Vulnerabilities’ Assessment and Mitigation Strategies for the Small Linux Server, Onion Omega2
Abstract
1. Introduction
2. Background
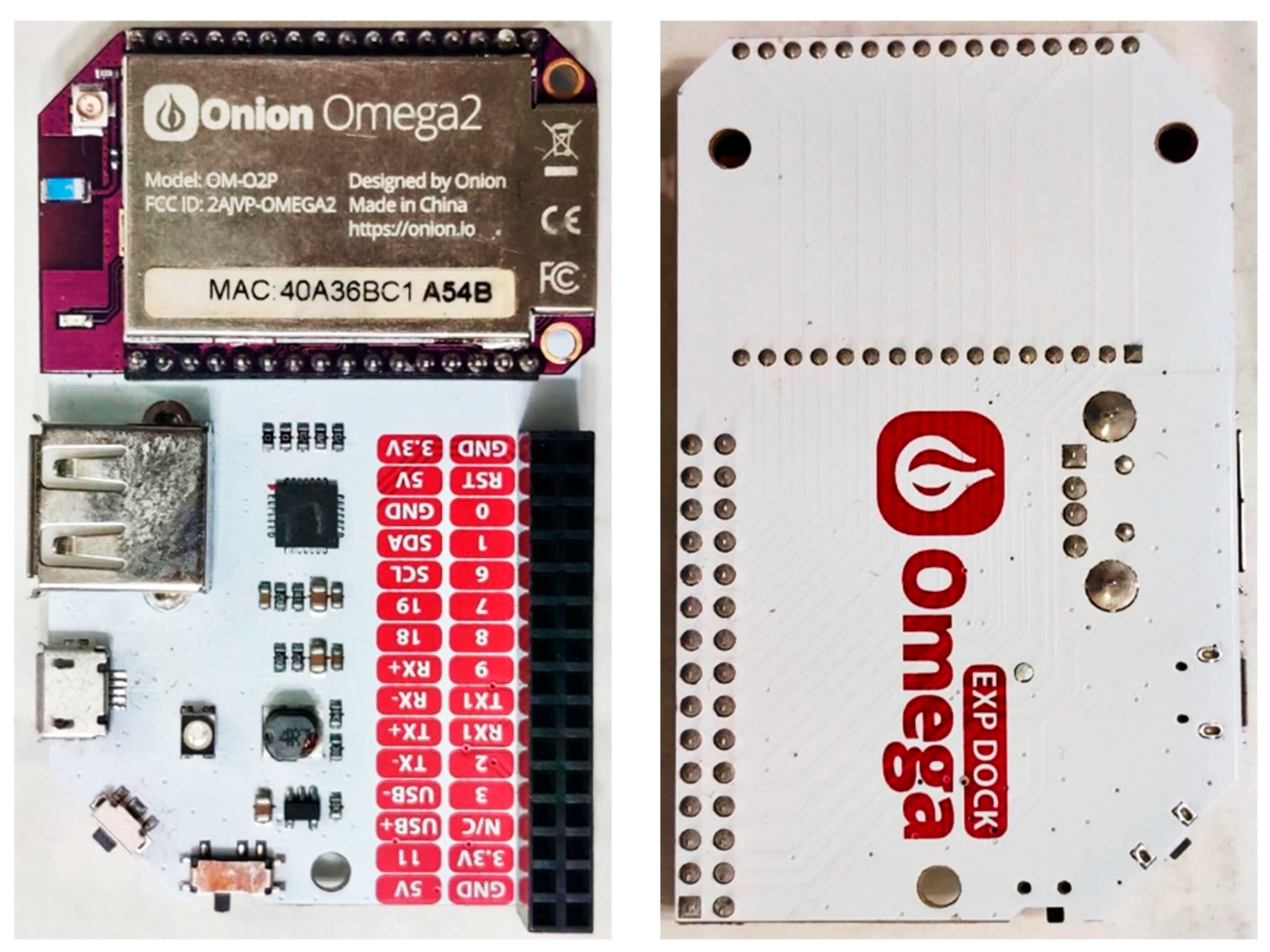
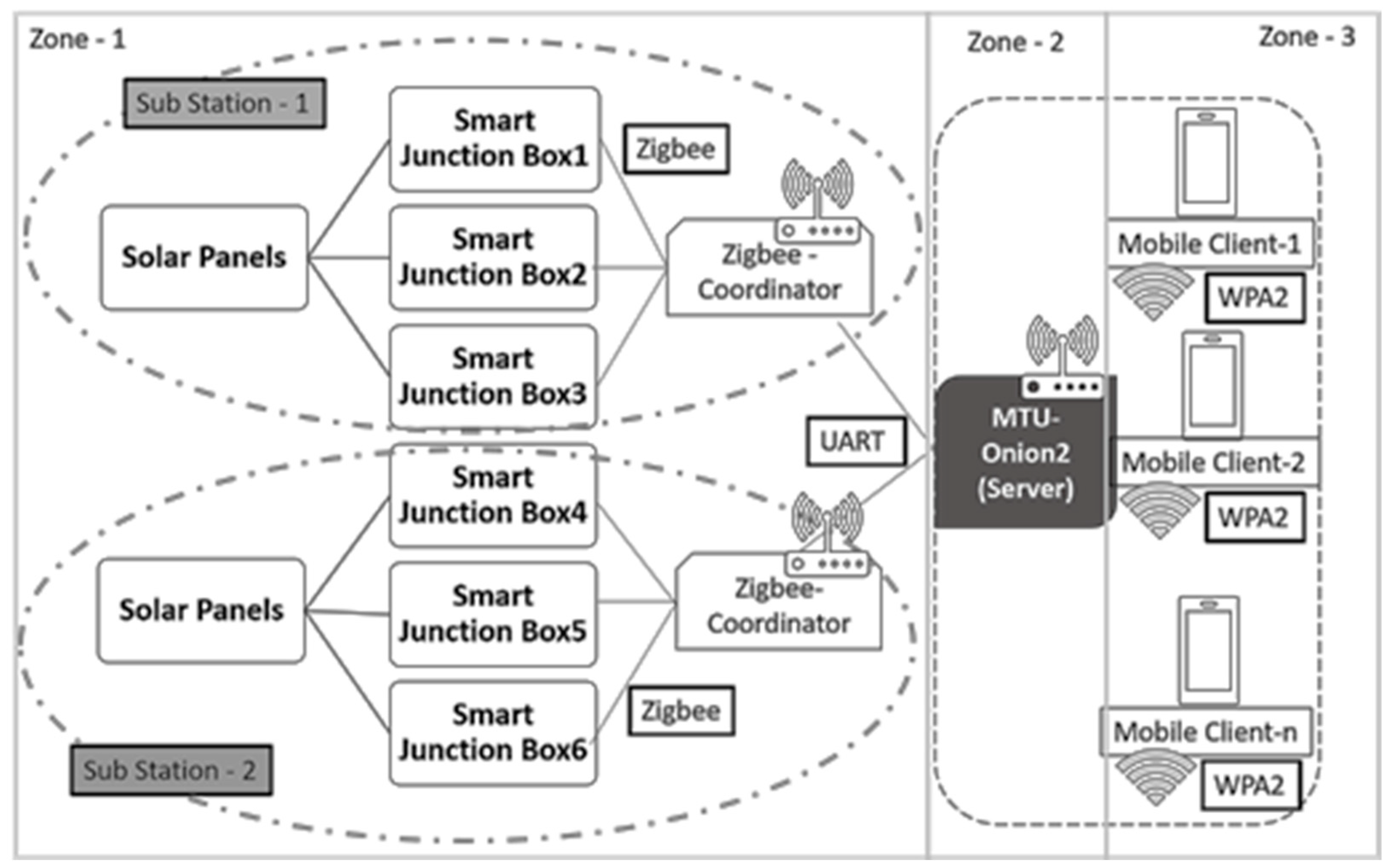
3. Onion Omega2 IoT Device
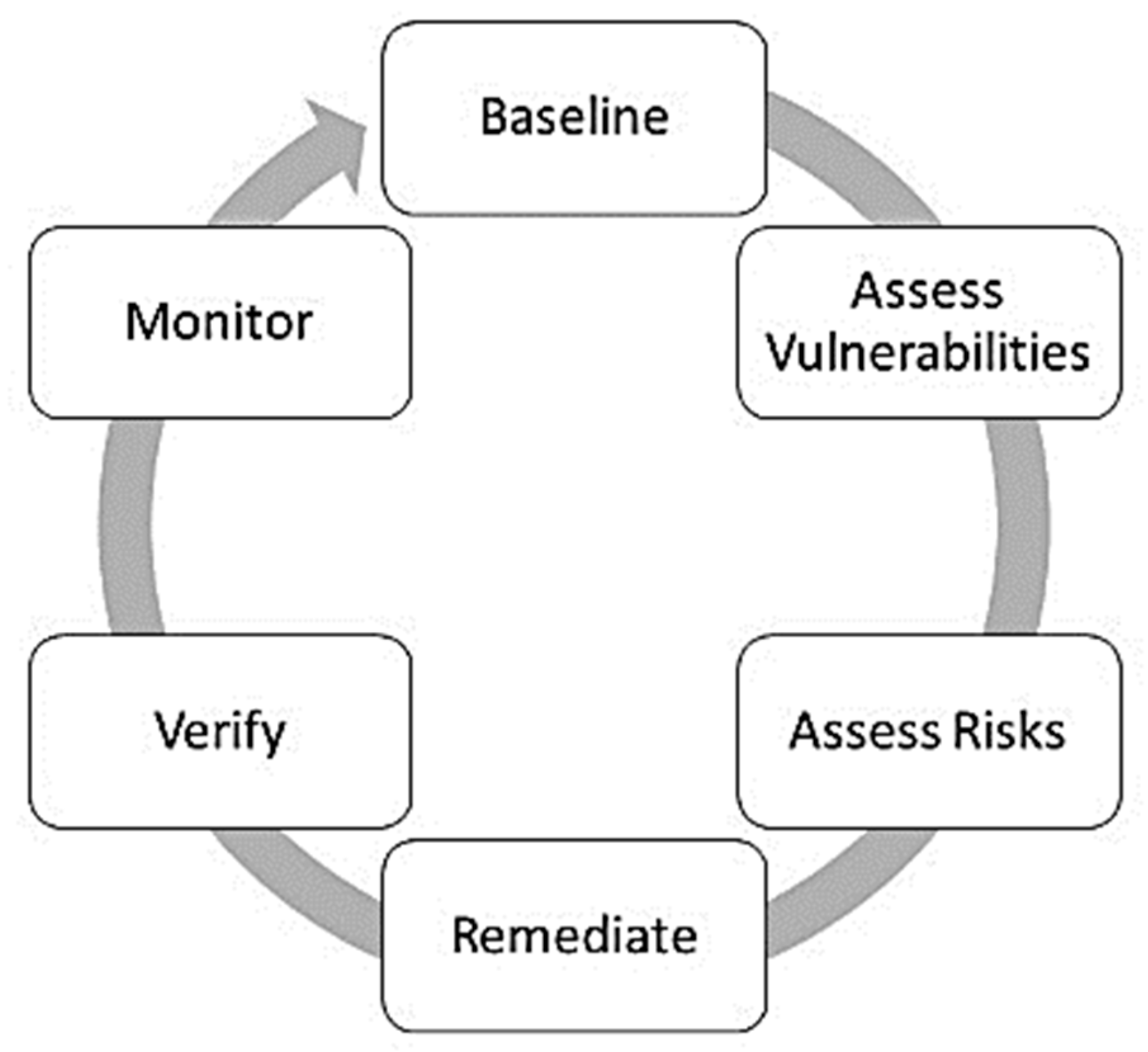
4. Vulnerability Assessments of Onion Omega2
- Vendor level fixes
- Network/Administrator level fixes
4.1. Vendor Level Fixes
4.1.1. Open Ports/Services
4.1.2. Web Server Assessment
4.1.3. DNS Server Assessment
4.2. Network/Administrator Fixes
4.2.1. IP Forwarding Service
4.2.2. SSL Medium Strength Suites
4.2.3. MQTT Broker Protocol
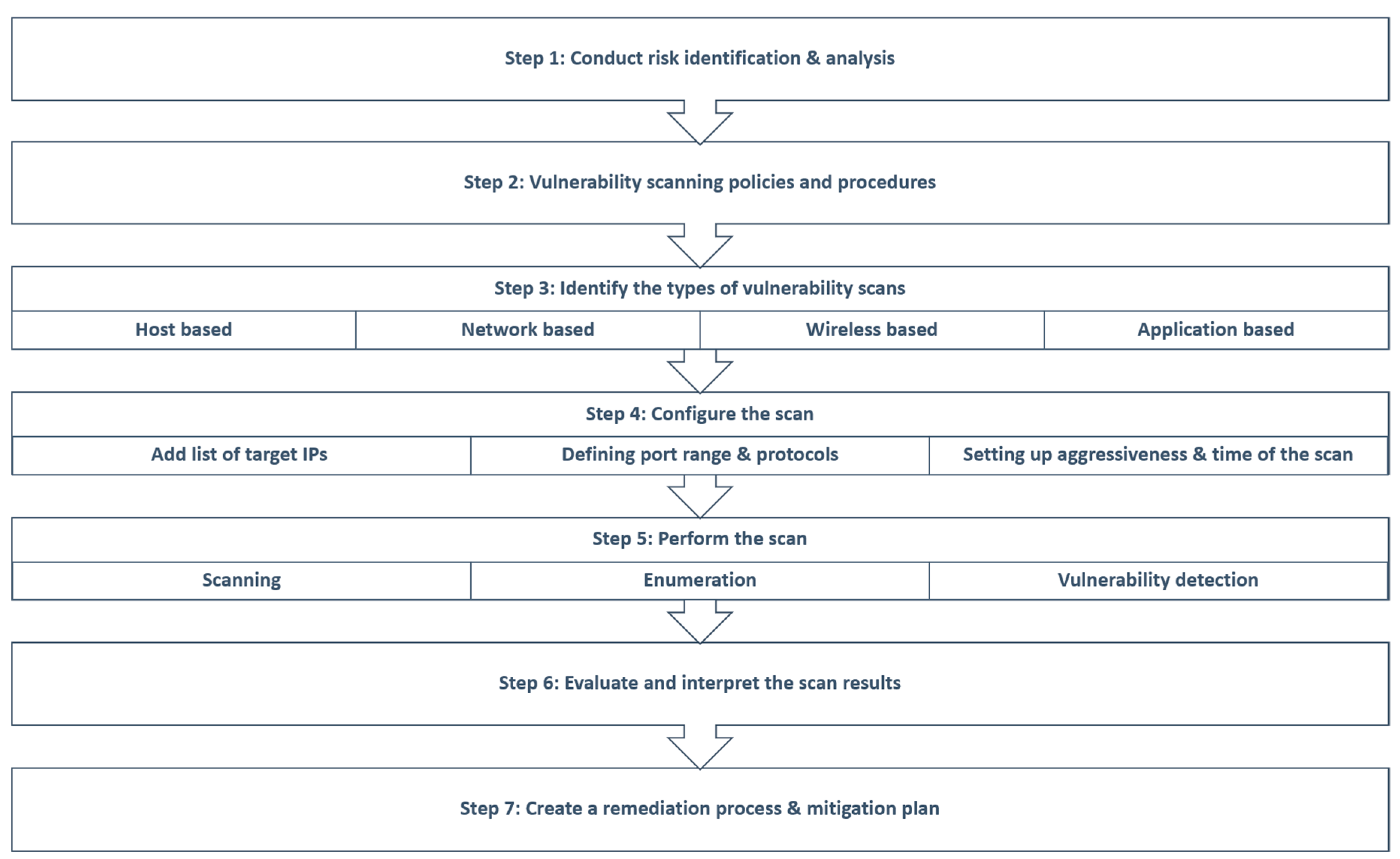
5. Generic Vulnerability Assessment
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Choo, K.-K.R.; Gritzalis, S.; Park, J.H. Cryptographic solutions for industrial Internet-of-Things: Research challenges and opportunities. IEEE Trans. Ind. Inf. 2018, 14, 3567–3569. [Google Scholar] [CrossRef]
- Garcia-Morchon, O.; Kumar, S.; Sethi, M. Internet of Things (IoT) Security: State of the Art and Challenges. 2019. Available online: https://www.rfc-editor.org/rfc/pdfrfc/rfc8576.txt.pdf (accessed on 8 May 2020).
- Ramos, A.; Lazar, M.; Filho, R.H.; Rodrigues, J.J.P.C. Model-Based Quantitative Network Security Metrics: A Survey. IEEE Commun. Surv. Tutor. 2017, 19, 2704–2734. [Google Scholar] [CrossRef]
- Ghaleb, A.; Zhioua, S.; Almulhem, A. On PLC network security. Int. J. Crit. Infrastruct. Prot. 2018, 22, 62–69. [Google Scholar] [CrossRef]
- Cyber-Attack on Indian Nuclear Power Plant Exposes Threat of “Snooping” Malware. Available online: https://www.bitsight.com/blog/cyber-attack-on-indian-nuclear-power-plant-exposes-threat-of-snooping-malware (accessed on 12 November 2019).
- National Cybersecurity and Communications Integration Center/Industrial Control Systems Cyber Emergency Response Team. NCCIC/ICS-CERT FY 2015 Annual Vulnerability Coordination Report; Homeland Security: Washington, DC, USA, 2015. [Google Scholar]
- Common Vulnerabilities Exposures Database CVE – Home. Available online: https://cve.mitre.org/cve/ (accessed on 2 October 2018).
- Cherdantseva, Y.; Burnap, P.; Blyth, A.; Eden, P.; Jones, K.; Soulsby, H.; Stoddart, K. A review of cyber security risk assessment methods for SCADA systems. Comput. Secur. 2016, 56, 1–27. [Google Scholar] [CrossRef]
- Onion – Compute Platform for IoT. Available online: https://onion.io/ (accessed on 8 June 2020).
- Upadhyay, D.; Sampalli, S. SCADA (Supervisory Control and Data Acquisition) Systems: Vulnerability Assessment and Security Recommendations. Comput. Secur. 2020, 89, 101666. [Google Scholar] [CrossRef]
- Nicholson, A.; Webber, S.; Dyer, S.; Patel, T.; Janicke, H. SCADA security in the light of Cyber-Warfare. Comput. Secur. 2012, 31, 418–436. [Google Scholar] [CrossRef]
- Horkan, M. Information Security Reading Room A Black-Box Approach to Embedded Systems; The SANS Institute: Bethesda, MD, USA, 2016. [Google Scholar]
- Onion Omega2 Known Firmware Issues | Onion Omega2 Documentation. Available online: https://docs.onion.io/omega2-docs/known-firmware-issues.html (accessed on 27 May 2020).
- Cagalaban, G.; Kim, T.; Kim, S. Towards Improving SCADA Control Systems Security with Vulnerability Analysis Improving SCADA Control Systems Security with Software Vulnerability. In Proceedings of the International Conference on Parallel and Distributed Computing and Networks, Chongqing, China, 13–14 December 2010. [Google Scholar]
- Coffey, K.; Smith, R.; Maglaras, L.; Janicke, H. Vulnerability Analysis of Network Scanning on SCADA Systems. Secur. Commun. Netw. 2018, 2018. [Google Scholar] [CrossRef]
- Andersson, S.; Josefsson, O. On the assessment of Denial of Service vulnerabilities Affecting Smart Home Systems: Vulnerability Scanning Using OpenVAS. 2019. Available online: https://muep.mau.se/handle/2043/29162 (accessed on 8 May 2020).
- Andrews, M. The state of web security. IEEE Secur. Privacy 2006, 4, 14–15. [Google Scholar] [CrossRef]
- Steven, J. Adopting an enterprise software security framework. IEEE Secur. Privacy 2006, 4, 84–87. [Google Scholar] [CrossRef]
- Samtani, S.; Yu, S.; Zhu, H.; Patton, M.; Matherly, J.; Chen, H. Identifying SCADA systems and their vulnerabilities on the internet of things: A text-mining approach. IEEE Intell. Syst. 2018, 33, 63–73. [Google Scholar] [CrossRef]
- Sun, Y.; Sun, L.; Shi, Z.; Yu, W.; Ying, H. Vulnerability finding and firmware association in power grid. In Proceedings of the 2019 5th International Conference on Mobile and Secure Services, MOBISECSERV 2019, Miami Beach, FL, USA, 2–3 March 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Carranza, A.; Mayorga, D.; DeCusatis, C.; Rahemi, H. Comparison of wireless network penetration testing tools on desktops and raspberry Pi platforms. In Proceedings of the LACCEI international Multi-conference for Engineering, Education and Technology, Boca Raton, FL, USA, 18–20 July 2018; pp. 19–21. [Google Scholar] [CrossRef]
- Binwalk Binwalk | Penetration Testing Tools. Available online: https://tools.kali.org/forensics/binwalk (accessed on 3 November 2019).
- Leszczyna, R. Approaching secure industrial control systems. IET Inf. Secur. 2015, 9, 81–89. [Google Scholar] [CrossRef]
- Maiolo, M.; Pantusa, D. Infrastructure Vulnerability Index of drinking water systems to terrorist attacks. Cogent Eng. 2018, 5, 1456710. [Google Scholar] [CrossRef]
- Department of Energy. Enhancing Control Systems Security in the Energy Sector NSTB National SCADA Test Bed Common Cyber Security Vulnerabilities Observed in Control System Assessments by the INL NSTB Program; Department of Energy: Washington, DC, USA, 2008. [Google Scholar]
- Van Der Maelen Uría, J.F.; Alvarez-Rúa Alvarez, C. Using Spline Functions for Obtaining Accurate Partial Molar Volumes in Binary Mixtures. Comput. Chem. 1998, 22, 225–235. [Google Scholar] [CrossRef]
- Nurse, J.R.C.; Creese, S.; De Roure, D. Security risk assessment in Internet of Things systems. IT Prof. 2017, 19, 20–26. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Yang, L.; Yang, S.-H.; Yao, F. Safety and security of remote monitoring and control of intelligent home environments. In Proceedings of the 2006 IEEE International Conference on Systems, Man and Cybernetics, Taipei, Taiwan, 8–11 October 2006; pp. 1149–1153. [Google Scholar]
- Ali, B.; Awad, A.I. Cyber and physical security vulnerability assessment for IoT-based smart homes. Sensors 2018, 18, 817. [Google Scholar] [CrossRef] [PubMed]
- Cohen, M.; Graf, R.; Kilani, M.; Pashley, C.; Ryan, J.; Shannon, G.; Walters, G.; Wills, T. Cyber Resilience and Response 2018 Public-Private Analytic Exchange Program. 2018. Available online: https://www.dhs.gov/sites/default/files/publications/2018_AEP_Cyber_Resilience_and_Response.pdf (accessed on 8 May 2020).
- Acunetix Clickjacking: X-Frame-Options Header Missing - Vulnerabilities – Acunetix. Available online: https://www.acunetix.com/vulnerabilities/web/clickjacking-x-frame-options-header-missing/ (accessed on 8 December 2019).
- OWASP. OWASP Secure Headers Project. Available online: https://www.owasp.org/index.php/OWASP_Secure_Headers_Project (accessed on 8 December 2019).
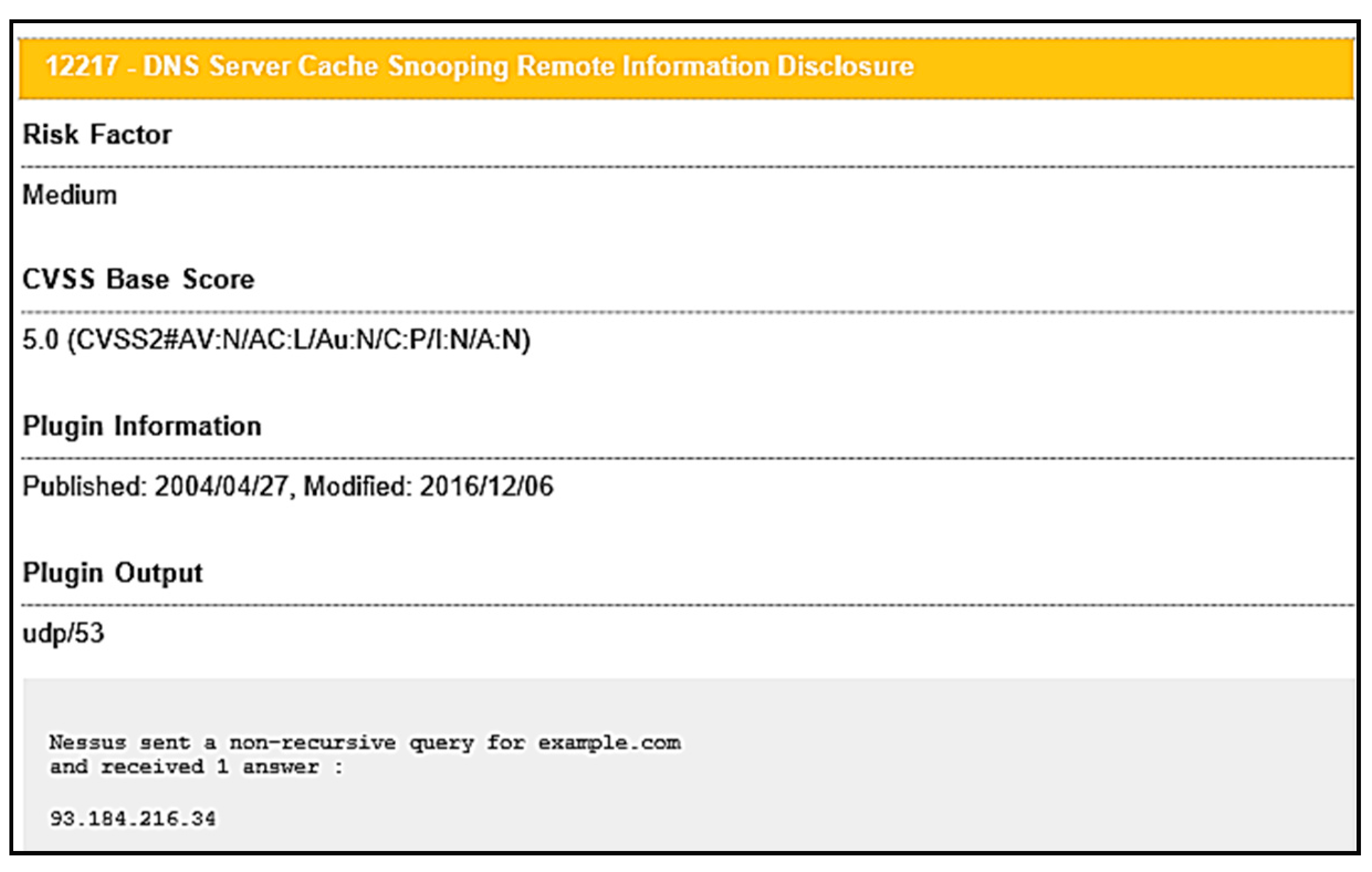
- Tenable Nessus DNS Server Cache Snooping Remote Information Disclosure | Tenable®. Available online: https://www.tenable.com/plugins/nessus/12217 (accessed on 11 November 2019).
- Grangeia, L. DNS Cache Snooping Snooping the Cache for Fun and Profit. Available online: http://www.rootsecure.net/content/downloads/pdf/dns_cache_snooping.pdf (accessed on 11 November 2019).
- Vanhoef, M.; Piessens, F. Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2. In Proceedings of the ACM Procedding; Publisher:Association for Computing Machinery, Dallas, TX, USA, 17–20 October 2017. [Google Scholar]
- Onion Omega2, S. GitHub - OnionIoT/Source: Onion’s fork of OpenWRT’s Source Build System. The Firmware for the Omega2, Omega2+, and Omega2 Pro is Based on the Openwrt-18.06 Branch. Available online: https://github.com/OnionIoT/source (accessed on 1 November 2019).
- Tenable Nessus IP Forwarding Enabled | Tenable®. Available online: https://www.tenable.com/plugins/nessus/50686 (accessed on 11 November 2019).
- Tenable Nessus. Nessus Report; Tenable: Columbia, MD, USA, 2009. [Google Scholar]
- Dinculean, D.; Cheng, X. Vulnerabilities and Limitations of MQTT Protocol Used between IoT Devices. Appl. Sci. 2019, 9, 848. [Google Scholar] [CrossRef]
- Crawley, S. MQTT Broker Does Not Require Authentication – QRIScloud. Available online: https://support.qriscloud.org.au/hc/en-us/articles/360000375956-MQTT-Broker-does-not-require-authentication (accessed on 11 November 2019).
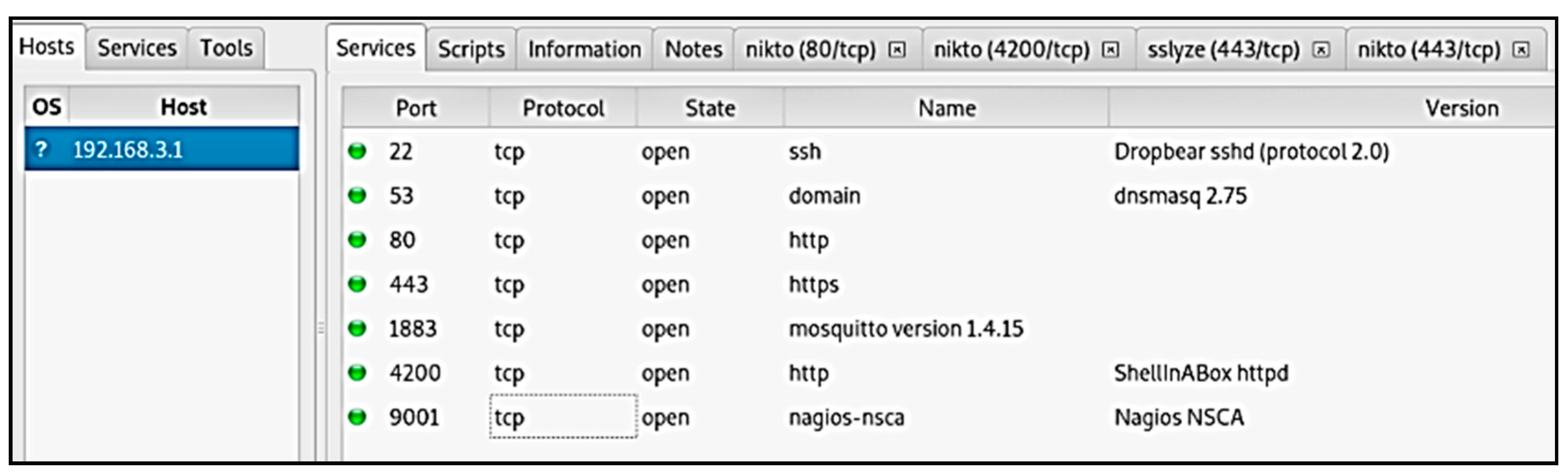

| Vulnerabilities | Description | Targeted Ports/Services | Scanning Tools Used | Mitigation |
|---|---|---|---|---|
| X-XSS-Protection header is not defined. | Cross-site scripting attack on index page is possible. This could allow the user agent to render the content of the site in a different fashion to the MIME type. | 4200, 80 Http | Nmap, Nikto, Sparta |
|
| Buffer Overflow attack possible. | Long string from remote host generates buffer overflow in memory. | 4200, Http | Nmap, OpenVAS | Vendor should upgrade the web server to the latest version by adopting proper validation techniques for each segment of the program code. |
| DNS Server Cache Snooping Remote Information Disclosure | This may allow a remote attacker to determine domains that have recently been resolved via this name server. | 53-DNS (UDP/TCP) dnsmasq 2.75 | Nmap, Nessus | Vendor should update the DNS server with proper patches to fix the problem. |
| SSH Weak MAC Algorithms Enabled | SSH server is configured to allow either MD5 or 96-bit MAC algorithms, both of which are considered weak. | 22-SSH | Nessus, OpenVAS | Vendor should patch it, or administrator should consult product documentation to disable MD5 and 96-bit MAC algorithms. |
| Key-Reinstallation Attack (KRACK) Vulnerability [36] | This breaks security of WPA2 protocol and able to access the critical information communicating between client and Access point. | WPA2 | Krackattacks-scripts [37] | Vendor should fix the issue by properly configured wpa-supplicant in Linux kernel. |
| HTTPS Secure Communication | Assessment Outcomes |
|---|---|
| Configuration Protocol | OK—TLS V1.2 (Strong Communication protocol) |
| Forward Secrecy | OK—Supported |
| Client-initiated renegotiations | OK—Supported |
| OpenSSL CCS Injection | OK—Not vulnerable to OpenSSL CCS injection |
| Deflate Compression | OK—Compression disabled |
| ROBOT Attack | OK—Not vulnerable |
| OpenSSL Heartbleed Attack | OK—Not vulnerable to Heartbleed |
| Downgrade Attacks (TLS_FALLBACK_SCSV) | OK—Supported |
| Default Configuration: ECDHE-RSA-DES-CBC3-SHA2 Medium Strength Ciphers: Uses 64 bits block cipher 3DES | Vulnerable to Sweet32 attacks Preferred Configuration: ECDHE-RSA-AES128-CBC3-SHA2 ECDHE-RSA-AES128-GCM-SHA3 |
| Default Configuration | Preferred Configuration |
|---|---|
| ECDHE-RSA-DES-CBC3-SHA2 | TLS_RSA_WITH_AES_128_GCM_SHA384 |
| ECDHE: Elliptic Curve Diffie-Hellman Key Exchange | (GCM uses parallel approach) |
| RSA: for Authentication | TLS_RSA_WITH_AES_256_CBC_SHA256 |
| 3DES-CBC: Symmetric Encryption | (CBC 256 bits consist of 14 rounds) |
| SHA2: Message Authentication Code | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 |
| vulnerable to SWEET32 attack (CVE-2016-2183) | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA256 |
| Vulnerabilities | Description | Scanning Tools | Mitigation |
|---|---|---|---|
| IP forwarding enabled | An attacker can exploit this path to route packets through the specific host to bypass targeted firewalls, routers or NAC filters. | OpenVAS, Nessus |
|
| SSL medium strength cipher suites supported | The default configuration supports encryption that uses 3DES-CBC for symmetric key cryptography which is vulnerable to SWEET32. | Nessus, OpenVAS, Nikto | Reconfigure the affected application to avoid use of medium strength ciphers [39]. |
| MQTT Broker does not required authentication | This may allow a remote attacker to gain access of the network without any authentication. Intruder can extract the information of the control/IoT networks. | OpenVAS | Enable authentication mode in Onion Omega2: By configuring Mosquitto Broker setting password in etc/mosquito/Passwd; |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Upadhyay, D.; Sampalli, S.; Plourde, B. Vulnerabilities’ Assessment and Mitigation Strategies for the Small Linux Server, Onion Omega2. Electronics 2020, 9, 967. https://doi.org/10.3390/electronics9060967
Upadhyay D, Sampalli S, Plourde B. Vulnerabilities’ Assessment and Mitigation Strategies for the Small Linux Server, Onion Omega2. Electronics. 2020; 9(6):967. https://doi.org/10.3390/electronics9060967
Chicago/Turabian StyleUpadhyay, Darshana, Srinivas Sampalli, and Bernard Plourde. 2020. "Vulnerabilities’ Assessment and Mitigation Strategies for the Small Linux Server, Onion Omega2" Electronics 9, no. 6: 967. https://doi.org/10.3390/electronics9060967
APA StyleUpadhyay, D., Sampalli, S., & Plourde, B. (2020). Vulnerabilities’ Assessment and Mitigation Strategies for the Small Linux Server, Onion Omega2. Electronics, 9(6), 967. https://doi.org/10.3390/electronics9060967







