1. Introduction
With the continuous development of technology, the development of the Internet of Things (IoT) has shown an exponential growth. Combining sensor technology, Internet technology, and wireless technology, IoT realizes real-time interaction between the virtual network and the real world. It senses and collects data in real time through a large number of sensors and transmits data to the server for data calculation and processing. In addition, the processed information is transmitted to the user. IoT has unlimited application prospects and is currently widely used in smart homes, wearable devices, implantable devices, medical devices, connected cars, and transportation systems. Therefore, the Internet of Everything has become an inevitable trend in technology development and industrial application. Although IoT has greatly improved the level of intelligence and automation of society, the information transmitted wirelessly and exposed to the public is highly likely to be tampered with, stolen, and interfered. Therefore, the security of the IoT system has been greatly threatened. Incidents caused by IoT security occur frequently in the real world, and their influence and destructive power are extremely great, so that IoT security has already become a topic of global concern. The issue of IoT security is the primary problem solved by the development of IoT. With the increasing attention paid to IoT data security, a secure and effective identity authentication protocol has become an important requirement for the rapid development of IoT.
IoT identity authentication is threatened by the following major aspects in terms of security. (1) Denial of service (DoS) attacks: When the data are transmitted, the data transmission of a large number of machines may cause network congestion, because IoT has a large number of nodes and exists in a cluster. The attacker may broadcast invalid information to perform a consumptive attack on the network bandwidth, so that the request of the legal user cannot be executed. (2) Node attack: There is a large number of sensing nodes in the IoT application, most of which are deployed in unattended scenarios. Attackers can easily destroy these nodes and impersonate legitimate nodes. Therefore, there will be a large number of damaged nodes and malicious nodes in the IoT. (3) Replay attack: The attacker can deceive the IoT system to obtain an authenticated identity by sending a packet when the destination host has accepted. (4) Eavesdropping and camouflage attacks: The attacker steals security information from a common channel and falsifies other users’ information through known security information. In order to solve these problems and protect the security of identity authentication, this paper proposes a multi-point collaborative authentication method based on user image intelligent collection in the IoT. Firstly, the intelligent collection technology is used to realize the image identity collection of legal users, that is the image information of the legal user is collected by the camera and stored in the database of the local domain management machine, the back-end image management machine, and the cloud server. Secondly, the camera is used to collect the unidentified user image information, which was transmitted to the three databases, as well. Thirdly, the legal user image information and the unidentified user image information in the three databases are compared to realize the identity authentication of the unidentified user, respectively. Not covering the field of imagery, the limitation of our method is that it just compares the image of the legal user with the that of the unidentified user, so there is no algorithm for the image in our method. The security analysis shows that the method is able to resist multiple attacks and prevent the sensor information from being illegally operated and stolen, protecting the security of the sensor information.
2. Related Work
With the rapid development of IoT technology, secure identity authentication has become the focus of research for IoT security in the recent years.
Smart card technology and cryptosystems are used in most identity authentication methods currently. Tai et al. [
1] analyzed Turkanović’s Internet of Things-based authentication and key agreement method for heterogeneous wireless sensor networks (WSN). Analysis showed that the method had two fatal flaws, that is user anonymity was not achieved, and the attacker could easily obtain a session key shared between a normal sensor node and a damaged sensor node that has been connected. In order to solve these two shortcomings, Tai proposed an improved Internet of Things-based authentication and key agreement method. Using smart card technology and a user password system, user and sensor node authentication can be realized with the help of network nodes. Through security analysis, the method has the advantages of user anonymity, ensuring the correctness of the session key and lightweight computing operations. In recent years, more and more identity authentication methods have combined smart card technology with other identification technologies. Challa et al. [
2] proposed a new signature-based authentication key establishment method by using Burrows–Abadi–Needham logic for the IoT environment, which can resist various known attacks. The method uses smart card technology, combined with the user’s personal biometric technology Bioi and the user’s password to achieve mutual authentication between the user and sensor equipment. The method has the advantages of high security, low computing cost, and efficient communication cost; in addition, it is suitable for practical applications in the IoT environment. Hu et al. [
3] proposed a security and privacy protection method in the IoT environment, outlined the face recognition and resolution framework based on fog computing, and summarized security and privacy issues, then proposed an authentication and session key agreement method, a data encryption method, and a data integrity check method in order to solve the confidentiality, integrity, and usability problems in the face recognition process. Dhillon and Kalra [
4] used biometrics technology to communicate with VoIP based on the session initiation protocol (SIP) and proposed a new authentication method based on multi-factor ECC. The method uses three users’ personal biometrics to provide strong identity checks and thus enhanced security, proving that the method is resistant to a variety of potential threats by conducting rigorous security analysis. Zhang et al. [
5] proposed a method for mobile terminal identity authentication based on two-dimensional code technology in a cloud computing environment. The method adopts QR encoding technology as the two-dimensional code processing technology and uses the QR code as the information transmission carrier to realize dynamic authentication of a mobile terminal. According to the security analysis, the method is simple in structure. The method does not require the use of third-party equipment and has high security and adaptability.
The elliptic curve encryption (ECC) algorithm has the advantages of a small key and high computational efficiency. Many researchers use the ECC algorithm to replace the traditional encryption algorithm in the identity authentication method. AL-Turjman et al. [
6] proposed a seamless secure authentication and key agreement (S-SAKA) method using bilinear pairing and elliptic curve cryptosystems. The method introduced a mobile receiver strategy to extend user authentication in cloud-based environments. The results showed that the proposed S-SAKA method satisfied the security attributes and was flexible for node-capture attacks. In addition, the method also resisted a large number of well-known potential attacks related to data confidentiality, mutual authentication, session key agreement, user anonymity, password guessing, and key emulation. Kalra and Sood [
7] proposed a secure ECC-based mutual authentication protocol for secure communication between embedded devices and cloud servers using Hypertext Transfer Protocol (HTTP) cookies. Through security analysis, the protocol is robust to multiple security attacks and provides basic security requirements. Mo et al. [
8] analyzed a secure and efficient user authentication and key agreement protocol (AKAP), and proposed a more efficient remote user mutual AKAP scheme using ECC with a provable security for mobile client–server environments. The proposed scheme not only provides mutual authentication, but also implements a session key agreement between the client and the server. An informal security analysis showed that the scheme protects against well-known attacks and provides anonymity to users.
Multi-factor authentication can enhance the security of the identity authentication process. More and more researchers have improved the traditional single-factor authentication into multi-factor authentication in identity authentication methods. Jiang et al. [
9] analyzed a three-factor mutual authentication protocol proposed by Amin for wireless sensor networks, indicating that the protocol was likely to suffer from smart card loss attacks, and the user identity and password could be guessed using brute force techniques. They proposed a lightweight and secure user authentication protocol based on the Rabin cryptosystem. The protocol can resist all possible attacks and provide the required security functions by mutual authentication among users, gateway nodes, and server nodes. The protocol was able to defend against all possible attacks and provide the required security functions. Wazid et al. [
10] designed a new secure lightweight three-factor remote user authentication method for the hierarchical IoT network (HloTN), which is called the user authentication key management protocol (UAKMP). The three factors used in UAKMP are user smart cards, passwords, and personal biometrics. The method provides a variety of features, including offline sensing node registration, freely password, biometric update facility, user anonymity, and perceived node anonymity. Xu and Wu [
11] proposed a new three-factor authentication method for wireless sensor networks with a multi-gateway architecture. The method achieved mutual authentication of four factors, which were user, home gateway node, foreign gateway node, and sensor node, respectively. After the formal verification of a protocol security analysis tool (ProVerif) and based on the results of informal analysis, the method was able to defend against various attacks and meet security attributes.
Dynamic identity authentication uses multiple encryption to protect data transmission. More and more researchers have improved the traditional static identity authentication into dynamic identity authentication in identity authentication methods. Gong et al. [
12] proposed an IoT-aware node authentication mechanism based on dynamic metrics. Firstly, by introducing the computing functions such as the trust function, the credibility risk assessment function, the feedback control function, and the active function of the sensing node, the dynamic credibility measurement of the sensing node was realized. The dynamic credibility measure of the multi-dimensional sensing node was able to effectively describe the change of the perceived value of the perceived node. Afterwards, a trusted attestation based on the node trusted measure was realized by using the revocable group signature mechanism of a local verifier. Zhang and Xu [
13] proposed a secure authentication technology based on a dynamic Bayesian network combined with a trusted protocol in the IoT. By introducing a secure authentication mechanism based on the combined public key and trusted measurement in the network, the security of the information exchange was enhanced. The node credibility and path reliability were considered in the routing decision, so that a highly secure and reliable path was selected for information transfer in the IoT. The evaluation results showed that the proposed algorithm had better security performance than the compared algorithm in terms of the overhead and computational complexity of the real-time application, and it also had the adaptive ability to respond quickly to denial of service attacks and effectively suppress the threat of abnormal entities in the IoT. Xie et al. [
14] proposed a new lattice-based dynamic group signature method. This method allows any user to dynamically join a group while achieving effective undo. In addition, the method can achieve non-framework security, ensuring that other users in the system cannot forge the signature of any user. It was proven that the method based on the hardness of the lattice problem in the random prediction model was safe.
As a key part of the development of the Internet of Things, RFID technology has also been the focus of researchers in the field of identity authentication in the Internet of Things in recent years. Shen et al. [
15] analyzed the RFID authentication methods of Chen et al. and pointed out that their methods were vulnerable to replay attacks and server spoofing attacks. They proposed a new RFID authentication method using elliptic curve cryptography (ECC). Security analysis showed that the method can meet the security requirements of RFID authentication and does not require additional performance costs, which is more suitable for practical applications. Fan et al. [
16] proposed an ultra-lightweight RFID authentication scheme called ULRAS in order to reduce the computational cost. ULRAS uses only bit and XOR operations to prevent DDOS attacks. ULRAS uses subkeys and sub-indexes throughout the key update process and uses the RR method throughout the protocol to make the protocol well resistant to various attacks. For each update process, ULRAS only needs to update a portion of the key
K randomly, which makes the update process more random. Compared to other protocols, ULRAS reduces the cost of computing and communication resources and is more secure. Aghili et al. [
17] evaluated the security of the ultra-lightweight RFID mutual authentication protocol (ULRMAPC) proposed by Fan and demonstrated that the protocol was vulnerable to denial of service, reader and tag emulation, and desynchronization attacks. They proposed a new improved authentication, which can provide sufficient resistance to known active and passive attacks.
In summary, most of the research on IoT authentication in the recent years still uses the smart card technology identity or the single identity authentication method. The identity authentication method using the smart card technology stores the user’s private information in the smart card chip, and the attacker can easily steal the user information in the smart card, while the smart card is easily lost or damaged. The single identity authentication method does not achieve multi-end mutual authentication and is vulnerable to server spoofing attacks and spoofing attacks. A multi-point collaborative authentication method based on user image intelligent collection in the IoT is proposed in this paper. Compared with the traditional single identity authentication method, our method uses three-party collaborative authentication, which is able to avoid the problems of sensor information theft and server spoofing attacks, frequently occurring in the single authentication method. Compared with the traditional identity authentication method using smart card technology, the method proposed in this paper using image intelligent collection technology is more friendly and direct and can avoid the problem of smart card information loss. Although the method does not use the password system, the user image is used as the unique identity information. Attacks on user password information, such as password guessing, are avoided.
The organization of this paper is as follows: The specific method of the multi-point collaborative authentication method is introduced in the
Section 3. The safety and cost of the method are analyzed in the
Section 4. The
Section 5 presents conclusions and future work.
3. Multi-Point Collaborative Authentication
This section proposes a multi-point collaborative authentication method based on user image intelligent collection in the IoT. The method mainly includes four phases: (1) the system establishment phase of user image intelligent multi-point collaborative authentication; (2) the authentication phase of the local domain management machine and the back-end image management machine; (3) the authentication phase of the local domain management machine and the cloud server; (4) the authentication phase of the back-end image management machine and the cloud server. Through these four phases, it is possible to realize the security of user image intelligent collection and its service intelligent control.
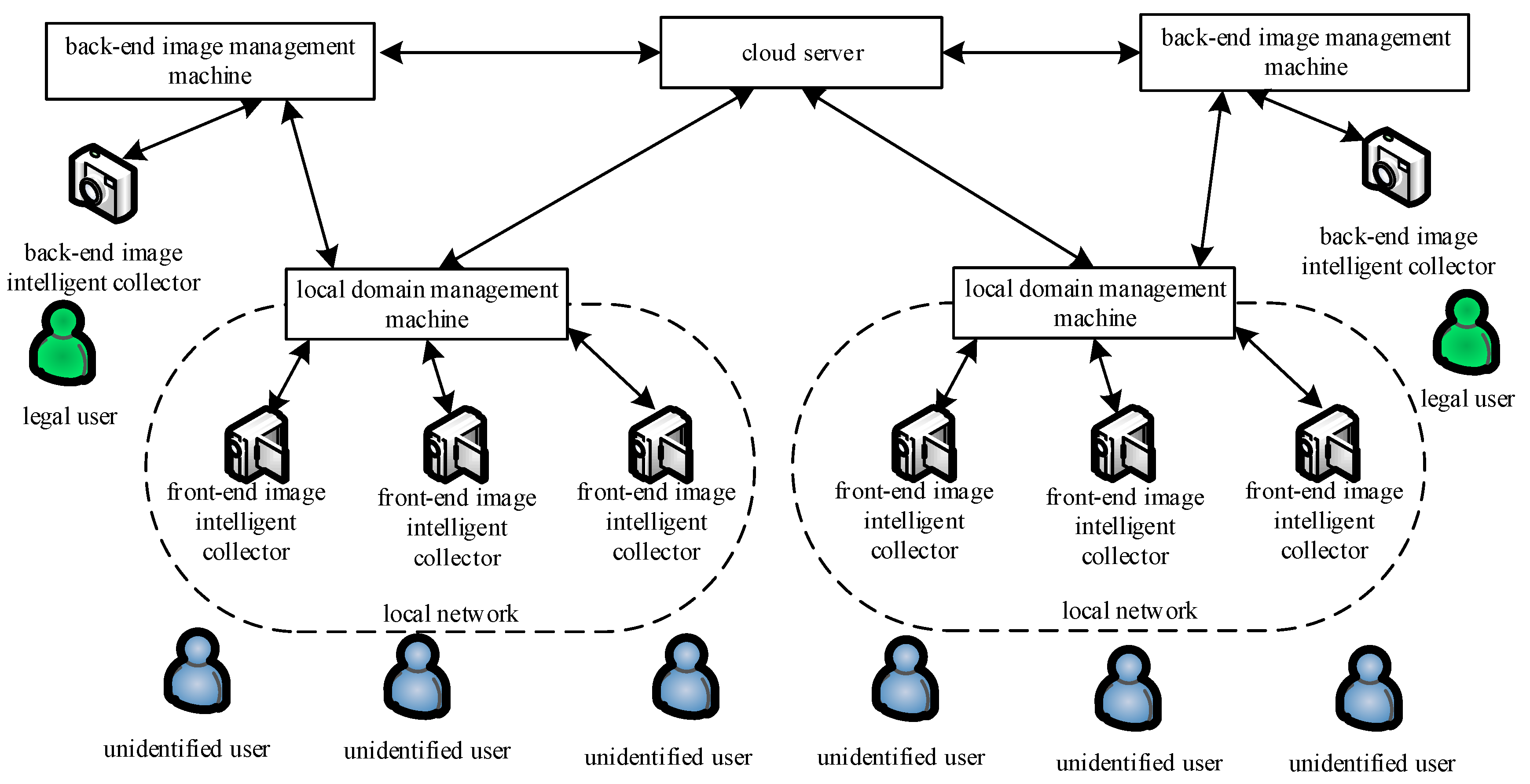
In these phases, the information transmission between the local domain management machine, the back-end image management machine, and the cloud server follows the SSL (secure socket layer) or TLS (transport later security) protocol. Its architecture diagram is shown in
Figure 1. The symbols and definitions used in this paper are shown in
Table 1.
3.1. The System Establishment Phase of User Image Intelligent Multi-Point Collaborative Authentication
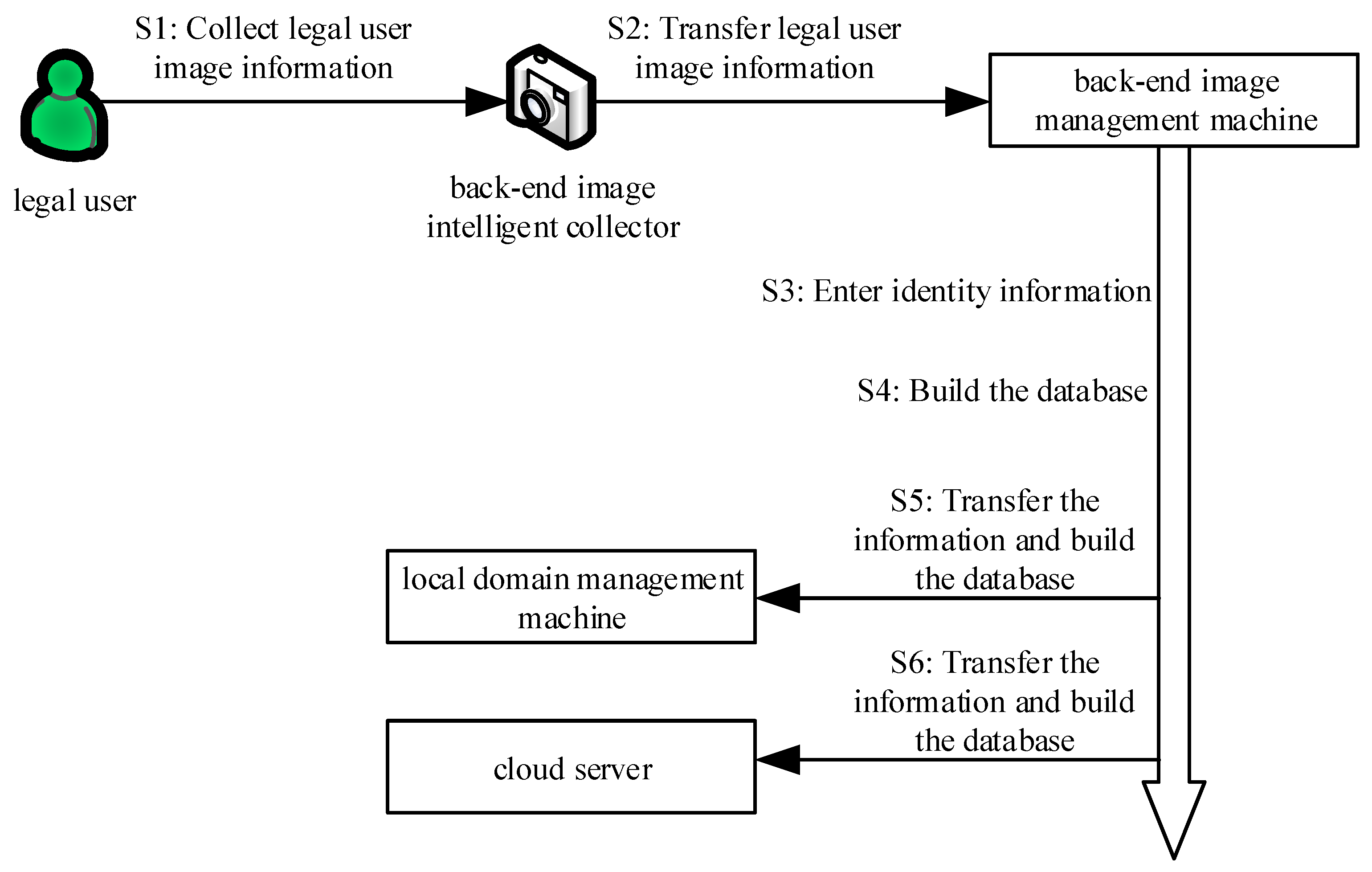
At this phase, the back-end image intelligent collector intelligently collects the image of the legal user and transmits it to the back-end image management machine. Then, the back-end image management machine requests the back-end manager to input the identity information and uses a secure encryption algorithm to transmit it to the local domain management machine and the cloud server through the secure channel. Finally, they establish their own image information database in the back-end image management machine, local domain management machine, and cloud server to complete the system establishment. The brief process diagram is shown in
Figure 2. The algorithm is shown in Algorithm 1.
| Algorithm 1: The System Establishment Phase of User Image Intelligent Multi-Point Collaborative Authentication |
,. ,,. . ,,, . , . ,. , . . , if it is not one, then go to (8), else . ,,. , . , . ,. ,. . , if it is not one, then go to (15), else . ,, if it is one, then go to (1),else go to (18). End.
|
The specific process execution is described as follows:
Step 1: The back-end image intelligent collector (j = 1, 2, 3, ⋯, n) intelligently collects the image of the legal user (i = 1, 2, 3, ⋯, n) according to the requirements of the back-end manager. The legal user image is transmitted to the corresponding back-end image management machine via the secret network.
Step 2: After receiving the legal user image transmitted by the back-end image intelligent collector, the back-end image management machine requests the back-end manager to input the identity information of the back-end image management machine and the identity information of this legal user.
Step 3: After receiving the identity information ) of the input legal user, the back-end image management machine constructs a corresponding back-end image management information database . This database contains the identity information of the back-end image management machine, the legal user name , the identity information of the legal user, and the image information of the legal user.
Step 4: After constructing the database , the back-end image management machine first generates a public key and a corresponding private key based on the elliptic curve encryption method. On this basis, the back-end image management machine encrypts the image of the legal user and its own identity information using the public key based on the elliptic curve encryption method. The encrypted file is sent to the local domain management machine via SSL or TLS.
Step 5: After receiving the encrypted file , the local domain management machine applies it to the back-end image management machine for the private key .
Step 6: After receiving the private key application of the local domain management machine, the back-end image management machine sends the private key to the local domain management machine via SSL or TLS.
Step 7: After receiving the private key sent by the back-end image management machine , the local domain management machine decrypts the received encrypted file .
Step 8: After decrypting the encrypted file , the local domain management machine construct a corresponding local domain management image information database . This database contains image information of the legal user, the back-end image management machine name , and the identity information of the back-end image management machine .
Step 9: The local domain management machine determines whether the local domain management image information database is constructed. If not, go the Step 8; otherwise, send confirmation message to the back-end image management machine .
Step 10: After receiving the confirmation message sent by the local domain management machine, the back-end image management machine generates a public key and a corresponding private key according to the elliptic curve encryption method.
Step 11: The back-end image management machine uses the public key to encrypt image of the legal user, the identity information of the user image, and its own identity information according to the elliptic curve encryption method, then sends its encrypted file to the cloud server via SSL or TLS.
Step 12: After receiving the encrypted file , the cloud server applies it to the back-end image management machine for the private key .
Step 13: After receiving the private key application of the cloud server, the back-end image management machine sends the private key to the cloud server via SSL or TLS.
Step 14: After receiving the private key sent by the back-end image management machine , the cloud server decrypts the received encrypted file .
Step 15: After decrypting the encrypted file , the cloud server constructs a corresponding cloud server image information database . This database contains the image information of the legal user, the identity information of the legal user, and the identity information of the back-end image management machine .
Step 16: The cloud server determines whether the cloud server image information database is constructed. If not, go to Step 15; otherwise, send a confirmation message to the back-end image management machine .
Step 17: After receiving the confirmation message sent by the cloud server, the back-end image management machine determines whether the back-end manager needs the back-end image intelligent collector to collect the legal user image, and if necessary, then go to the Step 1; otherwise, go to Step 18.
Step 18: End of system construction.
3.2. The Authentication Phase of the Local Domain Management Machine and the Back-End Image Management Machine
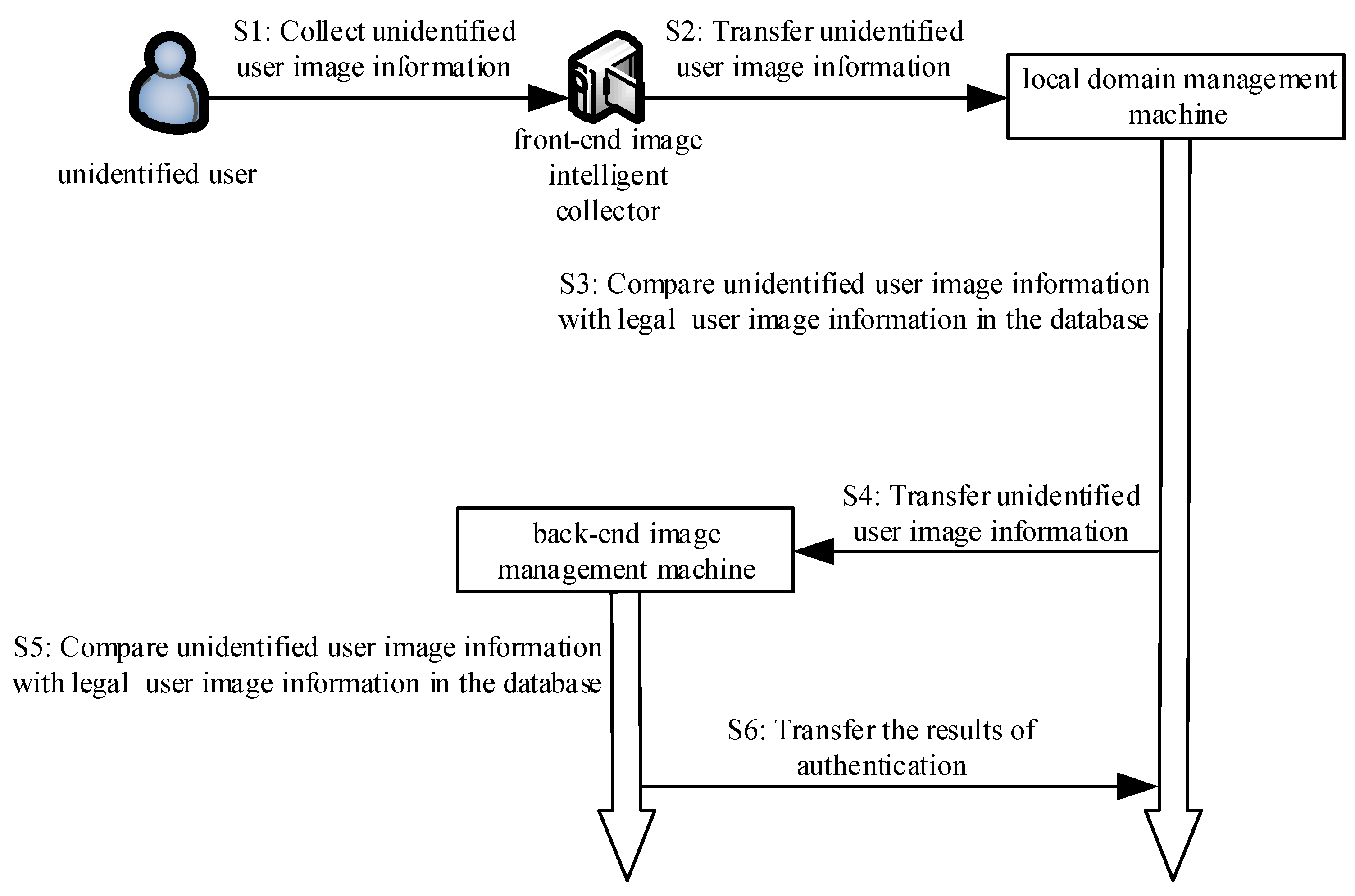
At this phase, the front-end image intelligent collector collects the unidentified user image information and transmits it to the local domain management machine via the secret network. The local domain management machine applies for authentication to the back-end image management machine in the form of a digital signature. Then, the local domain management machine encrypts the unidentified user image information and transmits it to the back-end image management machine through the encryption algorithm. Next, query the image information of all legal users in the local domain management image information database and the back-end image management image information database and respectively compare the legal user image information in these two databases with the image information of the unidentified user. Finally, complete mutual authentication between the local domain management machine and the back-end image management machine. The brief process diagram is shown in
Figure 3. The algorithm is shown in Algorithm 2.
| Algorithm 2: The Authentication Phase of the Local Domain Management Machine and the Back-End Image Management Machine |
, if it is one, then go to (3), else go to (2). wait 3 s, then go to (1). ,,. ,,, if it is one, delete , then go to (2), else , , if and , then go to (5), else delete , and go to (2). = (Apply for authentication), , . , , if it is one, then go to (7), else show “Apply for authentication failure”, and go to (3). message = (The authentication was successful, please transmit the image of the unidentified user) . ,. ,. ,, if it is one, then go to (11), else show “The verification of the image of the unidentified user failed”, and go to (3). . , , if and , then show “The verification is success between the local domain management machine and the back-end image management machine”, and go to (13), else show “The verification failed between the local domain management machine and the back-end image management machine”, and go to (15). message = (The verification was successful between the local domain management machine and the back-end image management machine), . . If it is over, then go to (15), else go to (13). End.
|
The specific process execution is described as follows:
Step 1: The front-end image intelligent collector intelligently judges whether there is an unidentified user who needs image collection according to the surrounding scenes. If needed, then go to Step 3, otherwise, go to Step 2.
Step 2: The front-end image intelligent collector waits for three seconds and then goes to Step 1.
Step 3: The front-end image intelligent collector intelligently collects the image of the unidentified user according to the surrounding scene and generates a timestamp value . Then, the image of the unidentified user and the current timestamp value are sent to the local domain management machine through the secret network.
Step 4: After receiving the image of the unidentified user and the current timestamp value sent by the front-end image intelligent collector , the local domain management machine generates a timestamp value . Firstly, check if the session delay is within the allowable time interval t. If , the session times out, and delete the image of the unidentified user sent by the front-end image intelligent collector , then go to Step 2. Then, query the image information of all legal users in the local domain management image information database , and compare the legal user image information in the database with the image of the unidentified user sent by the front-end image intelligent collector . If the image information of a certain legal user exists in the local domain management image information database and the image of the unidentified user sent by the front-end image intelligent collector is the same (i.e., = ), go to Step 5; otherwise, delete the image of the unidentified user sent by the front-end image intelligent collector , then go to Step 2.
Step 5: According to the back-end image management machine corresponding to the image information of the legal user in the database , the local domain management machine first uses the private key and signs the “Apply for authentication” message, i.e., (“Apply for authentication”). Then, it sends the signed message to the back-end image management machine .
Step 6: After receiving the signature message (“Apply for authentication”)) sent by the local domain management machine, the back-end image management machine authenticates the signature message by using the public key of the local domain management machine. If the authentication is successful, go to Step 7. Otherwise, display “Apply for authentication failure”, and go to Step 3.
Step 7: The back-end image management machine encrypts the “The authentication is successful, please transmit the image of the unidentified user” message using the public key , according to the elliptic curve encryption method, and then sends the encrypted message (“The authentication is successful, please transmit the image of the unidentified user”) to the local domain management machine via SSL or TLS.
Step 8: After receiving the encrypted message (“The authentication is successful, please transmit the image of the unidentified user”), the local domain management machine uses private key to decrypt.
Step 9: According to the decrypted message, the local domain management machine first uses the private key to sign the image message of the unidentified user collected by the front-end image intelligent collector , i.e., . Then, the signed message is sent to the back-end image management machine .
Step 10: After receiving the signature message sent by the local domain management machine, the back-end image management machine authenticates the signature message by using the public key of the local domain management machine. If the authentication is successful, go to Step 11. Otherwise, display “The verification of the image of the unidentified user failed”, and go to Step 3.
Step 11: The back-end image management machine receives the image of the unidentified user sent by the front-end image intelligent collector .
Step 12: The back-end image management machine first queries the image information of all legal users in its database and compares the legal user image information in the database with the image of the unidentified user sent by the front-end image intelligent collector . If the image information of a certain legal user exists in the back-end image management information database and the image of the unidentified user sent by the front-end image intelligent collector are the same (i.e., = ), the back-end image management machine displays “The verification is successful between the local domain management machine and the back-end image management machine”. Otherwise, the back-end image management machine displays “The verification failed between the local domain management machine and the back-end image management machine” and goes to Step 15.
Step 13: The back-end image management machine encrypts the image authentication result message “The verification is successful between the local domain management machine and the back-end image management machine” and then sends its encrypted message to the local domain management machine via SSL or TLS.
Step 14: The back-end image management machine determines whether the image authentication result message is sent. If sent, go to Step 15; otherwise, go to Step 13.
Step 15: End.
3.3. The Authentication Phase of the Local Domain Management Machine and Cloud Server
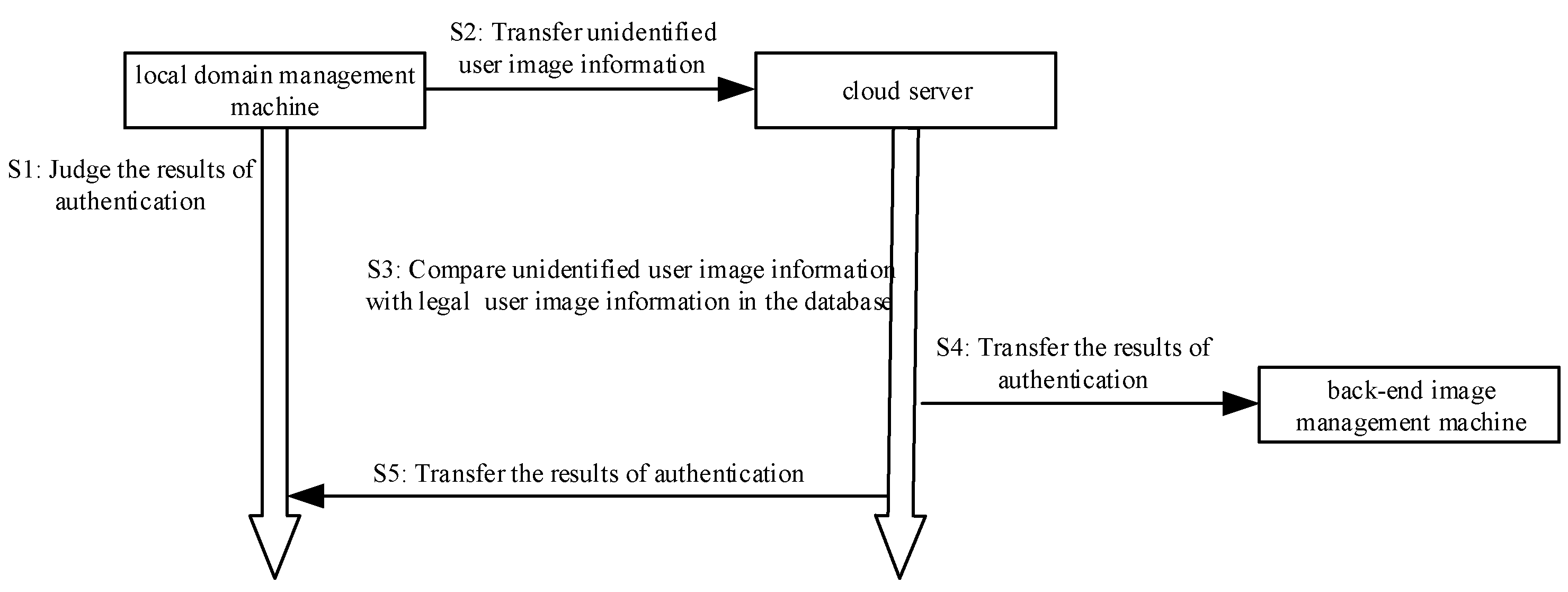
In this phase, the local domain management machine applies for authentication to the cloud server in the form of a digital signature. Then, the local domain management machine encrypts the unidentified user image information and transmits it to the cloud server through the encryption algorithm. Then, query the image information of all legal users in the cloud server image information database, and compare the legal user image information in the database with the image information of the unidentified user. Finally, complete mutual authentication between the local domain management machine and the cloud server. The brief process diagram is shown in
Figure 4. The algorithm is shown in Algorithm 3.
| Algorithm 3: The Authentication Phase of the Local Domain Management Machine and Cloud Server |
, . , if the verification is successful, then go to (3), else go to (13). = (Apply for authentication), , . , , if it is one, then go to (5), else show “Apply for authentication failure” and go to (13). = (The authentication is successful, please transmit the image of the unidentified user), . , . , . , . If it is one, then go to (9), else show “The authentication of the image of the unidentified user failed”, and go to (13). . , , if and , then the cloud server shows “The verification is successful between the local domain management machine and the cloud server”, and go to (11), else the cloud server shows “The verification failed between the local domain management machine and the cloud server”, and go to (13). = (The verification is successful between the local domain management machine and the cloud server), , . . If it is over, then go to (13), else go to (11). End.
|
The specific process execution is described as follows:
Step 1: The local domain management machine receives the image authentication result message sent by the back-end image management machine and decrypts the message.
Step 2: The local domain management machine determines the decrypted image authentication result message. If the authentication with the local domain management machine is successful, the process goes to Step 3. Otherwise, the process goes to Step 13.
Step 3: The local domain management machine first signs the “Apply for authentication” message using the private key , i.e. (“Apply for authentication”)), then sends the signed message (“Apply for authentication”)) to the cloud server.
Step 4: After receiving the signature message (“Apply for authentication”)) sent by the local domain management machine, the cloud server authenticates the signature message (“Apply for authentication”)) by using the public key of the local domain management machine. If the authentication is successful, go to Step 5. Otherwise, display “Apply for authentication failure”, and go to Step 13.
Step 5: According to the elliptic curve encryption method, the cloud server encrypts the “The authentication is successful, please transmit the image of the unidentified user” message using the public key and then sends the encrypted message (“The authentication is successful, please transmit the image of the unidentified user”) to the local domain management machine via SSL or TLS.
Step 6: After receiving the encrypted message (“The authentication is successful, please transmit the image of the unidentified user”), the local domain management machine uses the private key to decrypt the message.
Step 7: According to the decrypted message, the local domain management machine first uses the private key to sign the collected image of the unidentified user, i.e., , then sends the signature message to the cloud server.
Step 8: After receiving the signature message sent by the local domain management machine, the cloud server authenticates the signature message by using the public key of the local domain management machine. If the authentication is successful, go the Step 9. Otherwise, display “The authentication of the image of the unidentified user failed” and go to Step 13.
Step 9: The cloud server receives the image of the unidentified user sent by the front-end image intelligent collector .
Step 10: The cloud server first queries the image information of all legal users in its database and compares the legal user image information in the database with the image of the unidentified user sent by the front-end image intelligent collector . If the image information of a certain legal user exists in the cloud server database and the image of the unidentified user sent by the front-end image intelligent collector are the same (i.e., = ), the cloud server displays “The verification is successful between the local domain management machine and the cloud server”. Otherwise, the cloud server displays “The verification failed between the local domain management machine and the cloud server” and goes to Step 13.
Step 11: The cloud server encrypts the image authentication result message “The verification is successful between the local domain management machine and the cloud server” and then sends the encrypted message to the local domain management machine and the corresponding back-end image management machine via SSL or TLS.
Step 12: The cloud server determines whether the image authentication result message is sent. If sent, go to Step 13; otherwise, go to Step 11.
Step 13: End.
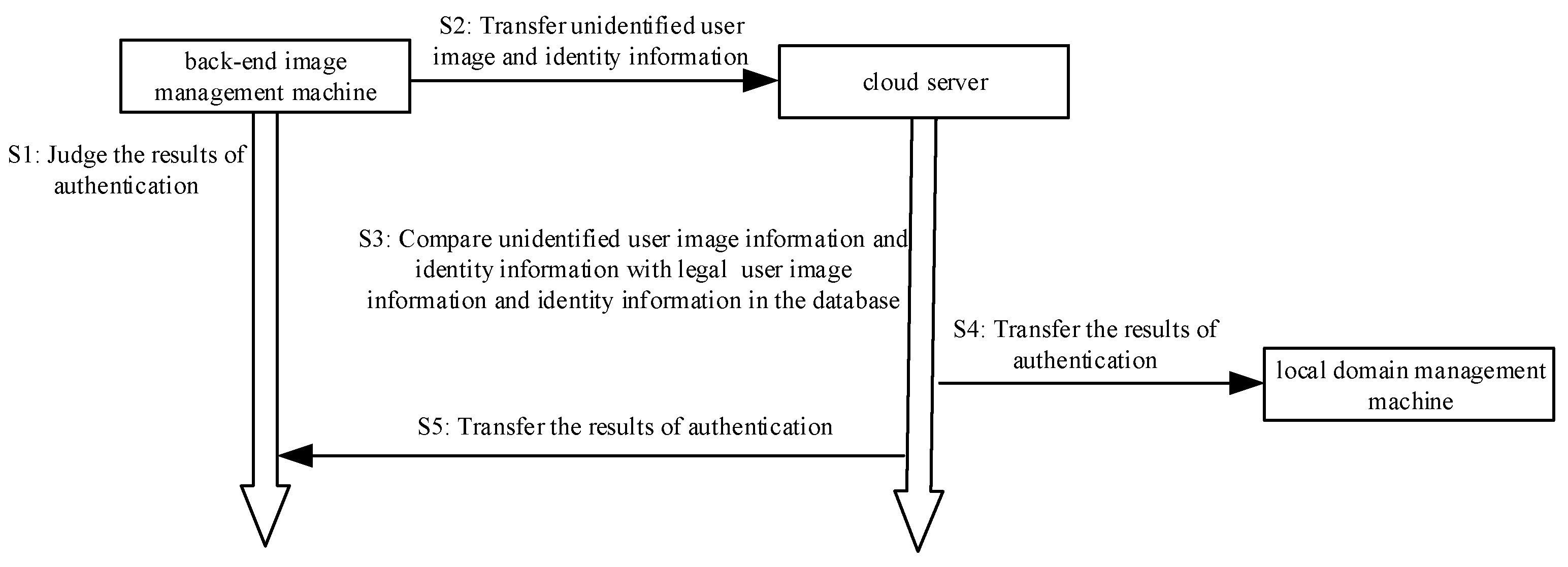
3.4. The Authentication Phase of the Back-End Image Management Machine and Cloud Server
In this phase, the back-end image management machine applies for authentication to the cloud server in the form of a digital signature. Secondly, the back-end image management machine encrypts the information such as the unidentified user image information and transmits it to the cloud server through the encryption algorithm. Then, query the image information of all legal users in the cloud server image information database. Next, compare the image information and the identity information with the image of the unidentified user, which has been authenticated by the signature and the identity information of the unidentified user. Finally, complete mutual authentication between the back-end image management machine and the cloud server. The brief process diagram is shown in
Figure 5. The algorithm is shown in Algorithm 4.
| Algorithm 4: The Authentication Phase of the Back-End Image Management Machine and Cloud Server |
, . . If the verification is success, then go to (3), else go to (14). = (Apply for authentication), , . , , if it is one, then go to (5), else show “Apply for authentication failure”, and go to (13). = (The authentication is successful, please transmit the image of the unidentified user), . ,. , . , . If it is one, then go to (9), else show “The authentication of the image of the unidentified user failed between the cloud server and the back-end image management machine”, and go to (13). . , , if and , then the cloud server shows “The verification is successful between the back-end image management machine and the cloud server”, and go to (11), else the cloud server shows “The verification failed between the back-end image management machine and the cloud server”, and go to (13). = (The verification is successful between the back-end image management machine and the cloud server), ,. . If it is over, then go to (13), else go to (11). End.
|
The specific process execution is described as follows:
Step 1: The back-end image management machine receives the image authentication result message sent by the cloud server and decrypts the message.
Step 2: The back-end image management machine determines the decrypted image authentication result message, and if it is “The verification is successful between the local domain management machine and the cloud server”, go to Step 3; otherwise, go to Step 14.
Step 3: The back-end image management machine first signs the “Apply for authentication” message using the private key , i.e., (“Apply for authentication”), then sends the signed message (“Apply for authentication”) to the cloud server.
Step 4: After receiving the signature message (“Apply for authentication”) sent by the back-end image management machine , the cloud server authenticates the signature message (“Apply for authentication”) by using the public key of the back-end image management machine . If the authentication is successful, go to Step 5. Otherwise, display “Apply for authentication failure”, and go to Step 13.
Step 5: The cloud server encrypts the “The authentication is successful, please transmit the image of the unidentified user” message according to the elliptic curve encryption method using the public key and then sends the encrypted message (“The authentication is successful, please transmit the image of the unidentified user”) to the back-end image management machine via SSL or TLS.
Step 6: After receiving the encrypted message, the back-end image management machine decrypts the message by the private key .
Step 7: According to the decrypted message, the back-end image management machine first uses the private key to sign the image of the unidentified user sent by the local domain management machine. Then, sign its corresponding user identity information, which is initially compared successfully by the local domain management machine and the back-end image management machine . Finally, sign its own identity information , i.e., , then send the signature message to the cloud server.
Step 8: After receiving the signature message sent by the back-end image management machine , the cloud server authenticates the signature message by using the public key of the back-end image management machine . If the signature authentication is successful, go to Step 9, otherwise, display “The authentication of the image of the unidentified user failed between the cloud server and the back-end image management machine”, and go to Step 13.
Step 9: The cloud server stores the image of the unidentified user, which has been authenticated by the signature, its corresponding user identity information , and identity information of the back-end image management machine .
Step 10: The cloud server first queries the image information of all legal users, the identity information of the legal user, and the identity information of the back-end image management machine in the cloud server image information database . Then, it respectively compares the image of the unidentified user, which has been authenticated by the signature and the identity information of the unidentified user image with the image information of all legal users and the identity information of the legal user in the cloud server image information database . If there is image information of a legal user and identity information of a legal user in the cloud server image information database , this image information and identity information are respectively the same as the image of the unidentified user, which has been authenticated by the signature and the identity information of the unidentified user image, i.e., ( = ), = ), and the cloud server displays “The verification is successful between the back-end image management machine and the cloud server”. Otherwise, the cloud server displays “The verification failed between the back-end image management machine and the cloud server”, and it goes to Step 13.
Step 11: The cloud server encrypts the image authentication result message “The verification is successful between the back-end image management machine and the cloud server” and then sends the encrypted message to the local domain management machine and the corresponding back-end image management machine via SSL or TLS.
Step 12: The cloud server determines whether the image authentication result message is sent. If sent, go to Step 13; otherwise, go to Step 11.
Step 13: End.