An Adaptive Delay-Tolerant Routing Algorithm for Data Transmission in Opportunistic Social Networks
Abstract
1. Introduction
- To analyze the fuzzy uncertain impact of the remaining energy and cache on data transmission, CMFI has been proposed. As an adaptive and extensible method for energy and cache, CMFI optimizes the selections of the next hop from neighbors via three fuzzy components.
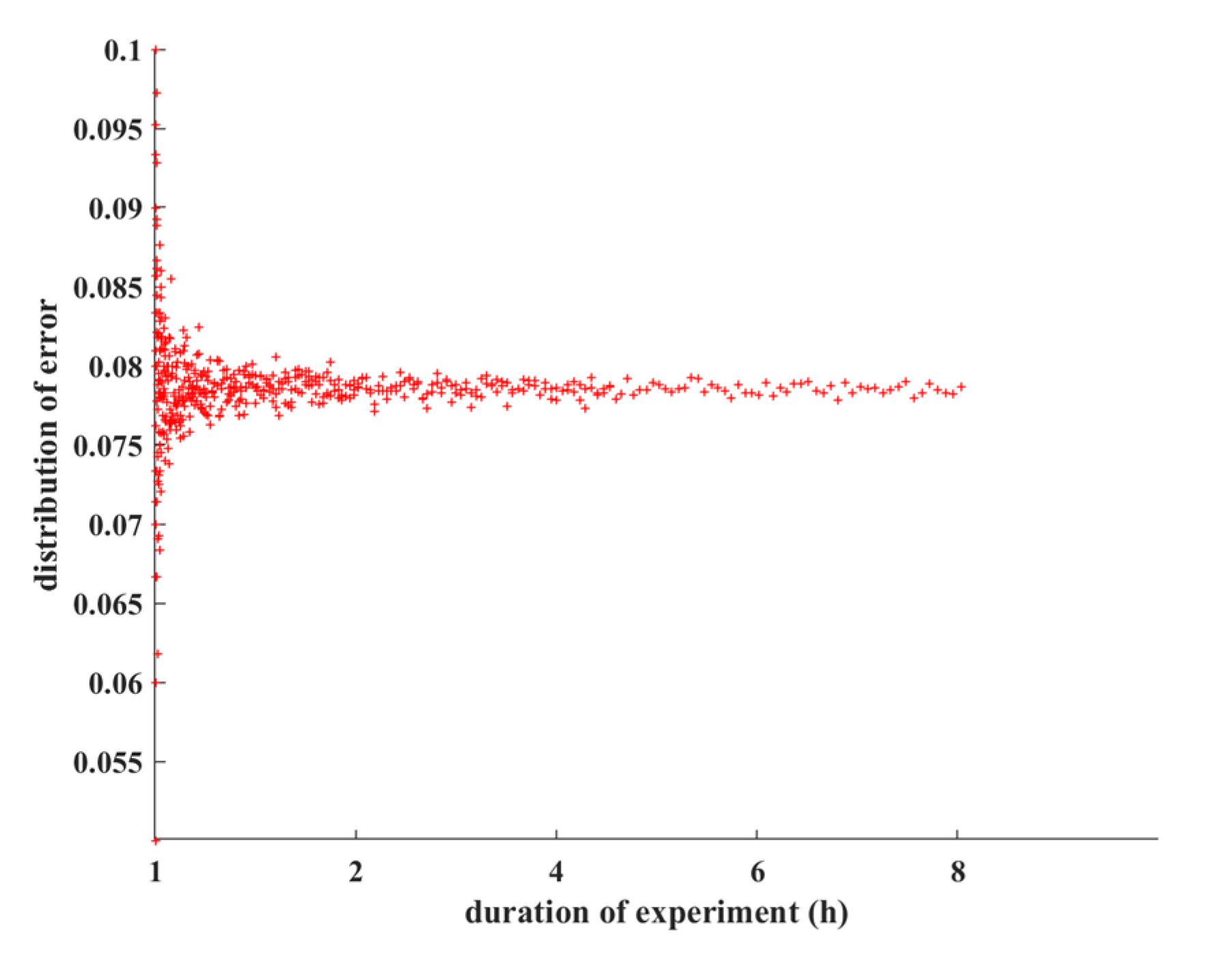
- Our experimental results show that within an error interval of 0.05~0.1, DTCM improves delivery ratio by about 20% and decreases end-to-end delay by approximate 25% as compared with Epidemic, and the network overhead from DTCM is in the middle horizon.
2. Related Works
2.1. The State of the Art of the Routing Algorithm Based on Cache
2.2. The State of the Art of the Routing Algorithm Based on Energy
3. System Model Design
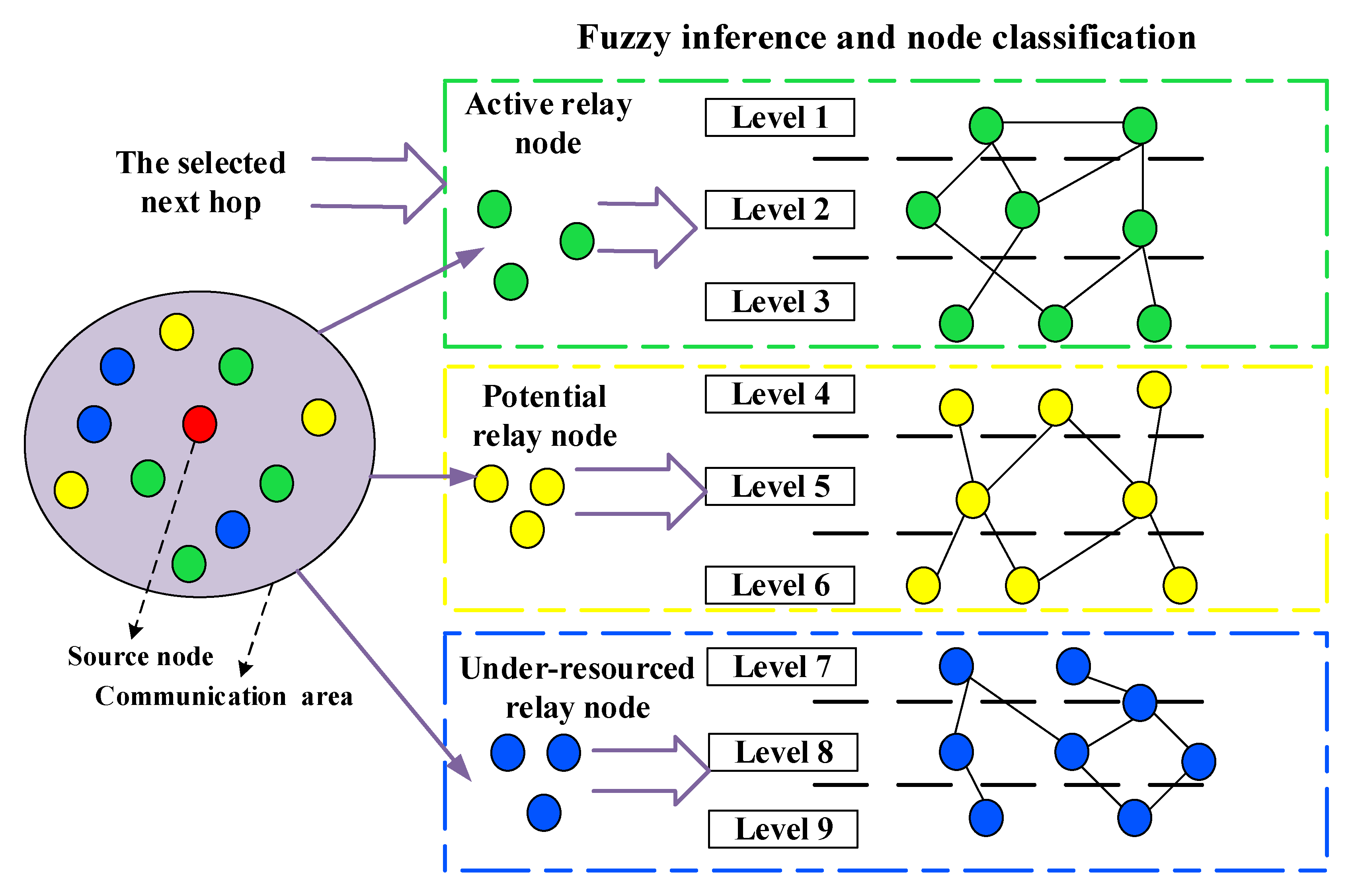
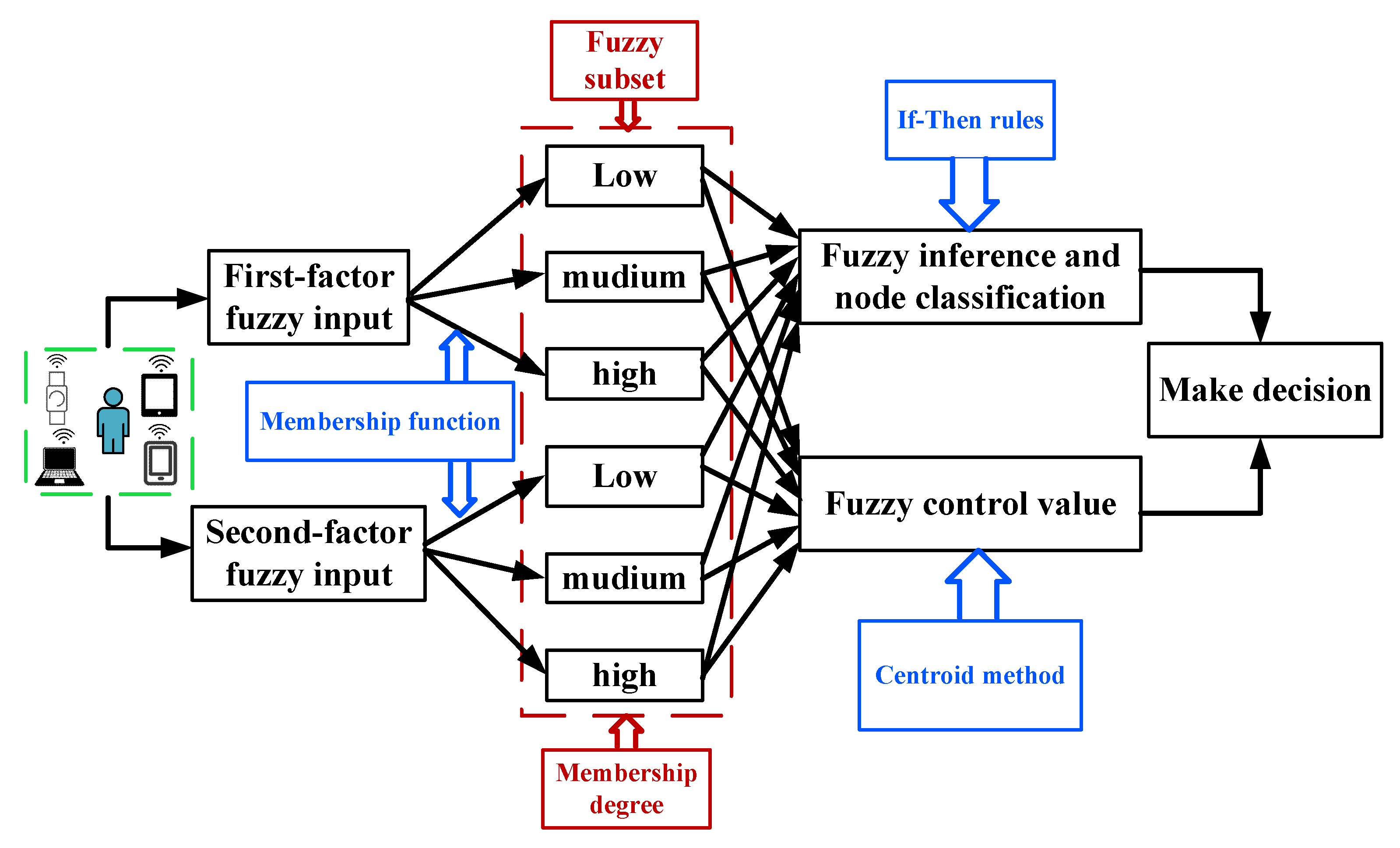
3.1. The Frame of Adaptive Curve-Trapezoid Mamdani Fuzzy Inference and Decision-Making System
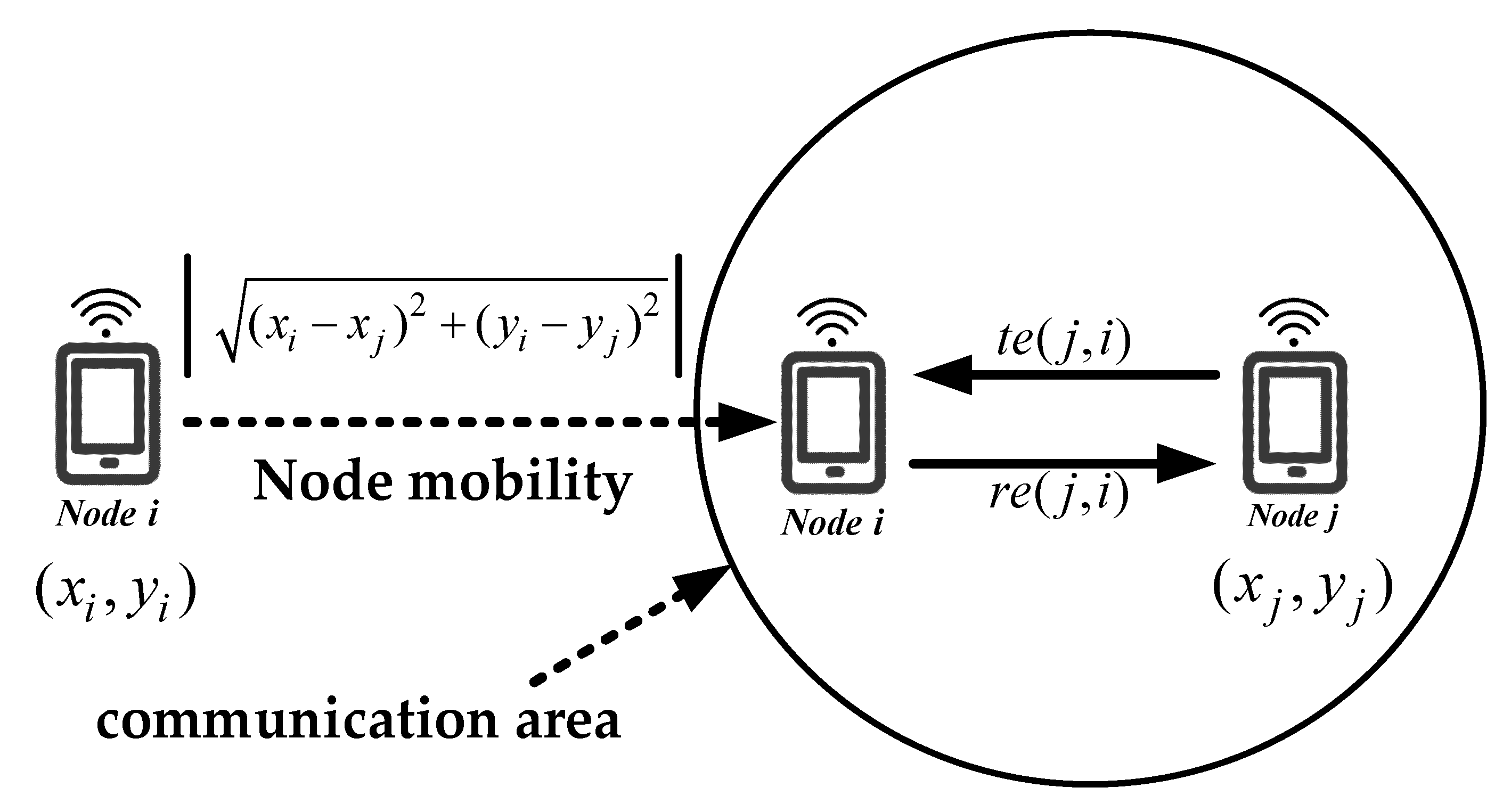
3.2. The First-Factor Fuzzy Input: Computation of the Remiaing Energy Level
3.3. The Second-Factor Fuzzy Input: Computation of the Remiaing Cache Level
3.4. Computation of Transmission Evaluation Value Based on CMFI
3.4.1. The Fuzzy Component
3.4.2. The Fuzzy Inference Component
3.4.3. The De-Blurring Component
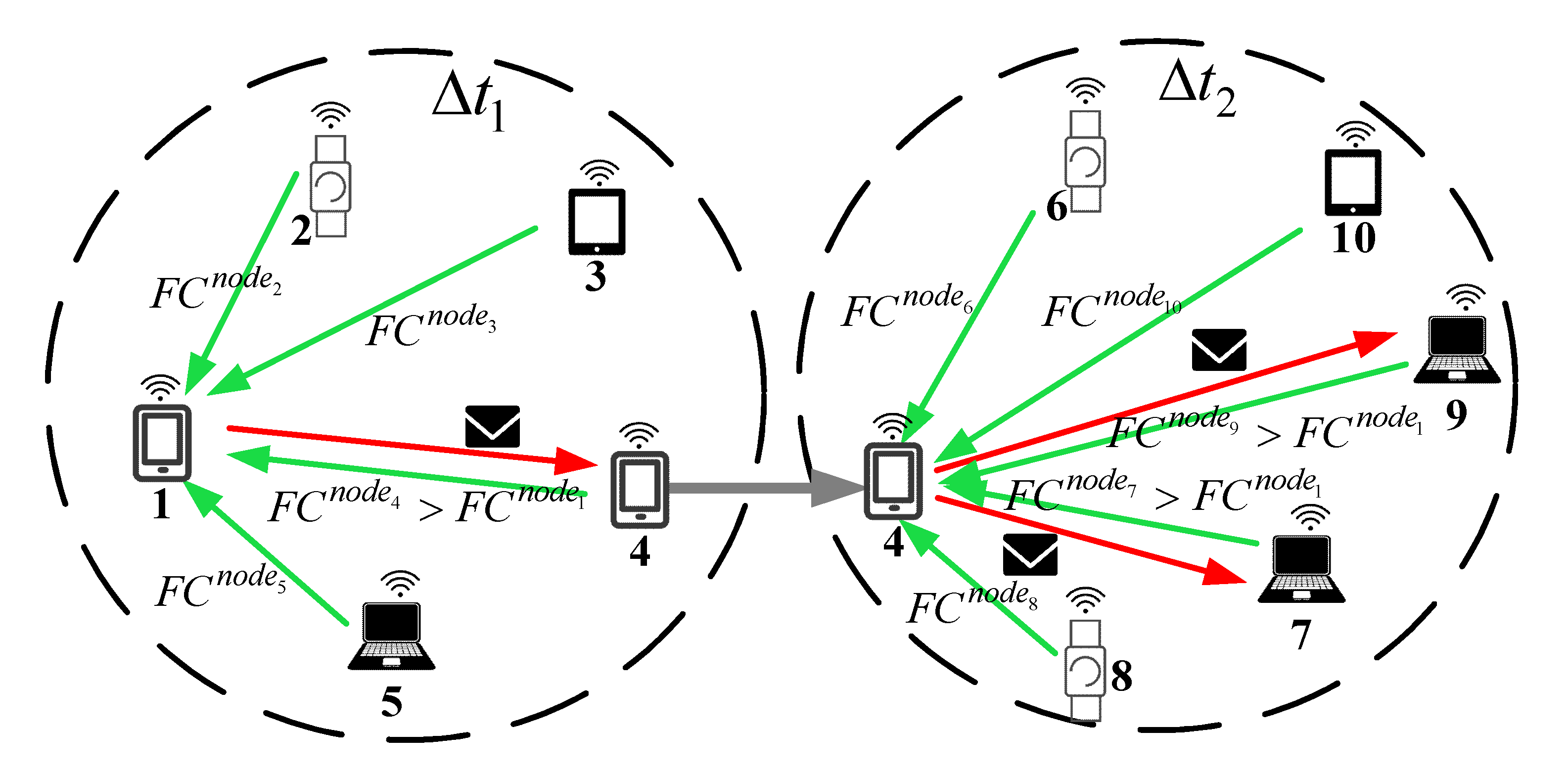
3.5. Data Routing Based on Two-Hop Feedback Mechanism
3.6. Algorithm Complexity Analysis
| Algorithm 1. Data routing and forwarding in a delay-tolerant routing (DTCM) algorithm based on the (curve-trapezoid Mamdani fuzzy inference) CMFI system. |
| Input: the source , neighbor nodes , and the destination |
| Output: |
| 1 Begin |
| 2 For (int i = 1; i ≤ n; i++) do |
| 3 collects state queue information from ; |
| 4 collects state queue information from ; |
| 5 End for |
| 6 For (int i = 1; i ≤ n; i++) do |
| 7 computing their own two-factor fuzzy input and ; |
| 8 determining the fuzzy evaluation subset and membership degree ; |
| 9 assessing the transmission evaluation value ; |
| 10 output ; |
| 11 End for |
| 12 If () then |
| 13 If () then |
| 14 the source forwards messages to its neighbor ; |
| 15 the relay node transmits messages to its neighbor ; |
| 16 End if |
| 17 End if |
| 18 End |
4. Simulation
4.1. Simulation Setup
4.1.1. Introduction of Benchmark and the Compared Protocols
4.1.2. Experimental Parameter Setting
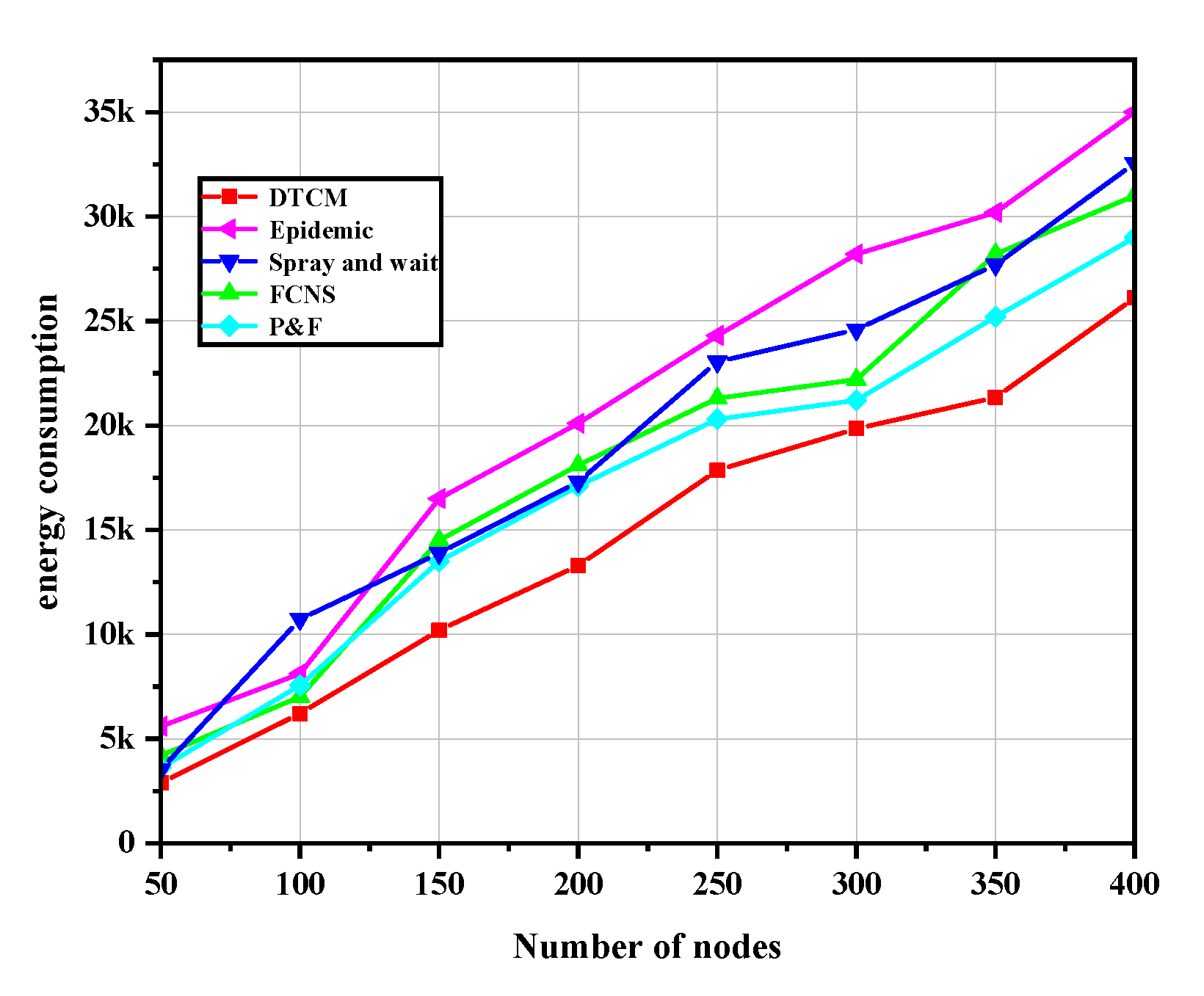
- Energy consumption: this parameter represents the total energy consumption from the network, including node mobility, data transmission, task processing, etc.
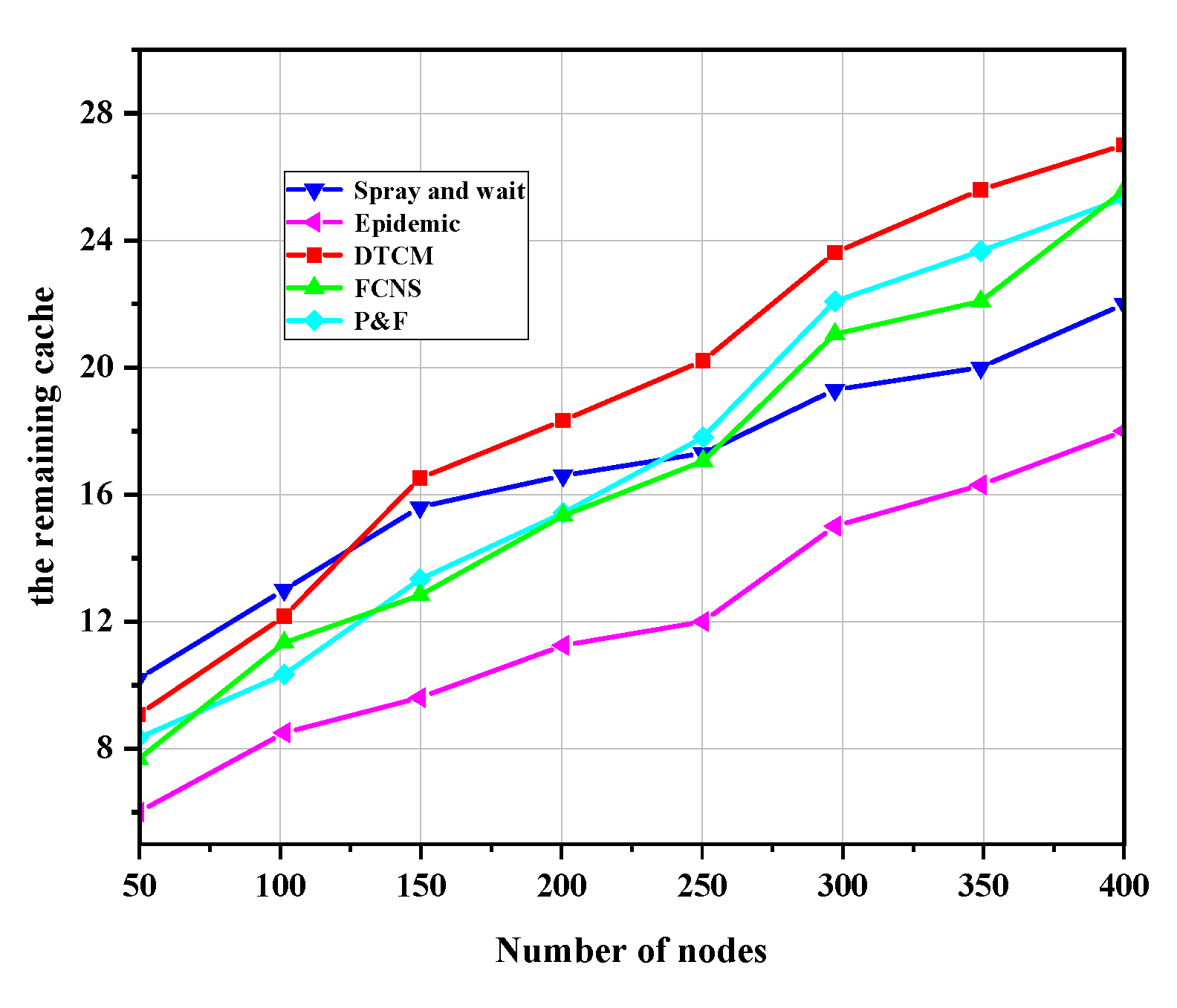
- The remaining cache: this parameter indicates that the size of the remaining cache space of a node after it stores enough data grouping.
- Delivery ratio: this indicator represents the ratio of the number of data packages accepted by destination to the total number of packages sent from message carriers. This indicator is calculated by DR = PA/PS, in which PA is the number of messages from all successful data transmission and PS is the number of messages sent from all mobile nodes.
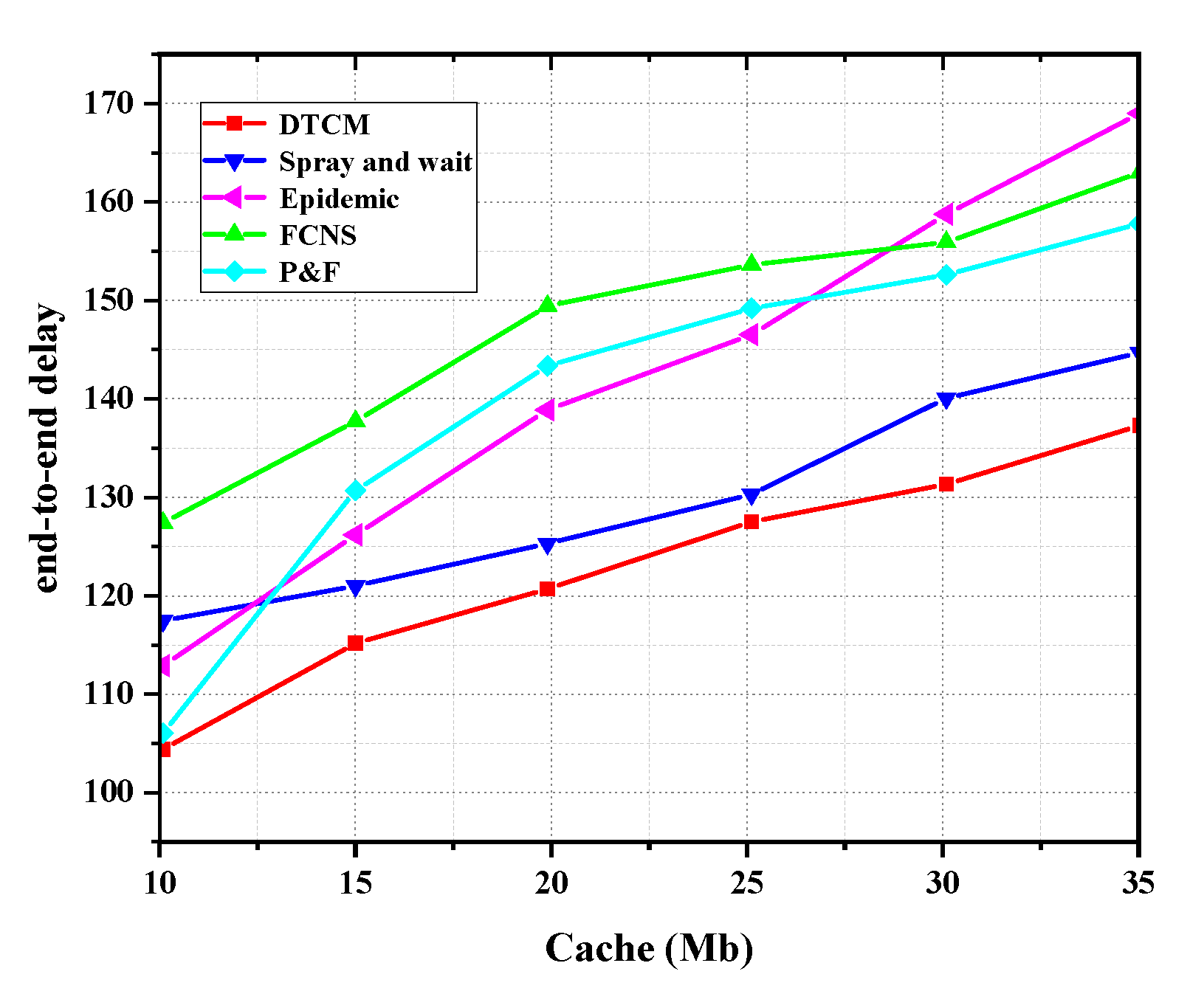
- Average end-to-end delay: this definition includes the delay from data routing, node waiting, and data transmission in a successful data transmission between a pair of mobile nodes. It is formalized as AD = TD/m, in which TD represents the total network delay and m is the number of data deliveries.
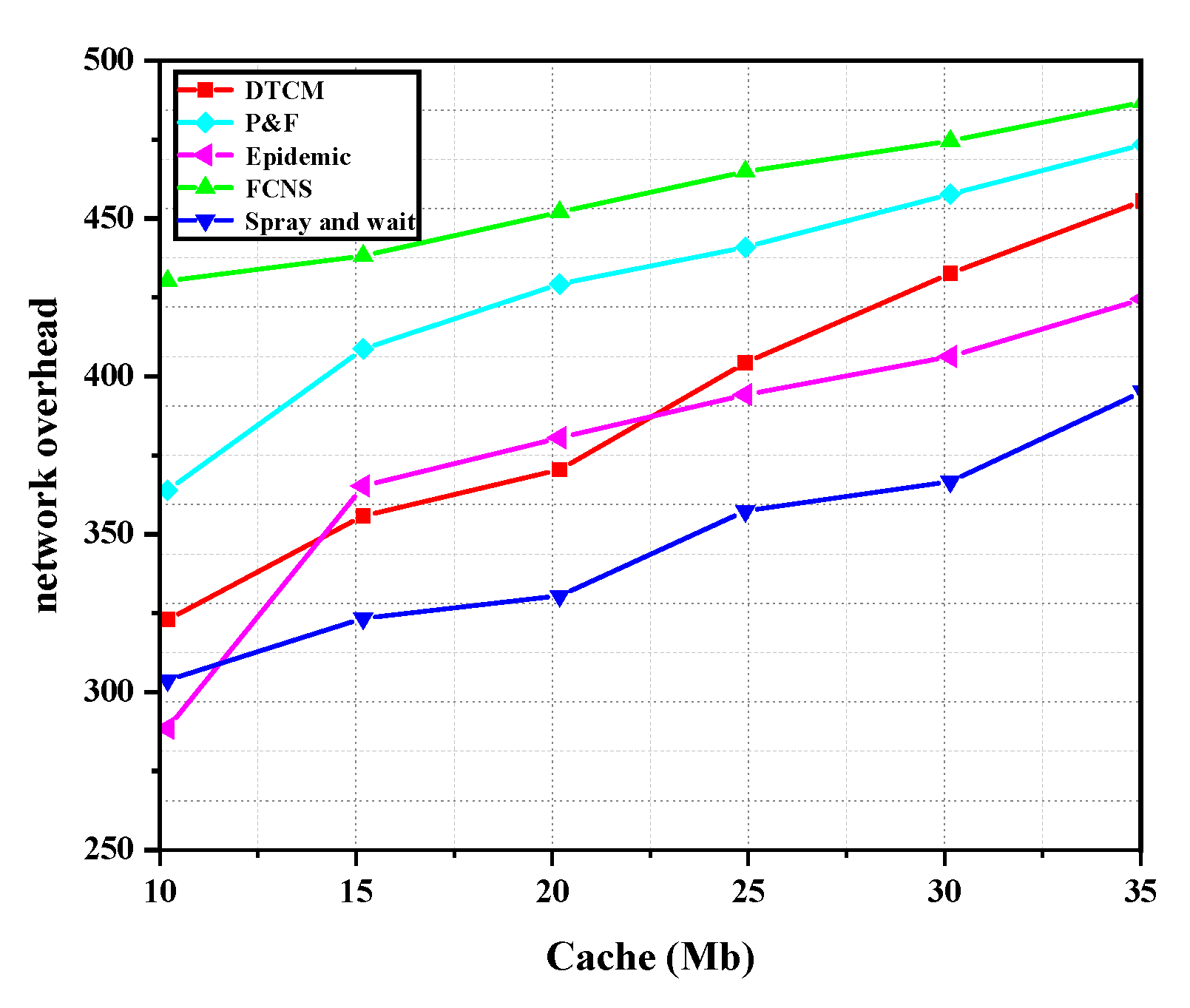
- Network overhead: this indicator denotes the total network overhead from the whole data transmission process among all nodes in the communication area, in which routing and forwarding delay, energy consumption, and memory usage are included.
4.2. Analysis of Experimental Results
4.2.1. Algorithm Performance Comparison between Five Routing Algorithms
4.2.2. Performance Comparison between the Five Algorithms
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
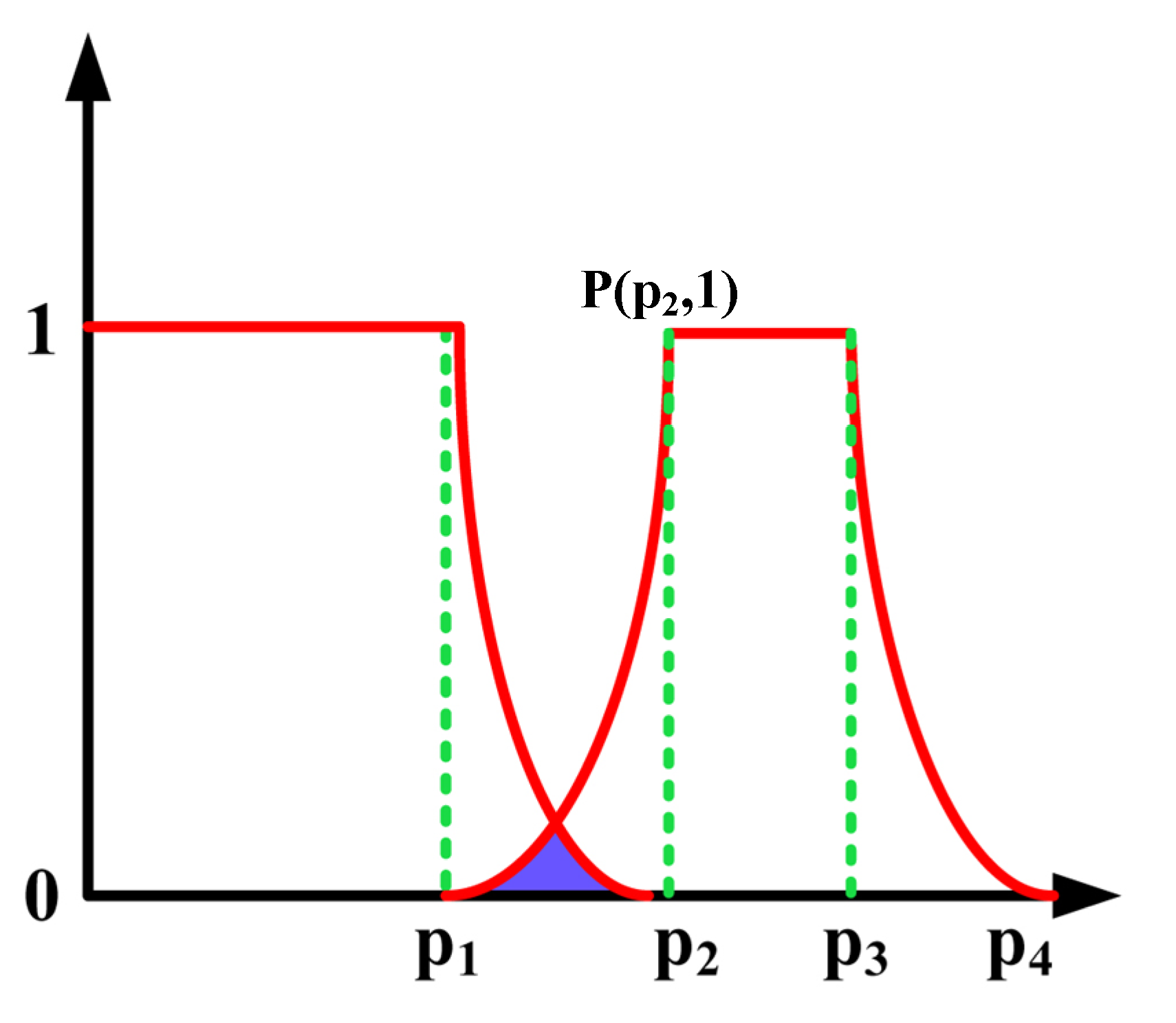
Appendix A. The Details of Curve-Trapezoid Mamdani Fuzzy Inference System
Appendix A.1. The Fuzzy Component

Appendix A.2. The Fuzzy Inference Component
| Rule No. | If (And) | Then (Membership Level) | |
|---|---|---|---|
| 1 | High | High | Absolutely high (level 1) |
| 2 | High | Medium | Very high (level 2) |
| 3 | High | Low | higher (level 3) |
| 4 | Medium | High | high (level 4) |
| 5 | Medium | Medium | medium (level 5) |
| 6 | Medium | Low | low (level 6) |
| 7 | Low | High | lower (level 7) |
| 8 | Low | Medium | Very low (level 8) |
| 9 | Low | Low | Absolutely low (level 9) |
Appendix A.3. The De-Blurring Component

References
- Passarella, A.; Conti, M. Analysis of Individual Pair and Aggregate Intercontact Times in Heterogeneous Opportunistic Networks. IEEE Trans. Mob. Comput. 2012, 12, 2483–2495. [Google Scholar] [CrossRef]
- Wu, J.; Chen, Z.; Zhao, M. An efficient data packet iteration and transmission algorithm in opportunistic social networks. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 3141–3153. [Google Scholar] [CrossRef]
- Liu, K.; Chen, Z.; Wu, J.; Tan, Y.; Wang, L.; Yan, Y.; Zhang, H.; Long, J. Big Medical Data Decision-Making Intelligent System Exploiting Fuzzy Inference Logic for Prostate Cancer in Developing Countries. IEEE Access 2018, 7, 2348–2363. [Google Scholar] [CrossRef]
- Peiyan, Y.; Mingyang, S. Lightweight distributed social distance routing algorithm in mobile opportunistic network. J. Comput. Appl. 2018, 1, 5. [Google Scholar]
- Martyna, J. Multicast modelling in mobile opportunistic networks. In Proceedings of the 2014 9th International Symposium on Communication Systems, Networks & Digital Sign (CSNDSP), Manchester, UK, 23–25 July 2014; pp. 238–242. [Google Scholar]
- Zhang, J.; Huang, H.; Yang, C. Destination-Aware Social Routing for Mobile Opportunistic networks. In Proceedings of the 2018 IEEE 20th International Conference on High Performance Computing and Communications; IEEE 16th International Conference on Smart City; IEEE 4th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Exeter, UK, 28–30 June 2018. [Google Scholar]
- Samanta, A.; Misra, S. Energy-Efficient and Distributed Network Management Cost Minimization in Opportunistic Wireless Body Area Networks. IEEE Trans. Mob. Comput. 2017, 17, 376–389. [Google Scholar] [CrossRef]
- Chakchouk, N. A Survey on Opportunistic Routing in Wireless Communication Networks. IEEE Commun. Surv. Tutorials 2015, 17, 2214–2241. [Google Scholar] [CrossRef]
- Kaysina, I.A.; Vasiliev, D.S.; Abilov, A.; Meitis, D.S.; Kaysin, A.E. Performance evaluation testbed for emerging relaying and coding algorithms in Flying Ad Hoc Networks. In Proceedings of the 2018 Moscow Workshop on Electronic and Networking Technologies (MWENT), Moscow, Russia, 14–16 March 2018; pp. 1–5. [Google Scholar]
- Chen, W. Buffer Aware Routing Algorithm for Opportunistic Network, Software Guide. 2019; 7, 7.
- Yu, L. A Wireless Sensor Networks Energy Multipath Routing Algorithm Based on Dynamic Priority. J. Jianghan Univ. 2019, 47, 239. [Google Scholar]
- Luo, J.; Wu, J.; Wu, Y. Advanced Data Delivery Strategy Base on Multi-Perceived Community with IoT in Social Complex Networks. Complexity 2020, 2020, 20. [Google Scholar] [CrossRef]
- Liu, K.; Chen, Z.; Wu, J.; Wang, L. FCNS: A Fuzzy Routing-Forwarding Algorithm Exploiting Comprehensive Node Similarity in Opportunistic Social Networks. Symmetry 2018, 10, 338. [Google Scholar] [CrossRef]
- Xu, M.; Song, W.; Zhao, Y. Collaborative Data Collection with Opportunistic Network Erasure Coding. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 1941–1950. [Google Scholar] [CrossRef]
- Yang, W.; Wu, J.; Luo, J. Effective Date Transmission and Control base on social communication in Social Opportunistic Complex Networks. Complexity 2020, 2020, 13. [Google Scholar]
- Jadhav, R.S.; Dongre, M.M.; Devurkar, G. Fuzzy logic-based data dissemination in Vehicular Ad Hoc Networks. In Proceedings of the 2017 International conference of Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 20–22 April 2017; pp. 479–483. [Google Scholar]
- Wu, J.; Chen, Z.; Zhao, M. Community recombination and duplication node traverse algorithm in opportunistic social networks. Peer-To-Peer Netw. Appl. 2020, 13, 940–947. [Google Scholar] [CrossRef]
- Liu, K.; Chen, Z.; Wu, J.; Xiao, Y.; Zhang, H. Predict and Forward: An Efficient Routing-Delivery Scheme Based on Node Profile in Opportunistic Networks. Futur. Internet 2018, 10, 74. [Google Scholar] [CrossRef]
- Zhao, P.; Yang, X. Opportunistic routing for bandwidth-sensitive traffic in wireless networks with lossy links. J. Commun. Netw. 2016, 18, 806–817. [Google Scholar]
- Yu, G.; Wu, J. Content caching based on mobility prediction and joint user Prefetch in Mobile edge networks. Peer-To-Peer Netw. Appl. 2020, 13, 1839–1852. [Google Scholar] [CrossRef]
- Borah, S.J.; Dhurandher, S.K.; Tibarewala, S.; Woungang, I.; Obaidat, M.S. Energy-Efficient Prophet-PRoWait-EDR Protocols for Opportunistic networks. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017. [Google Scholar]
- Hui, P.; Crowcroft, J.; Yoneki, E. BUBBLE Rap: Social-Based Forwarding in Delay-Tolerant Networks. IEEE Trans. Mobile Comput. 2011, 10, 1576–1589. [Google Scholar] [CrossRef]
- Khan, M.K.M.; Rahim, M.S. Performance Analysis of Social-Aware Routing Protocols in Delay Tolerant Networks. In Proceedings of the International Conference on Computer, Communication, Chemical, Material and Electronic Engineering, Rajshahi, Bangladesh, 8–9 February 2018. [Google Scholar]
- Mendes, P.; Sofia, R.C.; Tsaoussidis, V.; Soares, J.; Tsaoussidis, V.; Diamantopoulos, S.; Sarros, C.-A. Information-centric Routing for Opportunistic Wireless Networks. In Proceedings of the 5th ACM Conference on Information-Centric Networking, ICN ’18, New York, NY, USA, 21–23 September 2018; p. 9. [Google Scholar] [CrossRef]
- Wu, J.; Chen, Z.; Zhao, M. Information cache management and data transmission algorithm in opportunistic social networks. Wirel. Netw. 2018, 25, 2977–2988. [Google Scholar] [CrossRef]
- Kerk, Y.W.; Tay, K.M.; Lim, C.P. Monotone Interval Fuzzy Inference Systems. IEEE Trans. Fuzzy Syst. 2019, 27, 2255–2264. [Google Scholar] [CrossRef]
- Das, A.K.; Subramanian, K.; Sundaram, S.; Das Ankit, K. An Evolving Interval Type-2 Neuro-Fuzzy Inference System and Its Meta-Cognitive Sequential Learning Algorithm. IEEE Trans. Fuzzy Syst. 2015, 23, 1. [Google Scholar] [CrossRef]
- Cervantes, J.; Yu, W.; Salazar, S.; Chairez, I. Takagi–Sugeno Dynamic Neuro-Fuzzy Controller of Uncertain Nonlinear Systems. IEEE Trans. Fuzzy Syst. 2016, 25, 1601–1615. [Google Scholar] [CrossRef]
- Alizadeh, S.; Kalhor, A.; Jamalabadi, H.; Araabi, B.N.; Ahmadabadi, M.N. Online Local Input Selection Through Evolving Heterogeneous Fuzzy Inference System. IEEE Trans. Fuzzy Syst. 2016, 24, 1364–1377. [Google Scholar] [CrossRef]
- Abiyev, R.H.; Akkaya, N.; Gunsel, I. Control of Omnidirectional Robot Using Z-Number-Based Fuzzy System. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 238–252. [Google Scholar] [CrossRef]
- Wu, J.; Chen, Z.; Zhao, M. Information transmission probability and cache management method in opportunistic networks. Wirel. Commun. Mobile Comput. 2018, 2018, 1571974. [Google Scholar] [CrossRef]
- Singh, A.K.; Bera, T.; Pamula, R. PRCP: Packet replication control-based prophet routing strategy for delay tolerant network. In Proceedings of the 2018 4th International Conference on Recent Advances in Information Technology (RAIT), Dhanbad, India, 15–17 March 2018; pp. 1–5. [Google Scholar]
- Abubakar, H.; Tekanyi, A.; Sani, S. Node Cooperation Strategy on Security Aided and Group Encounter Prophet Routing Protocol of an Opportunistic Network. Int. J. Comput. Appl. 2017, 163, 34–38. [Google Scholar]
- Xiao, Z.; Han, G.; Xiujun, W.; Feng, Q. Contact Duration Aware Cooperative Data Caching in Mobile Opportunistic networks. J. Comput. Res. Dev. 2018, 55, 338. [Google Scholar]
- Bae, Y.H.; Baek, J.W. Achievable Throughput Analysis of Opportunistic Spectrum Access in Cognitive Radio Networks with Energy Harvesting. IEEE Trans. Commun. 2016, 64, 1399–1410. [Google Scholar] [CrossRef]
- Sharma, M.; Singh, Y. Middle Position Dynamic Energy Opportunistic Routing for Wireless Sensor Networks. In Proceedings of the 2015 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Kochi, India, 10–13 August 2015; pp. 948–953. [Google Scholar]
- Fradj, H.B.; Bouallegue, M.; Anane, R.; Bouallegue, R. Comparative study of opportunistic routing in Wireless Sensor Networks. In Proceedings of the 2017 13th International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, 26–30 June 2017; pp. 775–779. [Google Scholar]
- Kang, M.W.; Chung, Y.W. An energy-efficient opportunistic routing protocol in delay tolerant networks. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 25–27 May 2016; pp. 655–659. [Google Scholar]
- Wang, G.; Tao, J.; Zhang, H.; Pan, D. A improved Prophet routing based on congestion level of nodes in DTN. In Proceedings of the 2017 IEEE 2nd Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 25–26 March 2017; pp. 1666–1669. [Google Scholar]
- Lai, I.W.; Lee, C.H.; Chen, K.C.; Biglieri, E. Open-Loop End-to-End Transmission for Multi-hop Opportunistic networks with Energy-Harvesting Devices. IEEE Trans. Commun. 2016, 64, 2860–2872. [Google Scholar] [CrossRef]
- Kulkarni, L.; Bakal, J.; Shrawankar, U. Energy based incentive scheme for secure opportunistic routing in vehicular delay tolerant networks. Computing 2020, 102, 201–219. [Google Scholar] [CrossRef]
- He, W. Energy-Saving Algorithm and Simulation of Wireless Sensor Networks Based on Clustering Routing Protocol. IEEE Access 2019, 7, 172505–172514. [Google Scholar] [CrossRef]
- Loreti, P.; Bracciale, L. Optimized Neighbor Discovery for Opportunistic networks of Energy Constrained IoT Devices. IEEE Trans. Mob. Comput. 2019, 19, 1387–1400. [Google Scholar] [CrossRef]
- Bracciale, L.; Loreti, P.; Bianchi, G. The Sleepy Bird Catches More Worms: Revisiting Energy Efficient Neighbor Discovery. IEEE Trans. Mob. Comput. 2016, 15, 1812–1825. [Google Scholar] [CrossRef]
- Le Sommer, N.; Mahéo, Y.; Baklouti, F. Multi-Strategy Dynamic Service Composition in Opportunistic networks. Information 2020, 11, 180. [Google Scholar] [CrossRef]
- Amah, T.E.; Kamat, M.; Bakar, K.A.; Rahman, S.O.A.; Mohammed, M.H.; Abali, A.M.; Moreira, W.; Oliveira, A., Jr. The Impact of Message Replication on the Performance of Opportunistic networks for Sensed Data Collection. Information 2017, 8, 143. [Google Scholar] [CrossRef]
- Cui, J.; Cao, S.; Chang, Y.; Wu, L.; Liu, D.; Yang, Y. An Adaptive Spray and Wait Routing Algorithm Based on Quality of Node in Delay Tolerant Network. IEEE Access 2019, 7, 35274–35286. [Google Scholar] [CrossRef]
- Lenando, H.; Alrfaay, M. EpSoc: Social-Based Epidemic-Based Routing Protocol in Opportunistic Mobile Social Network. Mob. Inf. Syst. 2018, 2018, 6462826.1–6462826.8. [Google Scholar] [CrossRef]

| Routing Protocol | Implement of Details |
|---|---|
| Prophet | Frequency of encountering, cache space and contact duration |
| BubbleRap | Node community and centrality, limiting data duplicates |
| SCORP | Node sharing interest, number of encounters and contact duration, storage |
| DABBER | Energy consumption, storage and other routing metrics |
| ICMD | Cache management and node cooperation |
| Routing Algorithm | Details of Implementation |
|---|---|
| FCNS | Mamdani fuzzy inference system for node similarity; assessment of node attributes; two-hop transmission. |
| P&F | Two phases: prediction of meeting probabilities and forwarding of data packets; optimal stopping theory. |
| Spray and Wait | Nodes constantly exchange information copies when they meet; limiting the number of data packets. |
| Epidemic | Flooding model: information groups are transmitted to all neighbor nodes in same communication area. |
| DTCM | Curve-trapezoid fuzzy inference system for cache and energy; node classification; two-hop transmission. |
| Environment Setting | Description |
|---|---|
| Simulator | Opportunistic Network Environment (ONE) |
| Mobility model | HCMM (Health Capability Maturity Model) |
| Number of experiments | 80 (16 groups and 5 time for each group) |
| Communication area (m2) | 900 |
| Simulation time (h) | 1–8 |
| Number of nodes | 50, 100, 150, 200, 250, 300, 350, 400 |
| Speed of a node (m/s) | 2–20 |
| Cache of a mobile node (Mb) | 10 (Initial value), 15, 20, 25, 30, 35 |
| Size of a message (Kb) | 100 |
| Energy consumption of single delivery (J) | 10 |
| Total network energy (J) | 48000 |
| Consumption of a transmission (J) | 0.1 |
| Number of data packets carried by a node | 300 |
| Time to live (TTL) (h) | 2 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, S.; Chen, Z.; Wu, J.; Liu, K. An Adaptive Delay-Tolerant Routing Algorithm for Data Transmission in Opportunistic Social Networks. Electronics 2020, 9, 1915. https://doi.org/10.3390/electronics9111915
Chen S, Chen Z, Wu J, Liu K. An Adaptive Delay-Tolerant Routing Algorithm for Data Transmission in Opportunistic Social Networks. Electronics. 2020; 9(11):1915. https://doi.org/10.3390/electronics9111915
Chicago/Turabian StyleChen, Shupei, Zhigang Chen, Jia Wu, and Kanghuai Liu. 2020. "An Adaptive Delay-Tolerant Routing Algorithm for Data Transmission in Opportunistic Social Networks" Electronics 9, no. 11: 1915. https://doi.org/10.3390/electronics9111915
APA StyleChen, S., Chen, Z., Wu, J., & Liu, K. (2020). An Adaptive Delay-Tolerant Routing Algorithm for Data Transmission in Opportunistic Social Networks. Electronics, 9(11), 1915. https://doi.org/10.3390/electronics9111915







