Priority Determination to Apply Artificial Intelligence Technology in Military Intelligence Areas
Abstract
1. Introduction
2. Research Background and Trend Analysis
2.1. Concepts and Tasks of Military Intelligence
2.2. Development Trends of Military Information Systems
2.3. National Strategy for AI
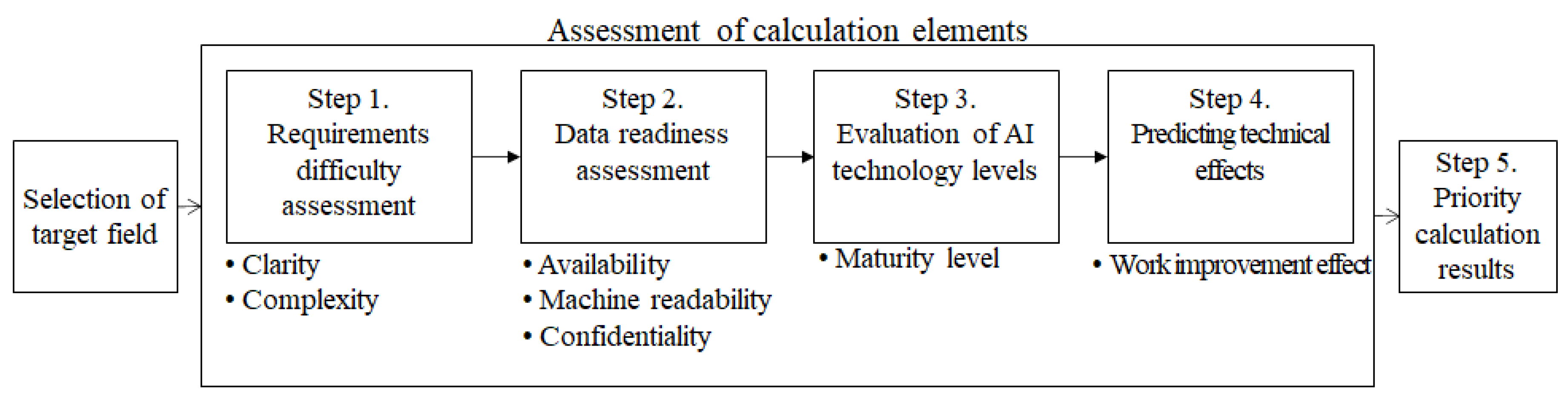
3. Method of Priority Determination for the Application of AI
3.1. Selection of Target Areas Subject to Technology Application
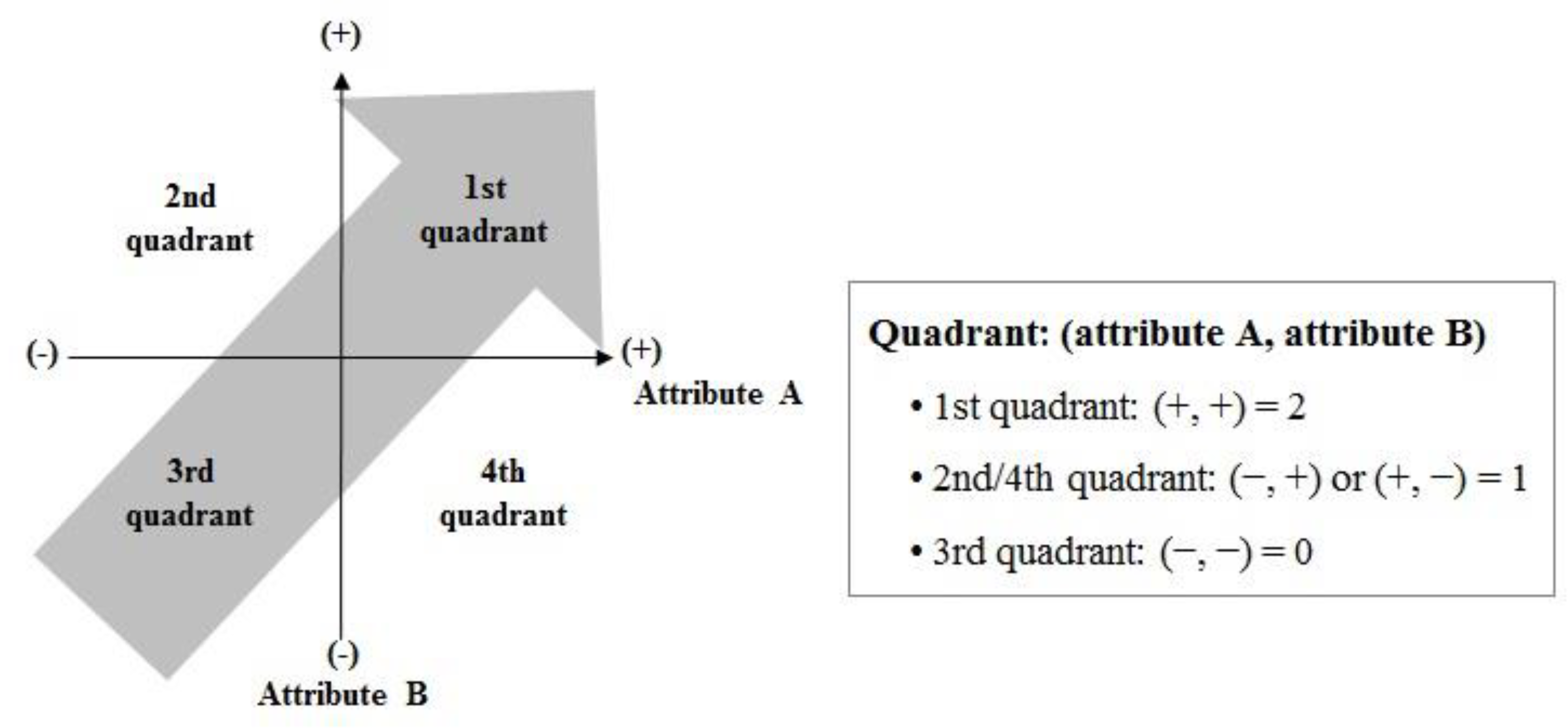
3.2. Criteria for Determining Priorities
3.3. Priority-Determination Procedure
4. Applying Priority Determination Methods for Applying AI to Military Intelligence Areas
4.1. Selection of the Target Domain
4.2. Priority Determination
4.3. Results of Priority Determination
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- 2018 Defense White Paper. The Ministry of National Defense. 2018. Available online: https://www.mnd.go.kr/cop/pblictn/selectPublicationUser.do?siteId=mnd&componentId=14&categoryId=15&publicationSeq=835&pageIndex=1&id=mnd_020704000000 (accessed on 29 October 2020).
- Wang, W.; Liu, H.; Lin, W.; Chen, Y.; Yang, J.A. Investigation on Works and Military Applications of Artificial Intelligence. IEEE Access 2020, 8, 131614–131625. [Google Scholar] [CrossRef]
- Joint Publication 2-0 Joint Intelligence. Joint Chiefs of Staff. 2013. Available online: https://www.jcs.mil/Portals/36/Documents/Doctrine/pubs/jp2_0.pdf (accessed on 29 October 2020).
- Boyd, J.R. A Discourse on Winning and Losing; Air University Press: Montgomery, AL, USA, 2018. [Google Scholar]
- Lingel, S.L.; Rhodes, C.; Cordova, A.; Hagen, J.; Kvitky, J.; Menthe, L. Methodology for Improving the Planning, Execution, and Assessment of Intelligence, Surveillance, and Reconnaissance Operations; RAND Corporation: Santa Monica, CA, USA, 2008; Available online: https://www.rand.org/pubs/technical_reports/TR459.html (accessed on 29 October 2020).
- The Operational Test and Evaluations. Distributed Common Ground System-Army (DCGS-A) Increment 1 Rease 2, January 2016. Available online: https://apps.dtic.mil/dtic/tr/fulltext/u2/1007951.pdf (accessed on 29 October 2020).
- Ortiz-Peña, H.J.; Nagi, R.; Sudit, M.; Moskal, M.D.; Dawson, M.; Fink, J.; Hanratty, T.; Heilman, E.; Tuttle, D. From information needs to information gathering: A system optimization perspective to ISR synchronization. In Proceedings of the SPIE: Ground/Air Multisensor Interoperability, Integration, and Networking for Persistent ISR III, Baltimore, MD, USA, 23–26 April 2012; Volume 8389. [Google Scholar]
- FM 3-05.102 Army Special Operations Forces Intelligence. U.S. Army. 2001. Available online: https://fas.org/irp/doddir/army/fm3-05-102.pdf (accessed on 29 October 2020).
- Raytheon IIS. FoxTEN, Washington, DC, USA. 2019. Available online: https://www.raytheon.com/capabilities/products/foxten (accessed on 29 October 2020).
- Rafael. IMILITE Rafael’s Proposal for the Republic of Korea, Seoul, Korea. Unpublished work. 2017. [Google Scholar]
- Janes. Janes Data Analytics Brochure, Washington, DC, USA. Unpublished work. 2019. [Google Scholar]
- Park, C.J. 3D Synthetic Battlefield Construction and Visualization Technology Based on Images Taken with Multi-Altitude, Heterogeneous Sensors; Electronics and Telecommunications Research Institute: Daejeon, Korea, 2019. [Google Scholar]
- Yu, J.J.; Park, C.J. 3D Structure Reconstruction from Aerial Imagery. In Proceedings of the ICCE-Asia, Seoul, Korea, 26–28 October 2016. [Google Scholar]
- Kim, H.S.; Ban, Y.J.; Park, C.J. A Seamless Texture Color Adjustment Method for Large-Scale Terrain Reconstruction. In Proceedings of the SIGGRAPH’18, Vancouver, BC, Canada, 12–16 August 2018. [Google Scholar]
- Ban, Y.J.; Kim, H.S.; Park, C.J. 3D Mesh Reconstruction from Height map and Post Processing. In Proceedings of the ICTC, Jeju, Korea, 17–19 October 2018. [Google Scholar]
- Preece, A.; Gomez, M.; Mel, G.; Vasconcelos, W.; Sleeman, D.; Colley, S.; Pearson, G.; Pham, T.; Porta, T. Matching sensors to missions using a knowledge-based approach. In Proceedings of the SPIE: Defense Transformation and Net-Centric Systems 2008, Orlando, FL, USA, 16–20 March 2008; Volume 6981, p. 698109. [Google Scholar]
- Fossaceca, J.M.; Young, S.H. Artificial intelligence and machine learning for future army applications. In Proceedings of the SPIE Ground/Air Multisensor Interoperability, Integration, and Networking for Persistent ISR IX, Orlando, FL, USA, 4 May 2018. [Google Scholar]
- Fan, J.; Liu, J. The challenges and some thinking for the intelligentization of precision guidance ATR. In Proceedings of the SPIE Security + Defense, Strasbourg, France, 19 September 2019. [Google Scholar]
- Atkins, S.A. Multidomain Observing and Orienting: ISR to Meet the Emerging Battlespace. Air Space Power J. 2018, 32, 26–44. [Google Scholar]
- Coman, C.; Veum, K. Automation within the ISR collection management. In Proceedings of the COMM 2014, Bucharest, Romania, 29–31 May 2014. [Google Scholar]
- Robert Work. Memorandum: Establishment of an Algorithmic Warfare Cross-Functional Team (Project Maven); Deputy Secretary of Defense: Washington, DC, USA, 2017. [Google Scholar]
- Morgan, F.E.; Boudreaux, B.; Lohn, A.J.; Ashby, M.; Curriden, C.; Klima, K.; Grossman, D. Military Applications of Artificial Intelligence: Ethical Concerns in an Uncertain World; RAND Corporation: Santa Monica, CA, USA, 2020; Available online: https://www.rand.org/pubs/research_reports/RR3139-1.html (accessed on 29 October 2020).
- Executive Order on Maintaining American Leadership in Artificial Intelligence. White House. 2019. Available online: https://www.whitehouse.gov/presidential-actions/executive-order-maintaining-american-leadership-artificial-intelligence/ (accessed on 29 October 2020).
- National Strategy for Artificial Intelligence. Joint of Related Ministries. 2019. Available online: https://www.korea.kr/news/pressReleaseView.do?newsId=156366736 (accessed on 29 October 2020).
- Review of French AI Recommendations and ICT Policies. Global ICT R&D Policy Trends, Issue 2018-01; Institute of Information & Communications Technology Planning & Evaluation: Daejeon, Korea, 2018; Available online: http://www.itfind.or.kr/admin/getFile.htm?identifier=02-001-180516-000001 (accessed on 29 October 2020).
- AI Policy Trends and Implementation Strategies in Japan. Global ICT R&D Policy Trends, Issue 2017-01; Institute of Information & Communications Technology Planning & Evaluation: Daejeon, Korea, 2017; Available online: http://www.itfind.or.kr/admin/getFile.htm?identifier=02-001-170623-000015 (accessed on 29 October 2020).
- The 4th Industrial Revolution Smart Defense Innovation Plan. The Ministry of National Defense. 2019. Available online: https://www.mnd.go.kr/mbshome/mbs/reform/subview.jsp?id=reform_010601000000 (accessed on 29 October 2020).
- 21–25 Defense Midterm Plan, Ministry of National Defense. 2020. Available online: https://www.mnd.go.kr/user/boardList.action?command=view&page=1&boardId=O_59748&boardSeq=O_256039&titleId=null&siteId=mnd&id=mnd_010403000000&column=null&search=null (accessed on 29 October 2020).
- The MND CIO Committee. Decision on Urgent Need for Defense Informatization Project. The Ministry of National Defense, Seoul, Korea. Unpublished work. 2019. [Google Scholar]
- Artificial Intelligence R&D Strategy. The Ministry of Science and ICT. 2018. Available online: https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwj74NmqoZrtAhXEc3AKHUGIBYYQFjABegQIAxAC&url=http%3A%2F%2Fpolicy.nl.go.kr%2Fcmmn%2FFileDown.do%3FatchFileId%3D221137%26fileSn%3D62558&usg=AOvVaw2zYO0HqcQHFfkrXPTJsQAm (accessed on 29 October 2020).
- Public Data Management Guidelines, Notification No. 2019-71. Ministry of the Interior and Safety, September 2019. Available online: https://www.mois.go.kr/frt/bbs/type001/commonSelectBoardArticle.do?bbsId=BBSMSTR_000000000016&nttId=72733 (accessed on 29 October 2020).
- Goodfellow, I.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative Adversarial Nets. In Proceedings of the NIPS 2014, Montreal, QC, Canada, 8–13 December 2014. [Google Scholar]
- Kim, T.; Cha, M.; Kim, H.; Lee, J.K.; Kim, J. Learning to Discover Cross-Domain Relations with Generative Adversarial Networks. In Proceedings of the ICML 2017, Sydney, Australia, 6–11 August 2017. [Google Scholar]
- Choi, Y.; Choi, M.; Kim, M.; Ha, J.W.; Kim, S.; Choo, J. StarGAN: Unified Generative Adversarial Networks for Multi-Domain Image-to-Image Translation. In Proceedings of the CVPR 2018, Salt Lake City, UT, USA, 18–23 June 2018; pp. 8789–8797. [Google Scholar]
- CLEVR Data Set Is a Dataset Containing 70,000 Images and 699,989 Relational/Non-Relational Inference Q&A. Available online: https://cs.stanford.edu/people/jcjohns/clevr/ (accessed on 29 October 2020).
- Santoro, A.; Raposo, D.; Barrett, D.; Malinowski, M.; Pascanu, R.; Battaglia, P.; Lillicrap, T. A simple neural network module for relational reasoning. In Proceedings of the NIPS 2017, Long Beach, CA, USA, 4–9 December 2017. [Google Scholar]
- Johnson, J.; Hariharan, B.; Maaten, L.; Fei-Fei, L.; Zitnick, C.L.; Girshick, R. CLEVR: A Diagnostic Dataset for Compositional Language and Elementary Visual Reasoning. In Proceedings of the CVPR 2017, Honolulu, HI, USA, 21–26 July 2017. [Google Scholar]
- ILSVRC Is a Competition for Evaluating Image Classification Algorithms Using Data from ImageNet. Available online: http://www.image-net.org/challenges/LSVRC/ (accessed on 29 October 2020).
- Yang, W.Y.; Zhang, H.; Song, D.; Lai, F. Review of face recognition methods. In Proceedings of the MSOTA 2018, Xiamen, China, 25–26 November 2018; pp. 560–564. [Google Scholar]
- Nagpal, K.; Foote, D.; Liu, Y.; Chen, P.C.; Wulczyn, E.; Tan, F.; Olson, N.; Smith, J.L.; Mohtashamian, A.; Wren, J.H.; et al. Development and validation of a deep learning algorithm for improving Gleason scoring of prostate cancer. Nat. NPJ Digit. Med. 2019, 2, 1–10. [Google Scholar] [CrossRef] [PubMed]
- Park, Y.; Patwardhan, S.; Visweswariah, K.; Gates, S.C. An Empirical Analysis of Word Error Rate and Keyword Error Rate. In Proceedings of the 9th Annual Conference of the International Speech Communication Association (INTERSPEECH 2008), Brisbane, Australia, 22–26 September 2008. [Google Scholar]
- Këpuska, V.; Bohouta, G. Comparing speech recognition system (Microsoft API, Google API and CMU Sphix). Int. J. Eng. Res. Appl. 2017, 7, 20–24. [Google Scholar]
- Glasser, A.; Kushalnagar, K.; Kushalnagar, R. Feasibility of Using Automatic Speech Recognition with Voices of Deaf and Hard-of-Hearing Individuals. In Proceedings of the ASSETS’17, Baltimore, MD, USA, 29 October–1 November 2017. [Google Scholar]
- ProBeat: Has Google’s Word Error Rate Progress Stalled? 10 May 2019. Available online: https://venturebeat.com/2019/05/10/probeat-has-googles-word-error-rate-progress-stalled (accessed on 29 October 2020).
- Xiong, W.; Wu, L.; Alleva, F.; Droppo, J.; Huang, X.; Stolcke, A. The Microsoft 2017 Conversational Speech Recognition System. In Proceedings of the ICASSP 2018, Calgary, AB, Canada, 15–20 April 2018; pp. 5934–5938. [Google Scholar]
- Kodish-Wachs, J.; Agassi, E.; Kenny, P.; Overhage, J.M. A systematic comparison of contemporary automatic speech recognition engines for conversational clinical speech. In Proceedings of the AMIA Annual Sysmposium 2018, Washington, DC, USA, 5 December 2018; pp. 683–689. [Google Scholar]
- Oord, A.; Dieleman, S.; Zen, H.; Simonyan, K.; Vinyals, O.; Graves, A.; Kalchbrenner, N.; Senior, A.; Kavukcuoglu, K. Wavenet: A Generative Model for Raw Audio. arXiv 2016, arXiv:1609.03499. [Google Scholar]
- Microsoft Emotion API. Available online: https://azure.microsoft.com/en-us/blog/tag/emotion-api/ (accessed on 29 October 2020).
- Vinyals, O.; Toshev, A.; Bengio, S.; Erhan, D. Show and tell: A neural image caption generator. In Proceedings of the CVPR 2015, Boston, MA, USA, 8–10 June 2015; Volume 1, pp. 3156–3164. [Google Scholar]
- Shanahan, J. Disruption in UAS: The Algorithmic Warfare Cross-Functional Team (Project Maven). Defense Intelligence, Office of the Under Secretary of Defense for Intelligence. 2018. Available online: https://airpower.airforce.gov.au/APDC/media/Events-Media/RAAF%20AP%20CONF%202018/1130-1200-Shanahan-Disruption-in-UAS-The-AWCFT.pdf (accessed on 29 October 2020).
- Hangul Is a Word Processor Developed by Hancom. Available online: https://www.hancom.com/main/main.do (accessed on 29 October 2020).
- Frefer, A.A.; Mahmoud, M.; Haleema, H.; Almamlook, R. Overview success criteria and critical success factors in project management. J. Ind. Eng. Manag. 2018, 7, 244. [Google Scholar] [CrossRef]
- Al-Tmeemy, S.H.; Abdul-Rahman, H.; Harun, Z. Future Criteria for Success of Building Projects in Malaysia. Int. J. Proj. Manag. 2010, 29, 337–348. [Google Scholar] [CrossRef]
- Gomesa, J.; Romao, M. Improving Project Success: A Case Study Using Benefits and Project Management. Procedia Comput. Sci. 2016, 100, 489–497. [Google Scholar] [CrossRef]
- Jurisch, M.C.; Ikas, C.; Palka, W.; Wolf, P.; Krcmar, H. A Review of Success Factors and Challenges of Public Sector BPR Implementations. In Proceedings of the 2012 45th Hawaii International Conference on System Sciences, Maui, HI, USA, 4–7 January 2012; pp. 2603–2612. [Google Scholar] [CrossRef]
- Oh, J.T. Proposal on National Competitiveness Elevation and Business Innovation Plan for Artificial Intelligence; Electronics and Telecommunications Research Institute: Daejeon, Korea, 2015. [Google Scholar]
- Radanliev, P.; De Roure, D.C.; Nurse, J.R.C.; Montalvo, R.M.; Cannady, S.; Santos, O.; Maddox, L.; Burnap, P.; Maple, C. Future developments in standardisation of cyber risk in the Internet of Things (IoT). Springer Nat. J. Appl. Sci. 2020, 2, 169. [Google Scholar] [CrossRef]

| Type | Description | |
|---|---|---|
| Learning | Machine Learning | Forms a recognition or understanding model based on data, or analyzes and learns data on its own to find the optimal answers. |
| Inference | Inference/Expression of knowledge | To derive the answer to problems (new information) by itself based on input and learning data |
| Recognition | Visual Intelligence | To obtain solutions using method equivalent to the sensory organs of human beings, such as looking, reading, and listening |
| Linguistic Intelligence | ||
| Auditory Intelligence | ||
| Application | Understanding Situation/Emotions | To understand situations and emotions by analyzing sensor data or user data |
| Intelligent Agent | To assist machine and robot movements as well as human behaviors and judgment to execute learning and judgment results | |
| Item | Considerations | Description |
|---|---|---|
| Requirement (Problem) | Clarity of requirements | Is there a problem to solve defined by applying AI? (current or future ISR work) |
| Complexity of requirements | How complex are the business procedures that need to be handled? (the number of information sources: one/multi-sources) | |
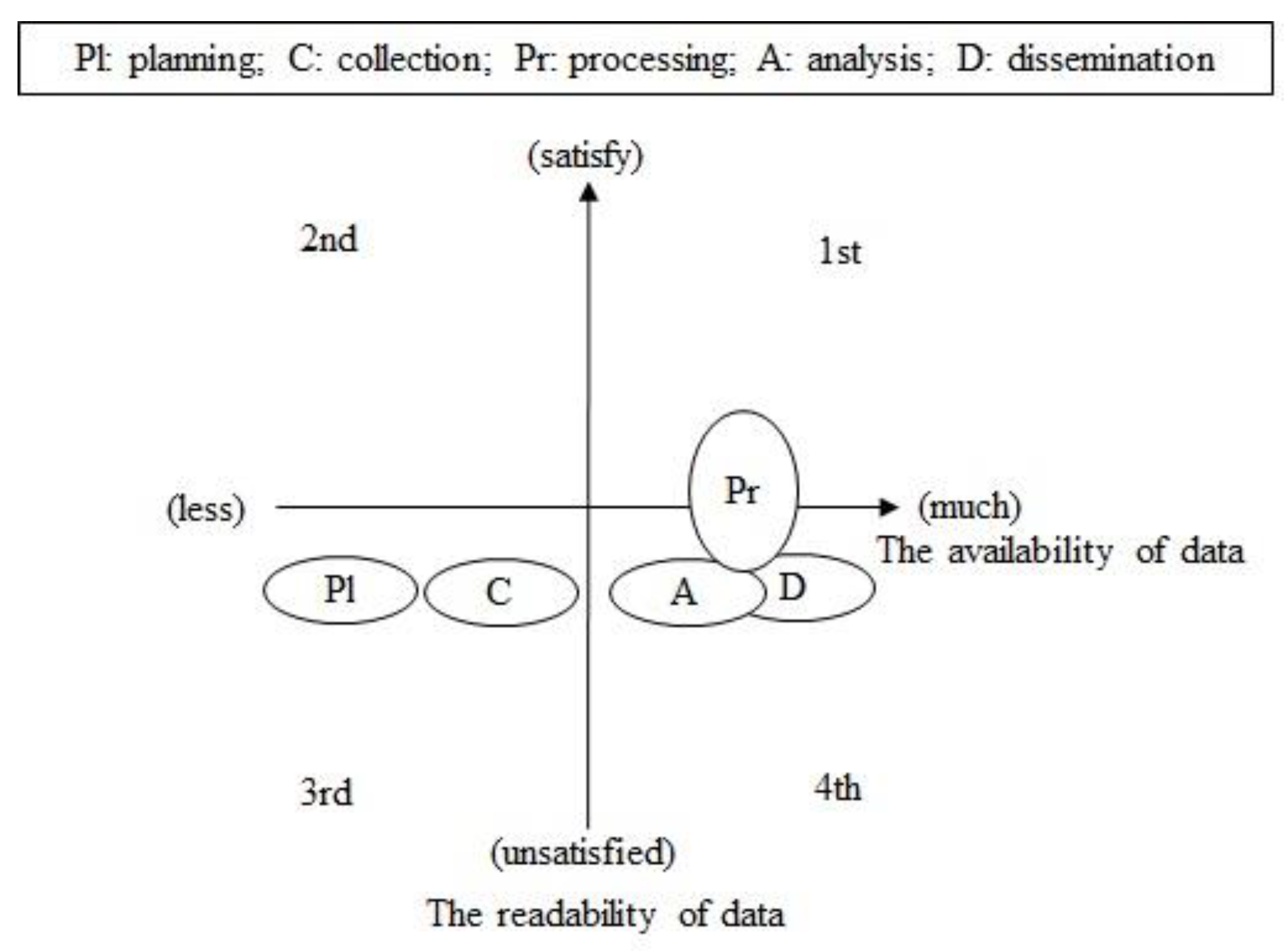
| Data | Data availability | Are there digitized data to be applied using the new technology? |
| Data readiness | Is the data machine readable? | |
| Data confidentiality | Can the data be released and shared? | |
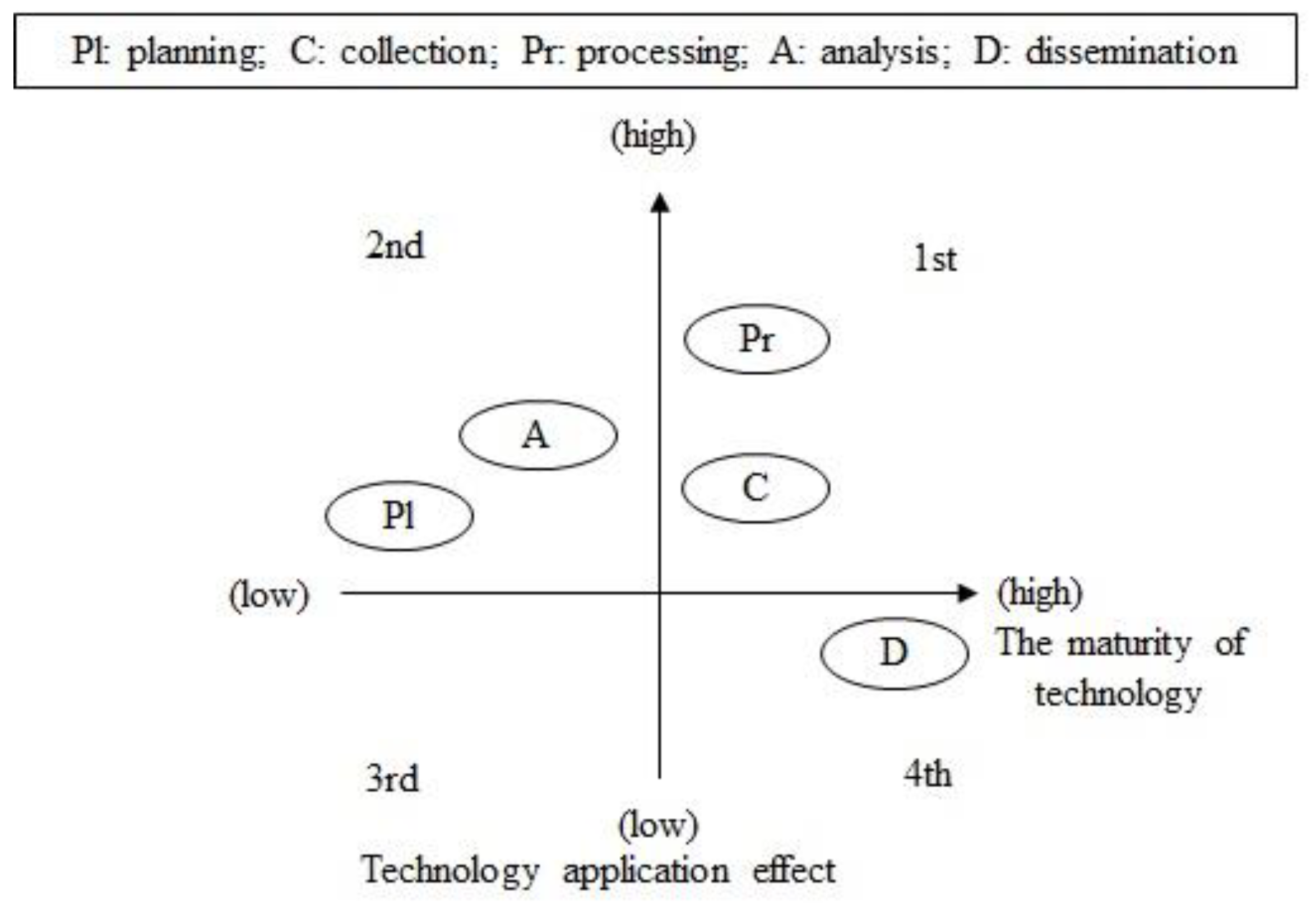
| Artificial Intelligence Technology | Maturity level of the AI Technology | Is there an AI algorithm to be applied? Is the technology maturity of the algorithm applicable? |
| Application Effect | Technology Application Effect | How effective is the application of the AI technology? (refer to Project Maven) |
| Level | Machine Readable Form | Characteristics | Example |
|---|---|---|---|
| 1 | Unsatisfied format | only specific software (SW) can read but cannot modify and convert | |
| 2 | Minimum satisfying format | only specific SW can read, modify, and convert | HWP, XLS, JPG, MPEG |
| 3 | Open format | all SW can read, modify, and convert | CSV, JSON, XML |
| 4 | data structure that describes data characteristic relationships based on URIs | RDF | |
| 5 | to be linked and shared with other data on the web | LOD |
| Stage | Work | Applicable Technology (Maturity) |
|---|---|---|
| Planning | Establish a collection plan while considering mission, sensors, and weather, among others | Machine Learning/Inference (3.5) |
| Collection | Identify the data to be processed Capture threat signs | Machine Learning/ Inference (3.5) Recognition intelligence (3.5) Application (2) |
| Processing | Process information such as imagery, signals, and open- source. | Machine Learning (3.5) Recognition intelligence (3.5) |
| Analysis | All-source intelligence analysis Threat signs/time-series target analysis | Machine Learning/Inference (3.5) Application (2) |
| Dissemination | Inquiry of the target information | Visualization (5) Pub/sub (5) Machine Learning/Inference (3.5) |
| Stage | Work | Applicable Technology (Maturity) | Technology Application Effect |
|---|---|---|---|
| Planning | Establish a collection plan while considering mission, sensors, and weather, among others | Machine Learning/Inference (3.5) | Sensor mgt./ optimization: 5× |
| Collection | Identify the data to be processed Capture threat signs | Machine Learning/Inference (3.5) Recognition intelligence (3.5) Application (2) | Optimization: 5× |
| Processing | Process information such as imagery, signals, and open- source. | Machine Learning (3.5) Recognition intelligence (3.5) | Computer vision/AI: 50× Voice-text conversion: 3× |
| Analysis | All-source intelligence analysis Threat signs/time-series target analysis | Machine Learning/Inference (3.5) Application (2) | Information fusion: 5× |
| Dissemination | Inquiry of the target information | Visualization (5) Pub/sub (5) Machine Learning/ Inference (3.5) | UI/UX: 2× Transfer data: 1× |
| Attribute | Requirement | Data | Technology Maturity | Technical Effect | Total | |
|---|---|---|---|---|---|---|
| Stage | ||||||
| Planning | 0 | 0 | 1.4 | 1 | 2.4 | |
| Collection | 1 | 0 | 0.8 | 1 | 3.8 | |
| Processing | 2 | 1.5 | 1.4 | 2 | 6.9 | |
| Analysis | 0 | 1 | 0.8 | 1 | 2.8 | |
| Dissemination | 2 | 1 | 0.8 | 1 | 4.8 | |
| Attribute | Requirement | Data | Technology Maturity/Effect | Technical Effect | Total | |
|---|---|---|---|---|---|---|
| Stage | ||||||
| Planning | 0 | 0 | 2.8 | 1 | 3.8 | |
| Collection | 1 | 0 | 1.6 | 2 | 4.6 | |
| Processing | 2 | 4.5 | 2.8 | 2 | 11.3 | |
| Analysis | 0 | 3 | 1.6 | 1 | 5.6 | |
| Dissemination | 2 | 3 | 1.6 | 1 | 7.6 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cho, S.; Shin, W.; Kim, N.; Jeong, J.; In, H.P. Priority Determination to Apply Artificial Intelligence Technology in Military Intelligence Areas. Electronics 2020, 9, 2187. https://doi.org/10.3390/electronics9122187
Cho S, Shin W, Kim N, Jeong J, In HP. Priority Determination to Apply Artificial Intelligence Technology in Military Intelligence Areas. Electronics. 2020; 9(12):2187. https://doi.org/10.3390/electronics9122187
Chicago/Turabian StyleCho, Sungrim, Woochang Shin, Neunghoe Kim, Jongwook Jeong, and Hoh Peter In. 2020. "Priority Determination to Apply Artificial Intelligence Technology in Military Intelligence Areas" Electronics 9, no. 12: 2187. https://doi.org/10.3390/electronics9122187
APA StyleCho, S., Shin, W., Kim, N., Jeong, J., & In, H. P. (2020). Priority Determination to Apply Artificial Intelligence Technology in Military Intelligence Areas. Electronics, 9(12), 2187. https://doi.org/10.3390/electronics9122187






