A Hybrid Cryptography Scheme for NILM Data Security
Abstract
1. Introduction
- A.
- Contributions of the paper
- First, we seek a method suitable for NILM data, which mainly belongs to the field of practical engineering application innovation.
- Second, after detailed analysis on the different classical cryptography techniques applied to NILM data, we conclude the most suitable scheme for NILM data.
- Finally, we present a performance analysis of security algorithms suitable for NILM data through practical examples.
- B.
- Organization of the paper
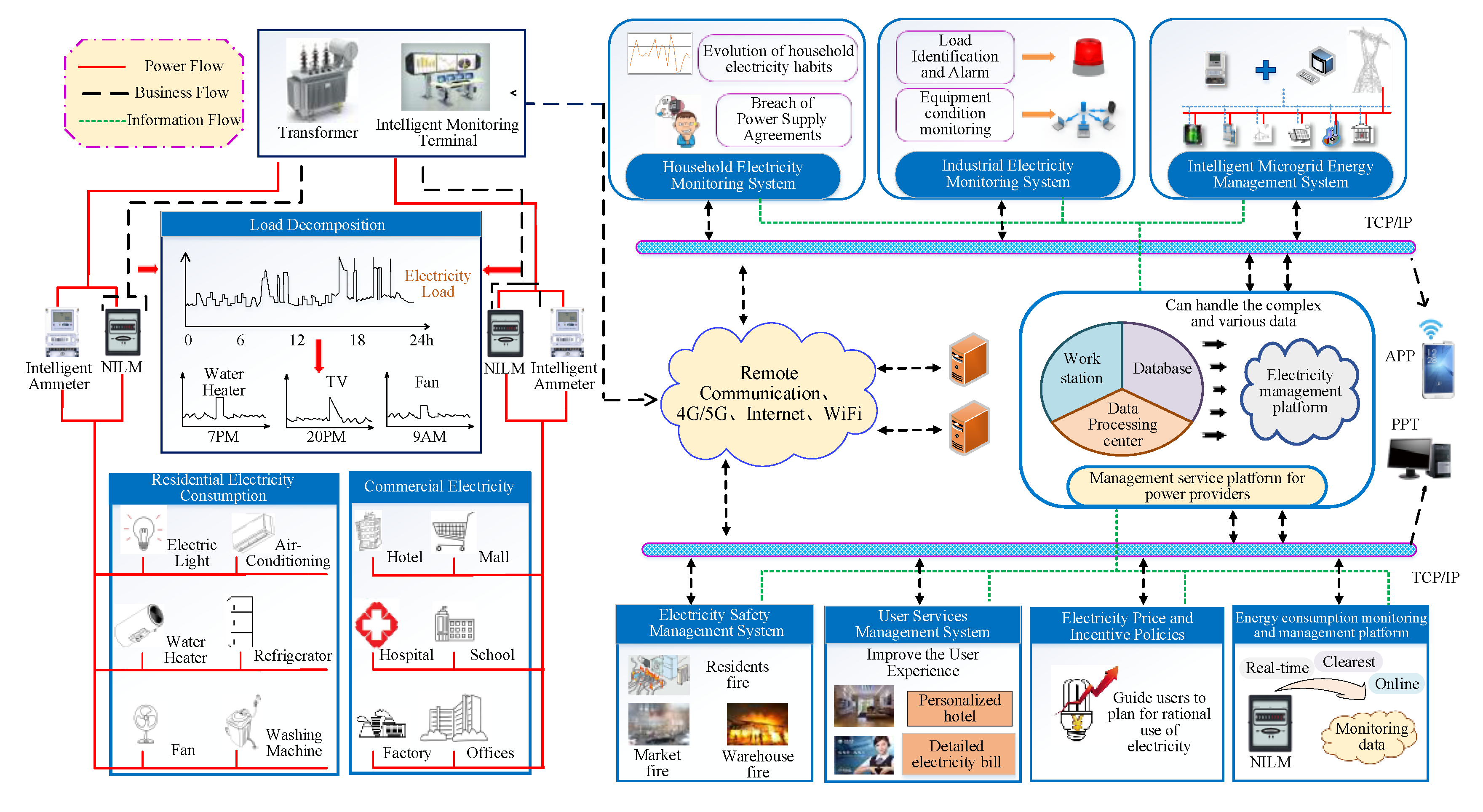
2. Technology of Non-Intrusive Load Monitoring
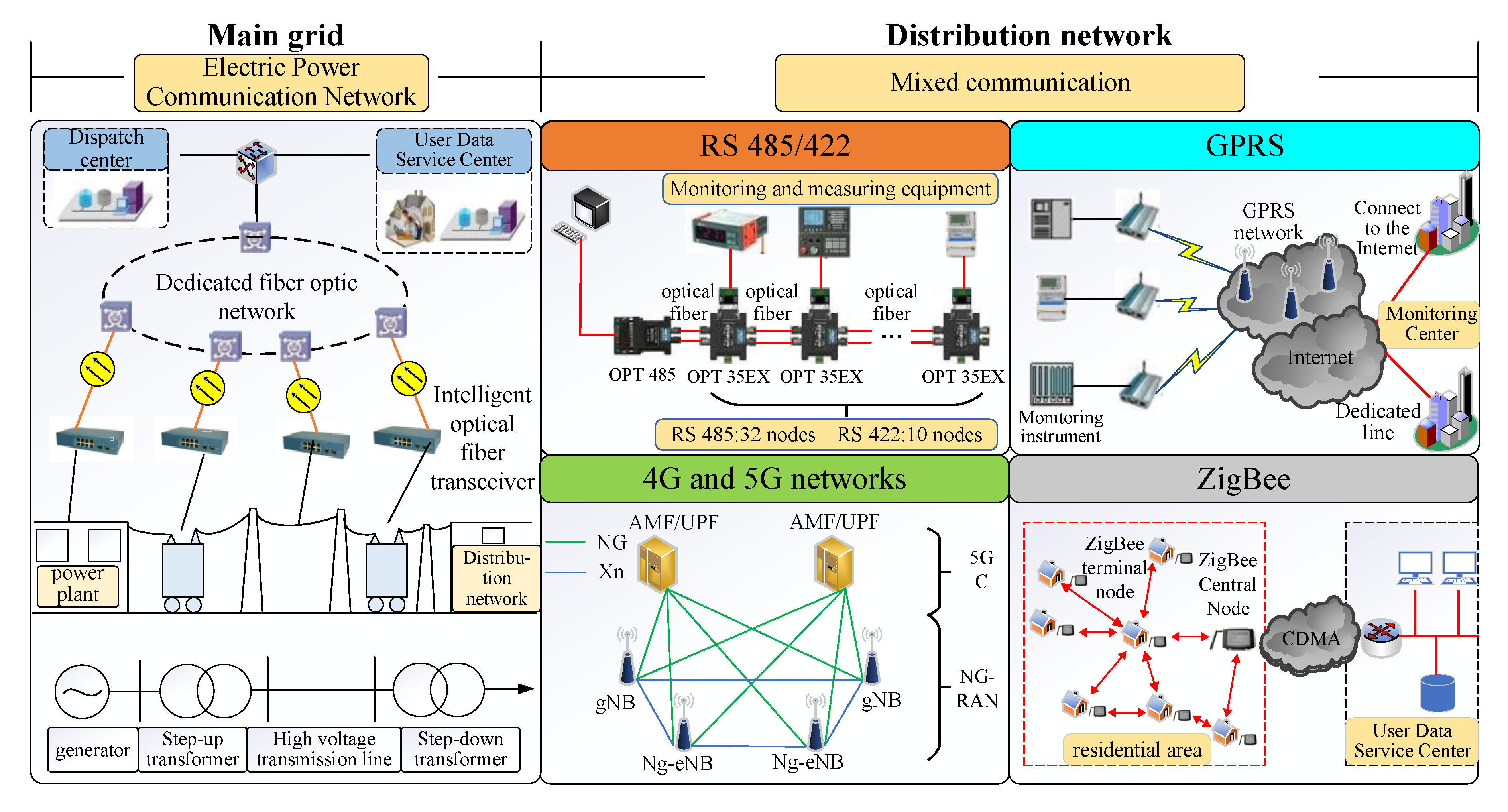
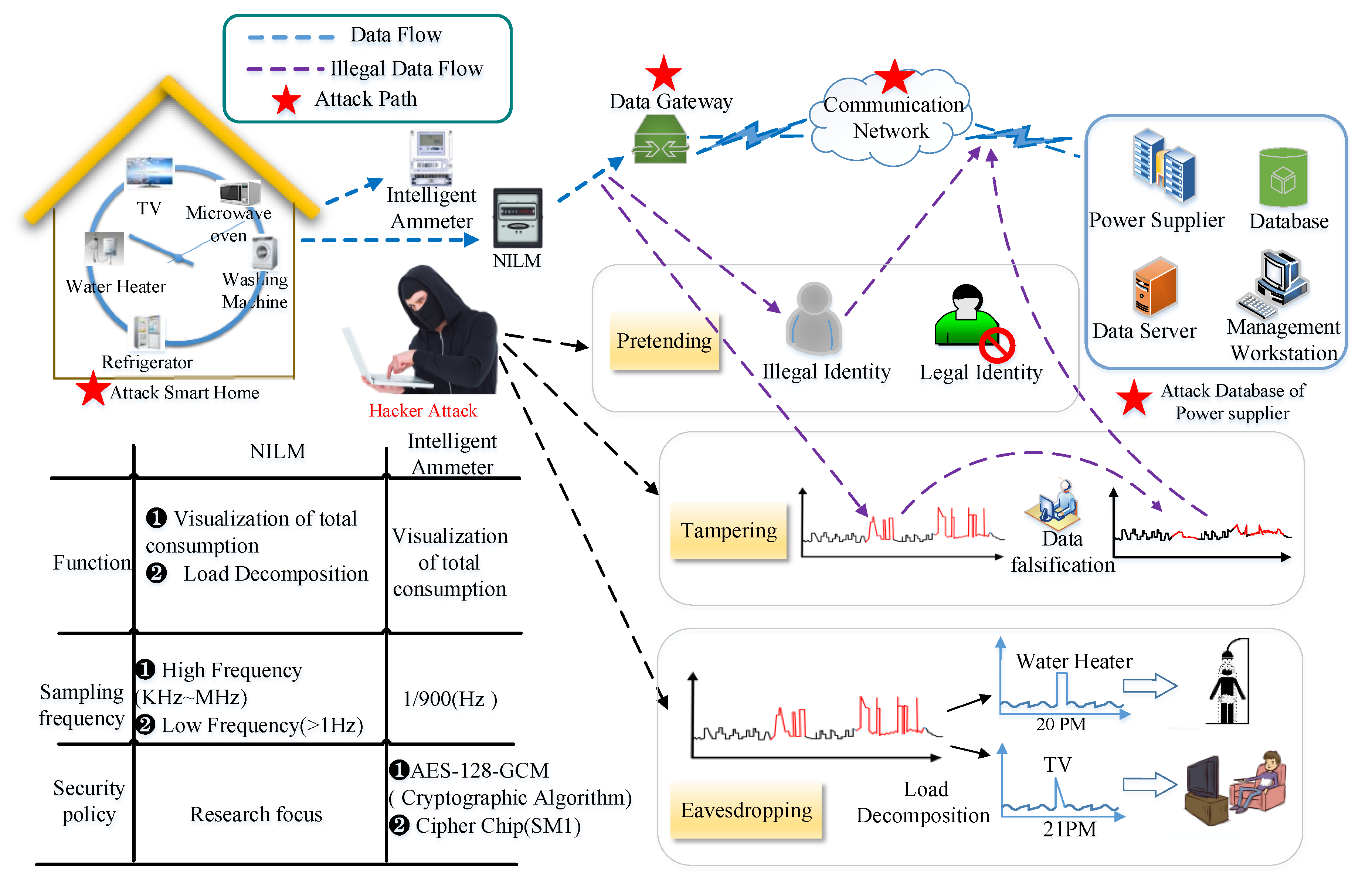
3. NILM Data Transmission Security
4. NILM Data Privacy Protection Scheme Based on Cryptographic Algorithm
4.1. Data Cryptography Technology
4.2. NILM Data Privacy Protection Scheme Based on Hybrid Cipher Algorithm
- (1)
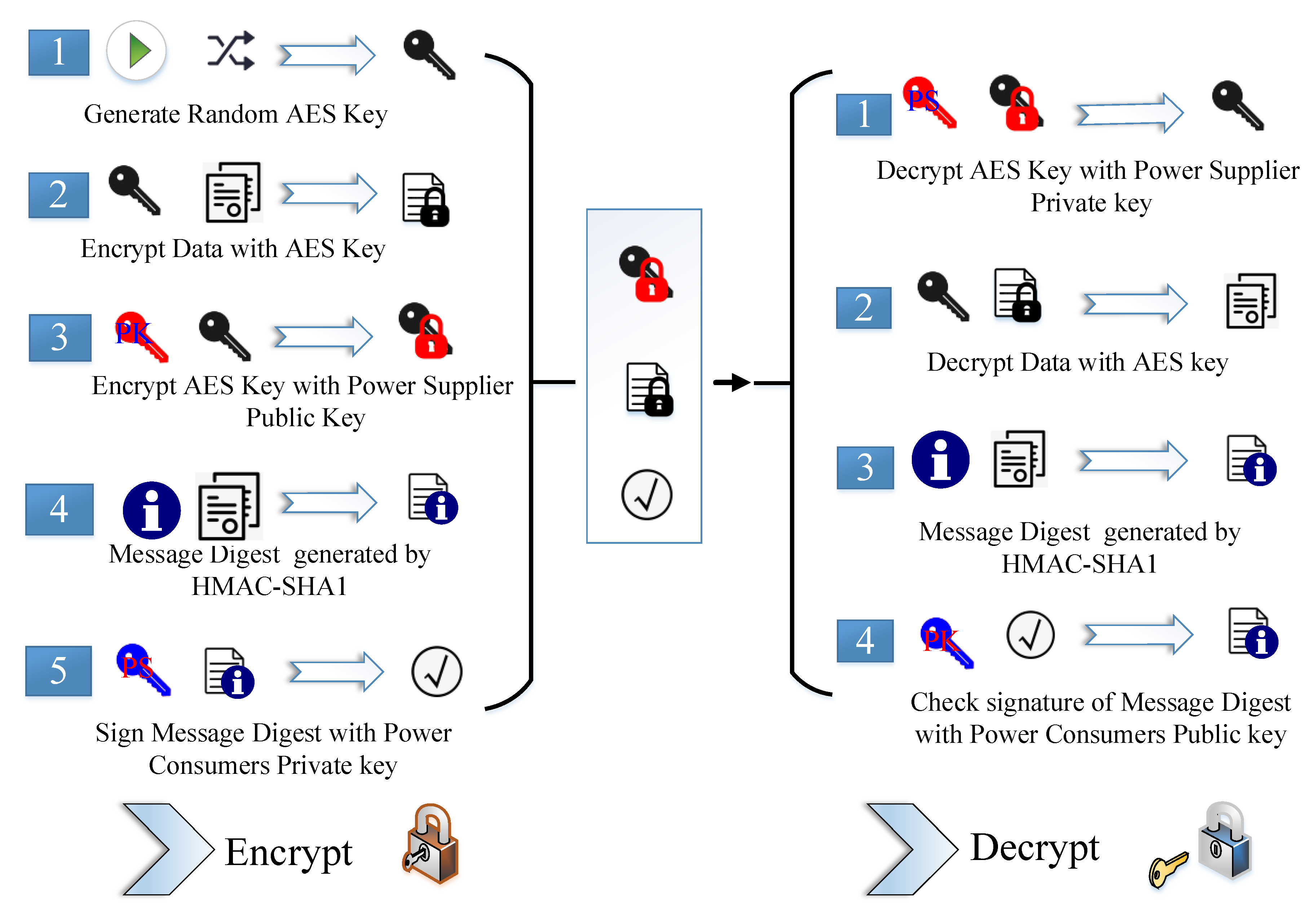
- Hybrid cipher algorithm. The scheme description is shown in Figure 5. Aiming at the threats of eavesdropping, tampering, and falsification in electro-data, three kinds of encryption algorithms, AES, RSA, and HMAC-SHA1, were used in this scheme. RSA algorithm protects the key of AES algorithm and AES algorithm encrypts the users’ large data. It can not only realize the safe and convenient key management, but also ensure the speed of data encryption. However, there are still loopholes in key management of RSA as the public key is public to the outside. If user B masquerades user A to send data to the power supplier by its public key, the power supplier cannot recognize the true identity of the sender. In order to solve this problem, hash algorithm HMAC-SHA1 was introduced. HMAC-SHA1 is a one-way encryption algorithm. Users can generate one unique digital digest with a specific length for real-time electro-data and combine it with RSA algorithm to generate users’ digital signature, and the integrity of data transmission and identity authentication of the sender can be guaranteed.
- (2)
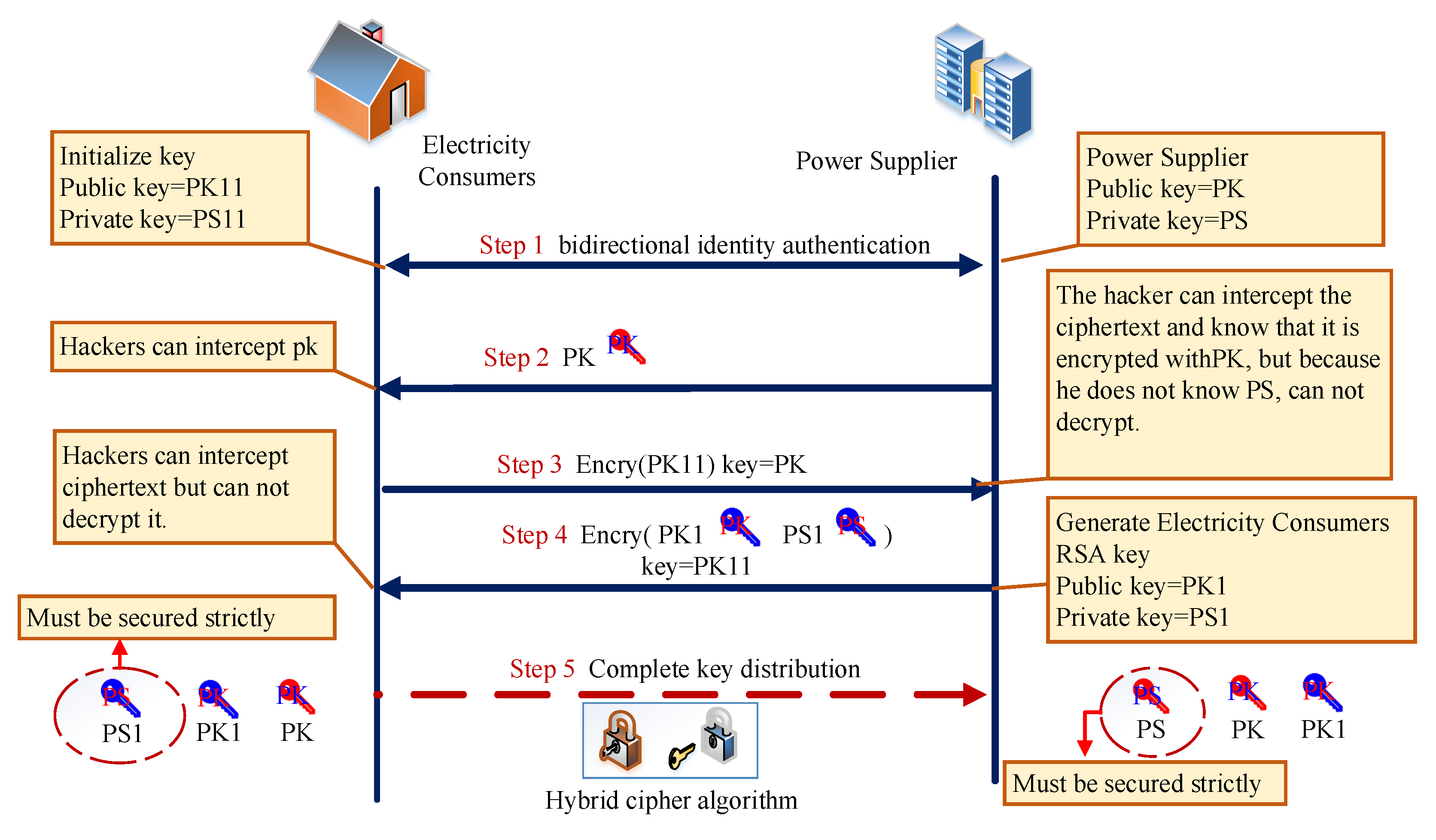
- Key distribution and management. The electricity customers newly load NILM and both sides conduct network authentication. The power supplier pre-installs the public key (PK) on the user side. NILM has configured factory initialization key (public key = PK11, private key = PS11). The power supplier has the key pairs public key = PK and private key = PS. The key distribution is shown in Figure 6.
- Power supplier sends the public key PK to electricity consumers. At this time, hackers can intercept PK;
- Electricity customers received PK and compared it with the public key pre-installed by the power supplier in NILM. If they are consistent, the public key is proved to be legal and the next step will be executed. If they are inconsistent, the public key is considered to be illegal and the next step will not be executed;
- Electricity consumers use the public key PK to encrypt the public key PK11 initialized in the NILM device and transmit it to the power supplier. At this time, the hacker can intercept the ciphertext and know that it is encrypted through PK, but because the hacker does not know the private key PS, he cannot decrypt the ciphertext;
- Power supplier receives the ciphertext, decrypts it with private key PS, and gets PK11;
- RSA key pair (public key = PK1, private key = PS1) is randomly generated by the key management center of the power supplier, encrypted with PK11, and transmitted to the user. Even if hackers intercept ciphertext, they cannot decrypt it. Electricity consumers decrypt the ciphertext with PS11 and obtain the public key PK1 and PS1 distributed by power supplier. The key distribution is complete;
- Electricity consumers need to secure private key PS1, and keep PK and PK1. The power supplier should keep the PS secret and have all users’ public key sequences. The key based on AES algorithm is generated randomly every time data are sent, so that it can be used up and discarded without saving and management, which effectively reduces the difficulty of key management.
- (3)
- Algorithm flow. After the electricity customer newly installs the non-intrusive load detection device and officially runs online, the power supplier side immediately initializes the electricity customer’s meter data, and identifies the electricity customer identity as A. Electricity consumers obtain PS1, PK1, and public key PK sent down by the power supplier. If electricity consumers need to send electricity data (start with identification A) to the power supplier, AES key should be randomly generated to encrypt the plaintext data and generate the ciphertext block of plaintext. Public key PK of power supplier is used to encrypt AES key to get the key ciphertext block. HMAC-SHA1 algorithm generates the digital digest for data, and the PS1 private key of electricity consumers encrypts it to form a digital signature. When the power supplier receives data sent from electricity consumers, the key ciphertext block with private key PS is firstly decrypted to get the AES key. Then, the AES key is used to decrypt the plaintext ciphertext block to obtain plain text. Finally, the AES key is discarded. According to the identification of user A in plain text, choose public key PA of user A to decrypt the digital signature. If there is no solution, it is shown that electricity customers’ identity information has been masqueraded and then discarded. Otherwise, extract the corresponding digital summary. The power supplier uses HMAC-SHA1 algorithm to get one new digital digest with the decrypted plain text and compares it with the received digital digest. If the two parts are consistent, it indicates that data integrity is maintained and the data have not been tampered with. The process of data transmission and reception is over. Similarly, if the power supplier needs to send information to the electricity customers, the same process should be adopted. The flow is shown in Figure 7.
5. Performance Analysis
5.1. Analysis of Encryption and Decryption Efficiency of AES Algorithm
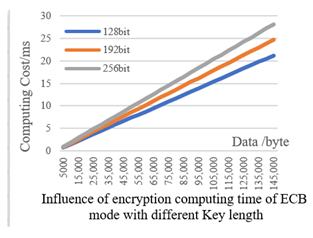
5.1.1. Computing Cost Analysis of Encryption in Different Working Modes
5.1.2. Comparative Analysis of Computing Cost between Encryption and Decryption
5.1.3. Influence on Encryption and Decryption Computing Cost with Different Key Lengths
5.2. Encryption and Decryption Efficiency of RSA Algorithm of Different Key Lengths
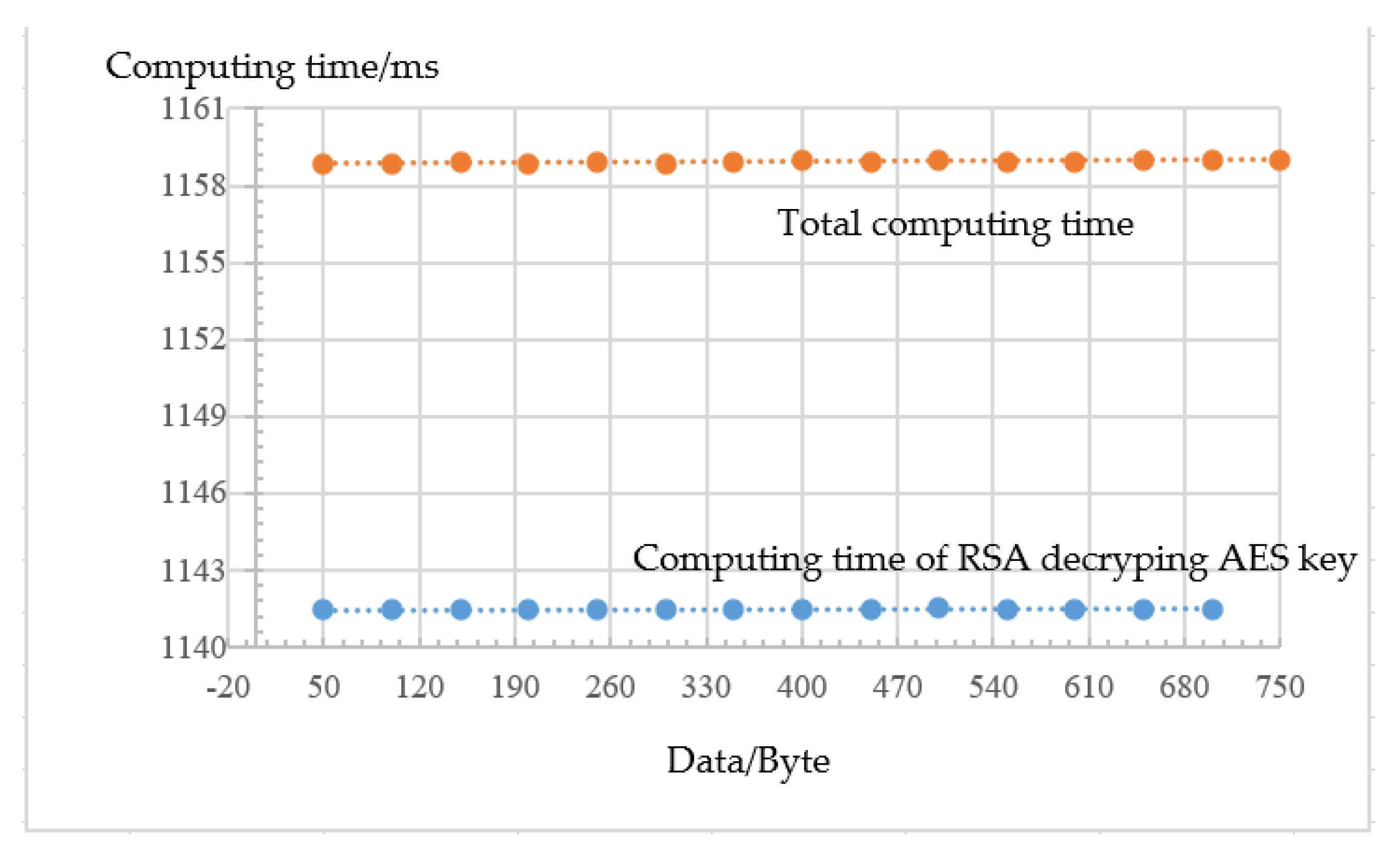
5.3. Hybrid Cryptography Scheme Test
6. Conclusions
- Five working modes of AES algorithm, including ECB, CBC, OFB, CFB, and CTR, were tested with different key lengths of 128 bit, 192 bit, and 256 bit, respectively. The test results showed that the computing cost of the five working modes was linear with the data length and the key length. In addition to CTR mode, the computing cost of the other four modes was highly coincident. When the data quantity of CTR mode was 145,000 byte, the computing cost of mode was only 2.5 ms higher than that of other modes, so it can be drawn that the computing cost of the five working modes is the same. From the test, the encryption and decryption time of the CTR mode were the same. On the basis of the real-time requirement of the NILM system, the AES-128-CTR mode was selected as the working mode of the hybrid cipher scheme.
- The efficiency of RSA algorithm with the key lengths of 1024 bit and 2048 bit was tested. The test results showed that speed of RSA public encryption was fast and private encryption was slow. The speed of data signature was slow and data signature verification was fast. Considering the security requirements of NILM, RSA-2048 was selected as the working mode of the hybrid cipher scheme.
- The effectiveness and efficiency of the hybrid cipher algorithm scheme were tested. By testing many times on the developed interface, the encrypted data were consistent with the decrypted data. Information digest of the power consumers and power supplier was consistent; therefore, the NILM hybrid cipher algorithm was effective. The computing cost of RSA decryption and signature basically determined the computing cost of the total scheme.
Author Contributions
Funding
Conflicts of Interest
References
- Hart, G.W. Nonintrusive appliance load monitoring. Proc. IEEE 1992, 80, 1870–1891. [Google Scholar] [CrossRef]
- Chen, Y.; Martínez-Ortega, J.-F.; Castillejo, P.; López, L. A homomorphic-based multiple data aggregation scheme for smart grid. IEEE Sens. J. 2019, 19, 3921–3929. [Google Scholar] [CrossRef]
- Abdallah, A.; Shen, X.S. A lightweight lattice-based homomorphic privacy-preserving data aggregation scheme for smart grid. IEEE Trans. Smart Grid 2018, 9, 396–405. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Zeadally, S.; Vinel, A.; Yang, L.T. Efficient and privacy-preserving data aggregation scheme for smart grid against internal adversaries. IEEE Trans. Smart Grid 2017, 8, 2411–2419. [Google Scholar] [CrossRef]
- Knirsch, F.; Eibl, G.; Engel, D. Error-resilient masking approaches for privacy preserving data aggregation. IEEE Trans. Smart Grid 2018, 9, 3351–3361. [Google Scholar] [CrossRef]
- Sui, Z.; De Meer, H. An efficient signcryption protocol for hop-by-Hop data aggregations in smart grids. IEEE IEEE J. Sel. Areas Commun. 2020, 38, 132–140. [Google Scholar] [CrossRef]
- Diao, F.; Zhang, F.; Cheng, X. A privacy-preserving smart metering scheme using linkable anonymous credential. IEEE Trans. Smart Grid 2015, 6, 461–467. [Google Scholar] [CrossRef]
- Zhao, J.; Liu, J.; Qin, Z.; Ren, K. Privacy protection scheme based on remote anonymous attestation for trusted smart meters. IEEE Trans. Smart Grid 2018, 9, 3313–3320. [Google Scholar] [CrossRef]
- Gong, Y.; Cai, Y.; Guo, Y.; Fang, Y. A privacy-preserving scheme for incentive-based demand response in the smart grid. IEEE Trans. Smart Grid 2016, 7, 1304–1313. [Google Scholar] [CrossRef]
- Ratliff, L.J.; Dong, R.; Ohlsson, H.; Cárdenas, A.A.; Sastry, S.S. Privacy and customer segmentation in the smart grid. In Proceedings of the 53rd IEEE Conference on Decision and Control, Los Angeles, CA, USA, 15–17 December 2014. [Google Scholar]
- Li, H.; Liu, D.; Dai, Y.; Luan, T.H.; Yu, S. Personalized search over encrypted data with efficient and secure updates in mobile clouds. IEEE Trans. Emerging Top. Comput. 2018, 6, 97–109. [Google Scholar] [CrossRef]
- Fu, Z.; Ren, K.; Shu, J.; Sun, X.; Huang, F. Enabling personalized search over encrypted outsourced data with efficiency improvement. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 2546–2559. [Google Scholar] [CrossRef]
- Kumar, P.; Gurtov, A.; Sain, M.; Martin, A.; Ha, P.H. Lightweight authentication and key agreement for smart metering in smart energy networks. IEEE Trans. Smart Grid 2019, 10, 4349–4359. [Google Scholar] [CrossRef]
- He, K.; Jakovetic, D.; Zhao, B.; Stankovic, V.; Stankovic, L.; Cheng, S. A generic optimisation-based approach for improving non-intrusive load monitoring. IEEE Trans. Smart Grid 2019, 10, 6472–6480. [Google Scholar] [CrossRef]
- Rahimpour, A.; Qi, H.; Fugate, D.; Kuruganti, T. Non-intrusive energy disaggregation using non-negative matrix factorization with sum-to-k constraint. IEEE Trans. Power Syst. 2017, 32, 4430–4441. [Google Scholar] [CrossRef]
- He, J.; Zhang, Z.; Zhu, L.; Zhu, Z.; Liu, J.; Gai, K. An efficient and accurate nonintrusive load monitoring scheme for power consumption. IEEE Internet Things J. 2019, 6, 9054–9063. [Google Scholar] [CrossRef]
- Morais, L.R.; Castro, A.R.G. Competitive autoassociative neural networks for electrical appliance identification for non-Intrusive load monitoring. IEEE Access 2019, 7, 111746–111755. [Google Scholar] [CrossRef]
- Rehman, A.U.; Lie, T.T.; Vallès, B.; Tito, S.R. Event-detection algorithms for low sampling nonintrusive load monitoring systems based on low complexity statistical features. IEEE Trans. Instrum. Meas. 2020, 69, 751–759. [Google Scholar] [CrossRef]
- Liu, Y.; Sun, Y.; Li, B. A modified IP-based NILM approach using appliance characteristics extracted by 2-SAX. IEEE Access 2019, 7, 48119–48128. [Google Scholar] [CrossRef]
- Chen, P.; Zhong, S. A non-intrusive load monitoring and identification system based on cloud platform. Appl. Electron. Tech. 2018, 44, 91–95. [Google Scholar]
- Wang, Z.; Wang, G.; Li, Y.; Tong, J. An encryption method for IEC 61850-9-2LE packet based on tiny encryption algorithm. Autom. Electr. Power Syst. 2016, 40, 121–127. [Google Scholar]
- Kolter, J.Z.; Johnson, M.J. REDD: A public data set for energy disaggregation rese arch. In Proceedings of the KDD workshop on Data Mining Applications in Sustainability (SustKDD 2011), San Diego, CA, USA, 21–24 August 2011. [Google Scholar]
- Cheng, X.; Li, L.; Wu, H.; Ding, Y.; Song, Y.; Sun, W. A survey of the research on non-intrusive load monitoring and disaggregation. Power Syst. Technol. 2016, 40, 3108–3117. [Google Scholar]
- Pereira, L.; Nunes, N. Performance evaluation in non-intrusive load monitoring: Datasets, metrics, and tools-A review. Wires Data Min. Knowl. Discovery 2018, 8. [Google Scholar] [CrossRef]
- Huang, B.; Knox, M.; Bradbury, K.; Collins, L.M.; Newell, R.G. Non-intrusive load monitoring system performance over a range of low frequency sampling rates. In Proceedings of the 2017 IEEE 6th International Conference on Renewable Energy Research and Applications (ICRERA), San Diego, CA, USA, 5–8 November 2017. [Google Scholar]
- Kelly, J.; Knottenbelt, W. The UK-DALE dataset, domestic appliance-level electricity demand and whole-house demand from five UK homes. Sci. Data 2015. [Google Scholar] [CrossRef] [PubMed]
- Wang, Z.; Ni, Y.; Zhang, Z.; Wang, G.; Chen, Z.; Deng, F.; Pu, Z.; Yang, L.; Zhang, Y.; Feng, R.; et al. Intelligent Distribution Network Information Processing Based on Power Data Virtual Plane. Appl. Sci. 2020, 10, 736. [Google Scholar] [CrossRef]
- Introduction to NISTIR 7628 Guidelines for Smart Grid Cyber Security. Available online: https://nvlpubs.nist.gov/nistpubs/ir/2010/NIST.IR.7628.pdf (accessed on 6 February 2020).
- Pillitteri, V.Y.; Brewer, T.L. Guidelines for smart grid cyber security. Nat. Inst. Stand. Technol. 2014. [Google Scholar] [CrossRef]
- Zhu, W.; Wang, Z.; Zhang, Z. Renovation of automation system based on industrial internet of things: A Case Study of a Sewage Treatment Plant. Sensors 2020, 20, 2175. [Google Scholar] [CrossRef]
- Asghar, M.R.; Dán, G.; Miorandi, D.; Chlamtac, I. Smart meter data privacy: A Survey. IEEE Commun. Surv. Tutorials 2017, 19, 2820–2835. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, K.; Lin, X.; Shen, X.S. Balancing security and efficiency for smart metering against misbehaving collectors. IEEE Trans. Smart Grid 2019, 10, 1225–1236. [Google Scholar] [CrossRef]
- Xiao, Y.; Zhang, L.; Li, X. EU-27 AMI rollout and inspiration of the next generation IR46 smart meter planning. Electr. Meas. Instrum. 2019, 56, 146–152. [Google Scholar]
- Li, Z.; Tong, W.; Jin, X. Construction of cyber security defense hierarchy and cyber security testing system of smart grid: Thinking and enlightenment for network attack events to national power grid of Ukraine and Israel. Autom. Electr. Power Syst. 2016, 40, 147–151. [Google Scholar]
- Tian, M.; Li, S. Application of the ESAM in the smart meters. Res. Discuss. 2018, 4, 29–31. [Google Scholar]
- Zhou, W.; Li, P.; Wang, Q.; Nabipour, N. Research on data transmission of wireless sensor networks based on symmetric key algorithm. Measurement 2020, 153, 107454. [Google Scholar] [CrossRef]
- Lavanya, R.; Karpagam, M. Enhancing the security of AES through small scale confusion operations for data communication. Microprocess. Microsyst. 2020, 75. [Google Scholar] [CrossRef]
- Pang, L.; Wei, M.; Li, H. Efficient and anonymous certificateless multi-message and multi-receiver signcryption scheme based on ECC. IEEE Access 2019, 7, 24511–24526. [Google Scholar] [CrossRef]
- Wang, F.; Xu, L.; Choo, K.-K.R.; Zhang, Y.; Wang, H.; Li, J. Lightweight certificate-based public/private auditing scheme based on bilinear pairing for cloud storage. IEEE Access 2019, 8, 2258–2271. [Google Scholar] [CrossRef]
- Feng, R.; Wang, Z.; Li, Z. Design and experiment on fertile solution pH value and electrical conductivity measuring instrument. J. Irrig. Drain. Eng. 2020, 38, 643–648. [Google Scholar]





| Working Mode | Difference Range of Encryption and Decryption Computing Time in Different Key Length/ms | Conclusion | ||
|---|---|---|---|---|
| 128 bit | 192 bit | 256 bit | ||
| ECB | −0.01~−0.16 | 0~−0.16 | 0~−0.16 | Decryption a little longer than encryption |
| CBC | −0.03~−0.87 | −0.04~−0.88 | −0.03~−0.87 | Decryption a little longer than encryption |
| CFB1 | 0.26~7.24 | 0.19~6.64 | 0.15~8.43 | Encryption longer than decryption |
| CFB8 | 0.03~0.5 | 0.01~0.5 | 0.01~0.51 | Encryption longer than decryption |
| CFB128 | 0~0.05 | 0.01~0.05 | 0~0.05 | Encryption a little longer than decryption |
| OFB | 0~0.02 | 0~0.01 | 0~0.02 | Encryption and decryption same time |
| CTR | 0~0.01 | 0~0.01 | 0~0.01 | Encryption and decryption same time |
 |  | ||||||
| Working Mode | ECB | CBC | CFB1 | CFB8 | CFB128 | OFB | CTR |
|---|---|---|---|---|---|---|---|
| Conclusion | Computing cost of encryption and decryption increases with the increase of key length | The trend table of the six modes is the same as that of ECB, and computing cost of encryption and decryption increases with the increase of key length | |||||
| Key Length Bit | Encryption Time (times/s) | Decryption Time (times/s) | Signature Time (times/s) | Verify Times (times/s) |
|---|---|---|---|---|
| 1024 | 212.3 | 5.7 | 5.6 | 213 |
| 2048 | 57.9 | 0.87 | 0.87 | 57.7 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Feng, R.; Wang, Z.; Li, Z.; Ma, H.; Chen, R.; Pu, Z.; Chen, Z.; Zeng, X. A Hybrid Cryptography Scheme for NILM Data Security. Electronics 2020, 9, 1128. https://doi.org/10.3390/electronics9071128
Feng R, Wang Z, Li Z, Ma H, Chen R, Pu Z, Chen Z, Zeng X. A Hybrid Cryptography Scheme for NILM Data Security. Electronics. 2020; 9(7):1128. https://doi.org/10.3390/electronics9071128
Chicago/Turabian StyleFeng, Ruijue, Zhidong Wang, Zhifeng Li, Haixia Ma, Ruiyuan Chen, Zhengbin Pu, Ziqiu Chen, and Xianyu Zeng. 2020. "A Hybrid Cryptography Scheme for NILM Data Security" Electronics 9, no. 7: 1128. https://doi.org/10.3390/electronics9071128
APA StyleFeng, R., Wang, Z., Li, Z., Ma, H., Chen, R., Pu, Z., Chen, Z., & Zeng, X. (2020). A Hybrid Cryptography Scheme for NILM Data Security. Electronics, 9(7), 1128. https://doi.org/10.3390/electronics9071128




