Biological Viral Infection Watermarking Architecture of MPEG/H.264/AVC/HEVC
Abstract
:1. Introduction
2. Biological Viral Infectious Watermarking (VIW) Architecture
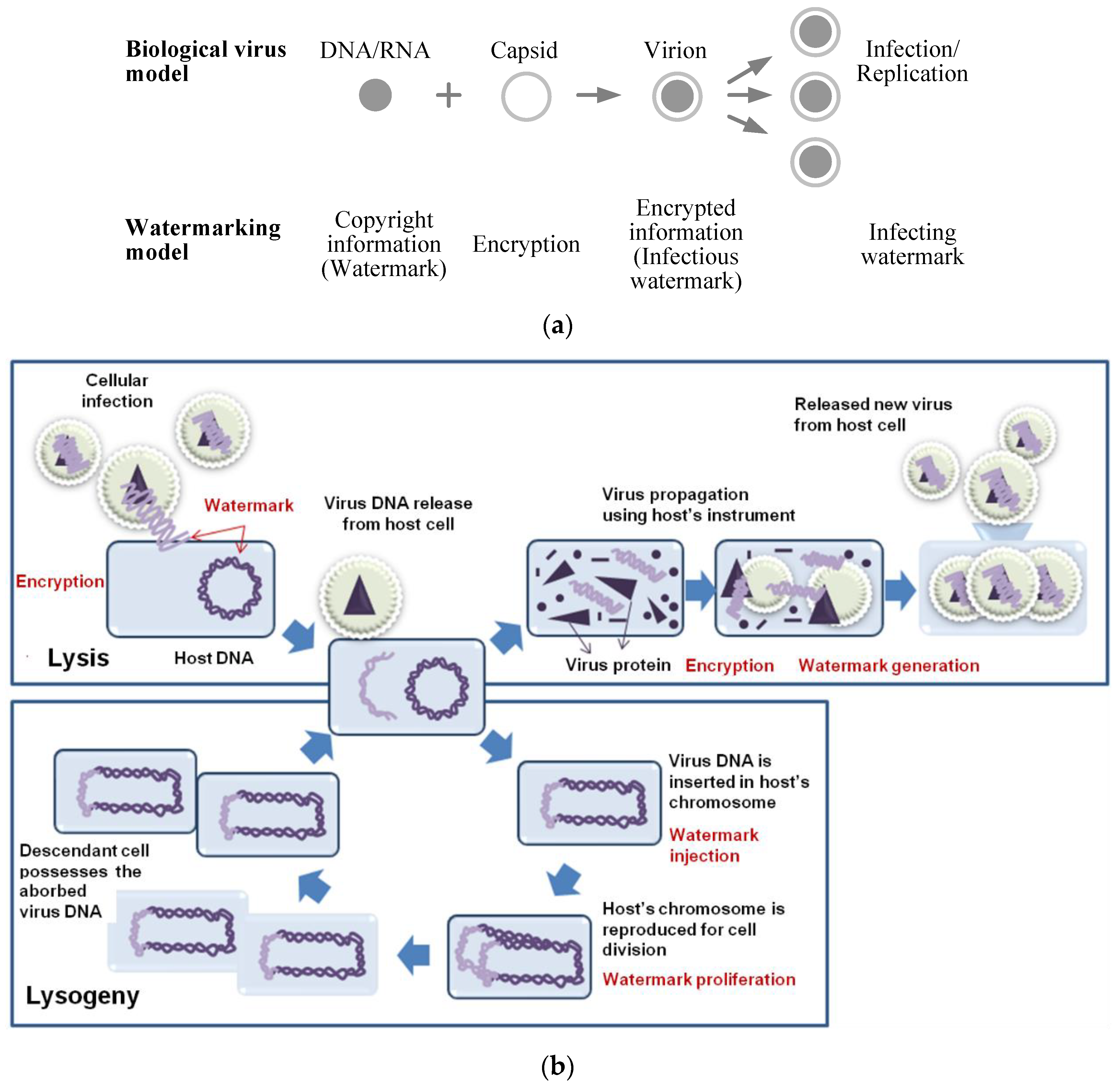
2.1. Biological Virus Model
- DNA/RNA: It can be considered as the watermark for copyright and access control of valuable video content.
- Capsid: It is a nucleic acid surrounded by a protective protein coat. It can be considered as the process of encryption and decryption of the copyright information.
- Virion: The combination of DNA and capsid generates virions of complete virus particle. Virions can be classified as pathogen, mutant, and contagion, depending on the way and type of infection. We use the name and concept of pathogen, mutant, and contagion and model VIW by encrypting the information of copyright and authority of videos.
2.1.1. Virus Infection
- (1)
- The infection and growth of virus have been accomplished by the process that a virion breaks in a target cell and delivers genetic material to cell. We model the watermarking process as the virus infection and growth process.
- (2)
- Here, there are many ways how descendant virions are made on the type of cells. Different ways can be modeled as watermarking methods that are compatible with the types of contents or codecs.
- (3)
- When the virus spreads to cells, hundreds of descendants are reproduced from the virion. This reproduction can be modelled as a re-hiding process of the infectious watermark during content reproduction or transcoding of video.
2.1.2. Virus Reproduction
- A lysis virus that disassembles or destroys a host cell can be modeled as an authority code or permission code for decoded video contents or display devices. A lysogeny virus that hides genetic material in host cells until it becomes reproductive can be modeled as copyright protection or authentication for hidden watermarks.
- Virus infections within a host cell are considered as a process of infectious watermarking. The infective ways of a virus are different on the structure of the host cell. When a host cell is considered to be a video content, the watermarking method can be applied differently depending on the type of video content or compressed bit stream.
- Because biological viruses are reproduced or spread by infected hosts, we design a watermark that should spread wholly through the reproduction or trans-coding of video contents.
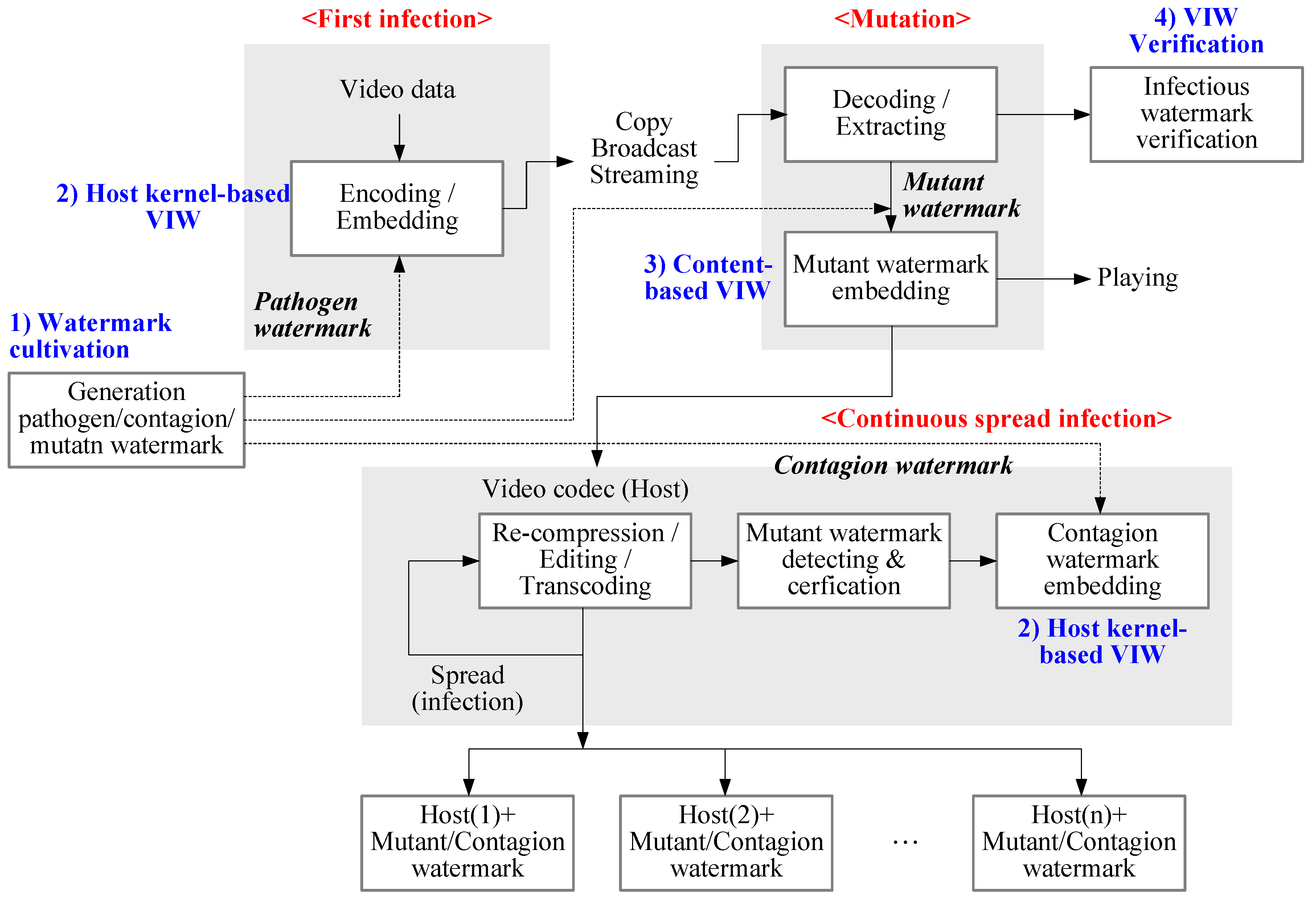
2.2. Technical VIW Concepts for Video Codec
2.2.1. Watermark Cultivation for Generation and Management
- Two watermarks on host type: Pathogen and contagion watermarks for host codec and mutant watermark for host content
- Watermark cultivation by the combination of copyright/ownership and authority: Reliable watermark cultivation by user information. Compatibility of copyright/ownership and authority in the mutation of pathogen, contagion, and mutant watermark
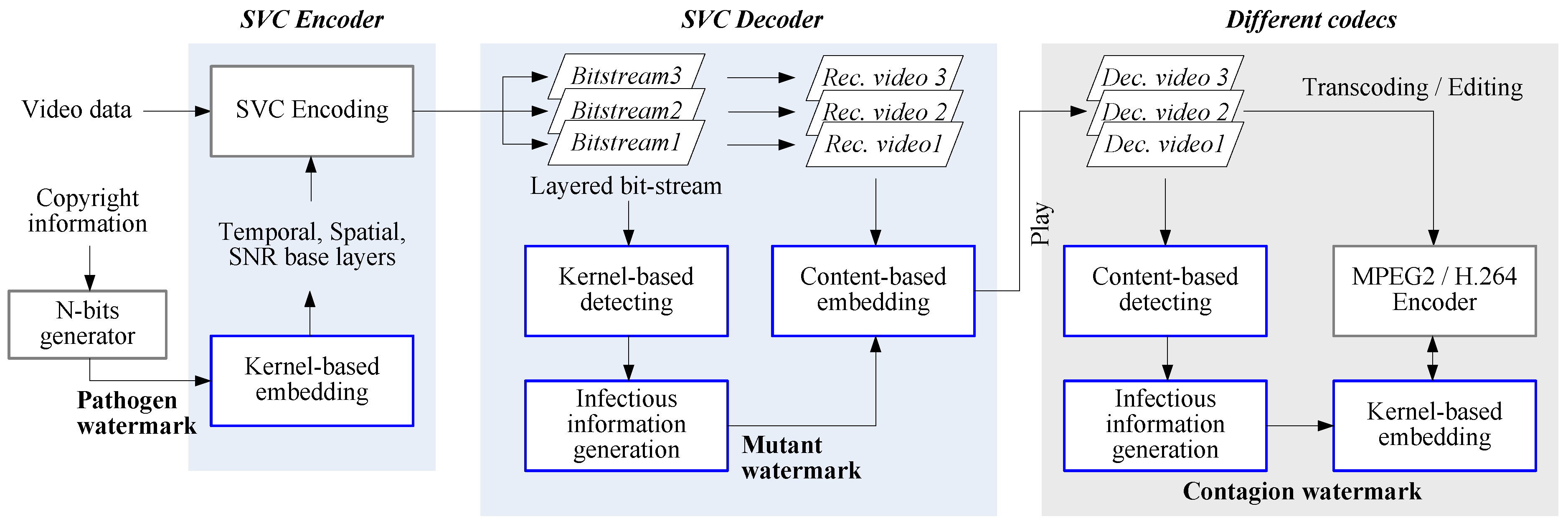
- Pathogen watermark: It is the infectious information for producers or copyright owners in the meaning of lysis virus. This watermark can be infected in macro-blocks of base layer in hierarchical video codec like SVC and MVC.
- Mutant watermark: It is the mutant of pathogen watermark and it can be used in content-based VIW for decoded and reconstructed video. This watermark can be infected into all layers in hierarchical video codec.
- Contagion watermark: It is the transfectant of extracted mutant watermark in decoding process. This watermark can be infected in the process of storing or re-compressing after video editing.
2.2.2. Host Kernel-Based VIW
- Infectious watermarking based on quantization, DCT/DWT kernel, or ME/MC in the encoding process.
- Reversible infectious watermarking in certification of authority and irreversible infectious watermarking in non-certification of authority.
2.2.3. Content-Based VIW
- Generation of first host watermarked video stream by the pathogen watermark or infected video stream by the mutant watermark;
- Robust infectious watermarking in spatial or frequency domain;
- Recovery or regeneration of attacked watermark;
- Intentional video degradation in case of non-certification.
2.2.4. VIW Verification (WV)
- Reliable verification technique;
- Policy of authority control for copying, link, editing using verified infectious watermark: Authorization technique in encoder/decoder, protocol, or syntax for reliability verification and authority control.
3. Proposed Viral Infectious Watermarking Model
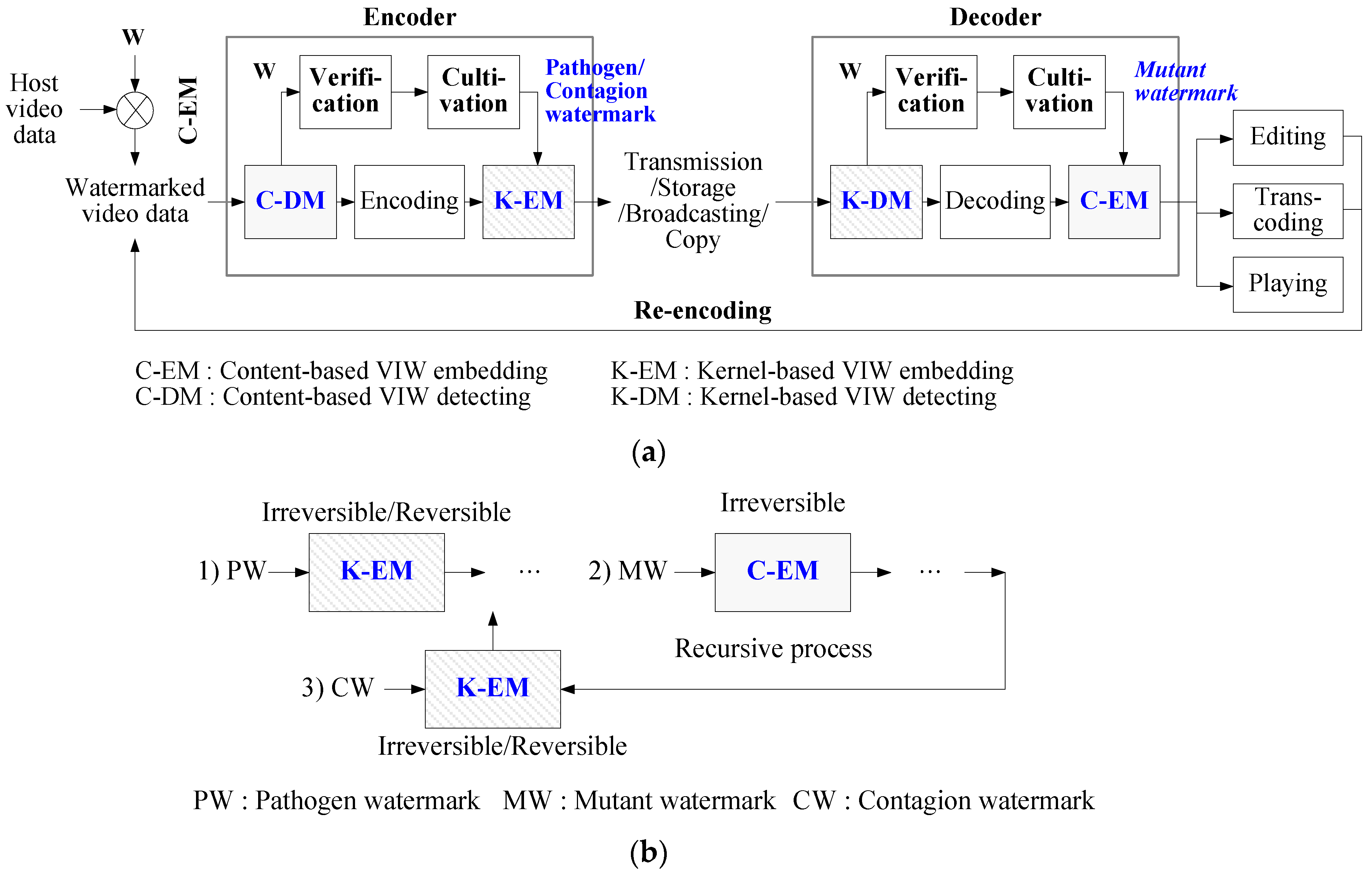
3.1. Overall of VIW Application for Video Codec
- Before encoding or re-encoding, C-DM detects the watermark in host or re-encoded video.
- IWC regenerates the watermark after verifying it.
- K-EM embeds pathogen and contagion watermarks into video stream. K-EM/K-DM has two properties of irreversible and reversible. The irreversible K-EM infects the watermark wholly under trans-coding between heterogeneous codecs and guarantees the safety of video contents against editing, trans-coding, or re-compression. The reversible K-EM regenerates and authenticates the watermark continuously and controls video contents.
- When watermarked video streams are played or edited on the decoder stage, the watermark verification and regeneration are performed in a similar process on the encoder stage. Then K-DM detects the pathogen or contagion watermark, and C-EM re-embeds the regenerated mutant watermark.
3.2. Infectious Watermark Cultivation (IWC)
3.3. Kernel-Based Watermarking (K-EM and K-DM) for Pathogen or Contagion Watermark
3.3.1. Irreversible K-EM/K-DM
3.3.2. Reversible K-EM/K-DM
3.4. Content-Based Watermarking (C-EM and C-DM) for Mutant Watermark
4. Experimental Results
4.1. Experimental Environment
4.2. Performance Comparison of BER and PSNR
4.2.1. BER Comparison
4.2.2. PSNR Comparison
4.3. Proposed Method Analysis
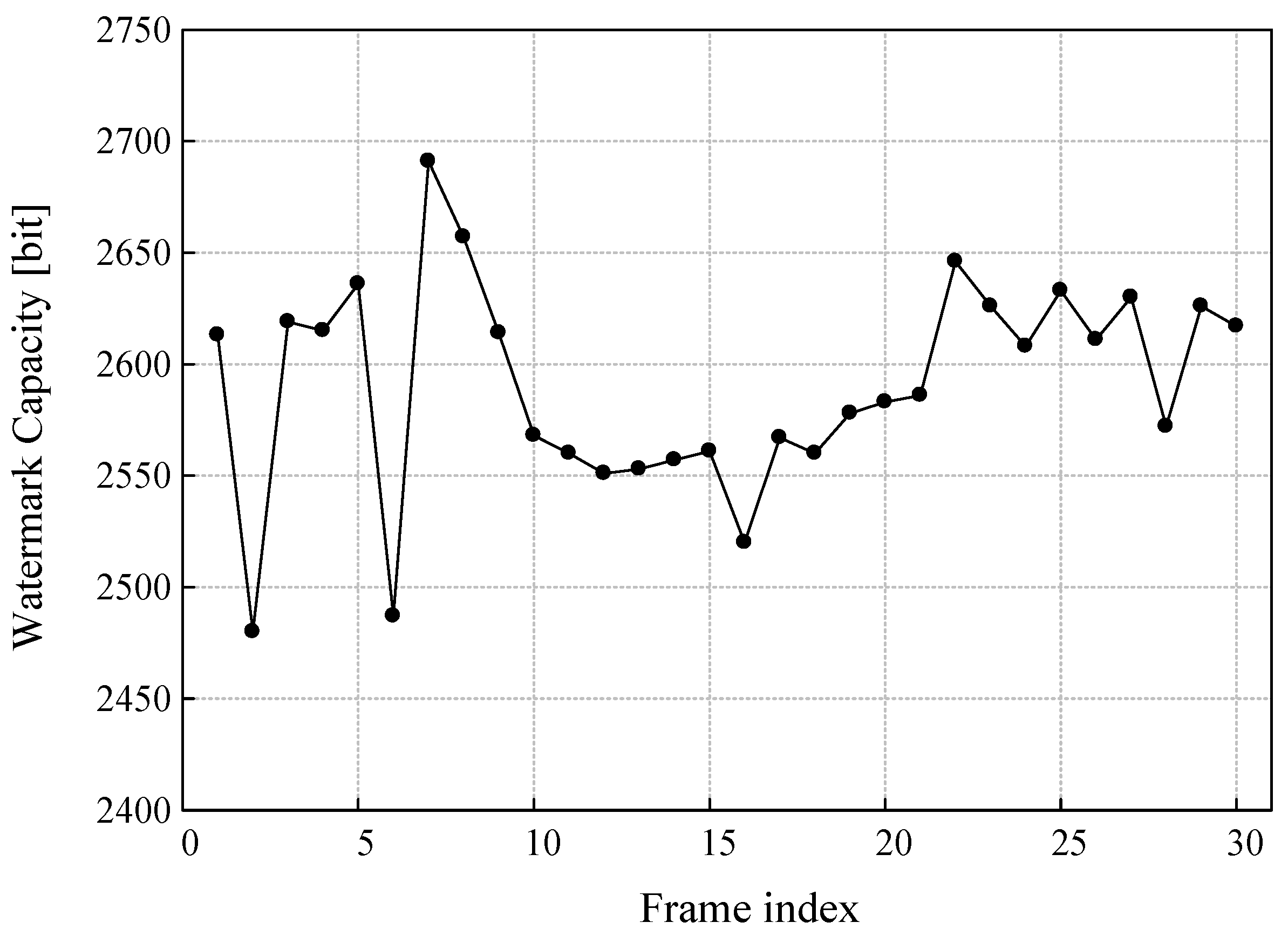
4.3.1. Watermark Capacity
4.3.2. Attack of Compressed Stream
4.3.3. Expired Video Stream
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Hartung, F.; Girod, B. Watermarking of uncompressed and compressed video. Signal Process. 1998, 66, 283–301. [Google Scholar] [CrossRef]
- Swanson, M.D.; Zhu, B.; Chau, B.; Tewfik, A.H. Object-based transparent video watermarking. In Proceedings of the IEEE First Workshop on Multimedia Signal Processing, Princeton, NJ, USA, 23–25 June 1997; pp. 369–374. [Google Scholar]
- Swanson, M.D.; Zhu, B.; Tewfik, A.H. Multiresolution scene-based video watermarking using perceptual models. IEEE J. Sel. Areas Commun. 1998, 16, 540–550. [Google Scholar] [CrossRef]
- Serdean, C.V.; Ambroze, M.A.; Tomlinson, M.; Wade, J.G. DWT-based high-capacity blind video watermarking, invariant to geometrical attacks. IEEE Proc. Vis. Image Signal Process. 2003, 150, 51–58. [Google Scholar] [CrossRef]
- Wang, Y.; Pearmain, A. Blind MPEG-2 video watermarking robust against geometric attacks: A set of approaches in DCT domain. IEEE Trans. Image Process. 2006, 15, 1536–1543. [Google Scholar] [CrossRef] [PubMed]
- Zhang, J.; Ho, A.T.S.; Gang, Q.; Marziliano, P. Robust video watermarking of H.264/AVC. IEEE Trans. Circuits Syst. Video Technol. 2007, 54, 205–209. [Google Scholar] [CrossRef]
- Asikuzzaman, M.; Alam, M.J.; Lambert, A.J.; Pickering, M.R. Imperceptible and robust blind video watermarking using chrominance embedding: A set of approaches in the DT CWT domain. IEEE Trans. Inf. Forensics Secur. 2014, 9, 1502–1517. [Google Scholar] [CrossRef]
- Fallahpour, M.; Shirmohammadi, S.; Semsarzadeh, M.; Zhao, J. Tampering detection in compressed digital video using watermarking. IEEE Trans. Instrum. Meas. 2014, 63, 1057–1072. [Google Scholar] [CrossRef]
- Stutz, T.; Autrusseau, F.; Uhl, A. Non-blind structure-preserving substitution watermarking of H.264/CAVLC inter-frames. IEEE Trans. Multimed. 2014, 16, 1337–1349. [Google Scholar] [CrossRef]
- Khalilian, H.; Bajic, I.V. Video watermarking with empirical PCA-based decoding. IEEE Trans. Image Process. 2013, 22, 4825–4840. [Google Scholar] [CrossRef]
- Boho, A.; Wallendael, G.V.; Dooms, A.; De Cock, J.; Braeckman, G.; Schelkens, P.; Preneel, B.; Van de Walle, R. End-to-end security for video distribution: The combination of encryption, watermarking, and video adaptation. IEEE Signal Process. Mag. 2013, 30, 97–107. [Google Scholar] [CrossRef]
- Wang, L.; Ling, H.; Fuhao, Z.; Zhengding, L. Real-time compressed-domain video watermarking resistance to geometric distortions. IEEE Multimed. 2012, 19, 70–79. [Google Scholar] [CrossRef]
- Lu, J.; Li, L.; Yang, Z. Video watermarking algorithm for H.264 scalable video coding. KSII Trans. Internet Inf. Syst. 2013, 7, 56–67. [Google Scholar]
- Ling, C.; Ur-Rehman, O.; Zhang, W. Semi-fragile watermarking scheme for H.264/AVC video content authentication based on manifold feature. KSII Trans. Internet Inf. Syst. 2014, 8, 4568–4587. [Google Scholar]
- Niu, K.; Yang, X.; Zhang, Y. A novel video reversible data hiding algorithm using motion vector for H.264/AVC. Tsinghua Sci. Technol. 2017, 22, 489–498. [Google Scholar] [CrossRef]
- Xu, D. Commutative encryption and data hiding in HEVC video compression. IEEE Access 2019, 7, 66028–66041. [Google Scholar] [CrossRef]
- Ma, Z.; Huang, J.; Jiang, M.; Niu, X. A video watermarking DRM method based on H.264 compressed domain with low bit-rate increasement. Chin. J. Electron. 2016, 25, 641–647. [Google Scholar] [CrossRef]
- Mareen, H.; Praeter, J.D.; Wallendael, G.V.; Lambert, P. A scalable architecture for uncompressed-domain watermarked videos. IEEE Trans. Inf. Forensics Secur. 2019, 14, 1432–1444. [Google Scholar] [CrossRef]
- Abdi, L.; Faten, B.A.; Meddeb, A. Real-time watermarking algorithm of H.264/AVC video stream. Int. Arab J. Inf. Technol. 2017, 14, 168–174. [Google Scholar]
- Jang, B.J.; Lee, S.H.; Lim, S.H.; Kwon, K.R. Biological infectious watermarking model for video copyright protection. J. Inf. Process. Syst. 2015, 11, 280–294. [Google Scholar]
- Yang, F.; Wang, C.; Huang, W.; Zhou, X. Embedding binary image watermark in DC components of all phase discrete cosine biorthogonal transform. Int. J. Secur. Its Appl. 2015, 8, 125–136. [Google Scholar] [CrossRef]
- Zhou, X.; Zhang, H.; Wang, C. A robust image watermarking technique based on DWT, APDCBT, and SVD. Symmetry 2018, 10, 77. [Google Scholar] [CrossRef]




| Infection Target | Encoder | Decoder | Output | Detection Watermark | ||
|---|---|---|---|---|---|---|
| Codec | Watermark | Codec | Watermark | |||
| Host video | SVC | Pathogen PW | SVC | Mutant MW1 | PW/MW1 video | PW |
| Output 1 | MPEG2 (qscale = 8) | Contagion CW1 | MPEG2 (qscale = 8) | Mutant MW2 | PW/MW1,2/CW1 video | PW/MW1/CW1 |
| Output 2 | H.264 (crf = 23) | Contagion CW2 | H.264 (crf = 23) | Mutant MW3 | PW/MW1,2,3/CW1,2 video | PW/MW1,2/CW1,2 |
| Infection Target | Encoder | Decoder | Output | Detection Watermark | ||
|---|---|---|---|---|---|---|
| Codec | Watermark | Codec | Watermark | |||
| Host video | SVC | Pathogen PW | SVC | Mutant MW1 | PW/MW1 video | PW |
| Output 1 | H.264 (crf = 23) | Contagion CW1 | H.264 (crf = 23) | Mutant MW2 | PW/MW1,2/CW1 video | PW/MW1/CW1 |
| Output 2 | HEVC (crf = 28) | Contagion CW2 | HEVC (crf = 28) | Mutant MW3 | PW/MW1,2,3/CW1,2 video | PW/MW1,2/CW1,2 |
| Test Sequences | Resolution@FPS | Host | 1st Infection | 2nd Infection | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| H.264 SVC | MPEG-2 (qscale 4) | H.264 (crf 23) | ||||||||
| PW(C-EM/DM) BER | CW1(K-EM/DM) BER/PW/MW1(C-EM/DM) BER | CW1,2(K-EM/DM) BER/PW/MW1,2(C-EM/DM) BER | ||||||||
| Propose | Previous [20] | Yang [21] | Propose | Previous [20] | Abdi [19]/Yang [20] | Propose | Previous | Abdi [19]/Yang [20] | ||
| Football | CIF@30fps | 0 | 0 | 0.02 | 0/0 | 0/0 | 0.01/0.04 | 0.01/0.02 | 0.02/0.03 | 0.03/0.10 |
| Foreman | CIF@30fps | 0 | 0 | 0.01 | 0/0 | 0/0 | 0.00/0.02 | 0.00/0.02 | 0.01/0.02 | 0.02/0.07 |
| Bus | CIF@30fps | 0 | 0 | 0.00 | 0/0 | 0/0 | 0.00/0.01 | 0.01/0.01 | 0.01/0.01 | 0.02/0.05 |
| Crew | 4CIF@30fps | 0 | 0 | 0.01 | 0/0 | 0/0 | 0.00/0.02 | 0.00/0.01 | 0.01/0.02 | 0.03/0.08 |
| Movie | 544p@24fps | 0 | 0 | 0.02 | 0/0 | 0/0 | 0.01/0.03 | 0.01/0.02 | 0.01/0.03 | 0.04/0.10 |
| Average BER | 0 | 0 | 0.012 | 0/0 | 0/0 | 0.004/0.024 | 0.006/0.016 | 0.012/0.022 | 0.028/0.080 | |
| Test Sequences | Resolution@23.967FPS | Host | 1st Infection | 2nd Infection | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| H.264 SVC | H.264 (crf 23) | HEVC (crf 28) | ||||||||
| PW(C-EM/DM) BER | CW1(K-EM/DM) BER/PW/MW1(C-EM/DM) BER | CW1,2(K-EM/DM) BER/PW/MW1,2(C-EM/DM) BER | ||||||||
| Propose | Previous [20] | Yang [21] | Propose | Previous | Abdi [19]/Yang [20] | Propose | Previous | Abdi [19]/Yang [20] | ||
| Simpsons | 1080p | 0 | 0 | 0.03 | 0/0 | 0/0 | 0.01/0.05 | 0.02/0.03 | 0.03/0.05 | 0.04/0.08 |
| IamLegend | 1080p | 0 | 0 | 0.04 | 0/0 | 0/0 | 0.02/0.06 | 0.02/0.04 | 0.02/0.06 | 0.05/0.11 |
| Serenity | 720p | 0 | 0 | 0.02 | 0/0 | 0/0 | 0.01/0.04 | 0.01/0.02 | 0.02/0.04 | 0.03/0.06 |
| Fantastic4 | 720p | 0 | 0 | 0.03 | 0/0 | 0/0 | 0.02/0.06 | 0.02/0.03 | 0.02/0.04 | 0.03/0.08 |
| Average BER | 0 | 0 | 0.03 | 0 | 0/0 | 0.015/0.053 | 0.018/0.030 | 0.023/0.048 | 0.038/0.083 | |
| Test Sequences | Resolution@FPS | Host | 1st Infection | 2nd Infection | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| H.264 SVC | MPEG-2 (qscale 4) | H.264 (crf 23) | ||||||||
| PW(C-EM/DM) PSNR | CW1(K-EM/DM) PSNR/PW/MW1(C-EM/DM) PSNR | CW1,2(K-EM/DM) PSNR/PW/MW1,2(C-EM/DM) PSNR | ||||||||
| Propose | Previous [20] | Yang [21] | Propose | Previous [20] | Abdi [19]/Yang [20] | Propose | Previous [20] | Abdi [19]/Yang [20] | ||
| Football | CIF@30fps | 41.39 | 41.14 | 40.73 | 36.92 | 36.46 | 36.78/35.45 | 35.66 | 36.77 | 34.27/33.63 |
| Foreman | CIF@30fps | 42.21 | 41.95 | 41.53 | 37.36 | 36.48 | 36.81/35.78 | 35.95 | 36.30 | 34.76/34.17 |
| Bus | CIF@30fps | 40.45 | 40.08 | 39.68 | 36.93 | 36.29 | 36.47/35.76 | 36.13 | 35.82 | 35.20/33.96 |
| Crew | 4CIF@30fps | 40.09 | 39.41 | 39.06 | 35.65 | 35.26 | 35.56/34.64 | 35.4 | 35.07 | 34.34/33.46 |
| Movie | 544p@24fps | 40.89 | 40.28 | 39.88 | 37.21 | 36.34 | 36.75/35.83 | 35.86 | 36.03 | 34.82/34.01 |
| Average PSNR | 40.99 | 40.57 | 40.18 | 36.81 | 36.17 | 36.47/35.49 | 35.80 | 35.19 | 34.68/33.85 | |
| Test Sequences | Resolution@23.967fps | Host | 1st Infection | 2nd Infection | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| H.264 SVC | H.264 (crf 23) | HEVC (crf 28) | ||||||||
| PW(C-EM/DM) PSNR | CW1(K-EM/DM)/PW/MW1(C-EM/DM) PSNR | CW1,2(K-EM/DM)/PW/MW1,2(C-EM/DM) PSNR | ||||||||
| Propose | Previous [20] | Yang [21] | Propose | Previous [20] | Abdi [19]/Yang [20] | Propose | Previous [20] | Abdi [19]/Yang [20] | ||
| Simpsons | 1080p | 40.88 | 40.44 | 39.72 | 39.25 | 38.85 | 39.15/38.06 | 38.26 | 37.39 | 36.98/36.22 |
| IamLegend | 1080p | 40.43 | 40.37 | 39.35 | 38.85 | 38.42 | 38.71/37.74 | 37.83 | 36.98 | 36.58/36.18 |
| Serenity | 720p | 41.56 | 41.07 | 40.64 | 40.21 | 39.50 | 39.78/38.69 | 38.89 | 37.92 | 37.57/37.21 |
| Fantastic4 | 720p | 41.78 | 41.62 | 40.95 | 40.42 | 39.70 | 40.04/38.97 | 39.09 | 38.23 | 38.02/37.14 |
| Average PSNR | 41.16 | 40.88 | 40.17 | 39.68 | 39.12 | 39.42/38.37 | 38.52 | 37.63 | 37.29/36.69 | |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jang, B.-J.; Lee, S.-H.; Lee, Y.-S.; Kwon, K.-R. Biological Viral Infection Watermarking Architecture of MPEG/H.264/AVC/HEVC. Electronics 2019, 8, 889. https://doi.org/10.3390/electronics8080889
Jang B-J, Lee S-H, Lee Y-S, Kwon K-R. Biological Viral Infection Watermarking Architecture of MPEG/H.264/AVC/HEVC. Electronics. 2019; 8(8):889. https://doi.org/10.3390/electronics8080889
Chicago/Turabian StyleJang, Bong-Joo, Suk-Hwan Lee, Young-Suk Lee, and Ki-Ryong Kwon. 2019. "Biological Viral Infection Watermarking Architecture of MPEG/H.264/AVC/HEVC" Electronics 8, no. 8: 889. https://doi.org/10.3390/electronics8080889
APA StyleJang, B.-J., Lee, S.-H., Lee, Y.-S., & Kwon, K.-R. (2019). Biological Viral Infection Watermarking Architecture of MPEG/H.264/AVC/HEVC. Electronics, 8(8), 889. https://doi.org/10.3390/electronics8080889





