Abstract
This paper explores the integration of Internet of Things (IoT) devices into modern cybersecurity frameworks, and it is intended to be a binder for the incorporation of these devices into emerging cybersecurity paradigms. Most IoT devices rely on WPA2-personal protocol, a wireless protocol with known security flaws, being effortless to penetrate by using various specific tools. Through this paper, we proposed the use of two Raspberry Pi platforms, with the help of which we created a secure wireless connection by implementing the 802.1X protocol and using digital certificates. Implementing this type of architecture and the devices used, we obtained huge benefits from the point of view of security and energy consumption. We tested multiple authentication methods, including EAP-TLS and EAP-MSCHAPv2, with the Raspberry Pi acting as an authentication server and certificate manager. Performance metrics such as power consumption, latency, and network throughput were analysed, confirming the architecture’s effectiveness and scalability for larger IoT deployments.
1. Introduction
Wi-Fi authentication protocols ensure user identity verification and secure access to wireless networks. They have the role of preventing unauthorized access and securing the data transmitted. The different authentication methods vary depending on the level of protection offered, the complexity of the implementation and the specific requirements of the networks. In general, an effective authentication protocol must guarantee data confidentiality, integrity, and availability. The choice of a protocol is influenced by factors such as device compatibility, ease of use, and the desired level of security. The proper implementation of an authentication protocol helps to reduce vulnerabilities and protect networks against cyber-attacks.
Although we can connect devices both wired and wirelessly, the vast majority of IoT devices are connected wirelessly for mobility and the lack of wires being a much more convenient way. Wireless connections are important because Wi-Fi is the second most important thing that people do not want to live without [1]. As wireless technology continues to evolve, ensuring secure authentication mechanisms becomes crucial for protecting sensitive data and maintaining network integrity. Modern Wi-Fi authentication protocols, such as WPA3-Enterprise with EAP-TLS, provide enhanced encryption and mutual authentication between clients and authentication servers. The use of digital certificates further strengthens security by eliminating the risks associated with password-based authentication. In addition, integrating blockchain-based identity verification can add an extra layer of protection by ensuring that device credentials remain immutable and tamper-proof.
For IoT ecosystems, where thousands of devices need to authenticate seamlessly, automated certificate management and blockchain verification can simplify administration and reduce the risk of credential compromise [2]. Organizations deploying Wi-Fi authentication solutions must carefully balance security, scalability, and usability to ensure a robust and efficient system. Continuous monitoring and real-time anomaly detection can further enhance security by identifying potential threats before they escalate. As technology advances, adopting innovative authentication mechanisms will be essential to safeguarding wireless communications against emerging cyber threats. In the context of a relevant secure communication architecture for IoT devices, a proxy server-based solution is described in [3]. The Raspberry Pi 4 Model B, which has 8 GB of storage, is the basis of the plan. The device serves as a proxy server through two network interfaces: one for the internal local network and another for connecting to the Internet. The user-selected operation mode determines whether the electronic system transmits data in clear or encrypted format to the receiver.
Although there are several solutions proposed for securing IoT [4,5,6,7], in which different algorithms are proposed for securing connections [8,9,10], we come up with a solution for securing IoT by adopting a design in which we implement the WiFi Enterprise protocol using Raspberry PI boards and with the implementation of digital certificates.
According to Cisco estimates, the number of hotspots will exceed 500 million globally [11]. But the benefits also come with security issues. The WPA2 protocol is the most widely accepted and used, but it presents great vulnerabilities that can be exploited very easily and with minimal resources [12,13].
Securing IoT devices presents unique challenges due to limited computational re-sources, heterogeneity of devices, and the need for scalable, low-latency communication. Several state-of-the-art methods have been proposed to address these issues. Below is a comparison between the proposed Raspberry Pi-based 802.1X authentication system and other leading solutions:
- Compared to other state-of-the-art solutions for securing IoT devices, the architecture proposed in this work—based on two Raspberry Pi boards, the 802.1X protocol, and digital certificate-based authentication—offers a highly effective balance between security, affordability, and ease of deployment.
- Blockchain-based security mechanisms provide strong protection through decentralized identity management and immutable transaction logs. However, these solutions often require higher processing power and increased energy consumption, making them less suitable for resource-constrained IoT environments. Additionally, the complexity of implementing blockchain in existing networks can be a barrier for many organizations.
- Cloud-based IoT security platforms (such as AWS IoT or Azure IoT Hub) are known for their scalability, centralized certificate management, and rich access control features. Despite their advantages, they depend on constant internet connectivity and introduce a degree of vendor lock-in. For sensitive or isolated networks—such as those in industrial or critical infrastructure contexts—the proposed local, offline-capable solution is more suitable.
- Lightweight encryption approaches, such as DTLS or CoAP with OSCORE, are designed for extremely constrained devices, offering low overhead and efficient performance. However, they typically rely on pre-shared keys and do not support robust mutual authentication. This can make them vulnerable to spoofing and replay at-tacks. In contrast, your system leverages EAP-TLS and digital certificates to achieve strong identity verification and encryption without relying on weak credentials.
- Zero Trust architectures, which implement continuous authentication, strict access segmentation, and real-time monitoring, proposed solution is far more accessible and easier to implement. While Zero Trust is highly effective for enterprise-level networks, it requires complex infrastructure and significant maintenance overhead, which are often unnecessary for small or medium-scale IoT deployments.
The contributions arising from this research bring more security to wireless connections by implementing the 802.1.X protocol, and secure connection is created based on the use of digital certificates even if the devices connected to the network are not capable of connecting via this protocol. By adopting this design, the WPA2 protocol is avoided, and we propose that for future networks, it be used globally because it brings increased security with minimal resources especially where there is no possibility of making wire connections, and high security is required. The traditional WPA2 protocol, while widely used, has known vulnerabilities [14], particularly in personal mode, which can be exploited using various attack methods such as dictionary or brute force attacks. In contrast, the use of the 802.1X protocol combined with digital certificates ensures robust mutual authentication [15] and strong encryption, making it significantly more resistant to such attacks.
One of the most significant advantages of this approach is enhanced security. Unlike shared passwords (as used in WPA2-Personal), digital certificates enable mutual authentication between clients and servers, ensuring that both parties are legitimate. This drastically reduces the risk of man-in-the-middle attacks, credential theft, and brute-force attempts. Additionally, certificates are not susceptible to replay attacks, and their expiration and revocation can be centrally managed, offering long-term security governance. Another benefit is the scalability in secure environments—once the certificate infrastructure is in place, onboarding new devices becomes a secure and automated process without the need to distribute passwords. The proposed solution presents a secure, low-cost, and flexible alternative that can be deployed in environments where traditional protocols like WPA2-Personal are insufficient, and where more complex systems like blockchain or Zero Trust would be excessive. It is particularly well suited for retrofitting legacy IoT devices with enhanced security, while maintaining simplicity and energy efficiency.
The paper is structured as follows. Section 1 provides the main purpose of this paper and a brief overview of the importance of using the proposed design in wireless connections. Section 2 describes the materials and protocols used in the proposed design. Section 3 is dedicated to the results obtained. Section 4 is for discussions based on the tests performed and the results obtained. Finally, Section 5 is for conclusions and perspectives of this work.
2. Materials and Methods
2.1. Fundamentals of the Security Protocols
The Extensible Authentication Protocol-Microsoft Challenge Handshake Authentication Protocol version 2 (EAP-MSCHAPv2) [1] is an authentication protocol used within Extensible Authentication Protocol (EAP) that provides authentication between a server and a client. It uses a challenge-response mechanism to validate a user’s identity without sending passwords directly over the network. It is commonly used in Microsoft’s RADIUS server implementations, such as in VPN and Wi-Fi networks (Figure 1).
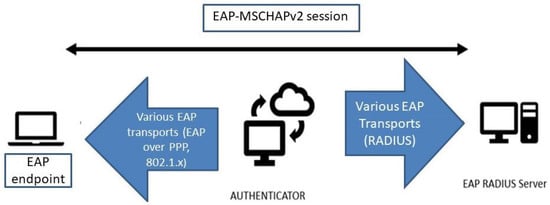
Figure 1.
EAP MSCHAPv2 method.
The Extensible Authentication Protocol-Message Digest 5 (EAP-MD5) is an authentication protocol that uses the MD5 hash function to validate the user. This is an implementation of EAP where the client sends a hash of the password to the server, where the validity of the hash is checked (Figure 2). Although it provides basic authentication, it has significant security weaknesses, as MD5 is considered a weak cryptographic algorithm and vulnerable to collision attacks [16].
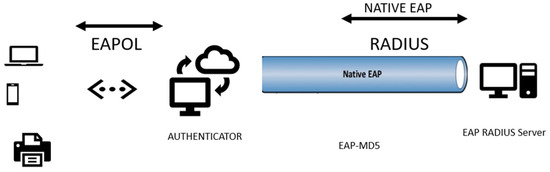
Figure 2.
EAP MD5 method.
The Extensible Authentication Protocol-Password Authentication Protocol (EAP-PAP) transmits passwords in plaintext, without encryption [16]. It is simple to implement, but extremely insecure.
The main features are as follows:
- Fast authentication—ideal for environments that require simple and fast security;
- Vulnerabilities—exposed to attacks;
- Deprecated—has been replaced by more secure protocols such as EAP-TLS.
Extensible Authentication Protocol-Transport Layer Security (EAP-TLS) is a cryptographic protocol essential for ensuring secure communication over a network. It is widely used to protect data between devices (Figure 3). EAP-TLS operates at higher levels of the OSI model, specifically between the application layer and the transport layer.
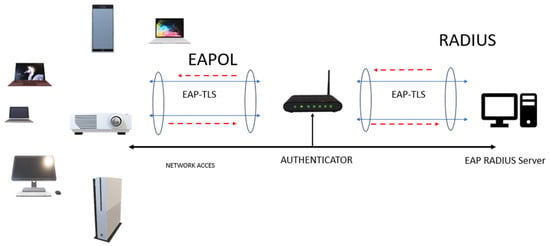
Figure 3.
EAP TLS method.
The most important features are as follows:
- Data encryption—ensures confidentiality by protecting data so that it cannot be intercepted;
- Integrity—guarantees that data has not been modified during transmission;
- Authentication—confirms the identity of the parties involved in communication.
Iperf3 is a software tool that can be used to determine the properties and performance of a connection. It can test using both TCP and UDP and allows one to send patterned packets between devices to accurately determine bandwidth, speed, packet loss, and other useful parameters [17].
2.2. Design of the Proposed Secure Communication Architecture
In this work, the IoT security system was developed using two Raspberry Pi devices. The FreeRadius server, which is used to authenticate clients in the Wi-Fi network, is housed on the first board. Wireless IoT devices that cannot run the 802.1X protocol will be connected to the second board.
To demonstrate the utility and benefits brought by the proposed system and the architecture used, we implemented several types of protocols as shown in Figure 4, which highlights the types of connections and types of devices.
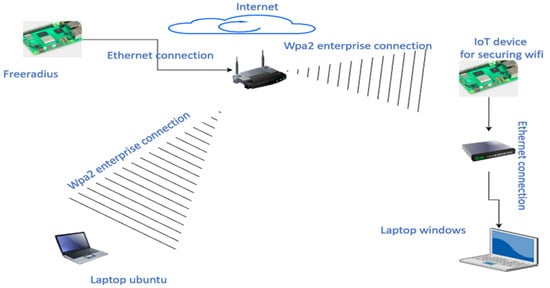
Figure 4.
Proposed security system topology.
To measure the properties of the connections made, we used Iperf3. It is worth noting that at the device level for securing Wi-Fi, we created a bridge through which we logically connected the wireless network card with the ethernet network card, and in this way, the packets are forwarded at layer 2. Thus, with the help of the wireless network card, we communicate via the 802.1X protocol with the wireless network and with the help of the ethernet network card we can connect to any type of device capable of communicating through such a connection.
Our newly developed approach for secure IoT connections utilizes the 802.1X protocol and the Raspberry Pi development platform, ensuring connectivity through these protocols (as shown in Figure 5). Through it, the connection to the Wi-Fi network of devices that do not have the capability to use the 802.1X protocol is achieved.
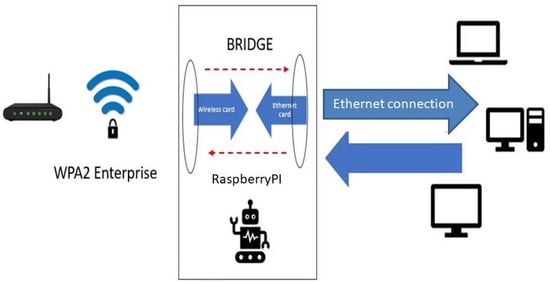
Figure 5.
Logical bridge between wireless board and ethernet board.
To test the connection made in this way, we used a laptop with a Windows operating system, used to implement Iperf3, which can later be replaced with any IoT (smart TV, printers) or any other device that communicates via ethernet.
With the help of the two Raspberry Pi boards, we made the connection using the 802.1X protocol integrating several types of encryptions. The first board was used to implement FreeRadius, and the second one was used to make the secure connection, calling it a “Wi-Fi security device”.
We tested the connection between the Ubuntu laptop and the Windows laptop using Iperf3 and the ICMP protocol and compared the properties of the connection using the different types of encryptions.
To create the testing framework, we created the setup, consisting of two Raspberry Pi boards (one for hosting FreeRadius and the other as a device for establishing a secure connection), a router received from the Internet Service Provider, and two laptops (one with Ubuntu operating system that connected to the network via the 802.1X protocol and the other with Windows operating system that was set up as IoT). Figure 6 illustrates the fundamental scheme regarding the operation of the proposed security system.
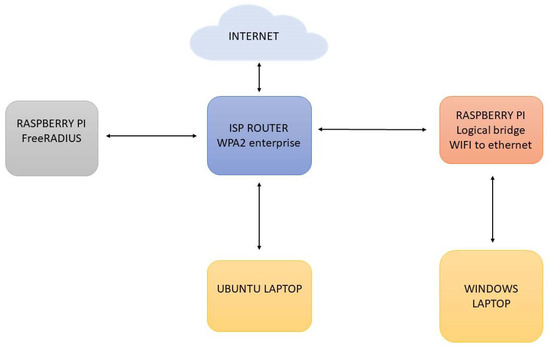
Figure 6.
General operation of the proposed security system.
To begin with, we created the connection using the EAP-MSCHAPv2 protocol because it is simpler to implement. This method allows authentication using username and password credentials, making it easier to integrate with existing network infrastructures. However, while EAP-MSCHAPv2 provides a reasonable level of security, it remains vulnerable to certain attacks, such as credential interception if not properly configured with server certificate validation. Without additional protections, attackers could exploit weaknesses in the protocol, such as performing offline password cracking attacks if the credentials are captured during the authentication process.
To mitigate these vulnerabilities, it is essential to configure the network to use server certificate validation, ensuring that the client verifies the authenticity of the authentication server. This helps to prevent man-in-the-middle attacks, where an attacker might impersonate the server to intercept credentials. However, even with this protection, EAP-MSCHAPv2 is considered less secure compared to more advanced protocols, such as EAP-TLS, which uses digital certificates for mutual authentication.
Authenticating the Ubuntu laptop, using the 802.1X protocol, is performed by entering credentials assigned to each user, as shown in Figure 7, as opposed to sharing a password among multiple users as is the case with the WPA2 Personal protocol [18].
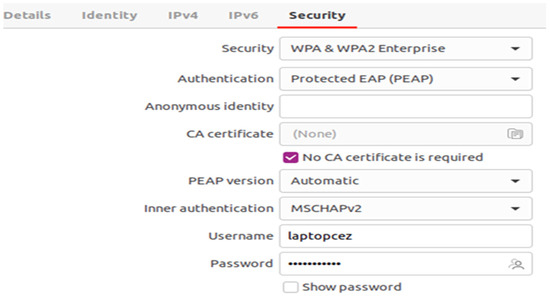
Figure 7.
Performing network authentication on Ubuntu laptop.
A major difference between the two protocols (WPA2 Personal and WPA2 Enterprise) already appears in the use of a username and password for each device that will be authenticated by the network. During the tests, we used several types of authentications to establish the connection, and we conducted multiple performance evaluations using Iperf3, a network-testing tool that measures throughput, jitter, and packet loss.
3. Results
In this section, we run experiments, collect data, and analyse the findings to assess the previously defined and implemented IoT security solution. Figure 8 shows the practical security system created and used for testing. The IoT security solution was tested using a Raspberry Pi board with CPU architecture Cortex-A72, 64 bits, frequency: 1.5 GHz, CPU with 4 cores and 4 GB of RAM memory with FreeRadius (1), a laptop with an Intel I3 processor and Ubuntu operating system (2), a laptop with an Intel I5 processor and Windows operating system (3), a second Raspberry Pi board with the same specifications as the first (4), and a dual-band AP router from ISP with a speed of up to 300 Mbps (5).

Figure 8.
Interconnection of the components of the entire security system that has been tested in the laboratory.
With the developed IoT security system shown in the above figure, under identical setup, we tested several authentication methods using UDP and TCP.
3.1. Results Obtained in UDP
In UDP, the bit rate was constant at 1.05 Mbit/s throughout the test, indicating a stable connection; also, there were no datagram losses at either the sender and receiver ends, suggesting reliable transmission. Jitter was minimal (0.000 ms at the sender and 0.280 ms at the receiver), indicating a consistent and predictable latency. With Iperf3, we determined the properties of the connection achieved by implementing several authentication protocols using both TCP and UDP. It can be seen from Figure 9 that Iperf3 was used to determine the connection between the Ubuntu laptop and the Windows laptop, which was used as an IoT device, solely for the purpose of identifying the properties of the connection.
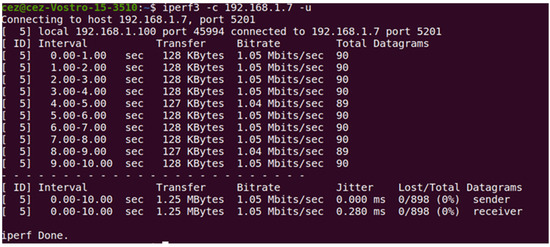
Figure 9.
Jitter determination using Iperf3 on a UDP connection between the two devices, Ubuntu and Windows, when EAP-TLS is used.
The constant transfer rate of 1.05 MB/sec and the very low jitter (0.280 ms) indicate a stable and well-configured network. The lack of packet loss confirms that the network is reliable and has no congestion or interference issues. The result shows that implementing EAP-TLS does not impact network performance even though it is only a test network. As can be seen in Figure 10 comparing the results of the protocols when UDP is used, it appears that the protocol that offers the highest security (EAP-TLS) also achieves very good results when is used. This is an important observation, as security and efficiency are often seen as trade-offs in network authentication.
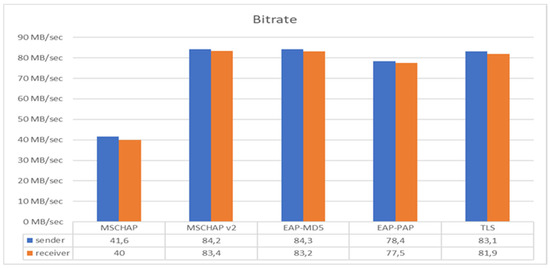
Figure 10.
Bitrate with different EAP protocols in UDP.
Despite its complex cryptographic mechanisms, EAP-TLS ensures not only strong mutual authentication but also efficient data transmission, minimizing delays in the authentication process. The use of UDP for authentication traffic further enhances performance by reducing overhead compared to TCP-based alternatives. This is particularly beneficial in high-density environments where a large number of devices need to authenticate simultaneously. Additionally, the robustness of EAP-TLS against attacks, such as man-in-the-middle and credential theft, makes it the preferred choice for securing enterprise and IoT networks. With the help of this test, the quality of transmission in the network is determined. Although the system performed well in the test environment, it is important to acknowledge that these results are based on a controlled experimental setup. As such, while they demonstrate the feasibility of the proposed approach, the findings must be further validated in more complex and dynamic real-world networks.
From Figure 11 it results that the protocols with the best performance following this test are EAP-MD5 and EAP-TLS.
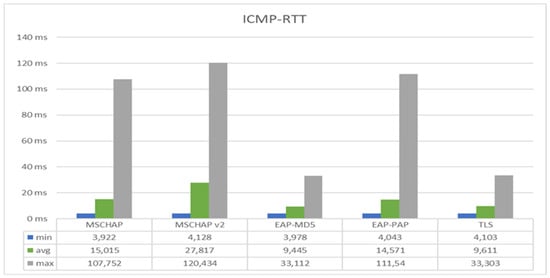
Figure 11.
ICMP-RTT with different EAP protocols in UDP.
Protocols with complex authentication processes can introduce higher jitter during configuration. Considering that in a network, a jitter of less than 30 ms is required for the proper functioning of sensitive applications (VoIP or videoconferencing) [19], as shown in Figure 12 during the test, everything behaves very well, but it must be taken into account that it is only a test environment. In real-world scenarios, additional latency might be introduced by external variables, including network load, authentication server performance, and certificate verification times. While EAP-TLS ensures a high level of security, its impact on jitter should be carefully monitored, especially in environments requiring real-time communication.
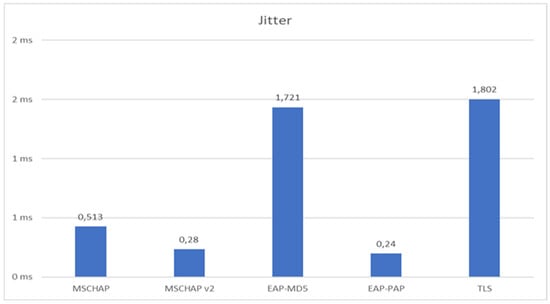
Figure 12.
Jitter with different EAP protocols in UDP.
3.2. Results Obtained in TCP
Using Wireshark, as shown in Figure 13, it is observed how the Ubuntu laptop authenticates to the WiFi network via TLS. The process begins with the client sending an EAP-Request message to the authentication server, followed by the server responding with an EAP-Response, requesting the client’s certificate for verification. During this phase, the laptop’s certificate is exchanged and validated by the authentication server. Once the server successfully verifies the certificate, a secure TLS tunnel is established, and the encrypted session begins.
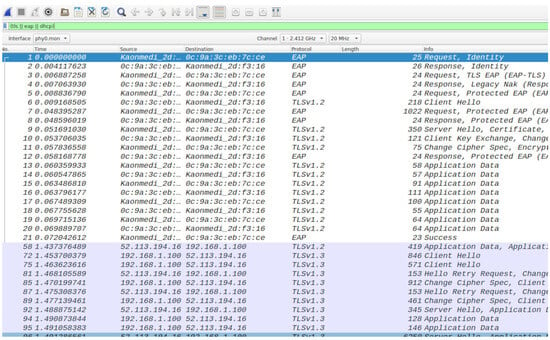
Figure 13.
Ubuntu laptop authentication via TLS protocol.
The Wireshark capture shows the exchange of the server’s certificate, the validation process, and the negotiation of encryption keys used to secure the connection. The results are presented in Figure 14.
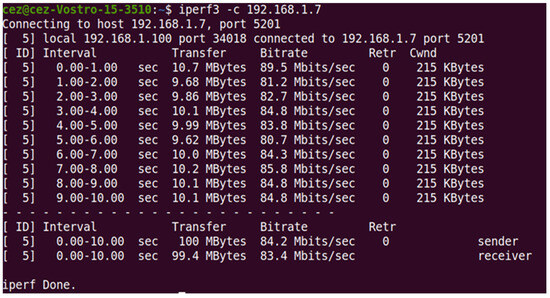
Figure 14.
Determining connection properties using Iperf3 on TCP connection and EAP-MD5 protocol between the two devices: Ubuntu and Windows.
In TCP, the bit rate was constant, ranging between 81.2 and 89.5 Mbit/sec throughout the test. There were no retransmissions, suggesting reliable and efficient transmission. The congestion window size remained constant at 215 Kbytes, indicating a well-managed network and no significant packet loss. These results confirm that the network infrastructure can sustain high data rates while maintaining reliability, which is crucial for real-time authentication mechanisms such as EAP-TLS. A stable congestion window implies that the TCP flow control mechanism is functioning optimally, preventing unnecessary retransmissions and ensuring smooth communication between authentication servers and clients.
As can be seen in Figure 15, the best results were obtained through the EAP-MD5 protocol, and the lowest result was obtained through the MSCHAP protocol. Regarding the results obtained through the MSCHAPv2, EAP-PAP and TLS protocols, it can be observed that they also have good results in terms of transfer. Regarding the results obtained through the MSCHAPv2, EAP-PAP, and TLS protocols, it can be observed that they also deliver good results in terms of transfer speed. While MSCHAPv2 offers a more secure alternative to MSCHAP, it still presents some performance trade-offs compared to EAP-MD5. EAP-PAP, despite being a relatively simple protocol, is susceptible to attacks and lacks strong encryption, which may hinder its suitability in environments where robust security is required.
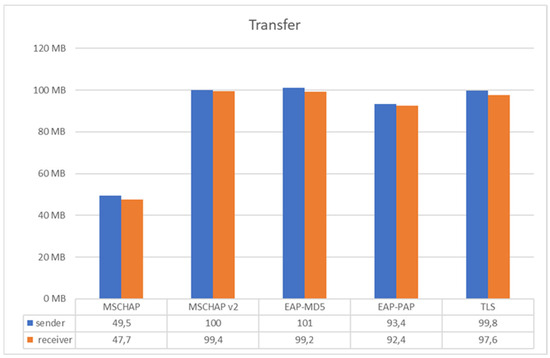
Figure 15.
Transfer with different EAP protocols in TCP.
In Figure 16, using Iperf3 in reverse mode, it is observed that the protocol with the worst results is EAP-PAP and the protocol that offers the highest security, namely TLS, has very good results compared to the other protocols. It should be added that by this method, Iperf3 also measures the flux transmitted from the receiver to the transmitter. It should be noted that, in this mode, Iperf3 also measures the data flow transmitted from the receiver to the transmitter. This aspect is particularly important when evaluating the bidirectional impact of authentication mechanisms on network performance. Since EAP-TLS relies on certificate-based authentication rather than password exchange, it minimizes retransmissions and ensures a smoother data flow. EAP-TLS, as expected, provides the highest level of security, offering excellent encryption and authentication, though it may involve higher computational overhead compared to simpler protocols. Despite this, it still performs relatively well in terms of data transfer, particularly when considering its significant security advantages. This balance of security and performance makes EAP-TLS a strong candidate for environments requiring both high performance and robust protection.
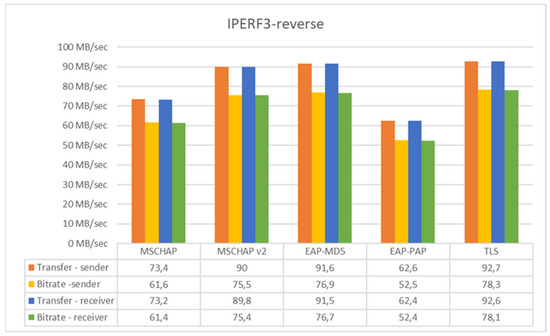
Figure 16.
Results with IPERF3 in reverse mode on TCP.
4. Discussion
As we showed in the results section, our approach increases the security of the devices used in the topology and is simple to use because it is built on Raspberry Pi boards, which are also reasonably priced. Also, the TLS protocol is a far more secure and quick authentication mechanism, even though EAP-PAP is easier to deploy, according to the tests conducted and the findings obtained.
4.1. Benefits of the Proposed Approach
Although the introduction of digital certificates is more difficult to implement for device authentication, it does not cause any other problems later and this fact becomes negligible considering the security implemented [20]. Considering the results obtained, it is observed that by implementing this type of architecture in the wireless environment there are many benefits brought on several levels:
- The energy consumed is insignificant because two Raspberry Pi platforms are used, and they are recognized for their low energy consumption [21].
- The two platforms cost around EUR 200, and the software used is open source, which determines zero additional costs (Raspbian, FreeRadius, Open-source Secure Sockets Layer (OpenSSL)).
- The system has very high security by implementing digital certificates in the topology [22] for authentication and encryption. Each device attempting to connect will be required to present a valid certificate issued by a trusted Certificate Authority (CA). This ensures that only authorized users and devices can access the network, mitigating the risk of unauthorized access. The certificates will be used in conjunction with EAP-TLS for WiFi authentication, providing mutual authentication between clients and the authentication server. Additionally, private keys associated with the certificates will be securely stored, preventing theft or misuse. The use of certificates eliminates reliance on passwords, which are more susceptible to attacks such as phishing or brute force. The entire certificate lifecycle, including issuance, renewal, and revocation, will be care-fully managed to maintain security. Integration with a blockchain-based verification mechanism will further enhance trust by ensuring certificate integrity. The FreeRadius server will handle certificate validation, rejecting any expired or untrusted certificates.
- With the help of this architecture, a secure connection is achieved where it is impossible to use any type of cables.
- It can secure IoT devices that do not have the possibility of connecting by implementing digital certificates. For example, most televisions, although they are considered “smart-tv” do not offer the possibility of making a connection by introducing digital certificates [20].
To substantiate the claim that the proposed solution exhibits low energy consumption, we assessed the power draw of the Raspberry Pi 4 Model B, which serves as the foundation of our architecture. According to empirical measurements and manufacturer specifications, Raspberry Pi 4 (4 GB model) typically consumes between 2.7 and 3.5 watts at idle, with peaks up to 6.4 watts under full CPU load [22]. This results in an estimated daily energy usage of approximately 0.06 to 0.15 kWh depending on the operating conditions, equating to roughly 216 to 540 kilojoules per day per device. For both boards used in our architecture, the combined consumption remains below 1.1 kWh per week, making it significantly more energy-efficient than traditional x86-based servers or enterprise-grade network appliances typically used for authentication tasks, which can consume 10–25 watts continuously [22]. In contrast, ESP32-based boards such as NodeMCU or Wemos D1 Mini are even more power-efficient, drawing only 0.08 to 0.15 watts during active processing and as little as 0.01 watts in deep sleep mode, translating to less than 0.005 kWh per week under typical IoT conditions [5]. However, while these microcontrollers are ideal as low-power clients in IoT applications, they lack the necessary CPU performance, memory, and Linux-based environment required to run a FreeRADIUS server or manage complex authentication mechanisms like EAP-TLS or PEAP [7]. Consequently, although ESP32 platforms offer unmatched energy efficiency for edge devices, the Raspberry Pi-based setup strikes a balance between energy consumption and computational capabilities, making it a viable and scalable solution for handling secure certificate-based authentication in small to medium-sized IoT networks.
4.2. Limitations in Deployment Environments
While the proposed architecture demonstrated strong performance in terms of authentication security and energy efficiency, a critical limitation observed during testing was the system’s scalability—specifically, its capacity to handle a large number of simultaneous device connections. When exceeding approximately 20 connected devices, noticeable congestion occurred, particularly at the authentication and certificate verification stages managed by the Raspberry Pi running the FreeRADIUS server. This congestion is manifested in several ways: increased latency during device authentication, longer connection setup times, and even occasional authentication timeouts. These issues are primarily due to the limited hardware resources of the Raspberry Pi board, including constrained CPU and memory capacity. Unlike enterprise-grade RADIUS servers, which are optimized for high concurrency and parallel processing, the Raspberry Pi has limited multitasking capabilities, making it less efficient at handling a large volume of authentication requests simultaneously. Additionally, as more devices attempt to authenticate and maintain secure sessions, the network interface and internal queue buffers of the Raspberry Pi become saturated, leading to packet drops and retransmissions. These effects were observed in Iperf3 tests as increased jitter and reduced throughput under high load conditions. Another factor contributing to this scalability issue is the overhead introduced by EAP-TLS. While this protocol offers superior security through mutual certificate-based authentication, it is computationally intensive, involving asymmetric cryptographic operations such as certificate parsing and signature verification. These processes consume significant CPU time, particularly when multiple handshakes occur in parallel.
Wi-Fi Coverage and Signal Stability: The effectiveness of the 802.1X based secure connection depends heavily on stable and strong Wi-Fi coverage. In larger or structurally complex buildings, signal attenuation may lead to intermittent connectivity, increased latency, or even authentication failure.
Compatibility with Legacy Devices: While our architecture allows non-802.1X-capable devices to connect securely via the Ethernet interface of a Raspberry Pi bridge, it assumes that these legacy devices sup-port standard Ethernet protocols. Devices with proprietary communication stacks or those requiring specialized drivers may not function properly without additional configuration.
Administrative and Network Setup Requirements: Deploying this solution in enterprise environments requires administrative privileges and technical expertise to configure FreeRADIUS, set up 802.1X certificates, and maintain the associated Certificate Authority. This could present a barrier to adoption in environments lacking specialized IT staff.
Hardware Constraints and Scalability: The Raspberry Pi, though cost-effective and versatile, has hardware limitations related to processing power, memory, and network throughput. As the number of connected devices increases, or as traffic volume intensifies, performance bottlenecks may occur. For large-scale deployments, we recommend upgrading to more powerful edge computing platforms or distributing the load across multiple nodes.
To mitigate these limitations, several potential solutions may be considered in forthcoming developments:
- Offloading authentication to a more powerful server or cloud-based FreeRADIUS implementation while retaining the Raspberry Pi as a bridge device.
- Load balancing between multiple Raspberry Pi units to distribute authentication requests more evenly.
- Lightweight alternatives such as EAP-FAST or pre-authenticated device provisioning for static IoT environments with known devices.
Despite this limitation, for small to medium IoT networks—such as smart homes, small offices, or labs—this solution remains highly practical. It offers a secure, manageable alternative to WPA2-Personal, with the added benefit of centralized certificate management and per-device access control. The proposed architecture is particularly beneficial in smart home labs, small offices, and educational settings, where budget constraints and security demands coexist. However, scaling the architecture beyond this point will require additional infrastructure enhancements or hardware upgrades.
Overall, this discussion highlights a key trade-off between security and scalability, emphasizing the importance of aligning architectural choices with the intended scale and performance needs of the IoT deployment. The results presented should, therefore, be interpreted with this limitation in mind. Generalizing these findings to larger-scale or dense IoT networks—such as those found in smart cities, large industrial environments, or massive sensor deployments—requires caution. For instance, in a high-density IoT environment, congestion and resource contention would likely introduce additional performance bottlenecks, particularly when it comes to device authentication and concurrent certificate validation. The Raspberry Pi’s limited processing power could become a major constraint under heavy loads, impacting both latency and authentication throughput. Therefore, while the architecture demonstrated strong security and efficiency for small networks, additional optimization—such as load balancing, hardware upgrades, or distributed authentication solutions—would be necessary for large-scale deployments.
The proposed architecture offers a foundation that could be scaled up, but it should be seen as a starting point for future investigations rather than a definitive solution for all IoT scenarios. Further testing in more realistic, dense IoT environments is required to fully understand the behaviour of the system under these conditions. The challenges faced in such contexts may require specialized strategies to handle the sheer volume of authentication requests, data traffic, and device management.
5. Conclusions
In this paper, we proposed a solution for a secure wireless connection by implementing the 802.1X protocol and using digital certificates. To achieve these goals, two Raspberry Pi platforms were used both as the authentication server and also as the central point for certificate management. In this way, we obtained a modular and extensible solution that could be adapted to slightly larger IoT deployments within constrained environments, such as smart labs or small offices, while maintaining acceptable performance. The logic of this work is that by implementing this type of design, cables can be eliminated and the IoT devices that do not support the 802.1X protocol can be connected in a secure way. This solution is very useful in the current context of Wi-Fi security and could be successfully implemented in large companies with the caveat that with more than 20 devices, this solution also has a weakness in the sense that congestion occurs and another access point is needed to authenticate more devices and to create a command mechanism for management of network [23]. The results of this study should be applied with consideration to the scale of deployment, and we recommend further experiments in real-world IoT ecosystems with varying densities to validate the scalability and robustness of the proposed solution.
In the near future, we plan to continue this work by introducing device authentication through a blockchain-based solution for device identity verification. Each device will be issued a unique digital certificate, whose hash will be stored immutably on a private blockchain. During authentication, the FreeRadius server will query the blockchain to verify the certificate’s validity before granting access. This eliminates the risk of certificate forgery or unauthorized modifications, as all records are cryptographically secured. This approach significantly strengthens security while maintaining efficiency in large-scale networks. By leveraging blockchain for authentication, we also reduce the risks associated with traditional centralized identity management systems, and, ultimately, this will provide a scalable and future-proof solution for secure Wi-Fi access and the proposed system could be integrated into an e-learning platform where even students who are unable to travel can study this type of approach as well as others [24]. To strengthen the validity of our conclusions, we plan to expand our evaluation in future work by including large-scale deployments with heterogeneous devices and real-world interference conditions. Additionally, we intend to incorporate long-term performance tracking, more granular latency measurements across authentication events, and comparative benchmarking with alternative security schemes.
Author Contributions
Both authors, C.-G.D. and P.A., contributed collaboratively to all stages of this research, from the conceptualization of the secure communication architecture to the development of the application and the testing and validation of the results, as well as writing the paper. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no funding.
Data Availability Statement
The original contributions presented in this study are included in the article.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| AAA | Authentication Authorization and Accounting |
| AES | Advanced encryption standard |
| AP | Access Point |
| CHAP | Challenge Handshake Authentication Protocol |
| CLI | Command line interface |
| EAP | Extensible Authentication Protocol |
| EAP-MD5 | Extensible Authentication Protocol—Message Digest Algorithm 5 |
| EAP-TLS | Extensible Authentication Protocol—Transport Layer Security |
| EAP-TTLS | Extensible Authentication Protocol—Tunnelled Transport Layer Security |
| ICMP | Internet control message protocol |
| IoT | Internet of Things |
| IIoT | Industrial Internet of Things |
| IPsec | Internet Protocol Security |
| LDAP | Lightweight Directory Access Protocol |
| MS-CHAP | Microsoft version of the Challenge-Handshake Authentication Protocol |
| PAP | Password Authentication Protocol |
| PEAP | Protected Extensible Authentication Protocol |
| RADIUS | Remote Authentication Dial in User Service |
| SSL | Secure Sockets Layer |
| TCP | Transport control protocol |
| UDP | User Datagram Protocol |
| WI-FI | Wireless Fidelity |
| WPA2 | Wi-Fi Protected Access |
| WPA2-PSK | Wi-Fi Protected Access Pre-Shared Key |
References
- Kampourakis, V.; Chatzoglou, E.; Kambourakis, G.; Dolmes, A.; Zaroliagis, C. WPAxFuzz: Sniffing Out Vulnerabilities in Wi-Fi Implementations. Cryptography 2022, 6, 53. [Google Scholar] [CrossRef]
- Marian, C.V. DNS Records Secure Provisioning Mechanism for Virtual Machines automatic management in high density data centers. In Proceedings of the IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Bucharest, Romania, 24–28 May 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Anghelescu, P. Design and Implementation of an Electronic Encryption System Based on Programmable Cellular Automata Algorithm. In Proceedings of the The 47th International Spring Seminar on Electronics Technology (ISSE), Prague, Czech Republic, 15–19 May 2024; pp. 1–4. [Google Scholar] [CrossRef]
- Fan, S.; Wang, J. Multi-dimension-precision chaotic encryption mechanism for Internet of Things. Internet Things 2024, 26, 101202. [Google Scholar] [CrossRef]
- Zhang, B.; Zhang, T.; Xi, Z.; Chen, P.; Wei, J.; Liu, Y. Secure Device-to-Device Communication in IoT: Fuzzy Identity from Wireless Channel State Information for Identity-Based Encryption. Electronics 2024, 13, 984. [Google Scholar] [CrossRef]
- Velmurugan, P.; Senthil Kumar, K.; Sridhar, S.S.; Gotham, E. An advanced and effective encryption methodology used for modern IoT security. Mater. Today 2023, 81, 389–394. [Google Scholar] [CrossRef]
- Cezar, D.; Gheorghe, G.; Gabriel, P.; Mariuca-Roxana, G. Device For Securing IoT In The Wireless Environment. In Proceedings of the 16th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Iasi, Romania, 27–28 June 2024. [Google Scholar] [CrossRef]
- Ahmad, N.; Madhura, K.; Agarwal, T.; Zaidi, T. Implementing Encryption Algorithms for the Protection of Wireless Networks. In Proceedings of the 5th International Conference on Data Science, Machine Learning and Applications, Hyderabad, India, 15–16 December 2023; Volume 2. [Google Scholar] [CrossRef]
- Faíscas, D. Security in Wi-Fi networks: A systematic review. ARIS2-J. 2024, 2, 17–23. [Google Scholar] [CrossRef]
- Kaur, N.; Gupta, L. Securing the 6G–IoT Environment: A Framework for Enhancing Transparency in Artificial Intelligence Decision-Making Through Explainable Artificial Intelligence. Sensors 2025, 25, 854. [Google Scholar] [CrossRef]
- Cisco: Powering an Inclusive, Digital Future for All, Powering an Inclusive, Digital Future for All. Available online: https://newsroom.cisco.com/c/r/newsroom/en/us/a/y2023/m01/powering-an-inclusive-digital-future-for-all.html (accessed on 20 February 2025).
- Abo-Soliman, M.A.; Azer, M.A. A study in WPA2 enterprise recent attacks. In Proceedings of the 13th International Computer Engineering Conference (ICENCO), Cairo, Egypt, 27–28 December 2017. [Google Scholar] [CrossRef]
- Kohlios, C.P.; Hayajneh, T. A Comprehensive Attack Flow Model and Security Analysis for Wi-Fi and WPA3. Electronics 2018, 7, 284. [Google Scholar] [CrossRef]
- Oproiu, M.I.; Ileana, M.; Marian, C.V. Exploring the Intricacies of the Architectural Framework Under-lying the Internet of Things Ecosystem. In Proceedings of the International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Iasi, Romania, 27–28 June 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Ileana, M.; Oproiu, M.I.; Marian, C.V. Exploring and Analyzing Internet of Things Devices for Process Optimization in Industrial Environments. In Proceedings of the Advanced Topics on Measurement and Simulation (ATOMS), Constanta, Romania, 28–30 August 2024; pp. 148–151. [Google Scholar] [CrossRef]
- How Authentication Protocols Work. Available online: https://networkradius.com/articles/2022/02/20/how-authentication-protocols-work.html (accessed on 20 February 2025).
- Available online: https://iperf.fr/iperf-doc.php (accessed on 20 February 2025).
- Chung, J.; Vlajic, N. Survey of Remote TLS Vulnerability Scanning Tools and Snapshot of TLS Use in Banking Sector. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), Austin, TX, USA, 3–5 October 2022. [Google Scholar] [CrossRef]
- Emily, L.; VoIP, J. What It Is and How to Fix It. Available online: https://www.openphone.com/blog/voip-jitter (accessed on 20 February 2025).
- Vivek, R. EAP-TTLS Versus PEAP (Protected Extensible Authentication Protocol) Authentication Method. Available online: https://www.securew2.com/blog/eap-tls-vs-eap-ttls-pap (accessed on 20 February 2025).
- Duan, L.; Li, Y.; Liao, L. Practical Certificate-Less Infrastructure with Application in TLS. Cryptography 2023, 7, 63. [Google Scholar] [CrossRef]
- Ibrar, A. A Comparative Study on the Power Usage of Raspberry Pi Models. Available online: https://projects-raspberry.com/a-comparative-study-on-the-power-usage-of-raspberry-pi-models (accessed on 6 March 2024).
- Lungu, R.S.; Marian, C.V. Data Collection and Command Mechanism for Management of Network Re-sources. In Proceedings of the 14th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Ploiesti, Romania, 30 June–1 July 2022; pp. 1–5. [Google Scholar] [CrossRef]
- Raceanu, D.N.; Marian, C.V. Cybersecurity Virtual Labs for Pentesting Education. In Proceedings of the 13th International Symposium on Advanced Topics in Electrical Engineering (ATEE), Bucharest, Romania, 23–25 March 2023; pp. 1–4. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).