Misbehavior-Aware On-Demand Collaborative Intrusion Detection System Using Distributed Ensemble Learning for VANET
Abstract
:1. Introduction
2. Related Work
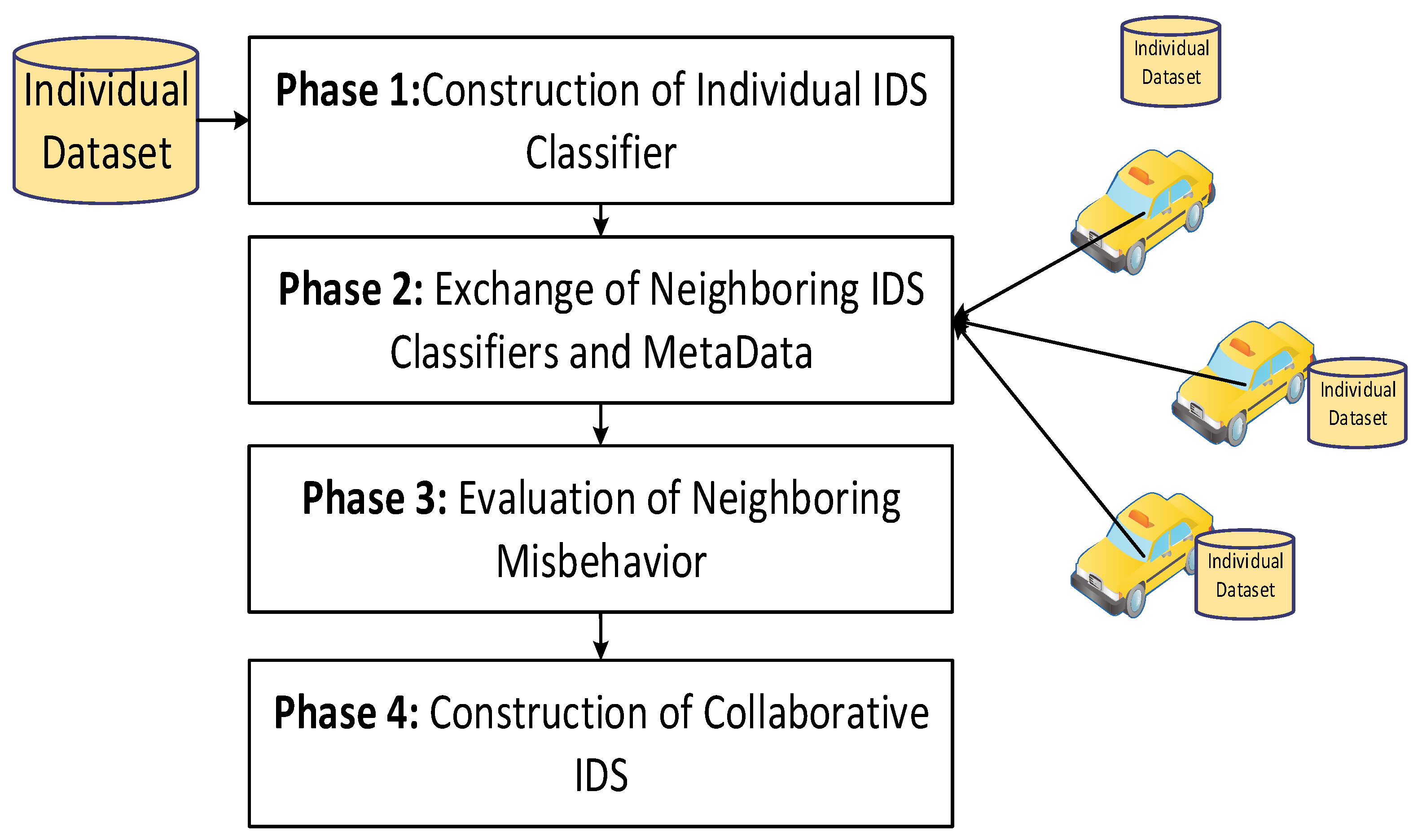
3. The Proposed MA-CIDs Model
3.1. Phase 1: Individual IDS Construction
3.2. Phase 2: Neighboring Classifiers and Metadata Exchanging
| Algorithm 1: On-Demand IDS Classifier Sharing Algorithm |
| Input: ,, , ,, , Output: . |
| Sender Vehicle 1: 2: broadcast (collaboration request message) Receiver Vehicle 1: 2: 3: 4: ): 5: ) 6 7: 20: return |
3.3. Phase 3: Neighboring Misbehavior Evaluation
| Algorithm 2: Misbehavior Evaluation Algorithm |
| Input: , , Output: . |
| 1: 2: 3: 4: 5: 6: 7: 8 9: 10: 11: if 12: return |
3.4. Phase 4: Collaborative IDS Construction
4. The Experimental Design and Results
4.1. The Experimental Environment Setup
4.2. The Performance Measures
4.3. Experimental Results
5. Analysis and Discussion
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Pathan, A.S.K. (Ed.) Security of Self-Organizing Networks: MANET, WSN, WMN, VANET; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Zhang, H.; Dai, S.; Li, Y.; Zhang, W. Real-time Distributed-Random-Forest-Based Network Intrusion Detection System Using Apache Spark. In Proceedings of the 2018 IEEE 37th International Performance Computing and Communications Conference (IPCCC), Orlando, FL, USA, 17–19 November 2018; pp. 1–7. [Google Scholar]
- Gasmi, R.; Aliouat, M. Vehicular Ad Hoc NETworks versus Internet of Vehicles—A Comparative View. In Proceedings of the 2019 International Conference on Networking and Advanced Systems (ICNAS), Annaba, Algeria, 26–27 June 2019; pp. 1–6. [Google Scholar]
- Chiti, F.; Fantacci, R.; Gu, Y.; Han, Z. Content sharing in Internet of Vehicles: Two matching-based user-association approaches. Veh. Commun. 2017, 8, 35–44. [Google Scholar] [CrossRef]
- Ji, B.; Zhang, X.; Mumtaz, S.; Han, C.; Li, C.; Wen, H.; Wang, D. Survey on the Internet of Vehicles: Network Architectures and Applications. IEEE Commun. Stand. Mag. 2020, 4, 34–41. [Google Scholar] [CrossRef]
- Santamaria, A.F.; Sottile, C.; De Rango, F.; Voznak, M. Road safety alerting system with radar and GPS cooperation in a VANET environment. In Wireless Sensing, Localization, and Processing IX; International Society for Optics and Photonics: Bellingham, WA, USA, 2014; Volume 9103, p. 91030G. [Google Scholar]
- Ghaleb, F.A.; Maarof, M.A.; Zainal, A.; Al-Rimy, B.; Alsaeedi, A.; Boulila, W. Alrimy Ensemble-Based Hybrid Context-Aware Misbehavior Detection Model for Vehicular Ad Hoc Network. Remote Sens. 2019, 11, 2852. [Google Scholar] [CrossRef] [Green Version]
- Wahab, O.A.; Mourad, A.; Otrok, H.; Bentahar, J. CEAP: SVM-based intelligent detection model for clustered vehicular ad hoc networks. Expert Syst. Appl. 2016, 50, 40–54. [Google Scholar] [CrossRef]
- Al-Rimy, B.A.S.; Maarof, M.A.; Alazab, M.; Alsolami, F.; Shaid, S.Z.M.; Ghaleb, F.A.; Al-Hadhrami, T.; Ali, A.M. A Pseudo Feedback-Based Annotated TF-IDF Technique for Dynamic Crypto-Ransomware Pre-Encryption Boundary Delineation and Features Extraction. IEEE Access 2020, 8, 140586–140598. [Google Scholar] [CrossRef]
- Al-Rimy, B.; Maarof, M.A.; Shaid, S.Z.M. Crypto-ransomware early detection model using novel incremental bagging with enhanced semi-random subspace selection. Future Gener. Comput. Syst. 2019, 101, 476–491. [Google Scholar] [CrossRef]
- Sharma, S.; Kaul, A. A survey on Intrusion Detection Systems and Honeypot based proactive security mechanisms in VANETs and VANET Cloud. Veh. Commun. 2018, 12, 138–164. [Google Scholar] [CrossRef]
- Liang, J.; Chen, J.; Zhu, Y.; Yu, R. A novel Intrusion Detection System for Vehicular Ad Hoc Networks (VANETs) based on differences of traffic flow and position. Appl. Soft Comput. 2019, 75, 712–727. [Google Scholar] [CrossRef]
- Ghaleb, F.A.; Maarof, M.A.; Zainal, A.; Al-Rimy, B.A.S.; Saeed, F.; Al Hadhrami, T. Hybrid and Multifaceted Context-Aware Misbehavior Detection Model for Vehicular Ad Hoc Network. IEEE Access 2019, 7, 159119–159140. [Google Scholar] [CrossRef]
- Azab, A.; Layton, R.; Alazab, M.; Oliver, J. Mining malware to detect variants. In Proceedings of the 2014 Fifth Cybercrime and Trustworthy Computing Conference, Auckland, New Zealand, 24–25 November 2014; pp. 44–53. [Google Scholar]
- Tzeng, S.-F.; Horng, S.-J.; Li, T.; Wang, X.; Huang, P.-H.; Khan, M.K. Enhancing Security and Privacy for Identity-Based Batch Verification Scheme in VANETs. IEEE Trans. Veh. Technol. 2017, 66, 3235–3248. [Google Scholar] [CrossRef]
- Kumar, N.; Chilamkurti, N. Collaborative trust aware intelligent intrusion detection in VANETs. Comput. Electr. Eng. 2014, 40, 1981–1996. [Google Scholar] [CrossRef]
- Engoulou, R.G.; Bellaïche, M.; Pierre, S.; Quintero, A. VANET security surveys. Comput. Commun. 2014, 44, 1–13. [Google Scholar] [CrossRef]
- Agrawal, S.; Agrawal, J. Survey on Anomaly Detection using Data Mining Techniques. Procedia Comput. Sci. 2015, 60, 708–713. [Google Scholar] [CrossRef] [Green Version]
- Lin, X.; Sun, X.; Ho, P.-H.; Shen, X. GSIS: A Secure and Privacy-Preserving Protocol for Vehicular Communications. IEEE Trans. Veh. Technol. 2007, 56, 3442–3456. [Google Scholar] [CrossRef] [Green Version]
- Daza, V.; Domingo-Ferrer, J.; Sebé, F.; Viejo, A. Trustworthy Privacy-Preserving Car-Generated Announcements in Vehicular Ad Hoc Networks. IEEE Trans. Veh. Technol. 2008, 58, 1876–1886. [Google Scholar] [CrossRef]
- Zhang, J.; Zulkernine, M.; Haque, A. Random-Forests-Based Network Intrusion Detection Systems. IEEE Trans. Syst. Man Cybern. Part C Appl. Rev. 2008, 38, 649–659. [Google Scholar] [CrossRef]
- Huang, D.; Misra, S.; Verma, M.; Xue, G. PACP: An Efficient Pseudonymous Authentication-Based Conditional Privacy Protocol for VANETs. IEEE Trans. Intell. Transp. Syst. 2011, 12, 736–746. [Google Scholar] [CrossRef]
- Shen, A.-N.; Guo, S.; Zeng, D.; Guizani, M. A lightweight privacy-preserving protocol using chameleon hashing for secure vehicular communications. In Proceedings of the 2012 IEEE Wireless Communications and Networking Conference (WCNC), Paris, France, 1–4 April 2012; pp. 2543–2548. [Google Scholar]
- Liu, J.K.; Yuen, T.H.; Au, M.H.; Susilo, W. Improvements on an authentication scheme for vehicular sensor networks. Expert Syst. Appl. 2014, 41, 2559–2564. [Google Scholar] [CrossRef] [Green Version]
- Li, W.; Song, H. ART: An Attack-Resistant Trust Management Scheme for Securing Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2015, 17, 960–969. [Google Scholar] [CrossRef]
- Chaubey, N. Security Analysis of Vehicular Ad Hoc Networks (VANETs): A Comprehensive Study. Int. J. Secur. Appl. 2016, 10, 261–274. [Google Scholar] [CrossRef]
- Daeinabi, A.; Rahbar, A.G.; Khademzadeh, A. VWCA: An efficient clustering algorithm in vehicular ad hoc networks. J. Netw. Comput. Appl. 2011, 34, 207–222. [Google Scholar] [CrossRef]
- Sedjelmaci, H.; Senouci, S.M. An accurate and efficient collaborative intrusion detection framework to secure vehicular networks. Comput. Electr. Eng. 2015, 43, 33–47. [Google Scholar] [CrossRef]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J.; Alazab, A. Hybrid Intrusion Detection System Based on the Stacking Ensemble of C5 Decision Tree Classifier and One Class Support Vector Machine. Electronics 2020, 9, 173. [Google Scholar] [CrossRef] [Green Version]
- Maglaras, L.A. A novel distributed intrusion detection system for vehicular ad hoc networks. Int. J. Adv. Comput. Sci. Appl. 2015, 6, 101–106. [Google Scholar]
- Jha, S.K.; Hassan, M. Building agents for rule-based intrusion detection system. Comput. Commun. 2002, 25, 1366–1373. [Google Scholar] [CrossRef]
- Li, L.; Yang, D.-Z.; Shen, F.-C. A novel rule-based Intrusion Detection System using data mining. In Proceedings of the 2010 3rd International Conference on Computer Science and Information Technology, Chengdu, China, 9–11 July 2010; Volume 6, pp. 169–172. [Google Scholar]
- Patel, S.K.; Sonker, A. Rule-Based Network Intrusion Detection System for Port Scanning with Efficient Port Scan Detection Rules Using Snort. Int. J. Futur. Gener. Commun. Netw. 2016, 9, 339–350. [Google Scholar] [CrossRef]
- Parameshwarappa, P.; Chen, Z.; Gangopadhyay, A. Analyzing attack strategies against rule-based intrusion detection systems. In Proceedings of the 19th International Conference on Distributed Computing and Networking-Workshops ICDCN’18, Varanasi, India, 4–7 January 2018; pp. 1–4. [Google Scholar]
- Barbará, D.; Jajodia, S. (Eds.) Applications of Data Mining in Computer Security; Springer Science & Business Media: Berlin, Germany, 2002; Volume 6. [Google Scholar]
- Yin, C.; Huang, S.; Su, P.; Gao, C. Secure routing for large-scale wireless sensor networks. In Proceedings of the International Conference on Communication Technology Proceedings, 2003. ICCT 2003, Beijing, China, 9–11 April 2003; Volume 2, pp. 1282–1286. [Google Scholar]
- Çam, H.; Ozdemir, S.; Nair, P.; Muthuavinashiappan, D.; Sanli, H.O. Energy-efficient secure pattern based data aggregation for wireless sensor networks. Comput. Commun. 2006, 29, 446–455. [Google Scholar] [CrossRef]
- Su, M.-Y. Real-time anomaly detection systems for Denial-of-Service attacks by weighted k-nearest-neighbor classifiers. Expert Syst. Appl. 2011, 38, 3492–3498. [Google Scholar] [CrossRef]
- Al-Jarrah, O.; Siddiqui, A.; ElSalamouny, M.; Yoo, P.; Muhaidat, S.; Kim, K. Machine-Learning-Based Feature Selection Techniques for Large-Scale Network Intrusion Detection. In Proceedings of the 2014 IEEE 34th International Conference on Distributed Computing Systems Workshops, Madrid, Spain, 30 June–3 July 2014; pp. 177–181. [Google Scholar]
- Rani, M.S.; Xavier, S.B. A Hybrid Intrusion Detection System Based on C5. 0 Decision Tree Algorithm and One-Class SVM with CFA. Int. J. Innov. Res. Comput. Commun. Eng. 2015, 3, 5526–5537. [Google Scholar] [CrossRef]
- Yi, Y.; Wu, J.; Xu, W. Incremental SVM based on reserved set for network intrusion detection. Expert Syst. Appl. 2011, 38, 7698–7707. [Google Scholar] [CrossRef]
- Amor, N.B.; Benferhat, S.; Elouedi, Z. Naive Bayes vs decision trees in intrusion detection systems. In Proceedings of the 2004 ACM symposium on Applied computing—SAC’04, Nicosia, Cyprus, 14–17 March 2004; pp. 420–424. [Google Scholar]
- Salo, F.; Injadat, M.; Nassif, A.B.; Shami, A.; Essex, A. Data Mining Techniques in Intrusion Detection Systems: A Systematic Literature Review. IEEE Access 2018, 6, 56046–56058. [Google Scholar] [CrossRef]
- Kim, G.; Lee, S.; Kim, S. A novel hybrid intrusion detection method integrating anomaly detection with misuse detection. Expert Syst. Appl. 2014, 41, 1690–1700. [Google Scholar] [CrossRef]
- Al-Yaseen, W.L.; Othman, Z.A.; Nazri, M.Z.A. Multi-level hybrid support vector machine and extreme learning machine based on modified K-means for intrusion detection system. Expert Syst. Appl. 2017, 67, 296–303. [Google Scholar] [CrossRef]
- Muniyandi, A.P.; Rajeswari, R.; Rajaram, R. Network Anomaly Detection by Cascading K-Means Clustering and C4.5 Decision Tree algorithm. Procedia Eng. 2012, 30, 174–182. [Google Scholar] [CrossRef] [Green Version]
- Thaseen, I.S.; Kumar, C.A. Intrusion detection model using fusion of chi-square feature selection and multi class SVM. J. King Saud Univ. Comput. Inf. Sci. 2017, 29, 462–472. [Google Scholar] [CrossRef] [Green Version]
- Shams, E.A.; Rizaner, A.; Ulusoy, A.H. Trust aware support vector machine intrusion detection and prevention system in vehicular ad hoc networks. Comput. Secur. 2018, 78, 245–254. [Google Scholar] [CrossRef]
- Zeng, Y.; Qiu, M.; Ming, Z.; Liu, M. Senior2Local: A Machine Learning Based Intrusion Detection Method for VANETs. In Proceedings of the Computer Vision, Tokyo, Japan, 10–12 December 2018; Springer Science and Business Media LLC: Berlin, Germany, 2018; pp. 417–426. [Google Scholar]
- Zhou, M.; Han, L.; Lu, H.; Fu, C. Distributed collaborative intrusion detection system for vehicular Ad Hoc networks based on invariant. Comput. Netw. 2020, 172, 107174. [Google Scholar] [CrossRef]
- Zhang, T.; Zhu, Q. Distributed Privacy-Preserving Collaborative Intrusion Detection Systems for VANETs. IEEE Trans. Signal Inf. Process. Netw. 2018, 4, 148–161. [Google Scholar] [CrossRef]
- Zhang, T.; Zhu, Q. Differentially Private Collaborative Intrusion Detection Systems for VANETs 2020. arXiv 2020, arXiv:2005.00703. [Google Scholar]
- Schmidt, D.A.; Khan, M.S.; Bennett, B.T. Spline-based intrusion detection for VANET utilizing knot flow classification. Int. Technol. Lett. 2020, 3, e155. [Google Scholar] [CrossRef] [Green Version]
- Schmidt, D. Knot Flow Classification and its Applications in Vehicular Ad-Hoc Networks (VANET). Master’s Thesis, East Tennessee State University, Johnson City, TN, USA, 2020. [Google Scholar]
- Gao, Y.; Wu, H.; Song, B.; Jin, Y.; Luo, X.; Zeng, X. A Distributed Network Intrusion Detection System for Distributed Denial of Service Attacks in Vehicular Ad Hoc Network. IEEE Access 2019, 7, 154560–154571. [Google Scholar] [CrossRef]
- Uzcategui, R.; De Sucre, A.J.; Acosta-Marum, G. Wave: A tutorial. IEEE Commun. Mag. 2009, 47, 126–133. [Google Scholar] [CrossRef]
- Zhang, L.; Wu, Q.; Solanas, A.; Domingo-Ferrer, J. A Scalable Robust Authentication Protocol for Secure Vehicular Communications. IEEE Trans. Veh. Technol. 2009, 59, 1606–1617. [Google Scholar] [CrossRef] [Green Version]





| Symbol | Description |
|---|---|
| The local trained classifier | |
| Time threshold for resending the local classifier | |
| Threshold of number of sharing requests per area | |
| Elapsed time since last approved sharing | |
| number of sharing requests per area | |
| Set of the number sharing requests | |
| Sharing decision true or false |
| Symbol | Description |
|---|---|
| Set of all received classifiers | |
| The corresponding set of all precisions of the as reported by collaborative vehicles | |
| The corresponding set of all recalls as reported by collaborative vehicles | |
| The classifier shared by vehicle | |
| The precision, recall, and F1 score of the, respectively. | |
| The corresponding set of F1 scores of the as tested by receiver vehicle | |
| Set of all evaluated with their ranks | |
| The mean of the box-and-whisker plot | |
| The upper adjacent value, and lower upper adjacent value of the box-and-whisker plot | |
| are the first and third quartile, and is the entire quartile range |
| Attacks in Dataset | Attack Type |
|---|---|
| Denial of Service (DoS) | Back, Land, Neptune, Pod, Smurf, Teardrop, Mailbomb, Processtable, Udpstorm, Apache2, Worm |
| Probe | Satan, IPsweep, Nmap, Portsweep, Mscan, Saint |
| R2L | Guess_password, Ftp_write, Imap, Phf, Multi, hop, Warezmaster, Xlock, Xsnoop, Snmpguess, Snmpgetattack, Httptunnel, Sendmail, Named |
| U2R | Buffer_overflow, Loadmodule, Rootkit, Perl, Sqlattack, Xterm, Ps |
| Tested Model | Precision | Recall | F1 Score | FPR | FNR | |
|---|---|---|---|---|---|---|
| MA-CIDS (RF) | 0.97 | 0.97 | 0.98 | 0.97 | 0.04 | 0.02 |
| MA-CIDS (SVM) | 0.94 | 0.92 | 0.90 | 0.95 | 0.11 | 0.00 |
| MA-CIDS (XGBoost) | 0.96 | 0.96 | 0.95 | 0.95 | 0.04 | 0.05 |
| CIDS (RF) | 0.92 | 0.91 | 0.95 | 0.93 | 0.11 | 0.05 |
| CIDS (SVM) | 0.86 | 0.80 | 0.99 | 0.89 | 0.29 | 0.00 |
| CIDS (XGBoost) | 0.93 | 0.93 | 0.93 | 0.93 | 0.08 | 0.07 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
A. Ghaleb, F.; Saeed, F.; Al-Sarem, M.; Ali Saleh Al-rimy, B.; Boulila, W.; Eljialy, A.E.M.; Aloufi, K.; Alazab, M. Misbehavior-Aware On-Demand Collaborative Intrusion Detection System Using Distributed Ensemble Learning for VANET. Electronics 2020, 9, 1411. https://doi.org/10.3390/electronics9091411
A. Ghaleb F, Saeed F, Al-Sarem M, Ali Saleh Al-rimy B, Boulila W, Eljialy AEM, Aloufi K, Alazab M. Misbehavior-Aware On-Demand Collaborative Intrusion Detection System Using Distributed Ensemble Learning for VANET. Electronics. 2020; 9(9):1411. https://doi.org/10.3390/electronics9091411
Chicago/Turabian StyleA. Ghaleb, Fuad, Faisal Saeed, Mohammad Al-Sarem, Bander Ali Saleh Al-rimy, Wadii Boulila, A. E. M. Eljialy, Khalid Aloufi, and Mamoun Alazab. 2020. "Misbehavior-Aware On-Demand Collaborative Intrusion Detection System Using Distributed Ensemble Learning for VANET" Electronics 9, no. 9: 1411. https://doi.org/10.3390/electronics9091411







