1. Introduction
In mobile data networks, data delivery between mobile nodes can be provided using infrastructure, such as a base station (BS) in cellular networks [
1]. If communication infrastructure does not exist, a mobile ad hoc network (MANET) can be used for data delivery, where dynamic routing path are maintained between nodes [
2]. Cellular networks have been developed very actively, from the first generation (1G) analog networks to current fifth generation (5G) networks, launched last year. Although a cellular network is sufficient to meet the various requirements, such as high data rate, low latency, and high mobility, if such communication infrastructure is not available for some reason, such as failure of infrastructure due to natural disaster or if node-to-node communication is more effective for some scenarios, then self-organizing networks can be a good candidate for enabling data communication between mobile nodes [
3,
4]. In a self-organizing network, such as MANET, mobile nodes form a network topology in a distributed way without a central entity, and communication between nodes is achieved through neighboring mobile nodes, where the topology varies due to the mobility of mobile nodes. Therefore, appropriate routing protocol to maintain the routing path between a source node and a destination node without the help of any centralized infrastructure should be essential to enable an efficient communication between mobile nodes. In a peer-to-peer (P2P) network, which is a logical overlay network, resources are shared between peers and actual routing is achieved using underlying physical networks. A distributed hash table (DHT) is used to search for the resources requested by peers in the underlying networks.
Works on MANET have been carried out significantly during the last decade and has been extended to vehicular ad hoc networks (VANET) or flying ad hoc networks (FANET) [
5,
6,
7]. In MANET, routing protocol is managed proactively or reactively. In proactive routing protocol, routing path between nodes is actively maintained periodically. On the other hand, routing path is maintained on demand in reactive routing protocol [
8,
9,
10]. MANET basically assumes that there exist at least one routing path between a source node S and a destination node D at any time even in mobile environment. However, if this assumption fails, in case where if the density of node is sparse, connection between nodes is broken and communication is not possible any more. Delay tolerant networks (DTN) can provide communication between nodes using store-carry-forward mechanism, even when connectivity between nodes is not guaranteed and it was proposed for communication in disaster or extreme environments [
11,
12].
To tradeoff the pros and cons of MANET and DTN protocols, hybrid protocols combining MANET and DTN have been proposed recently [
13,
14,
15,
16,
17,
18,
19,
20,
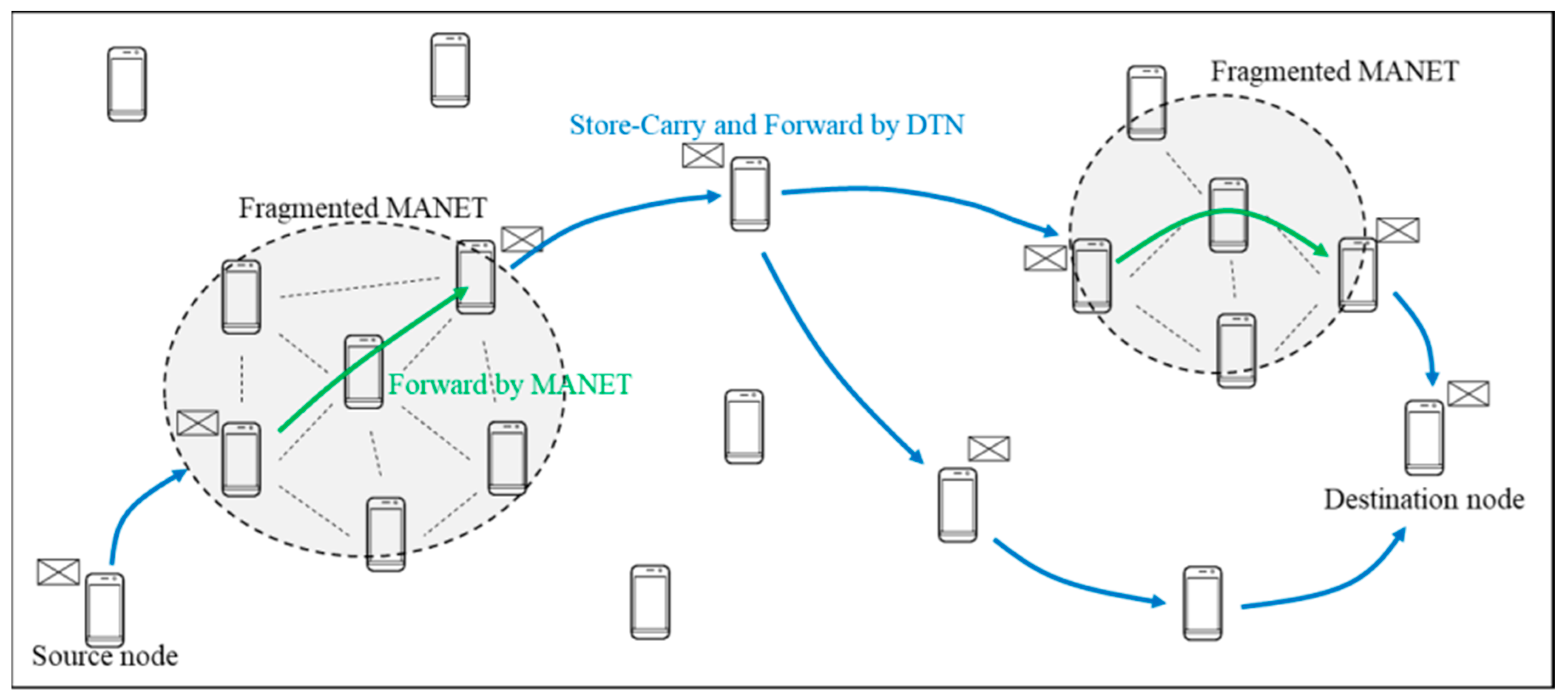
21]. In these works, it is generally assumed that a whole network is fragmented due to disaster or sparse density of nodes, and MANET is used for communication between nodes within the same fragmented network (intra-fragment communication) and DTN is used for communication between nodes belonging to different fragmented networks (inter-fragment communication), as shown in
Figure 1.
In this paper, we propose an improved hybrid routing protocol. If the routing path to the destination node from the source node is not successfully established within a predefined time period, a source node selects virtual source nodes, which was originally proposed in Reference [
13], in fragmented networks based on the delivery predictability to the destination node defined in PRoPHET protocol [
22]. After that, the source node operates based on DTN protocol for a predefined time period and forwards message to other node based on delivery predictability to the destination node. After the time period, the source node switches operates based on PRoPHET protocol. If virtual source nodes are selected, messages are delivered to the virtual source nodes and virtual source node operates as original source node. By doing this, messages can be efficiently disseminated through virtual source nodes.
This paper is organized as follows:
Section 2 reviews related works on hybrid MANET and DTN routing protocol.
Section 3 proposes an improved hybrid routing protocol. Performance of the proposed protocol is evaluated and compared with conventional protocols in
Section 4. Finally,
Section 5 concludes this work and presents future work.
2. Related Works
In Reference [
13], a hybrid social based routing algorithm (HSBR) was proposed, where a whole MANET network is fragmented into subnetworks or islands. In each island, a message is delivered from a source node to a last node which does not have connection with the next hop towards a destination node, and this node acts as a virtual source node and operates based on MANET firstly. Then it switches to DTN later if MANET does not work. In Reference [
14], DTN/MANET routing study for energy critical infrastructure protection project (DMRS) was proposed, where MANET protocol was extended to integrate MANET and DTN by improving the route discover mechanism which includes information from DTN-capable nodes along the routing discover path and taking decisions based on the criticality of the sent messages. The topology of DMRS includes sensor nodes, cluster coordinator nodes, central office nodes, vehicular nodes, recovery/maintenance mobile nodes, and gateway nodes. For integration between MANET and DTN, DTN information is added during the route discovery and criticality based routing is achieved using MANET protocol extension. In Reference [
15], hybrid DTN-MANET routing for dense and highly dynamic wireless networks (HYMAD) protocol was proposed, where network is split into disjoint groups of connected nodes and MANET is used for communication between nodes within the same group and DTN is used for communication between nodes belonging to different groups. Two control messages, i.e., enhanced distance vector and a list of messages held by nodes, are broadcast. An enhanced distance vector is used for intra-group distance vector routing and a list of the messages held by nodes are used for inter-group routing protocol. In addition, DTN protocol is used to transfer messages between nodes located in different groups.
In Reference [
16], a hybrid MANET and DTN protocol was proposed to cope with the limitation of infrastructure-based communication when a natural disaster, such as an earthquake and tsunami. Either MANET or DTN routing protocol is used to deliver messages depending on the number of neighboring mobile nodes, mobility and the remaining battery energy. If the number of neighboring mobile nodes is small, DTN mode is operated. If the mobility is high, DTN mode is selected to avoid link disruption problem of MANET. Since MANET exchanges more control messages, DTN is operated if the remaining battery power is substantially low. In Reference [
17], a hybrid MANET-DTN routing scheme was proposed for emergency response scenarios, where a node operated based on MANET mode switches to DTN mode if a link is not active for a predefined time duration and falls back to MANET mode if a new routing path to a destination nodes is established or a broken link becomes active. In Reference [
18], trust is calculated based on contact history and parameter values. Whenever a packet, such as route response (RREP), route request (RREQ), route acknowledgement (RACK), route error (RERR), and data, exists, the value of trust is calculated, which is divided into two parts: 1) trust calculation based on routing information and 2) trust calculation based on data packets. Then, the final value of trust is calculated. If a node which operates based on MANET faces a link failure, messages are delivered to a node with a higher trust and receiving node operates based on DTN.
In Reference [
19], a new hybrid protocol of MANET and DTN was proposed, where optimized link state routing (OLSR) protocol is assumed for MANET. If a routing path to the destination node for a packet exists, the packet is forwarded using MANET mode. On the other hand, if a routing path to the destination node is broken, the packet is stored in the queue and the node operates in DTN mode. In DTN mode, a packet is forwarded to neighboring nodes and if there is no end-to-end routing path to the destination node, they also store the packet in the queue and operate in DTN mode. In order to limit the flooding-based copying, the number of neighbors to which the packet is forwarded is limited as a predefined cap. In Reference [
20], a new algorithm for secure relay node selection in hybrid MANET and DTN based on the cooperation between routing, trust, and game theory was proposed. In the proposed algorithm, routing and data traffic is monitored in the networks and then the trust level for all mobile nodes are calculated. Then, trust is calculated and non-cooperative game theory is applied for relay node selection and the winning node is selected for relay node. Finally, data is sent to relay node and DTN forwarding mechanism is operated. In Reference [
21], a hybrid MANET and DTN scheme was proposed to use stable MANET contacts and a utility based DTN routing protocol calculates a utility score when two nodes contact each other. In the proposed scheme, stable connections have better utility score. For each contact check interval, service discovery request is started and for all new contacts utility sores are calculated. Then, message forwarding is carried out based on updated utility score.
3. Proposed Protocol
In the proposed protocol, a whole network is divided into fragmented networks based on the connectivity between nodes, which is similar to the works in Reference [
13,
15,
16], and the concept of virtual source node was adopted, which was originally proposed in Reference [
13]. In the proposed protocol, ad hoc on-demand distance vector (AODV) protocol is basically assumed for MANET protocol and it is extended for hybrid routing with DTN protocol. In original AODV protocol, route request (RREQ) messages are broadcast throughout the network from the source node and route response (RREP) messages are sent back to the source node from the destination node. Then, the source node delivers data to the destination node using the reverse path of RREP message. Route error (RERR) messages are broadcast if a link is broken to notify the loss of the link.
In the proposed protocol, if RREQ message is not delivered to the destination node successfully within a predefined maximum number of hop counts and time-to-live (TTL), the last nodes in each routing path of the RREQ messages generates extended RERR (E-RERR) messages and these are broadcast. As shown in
Figure 2, E-RERR message defines filed for E-RERR ID, source node ID of E-RERR, source node ID of RREQ, routing path of delivered RREQ, relay node ID of E-RERR, and delivery predictability of relay node with the destination node calculated based on PRoPHET protocol. The values of these fields are delivered to the source node in the E-RERR message. If E-RERR message is not received at the source node during a predefined timer value, RREQ messages are retransmitted. If there is no E-RERR reception after a predefined number of retries of RREQ message retransmission at the source node, the source node operates in DTN protocol.
In the proposed protocol, f the source node receives E-RERR messages, it selects virtual source nodes based on Equation (1) as follows:
where
is set of virtual source nodes,
is the intermediate relay node
,
is the delivery predictability threshold value, and
is the delivery predictability of node
to node
, which was originally defined in PRoPHET protocol [
22]. In PRoPHET protocol, if two nodes contact each other, the delivery predictability increases and the value decreases as time passes on after the last contact. Thus, P(A,B) is calculated as follow:
where P encounter, Δ, γ, and K are a scaling factor to control the increasing rate of the delivery predictability after contact, a parameter limiting an upper bound of delivery predictability, an aging constant, and the number of elapsed time units after the last contact.
The rationale behind the proposed selection of virtual source nodes, as defined in Equation (1), is to select more probable node to forward the message on behalf of the source node by comparing delivery predictability, where more favor is given to intermediate relay node than source node, in order to promote the message dissemination. That is, if any intermediate relay node in the returning path of E-RERR message satisfies the condition of Equation (1), it is selected as virtual source. In the proposed protocol, multiple virtual source nodes can be selected if they satisfy Equation (1).
In the proposed protocol, if a source node selects virtual source nodes, then it sends message to the selected virtual source nodes using the reverse path of received E-RERR messages. If a virtual source node receives message, it operates like an original source node. It firstly tries to deliver message using MANET protocol, but if it fails, it operates in DTN mode using store-carry-forward approach. Thus, it broadcasts RREQ message and E-RERR messages are returned to the source node. If there is no E-RERR message until the expiration of a predefined timer value, the source node tries to deliver message using DTN protocol. It periodically switches between MANET mode and DTN mode, and if message is successfully delivered to a destination node, it stops its operation.
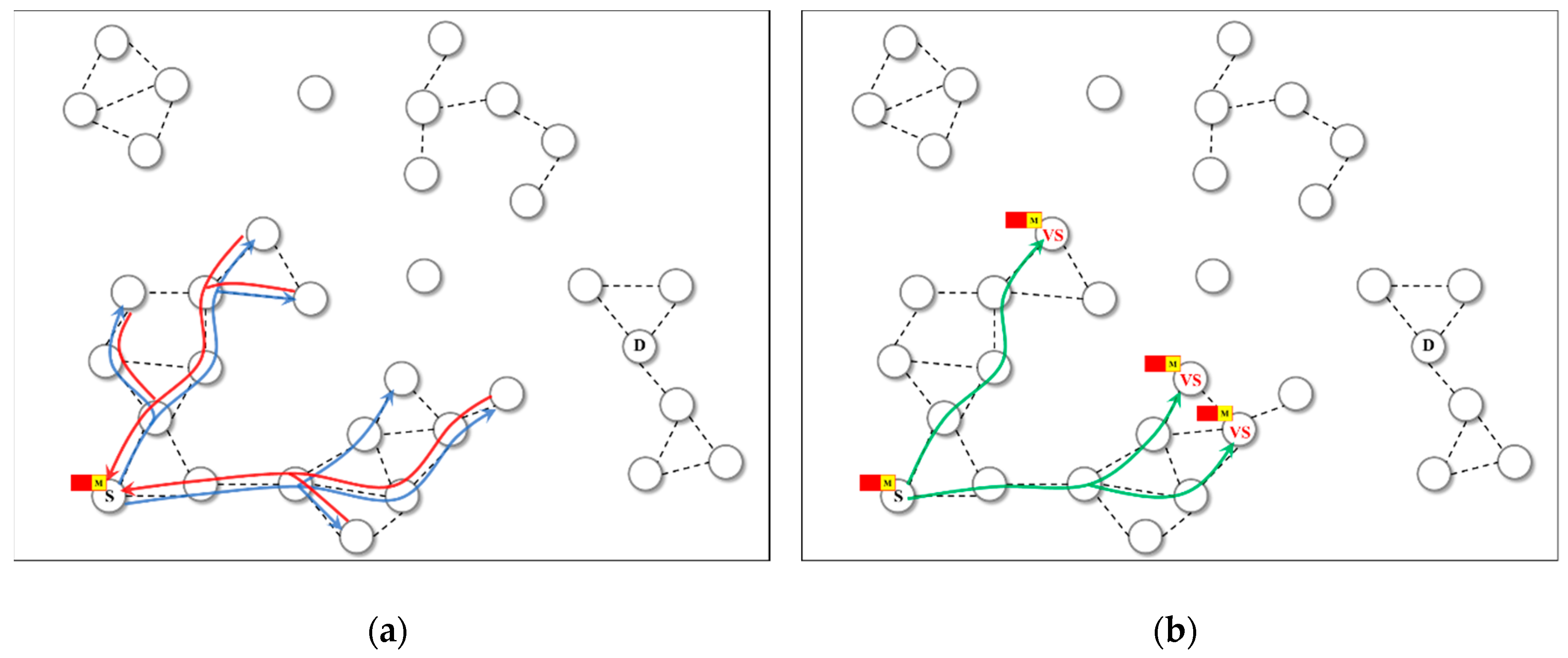
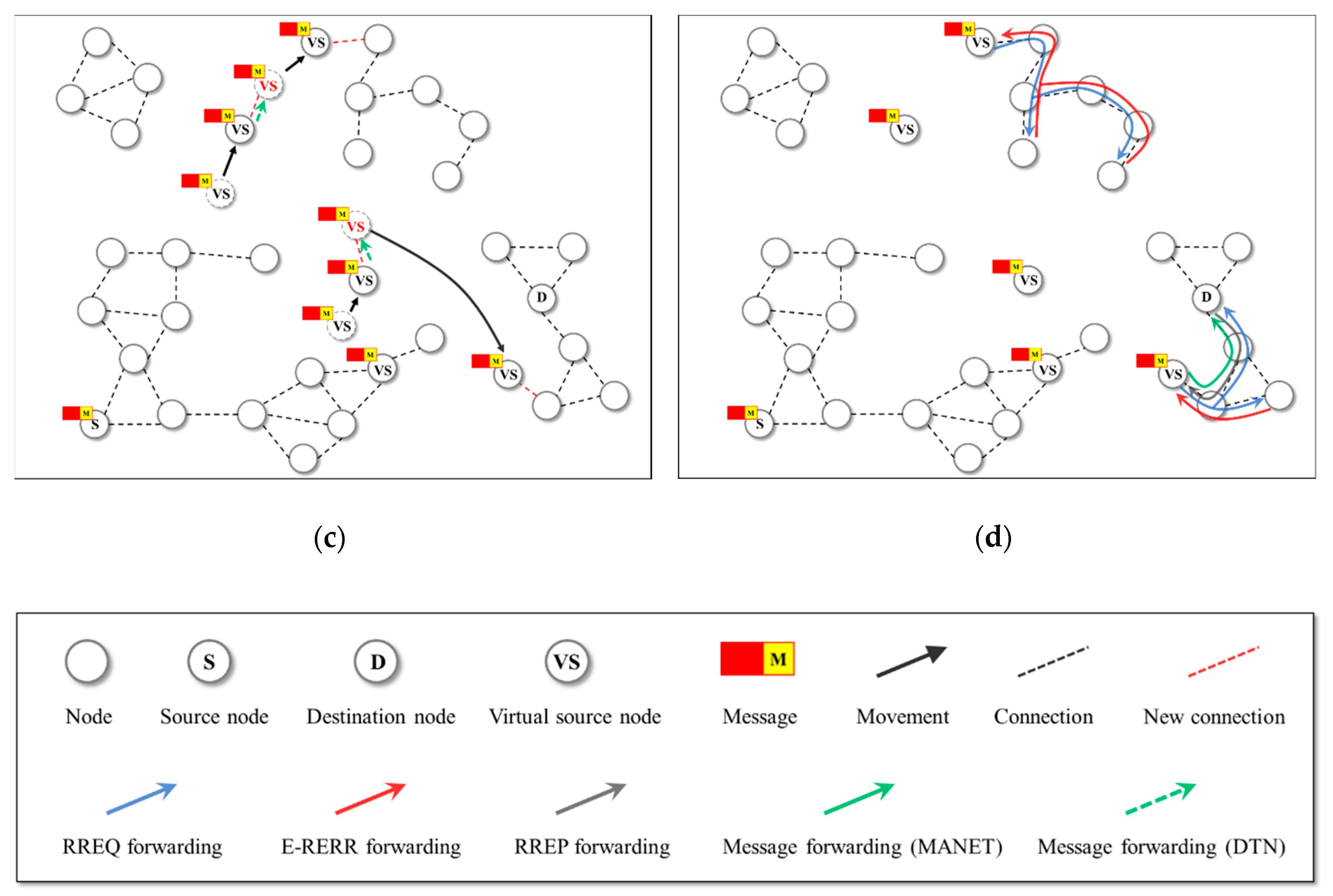
Figure 3 describes the operation of the proposed protocol. A source node broadcast RREQ messages but E-RERR messages are returned to the source node (
Figure 3a) because routing path from the source node to the destination node is not successfully established. Then, virtual source nodes are selected based on the delivery predictability to the destination node and messages are forwarded to the virtual source nodes (
Figure 3b). In this example, three nodes are selected as virtual source nodes. After that, selected virtual source nodes operates as original source node and forwards message to neighboring node when they contact another nodes by DTN protocol after movement, and the receiving nodes also move and contact another nodes (
Figure 3c). Finally, the message is delivered from the virtual source node to a destination node after exchange of RREQ and RREP messages defined by MANET protocol (
Figure 3d).
Although the proposed protocol is similar to the HSBR protocol by using virtual source node [
13], it is different from HSBR protocol. Basically, the proposed protocol is based on AODV protocol for MANET protocol and extended AODV (E-AODV) protocol is used. In the proposed protocol, if RREQ message is not delivered to a destination node, E-RERR message is routed to a source node. However, the HSBR protocol is based on dynamic source routing (DSR) protocol for MANET protocol and modified DSR (M-DSR) protocol is used. In the HSBR protocol, if message is not delivered to a destination node, modified RERR (M-RERR) is routed to a source node, where delivery predictability defined in PRoPHET protocol is assumed to deliver messages in this paper, since a specific algorithm to calculate a probability of delivery for social based opportunistic routing (SBOR) is not specified in detail in Reference [
13]. In the proposed protocol, any node can be selected as virtual source node, if Equation (1) is met. On the other hand, the last node of M-RERR path is generally selected as virtual source node in the HSBR protocol. In the proposed protocol, the operations of MANET and DTN are switched periodically. On the other hand, in the HSBR protocol, if MANET operation is failed to deliver messages, the operation of DTN is carried out. Then the operation of MANET is operated if MANET environment is available again. The distinguishing features of the proposed protocol are summarized as follows:
- (1)
E-RERR message is newly defined to deliver information of intermediate relay nodes, where defined fields for E-RERR message are E-RERR ID, source node ID of E-RERR, source node ID of RREQ, routing path of delivered RREQ, relay node ID of E-RERR, and delivery predictability of relay node with the destination node
- (2)
Multiple intermediate relay nodes can be selected as virtual source node, if they satisfy the condition of Equation (1).
- (3)
Delivery predictability with the destination node of a message is used to select virtual source node for the delivery of the message, and delivery predictability threshold value, , is newly defined, to control the speed of message dissemination.
- (4)
MANET phase and DTN phase are switched periodically to apply MANET or DTN protocol for the appropriate operation for message delivery in a given network topology and mobility/traffic characteristics of nodes.
Figure 4 shows a flowchart to describe the operation of the proposed protocol. Basically, the proposed protocol periodically switches between MANET phase and DTN phase, and each phase is operated for a predefined switching timer. In MANET phase, a source node with a message broadcasts RREQUATION If RREP is received, the message is delivered to a destination node of the message using the reverse path of RREP as in original MANET protocol. Otherwise, the source node checks E-RERR is received. If E-RERR is received successfully, virtual source nodes which satisfying the condition of Equation (1) are selected as virtual source nodes. Then the source node deliver the message to the selected virtual source nodes. If E-RERR is not received, it firstly checks predefined switching timer expires. If the timer expires, it switched to DTN phase. Otherwise, it waits for a next RREQ broadcast period and then broadcast RREP. In DTN phase, a source node checks any neighboring node N. If there is a neighboring node N, it checks whether it is the destination nod of the message. If it is, the message is forwarded to the destination node. Otherwise, a source node compares delivery predictability and if the neighboring node N has larger delivery predictability, the message is forwarded to the neighboring node N. Then, it checks predefined switching timer expires. If the timer expires, it switched to MANET phase, and MANET operation is carried out to deliver messages to a destination node. Otherwise, the above message delivery process is repeated in DTN phase until timer expires.
4. Performance Evaluation
The performance of the proposed protocol was evaluated by extending opportunistic network environment (ONE) simulator [
23], which was developed by Helsinki University to simulate DTN protocol. The performance measures used in this simulation are delivery ratio, overhead ratio, and delivery latency and they are defined as follow:
Parameter values assumed in the simulation are summarized in
Table 1.
Figure 5 shows delivery ratio for varying the number of nodes from 20 to 200. The performance of the proposed protocol is evaluated for different threshold values, i.e., 0, 0.1, 0.2, 0.4, and 0.8, and it was compared with that of AODV (only MANET mode), PRoPHET (only DTN mode), and HSBR. As shown in
Figure 5, AODV has the largest delivery ratio when the number of nodes is large but it has the smallest delivery ratio when the number of nodes is small. On the other hand, PRoPHET has the smallest delivery ratio when the number of nodes is large and it has similar delivery ratio with proposed protocol when the number of nodes is small. The proposed protocol has better delivery ratio than other protocols when the number of nodes is not high, i.e., when the number of nodes is smaller than 120 in this simulation. The proposed protocol has similar delivery ratio with HSBR protocol and it has slightly smaller delivery ratio than AODV when the number of nodes is high. In the proposed protocol, the proposed protocol with large values of delta has better delivery ratio when the number of nodes is small but the proposed protocol with small values of delta has better delivery ratio when the number of nodes is high. This is because, more message disseminations is more favorable for message delivery and results in higher delivery ratio when the number of nodes is small but smaller message dissemination, as shown in Equation (1). On the other hand, less message disseminations is more favorable for message delivery to avoid buffer overflow when the number of nodes is high. The result shows that the proposed protocol with appropriate promotion of message dissemination performs better than other protocols.
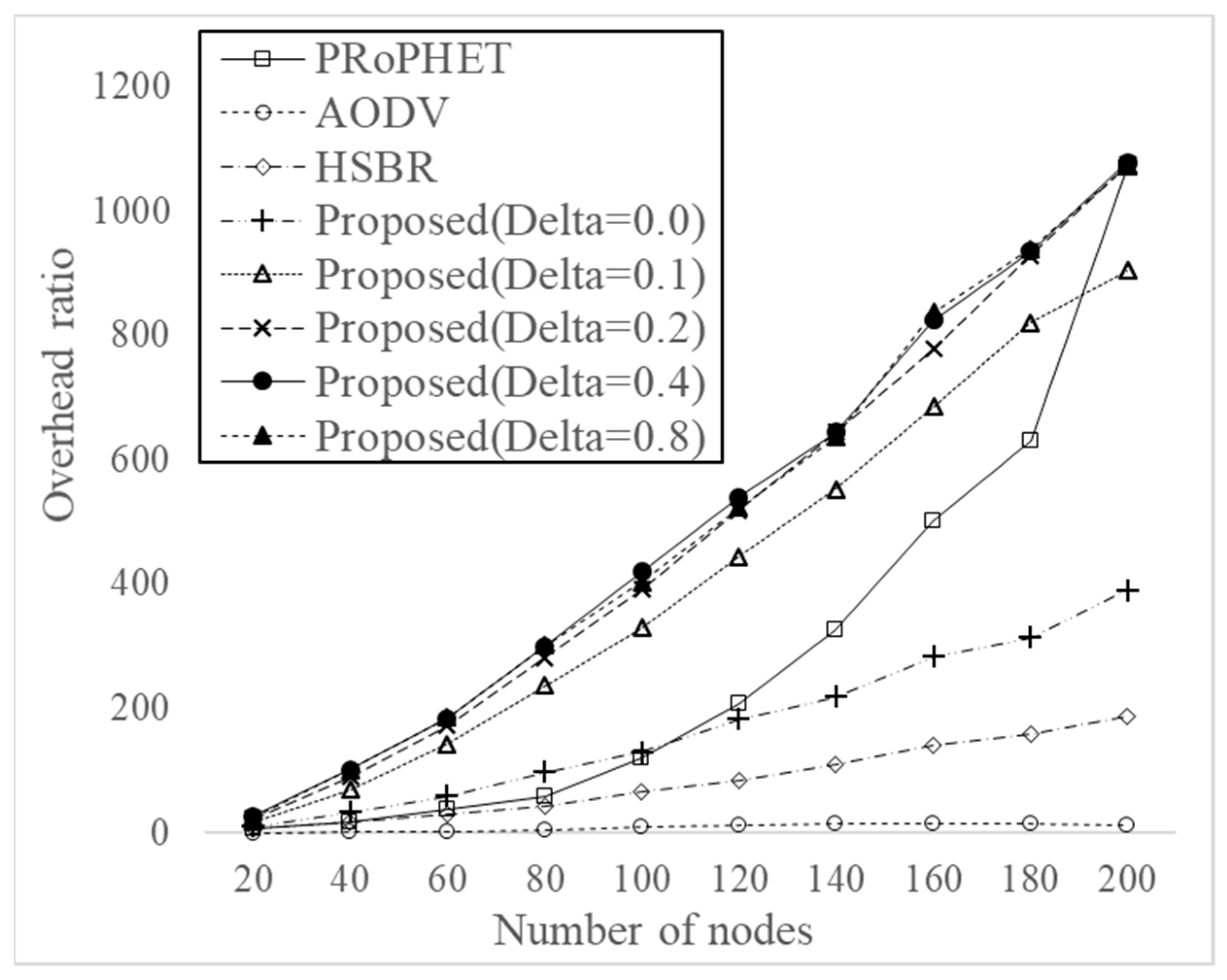
Figure 6 shows overhead ratio for varying the number of nodes from 20 to 200 with different threshold values, i.e., 0, 0.1, 0.2, 0.4, and 0.8. AODV has the smallest overhead ratio and then HSBBR has the second smallest overhead ratio. In the proposed protocol, the proposed protocol with large values of delta has high overhead ratio due to more message dissemination and the proposed protocol with small values of delta has small overhead ratio due to less message dissemination. Since PRoPHET has much smaller delivery ratio than the proposed protocols, the overhead ratio sharply increases when the number of nodes is high, as seen from Equation (5). The result shows that the proposed protocol has higher overhead ratio due to more message dissemination.
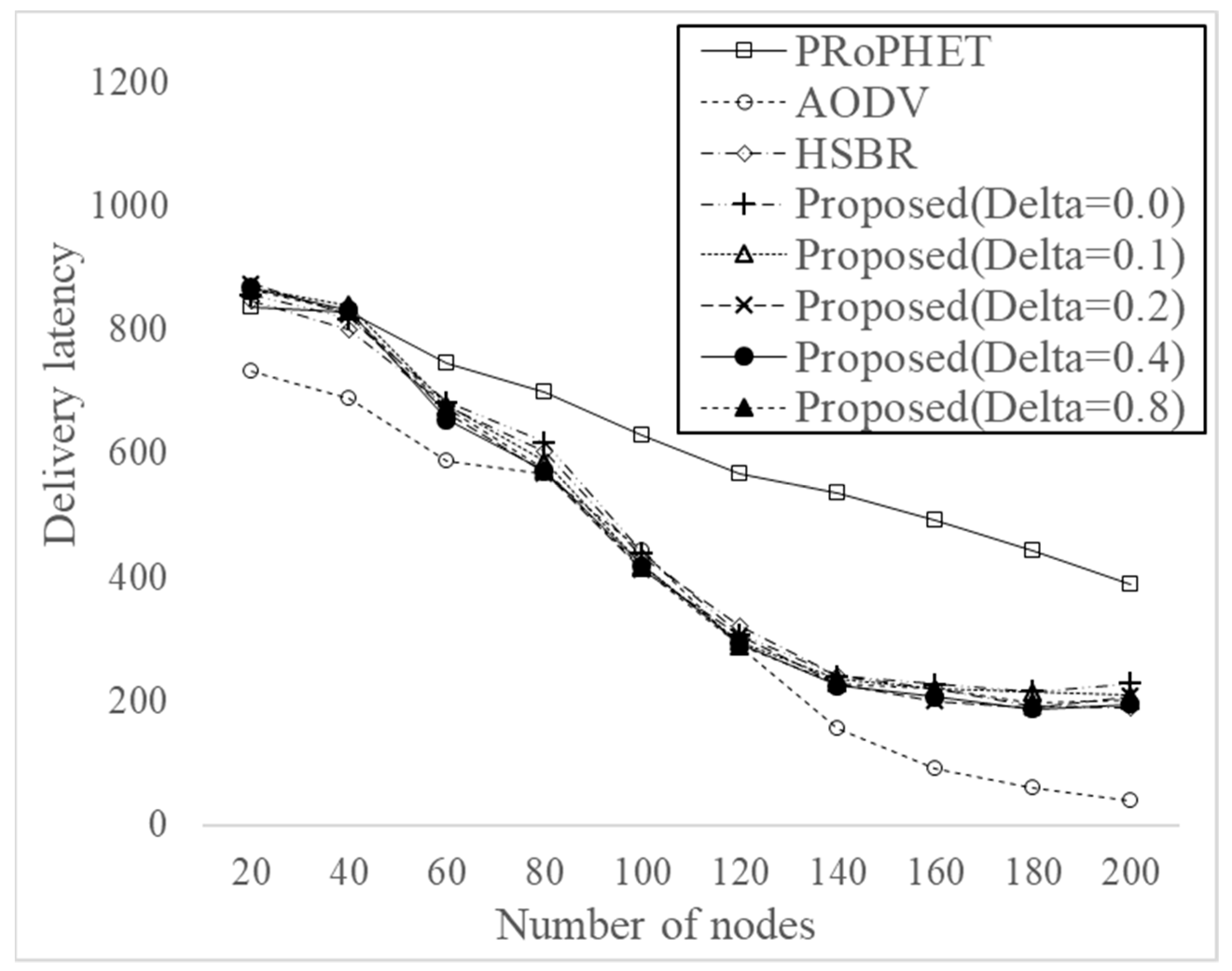
Figure 7 shows delivery latency for varying the number of nodes from 20 to 200 with different threshold values, i.e., 0, 0.1, 0.2, 0.4, and 0.8. As can be expected, AODV has the smallest delivery latency, but PRoPHET has the largest delivery latency since delivery latency is calculated for the successfully delivered messages only, as shown in Equation (6). The proposed protocol has larger delivery latency than AODV but smaller delivery latency than PRoPHET. The proposed protocol has similar delivery latency with HSBR. The results shows that the effect of threshold values on the delivery latency is not significant.
Figure 8 shows delivery ratio for varying the speed of nodes from U[0.0,0.5] (m/s) to U[4.5,5.0] (m/s) with different threshold values, i.e., 0, 0.1, 0.2, 0.4, and 0.8, when the number of node is 60. Since the number of nodes is fixed as 60, the proposed protocol with high values of delta has the largest delivery ratio and AODV has the smallest delivery ratio. When the speed of nodes increases, delivery ratio sharply increases, but it has similar values when the speed of nodes is not very small. Therefore, the effect of the speed of nodes is not significant when the mobility of nodes is not so small to contact with other nodes after movement.
Figure 9 shows overhead ratio for varying the speed of nodes from U[0.0,0.5] (m/s) to U[4.5,5.0] (m/s) with different threshold values, i.e., 0, 0.1, 0.2, 0.4, and 0.8, when the number of node is 60. AODV has the smallest overhead ratio, and then HSBR has the second smallest overhead ratio. In the proposed protocol, the proposed protocol with large values of delta has high overhead ratio due to more message dissemination, and the proposed protocol with small values of delta has small overhead ratio due to less message dissemination. The proposed protocol when the value of delta is 0 has a similar overhead ration with HSBR. The result shows that the proposed protocol has higher overhead ratio due to more message dissemination, when the value of delta is not so small.
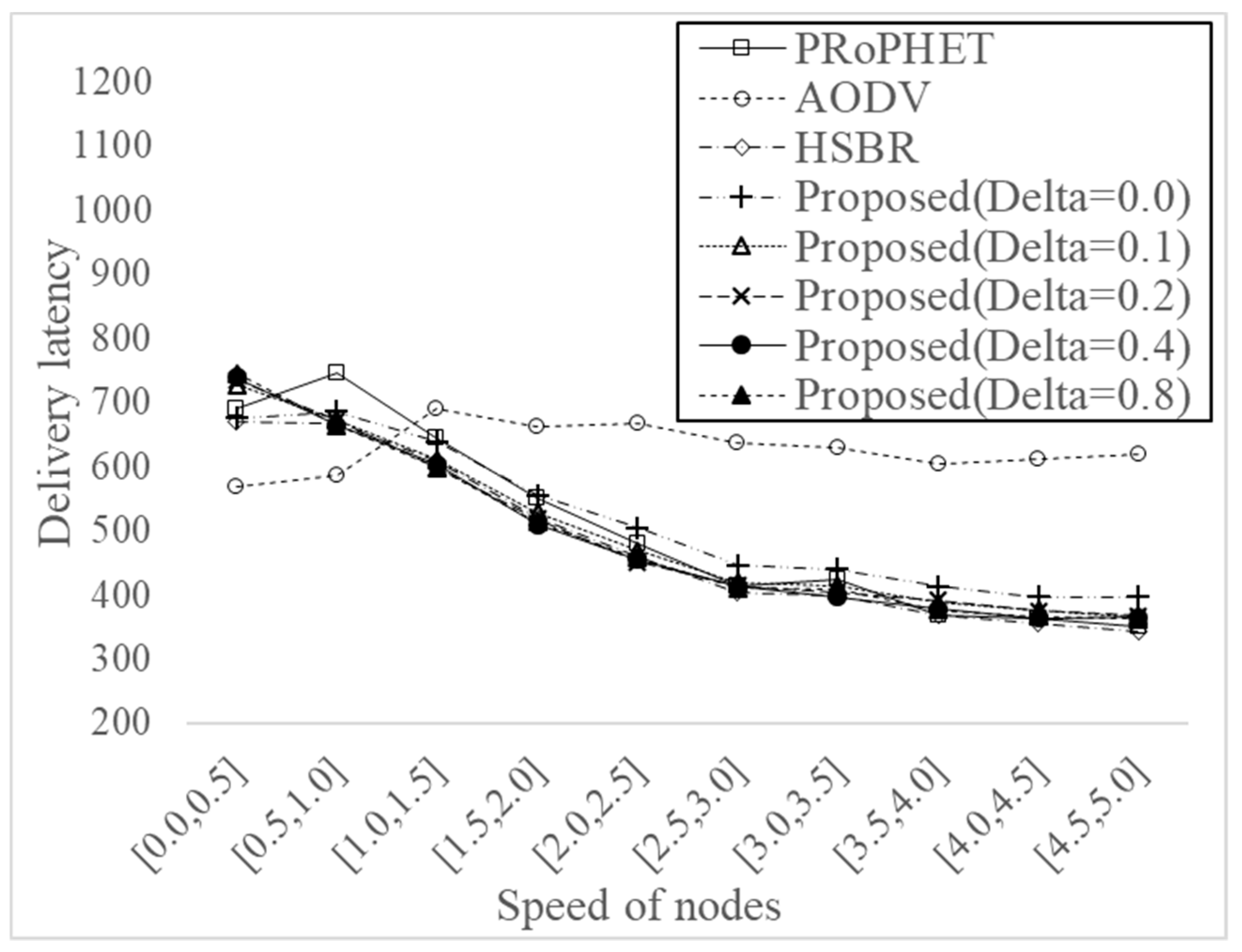
Figure 10 shows delivery latency for varying the speed of nodes from U[0.0,0.5] (m/s) to U[4.5,5.0] (m/s) with different threshold values, i.e., 0, 0.1, 0.2, 0.4, and 0.8, when the number of node is 60. The delivery latency of AODV is smallest and the delivery latency of PRoPHET is largest when the speed of nodes is U[0.5,1.0] (m/s), which is a default setting, as shown from
Figure 7. When the speed of nodes increases, however, the delivery latency of AODV is higher than other protocols since topology is not stable in high speed environment and thus most of the message delivery in AODV is achieved using direct delivery when it contacts the destination node directly. On the other hand, the delivery latency of other protocols based on DTN protocol is smaller than AODV when the speed of nodes is high and it decreases as the speed of nodes increases because of more contact with other nodes. The proposed protocol has similar delivery latency with HSBR. The results shows that the effect of threshold values on the delivery latency is not significant.
5. Conclusions and Future Works
In this paper, an improved hybrid routing protocol combining MANET and DTN was proposed. Then, the performance of the proposed protocol was compared from the aspects of delivery ratio, overhead ratio, and delivery latency. It was shown that the proposed protocol with appropriate selection of delivery predictability threshold values has better delivery ratio than HSBR protocol, at the expense of overhead ratio, and has similar delivery latency with HSBR protocol in the considered parameter setting. The result of this study can be used for an environment, such as disaster scenario or military scenario, where MANET and DTN should be used together in a hybrid way. In a disaster scenario or military scenario, infrastructure may not work well, and the connectivity between neighboring nodes is not stable. Thus, MANET can be used when the routing path to the destination node is available. Otherwise, DTN can be used, and a message can be delivered using store-carry-forward approach.
In our future work, we will study about how to select the delivery predictability threshold value dynamically in varying scenarios to adapt varying network environment well. In addition, fault tolerance of the proposed protocol will be studied in our future work, too, since mobile nodes may not work well due to either the battery power problem or the destruction of mobile nodes, and the analysis of the effect of this fault on the proposed protocol is important for the application of a real disaster or military scenario. Finally, mathematical modeling and analysis of the proposed protocol and optimization will be carried out, too.