A Dynamic Light-Weight Symmetric Encryption Algorithm for Secure Data Transmission via BLE Beacons
Abstract
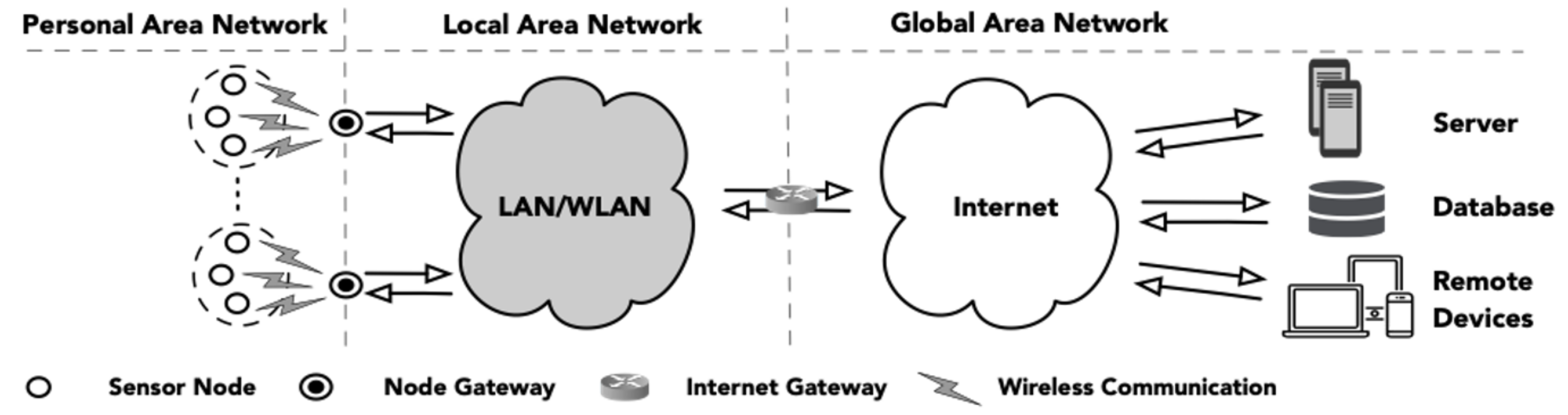
1. Introduction
- Tracking attack [25]: attackers identify messages from the same origin in order to collect information about an individual or to trace messages for personal information such as the sender’s location;
- A light-weight cryptography for secure data transmission via BLE beacon that applies dynamic temporal encryption key generation on top of existing symmetric encryption algorithms for further security enhancement;
- Two levels of security for secret key generation based on fixed-node secret key and random numbers obtained periodically from the server (adjustable security level by changing the number of bits of random numbers and counters);
- Support dynamic size of messages without requiring padding (thus saving more energy compared to a standard block cipher) and yielding cyphertext with the same size as the input message;
- Demonstration of its application across baseline encryption algorithms;
- Demonstration of its application on beacon data encryption by assessing its performance when implemented in a miniaturized sensor node.
2. Background and Related Work
3. Dynamic Light-Weight Symmetric Encryption Algorithm
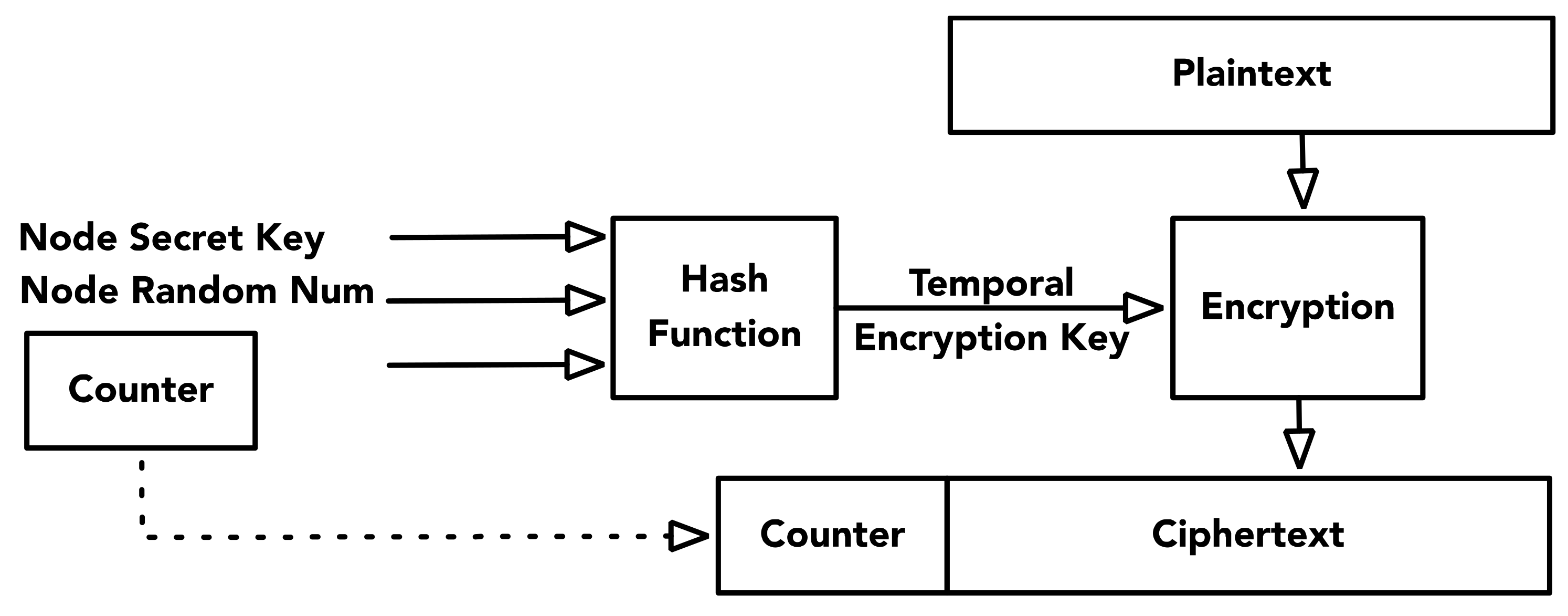
3.1. Key Generation
3.2. Message Encryption/Decryption
3.3. Evaluation Parameters
3.3.1. Security Criteria
- Avalanche effect: in cryptography, the avalanche effect is a desirable property. It refers to changes in the output of the algorithm (ciphertext) when a small change is made (i.e., flipping a single bit) either on an encryption key or a plaintext. The avalanche effect can be measured using Equation (1). A good cipher should always have at least 50% change in ciphertext bits with even a one-bit change in a plaintext or an encryption key [82]. This implies that the encryption algorithm can resist most possible attacks.
- Randomness: a randomness test can be used to determine the randomization in ciphertexts based on their diffusion characteristics. To pass the randomness test, there should not be any form of input/output relation in the cipher. The distribution of the number of zeros and ones in ciphertexts can be observed to check the randomness in ciphertexts.
3.3.2. Performance Metrics
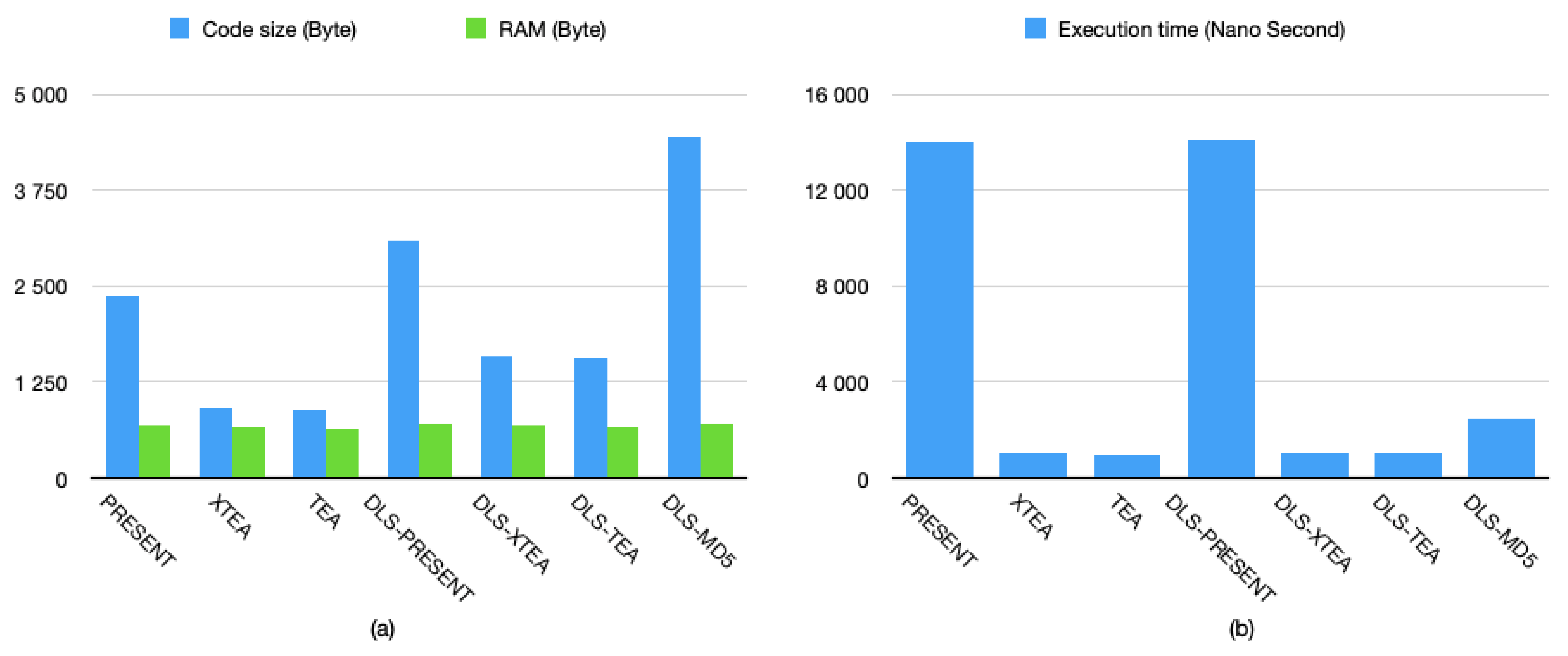
- Memory consumption (byte): more memory used by an application running on a sensor usually leads to higher power consumption. In this study, memory usage is measured in terms of code size and RAM in use for encrypting a plaintext.
- Execution time (second): the time required to encrypt a plaintext. Longer execution time implies higher power consumption and a delay in data transmission. In a real-time system with a low data latency requirement, encryption with lower execution time is preferred.
- Power consumption (mV/hr): a sensor with low power consumption has a longer battery-life and does not require frequent recharging.
4. Experiments and Results
4.1. Experiment Setup
4.2. Experimental Results
4.2.1. Security Criteria
4.2.2. Resource Consumption
4.2.3. Power Consumption
4.3. Cryptanalysis
5. Conclusions and Discussion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Mundt, C.W.; Montgomery, K.N.; Udoh, U.E.; Barker, V.N.; Thonier, G.C.; Tellier, A.M.; Ricks, R.D.; Darling, R.B.; Cagle, Y.D.; Cabrol, N.A.; et al. A Multiparameter Wearable Physiologic Monitoring System for Space and Terrestrial Applications. IEEE Trans. Inf. Technol. Biomed. 2005, 9, 382–391. [Google Scholar] [CrossRef] [PubMed]
- Sung, M.; Marci, C.; Pentland, A. Wearable Feedback Systems for Rehabilitation. J. NeuroEngineering Rehabil. 2005, 2, 17. [Google Scholar] [CrossRef] [PubMed]
- Oliver, N.; Flores-Mangas, F. HealthGear: A Real-Time Wearable System for Monitoring and Analyzing Physiological Signals. In Proceedings of the International Workshop on Wearable and Implantable Body Sensor Networks, Cambridge, MA, USA, 3–5 April 2006. [Google Scholar]
- Pop, V.; Francisco, R.D.; Pflug, H.; Santana, J.; Visser, H.; Vullers, R.; De Groot, H.; Gyselinckx, B. Human++: Wireless Autonomous Sensor Technology for Body Area Networks. In Proceedings of the Asia and South Pacific Design Automation Conference, Yokohama, Japan, 25–28 January 2011; pp. 561–566. [Google Scholar]
- Caldara, M.; Colleoni, C.; Guido, E.; Rosace, G.; Re, V.; Vitali, A. A Wearable Sensor Platform to Monitor Sweat pH and Skin Temperature. In Proceedings of the International Conference on Body Sensor Networks, Cambridge, MA, USA, 6–9 May 2013; pp. 1–6. [Google Scholar]
- Kirk, M.A.; Amiri, M.; Pirbaglou, M.; Ritvo, P. Wearable Technology and Physical Activity Behavior Change in Adults with Chronic Cardiometabolic Disease: A Systematic Review and Meta-Analysis. Am. J. Health Promot. 2018, 33, 1–14. [Google Scholar] [CrossRef] [PubMed]
- Wang, G.; Zhang, S.; Dong, S.; Lou, D.; Ma, L.; Pei, X.; Xu, H.; Farooq, U.; Guo, W. Stretchable Optical Sensing Patch System Integrated Heart Rate, Pulse Oxygen Saturation, and Sweat pH Detection. IEEE Trans. Biomed. Eng. 2018, 66, 1000–1005. [Google Scholar] [CrossRef]
- Fortino, G.; Gravina, R. Fall-MobileGuard: A Smart Real-Time Fall Detection System. In Proceedings of the EAI International Conference on Body Area Networks, Sydney, Australia, 28–30 September 2015. [Google Scholar]
- Mozaffari, N.; Rezazadeh, J.; Farahbakhsh, R.; Yazdani, S.; Sandrasegaran, K. Practical Fall Detection Based on IoT Technologies: A Survey. Internet Things 2019, 8, 100124. [Google Scholar] [CrossRef]
- Ramachandran, A.; Karuppiah, A. A Survey on Recent Advances in Wearable Fall Detection Systems. BioMed Res. Int. 2020, 2020, 2167160. [Google Scholar] [CrossRef]
- Manimaraboopathy, M.; Vijayalakshmi, S.; Hemavathy, D.; Priya, A. A Wearable Multiparameter Medical Monitoring and Alert System with First Aid. Int. J. Smart Sens. Intell. Syst. 2017, 10, 446–458. [Google Scholar] [CrossRef]
- Garbern, S.C.; Mbanjumucyo, G.; Umuhoza, C.; Sharma, V.K.; Mackey, J.; Tang, O.; Martin, K.D.; Twagirumukiza, F.R.; Rosman, S.L.; McCall, N.; et al. Validation of a Wearable Biosensor Device for Vital Sign Monitoring in Septic Emergency Department Patients in Rwanda. Digit. Health 2019, 5, 1–13. [Google Scholar] [CrossRef]
- Wu, R.C.; Ginsburg, S.; Son, T.; Gershon, A.S. Using Wearables and Self-Management Apps in Patients with COPD: A Qualitative Study. Eur. Respir. J. 2019, 5, 00036-2019. [Google Scholar] [CrossRef] [PubMed]
- Jovanov, E.; Milenkovic, A.; Otto, C.; De Groen, P. A Wireless Body Area Network of Intelligent Motion Sensors for Computer Assisted Physical Rehabilitation. J. NeuroEngineering Rehabil. 2005, 2, 6. [Google Scholar] [CrossRef]
- Bavan, L.; Surmacz, K.; Beard, D.; Mellon, S.; Rees, J. Adherence Monitoring of Rehabilitation Exercise with Inertial Sensors: A Clinical Validation Study. Gait Posture 2019, 70, 211–217. [Google Scholar] [CrossRef] [PubMed]
- Herrera-Luna, I.; Rechy-Ramirez, E.J.; Rios-Figueroa, H.V.; Marin-Hernandez, A. Sensor Fusion Used in Applications for Hand Rehabilitation: A Systematic Review. IEEE Sens. J. 2019, 19, 3581–3592. [Google Scholar] [CrossRef]
- Qiu, S.; Wang, Z.; Zhao, H.; Liu, L.; Wang, J.; Li, J. Gait Analysis for Physical Rehabilitation via Body-Worn Sensors and Multi-information Fusion: Technology, Communications and Computing. In Advances in Body Area Networks; Springer: Cham, Switzerland, 2019; pp. 139–148. [Google Scholar] [CrossRef]
- Patel, S.; Park, H.; Bonato, P.; Chan, L.; Rodgers, M. A Review of Wearable Sensors and Systems with Application in Rehabilitation. J. NeuroEngineering Rehabil. 2012, 9, 21. [Google Scholar] [CrossRef]
- Shin, G.; Jarrahi, M.H.; Fei, Y.; Karami, A.; Gafinowitz, N.; Byun, A.; Lu, X. Wearable Activity Trackers, Accuracy, Adoption, Acceptance and Health Impact: A Systematic Literature Review. J. Biomed. Inform. 2019, 93, 103153. [Google Scholar] [CrossRef] [PubMed]
- Lo, B.P.; Atallah, L.; Crewther, B.; Spehar-Deleze, A.M.; Anastasova, S.; West, A.A.; Conway, P.; Cook, C.; Drawer, S.; Vadgama, P.; et al. Pervasive Sensing for Athletic Training. In Delivering London 2012: ICT Enabling Game; Institution of Engineering and Technology: London, UK, 2011. [Google Scholar] [CrossRef]
- Aroganam, G.; Manivannan, N.; Harrison, D. Review on Wearable Technology Sensors Used in Consumer Sport Applications. Sensors 2019, 19, 1983. [Google Scholar] [CrossRef] [PubMed]
- Sperlich, B.; Aminian, K.; Düking, P.; Holmberg, H.C. Editorial: Wearable Sensor Technology for Monitoring Training Load and Health in the Athletic Population. Front. Physiol. 2020, 10, 1520. [Google Scholar] [CrossRef] [PubMed]
- Aileni, R.M.; Suciu, G.; Rajagopal, M.; Pasca, S.; Valderrama Sukuyama, C.A. Data Privacy and Security for IoMWT (Internet of Medical Wearable Things) Cloud; Springer: Cham, Switzerland, 2020. [Google Scholar] [CrossRef]
- Kompara, M.; Hölbl, M. Survey on Security in Intra-Body Area Network Communication. Ad Hoc Netw. 2018, 70, 23–43. [Google Scholar] [CrossRef]
- Tan, C.C.; Wang, H.; Zhong, S.; Li, Q. IBE-Lite: A Lightweight Identity-Based Cryptography for Body Sensor Networks. IEEE Trans. Inf. Technol. Biomed. 2009, 13, 926–932. [Google Scholar] [CrossRef] [PubMed]
- Li, M.; Lou, W.; Ren, K. Data Security and Privacy in Wireless Body Area Networks. IEEE Wirel. Commun. 2010, 17, 51–58. [Google Scholar] [CrossRef]
- Liu, J.; Kwak, S.K. Hybrid Security Mechanisms for Wireless Body Area Networks. In Proceedings of the International Conference on Ubiquitous and Future Networks, Jeju, South Korea, 16–18 June 2010; pp. 98–103. [Google Scholar]
- Huang, C.; Lee, H.; Lee, D.H. A Privacy-Strengthened Scheme for E-Healthcare Monitoring System. J. Med. Syst. 2012, 36, 2959–2971. [Google Scholar] [CrossRef]
- Al Ameen, M.; Liu, J.; Kwak, S.K. Security and Privacy Issues in Wireless Sensor Networks for Healthcare Applications. J. Med. Syst. 2012, 36, 93–101. [Google Scholar] [CrossRef] [PubMed]
- Ali, A.; Khan, F.A. Key Agreement Schemes in Wireless Body Area Networks: Taxonomy and State-of-the-Art. J. Med. Syst. 2015, 39, 115. [Google Scholar] [CrossRef] [PubMed]
- Yao, L.; Liu, B.; Yao, K.; Wu, G.; Wang, J. An ECG-Based Signal Key Establishment Protocol in Body Area Networks. In Proceedings of the International Conference on Ubiquitous Intelligence and Computing and International Conference on Autonomic and Trusted Computing, Xian, China, 26–29 October 2010; pp. 233–238. [Google Scholar]
- Drira, W.; Renault, E.; Zeghlache, D. A Hybrid Authentication and Key Establishment Scheme for WBAN. In Proceedings of the International Conference on Trust, Security and Privacy in Computing and Communications, Liverpool, UK, 25–27 June 2012; pp. 78–83. [Google Scholar]
- Pathan, A.S.K.; Lee, H.W.; Hong, C.S. Security in Wireless Sensor Networks: Issues and Challenges. In Proceedings of the International Conference Advanced Communication Technology, Phoenix Park, South Korea, 20–22 February 2006. [Google Scholar]
- Zhang, Z.; Cho, M.C.Y.; Wang, C.; Hsu, C.; Chen, C.; Shieh, S. IoT Security: Ongoing Challenges and Research Opportunities. In Proceedings of the Service-Oriented Computing and Applications, Matsue, Japan, 17–19 November 2014; pp. 230–234. [Google Scholar]
- Guan, Z.; Yang, T.; Du, X.; Guizani, M. Secure Data Access for Wireless Body Sensor Networks. In Proceedings of the Wireless Communications and Networking, Doha, Qatar, 3–6 April 2016. [Google Scholar]
- Fortino, G.; Russo, W.; Savaglio, C.; Viroli, M.; Zhou, M. Modeling Opportunistic IoT Services in Open IoT Ecosystems. In Proceedings of the Workshop from Objects to Agents (WOA), Catania, Italy, 29–30 July 2017; pp. 90–95. [Google Scholar]
- Bordel, B.; Alcarria, R.; De Andres, D.M.; You, I.; Martin, D. Securing Internet-of-Things Systems Through Implicit and Explicit Reputation Models. IEEE Access 2018, 6, 47472–47488. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating Critical Security Issues of the IoT World: Present and Future Challenge. IEEE Internet Things J. 2018, 5, 2483–2495. [Google Scholar] [CrossRef]
- Sivasangari, A.; Ananthi, A.; Deepa, D.; Rajesh, G.; Mercilin Raajini, X. Chapter 3-Security and Privacy in Wireless Body Sensor Networks Using Lightweight Cryptography Scheme; Academic Press: Cambridge, MA, USA, 2021. [Google Scholar] [CrossRef]
- Botta, M.; Simek, M.; Mitton, N. Comparison of Hardware and Software-Based Encryption for Secure Communication in Wireless Sensor Networks. In Proceedings of the International Conference on Telecommunications and Signal Processing, Rome, Italy, 2–4 July 2013; pp. 6–10. [Google Scholar]
- Zidek, A.; Tailor, S.; Harle, R. Bellrock: Anonymous Proximity Beacons From Personal Devices. In Proceedings of the Pervasive Computing and Communications, Athens, Greece, 19–23 March 2018. [Google Scholar]
- Martin, P.D.; Rushanan, M.; Tantillo, T.; Lehmann, C.U.; Rubin, A.D. Applications of Secure Location Sensing in Healthcare. In Proceedings of the Bioinformatics Computational Biology, and Health Informatics, Seattle, WA, USA, 2–5 October 2016; pp. 58–67. [Google Scholar]
- Khazanie, N.; Matias, Y. Growing Eddystone with Ephemeral Identifiers: A Privacy Aware & Secure Open Beacon Format. Available online: https://security.googleblog.com/2016/04/growing-eddystone-with-ephemeral-identifiers.html (accessed on 26 September 2021).
- Lee, J.P.; Lee, J.G.; Lee, J.H.; Yoon, K.; Lee, J.K. Design of a Secure Disaster Notification System Using the Smartphone Based Beacon. In Proceedings of the Networks and Communications, Sydney, Australia, 23–24 December 2016; pp. 1–12. [Google Scholar]
- Ziobro, A. Overview-Kontakt.io Secure for Beacons with Firmware 4.0+ (Firmware Preceeding the 1.x and 2.x from 2019 and 2020). Available online: https://support.kontakt.io/hc/en-gb/articles/206762009-Kontakt-io-Secure-Shuffling (accessed on 26 September 2021).
- Dwivedi, A.D. BRISK: Dynamic Encryption Based Cipher for Long Term Security. Sensors 2021, 21, 5744. [Google Scholar] [CrossRef]
- Needham, R.M.; Wheeler, D.J. TEA Extensions, Technical Report; Computer Laboratory, University of Cambridge: Cambridge, UK, 1997. [Google Scholar]
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.J.B.; Seurin, Y.; Vikkelsoe, C. PRESENT: An Ultra-Lightweight Block Cipher. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Vienna, Austria, 10–13 September 2007; pp. 450–466. [Google Scholar]
- Usman, M.; Ahmed, I.; Aslam, M.I.; Khan, S.; Shah, U.A. SIT: A Lightweight Encryption Algorithm for Secure Internet of Things. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 402–411. [Google Scholar] [CrossRef]
- Sehrawat, D.; Gill, N.S. Performance Evaluation of Newly Proposed Lightweight Cipher, BRIGHT. Int. J. Intell. Eng. Syst. 2019, 12, 71–80. [Google Scholar] [CrossRef]
- Knudsen, L.R. Dynamic Encryption. Cyber Secur. Mobil. 2015, 3, 357–370. [Google Scholar] [CrossRef][Green Version]
- Lindh, J. Bluetooth Low Energy Beacons; Texas Instruments Incorporated: Dallas, TX, USA, 2015. [Google Scholar]
- Rajesh, S.; Paul, V.; Menon, V.G.; Khosravi, M.R. A Secure and Efficient Lightweight Symmetric Encryption Scheme for Transfer of Text Files between Embedded IoT Devices. Symmetry 2019, 11, 293. [Google Scholar] [CrossRef]
- Arora, R.; Parashar, A. Secure User Data in Cloud Computing Using Encryption Algorithms. Int. J. Eng. Res. Appl. 2013, 3, 1922–1926. [Google Scholar]
- Ahmad, S.; Alam, K.M.R.; Rahman, H.; Tamura, S. A Comparison between Symmetric and Asymmetric Key Encryption Algorithm based Decryption Mixnets. In Proceedings of the Networking Systems and Security, Dhaka, Bangladesh, 5–7 January 2015; pp. 1–5. [Google Scholar]
- Kumar, P.; Rawat, S.; Choudhury, T.; Pradhan, S. A Performance Based Comparison of Various Symmetric Cryptographic Algorithms in Run-Time Scenario. In Proceedings of the System Modeling Advancement in Research Trends, Moradabad, India, 25–27 November 2016; pp. 37–41. [Google Scholar]
- Wheeler, D.J.; Needham, R.M. TEA, a Tiny Encryption Algorithm. In Proceedings of the International Workshop on Fast Software Encryption, Leuven, Belgium, 14–16 December 1995; pp. 363–366. [Google Scholar]
- Wenling, W.; Zhang, L. LBlock: A Lightweight Block Cipher. In Proceedings of the Applied Cryptography and Network Security, Nerja, Spain, 7–10 June 2011; pp. 327–344. [Google Scholar]
- Beaulieu, R.; Shors, D.; Smith, J.; Treatman-Clark, S.; Weeks, B.; Wingers, L. The SIMON and SPECK Families of Lightweight Block Ciphers. In Proceedings of the 52nd Annual Design Automation Conference, San Francisco, CA, USA, 7–11 March 2013. [Google Scholar]
- Ashur, T. Improved Linear Trails for the Block Cipher Simon. IACR Crypto 2015, 2015, 285. [Google Scholar]
- Tupsamudre, H.; Bisht, S.; Mukhopadhyay, D. Differential Fault Analysis on the Families of SIMON and SPECK Ciphers. In Proceedings of the Workshop on Fault Diagnosis and Tolerance in Cryptography, Busan, Korea, 23 September 2014; pp. 40–48. [Google Scholar]
- Bansod, G.; Pisharoty, N.; Patil, A. PICO: An Ultra Lightweight and Low Power Encryption Design for Ubiquitous Computing. Def. Sci. J. 2016, 66, 259–265. [Google Scholar] [CrossRef]
- Beierle, C.; Jean, J.; Kölbl, S.; Leander, G.; Moradi, A.; Peyrin, T.; Sasaki, Y.; Sasdrich, P.; Sim, S.M. The SKINNY Family of Block Ciphers and Its Low-Latency Variant MANTIS. In Proceedings of the Advances in Cryptology, Santa Barbara, CA, USA, 14–18 August 2016; pp. 123–153. [Google Scholar]
- Vafaei, N.; Saha, S.; Bagheri, N.; Mukhopadhyay, D. Fault Attack on SKINNY Cipher. J. Hardw. Syst. Secur. 2020, 4, 277–296. [Google Scholar] [CrossRef]
- Yang, D.; Wen-Feng, Q.; Hua-Jin, C. Impossible Differential Attacks on the SKINNY Family of Block Ciphers. IET Inf. Secur. 2017, 11, 377–385. [Google Scholar] [CrossRef]
- Li, L.; Liu, B.; Wang, H. QTL: A New Ultra-Lightweight Block Cipher. Microprocess. Microsyst. 2016, 45, 45–55. [Google Scholar] [CrossRef]
- Sadeghi, S.; Bagheri, N.; Abdelraheem, M.A. Cryptanalysis of Reduced QTL Block Cipher. Microprocess. Microsyst. 2017, 52, 34–48. [Google Scholar] [CrossRef]
- Banik, S.; Pandey, S.K.; Peyrin, T.; Sasaki, Y.; Sim, S.M.; Todo, Y. GIFT: A Small Present Towards Reaching the Limit of Lightweight Encryption. In Proceedings of the Cryptographic Hardware and Embedded Systems, Taipei, Taiwan, 25–28 September 2017; pp. 321–345. [Google Scholar]
- Zhao, B.; Dong, X.; Meier, W.; Jia, K.; Wang, G. Generalized Related-key Rectangle Attacks on Block Ciphers with Linear Key Schedule: Applications to SKINNY and GIFT. Des. Codes Cryptogr. 2020, 13, 1103–1126. [Google Scholar] [CrossRef]
- Dalmasso, L.; Bruguier, F.; Benoit, P.; Torres, L. Evaluation of SPN-Based Lightweight Crypto-Ciphers. IEEE Access 2019, 7, 10559–10567. [Google Scholar] [CrossRef]
- Patil, J.; Bansod, G.; Kant, K.S. LiCi: A New Ultra-Lightweight Block Cipher. In Proceedings of the Emerging Trends Innovation in ICT, Pune, India, 3–5 February 2017; pp. 40–45. [Google Scholar]
- Aboshosha, B.W.; Dessouky, M.M.; Elsayed, A. Energy Efficient Encryption Algorithm for Low Resources Devices. Acad. Res. Community Publ. 2019, 3, 26. [Google Scholar] [CrossRef]
- Thabit, F.; Alhomdy, S.; Jagtap, S. Security Analysis and Performance Evaluation of a New Lightweight Cryptographic Algorithm for Cloud Computing. Glob. Transit. Proc. 2021, 2, 100–110. [Google Scholar] [CrossRef]
- Kumar, V.G.K.; Rai, C.S. Design and Implementation of Novel BRISI Lightweight Cipher for Resource Constrained Devices. Microprocess. Microsyst. 2021, 84, 104267. [Google Scholar] [CrossRef]
- Sophia, B.; Jeril, L.; Kavin Harnesh, M.; Lalith Kumar, V. A Secure Remote Clinical Sensor Network Approach for Privacy Enhancement. In Proceedings of the 2021 International Conference on Computing, Communication, Electrical and Biomedical Systems (ICCCEBS), Coimbatore, India, 25–26 March 2021; Volume 1916, p. 012107. [Google Scholar] [CrossRef]
- Mousavi, S.K.; Ghaffari, A. Data Cryptography in the Internet of Things Using the Artificial Bee Colony Algorithm in a Smart Irrigation System. J. Inf. Secur. Appl. 2021, 61, 102945. [Google Scholar] [CrossRef]
- Al-Husainy, M.A.F.; Al-Shargabi, B.; Aljawarneh, S. Lightweight Cryptography System for IoT Devices Using DNA. Comput. Electr. Eng. 2021, 95, 107418. [Google Scholar] [CrossRef]
- Rashmi Chawla, V.; Sehgal, R.; Nagpal, R. The RC7 Encryption Algorithm. Int. J. Secur. Its Appl. 2015, 9, 55–60. [Google Scholar] [CrossRef]
- Kelsey, J.; Schneier, B.; Wagner, D. Related-Key Cryptanalysis of 3-WAY, Biham-DES, CAST, DES-X, NewDES, RC2, and TEA. In Proceedings of the Information and Communications Security, Beijing, China, 11–14 November 1997; pp. 233–246. [Google Scholar]
- Lu, J. Related-Key Rectangle Attack on 36 Rounds of the XTEA Block Cipher. Int. J. Inf. Secur. 2008, 8, 1–11. [Google Scholar] [CrossRef]
- Suzaki, T.; Minematsu, K.; Morioka, S.; Kobayashi, E. Twine: A Lightweight, Versatile Block Cipher. In Proceedings of the ECRYPT Workshop on Lightweight Cryptography, Louvain-la-Neuve, Belgium, 28–29 November 2011; pp. 146–169. [Google Scholar]
- Webster, A.F.; Tavares, S.E. On the Design of S-Boxes. In Proceedings of the Advances in Cryptology — CRYPTO ’85 Proceedings, Santa Barbara, CA, USA, 18–22 August 1986; pp. 523–534. [Google Scholar]
- Thiemjarus, S. Pervasive Sensing for Fall Detection and Beyond. In Proceedings of the The International Advanced Medical Robotics Symposium, Bangkok, Thailand, 15–16 March 2019. [Google Scholar]
- Yu, X.; Wang, C.; Zhou, X. Review on Semi-Fragile Watermarking Algorithms for Content Authentication of Digital Images. Future Internet 2017, 9, 56. [Google Scholar] [CrossRef]





| Encryption Algorithm | Tech | Key Size (bits) | Block Size (bits) | Number of Rounds | Possible Attacks |
|---|---|---|---|---|---|
| TEA [57], 1994 | FN | 128 | 64 | 32, 64 | Equivalent keys attack [79] |
| XTEA [47], 1997 | FN | 128 | 64 | 32, 64 | Related-key rectangle attack [80] |
| PRESENT [48], 2007 | SPN | 80, 128 | 64 | 31 | Saturated, weak key, and linear attacks |
| LBlock [58], 2011 | FN | 80 | 64 | 32 | Saturated attack [81] |
| SIMON [59], 2013 | FN | 64–256 | 32–128 | 32–72 | Key recovery attack [60], differential fault attack [61] |
| PICO [62], 2016 | SPN | 128 | 64 | 32 | - |
| SKINNY [63],2016 | SPN | n, 2n, 3n | 64, 128 | 32–56 | Differential faults attacks [64], impossible differential attacks [65] |
| QTL [66], 2016 | FN | 64, 128 | 64 | 16, 20 | Differential and linear cryptanalysis attack [67] |
| GIFT [68], 2017 | SPN | 128 | 64,128 | 28, 40 | Related key attack [69], side channel attack, and chosen plaintext attack [70] |
| SIT [49], 2017 | SPN, FN | 64 | 64 | 5 | - |
| LiCi [71], 2017 | FN | 128 | 64 | 31 | - |
| BRIGHT [50],2019 | FN | 80–256 | 64, 128 | 32–37 | - |
| SLEA [72], 2019 | FN | 2n | n | m | |
| NLCA [73], 2021 | SPN, FN | 128 | 128 | 10–20 | - |
| SPECG [39], 2021 | FN | 256 | 256 | 0–255 | - |
| BRISK [46], 2021 | FN | 80 | 2n | 32 | - |
| Encryption Algorithm | Plaintext | Ciphertext | Bits Changed | Avalanche Effect |
|---|---|---|---|---|
| PRESENT | 0×00000000 4431B782 0×00000000 4431B783 | 0×1089e85d 077ed1be 0×4c07946e f36dac79 | 36 | 56.25% |
| XTEA | 0×C0037A37 6BC98019 0×4E0F748A 96239243 | 33 | 51.56% | |
| TEA | 0×DF6F3D7E 722BCE66 0×B1218894 9A57CB71 | 34 | 53.12% | |
| DLS-PRESENT | 0×efbc5f36 d12fc516 0×d486981b 2836795c | 35 | 54.68% | |
| DLS-XTEA | 0×6AB29657 E7DBE6C5 0×168FF88F 16114132 | 39 | 60.00% | |
| DLS-TEA | 0×8cefa414 fa32ba72 0×0548e8bc d1b1505e | 29 | 45.31% | |
| DLS-MD5 | 0×c665c7f4 d0f0993a 0×f39b4a36 9ef7d0cd | 35 | 54.68% |
| Encryption Algorithm | Average Bits Changed | Average Avalanche Effect |
|---|---|---|
| PRESENT | 32.01 | 50.01% |
| XTEA | 32.00 | 50.00% |
| TEA | 31.96 | 49.95% |
| DLS-PRESENT | 31.98 | 49.98% |
| DLS-XTEA | 32.01 | 50.01% |
| DLS-TEA | 32.00 | 50.00% |
| DLS-MD5 | 31.98 | 49.97% |
| Encryption Algorithm | Encryption Key | Ciphertext | Bits Changed | Avalanche Effect |
|---|---|---|---|---|
| PRESENT | 0×000041A7 10D63AF1 60B7ACD9 4431B782 0×000041A7 10D63AF1 60B7ACD9 4431B783 | 0×a6096f79 60a39158 0×cbb6a496 074871c0 | 41 | 64.06% |
| XTEA | 0×322E8C81 A941DA47 0×47892894 E99202F3 | 37 | 46.87% | |
| TEA | 0×E7239A15 7C4601DD 0×95AB191E CCD20FC3 | 25 | 39.06% | |
| DLS-PRESENT | 0×5611add9 e3cf63ec 0×00af538 ddeb18660 | 39 | 60.93% | |
| DLS-XTEA | 0×9fe73cda 5046966c 0×f69477c6 27cc670b | 35 | 54.68% | |
| DLS-TEA | 0×3dda8056 4c345547 0×abb8187c 2aa15d37 | 25 | 39.06% | |
| DLS-MD5 | 0×fe3ba2d6 43541e23 0×6b05a37d 40778e7b | 25 | 39.06% |
| Encryption Algorithm | Average Bits Changed | Average Avalanche Effect |
|---|---|---|
| PRESENT | 32.03 | 50.04% |
| XTEA | 32.01 | 50.01% |
| TEA | 32.00 | 50.01% |
| DLS-PRESENT | 31.97 | 49.96% |
| DLS-XTEA | 31.97 | 49.95% |
| DLS-TEA | 31.99 | 49.98% |
| DLS-MD5 | 31.97 | 49.96% |
| Encryption Algorithm | Plaintext Sensitivity | Key Sensitivity | ||
|---|---|---|---|---|
| Average Number of | Average Number of | |||
| Zeros | Ones | Zeros | Ones | |
| PRESENT | 31.97 | 32.02 | 32.02 | 31.97 |
| XTEA | 31.97 | 32.02 | 31.98 | 32.01 |
| TEA | 31.99 | 32.00 | 31.97 | 32.02 |
| DLS-PRESENT | 31.99 | 32.00 | 31.99 | 32.00 |
| DLS-XTEA | 31.99 | 32.00 | 32.01 | 31.98 |
| DLS-TEA | 32.00 | 31.99 | 32.00 | 31.99 |
| DLS-MD5 | 31.97 | 32.02 | 32.01 | 31.98 |
| Encryption Scheme | DLS-XTEA | TEA | XTEA |
|---|---|---|---|
| Power consumption (mV/hr) | 6.16 | 5.66 | 5.83 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Banani, S.; Thiemjarus, S.; Wongthavarawat, K.; Ounanong, N. A Dynamic Light-Weight Symmetric Encryption Algorithm for Secure Data Transmission via BLE Beacons. J. Sens. Actuator Netw. 2022, 11, 2. https://doi.org/10.3390/jsan11010002
Banani S, Thiemjarus S, Wongthavarawat K, Ounanong N. A Dynamic Light-Weight Symmetric Encryption Algorithm for Secure Data Transmission via BLE Beacons. Journal of Sensor and Actuator Networks. 2022; 11(1):2. https://doi.org/10.3390/jsan11010002
Chicago/Turabian StyleBanani, Sam, Surapa Thiemjarus, Kitti Wongthavarawat, and Nattapong Ounanong. 2022. "A Dynamic Light-Weight Symmetric Encryption Algorithm for Secure Data Transmission via BLE Beacons" Journal of Sensor and Actuator Networks 11, no. 1: 2. https://doi.org/10.3390/jsan11010002
APA StyleBanani, S., Thiemjarus, S., Wongthavarawat, K., & Ounanong, N. (2022). A Dynamic Light-Weight Symmetric Encryption Algorithm for Secure Data Transmission via BLE Beacons. Journal of Sensor and Actuator Networks, 11(1), 2. https://doi.org/10.3390/jsan11010002






