A Learning-Based Energy-Efficient Device Grouping Mechanism for Massive Machine-Type Communication in the Context of Beyond 5G Networks
Abstract
1. Introduction
- We formulate a group number minimization problem to efficiently coordinate each device’s access to the network and propose a machine learning-powered energy-efficient mechanism, prompting devices to join a group to minimize the overall energy within delay constraints. Our model can interact with the dynamic environment without increasing the model’s complexity.
- We present the implementation of the grouping strategy as a Markov decision process (MDP)-based constrained optimization with a policy gradient. Constraints such as group condition, devices, application arrival, and time constraints are considered the state with the Lagrange relaxation technique. The action to group each device is based on the constraints mentioned above.
- We investigate the impact of massive access attempts on energy consumption and access delay in the proposed model. Given the heterogeneity of the applications in the real world, we show that certain delay-tolerant applications can afford the miss rate, so the non-tolerant ones can be completed before the expiration of the time constraint.
2. Related Works
2.1. Reinforcement Learning
2.2. Network Congestion and Signaling Overload in Wireless Network
2.3. Energy Consumption Minimization for MTC
3. System Model and Symbol Definitions
3.1. RACH Procedure Scenario
3.1.1. RACH Messaging Structure
3.1.2. Success and Collision Probability
- With the maximum preamble , the probability that the preamble is unclaimed is given bywhere is the binomial coefficient.
- The probability that only one device claimed the preamble is
- The probability that two or more devices are contending for the l-th preamble and colliding is
3.2. mMTC Architecture
3.3. mMTC Energy Consumption
- PSM:
- Connected mode:
- Idle mode:
3.4. mMTC Signaling Overload
3.5. mMTC Access Delay
4. Problem Formulation
4.1. The Execution Model for IoT Applications
4.2. The Group Number Minimization Problem
4.3. Grouping and Task Execution
5. Proposed mMTC Device Grouping Algorithms
5.1. Previously Proposed Algorithms
5.1.1. Best Fit Decreasing Solution with Dynamic Bin Size
5.1.2. MILP Solution with Fixed Time Constraints
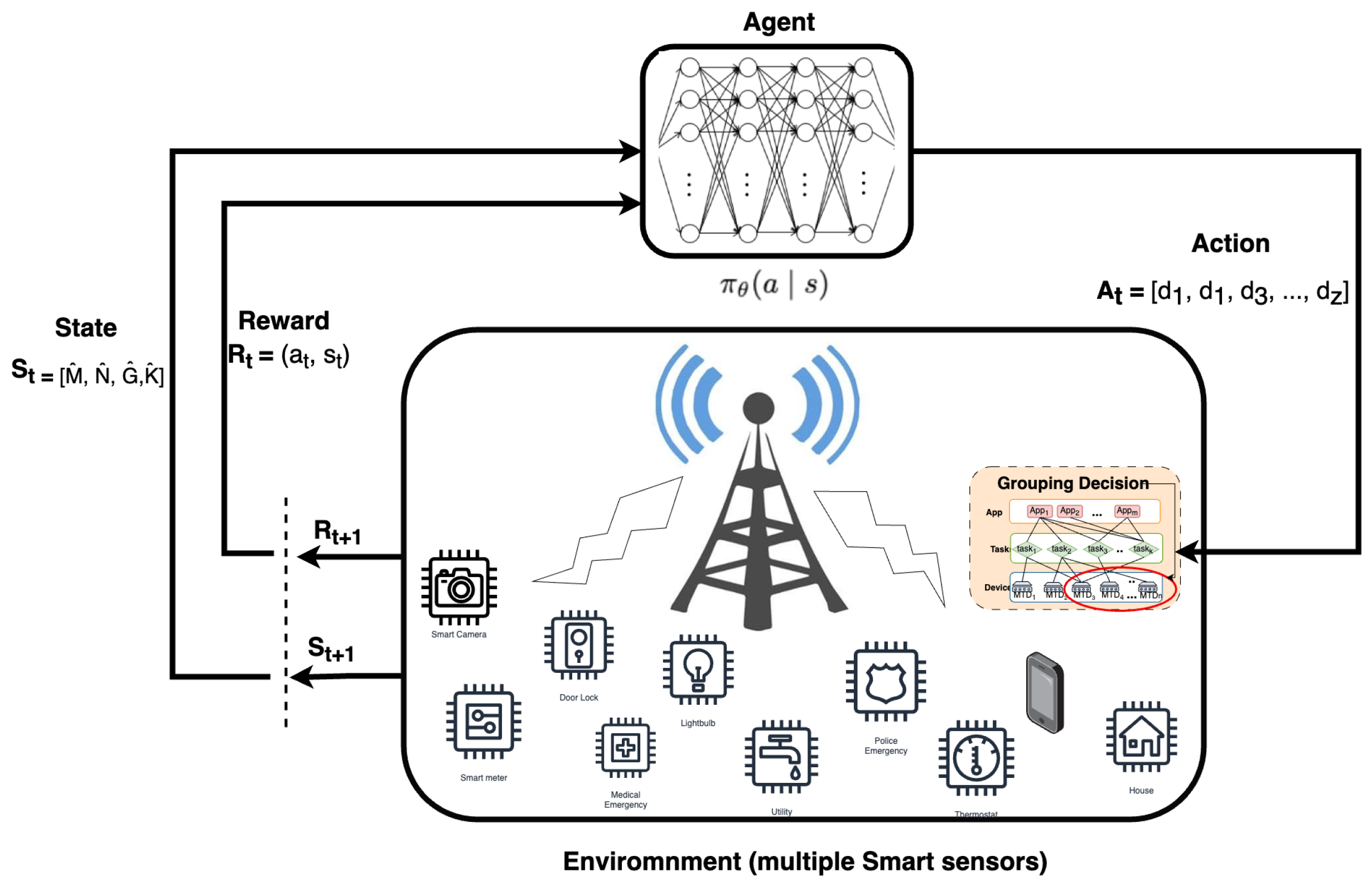
5.2. Reinforcement Learning-Based Device Grouping Algorithm
5.2.1. Constrained Optimization with Policy Gradients
The Reinforcement Learning Framework
RNN Architecture
5.2.2. Lagrange Relaxation
- is the augmented objective function, depending on policy parameters and Lagrange multipliers .
- denotes the expectation over trajectories generated by following policy parameterized by .
- is the reward received after executing action in state .
- represents the constraint function, which should ideally be non-positive for all states and actions. Positive values indicate constraint violations.
- is the Lagrange multiplier associated with the constraint.
Policy Gradient Update
- The grouping phase: As detailed in the Algorithm 1, in this phase, the agent generated a grouping vector to point out in which bin the device should be placed. This is performed according to some policies regulating the group size and the obligation of assigning the device to the group that has the least remaining space after the assignment.
- The evaluation phase: In the evaluation phase, the grouping action is evaluated, and the rewards are generated based on whether or not the assignment is correct given the policies mentioned above and the environmental state during the grouping phase.
| Algorithm 1 Lagrangian RL for Device Grouping | |
| 1: | Inputs: |
| 2: | : State set representing device characteristics |
| 3: | A: Action set for device grouping |
| 4: | : Policy function mapping S to A |
| 5: | : Constraints on states and actions |
| 6: | : Lagrange multiplier |
| 7: | Initialize RL model parameters , policy , state set S, action set A, and . |
| 8: | for each device in the network do |
| 9: | Observe state . |
| 10: | Determine action for device grouping. |
| 11: | Execute , grouping the device accordingly. |
| 12: | Update S with new device groupings. |
| 13: | end for |
| 14: | for each action during grouping do |
| 15: | Evaluate grouping effectiveness and constraint satisfaction. |
| 16: | Calculate reward and penalty . |
| 17: | Update using the gradient of . |
| 18: | Adjust based on constraint violations. |
| 19: | end for |
| 20: | Output: Optimized device groupings with minimal unallocated space, adhering to constraints. |
6. Performance Analysis
6.1. Simulation Setup and Environmental Parameters
6.1.1. Neural Network Configuration Parameters
6.1.2. Dataset
6.2. Performance Metrics
- Miss rate probability: This metric is the ratio between the number of failed devices or devices exceeding the maximum re-transmission limit or time constraint and the total number of devices N attempting to access the network via a RACH procedure.
- Total energy consumption: This metric is the total energy consumed for N devices performing a two-step RACH mechanism attempt.
- Overall RACH access delay: This metric is the average time for N successful data packet receptions started by the first RACH attempt. We consider the maximum re-transmission to be 20 and the back-off time to be 20 ms.
6.3. Comparing Algorithms
- Feature-based grouping: Groups devices based on specific features such as device type, data requirements, or application.
- Best fit decreasing (BFD): A heuristic algorithm that groups devices based on their task load and the application’s time constraint to minimize the number of failed RACH attempts. This algorithm also aims at minimizing the number of groups created [24].
- MILP grouping: Formulates the device grouping problem as a mixed-integer linear programming problem, including a relaxed version of BFD for reduced computational complexity [55].
6.4. Numerical Results
6.4.1. The Impact of Massive Access on the RACH Success Probability
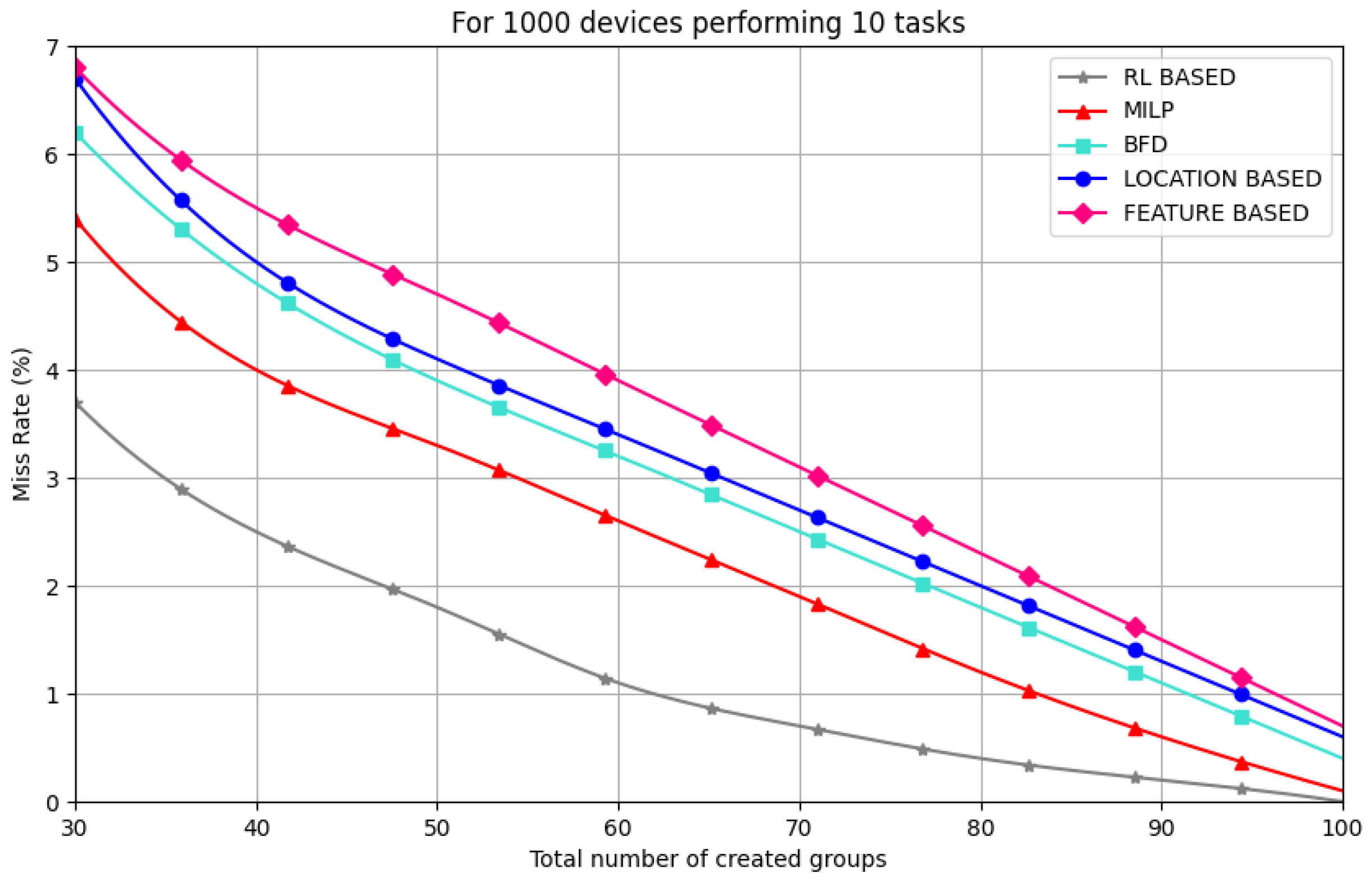
6.4.2. Loading and Miss Rate Analysis
6.4.3. Impact of Efficient Grouping on the Overall mMTC Energy Consumption
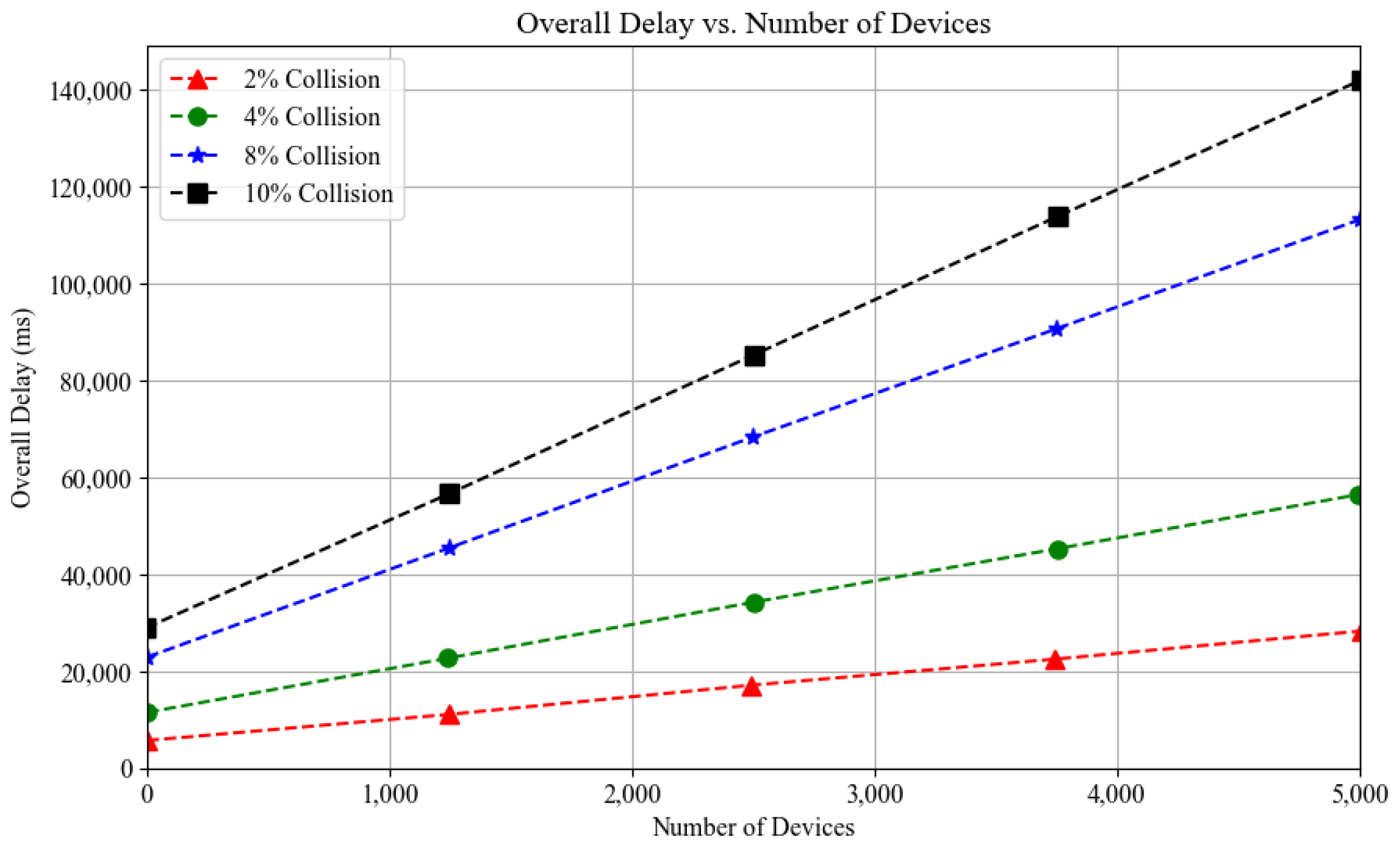
6.4.4. Impact of Efficient Grouping on the Overall mMTC Transmission Delay
7. Discussion
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Yang, B.; Wei, F.; She, X.; Jiang, Z.; Zhu, J.; Chen, P.; Wang, J. Intelligent Random Access for Massive-Machine Type Communications in Sliced Mobile Networks. Electronics 2023, 12, 329. [Google Scholar] [CrossRef]
- Taleb, T.; Ksentini, A.; Kobbane, A. Lightweight mobile core networks for machine type communications. IEEE Access 2014, 2, 1128–1137. [Google Scholar] [CrossRef]
- He, Y.; Ren, G. Cluster-Aided Collision Resolution Random Access in Distributed Massive MIMO Systems. IEEE Internet Things J. 2022, 9, 11453–11463. [Google Scholar] [CrossRef]
- Pardalos, P.M.; Du, D.-Z.; Graham, R.L. Handbook of Combinatorial Optimization, 2nd ed.; Springer: New York, NY, USA, 2005. [Google Scholar] [CrossRef]
- Zhang, N.; Zhu, X. A Hybrid Grant NOMA Random Access for Massive MTC Service. IEEE Internet Things J. 2023, 10, 5490–5505. [Google Scholar] [CrossRef]
- Shi, Y.; Lian, L.; Shi, Y.; Wang, Z.; Zhou, Y.; Fu, L.; Bai, L.; Zhang, J.; Zhang, W. Machine Learning for Large-Scale Optimization in 6G Wireless Networks. arXiv 2023, arXiv:2301.03377. [Google Scholar] [CrossRef]
- Jeon, W.; Seo, S.B.; Jeong, D. POMDP-Based Contention Resolution for Framed Slotted-ALOHA Protocol in Machine-Type Communications. IEEE Internet Things J. 2022, 9, 13511–13523. [Google Scholar] [CrossRef]
- Sejan, M.A.S.; Rahman, M.H.; Aziz, M.A.; You, Y.; Song, H.K. Temporal Neural Network Framework Adaptation in Reconfigurable Intelligent Surface-Assisted Wireless Communication. Sensors 2023, 23, 2777. [Google Scholar] [CrossRef]
- Tamim, I.; Aleyadeh, S.; Shami, A. Intelligent O-RAN Traffic Steering for URLLC Through Deep Reinforcement Learning. arXiv 2023, arXiv:2303.01960. [Google Scholar] [CrossRef]
- Varsamis, D.; Chanlioglou, F. A Parallel Approach of Best Fit Decreasing Algorithm. WSEAS Trans. Comput. 2018, 17, 79–85. [Google Scholar]
- Munien, C.; Mahabeer, S.; Dzitiro, E.; Singh, S.; Zungu, S.; Ezugwu, A. Metaheuristic Approaches for One-Dimensional Bin Packing Problem: A Comparative Performance Study. IEEE Access 2020, 8, 227438–227465. [Google Scholar] [CrossRef]
- Rahman, M.A.; Goel, A.; Sharma, S.; Gupta, B.; Aggarwal, A.; Guedalia, I.D.; Chandhok, R.P.; Guedalia, J. System and Method for Providing Content on an Electronic Device. U.S. Patent US20140241354A1, 28 August 2014. [Google Scholar]
- Ohtsuki, T. Machine Learning in 6G Wireless Communications. IEICE Trans. Commun. 2023, 106, 75–83. [Google Scholar] [CrossRef]
- Liu, Y.; Deng, Y.; Nallanathan, A.; Yuan, J. Machine Learning for 6G Enhanced Ultra-Reliable and Low-Latency Services. IEEE Wirel. Commun. 2023, 30, 48–54. [Google Scholar] [CrossRef]
- Tang, L.; Du, Y.; Chen, Q.; Liu, Q.; Li, J.; Li, S. Equilibrated and Fast Resources Allocation for Massive and Diversified MTC Services Using Multiagent Deep Reinforcement Learning. IEEE Internet Things J. 2023, 10, 664–681. [Google Scholar] [CrossRef]
- Li, Y.; Chai, K.K.; Chen, Y.; Loo, J. Smart duty cycle control with reinforcement learning for machine to machine communications. In Proceedings of the 2015 IEEE International Conference on Communication Workshop (ICCW), London, UK, 8–12 June 2015; pp. 1458–1463. [Google Scholar]
- Amaal, S.A.; El-Hameed, K.M.F.E. A Q-learning approach for machine-type communication random access in LTE-Advanced. Proc. Telecommun. Syst. 2019, 71, 397–413. [Google Scholar]
- Alves, T.A.B.; Abrão, T. NOMA-Based Random Access in mMTC XL-MIMO. IEEE Access 2023, 11, 1944–1954. [Google Scholar] [CrossRef]
- Harwahyu, R.; Sari, R.; Misbahuddin, M. Performance Evaluation of LTE Random Access Procedure under Distributed Location Data Mining for Road Traffic Monitoring. Int. J. Commun. Netw. Inf. Secur. 2016, 8, 171–178. [Google Scholar] [CrossRef]
- Lien, S.Y.; Chen, K.C.; Lin, Y. Toward ubiquitous massive accesses in 3GPP machine-to-machine communications. IEEE Commun. Mag. 2011, 49, 66–74. [Google Scholar] [CrossRef]
- Tsai, A.H.; Wang, L.C.; Huang, J.H.; Lin, T.M. Overload Control for Machine Type Communications with Femtocells. In Proceedings of the 2012 IEEE Vehicular Technology Conference (VTC Fall), Quebec City, QC, Canada, 3–6 September 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 1–5. [Google Scholar] [CrossRef]
- Lee, K.; Shin, J.; Cho, Y.; Ko, K.S.; Sung, D.K.; Shin, H. A group-based communication scheme based on the location information of MTC devices in cellular networks. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 4899–4903. [Google Scholar] [CrossRef]
- Taleb, T.; Ksentini, A. On alleviating MTC overload in EPS. Ad Hoc Netw. 2014, 18, 24–39. [Google Scholar] [CrossRef]
- Tseng, C.W.; Boisguene, R.; Huang, C.W.; Lin, P.; Kawamoto, Y. A scheduled grouping scheme for MTC device ID sharing. In Proceedings of the International Wireless Communications and Mobile Computing (IWCMC), Dubrovnik, Croatia, 24–28 August 2015. [Google Scholar] [CrossRef]
- Chen, G.; Huang, J.; Cheng, B.; Chen, J. A social network based approach for IoT device management and service composition. In Proceedings of the 2015 IEEE World Congress on Services, New York, NY, USA, 27 June–2 July 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1–8. [Google Scholar]
- Ito, M.; Nishinaga, N.; Kitatsuji, Y.; Murata, M. Reducing State Information by Sharing IMSI for Cellular IoT Devices. IEEE Internet Things J. 2016, 3, 1297–1309. [Google Scholar] [CrossRef]
- Sharma, S.K.; Wang, X. Toward Massive Machine Type Communications in Ultra-Dense Cellular IoT Networks: Current Issues and Machine Learning-Assisted Solutions. IEEE Commun. Surv. Tutorials 2020, 22, 426–471. [Google Scholar] [CrossRef]
- Bockelmann, C.; Pratas, N.K.; Wunder, G.; Saur, S.; Navarro, M.; Gregoratti, D.; Vivier, G.; De Carvalho, E.; Ji, Y.; Stefanović, Č.; et al. Towards massive connectivity support for scalable mMTC communications in 5G networks. IEEE Access 2018, 6, 28969–28992. [Google Scholar] [CrossRef]
- Li, X.; Luo, C.; Ji, H.; Zhuang, Y.; Zhang, H.; Leung, V.C. Energy consumption optimization for self-powered IoT networks with non-orthogonal multiple access. Int. J. Commun. Syst. 2020, 33, e4174. [Google Scholar] [CrossRef]
- Boisguene, R.; Tseng, S.C.; Huang, C.W.; Lin, P. A survey on NB-IoT downlink scheduling: Issues and potential solutions. In Proceedings of the 2017 13th International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, 26–30 June 2017; pp. 547–551. [Google Scholar] [CrossRef]
- Singh, R.K.; Puluckul, P.P.; Berkvens, R.; Weyn, M. Energy Consumption Analysis of LPWAN Technologies and Lifetime Estimation for IoT Application. Sensors 2020, 20, 4794. [Google Scholar] [CrossRef] [PubMed]
- Michelinakis, F.; Al-Selwi, A.S.; Capuzzo, M.; Zanella, A.; Mahmood, K.; Elmokashfi, A. Dissecting Energy Consumption of NB-IoT Devices Empirically. IEEE Internet Things J. 2021, 8, 1224–1242. [Google Scholar] [CrossRef]
- Elgarhy, O.; Reggiani, L.; Alam, M.M.; Zoha, A.; Ahmad, R.; Kuusik, A. Energy Efficiency and Latency Optimization for IoT URLLC and mMTC Use Cases. IEEE Access 2024, 12, 23132–23148. [Google Scholar] [CrossRef]
- Chang, B.J.; Lin, Y.T. Adaptive Flowing Traffic Prediction in Contention Random Access for Optimizing Virtual/Physical Resource in B5G/5G New Radio and Core Network. IEEE Trans. Netw. Sci. Eng. 2024, 11, 1934–1946. [Google Scholar] [CrossRef]
- Piao, Y.; Lee, T.J. Integrated 2-4 Step Random Access for Heterogeneous and Massive IoT Devices. IEEE Trans. Green Commun. Netw. 2023, 8, 441–452. [Google Scholar] [CrossRef]
- 3GPP. 3GPP TS 36.321, Radio Access Network (RAN); Medium Access Control (MAC) Protocol Specification; Part 1: Common Procedures; Technical Report; 3GPP: Marseille, France, 2020. [Google Scholar]
- Miuccio, L.; Panno, D.; Riolo, S. A New Contention-Based PUSCH Resource Allocation in 5G NR for mMTC Scenarios. IEEE Commun. Lett. 2021, 25, 802–806. [Google Scholar] [CrossRef]
- 3GPP. Architecture Enhancements to Facilitate Communications with Packet Data Networks and Applications; TS 23.682 V15.0.0; 3GPP: Marseille, France, 2017. [Google Scholar]
- Gerasimenko, M.; Petrov, V.; Galinina, O.; Andreev, S.; Koucheryavy, Y. Energy and delay analysis of LTE-Advanced RACH performance under MTC overload. In Proceedings of the 2012 IEEE Globecom Workshops, Anaheim, CA, USA, 3–7 December 2012; pp. 1632–1637. [Google Scholar] [CrossRef]
- Thota, J.; Aijaz, A. On Performance Evaluation of Random Access Enhancements for 5G uRLLC. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Shi, B.; Zhang, Y. A Novel Algorithm to Optimize the Energy Consumption Using IoT and Based on Ant Colony Algorithm. Energies 2021, 14, 1709. [Google Scholar] [CrossRef]
- Mitsuo Gen, R.C. Genetic Algorithms and Engineering Optimization, 1st ed.; Wiley-Interscience: Hoboken, NJ, USA, 1999; pp. 64–65. [Google Scholar]
- 3GPP. System Improvements for Machine-Type Communications (MTC) (Release 11) Technical Report; 3GPP: Marseille, France, 2012. [Google Scholar]
- MOSEK ApS. The MOSEK Optimization Toolbox for MATLAB Manual, Version 7.1, Revision 28; MOSEK ApS: Copenhagen, Denmark, 2015. [Google Scholar]
- Bello, I.; Pham, H.; Le, Q.V.; Norouzi, M.; Bengio, S. Neural Combinatorial Optimization with Reinforcement Learning. arXiv 2017, arXiv:1611.09940. [Google Scholar]
- Solozabal, R.; Ceberio, J.; Sanchoyerto, A.; Zabala, L.; Blanco, B.; Liberal, F. Virtual Network Function Placement Optimization with Deep Reinforcement Learning. IEEE J. Sel. Areas Commun. 2020, 38, 292–303. [Google Scholar] [CrossRef]
- Mazyavkina, N.; Sviridov, S.; Ivanov, S.; Burnaev, E. Reinforcement learning for combinatorial optimization: A survey. Comput. Oper. Res. 2021, 134, 105400. [Google Scholar] [CrossRef]
- Mirhoseini, A.; Pham, H.; Le, Q.V.; Steiner, B.; Larsen, R.; Zhou, Y.; Kumar, N.; Norouzi, M.; Bengio, S.; Dean, J. Device Placement Optimization with Reinforcement Learning. arXiv 2017, arXiv:1706.04972. [Google Scholar]
- Wang, K.; Shat, S.; Chen, H.; Perrault, A.; Doshi-Velez, F.; Tambe, M. Learning MDPs from Features: Predict-Then-Optimize for Sequential Decision Problems by Reinforcement Learning. arXiv 2021, arXiv:2106.03279. [Google Scholar]
- Yang, M.; Nachum, O. Representation matters: Offline pretraining for sequential decision making. arXiv 2021, arXiv:2102.05815. [Google Scholar]
- Puterman, M.L. Markov Decision Processes.: Discrete Stochastic Dynamic Programming; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2014; Volume 414, ISBN 978-0-471-72782-8. [Google Scholar]
- Müller, A.; Alatur, P.; Ramponi, G.; He, N. Cancellation-Free Regret Bounds for Lagrangian Approaches in Constrained Markov Decision Processes. arXiv 2023, arXiv:2306.07001. [Google Scholar] [CrossRef]
- Hu, P.; Chen, Y.; Pan, L.; Fang, Z.; Xiao, F.; Huang, L. Multi-User Delay-Constrained Scheduling with Deep Recurrent Reinforcement Learning. IEEE/ACM Trans. Netw. 2024, 1–16. [Google Scholar] [CrossRef]
- Kingma, D.P.; Ba, J. Adam: A Method for Stochastic Optimization. arXiv 2014, arXiv:1412.6980. [Google Scholar] [CrossRef]
- Rubbens, B.; Huang, C.W. Adaptive Congestion Control for Massive Machine Type Communications in Cellular Network. In Proceedings of the 2020 IEEE International Conference on Consumer Electronics—Taiwan (ICCE-Taiwan), Taoyuan, Taiwan, 28–30 September 2020; pp. 1–2. [Google Scholar] [CrossRef]
- Majumdar, C.; López-Benítez, M.; Merchant, S.N. Real Smart Home Data-Assisted Statistical Traffic Modeling for the Internet of Things. IEEE Internet Things J. 2020, 7, 4761–4776. [Google Scholar] [CrossRef]
- Leonardi, L.; Bello, L.L.L.; Patti, G. Combining Earliest Deadline First Scheduling with Scheduled Traffic Support in Automotive TSN-Based Networks. Appl. Syst. Innov. 2022, 5, 125. [Google Scholar] [CrossRef]
- Reddy, Y.S.; Chopra, G.; Dubey, A.; Kumar, A.; Panigrahi, T.; Cenkeramaddi, L.R. Rate-splitting random access mechanism for massive machine type communications in 5G cellular Internet-of-Things. In Proceedings of the 2021 IEEE 32nd Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Helsinki, Finland, 13–16 September 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 648–653. [Google Scholar]
- Butt, T.A.; Phillips, I.; Guan, L.; Oikonomou, G. Adaptive and Context-Aware Service Discovery for the Internet of Things. In Internet of Things, Smart Spaces, and Next Generation Networking; Balandin, S., Andreev, S., Koucheryavy, Y., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 36–47. [Google Scholar]






| Parameter Description | Value |
|---|---|
| Neural Network Configuration | LSTM-based RL model |
| LSTM Layers | 3 stacks with 64 hidden layers each |
| Batch Size | 64 |
| Epoch | 50 |
| Optimizer | Adam |
| Activation Function | ReLu |
| Learning Rate | 10−3 |
| Parameter | Description | Value |
|---|---|---|
| N | Number of devices | 1000 to 5000 |
| K | Number of different tasks | 10 and 40 |
| w | Number of preambles | 54 |
| - | Tasks per application run | 1 to 5, uniform distribution |
| - | Tasks per device support | 1, 3, 5, uniform distribution |
| M | Number of applications | 20 |
| Time constraint of an application | 2% of inter-arrival time | |
| Mean of application inter-arrival time | 30 min (5%), 1 h (15%), 2 h (40%), 24 h (40%) | |
| t | Device task execution time | uniform (0.1, 0.2) s |
| - | Targeted simulation time frame | 1 RAO |
| Maximum re-transmission | 10 | |
| Back-off time | 20 ms | |
| C | Energy consumption per RACH attempt | 264 J [58] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Boisguene, R.; Althamary, I.; Huang, C.-W. A Learning-Based Energy-Efficient Device Grouping Mechanism for Massive Machine-Type Communication in the Context of Beyond 5G Networks. J. Sens. Actuator Netw. 2024, 13, 33. https://doi.org/10.3390/jsan13030033
Boisguene R, Althamary I, Huang C-W. A Learning-Based Energy-Efficient Device Grouping Mechanism for Massive Machine-Type Communication in the Context of Beyond 5G Networks. Journal of Sensor and Actuator Networks. 2024; 13(3):33. https://doi.org/10.3390/jsan13030033
Chicago/Turabian StyleBoisguene, Rubbens, Ibrahim Althamary, and Chih-Wei Huang. 2024. "A Learning-Based Energy-Efficient Device Grouping Mechanism for Massive Machine-Type Communication in the Context of Beyond 5G Networks" Journal of Sensor and Actuator Networks 13, no. 3: 33. https://doi.org/10.3390/jsan13030033
APA StyleBoisguene, R., Althamary, I., & Huang, C.-W. (2024). A Learning-Based Energy-Efficient Device Grouping Mechanism for Massive Machine-Type Communication in the Context of Beyond 5G Networks. Journal of Sensor and Actuator Networks, 13(3), 33. https://doi.org/10.3390/jsan13030033







