Optimization of Routing-Based Clustering Approaches in Wireless Sensor Network: Review and Open Research Issues
Abstract
1. Introduction
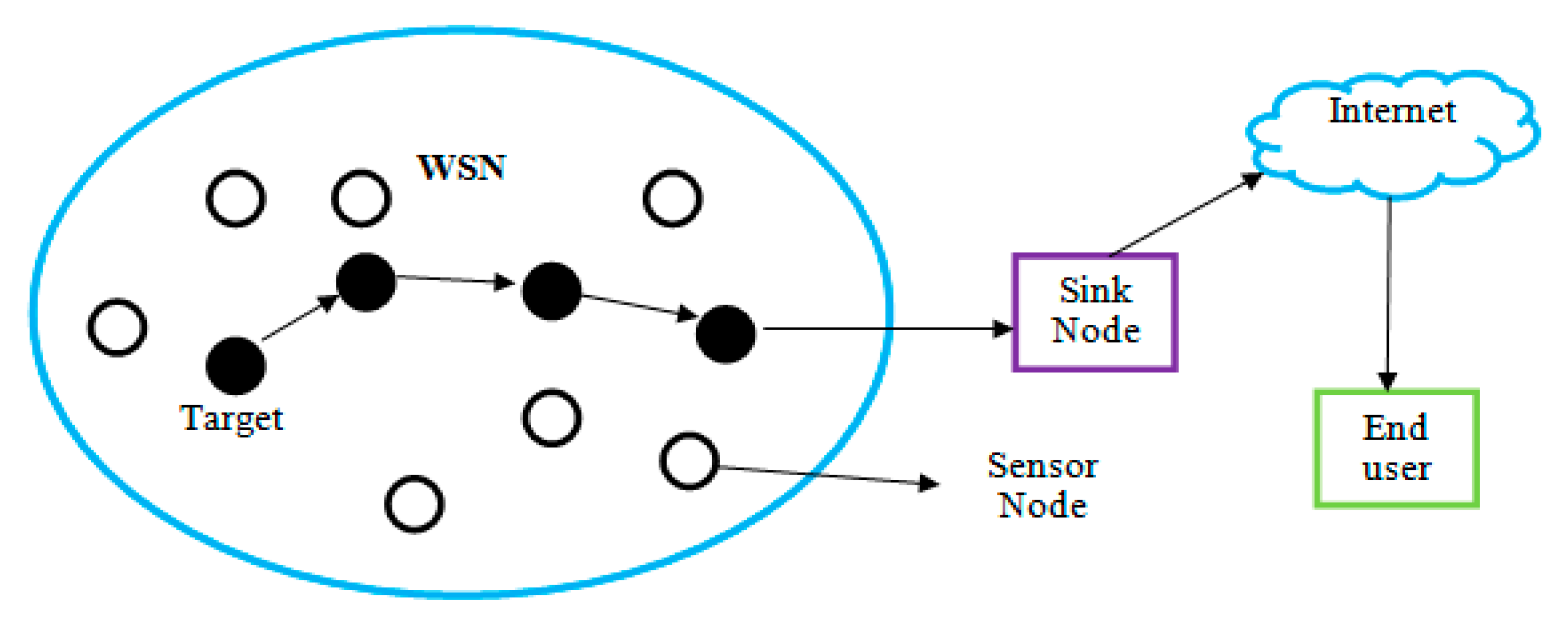
1.1. Wireless Sensor Networks
1.1.1. Sensor Node Architecture
- To receive the data;
- Processing of data;
- Data transfer through wireless communication.
1.1.2. WSN Types
Terrestrial WSN
Underground WSN
Underwater WSN
Mobile WSN
Multimedia WSN
1.1.3. WSN-Main Prerequisites
Power Efficiency
Reliability
Scalability
Mobility
1.1.4. WSN-Security Vulnerabilities
1.1.5. WSN-IoT
1.2. Clustering
1.2.1. Clustering—Design Challenges
- For clustering protocols, the number of clusters and formation processes are very essential. Balance among clusters is very important, and at the same time, message exchange during the formation of the clusters must be minimized.
- The algorithm complexity increases linearly as the network develops.
- CH selection is very important because it can directly affect the performance of the system.
- The most ideal hub should be chosen with the goal that the system steadiness period and general network lifetime should be expanded.
- In most of the strategies, CH choice depends on a few parameters, for example, energy level and hub location.
- CH will receive the sensed data from the nodes on which the data aggregation process is performed. That process is the reason that these steps form the key structural challenge [27].
- A clustering algorithm should handle all types of applications because WSNs are completely application dependent.
- The clustering algorithm design must support defense applications in which data are highly confidential, for example, military applications and health monitoring [26]
- Variable energy allocation becomes complicated in many of the researches.
- While applying the clustering model in a larger network it becomes complicated and energy consumption will be gradually increased.
- Clustering algorithms are combined with many hybrid models to improve the overall performance of the network. During that process interference of the network is also gradually increased.
1.2.2. Benefits of Clustering in WSN
- Clustering can execute optimized management methodologies in the network.
- From the sensor level, the topology of the network and communication overhead are managed by clusters because of hub associations with only the CHs.
- Clustering can maintain the bandwidth for communication, and it can also prevent redundancy of exchange messages [30].
2. Materials and Methods
2.1. Clustering-Based Routing Protocols
2.2. Optimization-Based Clustering Mechanisms
3. Cluster-Based Routing Protocol Classification—Overview
3.1. Parameter-Based Clustering
3.1.1. Clustering Based on Primary Parameters
Strategy for CH Selection
Objective
3.1.2. Clustering Based on Secondary Parameters
Types of Node
Cluster Size
Mobility of Nodes
Intercluster Communication
Intracluster Communication
Rotating of the CH
Methods
3.2. Optimization-Based Clustering
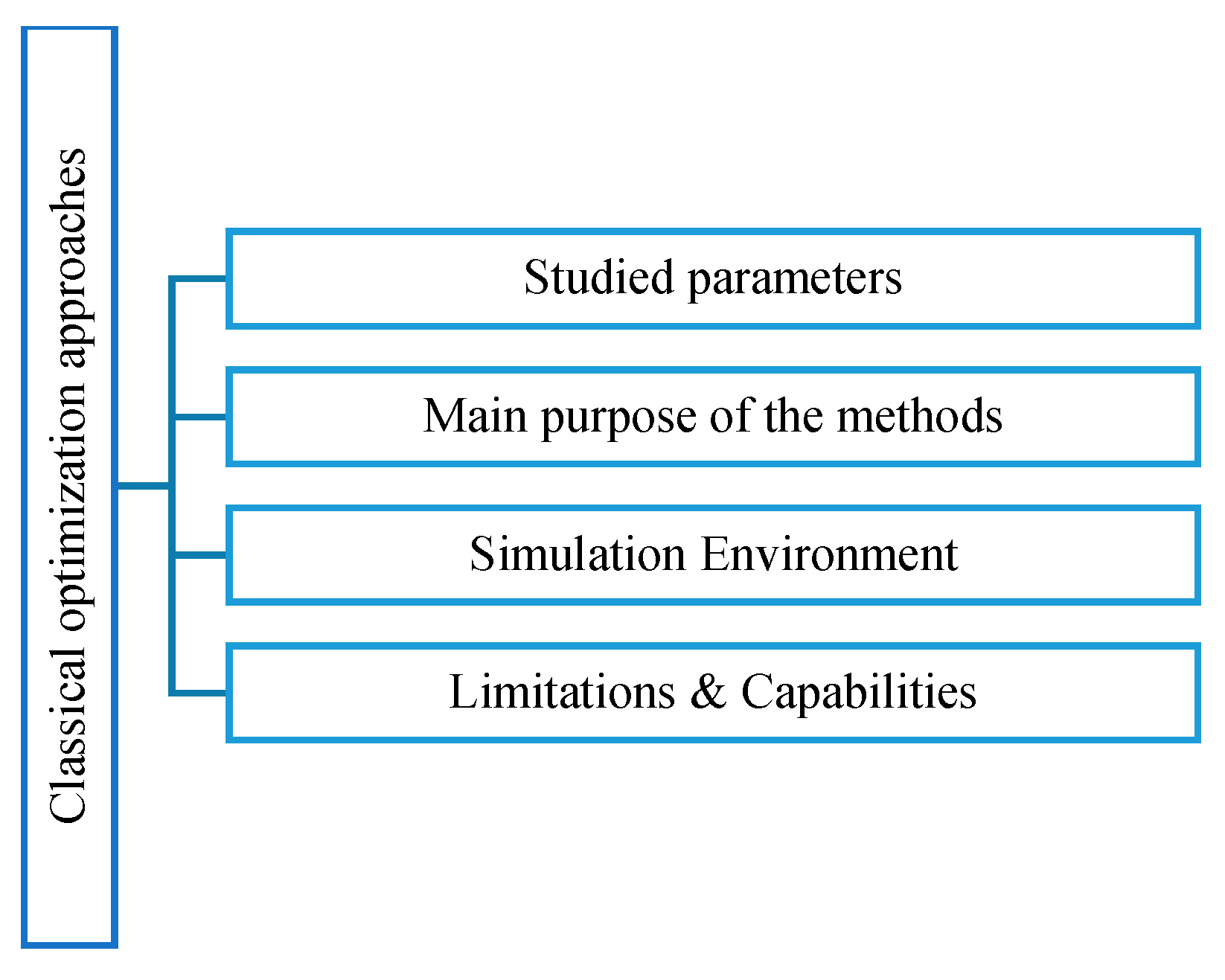
3.2.1. Classical Optimization Approaches
3.2.2. Hybrid Optimization Approaches
3.3. Methodology-Based Clustering
3.3.1. Fuzzy-Based Approaches
3.3.2. Metaheuristic-Based Approaches
4. Classification of Cluster-Based Routing Protocols
4.1. Parameter-Based Clustering
4.1.1. Clustering-Based Primary Parameters
SHPER: Scalable Hierarchical Power-Efficient Routing
HHRP: Heterogeneous Hierarchical Routing Protocol
EEQAHR: Energy-Efficient QoS Assurance Hierarchical Routing
4.1.2. Clustering-Based Secondary Parameters
Cluster-Based Routing Protocols for Energy Efficiency (CBRPEE)
IICC: Intra- and Intercluster Communication IICC
TSEENP: Threshold Sensitive Energy-Efficient Network Protocol
4.2. Optimization-Based Clustering
4.2.1. Classical Approaches
LEACH: Low-Energy Adaptive Clustering Hierarchy
- →Expected percentage of CH nodes in the population of sensors;
- →Current round number;
- G→Group of hubs which never transform into CHs in the last 1/s adjusts (turns).
- →Binary to confirm CH only once for all of the rounds.
- →Distance among hubs and BS;
- and →Residual energy of CH and non-CH nodes.
Maximum Energy Cluster Head (MECH)
Power-Efficient Clustering Routing Protocol (PECRP)
Energy-Efficient Heterogeneous Clustering (EEHC)
Flow-Balanced Routing (FBR)
Energy-Efficient Routing Algorithm (EERA)
Layered Clustering Routing Protocol with Overlapping Cluster Heads (LCRPOCH)
Low-Energy Fixed Clustering Algorithm (LEFCA)
Hamilton Energy-Efficient Routing Protocol (HEER)
Hierarchical Distributed Management Clustering (HDMC)
Energy-Aware Multihop Routing (EAMR)
4.2.2. Hybrid Optimization Methodologies
Fuzzy and Ant Colony Optimization-Based Combined MAC, Routing, and Unequal Clustering Cross-Layer Protocol for WSNs (FAMACROW)
Swarm-Intelligence-Based Fuzzy Routing Protocol (SIF)
Centralized Cluster-Based Routing Protocol Based on Sugeno Fuzzy Inference System (LEACH-SF)
Fuzzy Shuffled Frog-Leaping Algorithm (FSFLA)
4.3. Methodology-Based Clustering
4.3.1. Fuzzy-Based Approaches
LEACH Protocol Using Fuzzy Logic (LEACH-FL)
Energy-Aware Unequal Clustering Algorithm with Fuzzy (EAUCF)
Multiobjective Fuzzy Clustering Algorithm (MOFCA)
Fuzzy-Based Unequal Clustering Protocol (FUCP)
FL-Based Unequal Clustering (FBUC)
Distributed Unequal Clustering Using FL (DUCF)
Energy Conserved Unequal Clusters with Fuzzy Logic (ECUCF)
4.3.2. Metaheuristic Methodologies
Multipath Routing Protocol (MRP)
Genetic Algorithm-Based Threshold Sensitive Energy-Efficient Routing Protocol (GATERP)
Heuristic Algorithm for Clustering Hierarchy (HACH)
HSA Cluster-Based Protocol (HSACP)
S-EECP: Stable Energy-Efficient Clustering Protocol
Single-Hop Energy-Efficient Clustering and Multihop Energy-Efficient Clustering Protocols (S-EECP and M-EECP)
Distance-Based Residual Energy-Efficient Stable Election Protocol (DRESEP)
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Chijioke, W.; Jamal, A.A.; Mahiddin, N.A. Wireless Sensor Networks, Internet of Things, and Their Challenges. Int. J. Innov. Technol. Explor. Eng. 2019, 8, 2278–3075. [Google Scholar]
- Kim, B.S.; Park, H.; Kim, K.H.; Godfrey, D.; Kim, K.I. A survey on real-time communications in wireless sensor networks. Wirel. Commun. Mob. Comput. 2017, 2017, 1864847. [Google Scholar] [CrossRef]
- Ali, A.; Ming, Y.; Chakraborty, S.; Iram, S. A comprehensive survey on real-time applications of WSN. Future Internet 2017, 9, 77. [Google Scholar] [CrossRef]
- Albaladejo, C.; Sánchez, P.; Iborra, A.; Soto, F.; López, J.A.; Torres, R. Wireless sensor networks for oceanographic monitoring: A systematic review. Sensors 2010, 10, 6948–6968. [Google Scholar] [CrossRef]
- Rashid, B.; Rehmani, M.H. Applications of wireless sensor networks for urban areas: A survey. J. Netw. Comput. Appl. 2016, 60, 192–219. [Google Scholar] [CrossRef]
- Tandel, H.; Shah, R. A Survey Paper on Wireless Sensor Network. Int. J. Sci. Res. Dev. 2017, 5, 907–909. [Google Scholar]
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks: A survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Rawat, P.; Singh, K.D.; Chaouchi, H.; Bonnin, J.M. Wireless Sensor Networks: Recent developments and potential synergies. J. Supercomput. 2013, 68, 1–48. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Pompili, D.; Melodia, T. Challenges for efficient communication in underwater acoustic sensor networks. ACM Sigbed Rev. 2004, 1, 3–8. [Google Scholar] [CrossRef]
- Heinzelman, W.B.; Chandrakasan, A.P.; Balakrishnan, H. An application-specific protocol architecture for wireless microsensor networks. IEEE Trans. Wirel. Commun. 2002, 1, 660–670. [Google Scholar] [CrossRef]
- Swetha, R.; Santhosh Amarnath, V.; Anitha Sofia, V.S. Wireless Sensor Network: A Survey. Int. J. Adv. Res. Comput. Commun. Eng. 2018, 7, 114–117. [Google Scholar]
- Perrig, A.; Szewczyk, R.; Tygar, J.D.; Wen, V.; Culler, D.E. SPINS: Security protocols for sensor networks. Wirel. Netw. 2002, 8, 521–534. [Google Scholar] [CrossRef]
- Shi, E.; Perrig, A. Designing secure sensor networks. IEEE Wirel. Commun. 2004, 11, 38–43. [Google Scholar]
- Geetha, V.A.; Kallapur, P.V.; Tellajeera, S. Clustering in wireless sensor networks: Performance comparison of leach & leach-c protocols using ns2. Procedia Technol. 2012, 4, 163–170. [Google Scholar]
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Wood, A.D.; Stankovic, J.A. Denial of service in sensor networks. Computer 2002, 35, 54–62. [Google Scholar] [CrossRef]
- Zhu, Q.; Wang, R.; Chen, Q.; Liu, Y.; Qin, W. Iot gateway: Bridgingwireless sensor networks into internet of things. In Proceedings of the 2010 IEEE/IFIP International Conference on Embedded and Ubiquitous Computing, Hong Kong, China, 11–13 December 2010; pp. 347–352. [Google Scholar]
- Kuo, Y.W.; Li, C.L.; Jhang, J.H.; Lin, S. Design of a wireless sensor network-based IoT platform for wide area and heterogeneous applications. IEEE Sens. J. 2018, 18, 5187–5197. [Google Scholar] [CrossRef]
- Pirbhulal, S.; Zhang, H.; E Alahi, M.E.; Ghayvat, H.; Mukhopadhyay, S.C.; Zhang, Y.T.; Wu, W. A novel secure IoT-based smart home automation system using a wireless sensor network. Sensors 2017, 17, 69. [Google Scholar] [CrossRef]
- Sen, J. A survey on wireless sensor network security. arXiv 2010, arXiv:1011.1529. [Google Scholar]
- Hassan, A.A.H.; Shah, W.M.; Iskandar, M.F.; Mohammed, A.A.J. Clustering methods for cluster-based routing protocols in wireless sensor networks: Comparative study. Int. J. Appl. Eng. Res. 2017, 12, 11350–11360. [Google Scholar]
- Hassan, A.A.H.; Shah, W.; Husein, A.M.; Talib, M.S.; Mohammed, A.A.J.; Iskandar, M. Clustering approach in wireless sensor networks based on k-means: Limitations and recommendations. IJRTE 2019, 7, 119–126. [Google Scholar]
- Somasundaram, R.; Thangavel, T. An Enhanced Energy Efficient Unequal Layered Clustering Algorithm for Large Scale Wireless Sensor Networks. Int. J. Soft Comput. Eng. IJSCE 2013, 3, 2231–2307. [Google Scholar]
- Adhikary, D.R.D.; Mallick, D.K. An Energy Aware Unequal Clustering Algorithm using Fuzzy Logic for Wireless Sensor Networks. J. ICT Res. Appl. 2017, 11, 55–76. [Google Scholar] [CrossRef][Green Version]
- Gajendran, M.; Basavaraj, M. WSN Clustering Based on EECI (Energy Efficient Clustering using Interconnection) Method. Int. J. Innov. Technol. Explor. Eng. 2019, 9, 3564–3571. [Google Scholar]
- Zeb, A.; Islam, A.M.; Zareei, M.; Al Mamoon, I.; Mansoor, N.; Baharun, S.; Komaki, S. Clustering analysis in wireless sensor networks: The ambit of performance metrics and schemes taxonomy. Int. J. Distrib. Sens. Netw. 2016, 12, 4979142. [Google Scholar] [CrossRef]
- Mamta, V. Clustering Techniques in Wireless Sensor Network. Int. J. Comput. Appl. Technol. Res. 2014, 6, 3381–3384. [Google Scholar]
- Wu, J.; Zhang, L.; Bai, Y.; Sun, Y. Cluster-based consensus time synchronization for wireless sensor networks. IEEE Sens. J. 2014, 15, 1404–1413. [Google Scholar] [CrossRef]
- Khediri, S.E.; Nasri, N.; Wei, A.; Kachouri, A. A new approach for clustering in wireless sensors networks based on LEACH. Procedia Comput. Sci. 2014, 32, 1180–1185. [Google Scholar] [CrossRef]
- Jan, B.; Farman, H.; Javed, H.; Montrucchio, B.; Khan, M.; Ali, S. Energy efficient hierarchical clustering approaches in wireless sensor networks: A survey. Wirel. Commun. Mob. Comput. 2017, 2017, 6457942. [Google Scholar] [CrossRef]
- Singh, S.K.; Singh, M.P.; Singh, D.K. Routing protocols in wireless sensor networks—A survey. Int. J. Comput. Sci. Eng. Surv. 2010, 1, 63–83. [Google Scholar] [CrossRef]
- Zungeru, A.M.; Ang, L.M.; Seng, K.P. Classical and swarm intelligence based routing protocols for wireless sensor networks: A survey and comparison. J. Netw. Comput. Appl. 2012, 35, 1508–1536. [Google Scholar] [CrossRef]
- Rathi, N.; Saraswat, J.; Bhattacharya, P.P. A review on routing protocols for application in wireless sensor networks. arXiv 2012, arXiv:1210.2940. [Google Scholar] [CrossRef]
- Rostami, A.S.; Badkoobe, M.; Mohanna, F.; Hosseinabadi, A.A.R.; Sangaiah, A.K. Survey on clustering in heterogeneous and homogeneous wireless sensor networks. J. Supercomput. 2018, 74, 277–323. [Google Scholar] [CrossRef]
- Abbasi, A.A.; Younis, M. A survey on clustering algorithms for wireless sensor networks. Comput. Commun. 2007, 30, 2826–2841. [Google Scholar] [CrossRef]
- Fanian, F.; Rafsanjani, M.K.; Bardsiri, V.K. A survey of advanced LEACH-based protocols. Int. J. Energy Inf. Commun. 2016, 7, 1–16. [Google Scholar] [CrossRef]
- Akkaya, K.; Younis, M.A. survey on routing protocols for wireless sensor networks. Ad Hoc Netw. 2005, 3, 325–349. [Google Scholar] [CrossRef]
- Sha, K.; Gehlot, J.; Greve, R. Multipath routing techniques in wireless sensor networks: A survey. Wirel. Pers. Commun. 2013, 70, 807–829. [Google Scholar] [CrossRef]
- Afsar, M.M.; Tayarani-N, M.H. Clustering in sensor networks: A literature survey. J. Netw. Comput. Appl. 2014, 46, 198–226. [Google Scholar] [CrossRef]
- Riaz, M.N. Clustering algorithms of wireless sensor networks: A survey. Int. J. Wirel. Microwave Technol. IJWMT 2018, 8, 40–53. [Google Scholar]
- Pantazis, N.A.; Nikolidakis, S.A.; Vergados, D.D. Energy-efficient routing protocols in wireless sensor networks: A survey. IEEE Commun. Surv. Tutor. 2012, 15, 551–591. [Google Scholar] [CrossRef]
- Ramesh, K.; Somasundaram, D.K. A comparative study of clusterhead selection algorithms in wireless sensor networks. arXiv 2012, arXiv:1205.1673. [Google Scholar] [CrossRef]
- Singh, S.P.; Sharma, S.C. A survey on cluster-based routing protocols in wireless sensor networks. Procedia Comput. Sci. 2015, 45, 687–695. [Google Scholar] [CrossRef]
- Arjunan, S.; Pothula, S. A survey on unequal clustering protocols in Wireless Sensor Networks. J. King Saud Univ. Comput. Inf. Sci. 2019, 31, 304–317. [Google Scholar] [CrossRef]
- Dehghani, S.; Pourzaferani, M.; Barekatain, B. Comparison on energy-efficient cluster-based routing algorithms in wireless sensor network. Procedia Comput. Sci. 2015, 72, 535–542. [Google Scholar] [CrossRef]
- Sharma, D.; Ojha, A.; Bhondekar, A.P. Heterogeneity consideration in wireless sensor networks routing algorithms: A review. J. Supercomput. 2019, 75, 2341–2394. [Google Scholar] [CrossRef]
- Liu, X. A survey on clustering routing protocols in wireless sensor networks. Sensors 2012, 12, 11113–11153. [Google Scholar] [CrossRef]
- Kaur, L.; Kad, S. Clustering Techniques in Wireless Sensor Network: A Review. Int. J. Comput. Appl. 2017, 179, 30–34. [Google Scholar]
- Suhail, M. A Survey on Clustering Algorithms of Wireless Sensor Network. Int. J. Adv. Res. Electron. Commun. Eng. 2017, 6, 261–266. [Google Scholar]
- Radha, D.N.; Rashmi, K. Survey on Clustering Algorithms in Wireless Sensor Networks. Int. J. Res. Appl. Sci. Eng. Technol. 2015, 6, 49–52. [Google Scholar]
- Mitra, R.; Nandy, D. A survey on clustering techniques for wireless sensor network. Int. J. Res. Comput. Sci. 2012, 2, 51. [Google Scholar] [CrossRef]
- Santhiya, S.; Thamaraiselvi, A. Survey on Energy Efficient Clustering Algorithms for wireless Sensor Network. Int. J. Latest Trends Eng. Technol. 2013, 3, 57–60. [Google Scholar]
- SheikDawood, M.; Jayalakshmi, P.; Abdul Sikkandhar, R.; Athisha, G. A Survey on Energy Efficient Clustering Protocols for Wireless Sensor Network. Int. J. Comput. Sci. Mob. Comput. 2014, 3, 1158–1163. [Google Scholar]
- Kaur, S.; Mir, R.N. Energy efficiency optimization in wireless sensor network using proposed load balancing approach. Int. J. Comput. Netw. Appl. 2016, 3, 108–117. [Google Scholar] [CrossRef]
- Kumar, V.; Dhok, S.B.; Tripathi, R.; Tiwari, S. A review study of hierarchical clustering algorithms for wireless sensor networks. Int. J. Comput. Sci. Issues 2014, 11, 92. [Google Scholar]
- Nayyar, A.; Singh, R. Ant colony optimization (ACO) based routing protocols for wireless sensor networks (WSN): A survey. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 148–155. [Google Scholar] [CrossRef]
- Gambhir, A.; Payal, A.; Arya, R. Performance analysis of artificial bee colony optimization-based clustering protocol in various scenarios of WSN. Int. Conf. Comput. Intell. Data Sci. 2018, 132, 183–188. [Google Scholar] [CrossRef]
- Wohwe Sambo, D.; Yenke, B.O.; Förster, A.; Dayang, P. Optimized clustering algorithms for large wireless sensor networks: A review. Sensors 2019, 19, 322. [Google Scholar] [CrossRef]
- Wang, L.; Wu, W.; Qi, J.; Jia, Z. Wireless sensor network coverage optimization based on whale group algorithm. Comput. Sci. Inf. Syst. 2018, 15, 569–583. [Google Scholar] [CrossRef]
- Hemalatha, P.; Gnanambigai, J. A Survey on Optimization Techniques in Wireless Sensor Networks. Int. J. Adv. Res. Comput. Eng. Technol. 2015, 4, 4304–4309. [Google Scholar]
- Kaur, P.; Kumar, V. A Survey of Energy Optimization Techniques in Wireless Sensor Networks. Int. J. Adv. Res. Comput. Commun. Eng. 2015, 4, 393–396. [Google Scholar]
- Parwekar, P.; Rodda, S.; Kalla, N. A study of the optimization techniques for wireless sensor networks (WSNs). In Information Systems Design and Intelligent Applications; Springer: Singapore, 2018; pp. 909–915. [Google Scholar]
- More, S.; Nighot, M. Survey paper on Optimization of Wireless Sensor Networks using Artificial Intelligence Techniques. Int. J. Innov. Res. Comput. Commun. Eng. 2016, 4, 21105–21112. [Google Scholar]
- Swati, S.; Kanika, S. Review Paper on Optimization Techniques in Wireless Sensor Network. Int. J. Innov. Res. Electr. Electron. Instrum. Control Eng. 2016, 4, 25–28. [Google Scholar]
- Mangat, V. Survey on particle swarm optimization based clustering analysis. In Swarm and Evolutionary Computation; Springer: Berlin/Heidelberg, Germany, 2012; pp. 301–309. [Google Scholar]
- Ehsan, S.; Hamdaoui, B. A survey on energy-efficient routing techniques with QoS assurances for wireless multimedia sensor networks. IEEE Commun. Surv. Tutor. 2011, 14, 265–278. [Google Scholar] [CrossRef]
- Kandris, D.; Tsioumas, P.; Tzes, A.; Nikolakopoulos, G.; Vergados, D.D. Power conservation through energy efficient routing in wireless sensor networks. Sensors 2009, 9, 7320–7342. [Google Scholar] [CrossRef]
- Kim, J.M.; Seo, H.S.; Kwak, J. Routing protocol for heterogeneous hierarchical wireless multimedia sensor networks. Wirel. Pers. Commun. 2011, 60, 559–569. [Google Scholar] [CrossRef]
- Lin, K.; Rodrigues, J.J.; Ge, H.; Xiong, N.; Liang, X. Energy efficiency QoS assurance routing in wireless multimedia sensor networks. IEEE Syst. J. 2011, 5, 495–505. [Google Scholar] [CrossRef]
- Maimour, M.; Zeghilet, H.; Lepage, F. Cluster-based routing protocols for energy-efficiency in wireless sensor networks. In Proceedings of the 2011 International Conference on Computer Science and Network Technology, Harbin, China, 24–26 December 2010; pp. 167–188. [Google Scholar]
- Goyal, N.; Dave, M.; Verma, A.K. Energy efficient architecture for intra and inter cluster communication for underwater wireless sensor networks. Wirel. Pers. Commun. 2016, 89, 687–707. [Google Scholar] [CrossRef]
- Samant, T.; Mukherjee, P.; Mukherjee, A.; Datta, A. TEEN—V: A solution for intra-cluster cooperative communication in wireless sensor network. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, Tamil Nadu, India, 10–11 February 2017; pp. 209–213. [Google Scholar]
- Zhixiang, D.; Bensheng, Q. Three-layered routing protocol for WSN based on LEACH algorithm. In Proceedings of the IET Conference on Wireless, Mobile and Sensor Networks 2007 (CCWMSN07), Shanghai, China, 12–14 December 2007; pp. 72–75. [Google Scholar]
- Hong, J.; Kook, J.; Lee, S.; Kwon, D.; Yi, S. T-LEACH: The method of threshold-based cluster head replacement for wireless sensor networks. Inf. Syst. Front. 2009, 11, 513. [Google Scholar] [CrossRef]
- Bagherzadeh, J.; Samadzamini, M. A clustering algorithm for wireless sensor networks based on density of sensors. In Proceedings of the 7th International Conference on Advances in Mobile Computing and Multimedia, Kuala Lumpur, Malaysia, 14–16 December 2009; pp. 594–598. [Google Scholar]
- Jia, J.G.; He, Z.W.; Kuang, J.M.; Mu, Y.H. An energy consumption balanced clustering algorithm for wireless sensor network. In Proceedings of the 2010 6th International Conference on Wireless Communications Networking and Mobile Computing (WiCOM), Shenzhen, China, 23–25 September 2010; pp. 1–4. [Google Scholar]
- Kang, S.H.; Nguyen, T. Distance based thresholds for cluster head selection in wireless sensor networks. IEEE Commun. Lett. 2012, 16, 1396–1399. [Google Scholar] [CrossRef]
- Wang, A.; Yang, D.; Sun, D. A clustering algorithm based on energy information and cluster heads expectation for wireless sensor networks. Comput. Electr. Eng. 2012, 38, 662–671. [Google Scholar] [CrossRef]
- Mahmood, D.; Javaid, N.; Mahmood, S.; Qureshi, S.; Memon, A.M.; Zaman, T. MODLEACH: A variant of LEACH for WSNs. In Proceedings of the 2013 Eighth International Conference on Broadband and Wireless Computing, Communication and Applications, Compiegne, France, 28–30 October 2013; pp. 158–163. [Google Scholar]
- Chang, R.S.; Kuo, C.J. An energy efficient routing mechanism for wireless sensor networks. In Proceedings of the 20th International Conference on Advanced Information Networking and Applications-Volume 1 (AINA’06), Vienna, Austria, 18–20 April 2006; Volume 2, p. 5. [Google Scholar]
- Liu, T.; Li, F. Power-efficient clustering routing protocol based on applications in wireless sensor network. In Proceedings of the 2009 5th International Conference on Wireless Communications, Networking and Mobile Computing, Beijing, China, 24–26 September 2009; pp. 1–6. [Google Scholar]
- Kumar, D.; Aseri, T.C.; Patel, R. EEHC: Energy efficient heterogeneous clustered scheme for wireless sensor networks. Comput. Commun. 2009, 32, 662–667. [Google Scholar] [CrossRef]
- Tao, Y.; Zhang, Y.; Ji, Y. Flow-balanced routing for multi-hop clustered wireless sensor networks. Ad Hoc Netw. 2013, 11, 541–554. [Google Scholar] [CrossRef]
- Yin, G.; Yang, G.; Yang, W.; Zhang, B.; Jin, W. An energy-efficient routing algorithm for wireless sensor networks. In Proceedings of the 2008 International Conference on Internet Computing in Science and Engineering, Harbin, China, 28–29 January 2008; pp. 181–186. [Google Scholar]
- Agrawal, T.; Kushwah, R.S. Layered Clustering Routing Protocol with Overlapping Cluster Heads in WSN. In Proceedings of the 2015 Fifth International Conference on Communication Systems and Network Technologies, Gwalior, India, 4–6 April 2015; pp. 244–248. [Google Scholar]
- Cengiz, K.; Dağ, T. Low energy fixed clustering algorithm (LEFCA) for wireless sensor networks. In Proceedings of the 2015 International Conference on Computing and Network Communications (CoCoNet), Trivandrum, India, 16–19 December 2015; pp. 79–84. [Google Scholar]
- Yi, D.; Yang, H. HEER–A delay-aware and energy-efficient routing protocol for wireless sensor networks. Comput. Netw. 2016, 104, 155–173. [Google Scholar] [CrossRef]
- Shahraki, A.; Rafsanjani, M.K.; Saeid, A.B. Hierarchical distributed management clustering protocol for wireless sensor networks. Telecommun. Syst. 2017, 65, 193–214. [Google Scholar] [CrossRef]
- Cengiz, K.; Dag, T. Energy aware multi-hop routing protocol for WSNs. IEEE Access 2017, 6, 2622–2633. [Google Scholar] [CrossRef]
- Gajjar, S.; Sarkar, M.; Dasgupta, K. FAMACROW: Fuzzy and ant colony optimization based combined mac, routing, and unequal clustering cross-layer protocol for wireless sensor networks. Appl. Soft Comput. 2016, 43, 235–247. [Google Scholar] [CrossRef]
- Zahedi, Z.M.; Akbari, R.; Shokouhifar, M.; Safaei, F.; Jalali, A. Swarm intelligence based fuzzy routing protocol for clustered wireless sensor networks. Expert Syst. Appl. 2016, 55, 313–328. [Google Scholar] [CrossRef]
- Shokouhifar, M.; Jalali, A. Optimized sugeno fuzzy clustering algorithm for wireless sensor networks. Eng. Appl. Artif. Intell. 2017, 60, 16–25. [Google Scholar] [CrossRef]
- Fanian, F.; Rafsanjani, M.K. Memetic fuzzy clustering protocol for wireless sensor networks: Shuffled frog leaping algorithm. Appl. Soft Comput. 2018, 71, 568–590. [Google Scholar] [CrossRef]
- Ran, G.; Zhang, H.; Gong, S. Improving on LEACH protocol of wireless sensor networks using fuzzy logic. J. Inf. Comput. Sci. 2010, 7, 767–775. [Google Scholar]
- Bagci, H.; Yazici, A. An energy aware fuzzy approach to unequal clustering in wireless sensor networks. Appl. Soft Comput. 2013, 13, 1741–1749. [Google Scholar] [CrossRef]
- Sert, S.A.; Bagci, H.; Yazici, A. MOFCA: Multi-objective fuzzy clustering algorithm for wireless sensor networks. Appl. Soft Comput. 2015, 30, 151–165. [Google Scholar] [CrossRef]
- Gajjar, S.; Talati, A.; Sarkar, M.; Dasgupta, K. FUCP: Fuzzy based unequal clustering protocol for wireless sensor networks. In Proceedings of the 2015 39th National Systems Conference (NSC), Greater Noida, India, 14–16 December 2015; pp. 1–6. [Google Scholar]
- Logambigai, R.; Kannan, A. Fuzzy logic based unequal clustering for wireless sensor networks. Wirel. Netw. 2016, 22, 945–957. [Google Scholar] [CrossRef]
- Baranidharan, B.; Santhi, B. DUCF: Distributed load balancing unequal clustering in wireless sensor networks using fuzzy approach. Appl. Soft Comput. 2016, 40, 495–506. [Google Scholar] [CrossRef]
- Sundaran, K.; Ganapathy, V.; Sudhakara, P. Fuzzy logic based unequal clustering in wireless sensor network for minimizing energy consumption. In Proceedings of the 2017 2nd International Conference on Computing and Communications Technologies (ICCCT), Chennai, India, 23–24 February 2017; pp. 304–309. [Google Scholar]
- Yang, J.; Xu, M.; Zhao, W.; Xu, B. A multipath routing protocol based on clustering and ant colony optimization for wireless sensor networks. Sensors 2010, 10, 4521–4540. [Google Scholar] [CrossRef]
- Mittal, N.; Singh, U.; Sohi, B.S. An energy-aware cluster-based stable protocol for wireless sensor networks. Neural Comput. Appl. 2019, 31, 7269–7286. [Google Scholar] [CrossRef]
- Oladimeji, M.O.; Turkey, M.; Dudley, S. HACH: Heuristic Algorithm for Clustering Hierarchy protocol in wireless sensor networks. Appl. Soft Comput. 2017, 55, 452–461. [Google Scholar] [CrossRef]
- Hoang, D.C.; Yadav, P.; Kumar, R.; Panda, S.K. Real-time implementation of a harmony search algorithm-based clustering protocol for energy-efficient wireless sensor networks. IEEE Trans. Ind. Inform. 2013, 10, 774–783. [Google Scholar] [CrossRef]
- Mittal, N.; Singh, U.; Sohi, B.S. A stable energy efficient clustering protocol for wireless sensor networks. Wirel. Netw. 2017, 23, 1809–1821. [Google Scholar] [CrossRef]
- Kumar, D. Performance analysis of energy efficient clustering protocols for maximising lifetime of wireless sensor networks. IET Wirel. Sens. Syst. 2013, 4, 9–16. [Google Scholar] [CrossRef]
- Mittal, N.; Singh, U. Distance-based residual energy-efficient stable election protocol for WSNs. Arab. J. Sci. Eng. 2015, 40, 1637–1646. [Google Scholar] [CrossRef]
- Behera, T.M.; Mohapatra, S.K.; Samal, U.C.; Khan, M.S.; Daneshmand, M.; Gandomi, A.H. Residual energy-based cluster-head selection in WSNs for IoT application. IEEE Internet Things J. 2019, 6, 5132–5139. [Google Scholar] [CrossRef]
- Behera, T.M.; Mohapatra, S.K.; Samal, U.C.; Khan, M.S.; Daneshmand, M.; Gandomi, A.H. I-sep: An improved routing protocol for heterogeneous WSN for IoT-based environmental monitoring. IEEE Internet Things J. 2019, 7, 710–717. [Google Scholar] [CrossRef]
- Gandomi, A.H.; Yang, X.S.; Talatahari, S.; Alavi, A.H. (Eds.) Metaheuristic Applications in Structures and Infrastructures; Elsevier: Waltham, MA, USA, 2013; pp. 1–23. [Google Scholar]












| S. No. | Names of Algorithms | Energy Consumed | Energy Efficiency | Network Delay | Network Throughput | Network Loss | Overall QoS |
|---|---|---|---|---|---|---|---|
| 1 | LEACH [28] | Moderate | Moderate | Moderate | Moderate | High | Moderate |
| 2 | TL-LEACH [73] | Low | High | Moderate | High | Moderate | Moderate |
| 3 | T-LEACH [74] | Low | High | Moderate | High | Moderate | High |
| 4 | DS-LEACH [75] | Low | High | Moderate | High | Low | High |
| 5 | LEACH-EP [76] | Low | High | Moderate | High | Moderate | Moderate |
| 6 | LEACH-DT [77] | Low | High | Moderate | High | Moderate | Moderate |
| 7 | LEACHSWDN [78] | Low | High | Moderate | High | Low | Moderate |
| 8 | MODLEACH [79] | Moderate | Moderate | Moderate | Low | Low | High |
| 9 | MECH [80] | Low | High | Moderate | High | Moderate | Moderate |
| 10 | PECRP [81] | Low | High | Moderate | High | Low | High |
| 11 | EEHC [82] | Low | High | Moderate | High | Low | High |
| 12 | FBR [83] | High | Low | Moderate | Low | Low | High |
| 13 | EERA [84] | High | Low | Moderate | Low | Low | High |
| 14 | LCRPOCH [85] | Low | High | Moderate | Low | Moderate | Moderate |
| 15 | LEFCA [86] | Low | High | Moderate | Low | Moderate | Moderate |
| 16 | HEER [87] | Low | High | Moderate | Low | Low | Moderate |
| 17 | HDMC [88] | Moderate | Moderate | Moderate | Low | Low | Moderate |
| 18 | EAMR [89] | Low | High | Moderate | Low | Low | Moderate |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Manuel, A.J.; Deverajan, G.G.; Patan, R.; Gandomi, A.H. Optimization of Routing-Based Clustering Approaches in Wireless Sensor Network: Review and Open Research Issues. Electronics 2020, 9, 1630. https://doi.org/10.3390/electronics9101630
Manuel AJ, Deverajan GG, Patan R, Gandomi AH. Optimization of Routing-Based Clustering Approaches in Wireless Sensor Network: Review and Open Research Issues. Electronics. 2020; 9(10):1630. https://doi.org/10.3390/electronics9101630
Chicago/Turabian StyleManuel, Asha Jerlin, Ganesh Gopal Deverajan, Rizwan Patan, and Amir H. Gandomi. 2020. "Optimization of Routing-Based Clustering Approaches in Wireless Sensor Network: Review and Open Research Issues" Electronics 9, no. 10: 1630. https://doi.org/10.3390/electronics9101630
APA StyleManuel, A. J., Deverajan, G. G., Patan, R., & Gandomi, A. H. (2020). Optimization of Routing-Based Clustering Approaches in Wireless Sensor Network: Review and Open Research Issues. Electronics, 9(10), 1630. https://doi.org/10.3390/electronics9101630







