1. Introduction
In a dense wireless communication network (WCN), both the energy and security reliability need to be assured. This represents a challenge in the case of a network with a huge number of nodes [
1]. Thus, in order to keep up with the energy demands of the increasing number of network nodes, new radio frequency energy harvesting (EH) techniques like simultaneous wireless information and power transmission (SWIPT) are investigated for 5G networks [
1,
2,
3]. Apart from harvesting energy by using SWIPT techniques, many other signal processing applications like channel estimation with SWIPT [
4] and physical layer security (PLS) measures with the help of SWIPT technique were investigated in [
5]. One of the most important techniques in improving PLS in a wiretap channel is using artificial noise (AN) in the communication channel to degrade the signal-to-noise plus interference ratio (SINR) of eavesdroppers; thereby improving the security of legitimate users [
6]. The high energy signal that is used for harvesting energy in SWIPT can also be adopted for creating AN to improve PLS, as in [
7]. The secrecy rate of legitimate users in a wiretap channel can be improved with the SINR degradation of eavesdroppers as in [
8,
9]. Furthermore, the secrecy rate for the multiple-input and multiple-output (MIMO) system model was established in [
10]. To avoid the impact of AN on the legitimate receiver, AN is introduced in the null space of the legitimate receiver’s channel matrix. Thereby, AN degrades the SINR of eavesdroppers without compromising the quality of the legitimate users’ signal [
11]. However, the successful negation of AN is dependent on the channel state information (CSI) of the receiver at the legitimate transmitter and can be effectively used against very robust eavesdroppers as in [
12,
13]. This is considered as a challenge in the imperfect CSI condition [
14,
15]. Another challenge in using AN against eavesdroppers lies in the fact that a jamming attack depends on the channel correlation between the eavesdroppers and legitimate receiver; if the channel correlation is very high, then AN can be partially canceled out by the eavesdropper [
16,
17].
In this article, we use energy signals as a source of AN for secure communication, but also to harvest energy at the receiver. We consider the conventional MIMO system model with separate antennas for data and energy signal transmission and reception. AN is created by the transmitter by using channel precoding based on the CSI of the receiver. In this paper, we analyze the impact on channel precoding based on imperfect CSI. Furthermore, we also consider high channel correlation between eavesdroppers and the legitimate receiver as one of the challenges in the analysis. Our main contribution in this paper involves improving the error rate and secrecy rate performance of the legitimate receiver using iterative block decision feedback equalization (IB-DFE). IB-DFE is an efficient low complex receiver and performs better than non-iterative methods [
18]. IB-DFE is effectively used with the single carrier frequency-division multiple access (SC-FDMA) transmission technique, and its performance was studied in detail [
19,
20,
21]. IB-DFE can also be used to improve channel estimation at the transmitter side against imperfect CSI by using the robust superimposed pilot signal method for accurate channel estimation, as in [
4,
22]. For a fair comparison between the legitimate user and eavesdroppers, we also analyze the impact of imperfect CSI on the legitimate user’s performance.
Throughout this article, matrices or vectors are denoted by bold letters, and scalar variables are denoted by italic letters. The variables associated with the frequency domain and time domain are denoted by capital letters and small letters, respectively. , , , , and denote the conjugate, transpose, Hermitian, trace, and expectation operation, respectively.
2. System Model
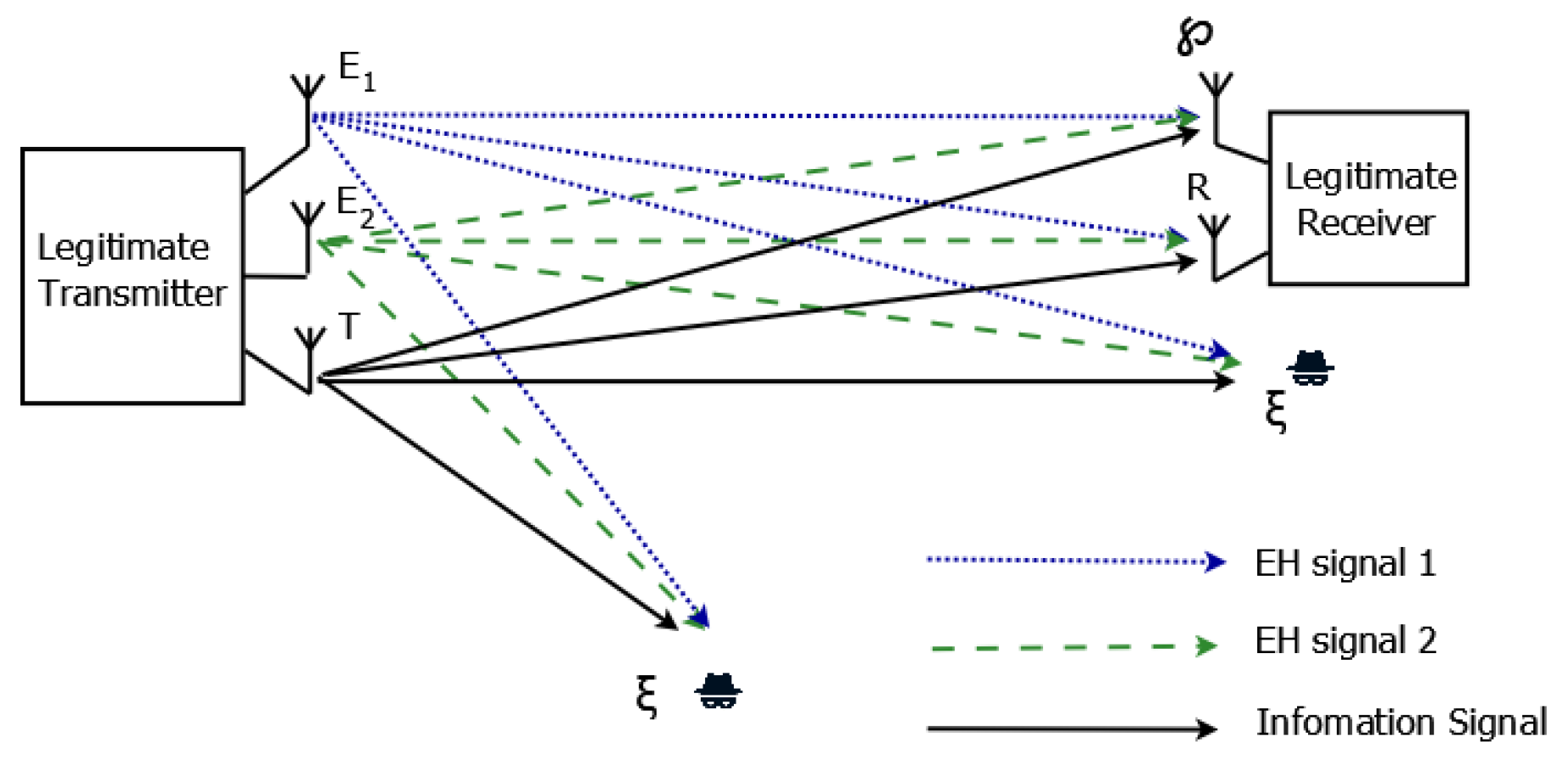
The MIMO system model is shown in
Figure 1. It is composed of three transmitting antennas and two receiving antennas, with a dedicated transmitting antenna and a receiving antenna for information transmission, denoted as
and
R, respectively. The other two transmitting antennas,
and
, are used for energy transmission, and the rectenna
℘ is used to harvest energy from the physical layer network coded (PLNC) signal. The eavesdropper is denoted as
. It is assumed that
,
, and
are not spatially correlated. In
Figure 1, based on the location of
, if
is very close to
R,
is considered to have high channel correlation with
R [
16]. The system adopts the quadrature amplitude modulation (QAM) signal over the Rayleigh frequency selective fading channel by using SC-FDMA for simultaneously transferring information from
and the high energy signal from
and
to both
R and
℘. The frequency domain signals transmitted from
,
, and
are denoted as
,
, and
, respectively, where
k represents the index of the symbol with
and
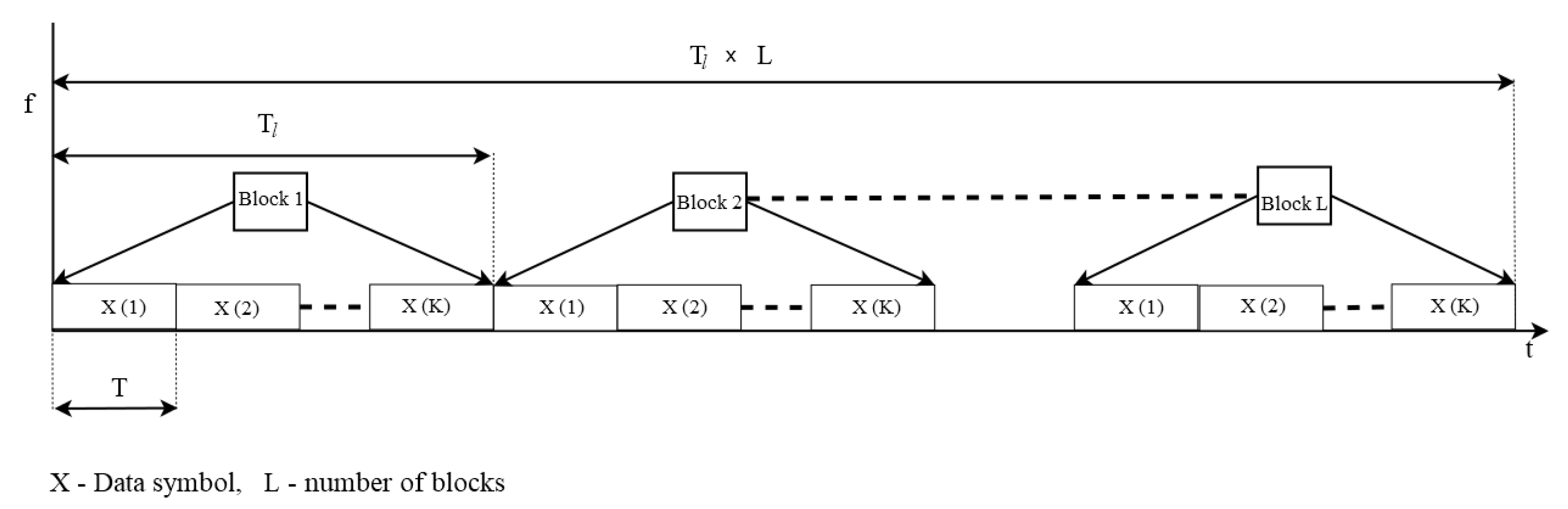
K is the total number of symbols in the respective signal stream. The frame structure of
,
, and
is illustrated in
Figure 2, where the time duration per symbol, block duration, and total time for all the blocks are denoted as
, and
, respectively. A frame consists of
L signal blocks where each signal block contains
N symbols. The signal blocks are denoted as
l, where
. We assume that
,
, and
are transmitted with perfect time synchronization and in equal block size. The following system of equations is considered for a single block, and therefore, we set
.
,
, and
are the unamplified versions of
,
, and
, respectively, and the power amplification levels of energy symbols and information symbols are at different levels.
,
, and
denote the transmit powers of
,
, and
, respectively. For the sake of simplicity, without loss of generality, we assume that
. The relationship between the power levels of energy and information symbols is given as:
where
is the ratio between the transmit power of the energy and information signal.
Throughout this paper, the channel coefficient for the channel link between two nodes, i.e., for example, nodes and R, is denoted as , where k represents the index of channel coefficient with respect to the transmitted symbol in the signal stream. Then, is characterized as , and its channel gain is given as , where is the variance of . Since all the channel links between the nodes are Rayleigh frequency selective fading channels, they follow similar notation and channel characterization as . Similarly, the channel coefficients corresponding to the channel link between and R, and R, and ℘, and ℘, and ℘, and , and , and and are denoted as , , , , , , , and , respectively. The received signals at R, ℘, and experience additive white Gaussian noise (AWGN) modeled as a zero mean complex Gaussian random variable, and their respective AWGNs are given as , , and , respectively.
The system model exploits the CSI of
and
, to cancel the interference of the energy signals to the information signal at
R.
and
will be precoded to equalize
and
, respectively. Unlike
R, the eavesdropper
receives a highly distorted signal, which makes the decoding process difficult. In general,
can decode the information based on the estimated value of
,
,
, and
. Furthermore, to reduce the accuracy of these estimated values at
, the EH signal should act as AN. Similar to
,
℘ will receive the combination of all the transmitted signals as a PLNC signal. Furthermore,
℘ can effectively take advantage of the PLNC signal for harvesting energy, and the received PLNC signal at
℘ is given as:
The performance of this secure self jamming SWIPT technique is analyzed based on the secrecy rate and the bit error rate (BER). Here, three different scenarios are considered, and in all the scenarios, R and are considered to have a CSI of and , respectively. Here, both R and do not have a CSI of and . The assumptions behind the three scenarios are explained as follows:
- A
Scenario A: has the CSI of and . is assumed to be far away from R, and does not have channel correlation. In this scenario, is denoted as , and R is denoted as .
- B
Scenario B: does not have the CSI of and , and estimates and . is assumed to be very close to R, and their channel correlation is very high. In this scenario, is denoted as , and R is denoted as .
- C
Scenario C: This scenario is similar to A where has the CSI of and , but here, is assumed to be very close to R, and their channel correlation is very high. In this scenario, is denoted as . Based on the perfect CSI condition, R is the same in Scenario A and Scenario C.
Then, the received signal at
is given as:
where
denotes the linear subspace of a vector and
. Here,
is the additive inverse of
, and this allows
to nullify the interference of
and
. To achieve
, both
and
should be precoded based on the CSI of the EH signals; thereby, the inference of EH signals to
can be reduced to a negligible level as in (
3). The precoded
and
are given in
Appendix A.1. Therefore, due to precoding, the SINR of
at
does not experience any interference from EH signals, which is given as:
where
. Thus, under the perfect channel condition, the EH signal does not affect the performance of the legitimate receiver
R.
Irrespective of its location,
receives the signal with low SINR due to the EH signal interference. The received signal at
is given as:
where
is the PLNC signal,
is the useful information component, and the EH signal components (
and
) are considered as interference to
. Hence, the SINR of
at
is given as:
Note that the performance of the legitimate user is dependent on the perfect channel condition, which allows
and
to perform signal precoding using CSI. With the imperfect channel condition, the performance of
R is dependent on a robust channel estimation technique as in [
2,
4]. The channel estimates of
and
are obtained by using training symbols from
R to
and
, respectively. The channel estimates of
and
, respectively, are given as
and
. Here,
and
are the channel estimation errors of
and
, respectively. Then, the new precoded EH signals denoted as
and
are expressed in
Appendix A.2.
and
are the precoding errors due to channel estimation error at
and
, respectively.
Similarly, the received signal at
based on the impact of
and
is given as:
where
,
, and
and
are the additional noise components of
due to precoding error. Then,
, where
. The SINR of
for the condition
is given as:
Note that, since
R does not need to equalize
and
, their respective channel estimation errors
and
are neglected in Equation (
8).
The performance of
is better than
due to high channel correlations between
and
and also between
and
. Let us denote the channel correlation between
and
as
. Furthermore, let us denote the channel correlation between between
and
as
.
and
are expressed in
Appendix B. The error due to
and
is denoted as
and
, respectively. The channel precodings at
and
from the perspective of
, respectively, are given as:
From the perspective of , and are the impacts on and , respectively, which degrade the precoded EH signals and increase the precoding errors.
The received signal at
is given as:
where
,
, and
and
are the additional noise components to
. Then,
, where
. The SINR of
for the condition
is given as:
The best scenario for
is
, where, the precoding errors due to the channel estimation errors can be avoided at
. However, there will be a precoding error due to
and
. Hence, the precoded EH signals can be written as:
Then, the received signal at
is given as:
where
and
. Then,
, where
. The SINR of
for the condition
is given as:
For all the scenarios of
and
, the channel precoding error is denoted as
, and its variance is denoted as
. In this system model, both the channel estimate errors and the channel correlation errors are considered to be the sole contributors of
, and
proportionally increases with the increase in
. To form the generalized SINR equation,
and
are assumed as one; then, the SINR of the received signal at
R and
can be written as:
At a very high SINR of the information signal,
can be neglected. Then, Equation (
15) can be written as:
Therefore, even at a very high SINR condition,
can be used to degrade the performance of
. The secrecy of
can be improved at
and
by increasing
under the condition that the
value in
and
is lesser than the
value in
,
, and
. Another observation from Equation (
15) indicates that, if
, then
will always be in the negative SINR region.
2.1. Secrecy Rate Analysis
The secrecy rate analysis of this system model is based on the Gaussian wiretap channel secrecy capacity, which deduces the difference between Shannon’s capacity of
R and
. The maximum achievable secrecy rate is the secrecy capacity of
R [
8,
9]. The secrecy capacity of
with respect to
and the secrecy capacity of
with respect to
, respectively, are given (The notation for the secrecy rate of
with respect to
is given as
, where
denotes
and
A denotes
. A similar rule is followed for the other three secrecy rate notions.) as:
where
is the bandwidth and
is the peak frequency deviation. The secrecy capacity of
with respect to
and the secrecy capacity of
with respect to
, respectively, are given as:
Here, the interference of the EH signals is used as the external noise to improve the maximum achievable secrecy rate of R, and by increasing , the secrecy capacity can be improved in all scenarios. Even though can reduce the capacity of due to the amplification of channel estimation errors, since also has channel correlation error in addition to the channel estimate errors, will improve R’s secrecy capacity.
2.2. Iterative Block Decision Feedback Equalization Receiver
In this system model, it is assumed that both
R and
employ IB-DFE to improve the accuracy of the information estimate as proposed in [
18]. The IB-DFE based estimate for
at
R is given as:
where
,
j is the number of iterations followed in the IB-DFE receiver,
is the previous iteration value of
, and
is the iteration of the feedforward coefficient, given as:
where
is written as:
and the correlation factor
, where
is time domain equivalent of
and
is the extrinsic information of
. Furthermore,
DFT
, and if the
time domain is inside the cycle prefix, then
is either one or zero. The feedback co-efficient
is written as:
In fact, the accuracy of
increases with each iteration up to its saturation point. Similarly, the accuracy of the information estimate can be improved at
R and
for all the scenarios except
. For
,
is completely distorted by EH signals.
The performance of the IB-DFE receiver can be improved at
with improved feedforward input in the iteration. The feedforward estimate,
, is derived in Equation (
21), and this estimate can be improved by including the impact of
in the SINR of the information signal. Therefore, by using Equation (
15) in (
21), we get:
Here, unlike the eavesdropper, can take advantage of the available knowledge from the legitimate transmitter and improve the performance of ; therefore, with the improved feedback estimate can perform better than .
3. Numerical Results
In this section, the BER performance of the legitimate user and eavesdropper in the system model is analyzed by using Monte Carlo simulations. The signal used the 2.4 GHz frequency band, , and it was considered that all the communication nodes including the eavesdroppers were operating in the non-line-of-sight channel condition. The secrecy rate was another performance metric of the legitimate user in the presence of the eavesdropper at various conditions and was analyzed through simulations. In the following simulations, the system adopted the 4-QAM signal with and , and the IB-DFE receiver was used in R and to improve their error rate performance. The channel estimate errors of the and links, i.e., and , respectively were assumed to be equal, i.e., , and was either or . We assumed that, under an exceptionally favorable circumstance, and ; this allowed and to perform better than . In the following figures, the BER performance results by default illustrate the fourth iteration of the IB-DFE decoder unless it is specified as zero-forcing (ZF) decoding.
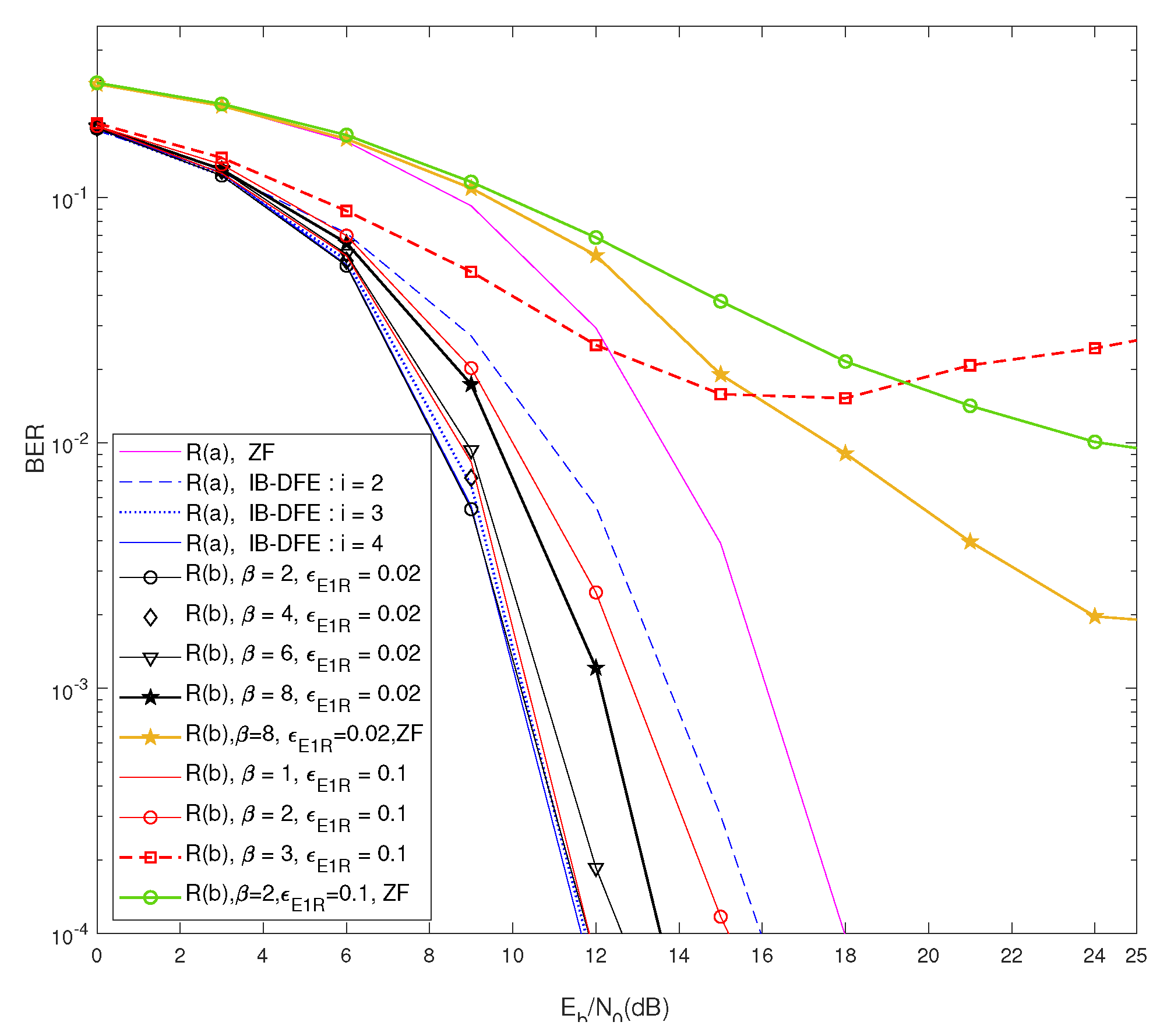
Figure 3 demonstrates the BER performance of
and
. We see that the BER performance of
did not vary with the change in
, due to the successful channel precoding, which was based on the complete CSI of the EH signals, i.e., jamming signals. Furthermore, the results of
demonstrated that the performance of IB-DFE receiver and BER improved up to the fourth iteration. In the first iteration, without any feedforward and feedback values, the resultant BER of the first iteration was equal to the ZF decoding. For
, the channel precoding error occurred due to
, where
and
, and the results demonstrated that due to the precoding error at the transmitter, the BER performance of
was poorer as compared to
. When
, up to
, the performance of
was equivalent to that of
, whereas for
, the performance of
degraded with the increase in
. The precoding error increased proportionally with the increase in
, and
acted as a multiplication factor in increasing the precoding error.
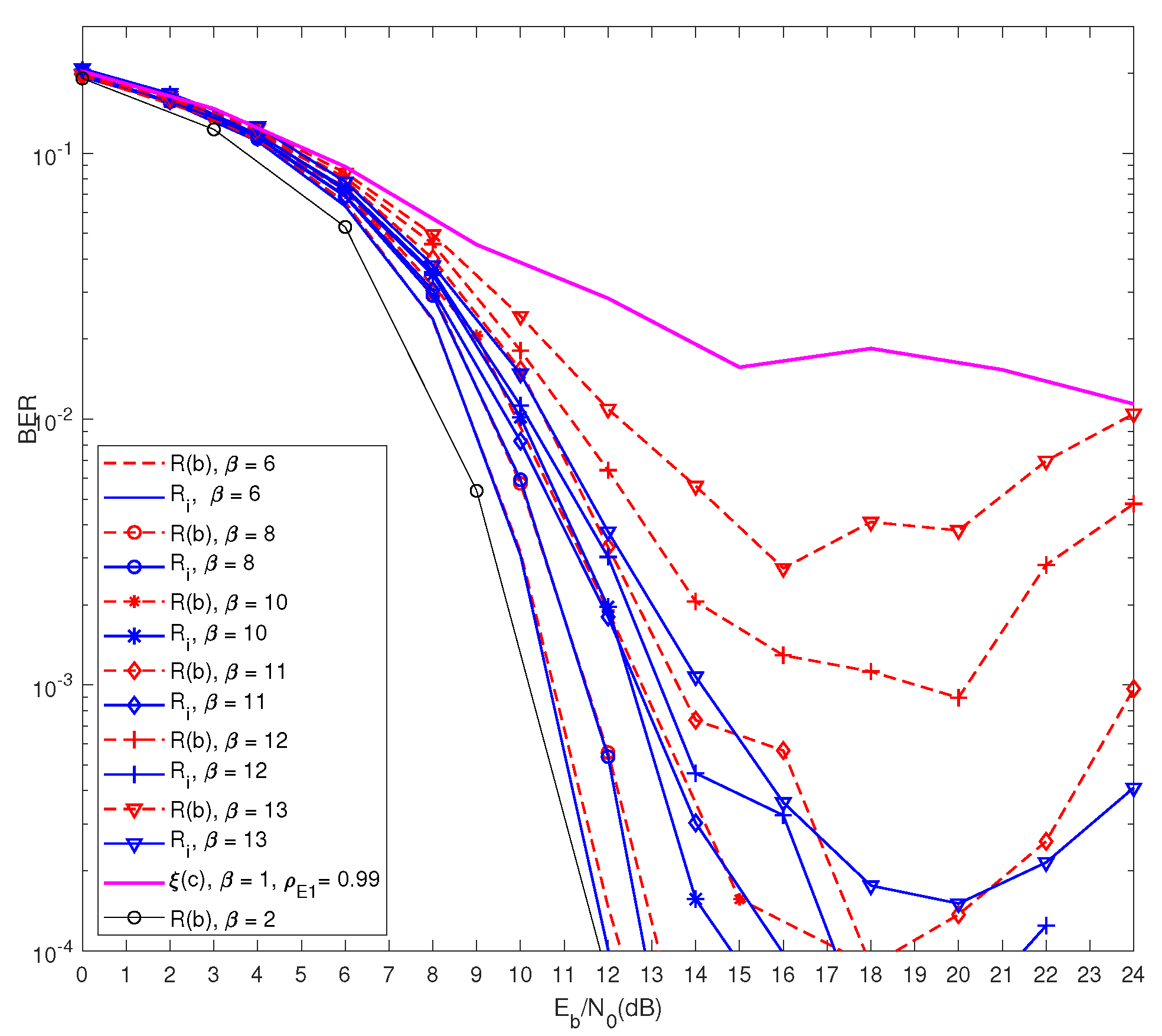
Figure 4 demonstrates the BER performance of
in all the scenarios with the comparison to BER of
R, and
received an incompatible signal for decoding the information. Unlike
, with
and
,
and
could partially decode the signal, and their performance degraded with the decrease in
as the precoding errors increased in turn. Due to high channel correlation between
and
and similarly between
and
, the jamming EH signals were partially canceled out in
and
, allowing them to perform better than
. With
,
performed slightly more poorly as compared to
. Even though
and
could decode information in the high channel correlation condition, the BER results of
R demonstrated that, by increasing
, the jamming signals could degrade the performance of
, while
R suffered a negligible loss.
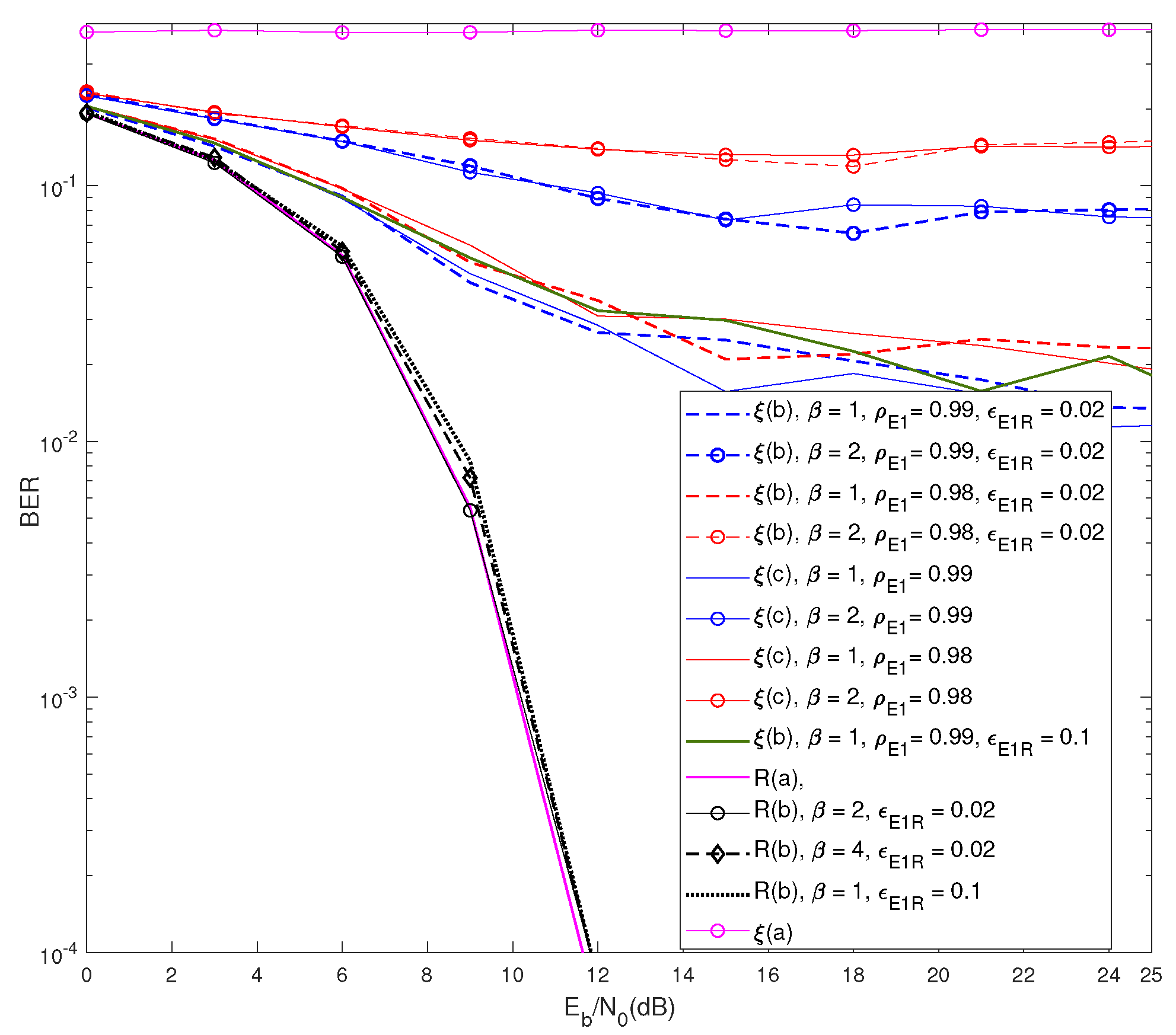
Figure 5 demonstrates the impact of the inclusion of
in the IB-DFE receiver, and the results validated the advantage of using (
23) over (
21) in the iterative loop.
had significant SINR gain over
with the increase in
. At
,
had
dBm SINR gain over
, and when
,
had more than 6 dBm SINR gain over
. The results also illustrated the BER difference between the best performance of
, i.e.,
with
and
versus the performance of
with
.
In
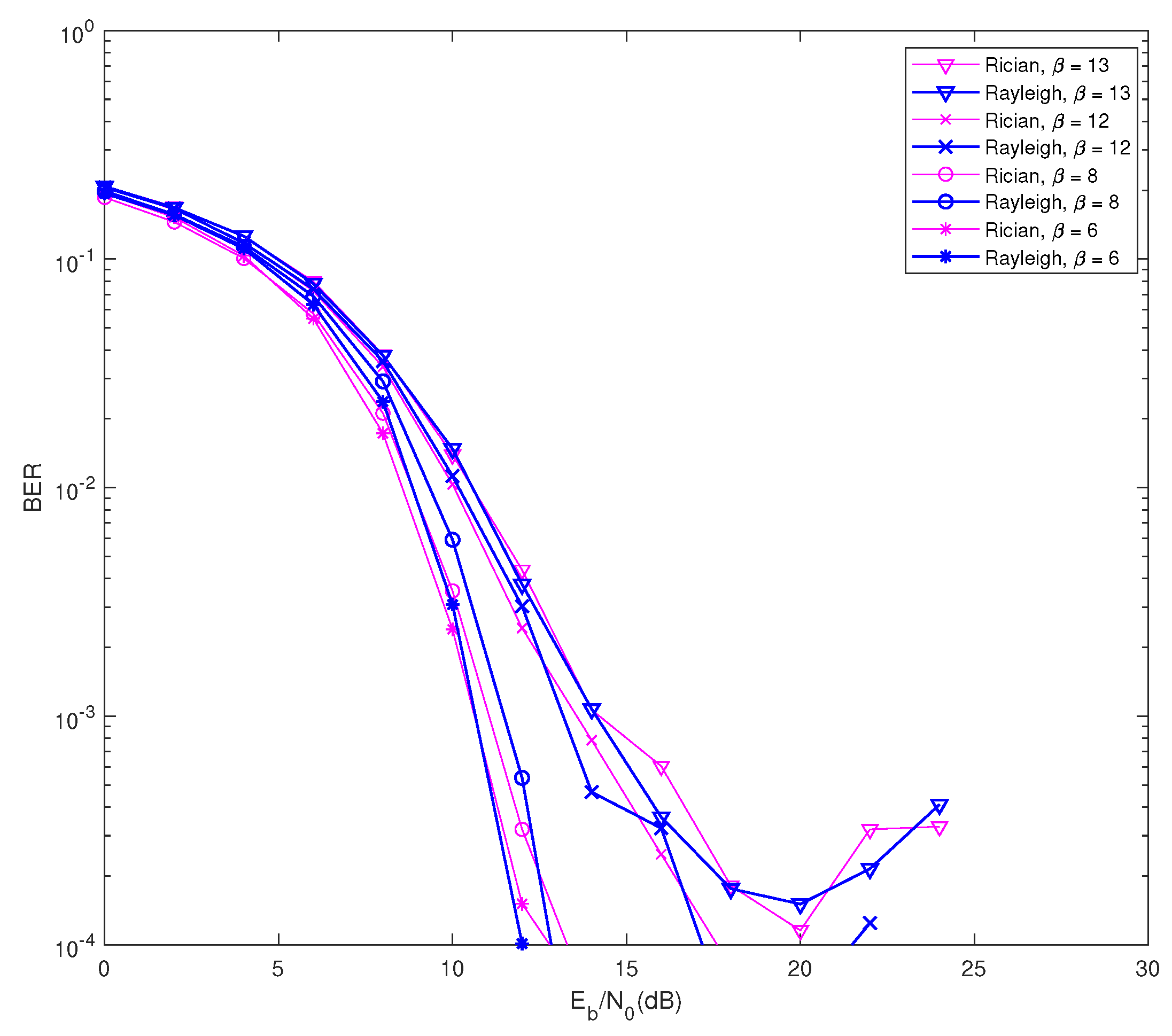
Figure 6, we compare the BER performance of
in Rician fading and Rayleigh frequency flat fading channel conditions. For the simulation of Rician fading, we set
for 256 symbols; the multipath gain range was
; the Doppler shift was 50; and the
kfactor was 10. The results of
Figure 6 demonstrate that the BER performance of
under both fading conditions had similar effects on the signal performance. The fading effects were relatively low due to the application of SC-FDMA, and the BER performance improved with the IB-DFE receiver.
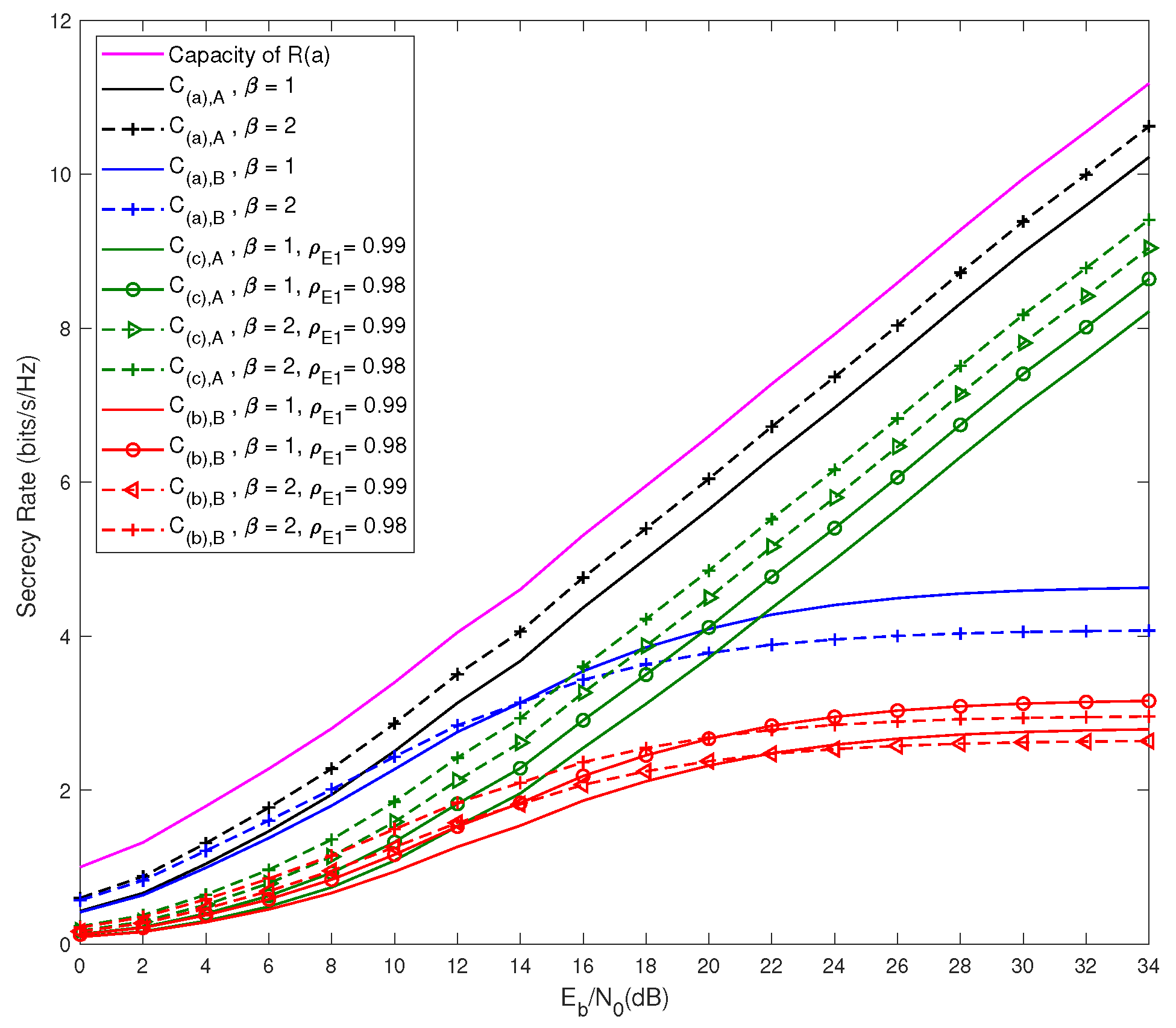
Figure 7 demonstrates the secrecy rate of
and
based on (
17) and (
18), respectively. Since
was always in the negative SINR region,
had the best performance over
,
and
. For any given
value,
always performed better than
because in
, neither
nor
experienced channel estimation error. The performance of
and
did not improve when the SINR was greater than 20 dBm because
experienced precoding error due to the channel estimate error of the EH signals, which was
, and it was independent of the SINR of the information signal as observed in (
15) and (
16). The results of
and
proved that, at high SINR (i.e., greater than 20 dBm),
could perform better than
, irrespective of
’s condition. At low SINR (i.e., less than 20 dBm), the performance of
as compared to
was better because
took advantage of
’s poor performance, and this characteristic validated (
15) and (
16). Similar to the BER results, the secrecy rate performance of
and
was better when
than their performance when
. The secrecy rate of
improved with the increase in
, but in the case of
, contrary to the BER results, the secrecy rate degraded with the increase in
due to the channel estimate error. Unlike the secrecy rate results of
, the impact of channel estimate error on the BER of
was reduced due to the implementation the IB-DFE receiver.