An Anomaly Mitigation Framework for IoT Using Fog Computing
Abstract
1. Introduction
- We proposed a hybrid anomaly mitigation framework for IoT networks using fog computing, which harnesses the resources of the fog. The framework employs signature-based and anomaly-based modules to ensure faster and accurate attack detection.
- In the proposed framework, we have used a blacklist of IP addresses in our signature-based module and an Extreme Gradient Boosting (XGBoost) [9] classifier for the anomaly-based module due to its resilience against overfitting. The performance of the blacklist look-up and XGBoost classifier was evaluated in terms of response time and classification accuracy (binary and multiclass) using the BoT-IoT dataset, respectively. The results show that the signature-based module detects attacks fast. Similarly, the XGBoost classifier has a superior performance over other classifier algorithms such as Decision Tree (DT) [10], k Nearest Neighbors (k-NN) [11], and Naïve Bayes (NB) [12].
- A review and comparison of some proposed state of the art anomaly mitigation schemes in IoT are provided. The review covers the objectives, operational procedures as well as the strength of each scheme, while the comparison is in terms of detection methodology, techniques employed, evaluation strategy used, attacks detected, and dataset utilized for evaluations.
2. Background
2.1. Internet of Things (IoT)
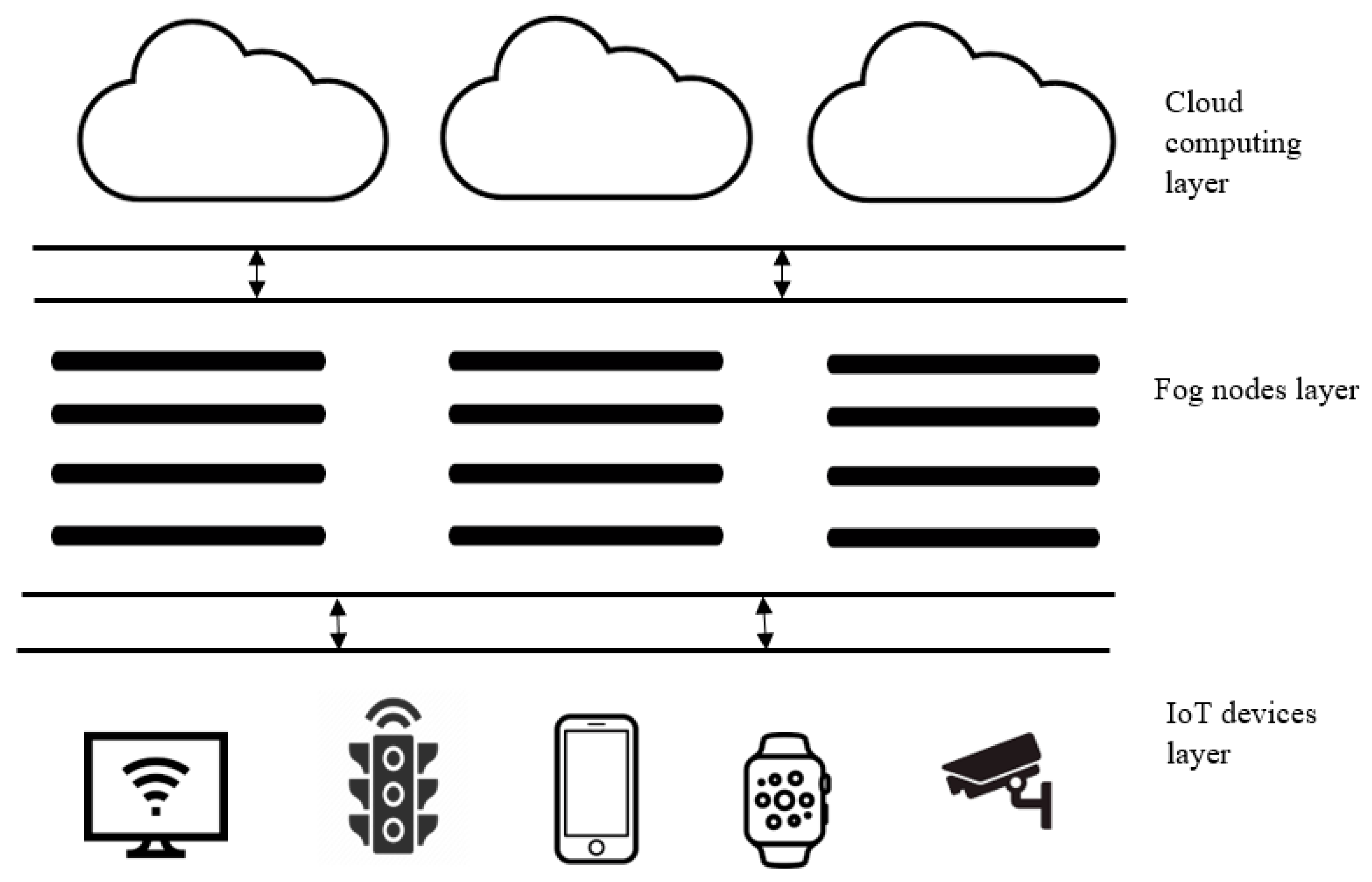
2.2. Fog Computing
2.3. Intrusion Detection System (IDS)
3. Related Work
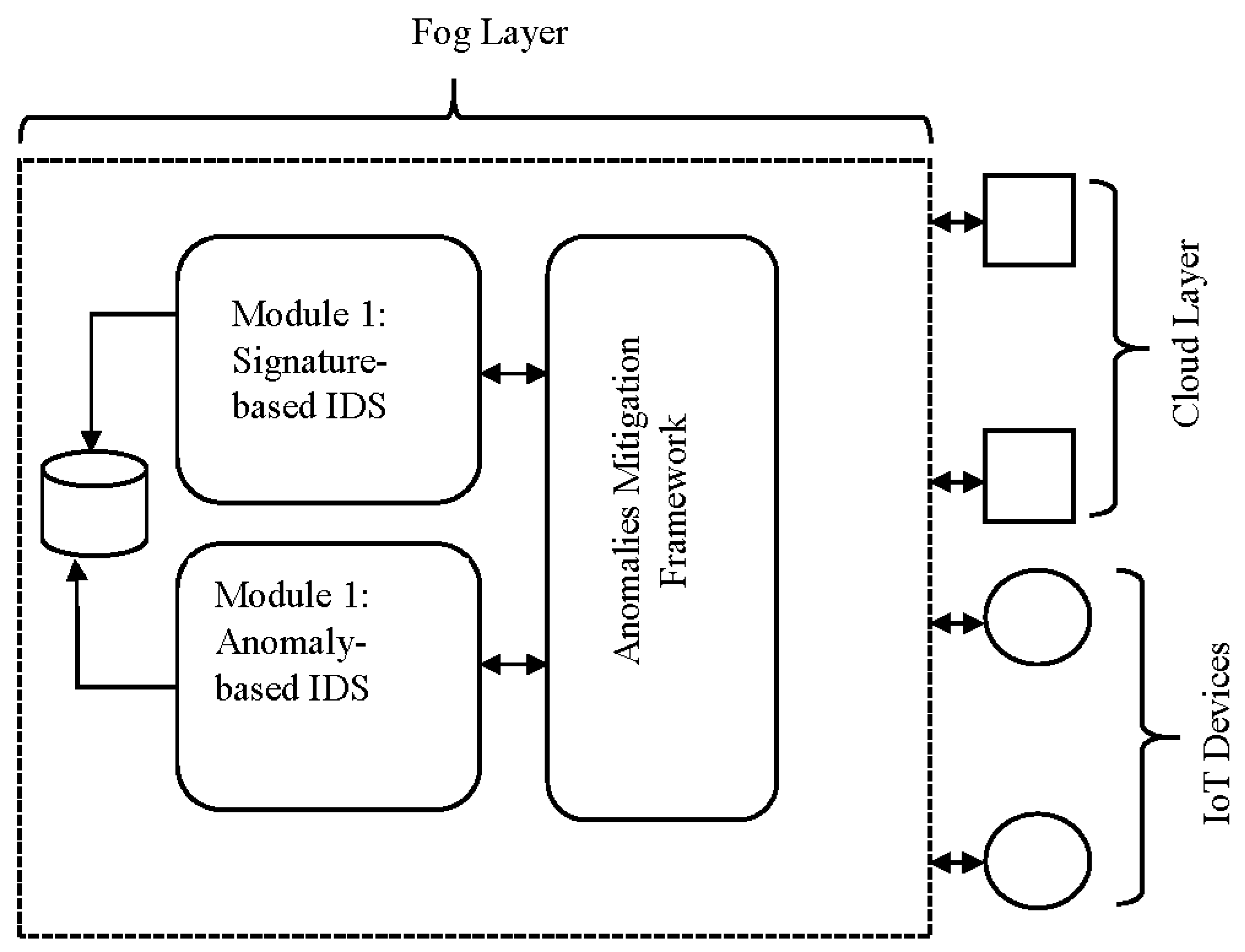
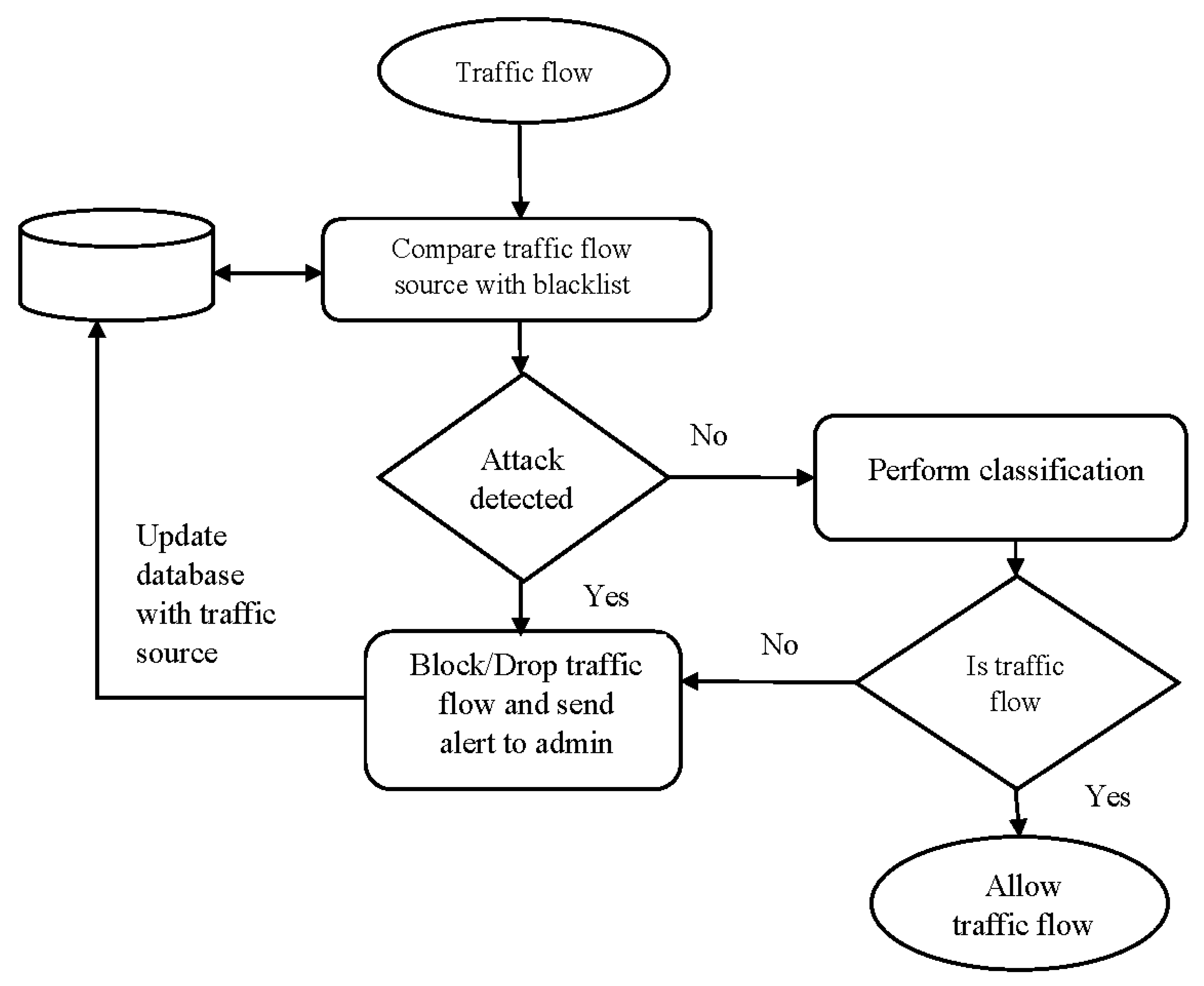
4. Proposed Framework
4.1. Use Case on the Application of the Fog Computing Framework and the Anomaly Mitigation
4.2. Extreme Gradient Boosting
5. Performance Evaluation
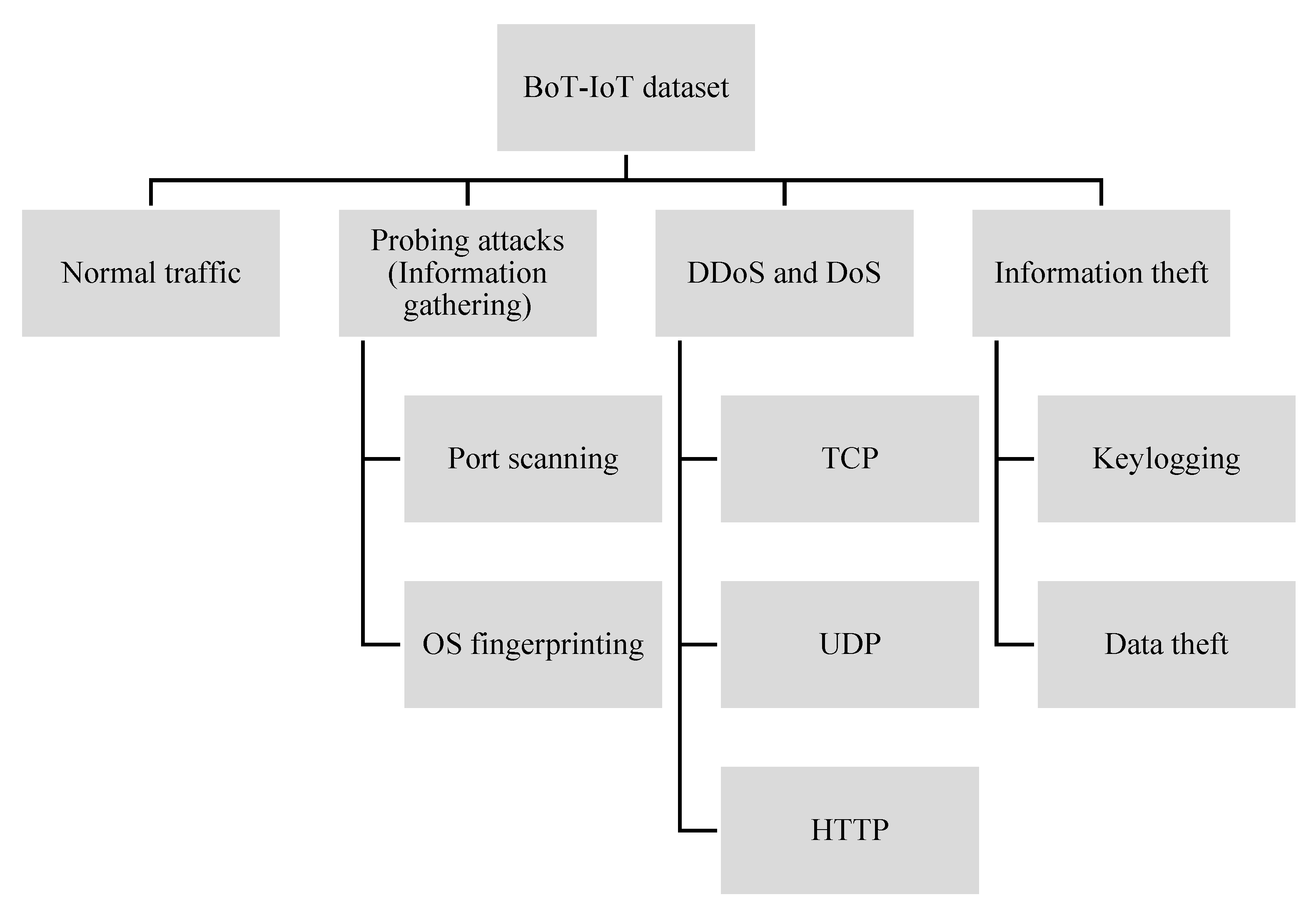
5.1. Description of the Dataset
- Normal Traffic: Normal traffic consists of legitimate network transactions. The dataset contains legitimate traffic flows generated from the virtual machines using the Ostinato tool [47].
- Probing attacks [42]: A probing attack, also called an information gathering attack, involves the process applied by malicious users in collecting information illegitimately from remote systems through scanning or fingerprinting. The BoT-IoT dataset contains two types of probing attacks which are: port scanning and OS fingerprinting. The port scanning attack instances are generated using the Nmap [42] and Hping3 [48] tools, while the fingerprinting was performed using Nmap [49] and Xprobe2 [50] tools.
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks [42]: These attacks involve the process employed by malicious users to deny legitimate users access to resources or services by overwhelming these resources or services with illegitimate requests. The attacks are usually executed using botnets, which are a collection of compromised nodes in the network. The dataset contains DoS and DDoS attacks instances based on HTTP, TCP, and UDP protocols. The TCP and UDP DoS and DDoS attacks were generated using the Hping3 [48] tool, while the HTTP DoS and DDoS attacks were generated using the Golden-eye tool.
- Information theft [42]: An information theft attack is a process employed by malicious users to violate the security of the system to obtain confidential or sensitive data. The dataset contains two types of information theft attacks, which are data theft and keylogging. These attacks were executed using the Metasploit framework [51].
5.2. Performance Metrics
- True Positive (TP): Total actual positive observations that are predicted positive.
- False Positive (FP): Total actual negative observations that are predicated positive.
- True Negative (TN): Total actual negative observations that are predicted negative.
- False Negative (FN): Total actual positive observations that are predicted negative.
- Accuracy is the ratio of the overall positive observations to the total observations; it shows the general success rate of any IDS, and is computed as,Accuracy = (TN + TP)/(TP + FP + TN + FN)
- The Detection Rate (DR), also called the true positive rate (TPR) or recall, is the ratio of correctly classified malicious observations to the total number of malicious observations and is computed as,DR = TP/(FN + TP)
- The False Positive Rate (FPR), also called the false alarm rate, is the ratio of normal observations to the total number of normal observations misclassified as attacks and is computed as,FPR = FP/(FP + TN)
- The False Negative Rate (FNR), also called precision, is the ratio of misclassified attack observations to the total number of attack observations, given as,FNR = FN/(FN + TP)
- The F1 Score is the weighted average of the recall and the precision, and is computed as,F1 Score = 2 × (Recall × Precision)/(Recall + Precision)
5.3. Evaluation Methodology
5.4. Results and Discussion
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Pacheco, J.; Hariri, S. Anomaly behavior analysis for IoT sensors. Trans. Emerg. Telecommun. Technol. 2018, 29, 1–15. [Google Scholar] [CrossRef]
- Ahmad, M.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar]
- Hoang, D.H.; Nguyen, H.D. A PCA-based method for IoT network traffic anomaly detection. In Proceedings of the International Conference on Advanced Communication Technology, ICACT, Chuncheon-si Gangwon-do, Korea, 11–14 February 2018; Volume 2018, pp. 381–386. [Google Scholar]
- Moustafa, N.; Hu, J.; Slay, J. A holistic review of Network Anomaly Detection Systems: A comprehensive survey. J. Netw. Comput. Appl. 2019, 128, 33–55. [Google Scholar] [CrossRef]
- Acarali, D.; Rajarajan, M.; Komninos, N.; Herwono, I. Survey of approaches and features for the identification of HTTP-based botnet traffic. J. Netw. Comput. Appl. 2016, 76, 1–15. [Google Scholar] [CrossRef]
- Simonovich, V. Imperva Blocks Our Largest DDoS L7/Brute Force Attack Ever (Peaking at 292,000 RPS). Available online: https://www.imperva.com/blog/imperva-blocks-our-largest-ddos-l7-brute-force-attack-ever-peaking-at-292000-rps (accessed on 18 December 2019).
- Asokan, A. Massive Botnet Attack Used More Than 400,000 IoT Devices. Available online: https://www.bankinfosecurity.com/massive-botnet-attack-used-more-than-400000-iot-devices-a-12841 (accessed on 18 December 2019).
- Yaseen, Q.; Albalas, F.; Jararwah, Y.; Al-Ayyoub, M. Leveraging fog computing and software defined systems for selective forwarding attacks detection in mobile wireless sensor networks. Trans. Emerg. Telecommun. Technol. 2018, 29, e3183. [Google Scholar] [CrossRef]
- Chen, T.; Guestrin, C. XGBoost: A Scalable Tree Boosting System. In Proceedings of the 22nd Acm Sigkdd International Conference on Knowledge Discovery and Data Mining, San Francisco, CA, USA, 13–17 August 2016; ACM: New York, NY, USA, 2016; pp. 785–794. [Google Scholar]
- Quinlan, J.R. C4. 5: Programs for Machine Learning; Morgan Kaufmann Publishers Inc.: San Francisco, CA, USA, 1993. [Google Scholar]
- Fix, E.; Hodges, J.L. Discriminatory Analysis. Nonparametric Discrimination; Consistency Properties; Technical Report 4; USAF School of Aviation Medicine Randolph Field: San Antonio, TX, USA, 1951. [Google Scholar]
- Zhang, H. Exploring conditions for the optimality of naïve bayes. Int. J. Pattern Recognit. Artif. Intell. 2005, 19, 183–198. [Google Scholar] [CrossRef]
- Elrawy, M.F.; Awad, A.I. Intrusion detection systems for IoT-based smart environments: A survey. J. Cloud Comput. Adv. Syst. Appl. 2018, 7, 21. [Google Scholar] [CrossRef]
- Minerva, R.; Biru, A.; Rotondi, D. Towards a definition of the Internet of Things (IoT). IEE Internet Initiat. 2015, 1, 1–86. [Google Scholar]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Futur. Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Ammar, M.; Russello, G.; Crispo, B. Internet of Things: A survey on the security of IoT frameworks. J. Inf. Secur. Appl. 2018, 38, 8–27. [Google Scholar] [CrossRef]
- Khattak, H.A.; Shah, M.A.; Khan, S.; Ali, I.; Imran, M. Perception layer security in Internet of Things. Futur. Gener. Comput. Syst. 2019, 100, 144–164. [Google Scholar] [CrossRef]
- Al-fuqaha, A.; Member, S.; Guizani, M.; Mohammadi, M.; Member, S. Internet of Things: A Survey on Enabling. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog Computing and Its Role in the Internet of Things. In Proceedings of the First Edition Workshop on Mobile Cloud Computing (MCC), Helsinki, Finland, 17 August 2012; ACM: New York, NY, USA, 2012; pp. 13–16. [Google Scholar]
- Rathore, S.; Park, J.H. Semi-supervised learning based distributed attack detection framework for IoT. Appl. Soft Comput. J. 2018, 72, 79–89. [Google Scholar] [CrossRef]
- Neware, R.; Shrawankar, U. Fog Computing Architecture, Applications and Security Issues: A Survey. Int. J. Fog Comput. 2020, 3, 75–105. [Google Scholar] [CrossRef]
- Raza, S.; Wallgren, L.; Voigt, T. SVELTE: Real-time intrusion detection in the Internet of Things. Ad Hoc Netw. 2013, 11, 2661–2674. [Google Scholar] [CrossRef]
- Shaikh, R.A.; Jameel, H.; d’Auriol, B.J.; Lee, H.; Lee, S.; Song, Y.J. Intrusion-aware alert validation algorithm for cooperative distributed intrusion detection schemes of wireless sensor networks. Sensors 2009, 9, 5989–6007. [Google Scholar] [CrossRef]
- L-Hawawreh, M.A.; Moustafa, N.; Sitnikova, E. Identification of malicious activities in industrial internet of things based on deep learning models. J. Inf. Secur. Appl. 2018, 41, 1–11. [Google Scholar]
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Lawal, M.A.; Shaikh, R.A.; Hassan, S.R. Security Analysis of Network Anomalies Mitigation Schemes in IoT Networks. IEEE Access 2020, 8, 43355–43374. [Google Scholar] [CrossRef]
- Sforzin, A.; Marmol, F.G.; Conti, M.; Bohli, J.M. RPiDS: Raspberry Pi IDS—A Fruitful Intrusion Detection System for IoT. In Proceedings of the 2016 Intl IEEE Conferences on Ubiquitous Intelligence Computing, Advanced and Trusted Computing, Scalable Computing and Communications, Cloud and Big Data Computing, Internet of People, and Smart World Congress (UIC/ATC/ScalCom/CBDCom/IoP/SmartWorld), Toulouse, France, 18–21 July 2016; pp. 440–448. [Google Scholar]
- Ioulianou, P.P.; Vassilakis, V.G.; Moscholios, I.D.; Logothetis, M.D. A Signature-based Intrusion Detection System for the Internet of Things. In Proceedings of the Information and Communication Technology Forum (ICTF), Graz, Austria, 11–13 July 2018. [Google Scholar]
- Kasinathan, P.; Pastrone, C.; Spirito, M.A.; Vinkovits, M. Denial-of-Service detection in 6LoWPAN based Internet of Things. In Proceedings of the International Conference on Wireless and Mobile Computing, Networking and Communications, Lyon, France, 7–9 October 2013; pp. 600–607. [Google Scholar]
- Ullah, I.; Mahmoud, Q.H. A Two-Level Hybrid Model for Anomalous Activity Detection in IoT Networks. In Proceedings of the 2019 16th IEEE Annual Consumer Communications and Networking Conference, CCNC 2019, Las Vegas, NV, USA, 11–14 January 2019; pp. 1–6. [Google Scholar]
- Jan, S.U.; Ahmed, S.; Shakhov, V.; Koo, I. Toward a Lightweight Intrusion Detection System for the Internet of Things. IEEE Access 2019, 7, 42450–42471. [Google Scholar] [CrossRef]
- Deshmukh-Bhosale, S.; Sonavane, S.S. A Real-Time Intrusion Detection System for Wormhole Attack in the RPL based Internet of Things. Procedia Manuf. 2019, 32, 840–847. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Slowinska, M.; Theodorakopoulos, G.; Burnap, P. A Supervised Intrusion Detection System for Smart Home IoT Devices. IEEE Internet Things J. 2019, 6, 9042–9053. [Google Scholar] [CrossRef]
- Otoum, Y.; Liu, D.; Nayak, A. DL-IDS: A deep learning–based intrusion detection framework for securing IoT. Trans. Emerg. Telecommun. Technol. 2019, e3803. [Google Scholar] [CrossRef]
- Verma, A.; Ranga, V. ELNIDS: Ensemble Learning based Network Intrusion Detection System for RPL based Internet of Things. In Proceedings of the 4th International Conference on Internet of Things: Smart Innovation and Usages, IoT-SIU 2019, Ghaziabad, India, 18–19 April 2019. [Google Scholar]
- Napiah, M.N.; Idris, M.Y.I.B.; Ramli, R.; Ahmedy, I. Compression Header Analyzer Intrusion Detection System (CHA - IDS) for 6LoWPAN Communication Protocol. IEEE Access 2018, 6, 16623–16638. [Google Scholar] [CrossRef]
- Alrashdi, I.; Alqazzaz, A.; Aloufi, E.; Alharthi, R.; Zohdy, M.; Ming, H. AD-IoT: Anomaly detection of IoT cyberattacks in smart city using machine learning. In Proceedings of the IEEE 9th Annual Computing and Communication Workshop and Conference, CCWC 2019, Las Vegas, NV, USA, 7–9 January 2019; pp. 305–310. [Google Scholar]
- Lyu, L.; Jin, J.; Rajasegarar, S.; He, X.; Palaniswami, M. Fog-Empowered Anomaly Detection in Internet of Things using Hyperellipsoidal Clustering. IEEE Internet Things J. 2017, 4, 1174–1184. [Google Scholar] [CrossRef]
- Diro, A.A.; Chilamkurti, N. Distributed attack detection scheme using deep learning approach for Internet of Things. Futur. Gener. Comput. Syst. 2018, 82, 761–768. [Google Scholar]
- Dhaliwal, S.S.; Al-Nahid, A.; Abbas, R. Effective Intrusion Detection System Using XGBoost. Information 2018, 9, 149. [Google Scholar]
- Chatterjee, D.R. Log Book—XGBoost, the Math behind the Algorithm. Available online: https://towardsdatascience.com/log-book-xgboost-the-math-behind-the-algorithm-54ddc5008850 (accessed on 11 September 2020).
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the Internet of Things for network forensic analytics: Bot-IoT dataset. Futur. Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Node-Red, Node Red Tool. Available online: https://nodered.org/ (accessed on 4 December 2019).
- Eclipse, Mosquitto MQTT Broker. Available online: https://mosquitto.org/ (accessed on 4 December 2019).
- Argus Tool. Available online: https://qosient.com/argus/index.shtm (accessed on 1 December 2019).
- Cron Scheduling Package. Available online: https://packages.ubuntu.com/search?keywords=cron (accessed on 3 December 2019).
- Ostinato Tool. Available online: https://ostinato.org (accessed on 30 November 2019).
- Hping. Available online: http://www.hping.org (accessed on 30 November 2019).
- Lyon, G.F. Nmap Network Scanning: The Offcial Nmap Project Guide to Network Discovery and Security Scanning; Insecure: Los Angeles, CA, USA, 2009. [Google Scholar]
- Xprobe2. Available online: https://www.aldeid.com/wiki/Xprobe2 (accessed on 29 November 2019).
- Metasploit Framework. Available online: https://www.metasploit.com (accessed on 30 November 2019).
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. Network Anomaly Detection: Methods, Systems and Tools. IEEE Commun. Surv. Tutor. 2014, 6, 303–336. [Google Scholar]
- Hall, G. Pearson’s correlation coefficient. Other Words 2015, 1, 1–4. [Google Scholar]
- Lesne, A.; Etudes, H. Shannon entropy: A rigorous mathematical notion at the crossroads between probability, information theory, dynamical systems and statistical physics. Math. Struct. Comput. Sci. 2014, 24. [Google Scholar] [CrossRef]
- Lundberg, S.M.; Erion, G.G.; Lee, S. Consistent Individualized Feature Attribution for Tree Ensembles. arXiv 2019, arXiv:1802.03888. [Google Scholar]
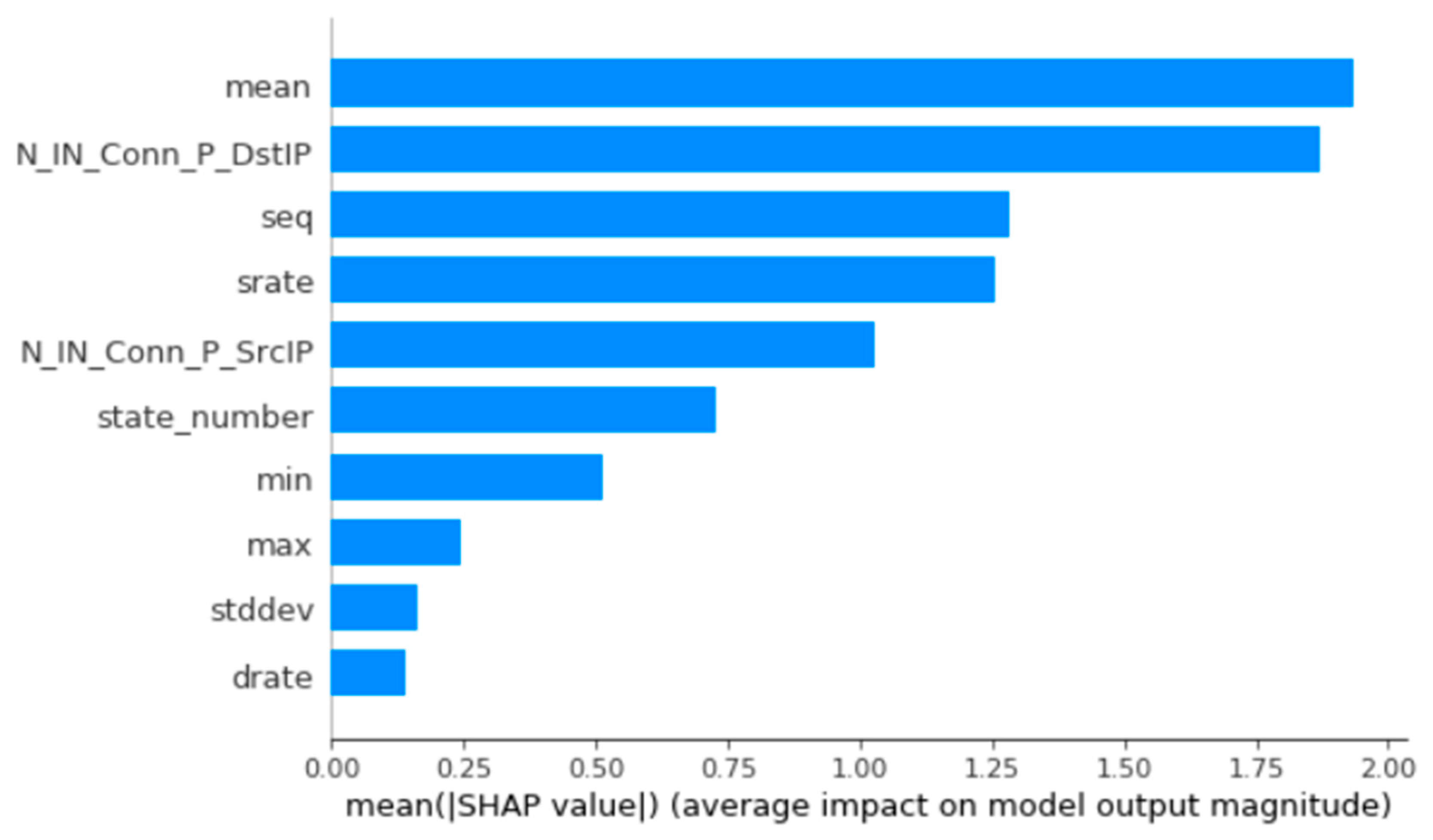
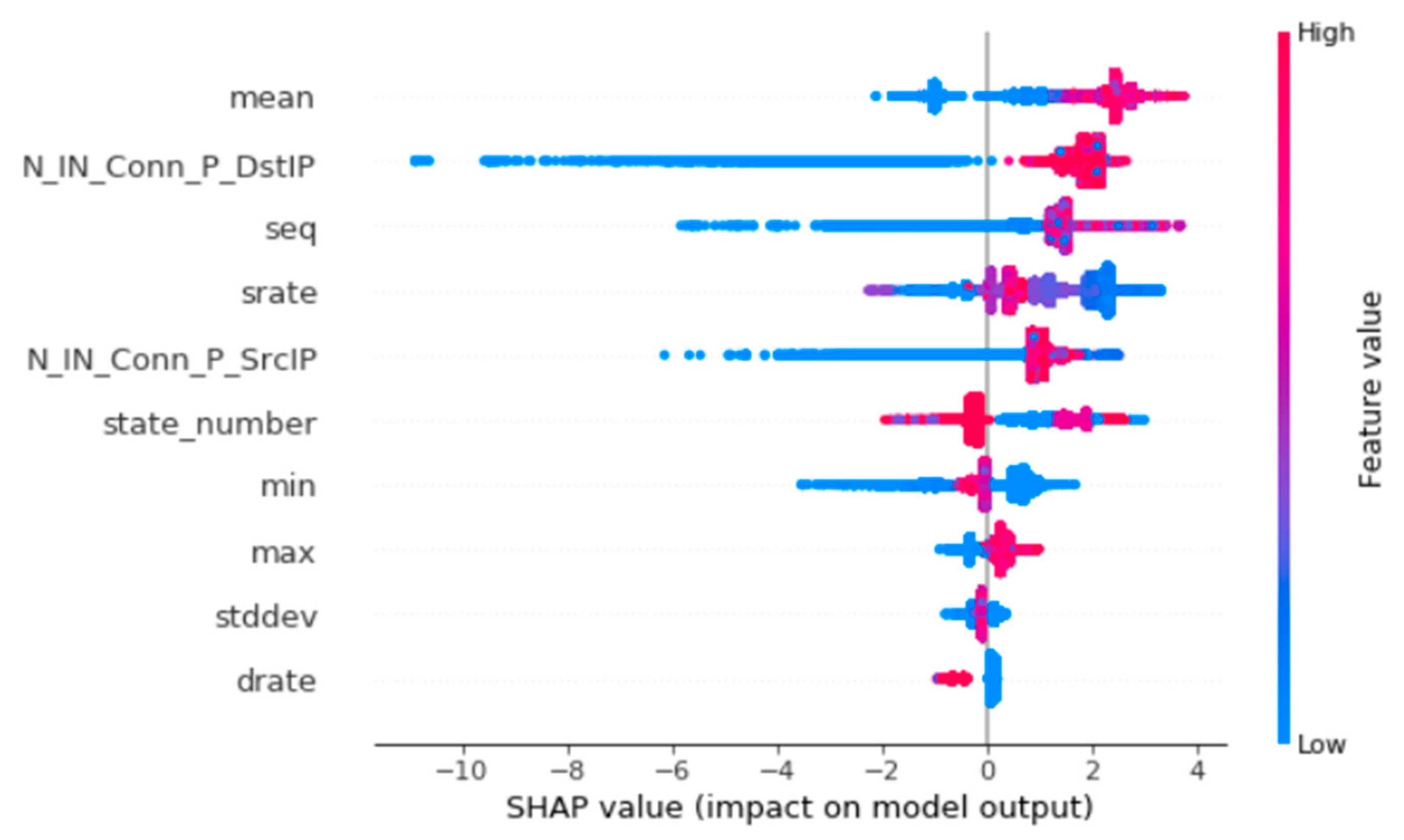
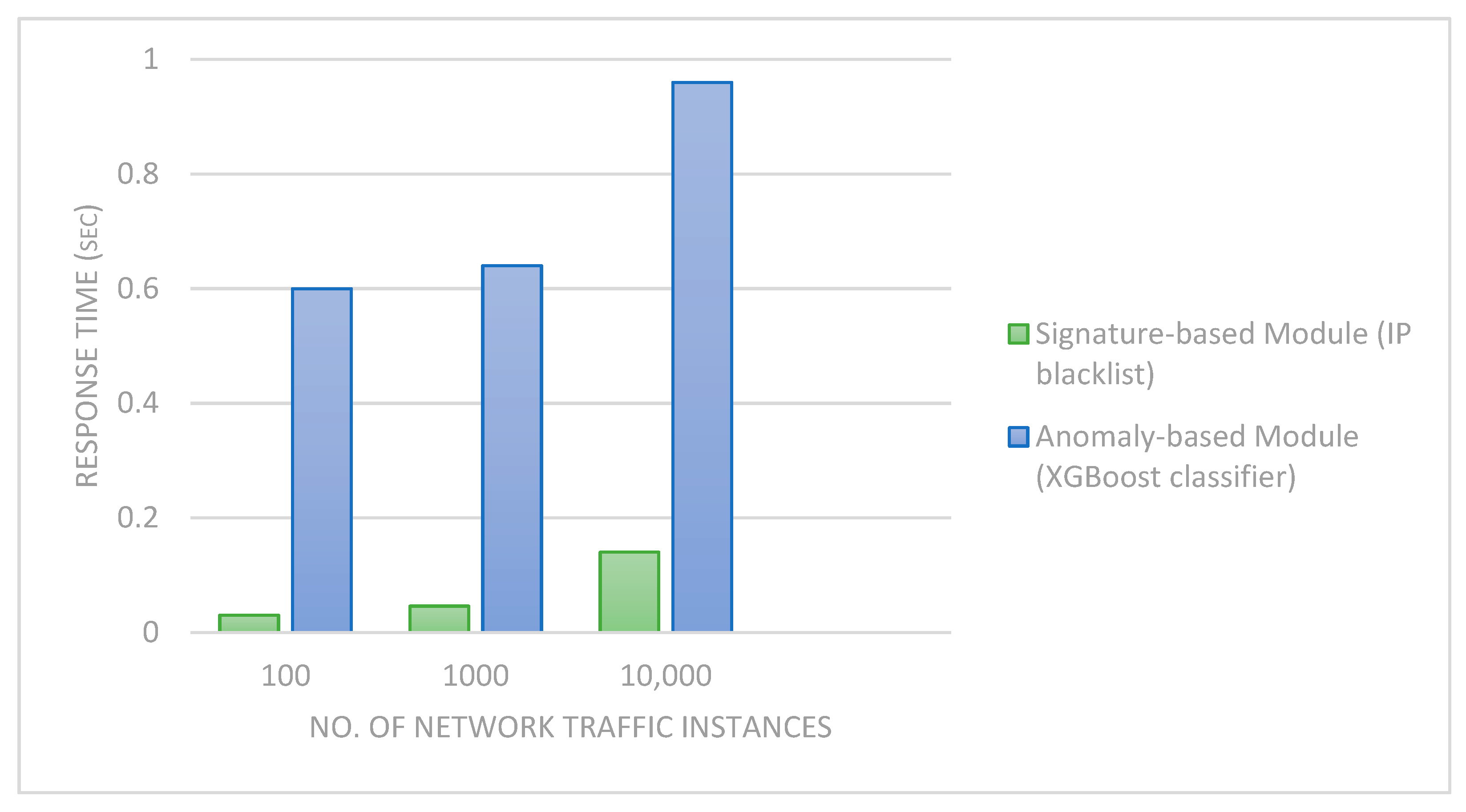
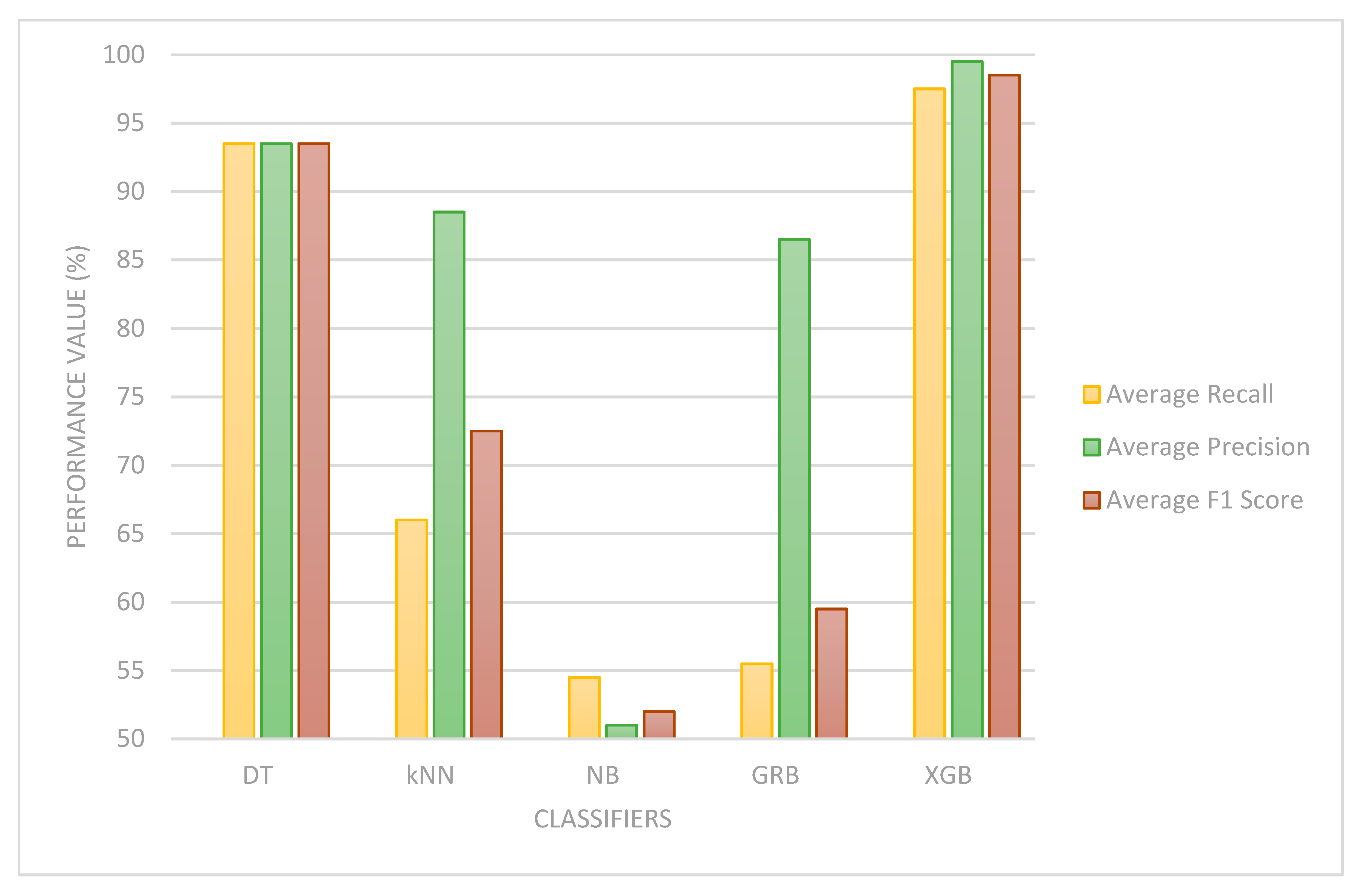

| S/No | Scheme | Detection Methodology | Technique | Evaluation Strategy | Attacks Detected | Dataset |
|---|---|---|---|---|---|---|
| 1 | A signature-based intrusion detection system (2018) [28] | Signature-based | Routing protocol information | Simulation | i. Hello flooding ii. Version number modification | N/A |
| 2 | A Raspberry Pi Intrusion Detection System (RPiIDS) (2016) [27] | Signature-based | Snort | Experiments | Not specified | N/A |
| 3 | A Denial-of-Service detection scheme (ebbits, 2013) [29] | Signature-based | Suricata (Packet threshold rule) | Simulation | DoS | N/A |
| 4 | A two-level hybrid model for anomalous activity detection scheme [30] | Anomaly-based | i. Decision Tree ii. Random Forest iii. RFE iv. SMOTE | Experiment | Attacks in the dataset | i. UNSW-NB 15 ii.CICIDS2017 |
| 5 | A lightweight IDS scheme [31] | Anomaly-based | SVM | i. Simulation ii. Experiments | DDoS | CICIDS2017 |
| 6 | A real-time IDS scheme [32] | Anomaly-based | i. Routing information ii. RSSI | Simulation | Wormhole | N/A |
| 7 | A supervised IDS scheme [33] | Anomaly-based | Decision Tree | Experiments | i. DoS ii. MITM iii. Reconnaissance iv. Replay | Generated from the experiment testbed. |
| 8 | A Deep Learning Intrusion Detection System (DL-IDS) scheme [34] | Anomaly-based | i. k-NN ii. SMO iii. SPDN | Experiments | i. DoS ii. Probe iii.R2L iv.U2R | NSL KDD |
| 9 | An Ensemble Learning based Network Intrusion Detection System (ELNIDS) scheme [35] | Anomaly-based | Ensemble ML | Experiments | Routing attacks. | RPL-NIDDS17 |
| 10 | SVELTE (2013) [22] | Hybrid | i. Routing protocol information ii. Signature based IDS | Simulation | i. Sinkhole ii. Selective forwarding attacks | N/A |
| 11 | CHA–IDS (2018) [36] | Hybrid | i. Best first search algorithm ii. Greedy stepwise algorithm iii. Correlation-based features selection iv. Signature-based IDS | Simulation | i. Hello flooding attack, ii. Sinkhole attack iii. Wormhole | N/A |
| 12 | An Anomaly Detection for IoT (AD-IoT) scheme [37] | Anomaly-based | Random Forest Algorithm | Experiment | Not specified | UNSW-NB 15 |
| 13 | A distributed attack detection scheme (2018) [39] | Anomaly-based | Deep learning | Experiments | i. DoS ii. Probe iii.R2L iv.U2R | NSL KDD |
| 14 | A fog empowered anomaly detection scheme for IoT (2017) [38] | Anomaly-based | i. HyCARCE ii. ENOF | Experiments | Not specified | i. S12 ii. Banana iii. Melbourne IoT data iv. Intel Berkeley Research Laboratory IBRL(IBRL) |
| 15 | Semi-Supervised learning based distributed attack detection framework (2019) [20] | Anomaly-based | i. Extreme Learning Machine (ELM) and ii. Semi-Supervised Fuzzy C-Means (SFCM) algorithm | Experiments | i. DoS ii. Probe iii. R2L iv.U2R | NSL KDD |
| S/No | Scheme | Detection Methodology | Techniques | Evaluated with IoT-Based Dataset |
|---|---|---|---|---|
| 1 | A distributed attack detection scheme (2018) [39] | Anomaly-based | Deep learning | No |
| 2 | A fog empowered anomaly detection scheme for IoT (2017) [38] | Anomaly-based | i. HyCARCE ii. ENOF | No |
| 3 | Semi-Supervised learning based distributed attack detection framework (2018) [22] | Anomaly-based | i. Extreme Learning Machine (ELM) and ii. Semi-Supervised Fuzzy C-Means (SFCM) algorithm | No |
| 4 | An Anomaly Detection for IoT (AD-IoT) scheme [37] | Anomaly-based | Random Forest | No |
| 5 | Proposed framework | Hybrid-based | Extreme Gradient Boosting | Yes |
| S/No | Type of Attack | Number of Instances | Number of Extracted Instances |
|---|---|---|---|
| 1 | Normal | 9543 | 225 |
| 2 | DoS TCP | 12,315,997 | 123,185 |
| 3 | DoS UDP | 20,659,491 | 206,626 |
| 4 | DoS HTTP | 29,706 | 301 |
| 5 | DDoS TCP | 19,547,603 | 1,951,525 |
| 6 | DDoS UDP | 18,965,106 | 189,954 |
| 7 | DDoS HTTP | 19,771 | 203 |
| 8 | Keylogging | 1469 | 34 |
| 9 | OS fingerprinting | 358,275 | 4953 |
| 10 | Port scanning | 1,463,364 | 20,004 |
| 11 | Data theft | 118 | - |
| Total | 73,370,443 | 740,637 | |
| Actual Class Label | Predicted Class Label | |
|---|---|---|
| Positive | Negative | |
| Positive | True positive | False negative |
| Negative | False positive | True negative |
| S/No | Feature Name | Description |
|---|---|---|
| 1 | seq | Argus sequence number |
| 2 | N_IN_Conn_P_DstIP | Number of inbound connections per destination IP |
| 3 | stddev | Standard deviation of aggregated records |
| 4 | N_IN_Conn_P_SrcIP | Number of inbound connections per source IP |
| 5 | min | Minimum duration of aggregated records |
| 6 | state_number | Numerical representation of feature state |
| 7 | srate | Source-to-destination packets per second |
| 8 | mean | Average duration of aggregated records |
| 9 | max | Maximum duration of aggregated records |
| 10 | drate | Destination-to-source packets per second |
| S/No | ML Algorithm | Accuracy (%) | False Positive Rate |
|---|---|---|---|
| 1 | DT | 99.96 | 0.13 |
| 2 | k-NN | 99.97 | 0.68 |
| 3 | NB | 99.85 | 0.91 |
| 4 | Gradient Boosting | 99.99 | 0.89 |
| 5 | XGBoost | 99.99 | 0.05 |
| S/No | ML Algorithm | Recall (%) | Precision (%) | F1 Score (%) | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Normal | Attack | Average | Normal | Attack | Average | Normal | Attack | Average | ||
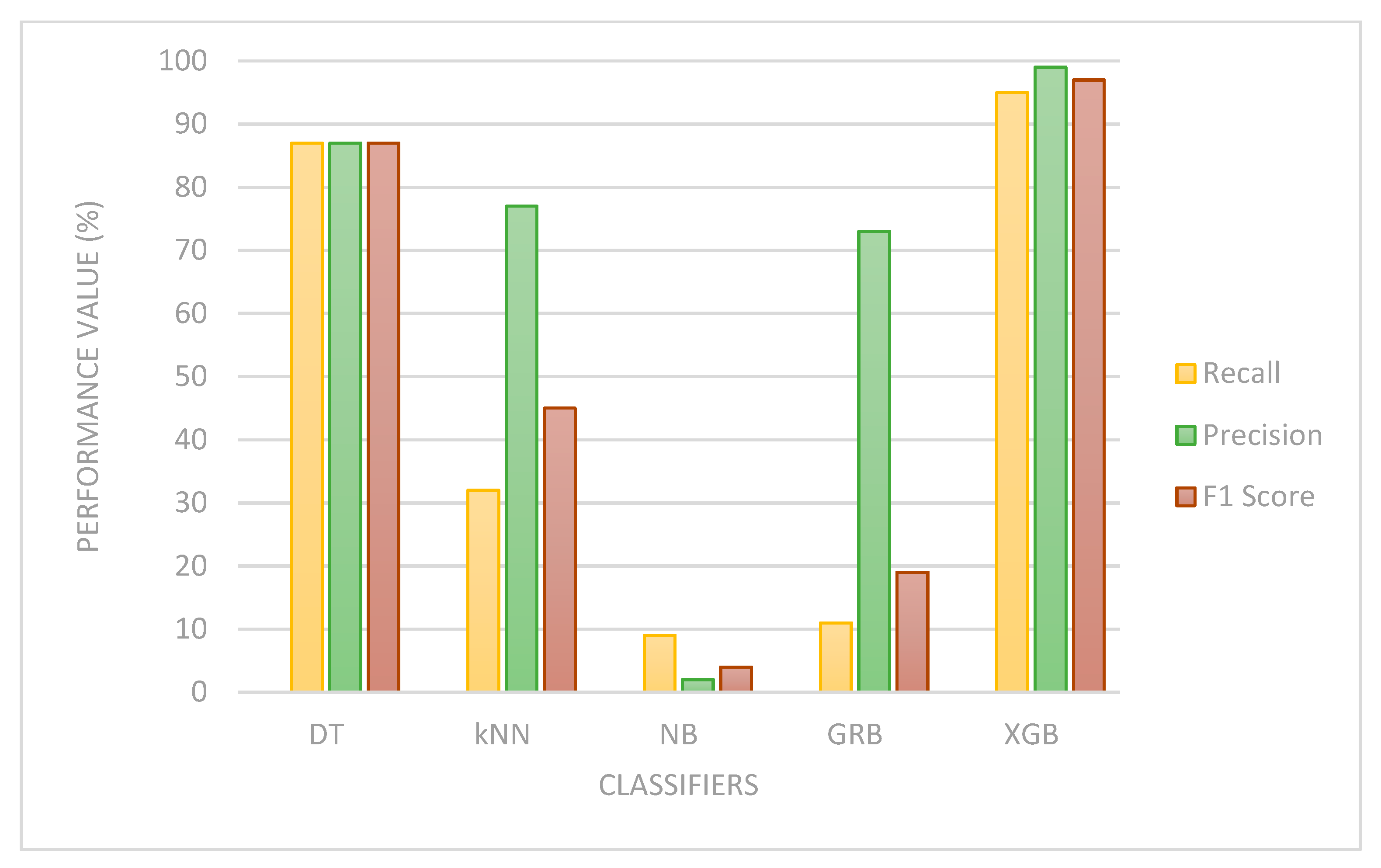
| 1 | DT | 87 | 100 | 93.5 | 87 | 100 | 93.5 | 87 | 100 | 93.5 |
| 2 | k-NN | 32 | 100 | 66 | 77 | 100 | 88.5 | 45 | 100 | 72.5 |
| 3 | NB | 9 | 100 | 54.5 | 2 | 100 | 51 | 4 | 100 | 52 |
| 4 | Gradient Boosting | 11 | 100 | 55.5 | 73 | 100 | 86.5 | 19 | 100 | 59.5 |
| 5 | XGBoost | 95 | 100 | 97.5 | 99 | 100 | 99.5 | 97 | 100 | 98.5 |
| S/No | ML Algo | DoS TCP | DoS UDP | DoS HTTP | DDoS TCP | DDoS UDP | DDoS HTTP | Key Logging | OS F | Port Sc | Normal | Average Accuracy |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
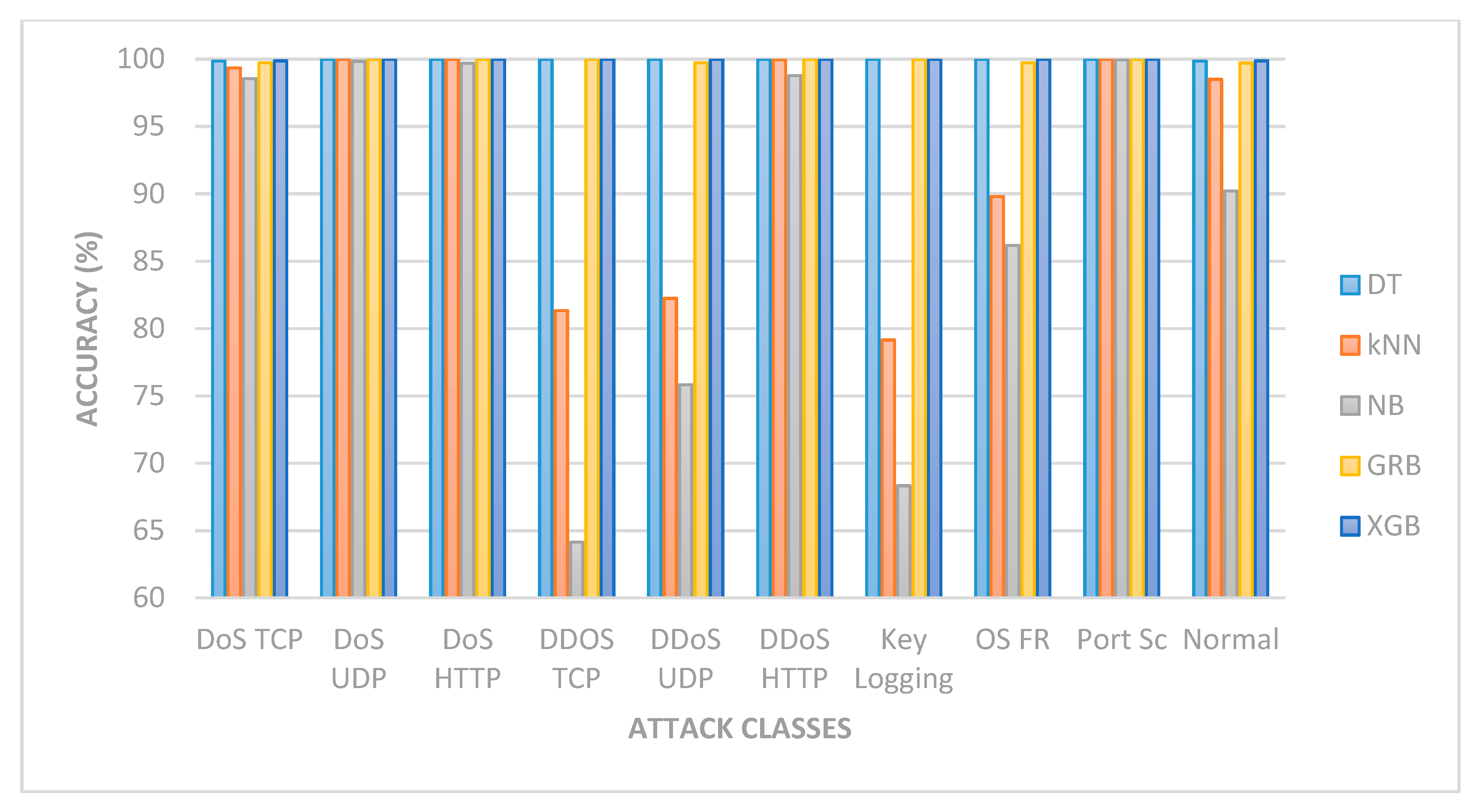
| 1 | DT | 99.86 | 99.99 | 99.99 | 99.99 | 99.98 | 99.99 | 99.99 | 99.99 | 99.97 | 99.86 | 99.96 |
| 2 | k-NN | 99.35 | 99.99 | 99.99 | 81.34 | 82.24 | 99.96 | 79.15 | 89.80 | 99.97 | 98.50 | 93.00 |
| 3 | NB | 98.55 | 99.84 | 99.70 | 64.14 | 75.83 | 98.77 | 68.33 | 86.17 | 99.95 | 90.20 | 78.17 |
| 4 | GRB | 99.72 | 99.99 | 99.97 | 99.97 | 99.73 | 99.99 | 99.97 | 99.73 | 99.99 | 99.71 | 99.88 |
| 5 | XGB | 99.87 | 99.99 | 99.99 | 99.99 | 99.99 | 99.99 | 99.99 | 99.97 | 99.99 | 99.87 | 99.96 |
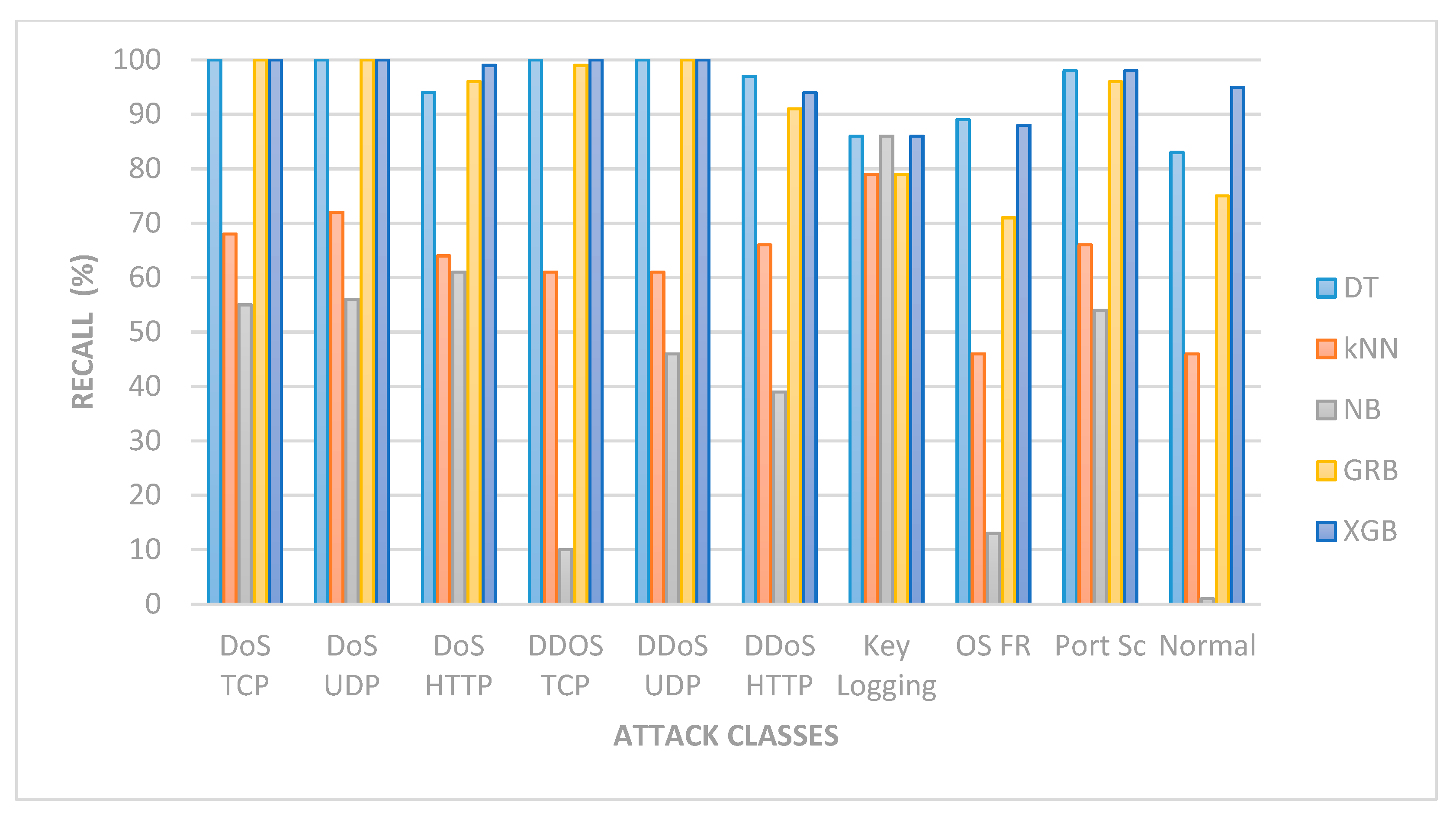
| S/No | ML Algo | DoS TCP | DoS UDP | DoS HTTP | DDoS TCP | DDoS UDP | DDoS HTTP | Key Logging | OS F | Port Sc | Normal | Average Recall |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | DT | 100 | 100 | 94 | 100 | 100 | 97 | 86 | 89 | 98 | 83 | 95 |
| 2 | k-NN | 68 | 72 | 64 | 61 | 61 | 66 | 79 | 46 | 66 | 46 | 63 |
| 3 | NB | 55 | 56 | 61 | 10 | 46 | 39 | 86 | 13 | 54 | 1 | 42 |
| 4 | GRB | 100 | 100 | 96 | 99 | 100 | 91 | 79 | 71 | 96 | 75 | 93 |
| 5 | XGB | 100 | 100 | 99 | 100 | 100 | 94 | 86 | 88 | 98 | 95 | 98 |
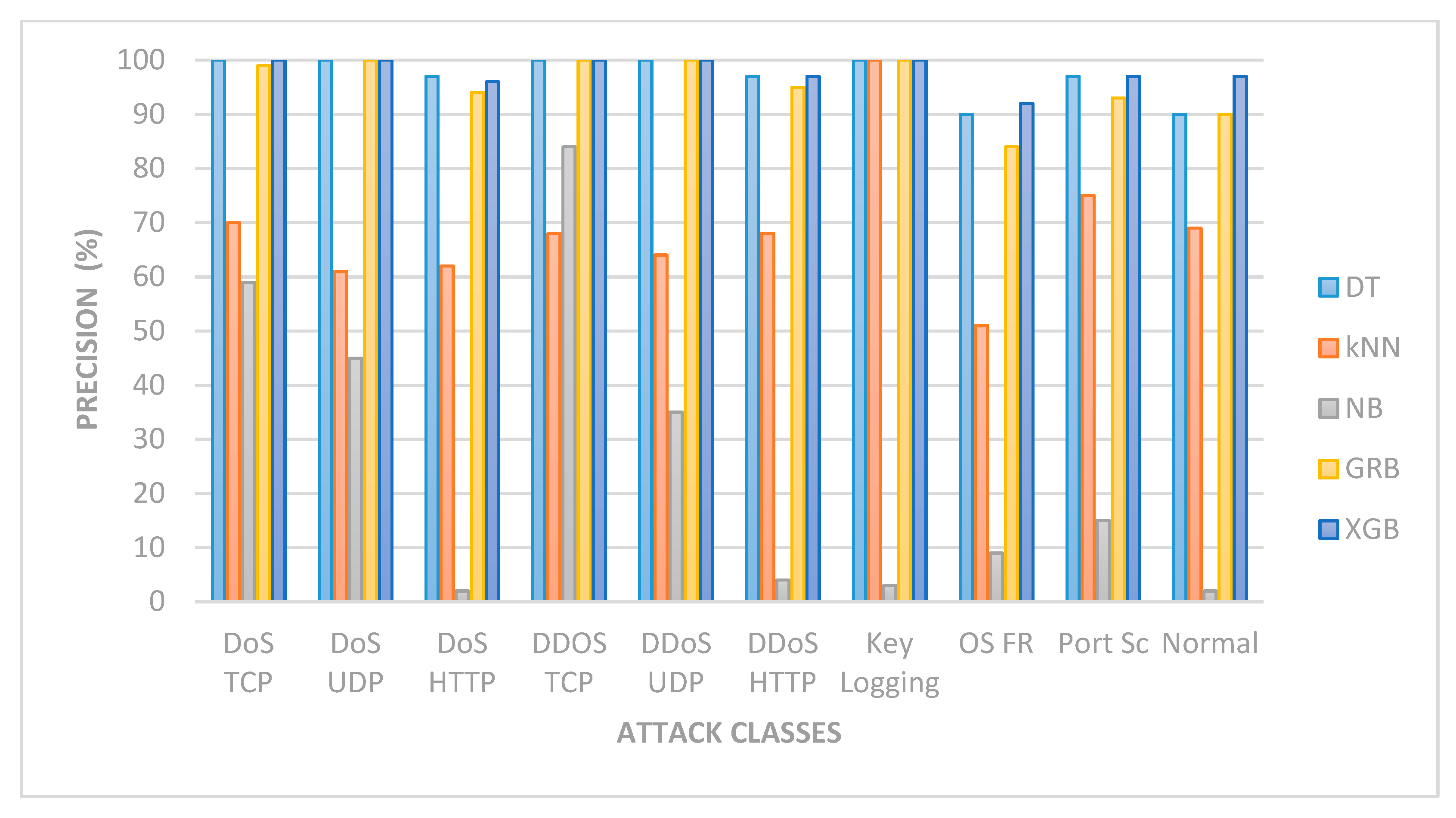
| S/No | ML Algo | DoS TCP | DoS UDP | DoS HTTP | DDoS TCP | DDoS UDP | DDoS HTTP | Key Logging | OS F | Port Sc | Normal | Average Precision |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | DT | 100 | 100 | 97 | 100 | 100 | 97 | 100 | 90 | 97 | 90.0 | 97 |
| 2 | k-NN | 70 | 61 | 62 | 68 | 64 | 68 | 100 | 51 | 75 | 69 | 69 |
| 3 | NB | 59 | 45 | 2 | 84 | 35 | 4 | 3 | 9 | 15 | 2 | 26 |
| 4 | GRB | 99 | 100 | 94 | 100 | 100 | 95 | 100 | 84 | 93 | 90 | 95 |
| 5 | XGB | 100 | 100 | 96 | 100 | 100 | 97 | 100 | 92 | 97 | 97 | 97 |
| S/No | ML Algo | DoS TCP | DoS UDP | DoS HTTP | DDoS TCP | DDoS UDP | DDoS HTTP | Key Logging | OS F | Port Sc | Normal | Average F1 Score |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | DT | 100 | 100 | 96 | 100 | 100 | 97 | 92 | 90 | 97 | 86 | 96 |
| 2 | k-NN | 55 | 69 | 66 | 63 | 64 | 63 | 67 | 88 | 49 | 70 | 65 |
| 3 | NB | 57 | 50 | 4 | 18 | 40 | 7 | 6 | 10 | 23 | 2 | 22 |
| 4 | GRB | 99 | 100 | 95 | 99 | 100 | 93 | 88 | 77 | 95 | 82 | 93 |
| 5 | XGB | 100 | 100 | 98 | 100 | 100 | 95 | 92 | 90 | 98 | 96 | 97 |
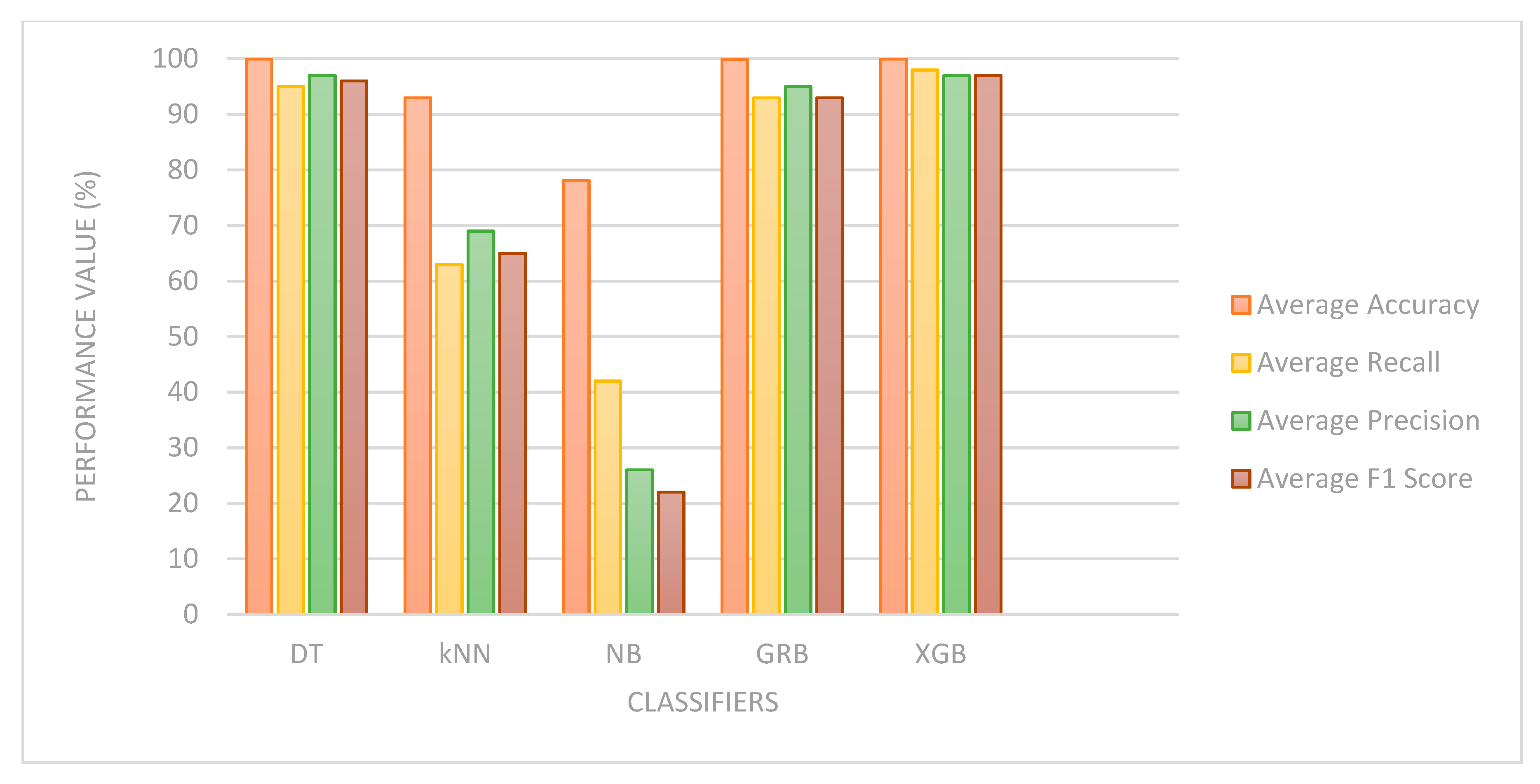
| S/No | ML Algo | Accuracy (%) | Recall (%) | Precision (%) | F1 Score (%) | ||||
|---|---|---|---|---|---|---|---|---|---|
| Binary | Multi Class | Binary | Multi Class | Binary | Multi Class | Binary | Multi Class | ||
| 1 | DT | 99.96 | 99.96 | 93.5 | 95 | 93.5 | 97 | 93.5 | 96 |
| 2 | k-NN | 99.97 | 93.00 | 66 | 63 | 88.5 | 69 | 72.5 | 65 |
| 3 | NB | 99.85 | 78.17 | 54.5 | 42 | 51 | 26 | 52 | 22 |
| 4 | Gradient Boosting | 99.99 | 99.88 | 55.5 | 93 | 86.5 | 95 | 59.5 | 93 |
| 5 | XGBoost | 99.99 | 99.96 | 97.5 | 97 | 99.5 | 97 | 98.5 | 97 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lawal, M.A.; Shaikh, R.A.; Hassan, S.R. An Anomaly Mitigation Framework for IoT Using Fog Computing. Electronics 2020, 9, 1565. https://doi.org/10.3390/electronics9101565
Lawal MA, Shaikh RA, Hassan SR. An Anomaly Mitigation Framework for IoT Using Fog Computing. Electronics. 2020; 9(10):1565. https://doi.org/10.3390/electronics9101565
Chicago/Turabian StyleLawal, Muhammad Aminu, Riaz Ahmed Shaikh, and Syed Raheel Hassan. 2020. "An Anomaly Mitigation Framework for IoT Using Fog Computing" Electronics 9, no. 10: 1565. https://doi.org/10.3390/electronics9101565
APA StyleLawal, M. A., Shaikh, R. A., & Hassan, S. R. (2020). An Anomaly Mitigation Framework for IoT Using Fog Computing. Electronics, 9(10), 1565. https://doi.org/10.3390/electronics9101565






