Abstract
Because of the popularity of wireless technology, jamming attack is one of the most critical issues in wireless networks. Wireless jamming attack is one type of denial-of-service attacks where attackers send malicious messages or signal on a legitimate channel by causing intentional interference in the network. In order to avoid jamming attacks, various jamming defense schemes have been proposed. One of the popular methods is a channel-hopping scheme. However, the main challenge of this method is generating a common channel number between the users and the access point without leaking that information to the jammer. We propose a new channel-hopping scheme where the access point shares a separate key with each user to isolate the damage on the network when a key has been compromised, while maintaining high throughput and fairness. We evaluate the proposed scheme through experiment on a test bed.
1. Introduction
Due to the development of wireless technology, wireless networks are used in many diverse fields. Especially, 802.11 is one of most popular access network options these days. Wireless protocols are designed to utilize the resource fairly among different users. While providing fairness, wireless network protocols attempt to achieve maximum throughput among users. However, existing wireless protocols are not designed to consider jamming attacks. Due to the open nature of a wireless medium, wireless networks are vulnerable to numerous security threats. Anyone with a transceiver can eavesdrop on ongoing transmissions, inject spurious messages, or block the transmission of a legitimate user. One of the basic ways to block a legitimate transmission is by jamming a wireless transmission. Jamming can cause denial-of-service (DoS) problems, which may result in several other higher-layer security problems [1]. Existing wireless protocols are not designed to consider jamming attacks. For example, a jamming attack could disrupt a wireless network, and this can be easily achieved by a malicious attacker (jammer) by injecting noise signals into the shared medium. To remain inconspicuous, the jammer would need to jam with conventional (802.11) hardware, such as a laptop with one or two wireless interfaces. There are several methods to jam wireless channels [1]. Figure 1 shows a classification of wireless jammers. Among them, we will consider only well-known intelligent jamming methods.
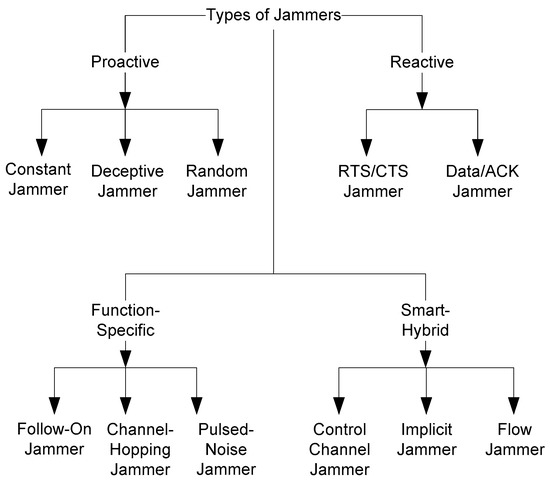
Figure 1.
Types of jammers in a wireless network.
Proactive jammers—A proactive jammer transmits jamming (interfering) signals regardless of whether there is data communication in a network. Constant, deceptive, random jammers belong to this category [2].
Reactive jammers—Reactive jammers jam the channel only when they find an ongoing transmission on the current channel [2,3]. Their effectiveness is much higher compared with proactive jamming methods.
Smart-hybrid—Smart-hybrid methods are called smart because of their power-efficient jamming nature. The main aim of these jammers is to magnify their jamming effect in their target network. Moreover, they take care of themselves by conserving their energy. They place sufficient energy in the right place so as to hinder the communication bandwidth for the entire network or a major part of the network in very large networks. Control channel, implicit, and flow jammers are representative examples of smart-hybrid jammers [4,5,6]. Each of these jammers can be implemented as both proactive and reactive, hence hybrid.
Function-specific jamming—Follow-on, channel-hopping, and pulsed-noise jammers belong to this category. Function-specific jamming methods are implemented using predetermined functions [7,8,9]. They can work as either a reactive or a proactive jammer.
Channel-hopping—A channel-hopping jammer can only transmit or receive on a single channel at a time and has knowledge of the specific channel-hopping sequence. In this paper, we model the jammer as a smart reactive channel-hopping jammer. Our goal is to build a channel-hopping scheme that maximizes the throughput of normal nodes in the existence of the smart channel-hopping jammer.
Wireless jamming is a very destructive DoS attack, and thus, it is important to detect jamming attacks because it is the first step towards building a secure wireless network. Jamming detection is challenging because jammers can employ different models, as we mentioned above. There are several detection strategies that have been proposed thus far.
Packet delivery ratio (PDR)—PDR is defined as the ratio of the total number of packets delivered successfully to a destination to the total number of packets transmitted by the source. In this method, jamming is detected based on the value of the PDR [10]. If the value of the PDR is close to zero, this indicates the presence of jammers. The PDR is effective in differentiating jamming and network congestion.
Signal strength—The strength of a signal gets affected by the presence of interference. Hence, in this method the detection of jamming is done by the strength of the received signal. Here, we compare the average signal strength with the threshold, which is calculated by the noise levels.
Traditionally, channel hopping has been considered a solution that can help alleviate the effects of jamming; both proactive and reactive channel-hopping strategies have been proposed in the literature [11,12,13]. However, the main challenge in this approach is to derive the same channel number among different nodes without exchanging channel information explicitly. Most channel-hopping schemes assume the access point (AP) and legitimate users know the next hopping channel in advance, and they will share the channel sequence for subsequent time slots. The main disadvantage of this method is that if the channel sequence is known to the attacker, the attacker can easily follow the sequence and jam continuously. Random channel-hopping mechanism is another approach used to deal with the issue of generating the next channel number. A random channel-hopping scheme based on a quorum system ensures that within a bounded amount of time the nodes meet each other [11]. However, the throughput goes down dramatically. In [14,15], respectively, Premnath and Jana and their colleagues proposed adaptive schemes to generate bits from a channel repository, such as a single received signal strength (RSS) measurement. Key generation schemes using a wireless channel repository have been studied in many fields and implemented successfully [16,17]. The basic idea is to use the wireless channel reciprocity, which means that the receiver and the transmitter of one wireless link observe the same channel characteristics simultaneously.
In this work, we consider an approach where a channel-hopping sequence is produced using a key that is shared between a user and the AP. We use a secret key to calculate the next hopping channel. When each user has a different key, they generate different channel sequence numbers. This can be helpful in avoiding the worst case in the presence of a jammer. Figure 2 shows the principle of the proposed scheme. For each time slot, at least one user gets service from the AP on different channels. If there are two or more users at the same time slot as shown between t6 and t7, those users share a medium fairly according to wireless MAC protocols.
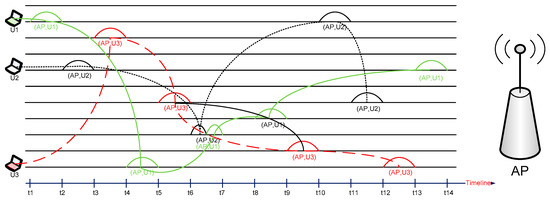
Figure 2.
Proposed scheme working principle.
The main contributions of this paper are given as follows.
First, we investigate a new jamming mitigation scheme that considers both the aggregate throughput and the fairness among the users when there are multiple user nodes around a single AP. Thus far, there have been several research efforts on a channel-hopping method for jamming mitigation. However, there has been no research that considers these two metrics (i.e., throughput and fairness) simultaneously under jamming attack. There have been several attempts to find the resource allocation scheme by defining a utility function based on both throughput and fairness and applying an optimization technique to the problem [18,19,20,21]. However, jamming attacks have not been considered in those works. Since the jammer’s strategy may not be known to the AP, it is not easy to define the utility function reflecting the jammer’s behavior. Thus, we attempt to develop a new heuristic and practical defense scheme that considers both throughput and fairness in this paper. Second, the throughput of the proposed channel-hopping scheme is analyzed mathematically and compared with that of the random channel-hopping scheme. Third, although our scheme requires a key establishment between a user and an AP, since the AP shares a different secret key with each user, the damage is isolated to a single user when one key is compromised by an attacker.
The rest of the article is organized as follows. In Section 2, we discuss existing channel-hopping schemes. In Section 3, we review channel generation schemes using channel characteristics of the wireless link. In Section 4, we introduce a new channel selection scheme based on the throughput of the nodes. In Section 5, we mathematically analyze the proposed scheme. Section 6 and Section 7 describe the attacker model and experiment topology. Section 8 shows experiment results by comparing our proposed scheme with a random channel-hopping scheme in terms of throughput and fairness. Section 9 concludes the paper.
2. Related Work
Once the presence of a jammer is detected, it is necessary to decide how to defend the legitimate transmissions against jamming attacks. There are several well-known defense mechanisms against jamming attacks.
Directional antenna-based approach—One approach used to cope with jamming attacks is using directional antenna instead of omnidirectional antenna [22]. In this way, we target to reduce the antenna gain from the jammer to the receiver. Most directional antenna-based approaches are implemented in wireless ad hoc networks. A directional antenna-based approach may not be efficient in maximizing throughput in public wireless networks, and it requires a specific antenna to receive and transmit data [23].
Game theory-based approach—Game theory-based schemes have been proposed in many papers [24,25]. The jamming activities can be considered a game between the jammer and the normal user players. Altman et al. [25] studied the jamming game in wireless networks with transmission cost. In this game, both the user and the jammer take the power allocation on channels as their strategies. The utility of the user is the weighted capacity minus transmission cost. However, most of existing game theory-based approaches consider a single-user and single-AP scenario in the case of 802.11.
Frequency-hopping spread spectrum (FHSS)—The FHSS is a method of transmitting radio signals by rapidly changing the carrier frequency among many distinct frequencies occupying a large spectral band. The changes are controlled by a code known to both the transmitter and the receiver. There are many research works on antijamming frequency-hopping protocol [7,26,27]. Since a protocol requires a special antenna to operate, it is costly to implement in a real environment. Moreover, the FHSS requires the prior exchange of sequence information, namely, code establishment, before data transmission, and this is a critical limitation of this approach.
Channel hopping—Channel hopping is a well-known classic antijamming technique that rapidly changes the channel with the aid of a pseudorandom sequence known to both the transmitter and the receiver. Many channel-hopping schemes have been proposed in the past [28,29,30]. Most of them consider a channel-hopping scheme between legitimate users and the AP, and this can be one efficient approach against intelligent jamming attacks. The idea of channel hopping is motivated by frequency hopping. Channel hopping is similar to frequency hopping in that both of them change frequencies during the communication. However, the difference between them is that frequency hopping, unlike channel hopping, requires specialized antennas for transmitting and receiving signals. Channel hopping is a link-layer technology, and it is easy to use compared with frequency hopping. This approach can be applied to existing wireless devices without frequency-hopping features [31]. The channel-hopping scheme can be either proactive or reactive. In a proactive channel-hopping scheme, a pair of transceivers switch channels periodically at an interval of every k seconds, regardless of whether there is a jammer on the current channel [12,32]. However, the main issue in this approach is deriving the same hopping channel that is common to both the AP and a user. Another disadvantage of this approach is the AP and legitimate users need to negotiate channel numbers in advance, which may not be easy in public places where users come and leave frequently. Navda et al. [12] implemented a proactive channel-hopping protocol with pseudorandom channel switching for coping with a jammer. They assumed that the channel sequence is only known to legitimate users and the AP. The disadvantage of this approach is as follows. If a jammer becomes aware of the sequence information, then no communication would succeed due to jamming attacks on all the subsequent channels. Gummadi et al. [32] proposed a rapid channel-hopping scheme in which a node occupies a channel for a short period of time (i.e., 10 ms) with 250 µs channel-switching latency. Practically 10 ms may not be long enough to transfer a large amount of data, and it can degrade the throughput because of the wasted time for channel switching.
In a reactive channel-hopping scheme, we need to detect jamming attacks first. There are numerous works proposed in order to detect jamming in wireless networks [2,33,34]. We use packet delivery ratio (PDR) to detect jamming attacks at the link-layer level since a signal strength-based detection scheme can only detect a constant jammer. If an attacker works as a deceptive jammer, the signal strength-based scheme cannot discriminate the jammer [1,2,29,35]. Thus, PDR-based detection can be more efficient than a signal strength-base one in detecting jammers on a link layer.
Xu et al. [29,36] proposed a reactive channel-hopping strategy. The key idea is that when a node is jammed, it switches to a new but predetermined channel. The other party of the communication switches to the same channel upon not hearing from its partner for a prolonged period of time. The authors point out the challenges in the implementation of such strategy, but do not provide solutions. In particular, there are issues related to synchronization, scalability, loss of packets, and latency [13]. Djuraev et al. [31] proposed a channel-hopping scheme without prior channel agreement. However, the scheme considers the scenario of only a single user and a single AP. In the case of multiple user nodes, most of the existing works considered a predefined channel sequence [12,32,37].
In our paper, we propose a new channel selection mechanism called accumulated throughput-based channel selection scheme. Our proposed scheme generates the initial key between the user and the AP only once at the beginning. Each user generates its own channel sequence based on the initial key, and the AP selects the channel number, considering both throughput and fairness. Since the channel sequence numbers of the users are different from each other, the damage can be isolated when one key is compromised by an attacker. We discuss more details about key generation schemes and channel selection mechanisms in Section 3 and Section 4.
3. Initial Key Generation
Various key generation schemes have been proposed in order to derive keys using wireless characteristics. Most of them are based on channel reciprocity that the multipath and fading at both ends of the same link (i.e., same carrier frequency) are identical. It is the basis for two users to generate the same key. Received signal strength (RSS) and channel state information (CSI) channel parameters are the essential parts of a key generation scheme. In order to get CSI, we need specialized wireless devices, which makes it difficult to monitor these characteristics in current wireless networks. RSS is currently the channel parameter most frequently used in key generation, especially for practical implementation, due to its availability. Numerous RSS-based key generation systems have been proposed [14,15,31,38]. In our previous work, we generated a key based on the received signal strength by dividing RSS values into groups. The AP and a user node exchange two frames in order to measure the signal strength between them. Let us say two RSS values, S1 and S2, are measured by the AP and the user node, respectively. Instead of comparing S1 and S2 as floating point numbers, they check whether these two values belong to the same group (i.e., same interval). If two numbers are in the same group, they generate the same key based on a group index. However, it does not work in a multiple-user-based environment because the RSS values cannot be the same among different users.
In this section, we will discuss a key generation scheme using wireless channel characteristics. A unique key is generated for each user in our proposed scheme. We generate keys using the RSS value of the channel. To establish a shared key between the AP and a user, we measure the variations of the wireless channel between them over time by sending simple ping messages to each other and measuring the RSS values of the received messages [14,15,38]. In an ideal case, the AP and a user must measure the same RSS value. In a practical case, the RSS values might be close to each other if the time between two-directional channel measurements is sufficiently small considering the rate of change of the channel. Figure 3 shows a packet exchange between a user and an AP. Let us assume that the AP and a user node exchange two frames, one in each direction, and measure the signal strength during [t1–t4], whose duration is smaller than coherence time Tc (i.e., t1–t4 < Tc). Coherence time is the time duration over which the channel impulse response is considered to be not varying. Let S1 and S2 denote the signal strength (in dBm) measured by the user and the AP, respectively. The AP sends a ping request message at time t1, and the user gets the message at time t2. From the received message, the user obtains the RSS value S1. An immediate response message is sent to the AP at time t3, and the AP measures the signal strength S2 of the response message from each user. Each packet is sent at an interval of 1 s. In order to generate a 128-bit key, the AP and the user node should exchange at least 128 packages for each direction. After exchanging n messages, we have a set of from the AP and .
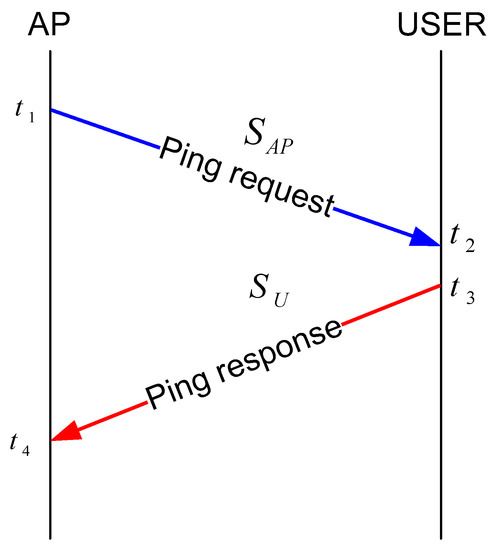
Figure 3.
Message exchange between access point (AP) and user.
After exchange of multiple packets between the user and the AP, each node obtains a series of measured RSS values. Then, each node quantizes Q(x), the time series, to generate an initial secret bit sequence. The AP and the user calculate their mean values μ from collected RSS values. Figure 4 shows how a quantizer works with collected RSS information in the system [14].
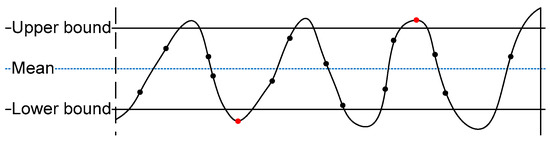
Figure 4.
A simple received signal strength (RSS) quantizer. A value greater than the mean value is encoded as 1, and a value less than the mean value is encoded as 0.
In Figure 4, the values between the upper and lower thresholds are dropped [14,15], and we compare the remaining RSS values with the mean value μ. If the value is larger than the mean value, then we obtain 1. If it is smaller than the mean value, then we obtain 0 according to Equation (1). We determined the upper and lower thresholds after several experiments, and they are set to and , respectively, in this paper, where μ and σ are the average and standard deviation of the RSS values.
Once both the AP and the user extract the bit stream by applying quantizers to the RSS measurements, they need to correct the bits where the two bit streams differ to obtain the same key. The AP divides a long bit sequence into small blocks and sends the permutation and parity information of each block to the user. The user also permutes his bit stream the same way and checks whether the parity of the blocks agrees with the values. For each block whose parity information does not match, the user implements a binary search to find whether a small number of bits in the block can be changed to make the block match the parity information. After information reconciliation, the AP and the user will have a unique extracted key between them. The AP will generate an individual key with each user node one by one until all users have a shared key between the AP and them.
4. Channel Selection Strategy for Multiple User Nodes to Mitigate Jamming Attacks
In this section, we assume that there are one AP, multiple (n) user nodes, and one jamming attacker node as shown in Figure 5, and we explain how the jamming attack can be mitigated based on the keys shared between the AP and the user nodes. Let denote the secret key shared between the AP and the i-th user node.
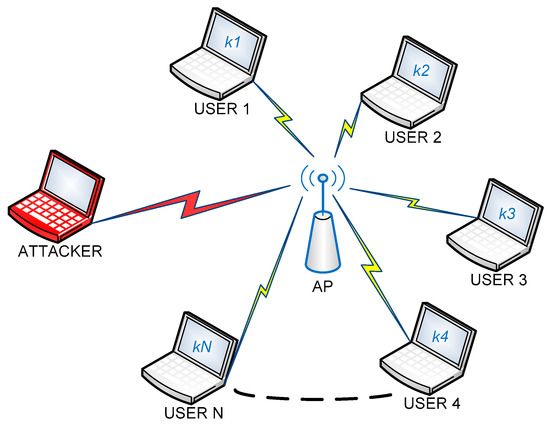
Figure 5.
Wi-Fi network with one AP, one attacker, and multiple user nodes.
When the jamming attack is detected, we assume that each user node changes its own channel number at the interval of Δ, and this time interval is also referred to as time slot throughout this paper. denotes the channel number selected by node i at time slot t. Then, the first channel number (i.e., ) is the number of the AP’s channel just before the detection of the jamming attack. The subsequent channel numbers are determined by the following equation:
where is the total number of channels, TS means the current time in seconds, and is a cryptographic hash function. Thus, since the AP also knows and the secret key if the AP finds the channel number of the user node i, then it can infer the channel numbers of node i based on Equation (2). In the case of the attacker, even though the attacker finds of node i, it cannot infer without knowing the secret key .
From now on, we discuss the channel selection policy of the AP. Since each user node shares its unique secret key with the AP, the AP can determine the channel number selected by each user node in advance as shown in Figure 6. In this paper, we design the channel selection policy of the AP, considering both the total throughput and the fairness among the user nodes. Figure 6 shows the channel numbers selected by each user node over time, and the channel numbers of each user have been determined by Equation (2). If the AP monitors the channel numbers selected by each user node at time slot 1, then the AP can know the channel numbers selected by each user at time slot 2 since the channel numbers are selected by Equation (2), and the AP knows the secret key of each user. In order to maximize short-term fairness, the AP tries to choose the channel number selected by the largest number of users, which corresponds to the value inside the dotted circle in Figure 6, at each time slot. The AP tries to serve as many users as possible at each time slot. However, if the AP makes a decision on the next channel number only, considering the number of users, there might be a starvation problem. In Figure 6, we can find that the 6-th user node gets significantly less service compared with the other users when the AP considers only the number of users and randomly chooses a channel number when there is a tie in the majority group.
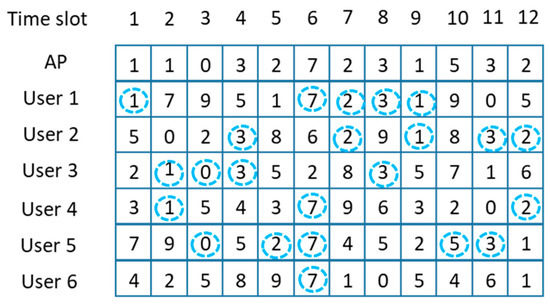
Figure 6.
Channel selection of AP only based on throughput (random tie-breaking).
It is possible to improve the fairness and resolve the starvation problem by applying the tie-breaking rule while considering the aggregate throughput (Figure 7). Hereafter, we explain the channel selection rule of the AP in more detail.
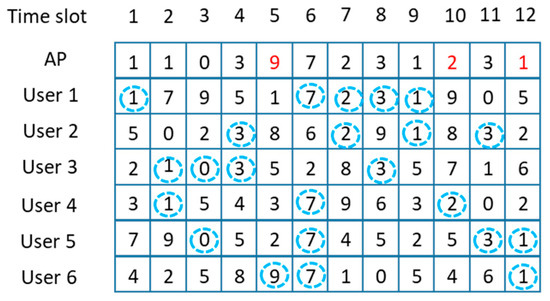
Figure 7.
Channel selection of AP based on throughput and fairness.
Algorithm 1 decides the next channel number based on the number of users on each channel to maximize the throughput and breaks a tie in the majority group, considering the starvation and fairness problem. In order to solve a starvation problem, we need the channel history information of each user. In other words, the AP should know which user has received less service from the AP. We can calculate the total opportunity of each user during time period L.
Let denote the expected normalized throughput of node i at time t. = 1 if node i stays on the same channel as the AP at time t, and = 0 otherwise. Accumulated throughput of user node i is defined by Equation (3).
That is, is defined as the summation of per-user normalized throughput of node i during the last L time slots. Let denote the channel number selected by the AP at time slot t. Let denote the set of user nodes that selected the channel number c at time slot t. Then, is determined by the following algorithm.
| Algorithm 1 AP’s Channel Selection Algorithm |
| 1: At time t, calculate , , for each user . |
| 2: Find the channel number such that |
| 3: If is uniquely determined in step 2, |
| (fairness maximization). |
| Move to step 9. |
| 4: If is not determined uniquely in step 2, then we number those channels . |
| 5: For each channel , we calculate the following group-accumulated opportunity |
| 6: Find the channel number c″ such that (for the prevention of starvation and guarantee of fairness). |
| 7: If is not unique, then break the tie randomly. |
| 8: . |
| 9: Repeat the process from step 1 at the interval of until the jamming attack finishes. |
However, the AP cannot store all history information indefinitely due to limited storage space on the AP. In order to solve this problem, we will manage the throughput of each user only for the last L time slots, and this concept is reflected in Equation (3). The throughput for the last L time slots can be managed by storing the throughput for each time slot in an array of size L in a wraparound manner, as shown in Figure 8. As we can see in Figure 8, the AP keeps only the last L values, and if the table is full when new values are obtained, the AP will fill the table from beginning again.
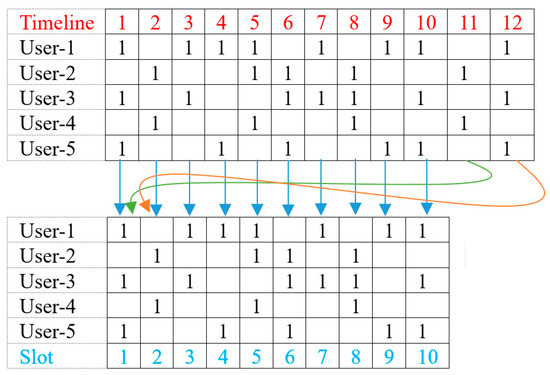
Figure 8.
Cyclic buffer to store the throughput information only for the last L time slots at the AP.
We find an optimal value for L. We run an experiment that compares the total throughput of 10 nodes by increasing the sliding window size L from 10 s to 50 s. In this experiment, we did not consider the jammer. As we can see in Figure 9, 20 s gives a higher throughput compared with the other window sizes.
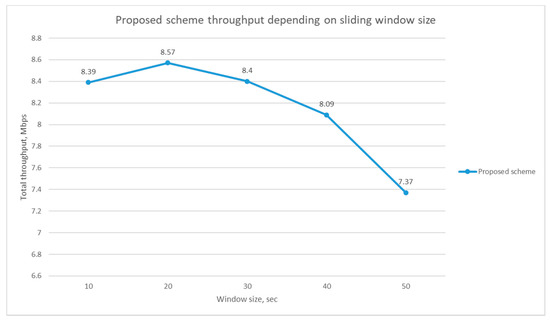
Figure 9.
Optimal window size for L history information.
We also want to investigate the effect of the window size L on the starvation of existing nodes, especially in a dynamic case, where some nodes can easily join or leave. Let us consider a case where five nodes have been served by the AP for a long time, and L is 1 day. Then, the accumulated throughput (AT) for the existing five nodes will be a large number if the time slot duration is 1 s. In this case, if a new node joins this subnet, the AP will continuously select the new node in a tie-breaking situation until the AT of the new node reaches that of other existing nodes, and some of the existing nodes might suffer from starvation during this interval. This time interval (i.e., the time duration from the arrival of the new node till the AT of the new node reaches that of the existing nodes) is called the channel recovery time in this paper. We ran an experiment to find an optimal channel recovery time when a new node joins a subnet with nine existing wireless nodes. We measured the channel recovery time (tx) by changing the window size L from 10 s to 50 s, and Figure 10 shows the experiment results. As we can see in Figure 10, the recovery time increases as the window size increases based on the reason explained above. If the channel recovery time increases, then the starvation time can also increase accordingly. By considering the results in Figure 9 and Figure 10, the window size for channel history information window size L is chosen to be 20 s. The scheme with a window size (L) of 20 s gives a higher throughput and a rather small channel recovery time of 11 s.
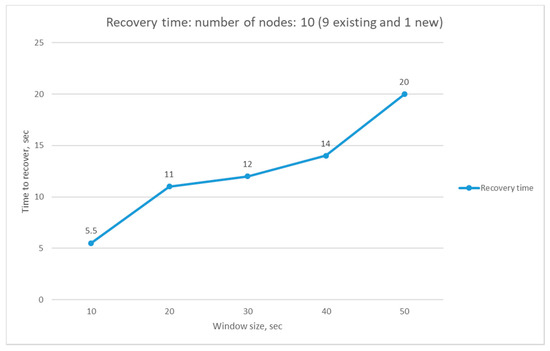
Figure 10.
Channel recovery time depending on window size.
5. Mathematical Analysis of System
We now investigate the advantage of the proposed scheme compared with the random switching scheme through an analysis. N and U denote the number of channels and the number of users associated with a selected AP. Let denote the traffic rate supported by the selected AP at time t when the random switching scheme is used, and we analyze hereafter. V is a random variable denoting the number of users that are on the same channel as the AP at time t. To simplify the analysis, we assume that V users share the link bandwidth R fairly when there is no jammer. Then, can be expressed as
.
The distribution of V can be obtained as
Then, we can obtain
Let denote the traffic rate supported by the selected AP at time t when the proposed channel switching scheme is used. V’ is a random variable denoting the number of users on the channel with the largest number of users among N channels at time t, which is selected by the AP according to the algorithm explained in Section 4. Then, can be expressed as
.
If U is positive, V’ cannot be zero in the channel selection algorithm. The AP, , becomes R for a positive number U. The distribution of V’ can be approximated in the following manner. If Vi is a random variable denoting the number of users on the i-th channel at time t, then V’ can be expressed as
Each of the Vi’s has the distribution of Equation (4). If we assume that Vi’s are independent from each other to simplify the analysis, then we can obtain
where has the distribution of Equation (4). Since for a positive U, we can calculate the advantage of the proposed scheme compared with the random switching scheme in terms of throughput as
For example, when N = 11 and U = 10, becomes 1.63 according to Equation (7).
6. Attacker Model
We assume that the jammer is aware of our channel-hopping protocol and will do as much as it can, given its limited set of hardware resources, to interrupt the legitimate communication. Since the hopping sequence is totally dependent on the AP’s decision, the AP’s channel, we assume that the jammer cannot know all the secret keys for the individual users simultaneously. The AP’s channel cannot be predicted by the jammer easily. The best remaining jam strategy is to quickly scan the entire spectrum of channels looking for the legitimate communication to jam that channel. A jammer works as a function-specific channel-hopping smart proactive jammer. When a channel is found containing meaningful communication (e.g., a packet with MAC addresses of nodes whose communication the jammer wishes to disrupt), the jammer interrupts the channel completely by transmitting back-to-back packets that interfere with this communication. Similar to the assumption in traditional channel-hopping schemes, instead of considering a powerful attacker, we assume that the jammer uses the same or similar hardware as legitimate users in terms of capability, energy capacity, and complexity, and the power-limited attacker can jam only one channel at a given time. The jammer must periodically stop jamming and listen for a brief period of time on the channel to determine whether the legitimate communication has already hopped to another channel.
7. Implementation
We ran experiments using one AP and 10 user nodes with Ubuntu 14.04 and wireless PCI LAN cards. The attacker was equipped with the same PCI LAN card. Figure 11 shows a network topology for experiment. We performed experiments on 802.11 g 2.4 GHz (11 nonoverlapping channels). Each experiment was run for 50 min to measure the throughput. We increased the number of nodes one by one. We ran the experiments at night in order to avoid interference from other nearby WLAN devices that operated in the same frequency band.
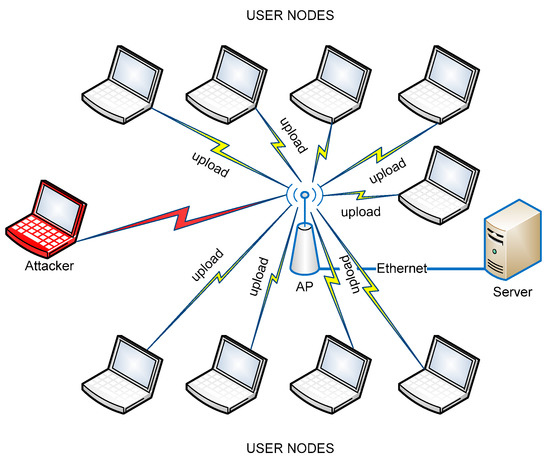
Figure 11.
Experiment topology.
The jammer occupies the whole channel once he finds the AP’s channel. In this paper, the channel sojourn time is defined as the duration during which the AP stays in the selected channel before it changes the channel number in the presence of a jamming attack. In our experiment, the sojourn time was fixed to 250 ms. We found the optimal sojourn time by running an experiment to investigate the effect of channel switching time on the throughput for our proposed scheme when there is a jamming attack. In this experiment, we set the number of nodes to 5. Figure 12 shows the throughput of the proposed scheme for various channel switching times. As we can see in Figure 12, 100 ms is not sufficiently long to send an enough amount of data after the association process. Increasing the channel sojourn time would give an opportunity to the user to send more data, but it increases the chance for an attacker to find the channel and jam the channel as well.
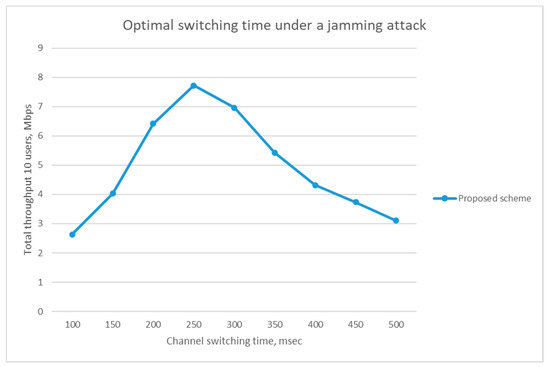
Figure 12.
Optimal channel switching time for the proposed scheme under jamming attack.
We found that a channel switching time of 250 ms gives the highest throughput in the presence of an attacker in our experiment. Thus, the channel sojourn time is fixed to 250 ms hereafter.
8. Experiment Results
As an initial step, each node generates a unique secret key with the AP. The AP stores all the keys along with the MAC address of the user. After detecting a jamming attack, each node finds and moves to the next hopping channel independently, and the AP also calculates the next hopping channel according to the algorithm explained in Section 4. We compared our proposed scheme with a random channel switching scheme in terms of throughput and fairness. In the random channel switching scheme, the AP and each user selected the next channel number randomly independent of each other. In this experiment, we varied the number of nodes from 1 to 10. The aggregate throughput was measured for our proposed scheme and the random switch scheme without the jammer in the first scenario, and the throughput was measured for these two schemes under jamming attacks in the subsequent scenarios.
8.1. Throughput
As we can see in Figure 13, the throughput for the random channel-hopping scheme stays very low when the number of users is small because of the disagreement of the channel numbers selected by the AP and the user. Our proposed scheme shows almost 10 times higher throughput compared with the random channel-hopping scheme when the number of nodes is small.
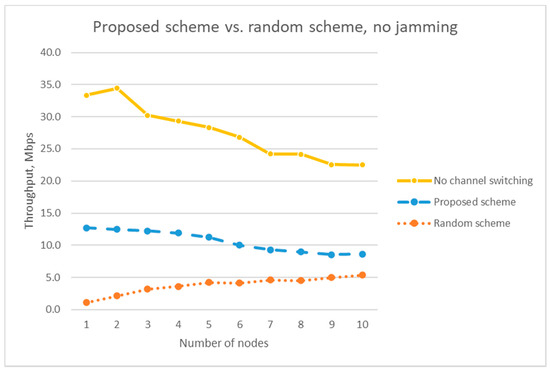
Figure 13.
Throughput comparison of the proposed scheme and the random channel-hopping scheme without a jammer.
We compared the experiment results with the mathematical analysis result. In Figure 13, we can calculate the ratio of the throughput of the proposed scheme to that of the random switching scheme. For example, when the number of nodes is 1, the throughput ratio between the two schemes is 11.7, and when the number of nodes is 10, the throughput ratio is 1.6. Figure 14 compares the throughput ratio obtained by the analysis in Section 5 with the one obtained by the experiment. As we can see in Figure 14, the analysis result agrees well with the experiment results.
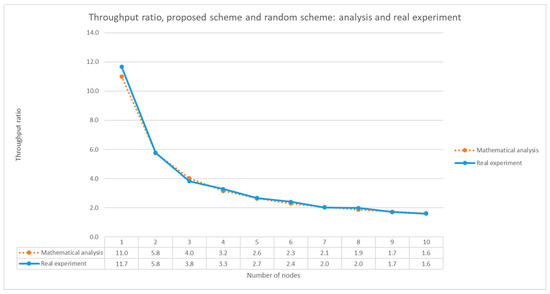
Figure 14.
Comparison of the mathematical analysis with experiment results without jamming attack.
Figure 15 compares the throughput of the proposed scheme with the throughput of the random channel selection scheme when there is a jammer, which behaves according to the attacker model described in Section 4. Figure 15 shows that the proposed scheme yields much higher throughput compared with the random channel selection scheme. The throughput of our proposed scheme is about 5.4 times higher than that of the random channel-hopping scheme when the number of nodes is 10.
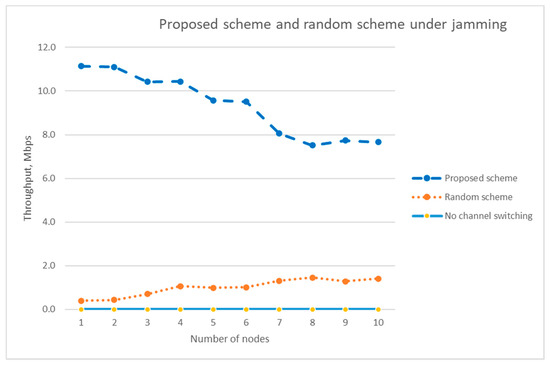
Figure 15.
Comparison of the throughputs of the proposed scheme and the random channel-hopping scheme under jamming attack.
8.2. Fairness
Now we evaluate the fairness of our proposed scheme and that of the random scheme using a generalized Jain’s index [20], defined in terms of the parameter β and the throughput of each user:
where N is the number of users, sign(x) is 1 for a positive x and 0 for a negative x, and is the accumulated throughput of the i-th node during a short amount of time t. When , becomes a multiple of the well-known Jain’s fairness index (J) [39]. In other words, we have
where J is defined as
We fixed the duration of the measurement interval to 2 s, and we calculated the fairness index of each scheme for time slot t. We averaged the fairness index over the total simulation time. Figure 16 compares the generalized Jain’s index for the two schemes when there is no jammer. We measured the fairness index for the positive and negative values of β, and Figure 16 shows that our proposed scheme exhibits better fairness than the random switching scheme regardless of the values of β when there is no jammer. Figure 17 compares the two schemes in terms of Jain’s fairness index (J) under the same condition. According to Equation (9), J is different from only by a factor of N, (i.e., the number of users), and we can find an increasing trend in from Figure 16a because of this factor. If from Figure 16a is normalized by N, it agrees well with the graph in Figure 17.
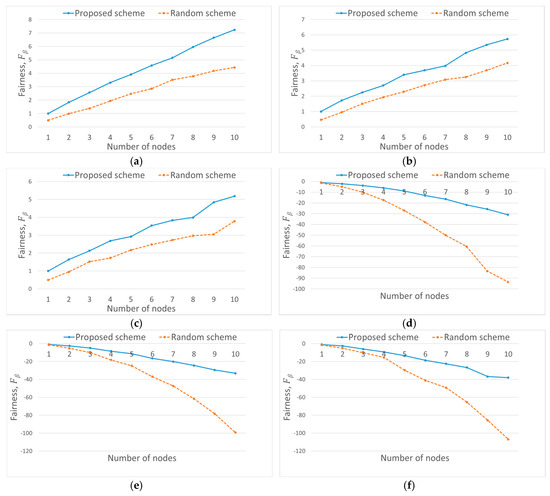
Figure 16.
Comparison of the generalized Jain’s fairness index between the proposed scheme and the random channel-hopping scheme without jamming attack. (a) , (b) , (c) , (d) , (e) (f) .
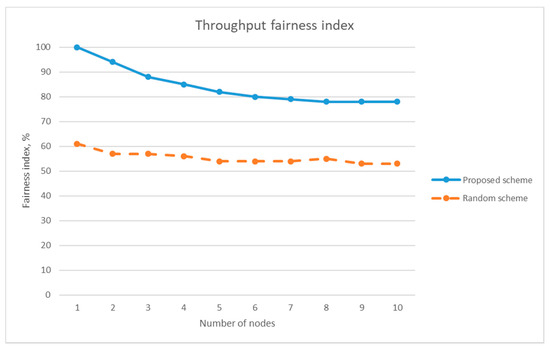
Figure 17.
Jain’s fairness index of the proposed scheme and the random channel-hopping scheme without jamming attack.
Figure 18 compares the Jain’s fairness index of the two schemes under jamming attack. As we can see, the proposed scheme shows two times higher performance compared with the random channel-hopping scheme regardless of the number of user nodes.
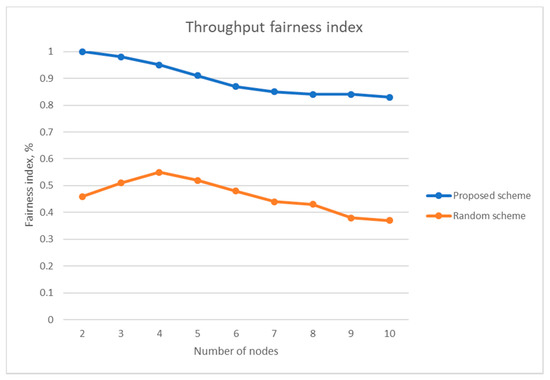
Figure 18.
Jain’s fairness index of the proposed scheme and the random channel-hopping scheme under jamming attack.
9. Conclusions
In this paper, we proposed a new channel-hopping scheme to mitigate jamming attacks. In this scheme, each user generates a secret key that will be shared with the AP using the channel characteristics, and the next channel number is calculated from the secret key. Then, the AP selects the next channel number, considering the aggregate throughput and the fairness among the users. Since the AP shares a different key with each user, even if one key is compromised by an attacker, the damage is isolated to a single user, and there is no need to update any other keys in this case. The experiment results show that our proposed scheme achieves a higher throughput and better fairness among the users compared with the random channel switching scheme.
Author Contributions
Conceptualization, S.Y.N. and S.D.; methodology, S.Y.N. and S.D.; software, S.D.; validation, S.Y.N. and S.D.; formal analysis, S.Y.N.; investigation, S.Y.N.; resources, S.D.; data curation, S.D.; writing—original draft preparation, S.D.; writing—review and editing, S.Y.N.; visualization, S.D.; supervision, S.Y.N.; project administration, S.Y.N.; funding acquisition, S.Y.N. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported in part by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (2020R1A2C1010366, 2015R1D1A1A01058595). This research was supported in part by the MSIT, Korea, under the ITRC (Information Technology Research Center) support program (IITP-2020-2016-0-00313) supervised by the IITP (Institute for Information & communications Technology Planning & Evaluation).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Grover, K.; Lim, A.; Yang, Q. Jamming and anti-jamming techniques in wireless networks: A. survey. Int. J. Ad Hoc Ubiquitous Comput. 2014, 17, 197–215. [Google Scholar] [CrossRef]
- Xu, W.; Trappe, W.; Zhang, Y.; Wood, T. The feasibility of launching and detecting jamming attacks in wireless networks. In Proceedings of the International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc), Urbana-Champaign, IL, USA, 25–27 May 2005; pp. 46–57. [Google Scholar] [CrossRef]
- Pelechrinis, K.; Iliofotou, M.; Krishnamurthy, S.V. Denial of service attacks in wireless networks: The case of jammers. IEEE Commun. Surv. Tutor. 2011, 13, 245–257. [Google Scholar] [CrossRef]
- Lazos, L.; Liu, S.; Krunz, M. Mitigating control-channel jamming attacks in multi-channel ad hoc networks. In Proceedings of the 2nd ACM Conference on Wireless Network Security, WiSec’09, Zurich, Switzerland, 16–18 March 2009. [Google Scholar] [CrossRef]
- Pelechrinis, K.; Koutsopoulos, I.; Broustis, I.; Krishnamurthy, S.V. Lightweight jammer localization in wireless networks: System design and implementation. In Proceedings of the GLOBECOM—IEEE Global Telecommunications Conference, Honolulu, HI, USA, 30 November–4 December 2009. [Google Scholar] [CrossRef]
- Tague, P.; Slater, D.; Poovendran, R.; Noubir, G. Linear programming models for jamming attacks on network traffic flows. In Proceedings of the 6th International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks, WiOpt 2008, Berlin, Germany, 31 March–4 April 2008. [Google Scholar] [CrossRef]
- Mpitziopoulos, A.; Gavalas, D.; Pantziou, G.; Konstantopoulos, C. Defending wireless sensor networks from jamming attacks. In Proceedings of the IEEE International Symposium on Personal, Indoor and Mobile Radio Communications, PIMRC, Athens, Greece, 3–7 September 2007. [Google Scholar] [CrossRef]
- Alnifie, G.; Simon, R. A multi-channel defense against jamming attacks in wireless sensor networks. In Proceedings of the Q2SWinet’07: The Third ACM Workshop on Q2S and Security for Wireless and Mobile Networks, Crete Island, Greece, 22 October 2007. [Google Scholar] [CrossRef]
- Muraleedharan, R.; Osadciw, L.A. Jamming attack detection and countermeasures in wireless sensor network using ant system. In Proceedings of the Wireless Sensing and Processing, Istanbul, Turkey, 11–15 June 2006. [Google Scholar] [CrossRef]
- Sufyan, N.; Saqib, N.A.; Zia, M. Detection of jamming attacks in 802.11b wireless networks. EURASIP J. Wirel. Commun. Netw. 2013, 208. [Google Scholar] [CrossRef]
- Lee, E.K.; Oh, S.Y.; Gerla, M. Randomized channel hopping scheme for anti-jamming communication. In Proceedings of the 2010 IFIP Wireless Days, WD 2010, Venice, Italy, 20–22 October 2010. [Google Scholar] [CrossRef]
- Navda, V.; Bohra, A.; Ganguly, S.; Rubenstein, D. Using channel hopping to increase 802.11 resilience to jamming attacks. In Proceedings of the IEEE INFOCOM 2007, Anchorage, AK, USA, 6–12 May 2007. [Google Scholar] [CrossRef]
- Pelechrinis, K.; Koufogiannakis, C.; Krishnamurthy, S.V. On the efficacy of frequency hopping in coping with jamming attacks in 802.11 networks. IEEE Trans. Wirel. Commun. 2010, 9, 3258–3271. [Google Scholar] [CrossRef]
- Premnath, S.N.; Jana, S.; Croft, J.; Gowda, P.L.; Clark, M.; Kasera, S.K.; Patwari, N.; Krishnamurthy, S.N. Secret key extraction from wireless signal strength in real environments. IEEE Trans. Mob. Comput. 2012, 12, 917–930. [Google Scholar] [CrossRef]
- Jana, S.; Premnath, S.N.; Clark, M.; Kasera, S.K.; Patwari, N.; Krishnamurthy, S.V. On the effectiveness of secret key extraction from wireless signal strength in real environments. In Proceedings of the Annual International Conference on Mobile Computing and Networking, MOBICOM, Beijing, China, 20–25, September 2009. [Google Scholar] [CrossRef]
- Wang, T.; Liu, Y.; Vasilakos, A.V. Survey on channel reciprocity based key establishment techniques for wireless systems. Wirel. Netw. 2015, 21, 1835–1846. [Google Scholar] [CrossRef]
- Guillaud, M.; Slock, D.T.M.; Knopp, R. A practical method for wireless channel reciprocity exploitation through relative calibration. In Proceedings of the 8th International Symposium on Signal. Processing and its Applications, ISSPA 2005, Sydney, Australia, 28–31 August 2005. [Google Scholar] [CrossRef]
- Tang, A.; Wang, J.; Low, S.H. Counter-intuitive throughput behaviors in networks under end-to-end control. IEEE/ACM Trans. Netw. 2006, 14, 355–368. [Google Scholar] [CrossRef]
- Fu, J.; Zhang, X.; Cheng, L.; Shen, Z.; Chen, L.; Yang, D. Utility-based flexible resource allocation for integrated LTE-U and LTE wireless systems. In Proceedings of the IEEE Vehicular Technology Conference, Glasgow, Scotland, 11–14 May 2015. [Google Scholar] [CrossRef]
- Zabini, F.; Bazzi, A.; Masini, B.M.; Verdone, R. Optimal Performance Versus Fairness Tradeoff for Resource Allocation in Wireless Systems. IEEE Trans. Wirel. Commun. 2017, 16, 2587–2600. [Google Scholar] [CrossRef]
- Zabini, F.; Bazzi, A.; Masini, B.M. Throughput versus fairness tradeoff analysis. In Proceedings of the IEEE International Conference on Communications, Budapest, Hungary, 9–13 June 2013. [Google Scholar] [CrossRef]
- Noubir, G. On connectivity in ad hoc networks under jamming using directional antennas and mobility. In Proceedings of the International Conference on Wired/Wireless Internet Communications, Frankfurt/Oder, Germany, 4–6 February 2004. [Google Scholar]
- Spyropoulos, A.; Raghavendra, C.S. Energy efficient communications in Ad Hoc networks using directional antennas. In Proceedings of the IEEE INFOCOM 2002, New York, NY, USA, 23–27 June 2002. [Google Scholar] [CrossRef]
- Altman, E.; Avrachenkov, K.; Gamaev, A. Jamming in wireless networks: The case of several jammers. In Proceedings of the 2009 International Conference on Game Theory for Networks, GameNets ’09, Istambul, Turkey, 20–22 May 2009. [Google Scholar] [CrossRef]
- Altman, E.; Avrachenkov, K.; Garnaev, A. A jamming game in wireless networks with transmission cost. In Proceedings of the Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Redondo Beach, CA, USA, 8–11 July 2007. [Google Scholar] [CrossRef]
- Xu, W. Jamming Attack Defense. In Encyclopedia of Cryptography and Security; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Chang, G.Y.; Huang, J.F.; Wu, Z.H. A frequency hopping algorithm against jamming attacks under asynchronous environments. In Proceedings of the 2014 IEEE Global Communications Conference, GLOBECOM 2014, Austin, TX, USA, 8–12 December 2014. [Google Scholar] [CrossRef]
- Yoon, S.U.; Murawski, R.; Ekici, E.; Park, S.; Mir, Z.H. Adaptive channel hopping for interference robust wireless sensor networks. In Proceedings of the IEEE International Conference on Communications, Cape Town, South Africa, 23–27 May 2010. [Google Scholar] [CrossRef]
- Xu, W.; Wood, T.; Trappe, W.; Zhang, Y. Channel surfing and spatial retreats: Defenses against wireless denial of service. In Proceedings of the 2004 ACM Workshop on Wireless Security, WiSe, Philadelphia, PA, USA, 1 October 2004. [Google Scholar]
- Wang, L.; Wyglinski, A.M. A combined approach for distinguishing different types of jamming attacks against wireless networks. In Proceedings of the IEEE Pacific RIM Conference on Communications, Computers, and Signal. Processing—Proceedings, Victoria, BC, Canada, 23–26 August 2011. [Google Scholar] [CrossRef]
- Djuraev, S.; Choi, J.G.; Sohn, K.S.; Nam, S.Y. Channel hopping scheme to mitigate jamming attacks in wireless LANs. EURASIP J. Wirel. Commun. Netw. 2017, 11. [Google Scholar] [CrossRef]
- Gummadi, R.; Wetherall, D.; Greenstein, B.; Seshan, S. Understanding and mitigating the impact of RF interference on 802.11 networks. ACM SIGCOMM Comput. Commun. Rev. 2007, 37, 385–396. [Google Scholar] [CrossRef]
- Hamieh, A.; Ben-Othman, J. Detection of jamming attacks in wireless ad hoc networks using error distribution. In Proceedings of the IEEE International Conference on Communications, Dresden, Germany, 14–18 June 2009. [Google Scholar] [CrossRef]
- Liu, G.; Liu, J.; Li, Y.; Xiao, L.; Tang, Y. Jamming detection of smartphones for WiFi signals. In Proceedings of the IEEE Vehicular Technology Conference, Glasgow, Scotland, 11–14 May 2015. [Google Scholar] [CrossRef]
- Xu, W.; Trappe, W.; Zhang, Y. Anti-jamming timing channels for wireless networks. In Proceedings of the WiSec’08: The 1st ACM Conference on Wireless Network Security, Alexandria, VA, USA, 31 March–2 April 2008. [Google Scholar] [CrossRef]
- Xu, W.; Ma, K.; Trappe, W.; Zhang, Y. Jamming sensor networks: Attack and defense strategies. IEEE Netw. 2006, 20, 41–47. [Google Scholar] [CrossRef]
- Bahl, P.; Chandra, R.; Dunagan, J. SSCH: Slotted seeded channel hopping for capacity improvement in IEEE 802.11 ad-hoc wireless networks. In Proceedings of the Annual International Conference on Mobile Computing and Networking, MOBICOM, Philadelphia, PA, USA, 23 September 2004. [Google Scholar]
- Mathur, S.; Trappe, W.; Mandayam, N.; Ye, C.; Reznik, A. Radio-telepathy: Extracting a secret key from an unauthenticated wireless channel. In Proceedings of the Annual International Conference on Mobile Computing and Networking, MOBICOM, San Francisco, CA, USA, 14–19 September 2008. [Google Scholar] [CrossRef]
- Jain, R.; Durresi, A.; Babic, G. Throughput fairness index: An explanation. ATM Forum Contrib. 1999. Available online: https://www.cse.wustl.edu/~jain/atmf/ftp/atm99-0045.pdf (accessed on 21 October 2020).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).