Enhancing PUF Based Challenge–Response Sets by Exploiting Various Background Noise Configurations
Abstract
:1. Introduction
- A new quantization method allows us to increase the size of CRPs by exploiting multiple bits of a RO-PUF response.
- A new RO pair-selection mechanism based on the reliability of the PUF responses involves different levels of background noise.
- The evaluation of a physical implementation of the quantization method and different background configurations using 25 Xilinx Spartan 3E FPGA boards is presented.
- A validation of the methodology using some of the most extended PUF quality metrics (uniformity, bit-aliasing, reliability and uniqueness) for different operating conditions (i.e., core voltage variations) is presented.
2. Background
2.1. Basics of Ring Oscillator-Based PUFs and CRPs
2.2. Impact of Switching Activity on RO-PUFs
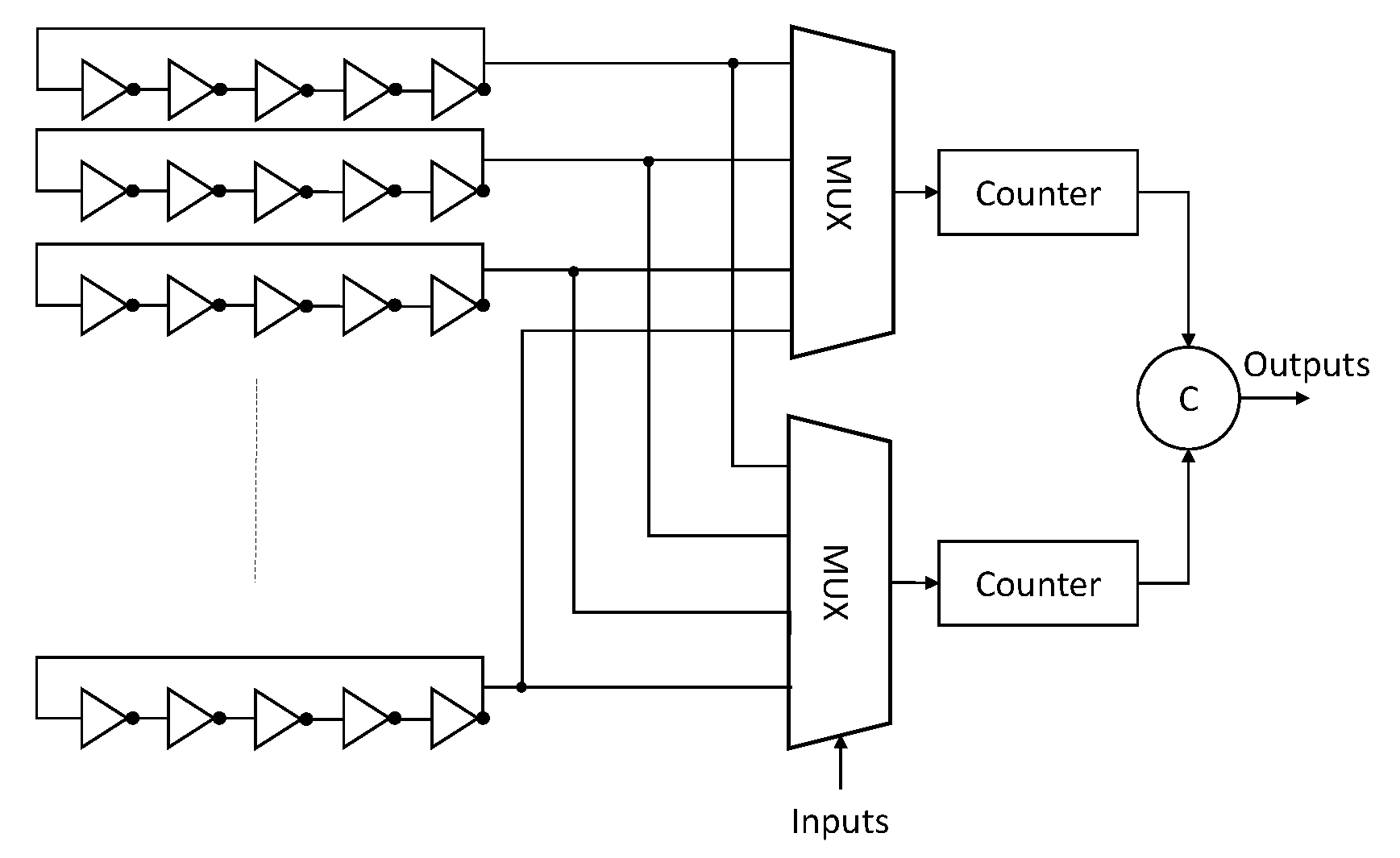
3. Proposed Method
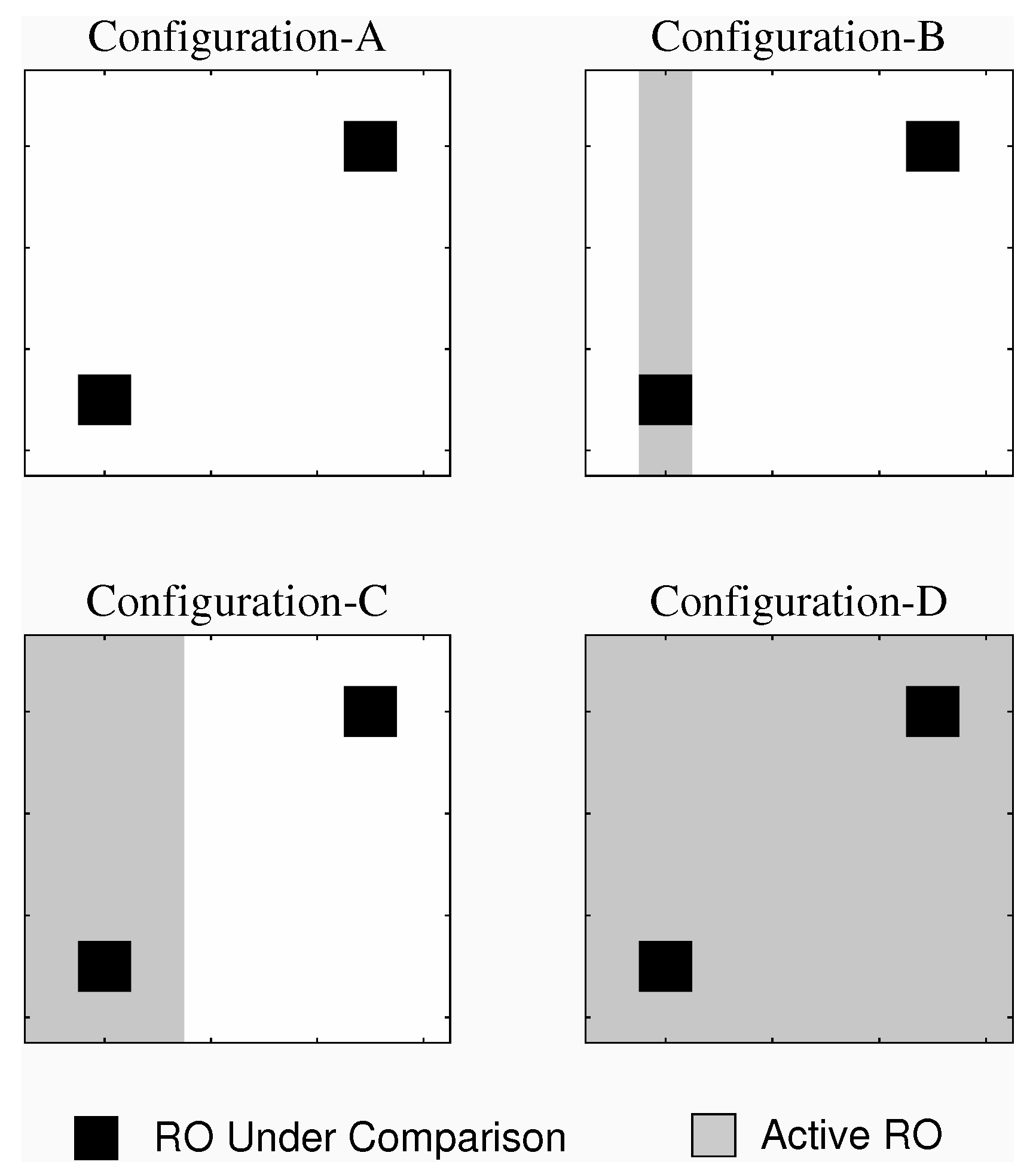
3.1. Background Noise Configuration
- The user introduces a challenge that contains the two ROs under comparison while selecting one of the four background configuration randomly or based on user preference. The frequency of only one of the ROs under comparison is acquired.
- In this step, the the RO frequency of the second RO under comparison is acquired. However, during this step, a different background configuration can be used.
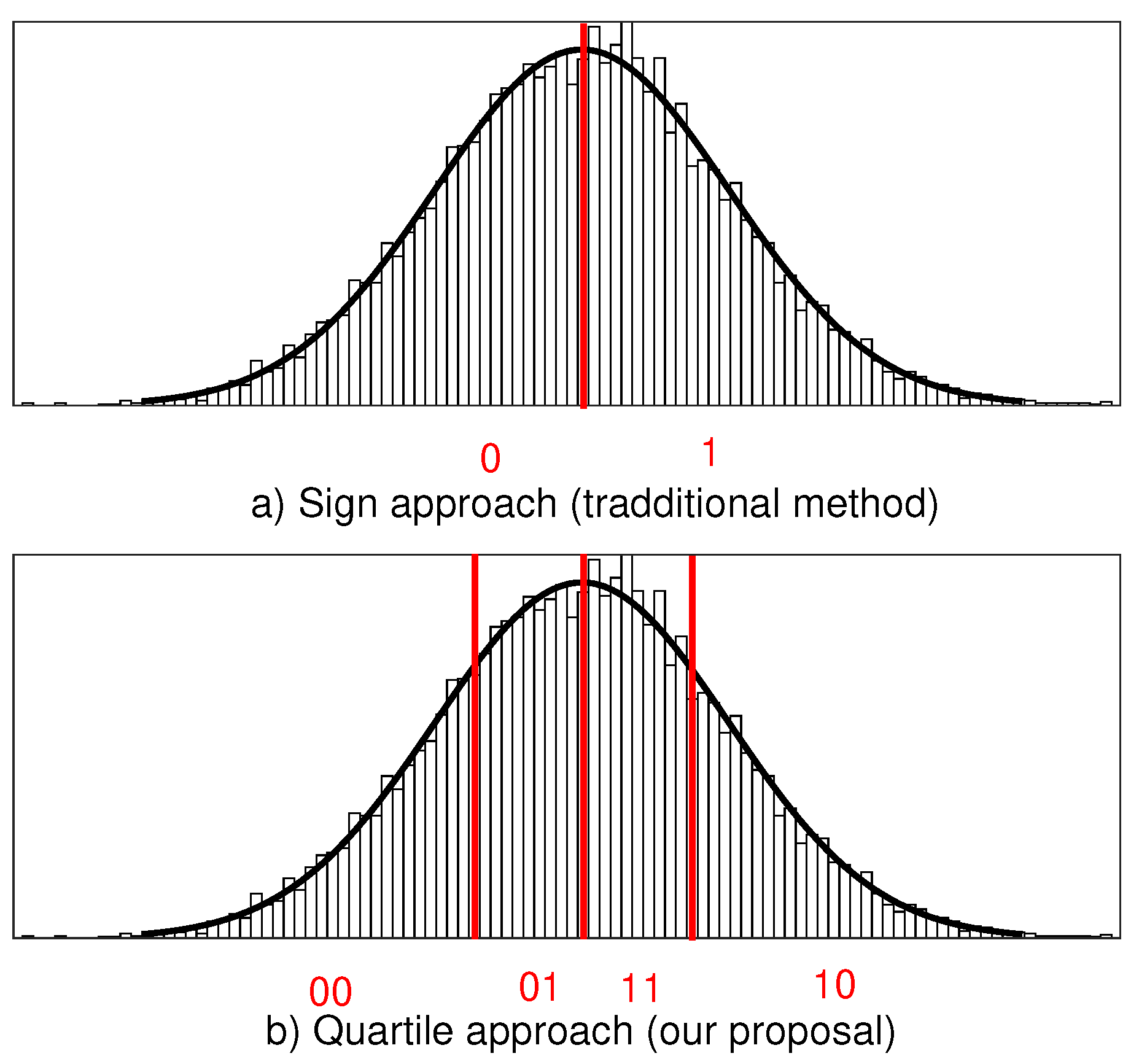
3.2. CRP Expansion
3.3. CRP Reliability Enhancement
4. Experimental Results
4.1. Set-Up
4.2. Performance Evaluation of the PUF Responses
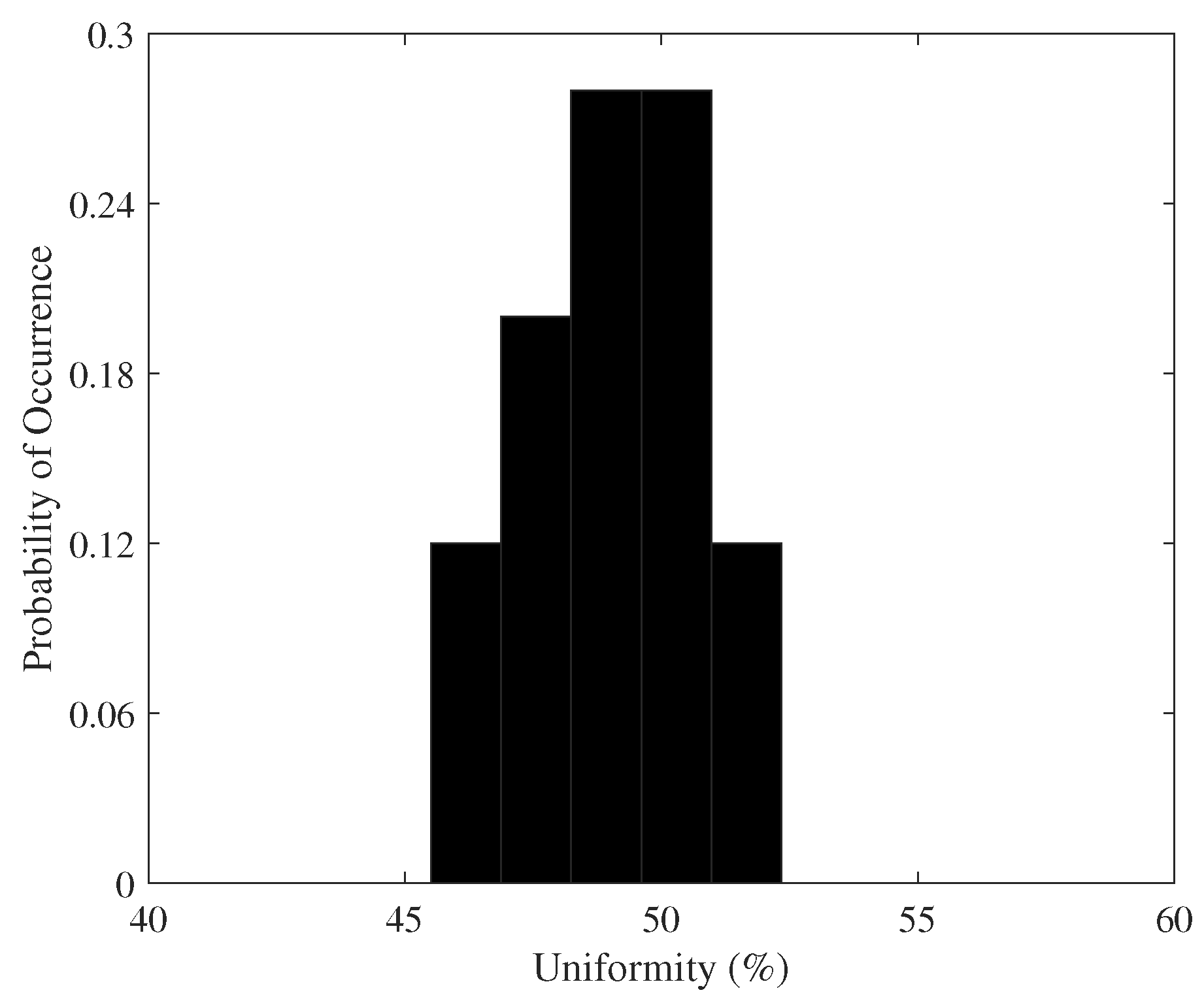
4.2.1. Uniformity
4.2.2. Bit-Aliasing
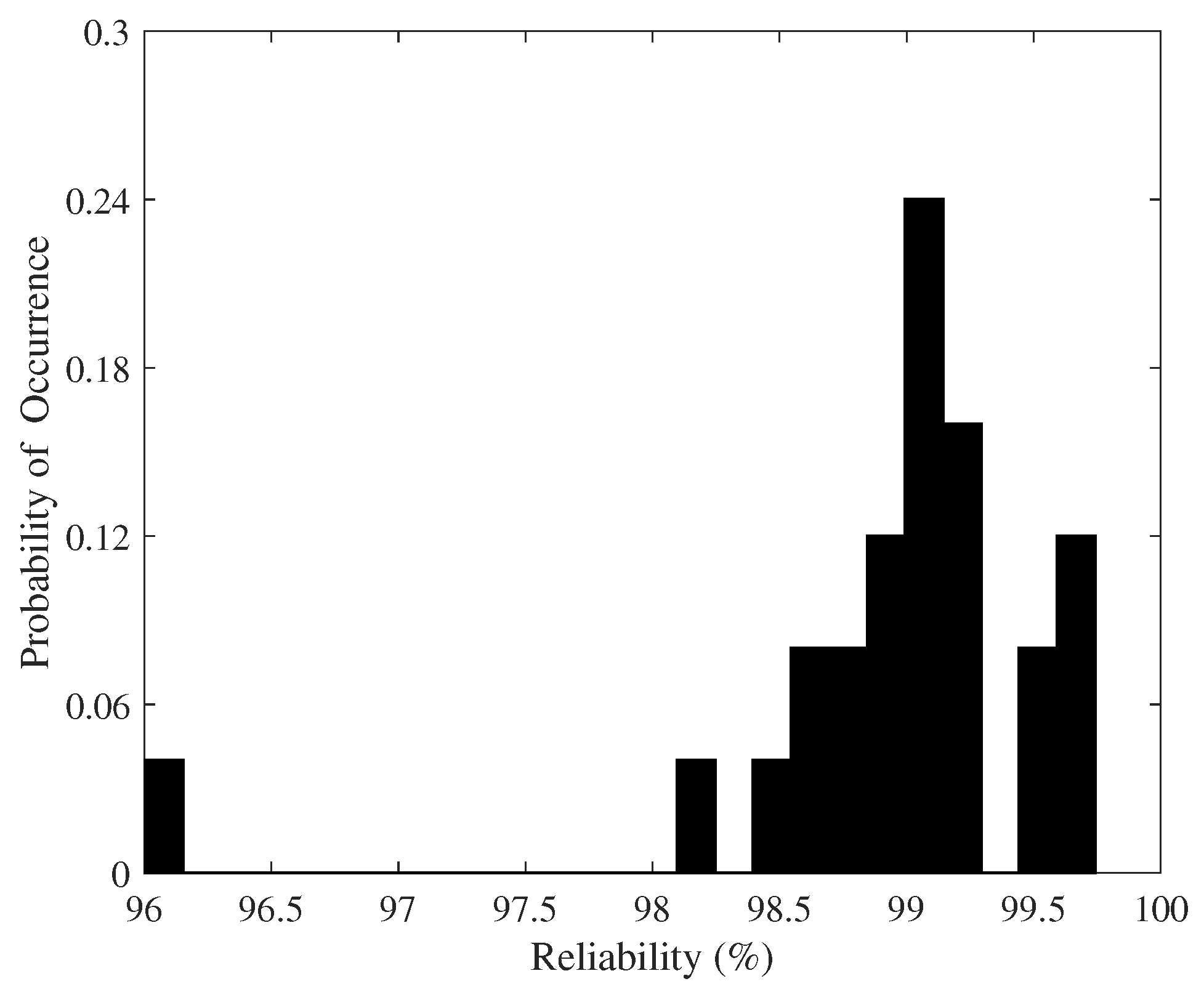
4.2.3. Reliability
4.2.4. Uniqueness
4.2.5. Entropy
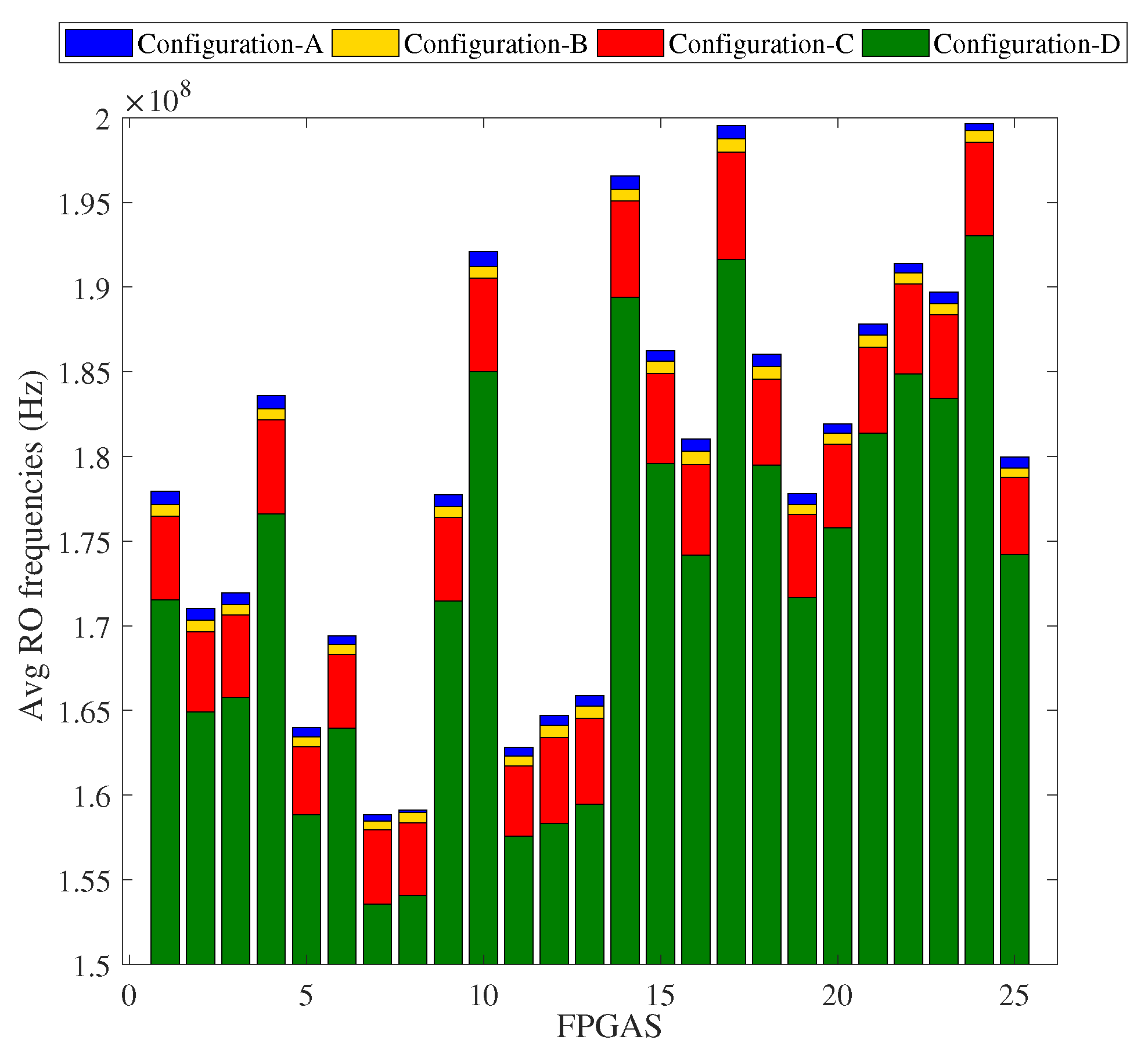
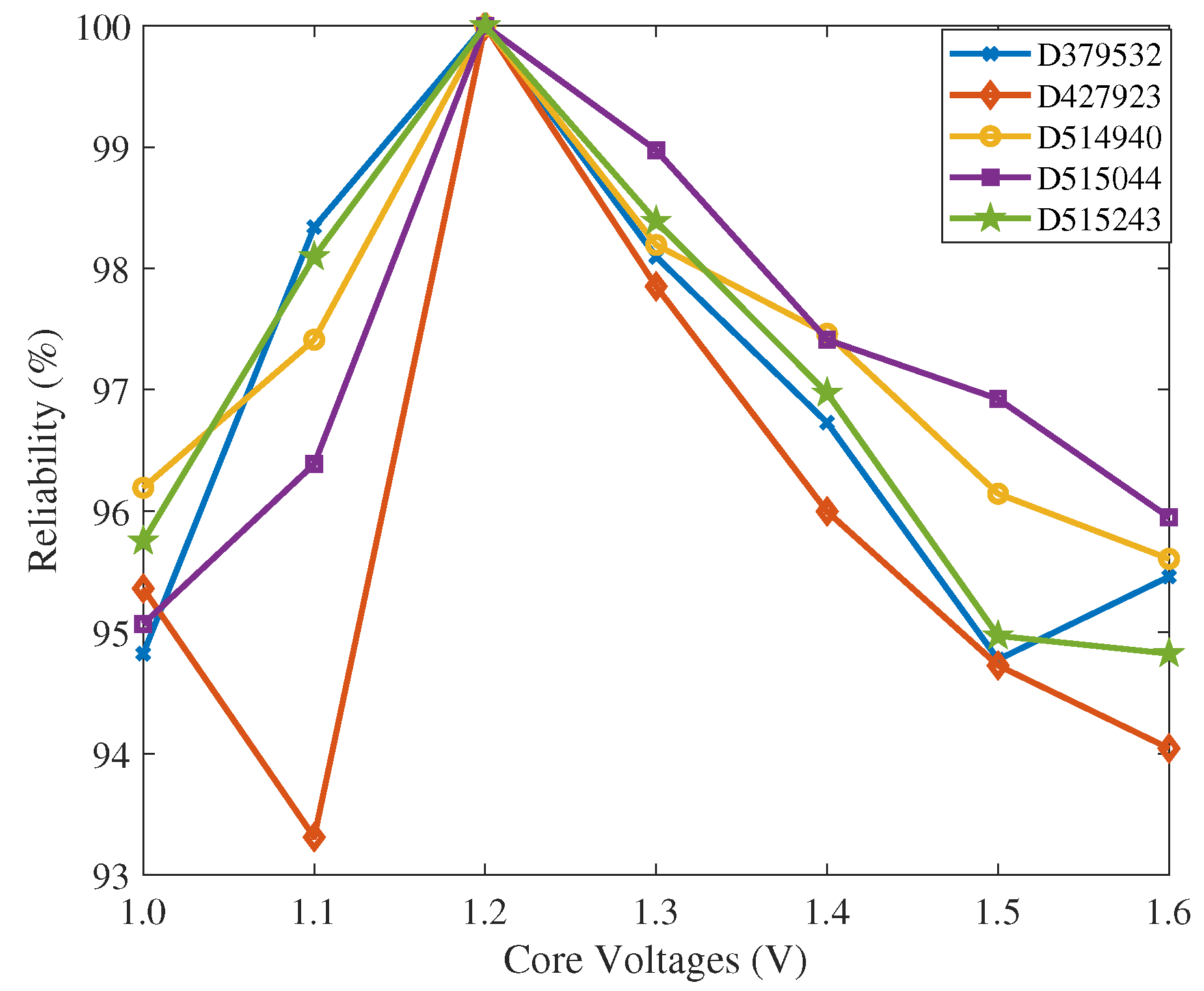
4.3. Impact of Environmental Variations
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Gassend, B.; Clarke, D.; van Dijk, M.; Devadas, S. Silicon Physical Random Functions. In Proceedings of the 9th ACM Conference on Computer and Communications Security (CCS’02), Washington, DC, USA, 18–22 November 2002; ACM: New York, NY, USA, 2002; pp. 148–160. [Google Scholar] [CrossRef]
- Rampon, J.; Perillat, R.; Torres, L.; Benoit, P.; Natale, G.D.; Barbareschi, M. Digital Right Management for IP Protection. In Proceedings of the 2015 IEEE Computer Society Annual Symposium on VLSI, Montpellier, France, 8–10 July 2015; pp. 200–203. [Google Scholar] [CrossRef]
- Zhang, J.; Qu, G. A survey on security and trust of FPGA-based systems. In Proceedings of the 2014 International Conference on Field-Programmable Technology (FPT), Shanghai, China, 10–12 December 2014; pp. 147–152. [Google Scholar] [CrossRef]
- Karri, R.; Sinanoglu, O.; Rajendran, J. Physical Unclonable Functions and Intellectual Property Protection Techniques. In Fundamentals of IP and SoC Security: Design, Verification, and Debug; Bhunia, S., Ray, S., Sur-Kolay, S., Eds.; Springer International Publishing: Cham, Swtzerland, 2017; pp. 199–222. [Google Scholar] [CrossRef]
- Maiti, A.; Schaumont, P. Improved Ring Oscillator PUF: An FPGA-friendly Secure Primitive. J. Cryptol. 2011, 24, 375–397. [Google Scholar] [CrossRef]
- Maiti, A.; Kim, I.; Schaumont, P. A Robust Physical Unclonable Function With Enhanced Challenge-Response Set. IEEE Trans. Inf. Forensics Secur. 2012, 7, 333–345. [Google Scholar] [CrossRef]
- Kömürcü, G.; Pusane, A.E.; Dündar, G. Enhanced challenge-response set and secure usage scenarios for ordering-based ring oscillator-physical unclonable functions. IET Circuits Devices Syst. 2015, 9, 87–95. [Google Scholar] [CrossRef]
- Bossuet, L.; Ngo, X.T.; Cherif, Z.; Fischer, V. A PUF Based on a Transient Effect Ring Oscillator and Insensitive to Locking Phenomenon. IEEE Trans. Emerg. Top. Comput. 2014, 2, 30–36. [Google Scholar] [CrossRef]
- Yu, L.; Wang, X.; Rahman, F.; Tehranipoor, M. iPUF: Interconnect PUF with Self-Masking Circuit for Performance Enhancement. In Proceedings of the 2017 18th International Workshop on Microprocessor and SOC Test and Verification (MTV), Austin, TX, USA, 11–12 December 2017; pp. 45–50. [Google Scholar] [CrossRef]
- Gao, M.; Lai, K.; Qu, G. A highly flexible ring oscillator PUF. In Proceedings of the 2014 51st ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 1–5 June 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Delavar, M.; Mirzakuchaki, S.; Mohajeri, J. A Ring Oscillator-Based PUF With Enhanced Challenge-Response Pairs. Can. J. Electr. Comput. Eng. 2016, 39, 174–180. [Google Scholar] [CrossRef]
- Suh, G.E.; Devadas, S. Physical Unclonable Functions for Device Authentication and Secret Key Generation. In Proceedings of the 2007 44th ACM/IEEE Design Automation Conference, San Diego, CA, USA, 4–8 June 2007; pp. 9–14. [Google Scholar]
- Merli, D.; Stumpf, F.; Eckert, C. Improving the Quality of Ring Oscillator PUFs on FPGAs. In Proceedings of the 5th Workshop on Embedded Systems Security (WESS’10), Scottsdale, AZ, USA, 24 October 2010; ACM: New York, NY, USA, 2010; pp. 9:1–9:9. [Google Scholar] [CrossRef]
- Liu, W.; Yu, Y.; Wang, C.; Cui, Y.; O’Neill, M. RO PUF design in FPGAs with new comparison strategies. In Proceedings of the 2015 IEEE International Symposium on Circuits and Systems (ISCAS), Lisbon, Portugal, 24–27 May 2015; pp. 77–80. [Google Scholar] [CrossRef]
- Barbareschi, M.; Natale, G.D.; Bruguier, F.; Benoit, P.; Torres, L. Ring oscillators analysis for security purposes in Spartan-6 FPGAs. Microprocess. Microsyst. 2016, 47, 3–10. [Google Scholar] [CrossRef]
- Xilinx. ChipScope Pro Software and Cores, User Guide; Xilinx Inc.: San Jose, CA, USA, 2012. [Google Scholar]
- Maiti, A.; Casarona, J.; McHale, L.; Schaumont, P. A large scale characterization of RO-PUF. In Proceedings of the 2010 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Anaheim, CA, USA, 13–14 June 2010; pp. 94–99. [Google Scholar] [CrossRef]
- Turan, M.S.; Barker, E.; Kelsey, J.; McKay, K.A.; Baish, M.L.; Boyle, M. NIST Special Publication 800-90B: Recommendation for the Entropy Sources Used for Random Bit Generation; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018.
- Wilde, F.; Gammel, B.M.; Pehl, M. Spatial Correlation Analysis on Physical Unclonable Functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1468–1480. [Google Scholar] [CrossRef]
- Maiti, A.; Gunreddy, V.; Schaumont, P. A Systematic Method to Evaluate and Compare the Performance of Physical Unclonable Functions. Available online: https://eprint.iacr.org/2011/657 (accessed on 29 January 2019).
- Hagerty, P.; Draper, T.H.J. Entropy Bounds and Statistical Tests. In Proceedings of the NIST Random Bit Generation Workshop, Gaithersburg, MD, USA, 5–6 December 2012; pp. 1319–1327. [Google Scholar]
- Herder, C.; Ren, L.; van Dijk, M.; Yu, M.; Devadas, S. Trapdoor computational fuzzy extractors and stateless cryptographically-secure physical unclonable functions. IEEE Trans. Dependable Secur. Comput. 2017, 14, 65–82. [Google Scholar] [CrossRef]
- Jin, C.; Herder, C.; Ren, L.; Nguyen, P.H.; Fuller, B.; Devadas, S.; van Dijk, M. FPGA Implementation of a Cryptographically-Secure PUF Based on Learning Parity with Noise. Cryptography 2017, 1, 23. [Google Scholar] [CrossRef]
- Ulrich, R.; Frank, S.; Jan, S.; Gideon, D.; Srinivas, D.; Jürgen, S. Modeling Attacks on Physical Unclonable Functions. In Proceedings of the 17th ACM Conference on Computer and Communications Security (CCS’10), Chicago, IL, USA, 4–8 October 2010; ACM: New York, NY, USA, 2010; pp. 237–249. [Google Scholar] [CrossRef]
- Burmester, M.; Munilla, J. Lightweight RFID Authentication with Forward and Backward Security. ACM Trans. Inf. Syst. Secur. 2011, 14, 11:1–11:26. [Google Scholar] [CrossRef]



| Most Common Value | Collision | Markov | Compression | t-Tuple | LRS | MultiMCW | Lag | MultiMMC | LZ78Y | Min-Entropy |
|---|---|---|---|---|---|---|---|---|---|---|
| 0.976847 | 0.794207 | 0.977158 | 0.907573 | 0.925103 | 0.940845 | 0.956122 | 0.945201 | 0.985189 | 0.971355 | 0.794207 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Martin, H.; Peris-Lopez, P.; Natale, G.D.; Taouil, M.; Hamdioui, S. Enhancing PUF Based Challenge–Response Sets by Exploiting Various Background Noise Configurations. Electronics 2019, 8, 145. https://doi.org/10.3390/electronics8020145
Martin H, Peris-Lopez P, Natale GD, Taouil M, Hamdioui S. Enhancing PUF Based Challenge–Response Sets by Exploiting Various Background Noise Configurations. Electronics. 2019; 8(2):145. https://doi.org/10.3390/electronics8020145
Chicago/Turabian StyleMartin, Honorio, Pedro Peris-Lopez, Giorgio Di Natale, Mottaqiallah Taouil, and Said Hamdioui. 2019. "Enhancing PUF Based Challenge–Response Sets by Exploiting Various Background Noise Configurations" Electronics 8, no. 2: 145. https://doi.org/10.3390/electronics8020145
APA StyleMartin, H., Peris-Lopez, P., Natale, G. D., Taouil, M., & Hamdioui, S. (2019). Enhancing PUF Based Challenge–Response Sets by Exploiting Various Background Noise Configurations. Electronics, 8(2), 145. https://doi.org/10.3390/electronics8020145





