GLOBECOM Workshops (GC Wkshps), Houston, TX, USA, 5–9 December 2011; pp. 368–372. [Google Scholar]
- Wu, H.; Zhu, C.; La, R.; Liu, X.; Zhang, Y. FASA: Accelerated S-ALOHA Using Access History for Event-Driven M2M Communications. IEEE/ACM Trans. Netw. 2013, 21, 1904–1917. [Google Scholar] [CrossRef]
- 3GPP. 3GPP TS 37.868 V11.0. Study on RAN Improvements for Machine Type Communications; Technical Report; 3GPP: Valbonne, France, 2011. [Google Scholar]
- Lo, A.; Law, Y.W.; Jacobsson, M.; Kucharzak, M. Enhanced LTE-Advanced Random-Access Mechanism for Massive Machine-to-Machine (M2M) Communications. In Proceedings of the 27th Meeting of Wireless World Research Forum (WWRF), Düsseldorf, Germany, 23–25 October 2011. [Google Scholar]
- Mišić, J.; Mišić, V.B.; Ali, M.Z. Explicit power ramping during random access in LTE/LTE-A. In Proceedings of the IEEE Wireless Communications and Networking Conference, San Francisco, CA, USA, 19–22 March 2017. [Google Scholar]
- Ali, M.S.; Hossain, E.; Kim, D.I. LTE/LTE-A random access for massive machine-type communications in smart cities. IEEE Commun. Mag. 2017, 55, 76–83. [Google Scholar] [CrossRef]
- Mišić, J.; Mišić, V.; Khan, N. Sharing It My Way: Efficient M2M Access in LTE/LTE-A Networks. IEEE Trans. Veh. Technol. 2017, 66, 696–709. [Google Scholar]
- Mišić, J.; Mišić, V. Wireless Personal Area Networks—Performance, Interconnections and Security with IEEE 802.15.4; John Wiley and Sons: Hoboken, NJ, USA, 2008. [Google Scholar]
- Mišić, J.; Mišić, V. Adapting LTE/LTE-A to M2M and D2D Communications. IEEE Netw. 2017, 31, 63–69. [Google Scholar] [CrossRef]
- Rashwand, S.; Mišić, J.; Mišić, V.B. Analysis of CSMA/CA Mechanism of IEEE 802.15.6 under Non-Saturation Regime. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 1279–1288. [Google Scholar] [CrossRef]
- Boccardi, F.; Heath, R.W.; Lozano, A.; Marzetta, T.L.; Popovski, P. Five disruptive technology directions for 5G. IEEE Commun. Mag. 2014, 52, 74–80. [Google Scholar] [CrossRef]
- 3GPP. 3GPP TS 36.321 V10.1.0. Medium Access Control (MAC) Protocol Specifications; Technical Report; 3GPP: Valbonne, France, 2011. [Google Scholar]
- 3GPP. 3GPP TS 36.331 V10.1.0. Radio Resource Specifications; Technical Report; 3GPP: Valbonne, France, 2011. [Google Scholar]
- Dahlman, E.; Parkval, S.; Skold, J. 4G: LTE/LTE-Advanced for Mobile Broadband; Academic Press: Cambridge, MA, USA, 2011. [Google Scholar]
- Wan, J.; Li, D.; Zou, C.; Zhou, K. M2M Communications for Smart City: An Event-Based Architecture. In Proceedings of the 2012 IEEE 12th International Conference on Computer and Information Technology, Chengdu, China, 27–29 October 2012; pp. 895–900. [Google Scholar] [CrossRef]
- Araniti, G.; Campolo, C.; Condoluci, M.; Iera, A.; Molinaro, A. LTE for vehicular networking: A survey. IEEE Commun. Mag. 2013, 51, 148–157. [Google Scholar] [CrossRef]
- Mir, Z.H.; Filali, F. LTE and IEEE 802.11p for vehicular networking: A performance evaluation. EURASIP J. Wirel. Commun. Netw. 2014, 1, 89. [Google Scholar]
- Vinel, A. 3GPP LTE Versus IEEE 802.11p/WAVE: Which Technology is Able to Support Cooperative Vehicular Safety Applications? IEEE Wirel. Commun. Lett. 2012, 1, 125–128. [Google Scholar] [CrossRef]
- Arora, A.; Rakesh, N.; Mishra, K.K. Analysis of Safety Applications in VANET for LTE Based Network. In Networking Communication and Data Knowledge Engineering; Perez, G.M.E., Ed.; Springer: Singapore, 2018; pp. 141–154. [Google Scholar]
- Abid, H.; Chung, T.C.; Lee, S.; Qaisar, S. Performance Analysis of LTE Smartphones-Based Vehicle-to-Infrastructure Communication. In Proceedings of the 2012 9th International Conference on Ubiquitous Intelligence and Computing and 9th International Conference on Autonomic and Trusted Computing, Fukuoka, Japan, 4–7 September 2012; pp. 72–78. [Google Scholar]
- Campolo, C.; Molinaro, A. Data rate selection in WBSS-based IEEE 802.11p WAVE vehicular ad hoc networks. In Proceedings of the 2010 7th International Symposium on Communication Systems, Networks and Digital Signal Processing, Newcastle upon Tyne, UK, 21–23 July 2010; pp. 412–416. [Google Scholar]
- Zaouiat, C.; Latif, A. Performances Comparison of IEEE 802.15. 6 and IEEE 802.15. 4. IJACSA Int. J. Adv. Comput. Sci. Appl. 2017, 8, 461–467. [Google Scholar]
- Hu, L.; Dung, O.M.; Liu, Q.; Han, T.; Sun, Y. Integration of Wireless Body Area Networks (WBANs) and WAN, WiMAX and LTE. KSII Trans. Internet Inf. Syst. 2013, 7, 980–997. [Google Scholar]
- Castel, T.; Lemey, S.; Agneessens, S.; Torre, P.V.; Rogier, H.; Oestges, C. LTE as a potential standard for public safety indoor body-to-body networks. In Proceedings of the 2015 IEEE Symposium on Communications and Vehicular Technology in the Benelux (SCVT), Luxembourg, 24 November 2015; pp. 1–6. [Google Scholar]
- Rashwand, S. Efficient Wireless Communication in Healthcare Systems; Design and Performance Evaluation. Ph.D. Thesis, The University of Manitoba, Winnipeg, MB, Canada, 2012. [Google Scholar]
- Cherkaoui, S.; Keskes, I.; Rivano, H.; Stanica, R. LTE-A random access channel capacity evaluation for M2M communications. In Proceedings of the 8th IFIP Wireless Days (WD 2016), Toulouse, France, 23–25 March 2016. [Google Scholar]


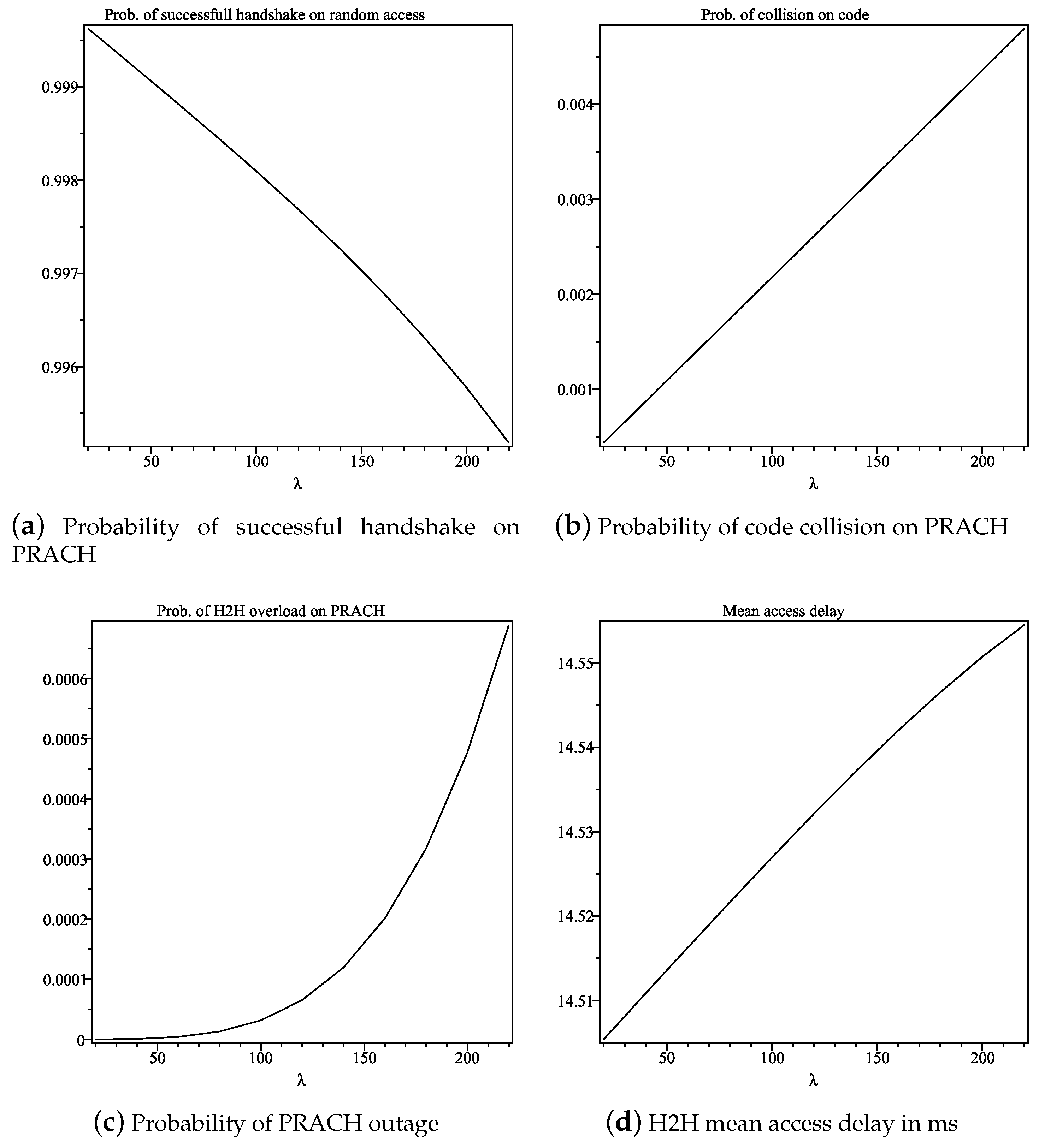


| UP | Traffic | ||
|---|---|---|---|
| 0 | Background (BK) | 16 | 64 |
| 1 | Best Effort (BE) | 16 | 32 |
| 2 | Excellent Effort (EF) | 8 | 32 |
| 3 | Controlled Load (CL) | 8 | 16 |
| 4 | Video (VI) | 4 | 16 |
| 5 | Voice | 4 | 8 |
| 6 | Network control | 2 | 8 |
| 7 | Emergency or medical event data | 1 | 4 |
| Parameter | Value |
|---|---|
| codes per cell, N | 64 |
| codes for H2H traffic, | 46 |
| codes for PM2M overlay traffic, | 8 |
| LTE frame duration | 540 overlay backoff periods |
| LTE system bandwidth | 5 MHz |
| PRACH bandwidth | W = 1.08 MHz |
| preamble length | 839 elements |
| preamble duration | 1600 s |
| preamble elements | = 16 |
| preamble format | 2 |
| RACH configuration index | = 5 |
| preamble element rate | = 1.048 M elements |
| traffic class | and |
| one backoff period | 18.51 s |
| superframe beacon interval | 540 backoff periods |
| PM2M superframe duration | 410 backoff periods |
| PM2M MAC data packet size | 150 bytes with header |
| Maximum number of attempts to transmit the packet, R | 7 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, N.; Mišić, J.; Mišić, V.B. Priority-Based Machine-To-Machine Overlay Network over LTE for a Smart City. J. Sens. Actuator Netw. 2018, 7, 27. https://doi.org/10.3390/jsan7030027
Khan N, Mišić J, Mišić VB. Priority-Based Machine-To-Machine Overlay Network over LTE for a Smart City. Journal of Sensor and Actuator Networks. 2018; 7(3):27. https://doi.org/10.3390/jsan7030027
Chicago/Turabian StyleKhan, Nargis, Jelena Mišić, and Vojislav B. Mišić. 2018. "Priority-Based Machine-To-Machine Overlay Network over LTE for a Smart City" Journal of Sensor and Actuator Networks 7, no. 3: 27. https://doi.org/10.3390/jsan7030027
APA StyleKhan, N., Mišić, J., & Mišić, V. B. (2018). Priority-Based Machine-To-Machine Overlay Network over LTE for a Smart City. Journal of Sensor and Actuator Networks, 7(3), 27. https://doi.org/10.3390/jsan7030027





