Improved Buffer-Aided Multi-Hop Relaying with Reduced Outage and Packet Delay in Cognitive Radio Networks
Abstract
:1. Introduction
Contributions
- A buffer-aided multi-hop relay selection (BAMR) technique is proposed that integrates a virtual duplex multi-hop mechanism with the simple buffer-aided relaying in a CRN; this enables overcoming the possible limitation of incurring additional delays associated with simple buffer-aided relaying. The incorporation of virtual duplexing, a delay-reducing technique, primarily augments the relay selection mechanism, which in turn increases the throughput and reduces end-to-end delay.
- A Markov chain-based model of the BAMR for an underlay cognitive radio network operating in virtual duplex mode is developed. This model simultaneously takes into account the inter-relay interference and the power constraints imposed by the primary network. The interference from the primary user to the secondary user (at both the receiving relay and the destination) is also considered in the model.
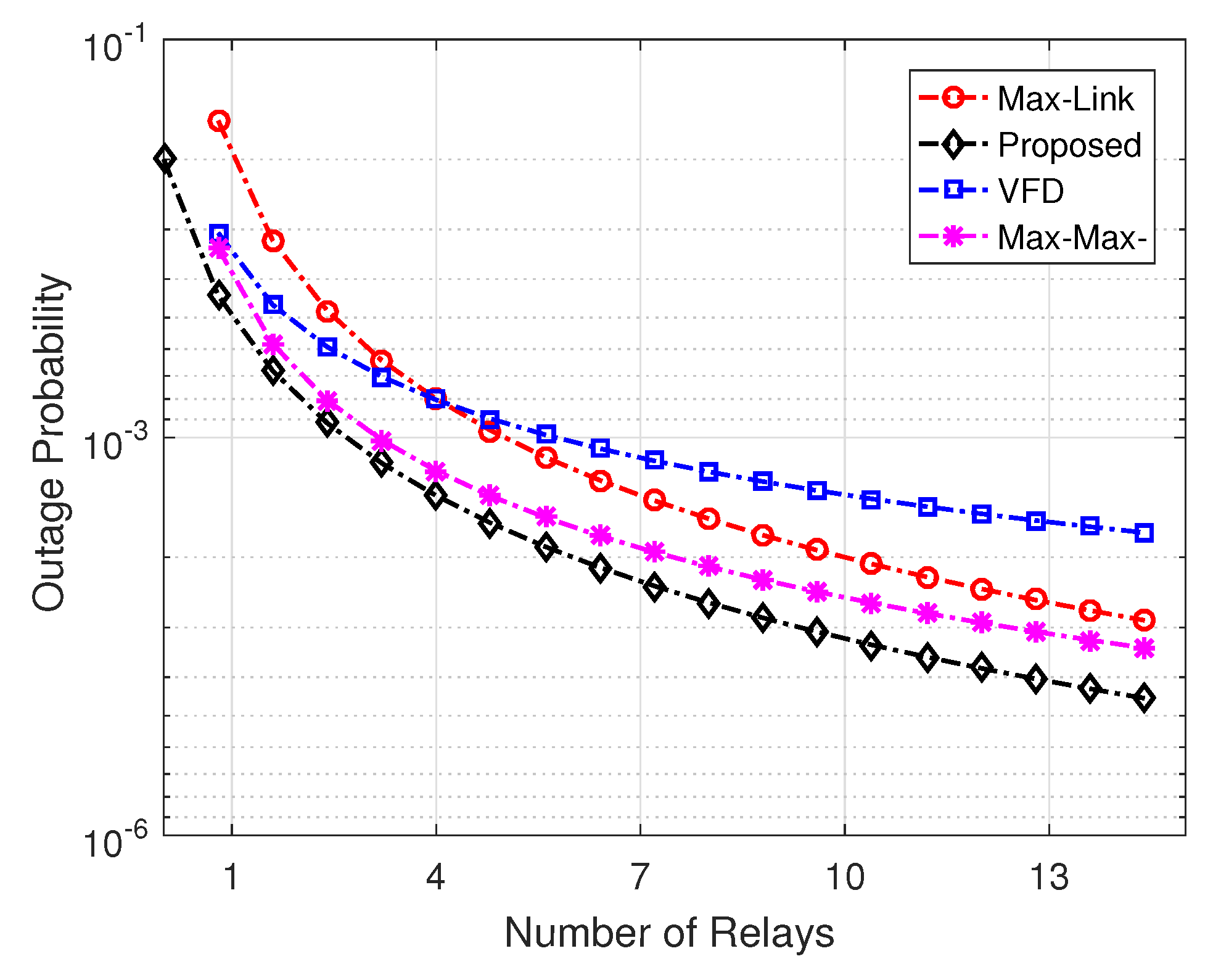
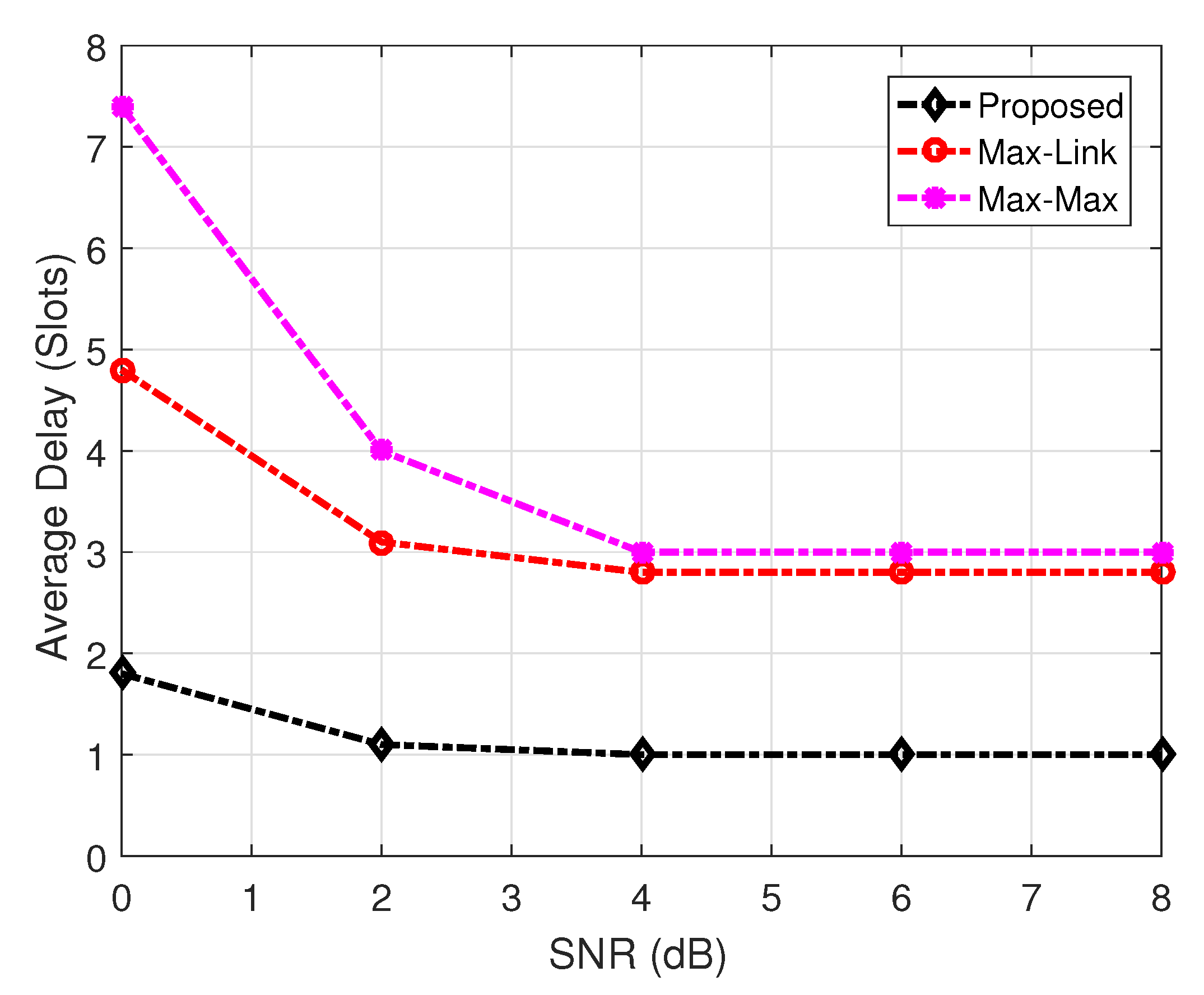
- Considering finite buffers at the source and the relay cluster, the outage probability, delay, and target rate/capacity are analyzed using the developed Markov modeling framework. For the delay performance, end-to-end delay rather than the delay only at the relay nodes is considered in this work. When compared with contemporary schemes, like max-max [7] and max-link [8], the proposed scheme shows significant improvement in key performance measures that include outage probability, throughput, and average packet delay.
2. Related Work on Buffer-Aided CRN
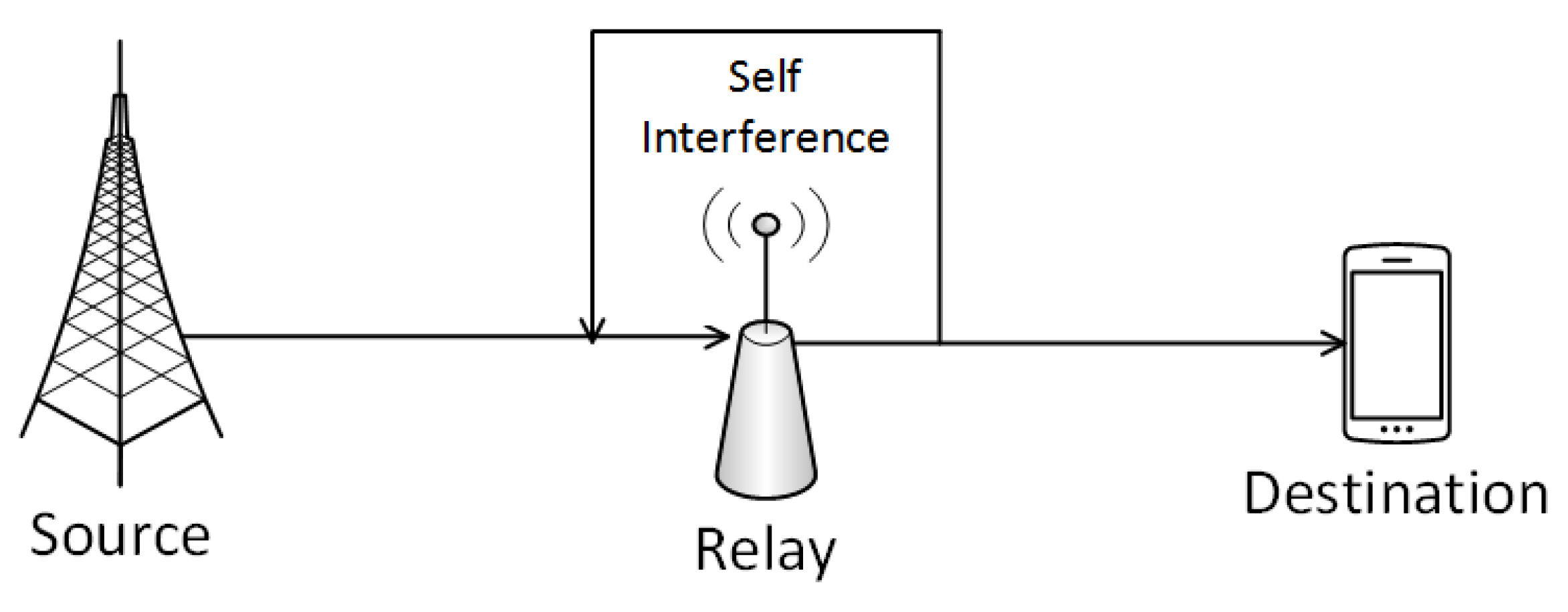
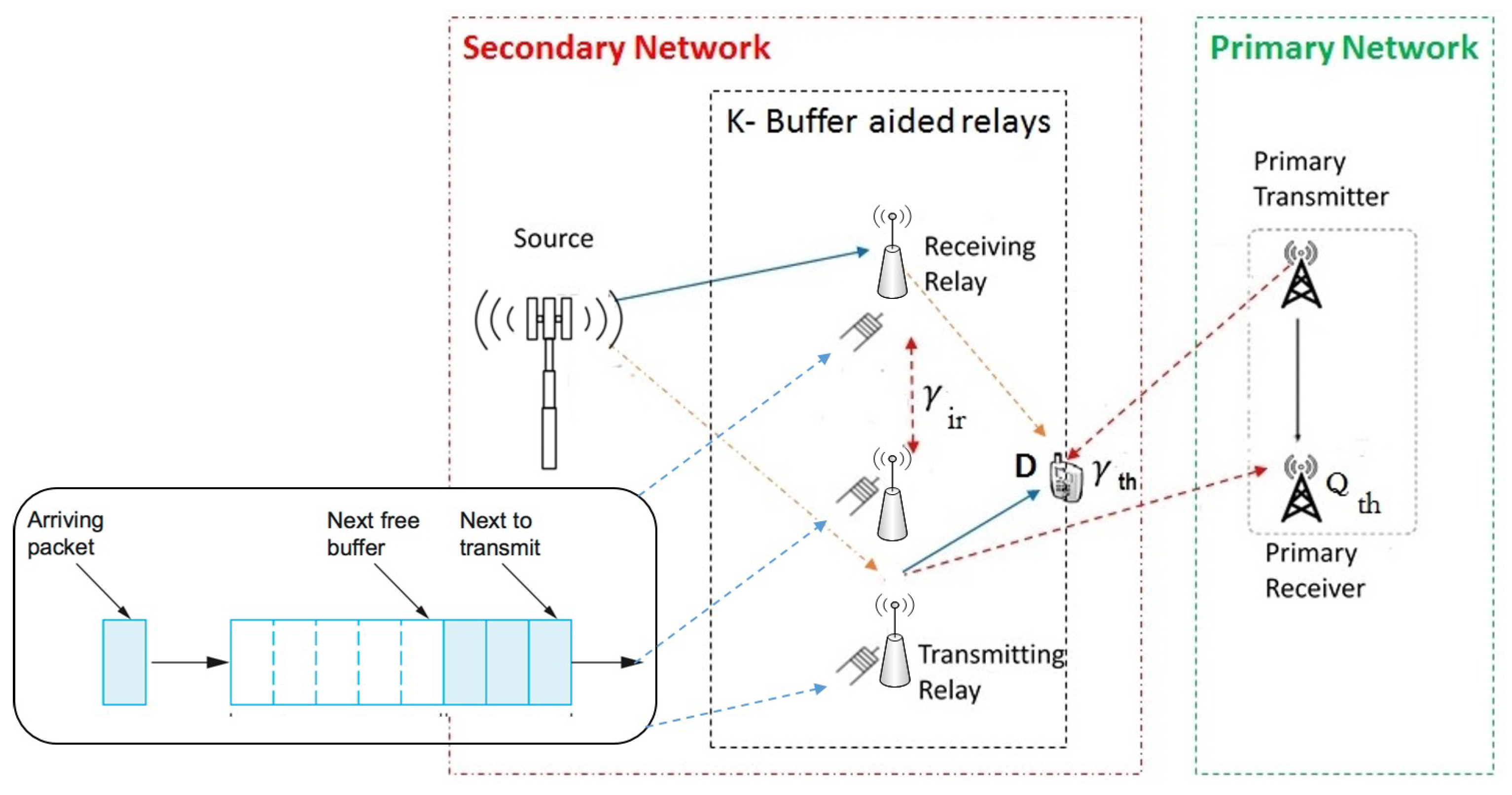
3. Preliminaries and System Model
3.1. Preliminaries
3.2. CSI and Buffer State-Based Scheme
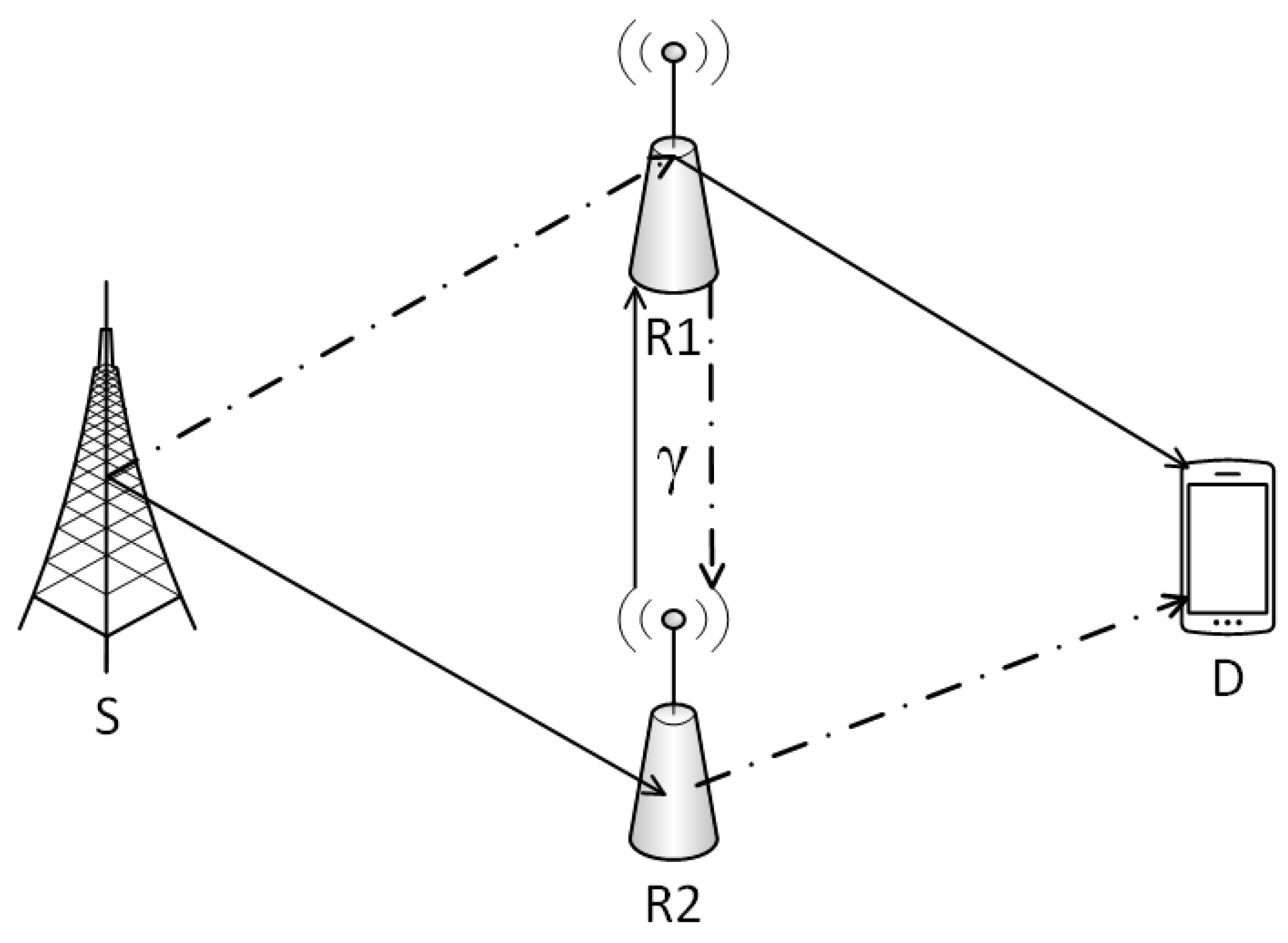
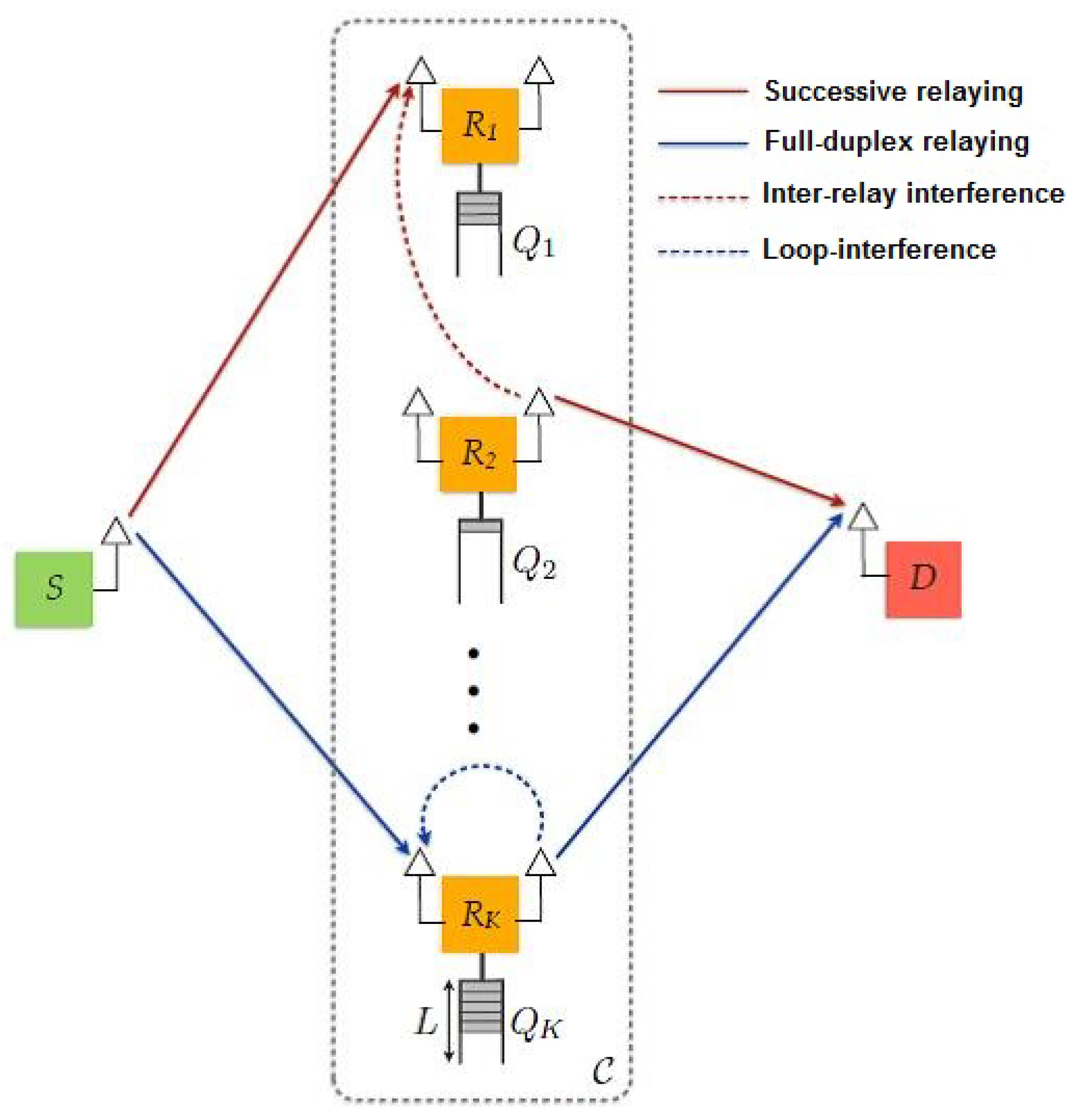
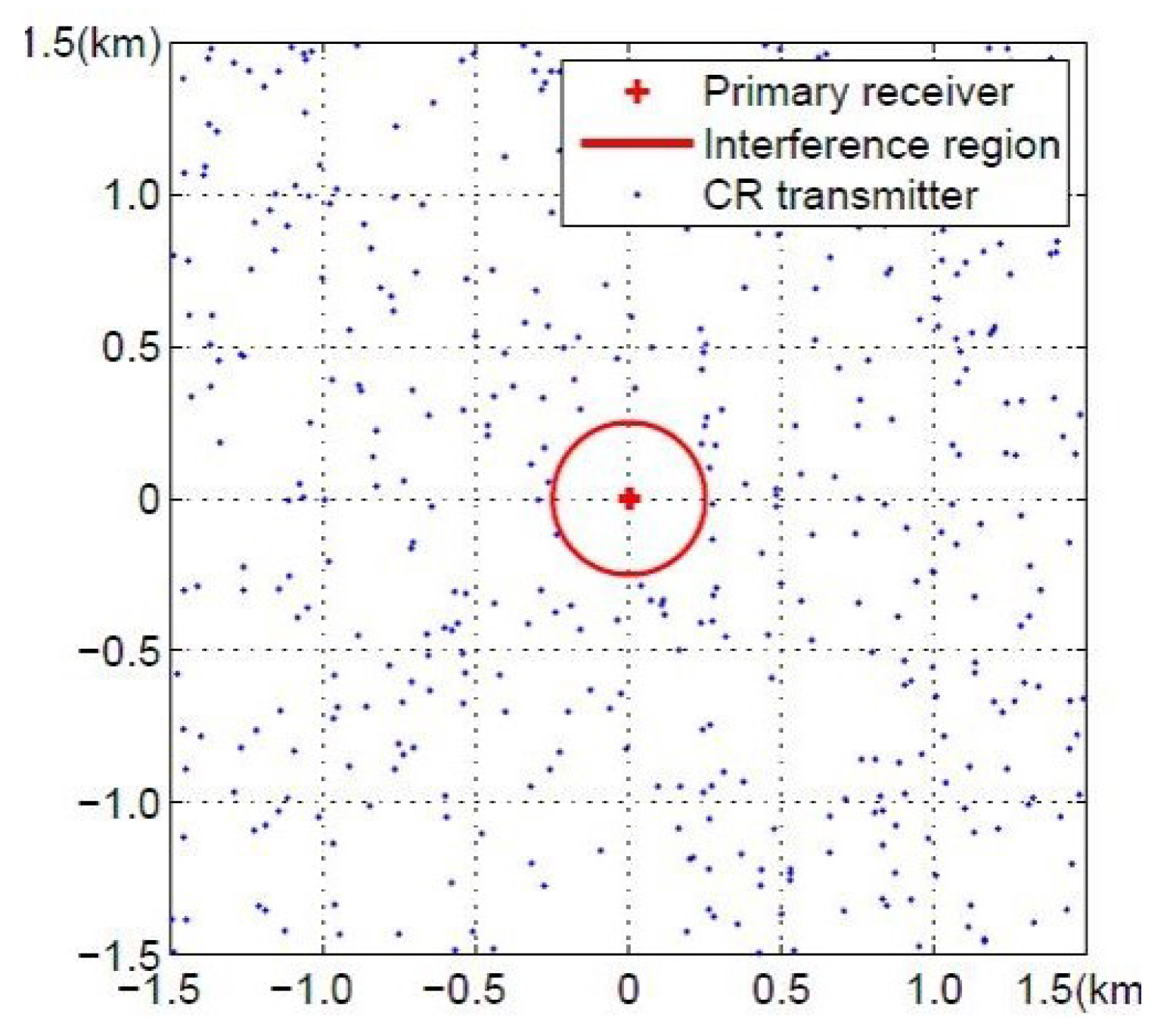
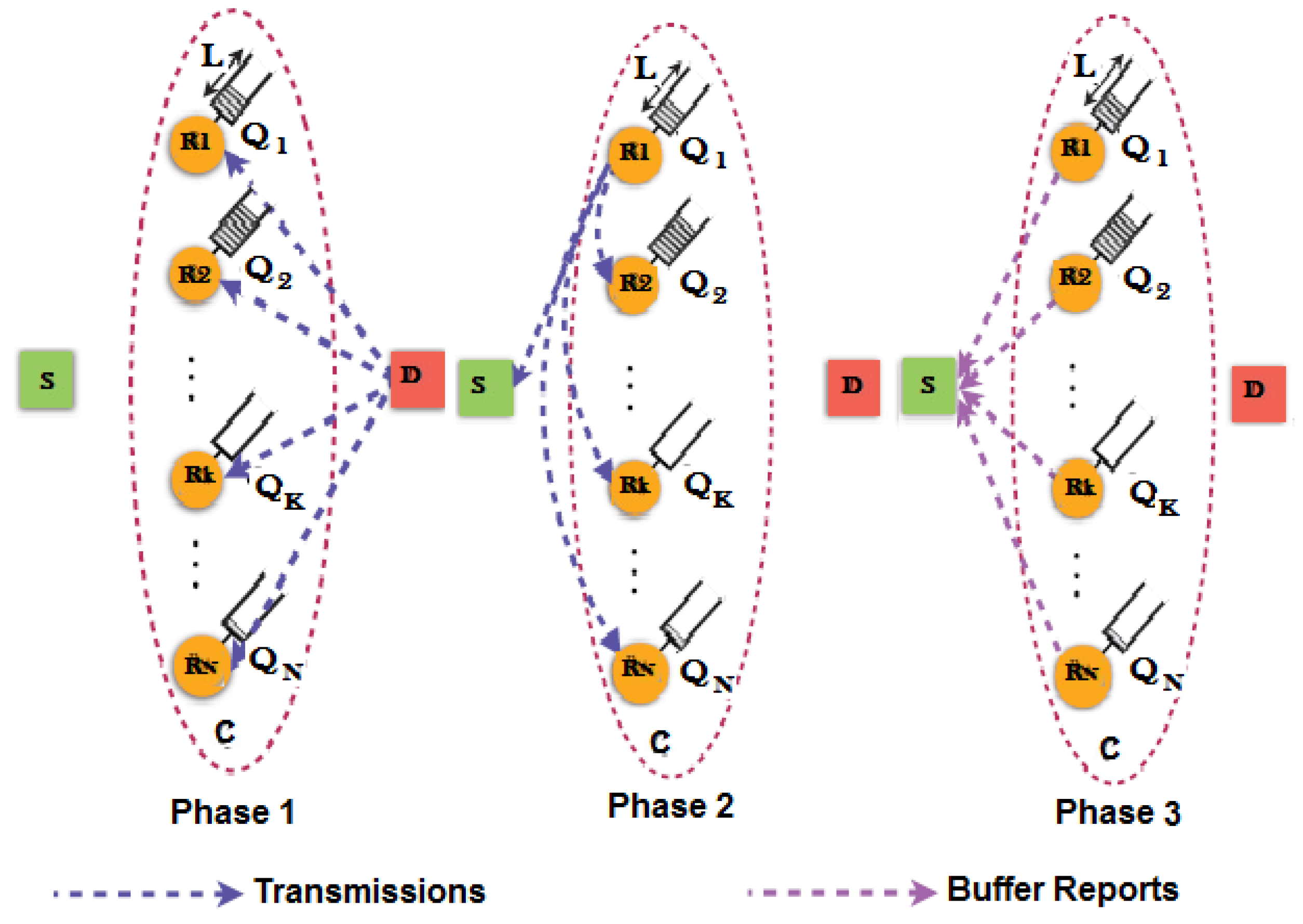
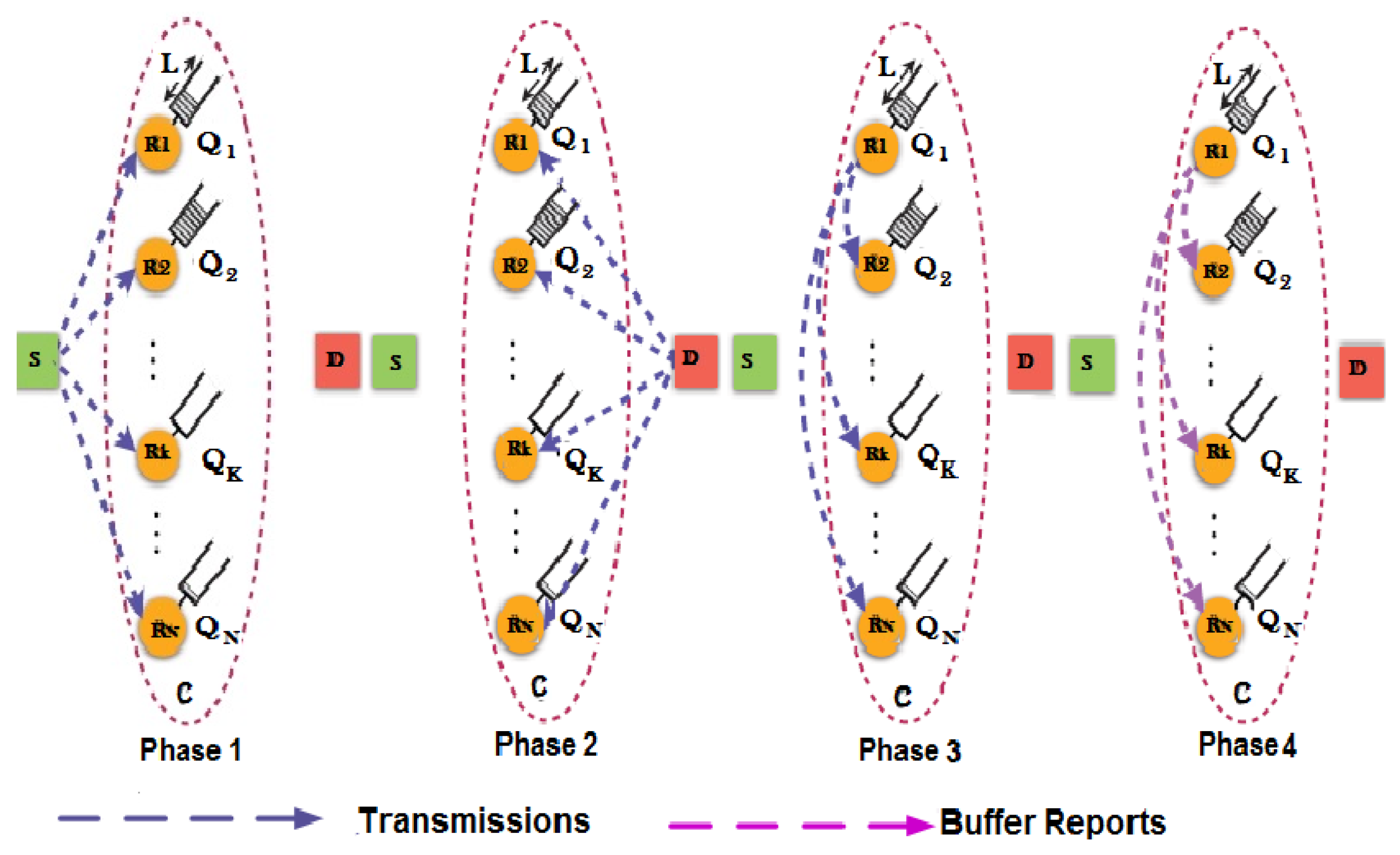
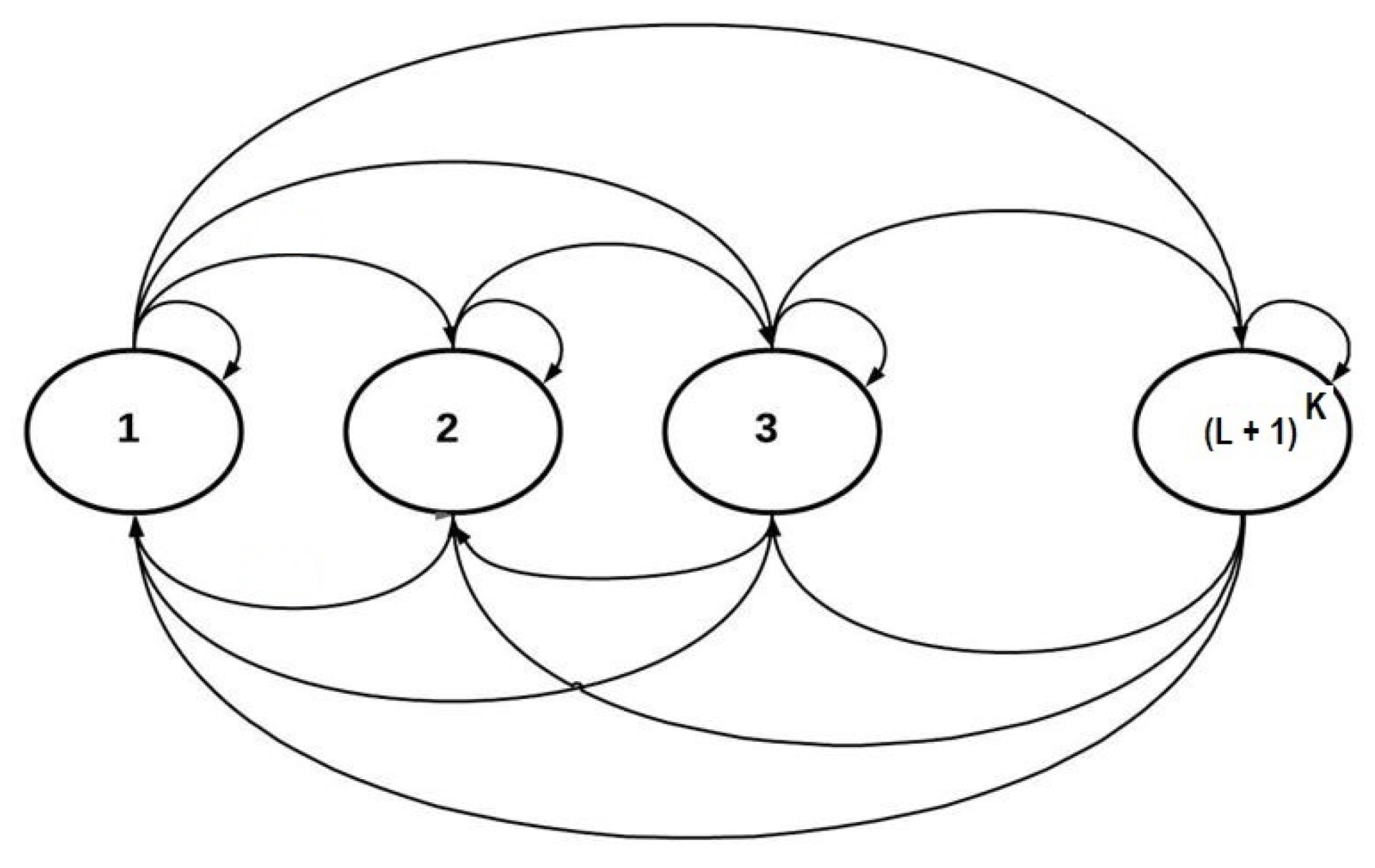
3.3. System Model
3.4. Analytical Modeling
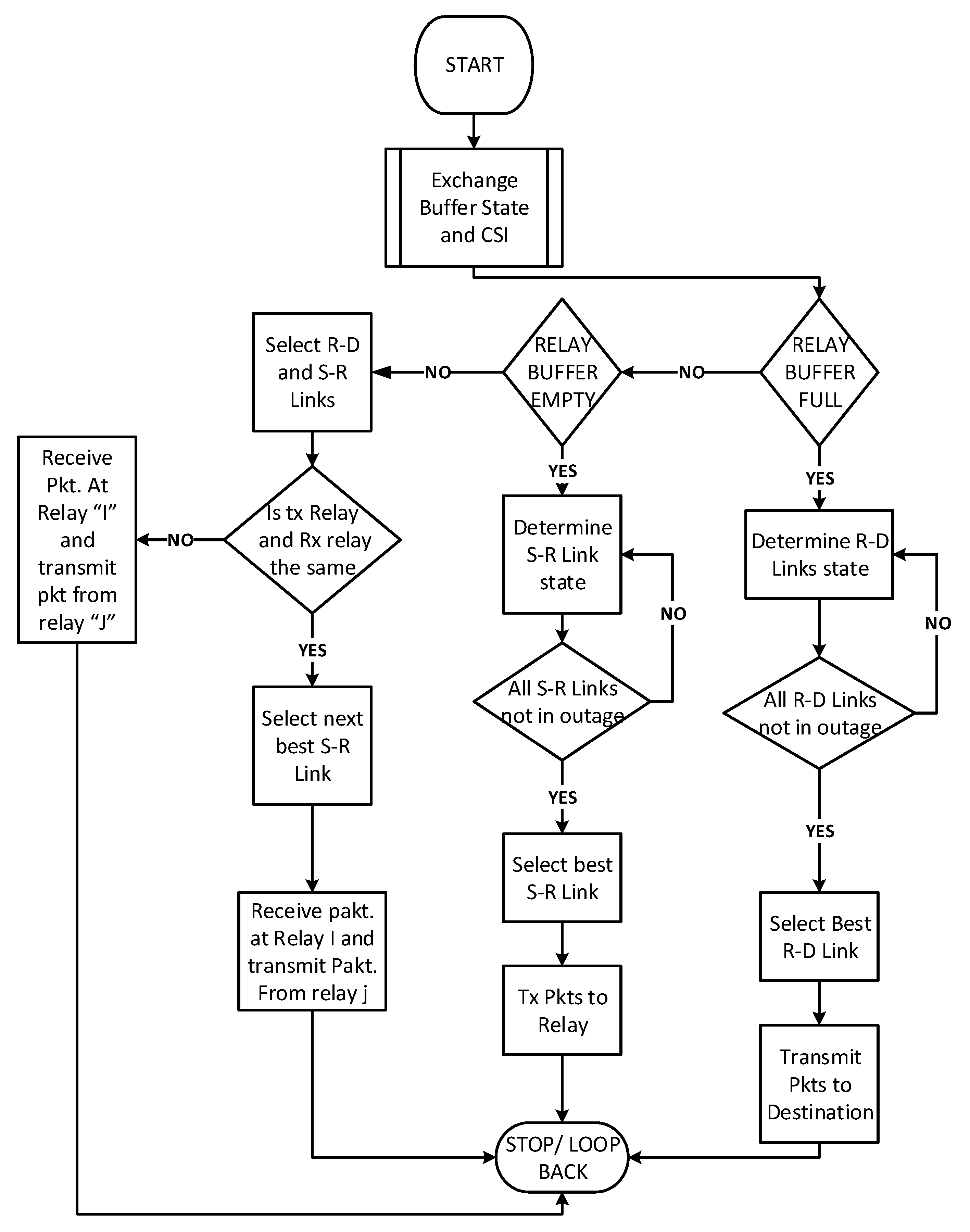
3.5. Relay Selection Scheme
- The participating relays of the cluster exchange CSI and buffer state information.
- Among all available relay-to-destination links, select the link j with the highest SINR .
- Among all available source-to-relay links, select the link i with the highest SINR .
- Check that the same relay is not selected for reception and transmission, i.e., ; if the same, then select the next best for receiving as the transmitting relay will be given priority.
- Check the transmission power constraints imposed by the primary network are met.
- If the receiving relay buffer is not full, then transmit packets to it, and if the transmitting relay is not empty, transmit packets from this relay; both may be done simultaneously, i.e., virtual duplex relaying is enabled.
- The scheme goes into outage if no link with requisite SINR is available or the receiving relay buffer is full and the transmitting relay buffer is empty, thus resulting in no change in any of the buffers, i.e., no state change occurs.
- To exploit higher data rate capability, the priority is given to the link with better SINR from , but in the case of the source buffer getting full, the priority will change, and links with higher SINR will be selected.
4. Outage Probability Analysis
4.1. Analysis Using Markov Chain
4.2. Stationary Probabilities
4.3. Delay Analysis
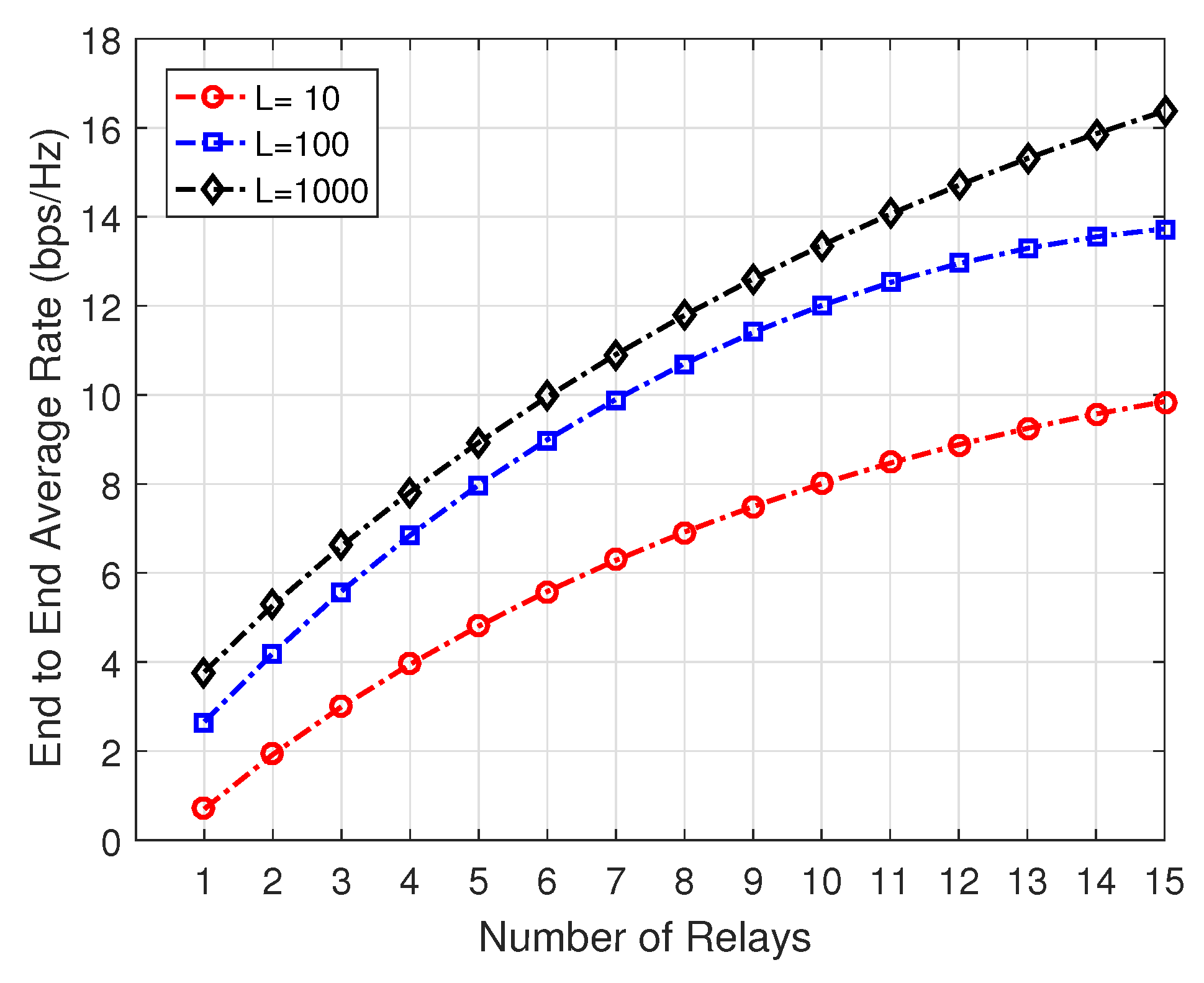
4.4. Data Rate and Capacity Analysis
5. Results and Discussion
6. Future Work
6.1. Internet of Things
6.2. D2D Communications
6.3. Proactive Caching
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| CRN | cognitive radio network |
| BA | buffer aided |
| BAFD | buffer-aided full-duplex |
| DTN | delay-tolerant network |
| IoT | Internet of Things |
| IID | independent and identically distributed |
| LI | loop interference |
| CSI | channel state information |
| MC | Markov chain |
| DPC | dirty paper coding |
| FD | full duplex |
| LTE | Long-Term Evolution |
| PU | primary user |
| SU | secondary user |
| VFD | virtual full duplex |
| DF | decode and forward |
| AF | amplify and forward |
| CoF | compute and forward |
| AWGN | additive white Gaussian noise |
References
- Peters, S.W.; Heath, R.W., Jr. The future of WiMAX: Multihop relaying with IEEE 802.16 j. IEEE Commun. Mag. 2009, 47, 104–111. [Google Scholar] [CrossRef]
- Peters, S.W.; Panah, A.Y.; Truong, K.T.; Heath, R.W. Relay architectures for 3GPP LTE-advanced. EURASIP J. Wirel. Commun. Netw. 2009, 2009, 618787. [Google Scholar] [CrossRef]
- Parkvall, S.; Dahlman, E.; Furuskar, A.; Jading, Y.; Olsson, M.; Wanstedt, S.; Zangi, K. LTE-advanced-evolving LTE towards IMT-advanced. In Proceedings of the 2008 IEEE 68th Vehicular Technology Conference, Calgary, BC, Canada, 21–24 September 2008; pp. 1–5. [Google Scholar]
- Mitola, J.; Maguire, G.Q. Cognitive radio: Making software radios more personal. IEEE Pers. Commun. 1999, 6, 13–18. [Google Scholar] [CrossRef]
- Giupponi, L.; Ibars, C. Distributed cooperation in cognitive radio networks: Overlay versus underlay paradigm. In Proceedings of the VTC Spring 2009-IEEE 69th Vehicular Technology Conference, Barcelona, Spain, 26–29 April 2009; pp. 1–6. [Google Scholar]
- Stevenson, C.R.; Chouinard, G.; Lei, Z.; Hu, W.; Shellhammer, S.J.; Caldwell, W. IEEE 802.22: The first cognitive radio wireless regional area network standard. IEEE Commun. Mag. 2009, 47, 130–138. [Google Scholar] [CrossRef]
- Ikhlef, A.; Michalopoulos, D.S.; Schober, R. Max-max relay selection for relays with buffers. IEEE Trans. Wirel. Commun. 2012, 11, 1124–1135. [Google Scholar] [CrossRef]
- Tian, Z.; Chen, G.; Gong, Y.; Chen, Z.; Chambers, J.A. Buffer-aided max-link relay selection in amplify-and-forward cooperative networks. IEEE Trans. Veh. Technol. 2015, 64, 553–565. [Google Scholar] [CrossRef]
- Nomikos, N.; Charalambous, T.; Krikidis, I.; Skoutas, D.N.; Vouyioukas, D.; Johansson, M.; Skianis, C. A survey on buffer-aided relay selection. IEEE Commun. Surv. Tutor. 2016, 18, 1073–1097. [Google Scholar] [CrossRef]
- Poulimeneas, D.; Charalambous, T.; Nomikos, N.; Krikidis, I.; Vouyioukas, D.; Johansson, M. Delay-and diversity-aware buffer-aided relay selection policies in cooperative networks. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3–6 April 2016; pp. 1–6. [Google Scholar]
- Sultan, R.A.; Sultan, A.K.; Youssef, M. Buffered-relay selection in an underlay cognitive radio network. In Proceedings of the 2013 11th International Symposium and Workshops on Modeling and Optimization in Mobile, Ad Hoc and Wireless Networks (WiOpt), Tsukuba Science City, Japan, 13–17 May 2013; pp. 201–207. [Google Scholar]
- Darabi, M.; Maham, B.; Zhou, X.; Saad, W. Buffer-aided relay selection with interference cancellation and secondary power minimization for cognitive radio networks. In Proceedings of the 2014 IEEE International Symposium on Dynamic Spectrum Access Networks (DYSPAN), McLean, VA, USA, 1–4 April 2014; pp. 137–140. [Google Scholar]
- Chen, G.; Tian, Z.; Gong, Y.; Chambers, J. Decode-and-forward buffer-aided relay selection in cognitive relay networks. IEEE Trans. Veh. Technol. 2014, 63, 4723–4728. [Google Scholar] [CrossRef]
- Tian, Z.; Gong, Y.; Chen, G.; Chambers, J.A. Buffer-aided relay selection with reduced packet delay in cooperative networks. IEEE Trans. Veh. Technol. 2017, 66, 2567–2575. [Google Scholar] [CrossRef]
- Duarte, M.; Dick, C.; Sabharwal, A. Experiment-driven characterization of full-duplex wireless systems. IEEE Trans. Wirel. Commun. 2012, 11, 4296–4307. [Google Scholar] [CrossRef]
- Bliss, D.; Parker, P.; Margetts, A. Simultaneous transmission and reception for improved wireless network performance. In Proceedings of the 2007 IEEE/SP 14th Workshop on Statistical Signal Processing, Madison, WI, USA, 26–29 August 2007; pp. 478–482. [Google Scholar]
- Bharadia, D.; McMilin, E.; Katti, S. Full duplex radios. In ACM SIGCOMM Computer Communication Review; ACM: New York, NY, USA, 2013; Volume 43, pp. 375–386. [Google Scholar]
- Oechtering, T.; Sezgin, A. A new cooperative transmission scheme using the space-time delay code. In Proceedings of the ITG Workshop on Smart Antennas (IEEE Cat. No. 04EX802), Munich, Germany, 18–19 March 2004; pp. 41–48. [Google Scholar]
- Bagheri, H.; Motahari, A.S.; Khandani, A.K. On the capacity of the half-duplex diamond channel. In Proceedings of the 2010 IEEE International Symposium on Information Theory, Austin, TX, USA, 13–18 June 2010; pp. 649–653. [Google Scholar]
- Hong, S.; Caire, G. Virtual full-duplex relaying with half-duplex relays. IEEE Trans. Inf. Theory 2015, 61, 4700–4720. [Google Scholar] [CrossRef]
- Michalopoulos, D.S.; Karagiannidis, G.K. Bypassing orthogonal relaying transmissions via spatial signal separation. IEEE Trans. Commun. 2010, 58, 3028–3038. [Google Scholar] [CrossRef]
- Ikhlef, A.; Kim, J.; Schober, R. Mimicking full-duplex relaying using half-duplex relays with buffers. IEEE Trans. Veh. Technol. 2012, 61, 3025–3037. [Google Scholar] [CrossRef]
- Karakus, C.; Suhas, D. Opportunistic scheduling for full-duplex uplink-downlink networks. proceedings of the International Symposium on Information Theory (ISIT), Hong Kong, China, 14–19 June 2015; pp. 1019–1023. [Google Scholar]
- Muthuramalingam, B.; Bhashyam, S.; Thangaraj, A. A decode and forward protocol for two-stage Gaussian relay networks. IEEE Trans. Commun. 2012, 60, 68–73. [Google Scholar] [CrossRef]
- Avestimehr, S.; Diggavi, S.; Tse, D. Wireless network information flow: A deterministic approach. arXiv 2009, arXiv:0906.5394. [Google Scholar] [CrossRef]
- Lim, S.H.; Kim, Y.H.; El Gamal, A.; Chung, S.Y. Noisy network coding. In Proceedings of the 2010 IEEE Information Theory Workshop on Information Theory (ITW 2010, Cairo), Cairo, Egypt, 6–8 January 2010; pp. 1–5. [Google Scholar]
- Hou, J.; Kramer, G. Short message noisy network coding with a decode–forward option. IEEE Trans. Inf. Theory 2016, 62, 89–107. [Google Scholar] [CrossRef]
- Lan, P.; Sun, F.; Chen, L.; Xue, P.; Hou, J. Power allocation and relay selection for cognitive relay networks with primary QoS constraint. IEEE Wirel. Commun. Lett. 2013, 2, 583–586. [Google Scholar] [CrossRef]
- Kim, S.M.; Kim, J. Virtual full-duplex relay selection in relay-assisted cognitive radio networks. In Proceedings of the 2017 Ninth International Conference on Ubiquitous and Future Networks (ICUFN), Milan, Italy, 4–7 July 2017; pp. 12–14. [Google Scholar]

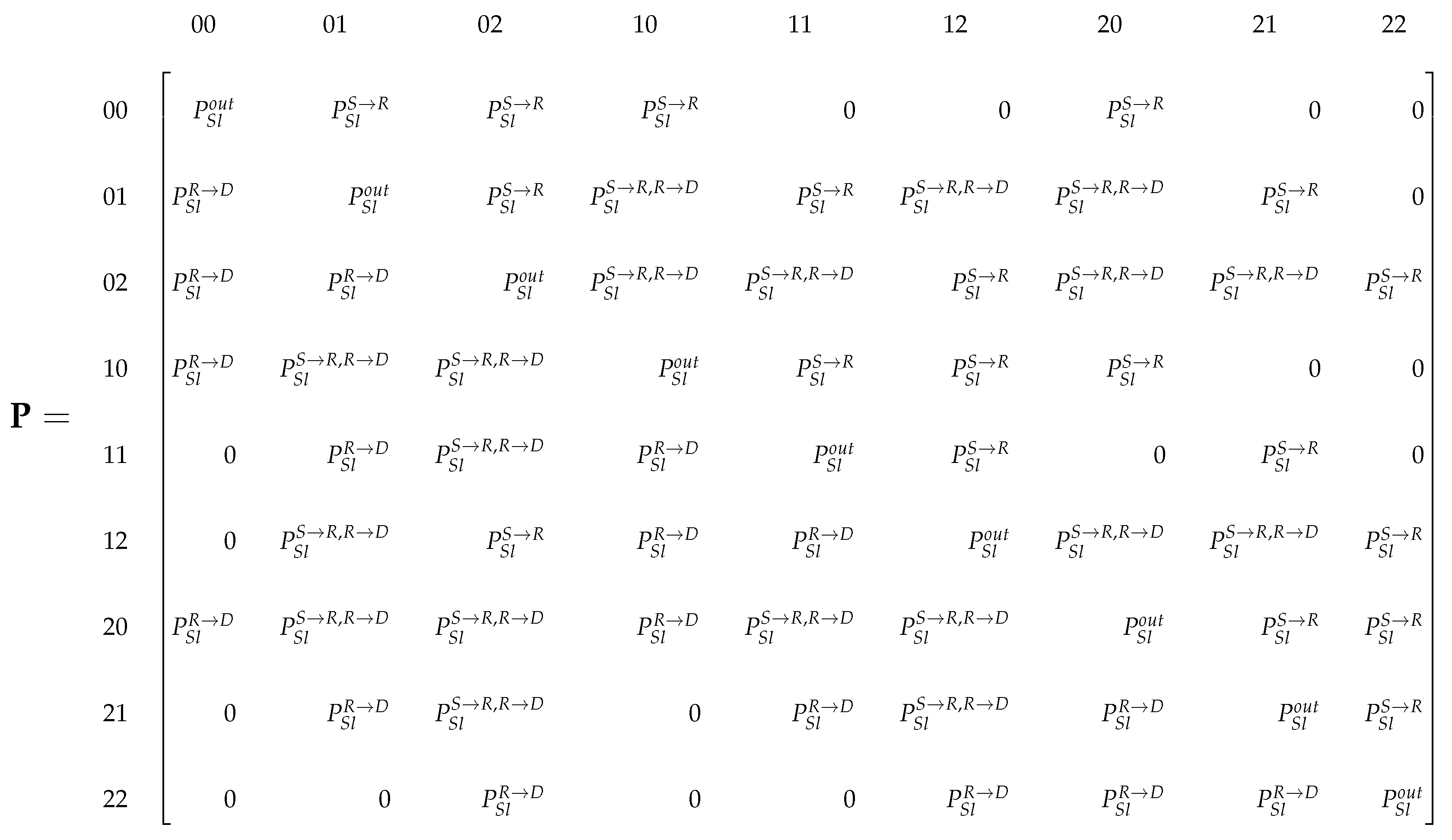



© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alvi, S.A.; Hussain, R.; Hasan, Q.U.; Malik, S.A. Improved Buffer-Aided Multi-Hop Relaying with Reduced Outage and Packet Delay in Cognitive Radio Networks. Electronics 2019, 8, 895. https://doi.org/10.3390/electronics8080895
Alvi SA, Hussain R, Hasan QU, Malik SA. Improved Buffer-Aided Multi-Hop Relaying with Reduced Outage and Packet Delay in Cognitive Radio Networks. Electronics. 2019; 8(8):895. https://doi.org/10.3390/electronics8080895
Chicago/Turabian StyleAlvi, Shakeel Ahmed, Riaz Hussain, Qadeer Ul Hasan, and Shahzad Ali Malik. 2019. "Improved Buffer-Aided Multi-Hop Relaying with Reduced Outage and Packet Delay in Cognitive Radio Networks" Electronics 8, no. 8: 895. https://doi.org/10.3390/electronics8080895





