Max-Min Fairness and Sum Throughput Maximization for In-Band Full-Duplex IoT Networks: User Grouping, Bandwidth and Power Allocation
Abstract
1. Introduction
1.1. Related Works
1.2. Main Contributions
- Aiming at max-min throughput fairness, we propose a new user grouping method to divide all users into two groups, which are served in different frequency bands. The proposed method helps not only to mitigate network interference, but also to better exploit the spatial degrees-of-freedom (DoF), because the number of users served at the same time is significantly reduced. In order to reduce the complexity that is caused by the downlink beamforming, which has been widely done by the previous works, we develop a ZF beamforming that requires solving the problem of scalar variables, instead of vectors.
- In order to solve the nonconvex problem, we resort to the inner approximation (IA) framework [26,27] to approximate the nonconvex parts. We then develop an iterative algorithm for its solution, which requires solving a simple convex program at each iteration. The convex problem can be cast to a conic quadratic program, which can be efficiently solved by standard convex solvers. The computational complexity is also provided and discussed.
- In addition, we also formulate the sum throughput (ST) maximization problem, which has been advocated as the key performance metric for the next generation of wireless networks. To solve this problem, we develop newly approximate functions to tackle nonconvex parts and adopt the proposed iterative algorithm (for solving the max-min throughput fairness problem) for its solution.
- Extensive numerical results are presented in order to demonstrate the effectiveness of the proposed method in terms of convergence speed, throughput fairness, and sum throughput. The performance improvement of the proposed scheme over state-of-the-art approaches, i.e., half-duplex and conventional IBFD (without user grouping) schemes.
1.3. Paper Organization and Notation
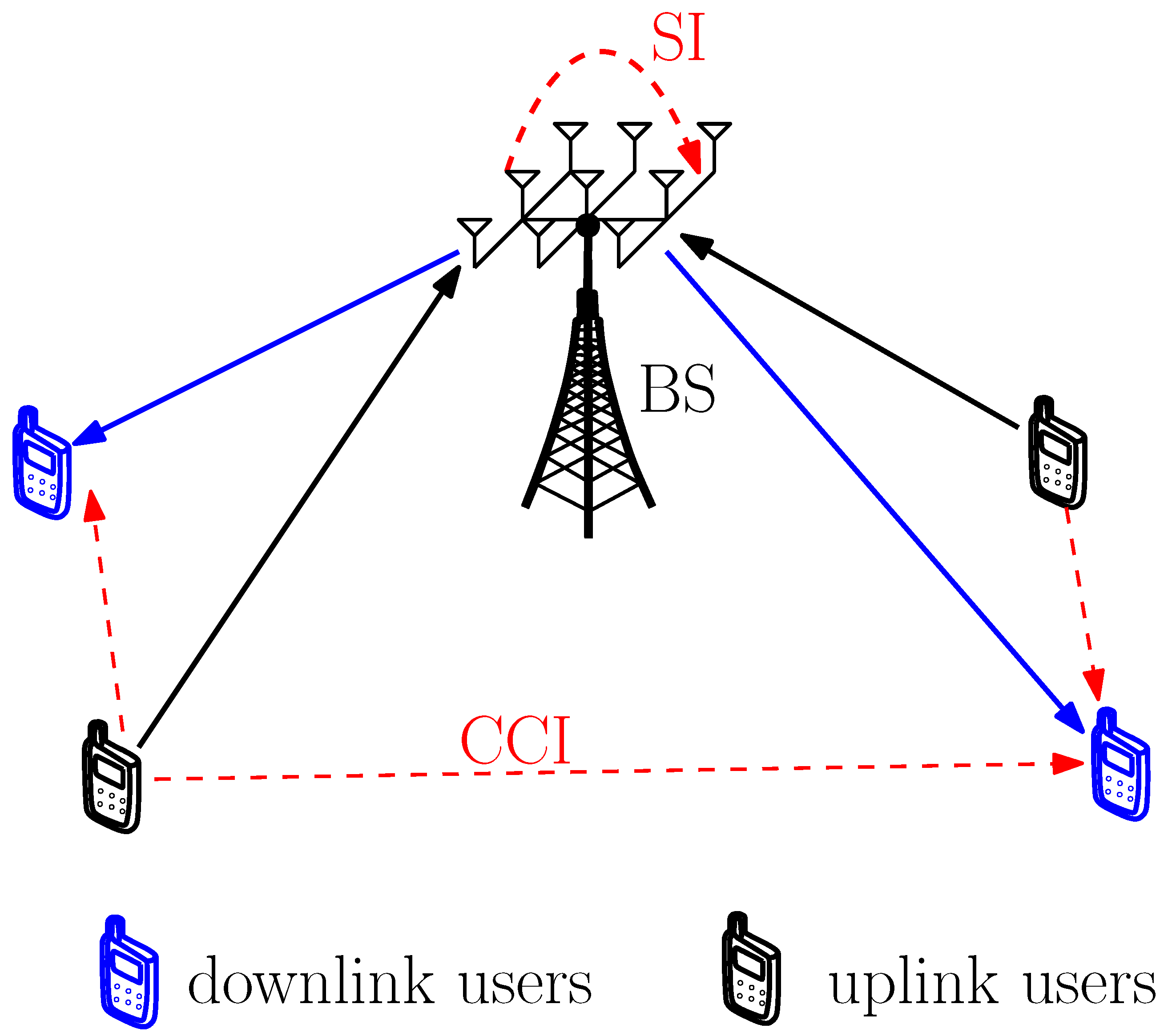
2. System Model and Problem Formulation
2.1. Channel Model
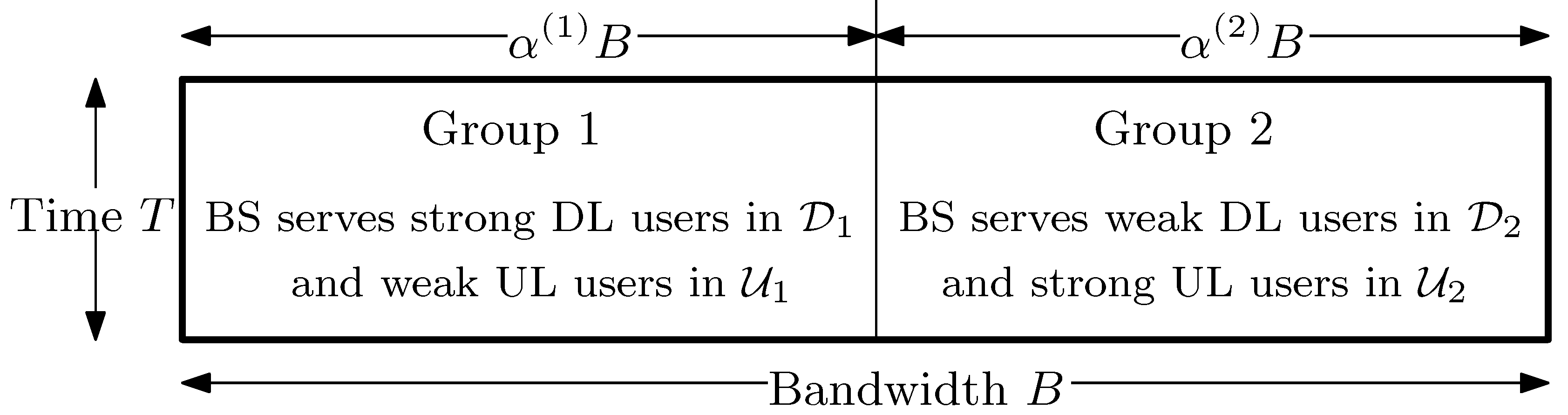
2.2. User Grouping Method
2.3. Beamforming Design
2.4. Optimization Problem Formulation
3. Proposed Algorithm for Max-Min Throughput Fairness
| Algorithm 1 Proposed Iterative Algorithm for Solving Max-Min Throughput Fairness Problem (13) |
| 1: Initialization: Set , , , and generate a random initial point , satisfying constraints in (20b). |
| 2: repeat |
| 3: Find the optimal solution by solving the following convex program: |
| s. t. (20b)–(20j) |
| 4: Update := and . |
| 5: Set . |
| 6: until. |
| 7: Output: The final solution := and the max-min throughput . |
4. Proposed Algorithm for Sum Throughput Maximization
| Algorithm 2 Proposed Iterative Algorithm for Solving Sum Throughput Maximization Problem (26) |
| 1: Initialization: Set , , , and generate a random initial point , satisfying constraints (29b)–(29j). |
| 2: repeat |
| 3: Find the optimal solution by solving the convex program (29) (or (30)) |
| 4: Update := and . |
| 5: Set . |
| 6: until . |
| 7: Output: The final solution := and the max-min throughput . |
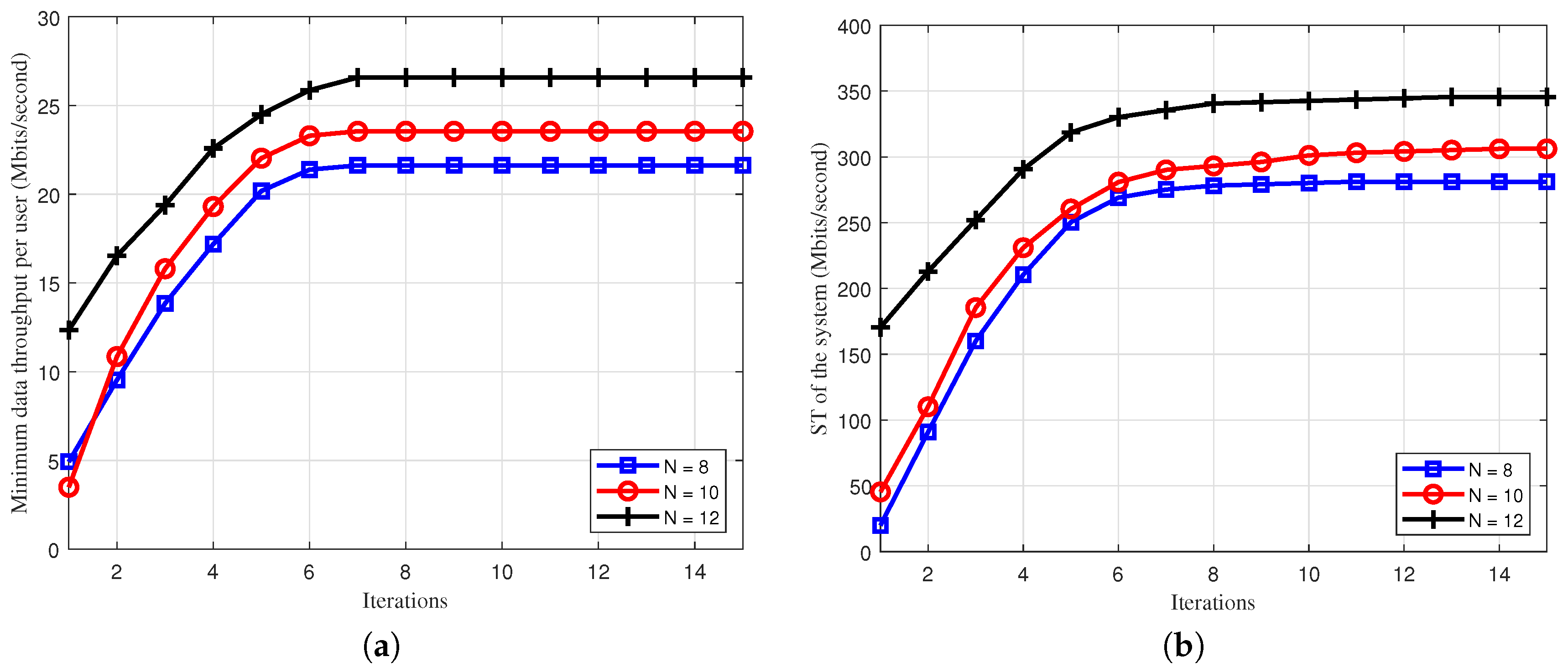
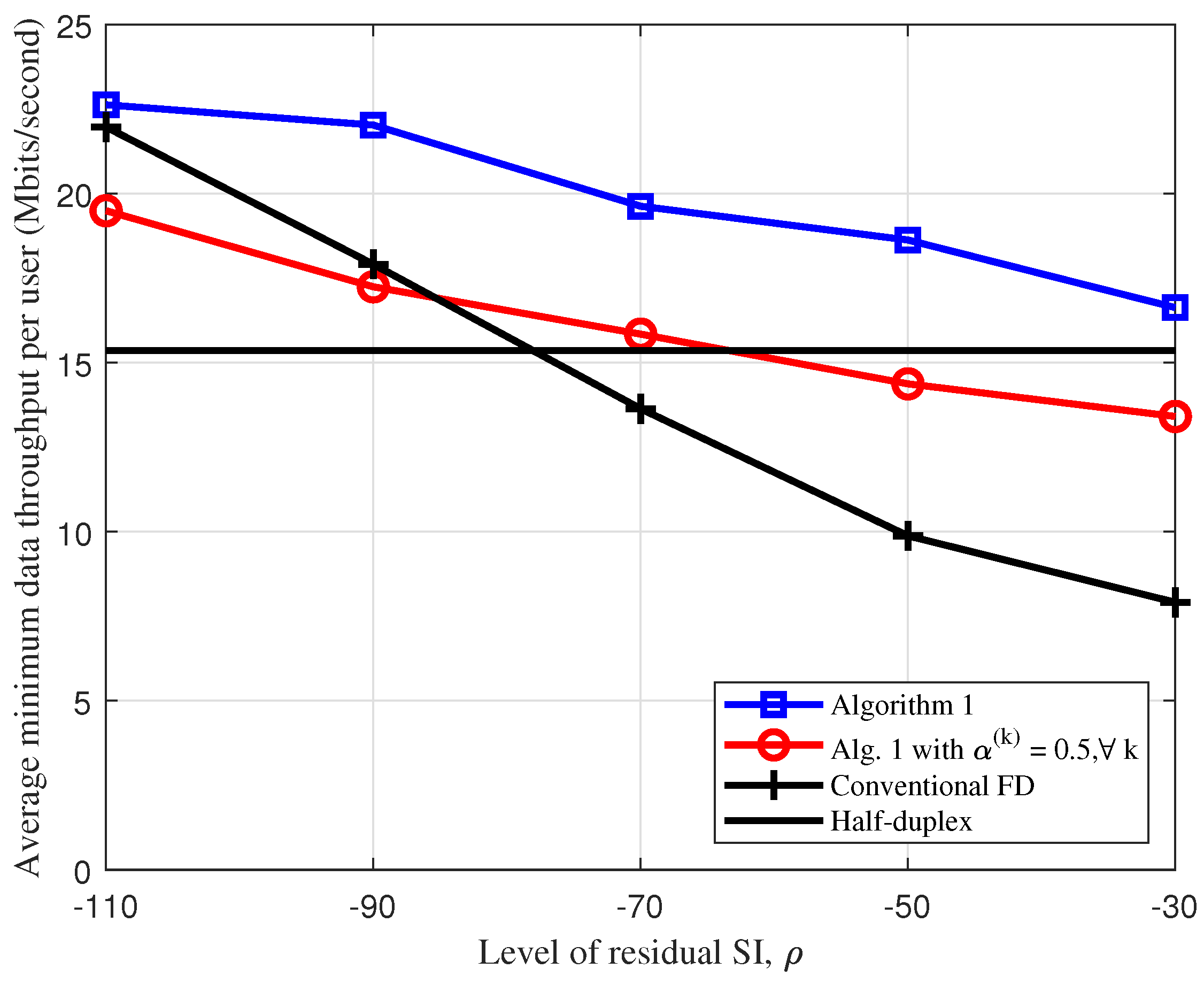
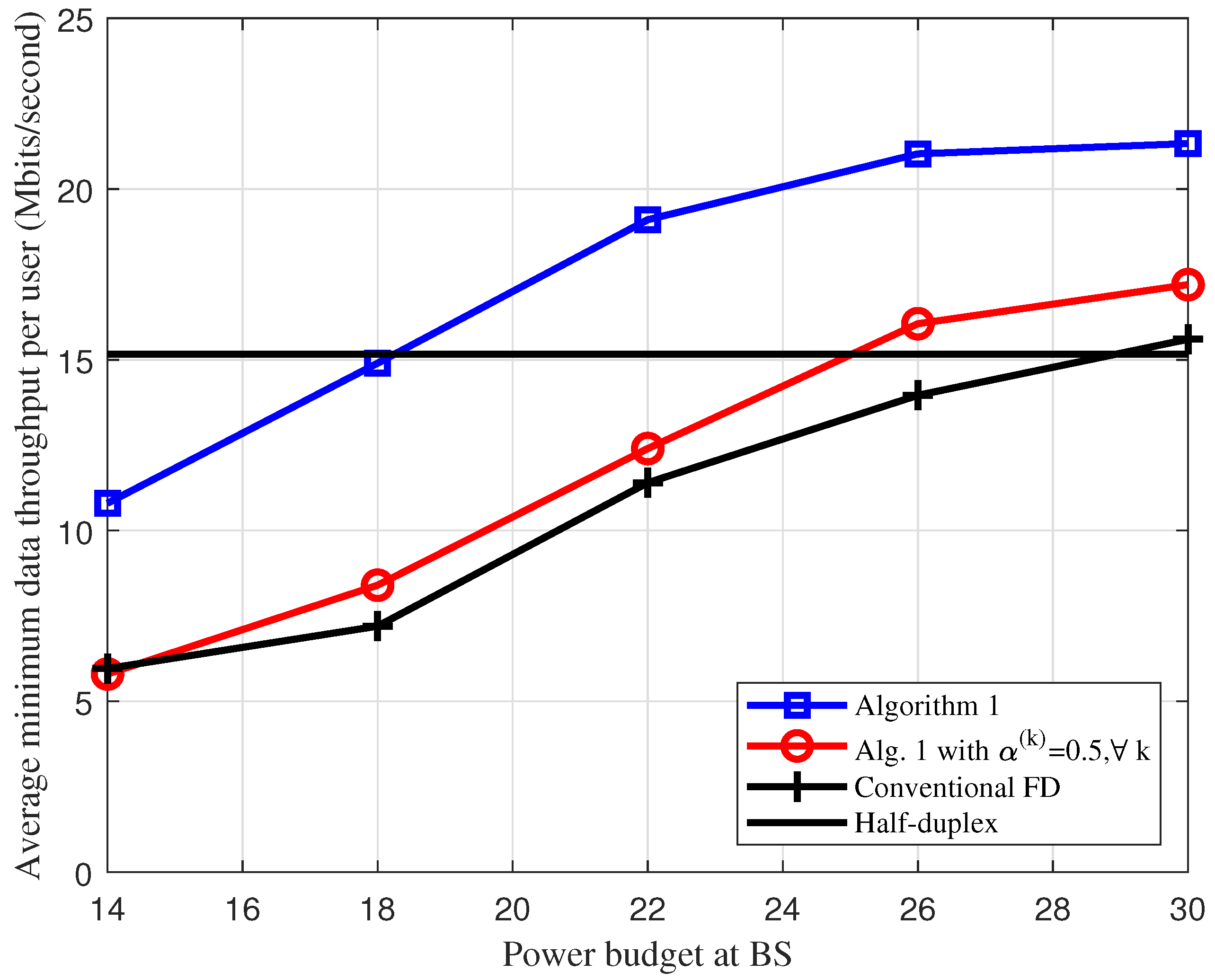
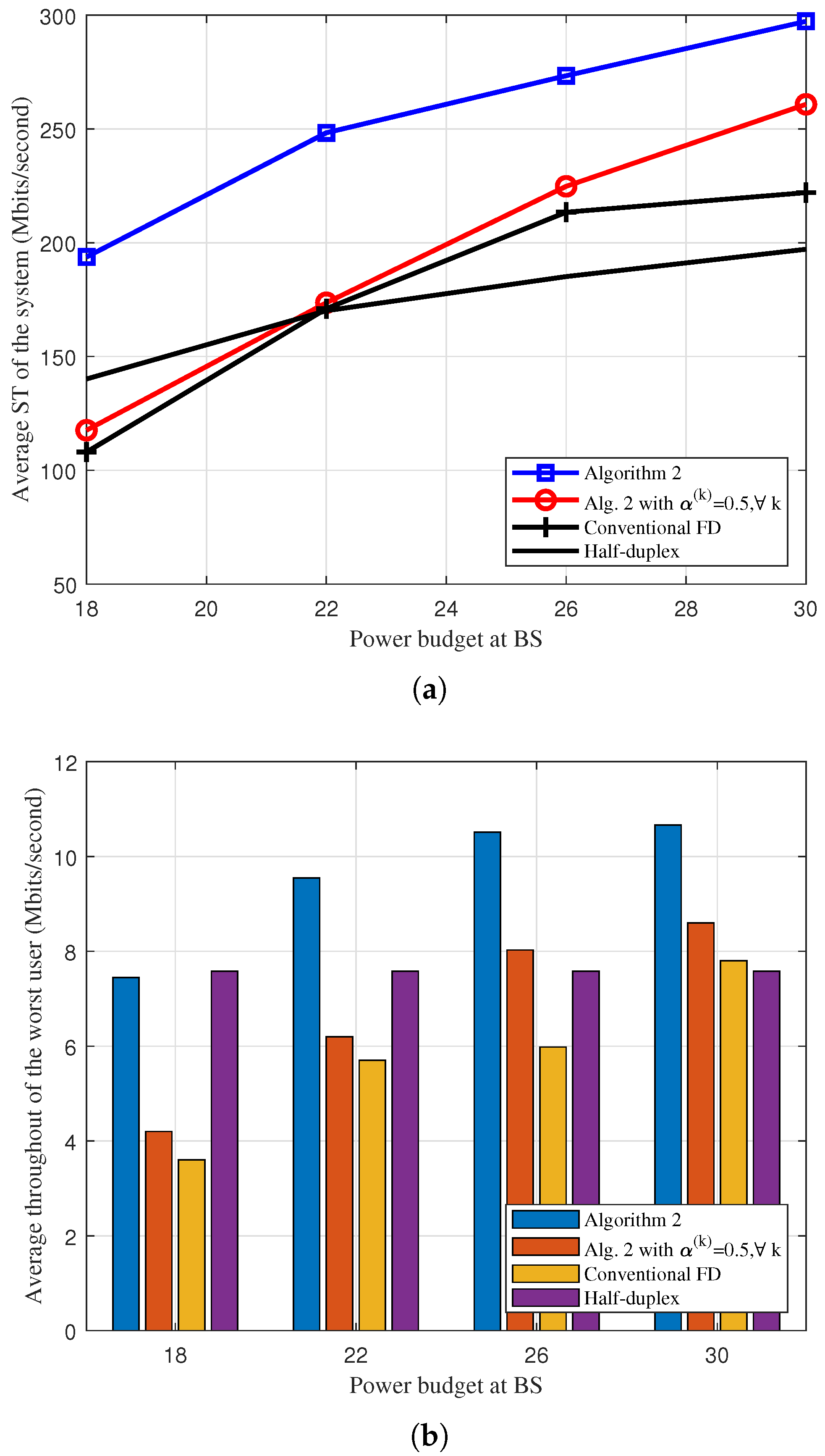
5. Numerical Results and Discussions
- “Conventional FD:” in this scheme, all downlink and uplink users are served in the same time-frequency resource (without user grouping) [15]).
- “Algorithm 1 or 2 with :” The solution of this scheme can be easily obtained with a slight modification of Algorithms 1 and 2, where the total bandwidth is divided equally for two groups.
- “Half-duplex:” BS servers all downlink and uplink users in the same frequency resource, but in two separate time blocks. The effective max-min throughput or sum throughput will be divided by two.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| IBFD | In-band full-duplex |
| HD | Half-duplex |
| IA | Inner approximation |
| BS | Base station |
| SI | Self-interference |
| CCI | Co-channel interference |
| CSI | Channel state information |
| 5G | Fifth-generation wireless network |
| IoT | Internet of Things |
| SEM | Spectral efficiency maximization |
| ST | Sum throughput |
| DoF | Degrees-of-freedom |
| ZF | Zero-forcing |
| NOMA | Non-orthogonal multiple access |
| DL | Downlink |
| UL | Uplink |
Appendix A. Proof of Lemma 1
References
- Cisco Annual Internet Report (2018–2023) White Paper. 2020. Available online: https://www.cisco.com/c/en/us/solutions/collateral/executive--perspectives/annual--internet--report/white--paper--c11--741490.html (accessed on 9 March 2020).
- Ma, Z.; Xiao, M.; Xiao, Y.; Pang, Z.; Poor, H.V.; Vucetic, B. High-Reliability and Low-Latency Wireless Communication for Internet of Things: Challenges, Fundamentals, and Enabling Technologies. IEEE Internet Things J. 2019, 6, 7946–7970. [Google Scholar] [CrossRef]
- Ghahramani, M.; Qiao, Y.; Zhou, M.C.; O’Hagan, A.; Sweeney, J. AI-based modeling and data-driven evaluation for smart manufacturing processes. IEEE/CAA J. Autom. Sin. 2020, 7, 1026–1037. [Google Scholar] [CrossRef]
- Ericsson Mobility Report; Ericsson AB: Stockholm, Sweden, 2018. Available online: https://goo.gl/bSxgss (accessed on 16 November 2018).
- Andrews, J.; Buzzi, S.; Choi, W.; Hanly, S.; Lozano, A.; Soong, A.; Zhang, J. What Will 5G Be? IEEE J. Select. Area Commun. 2014, 32, 1065–1082. [Google Scholar] [CrossRef]
- Zhang, Z.; Long, K.; Vasilakos, A.V.; Hanzo, L. Full-Duplex Wireless Communications: Challenges, Solutions, and Future Research Directions. Proc. IEEE 2016, 104, 1369–1409. [Google Scholar] [CrossRef]
- Bazzi, A.; Masini, B.M.; Zanella, A. Performance Analysis of V2V Beaconing Using LTE in Direct Mode With Full Duplex Radios. IEEE Wirel. Commun. Lett. 2015, 4, 685–688. [Google Scholar] [CrossRef]
- Mahmood, N.H.; Sarret, M.G.; Berardinelli, G.; Mogensen, P. Full duplex communications in 5G small cells. In Proceedings of the 2017 13th International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, 26–30 June 2017; pp. 1665–1670. [Google Scholar] [CrossRef]
- Zhang, Z.; Chai, X.; Long, K.; Vasilakos, A.V.; Hanzo, L. Full duplex techniques for 5G networks: Self-interference cancellation, protocol design, and relay selection. IEEE Commun. Mag. 2015, 53, 128–137. [Google Scholar] [CrossRef]
- Bharadia, D.; McMilin, E.; Katti, S. Full duplex radios. Proc. ACM SIGCOMM Comput. Commun. Rev. 2013, 43, 375–386. [Google Scholar] [CrossRef]
- Riihonen, T.; Werner, S.; Wichman, R. Mitigation of loopback self-interference in full-duplex MIMO relays. IEEE Trans. Signal Process. 2011, 59, 5983–5993. [Google Scholar] [CrossRef]
- System Scenarios and Technical Requirements for Full-Duplex Concept. DUPLO Project, Deliverable D1.1. Available online: https://cordis.europa.eu/docs/projects/cnect/9/316369/080/deliverables/001-D11v10.pdf (accessed on 16 November 2018).
- Duarte, M.; Dick, C.; Sabharwal, A. Experiment-driven characterization of full-duplex wireless systems. IEEE Trans. Wirel. Commun. 2012, 11, 4296–4307. [Google Scholar] [CrossRef]
- Sabharwal, A.; Schniter, P.; Guo, D.; Bliss, D.W.; Rangarajan, S.; Wichman, R. In-band full-duplex wireless: Challenges and opportunities. IEEE J. Select. Areas Commun. 2014, 32, 1637–1652. [Google Scholar] [CrossRef]
- Nguyen, D.; Tran, L.N.; Pirinen, P.; Latva-aho, M. On the spectral efficiency of full-duplex small cell wireless systems. IEEE Trans. Wirel. Commun. 2014, 13, 4896–4910. [Google Scholar] [CrossRef]
- Huberman, S.; Le-Ngoc, T. MIMO Full-Duplex Precoding: A Joint Beamforming and Self-Interference Cancellation Structure. IEEE Trans. Wirel. Commun. 2015, 14, 2205–2217. [Google Scholar] [CrossRef]
- Nguyen, V.D.; Nguyen, H.V.; Nguyen, C.T.; Shin, O.S. Spectral Efficiency of Full-Duplex Multi-user System: Beamforming Design, User Grouping, and Time Allocation. IEEE Access 2017, 5, 5785–5797. [Google Scholar] [CrossRef]
- Tam, H.H.M.; Tuan, H.D.; Ngo, D.T. Successive Convex Quadratic Programming for Quality-of-Service Management in Full-Duplex MU-MIMO Multicell Networks. IEEE Trans. Commun. 2016, 64, 2340–2353. [Google Scholar] [CrossRef]
- Nguyen, H.V.; Nguyen, V.D.; Dobre, O.A.; Wu, Y.; Shin, O.S. Joint antenna array mode selection and user assignment for full-duplex MU-MISO systems. IEEE Trans. Wirel. Commun. 2019, 18, 2946–2963. [Google Scholar] [CrossRef]
- Chalise, B.K.; Suraweera, H.A.; Zheng, G.; Karagiannidis, G.K. Beamforming Optimization for Full-Duplex Wireless-Powered MIMO Systems. IEEE Trans. Commun. 2017, 65, 3750–3764. [Google Scholar] [CrossRef]
- Nguyen, V.D.; Duong, T.Q.; Tuan, H.D.; Shin, O.S.; Poor, H.V. Spectral and Energy Efficiencies in Full-Duplex Wireless Information and Power Transfer. IEEE Trans. Commun. 2017, 65, 2220–2233. [Google Scholar] [CrossRef]
- Aquilina, P.; Cirik, A.C.; Ratnarajah, T. Weighted Sum Rate Maximization in Full-Duplex Multi-User Multi-Cell MIMO Networks. IEEE Trans. Commun. 2017, 65, 1590–1608. [Google Scholar] [CrossRef]
- Nguyen, H.V.; Nguyen, V.D.; Dobre, O.A.; Nguyen, D.N.; Dutkiewicz, E.; Shin, O.S. Joint Power Control and User Association for NOMA-Based Full-Duplex Systems. IEEE Trans. Commun. 2019, 67, 8037–8055. [Google Scholar] [CrossRef]
- Nguyen, V.D.; Nguyen, H.V.; Dobre, O.A.; Shin, O.S. A New Design Paradigm for Secure Full-Duplex Multiuser Systems. IEEE J. Select. Areas Commun. 2018, 36, 1480–1498. [Google Scholar] [CrossRef]
- Zabini, F.; Bazzi, A.; Masini, B.M.; Verdone, R. Optimal Performance Versus Fairness Tradeoff for Resource Allocation in Wireless Systems. IEEE Trans. Wirel. Commun. 2017, 16, 2587–2600. [Google Scholar] [CrossRef]
- Marks, B.R.; Wright, G.P. A general inner approximation algorithm for nonconvex mathematical programs. Oper. Res. 1978, 26, 681–683. [Google Scholar] [CrossRef]
- Beck, A.; Ben-Tal, A.; Tetruashvili, L. A sequential parametric convex approximation method with applications to nonconvex truss topology design problems. J. Glob. Optim. 2010, 47, 29–51. [Google Scholar] [CrossRef]
- Peaucelle, D.; Henrion, D.; Labit, Y. Users Guide for SeDuMi Interface 1.03; LAAS-CNRS: Toulouse, France, 2002. [Google Scholar]
- I. MOSEK ApS. 2014. Available online: http://www.mosek.com (accessed on 16 November 2018).
| Simulation Parameter | Value |
|---|---|
| System bandwidth | 10 MHz |
| Noise power spectral density at BS and uplink users | = −174 dBm/Hz |
| Path loss between BS and users | 103.8 + 20.9 dB |
| Path loss between a uplink user and a downlink user | 145.4 + 37.5 dB |
| Power budget at BS | = 26 dBm |
| Power budget at uplink users | =23 dBm, |
| Level of residual SI, | −75 dB |
| Number of antennas at BS | 8 |
| Number of downlink users | 6 |
| Number of uplink users | 6 |
| Predetermined throughput threshold | = 1 bits/s |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khanh, N.T.V.; Nguyen, V.D. Max-Min Fairness and Sum Throughput Maximization for In-Band Full-Duplex IoT Networks: User Grouping, Bandwidth and Power Allocation. Electronics 2020, 9, 2182. https://doi.org/10.3390/electronics9122182
Khanh NTV, Nguyen VD. Max-Min Fairness and Sum Throughput Maximization for In-Band Full-Duplex IoT Networks: User Grouping, Bandwidth and Power Allocation. Electronics. 2020; 9(12):2182. https://doi.org/10.3390/electronics9122182
Chicago/Turabian StyleKhanh, Ngo Tan Vu, and Van Dinh Nguyen. 2020. "Max-Min Fairness and Sum Throughput Maximization for In-Band Full-Duplex IoT Networks: User Grouping, Bandwidth and Power Allocation" Electronics 9, no. 12: 2182. https://doi.org/10.3390/electronics9122182
APA StyleKhanh, N. T. V., & Nguyen, V. D. (2020). Max-Min Fairness and Sum Throughput Maximization for In-Band Full-Duplex IoT Networks: User Grouping, Bandwidth and Power Allocation. Electronics, 9(12), 2182. https://doi.org/10.3390/electronics9122182





