1. Introduction
Cognitive radio (CR) is an intelligent technology to improve the spectrum utilization in mobile ad-hoc networks (MANETs) by allowing cognitive users flexibly use the spectrum allocated to licensed primary users. In this approach, each cognitive user can sense status of channels and immediately switch to vacant channels to avoid interfering with primary users or other users [
1,
2]. Hence, CR has been considered as a promising technology to improve the spectrum utilization in CR-MANETs. There are three main cognitive radio network paradigms: underlay, overlay and interweave. In underlay systems, cognitive (secondary) user knows the channel strengths to primary users and can transmit simultaneously with primary user as long as interference caused is below an acceptable limit. Moreover, the transmit power of cognitive user is limited by the interference constraint. In overlay systems, cognitive users know channel gains, codebooks and the message of the primary users. Each cognitive user can transmit simultaneously with primary user. The interference to primary user can be offset by using part of the power of cognitive user to relay the primary user’s message. Moreover, cognitive user can transmit at any power, the interference to primary user can be offset by relaying the primary user’s message. In interweave systems, cognitive user knows the spectral holes in space, time, or frequency when primary user is not using these holes. Each cognitive user can transmit simultaneously with a primary user only in the event of false spectral hole detection. Moreover, the transmit power of cognitive user is limited by the range of its spectral hole sensing. In our paper, we considered the system model as a overlay system.
There are many challenges for clustering and routing in MANET such as no fixed infrastructure, decentralized management, dynamic topology, limited bandwidth, limited resources, limited physical security, poor transmission quality, dynamic connection and disconnection of the links and updating information of dynamic links among nodes. In this paper, we focus on clustering and routing issues in network layer. However, there exist important issues of lower layers which can be occured at network layer such as throughput, energy efficiency, traffic optimization, packet loss, security, delay, QoS, admission control, mobility, routing and data gathering. These issues significantly impact to the routing process in network layer. However, we mainly focus on establishing the best route in network layer to improve packet delivery ratio (PDR), control overheads, delay and energy consumption. Thus, we assume that these above issues were fully supported by lower layers, that is, physical and data link layers.
Since MANET is a mobile environment which does not depend on any fixed infrastructure or centralized management, clustering approach is an efficient approach to design virtual infrastructures and make routing process stable [
3]. In this paper, we focus on clustering and routing problems with multi-channel to improve network performance in CR-MANETs. In routing process, routes established at the network layer will affect significantly the licensed channel of primary users, arising a challenging problem in guaranteeing quality of service in MANETs. CR technology is adopted for routing process by enabling channel selection and transmission direction to solve such a problem. However, the impacts of clustering and routing problems with channel selection and transmission direction on multi-channel cognitive MANETs, which cover a lot of attractive research problems, have received less attention in the literature.
In this section, we discuss the recent works on clustering and routing algorithms in MANETs. In Reference [
4], the authors presented that typical clustering schemes of MANETs were classified into six categories such as dominating-set-based (DS-based) clustering, low-maintenance clustering, mobility-aware clustering, energy-efficient clustering, load-balancing clustering and combined-metrics-based clustering. Particularly, the idea of DS-based clustering is to find a connected set of dominating nodes (CDS) with a minimum size. The obtained CDS is used as a routing space for routing process. In low-maintenance clustering approach, the main goal of clustering is to provide a stable cluster architecture by minimizing re-clustering situations. This issue helps to save the cost of clustering process. The main task of mobility-aware clustering is also to construct a stable cluster structure. The main idea of this clustering approach is that mobile nodes are classified into groups based on the movement of node. In energy-efficient clustering scheme, a MANET should try to save its energy consumption in order to prolong the network lifespan. Because a cluster head has to handle more tasks than a member, its energy is easily exhausted and network communication may be interrupted. There are some approaches to solve this problem such as limiting the time that a mobile node can serve as a cluster head continuously, guaranteeing the CDS connected and removing unnecessary mobile nodes with low energy level from the CDS and serving slave nodes as many as possible and minimizing the total energy consumption between all communicating master-slave pairs, where a master is a cluster head and a slave is a member. Load-balancing clustering algorithms provides an optimum number of clusters to improve the system performances. The number of mobile nodes in each cluster is set by an upper and a lower limit. When a cluster size exceeds its limit, the number of mobile nodes is adjusted by re-clustering. The main idea of combined-metrics-based clustering is to produce a weighted function which is a combination of parameters such as node degree, residual energy capacity, moving speed. This weighted function is used for the cluster heads selection process to obtain a cluster structure, which improves the system performances. In Reference [
5], the authors proposed a probabilistic clustering algorithm. In this algorithm, a node with more vacant channels has a higher probability to become a cluster head. Next, each CH broadcasts their list of vacant channels. If a node has one or more common channels with a CH, it sends a join request message including its vacant channels’ list and ID to the cluster head. Finally, each cluster head decides a final communication channel based on the received channel lists from non-cluster head nodes. In Reference [
6], a weighted function was proposed by combining the degree of connectivity, mobility, time of a cluster head (CH) and sum of distances to neighbors to elect cluster heads in MANETs. A distributed weighted clustering algorithm (DWCA) was presented in Reference [
7] to optimize the configuration and power for the cluster heads in MANETs. In Reference [
8], a weighted clustering algorithm was studied, called enhancement on weighted clustering algorithm (EWCA). In EWCA, transmission power, transmission range, mobility and battery energy parameters were used to elect CHs and achieve the load balancing to enhance the stability of clusters in MANETs. A mobility based clustering approach was proposed in Reference [
9] to support mobility management and multicast routing in MANETs. Topology control is a challenging problem because there is no fixed infrastructure in MANETs, the connected dominating set (CDS) has been considered as an effective approach to design clusters and virtual backbones in MANETs [
10]. In Reference [
11], a CDS based distributed algorithm was proposed based on node IDs to reduce the size of CDS. A reduction-based methods were presented in References [
12,
13] to find a CDS from one node with maximum vertex degree and some rules were also introduced to reduce the size of CDS. To construct a CDS for routing protocol, an algorithm with rules based on energy level and degree of nodes was proposed in Reference [
14]. The authors of Reference [
15] proposed an energy efficient and salable routing algorithm based on length of route and remaining energy for extreme emergency ad hoc communications. In Reference [
16], the authors proposed an efficient flooding and repairing local route algorithm based on a stable connected dominating set in MANETs. In this algorithm, if a node has minimum velocity and maximum signal strength, it is selected as a dominator.
Besides, several studies on the routing issue were presented as follows. In Reference [
17], the authors proposed a distributed interference-aware relay selection (DIRS) algorithm for IEEE 802.11-based wireless networks with multiple source–destination pairs. Each source–destination pair selects best relay by using inter-node interference and channel statistics without the knowledge of topology information. In DIRS algorithm, inter-node interference can be minimized by optimising relay selection. In Reference [
18], the authors proposed a new multi-channel MAC protocol to solve the channel assignment and medium access problems in an integrated manner. In this protocol, each mobile host was assigned a common channel for control purpose and it switched to remaining channels for data exchange. In Reference [
19], the authors proposed an optimization methodology to analytically calculate the end-to-end throughput capacity of IEEE 802.11-based multi-hop wireless networks. The proposed methodology provided a very accurate calculation of the end-to-end throughput capacity by considering the node interference, the impact of hidden node collision and multi-rate terminals. In Reference [
20], this article addressed a number of problems when implementing two routing protocols on actual wireless networks. There was no protocol which provided a stable multi-hop route. Based on the authors’ experiences, several outlines are recommended for future work in MANET researches. Most of routing protocols in cognitive mobile ad hoc networks have recently considered in dynamic spectrum allocation and path establishment by observing primary user activity regions in Reference [
21]. Layered graphs were utilized to model multi-channel networks [
22] and colored graphs were deployed for model spectrum sharing and allocation problems [
23]. In Reference [
24], a cognitive ad hoc on-demand distance vector (CAODV) protocol was proposed based on the ad hoc on-demand distance vector (AODV) protocol. Both route formation and packet discovery of the CAODV avoids the affected region of primary user. Moreover, the CAODV applies joint path and channel selection at each forwarder to minimize the route cost. This protocol broadcasts the route request packet to neighbors on all the channels that leads to increase control overheads and reduce network life time. In Reference [
25], the authors proposed a distributed prediction-based cognitive topology control (PCTC) scheme which is a middle-ware approach (between the cognitive radio module and routing). The PCTC uses cognitive link availability prediction to aware the affected region of primary users and to predict the available duration of links in CR-MANETs. The PCTC constructs efficient and reliable topology in order to reduce re-routing and improve end-to-end network performance. In Reference [
26], the authors proposed a SEARCH routing protocol for CR-MANETs to find a route subject to minimum end-to-end delay from the source to the destination without affecting primary user activities. Aiming at improving network throughput and mitigating interference to primary users, various routing problems are formulated based on graph theory [
27,
28,
29]. In particular, the authors of Reference [
27] introduced a mixed integer non-linear programming to minimize spectrum usage and aggregate interference from cognitive users to a primary user. In Reference [
28], a routing and dynamic spectrum allocation (ROSA) algorithm was proposed subject to spectrum allocation, scheduling and transmission power control scheme to maximize network throughput and limit physical interference to other users. Based on interference model, the authors of Reference [
29] proposed joint routing, opportunistic spectrum scheduling and time sharing scheduling algorithms to minimize aggregate interference from cognitive users to a primary user. Besides, spectrum availability may change from time to time and hop by hop which is unpredictable. In Reference [
30], the authors presented several types of prediction algorithms to forecast the node’s locations. These prediction algorithms with Markov analysis, text compression, user’s movement history and Bayesian and neural networks, significantly improved the system performance in mobile wireless systems. For improving routing reliability and scalability, the authors of Reference [
31] used some prediction techniques to efficiently predict time of next movement and the next location of mobile nodes in MANETs. The authors of Reference [
32] proposed an energy reduction multipath routing protocol by using a recoil technique (AOMDV-ER) in MANETs to improve the system performances. In AOMDV-ER, the mobile nodes used a varying recoil off time technique to establish the route to their destination based on the geographical location. In Reference [
33], the authors proposed a topology change aware-based routing protocol choosing scheme (TARCS) for flying ad hoc networks to improve the system performances. In TARCS, mobile nodes can sense changes of the surrounding network topology periodically to provide a suitable routing protocol. In Reference [
34], the authors proposed a node-disjoint multipath routing (NDMR) protocol to establish two node-disjoint paths between a source and a destination in a wireless network in order to solve the unstable state of wireless links, and unpredictable environmental interference. The proposed approach uses the request-reply mechanism to find the node-disjoint paths. In Reference [
35], the authors presented a key exchange technique based on the fluctuating topology characteristic of MANETs. The ever changing topology of the network almost completely removes an active attacker’s success ratio by using splitting key exchange information technique.
However, the aforementioned works just focused on clustering or routing separately in conventional MANETs. Since the cost of established routes is greatly expensive, clustering is considered as an effective approach in simplifying routing process and reducing such a cost, that is, the size of routing space is reduced and energy balancing is achieved. In multi-channel cognitive radio environments, cognitive users have to be aware of channel status to establish a route from a source to a destination. Particularly, cognitive users first detect dynamically vacant channels to make a decision of either switching channel or using different regions to avoid the licensed spectrum in the transmission range of primary users [
26,
28]. To provide comprehensibly the advantages of the proposed CRD protocol compared to the state-of-the art protocol, we summarize the main features in
Table 1, where notation “-” is denoted as “not mentioned.”
This paper proposes an efficient connected dominating set clustering based routing protocol with dynamic channel selection (CRD) in multi-channel cognitive mobile ad hoc networks (MCR-MANETs) to obtain high packet delivery ratio (PDR), low control overheads, low delay and low energy consumption when mobile nodes are moving in high speed. Moreover, CRD protocol can apply for Vehicular Ad Hoc Network (VANET), IoT and 5G. The main contributions of the paper can be summarized as follows:
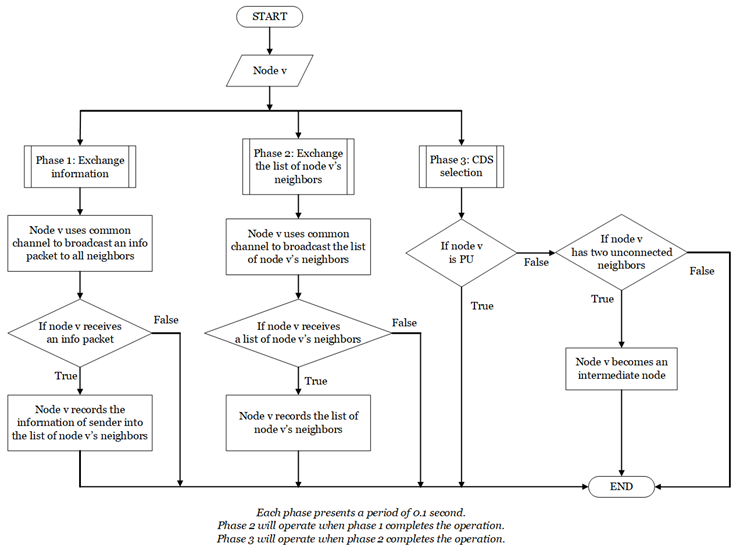
We propose a CDS selection and a CDS size reduction algorithms to achieve a set of intermediate nodes which is latter used as a route searching space underlying infrastructure for routing process. Particularly, the CDS selection algorithm provides a CDS while the CDS size reduction algorithm uses some rules and the weighted function to reduce the size of CDS which supports the cluster process more effective.
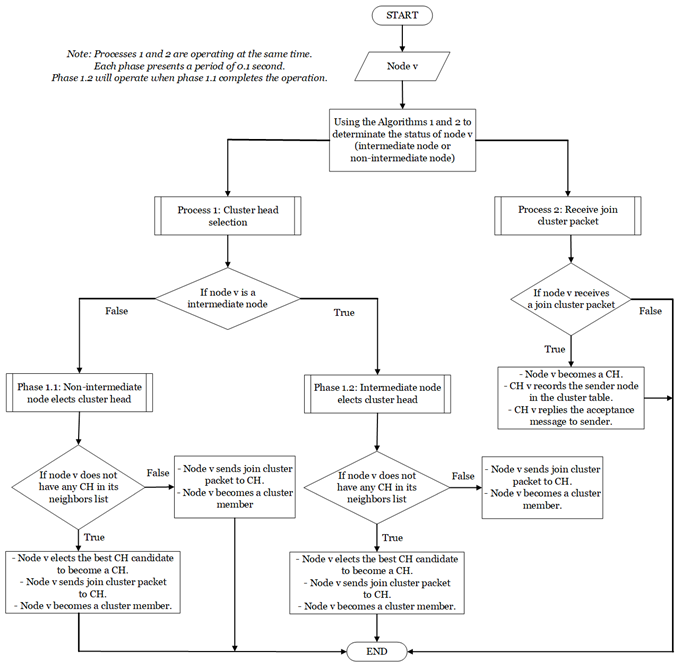
We next propose a CDS based clustering algorithm to formulate clusters by using the weighted function and a node’s identify for the cluster head election process. Moreover, this algorithm also helps to select the gateways and cluster heads in the set intermediate nodes which makes the routing process more efficient.
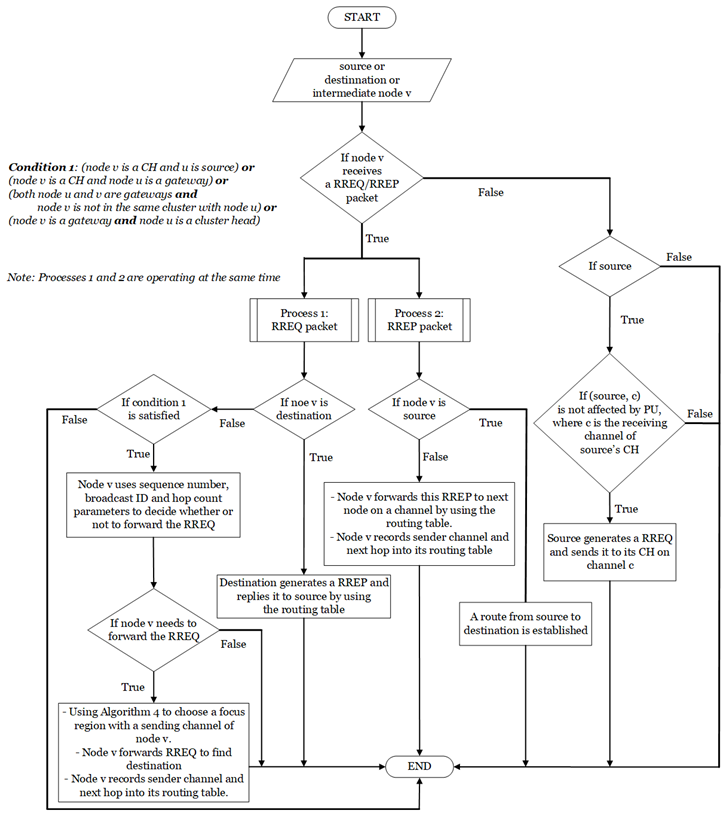
We develop a sending channel based focus region selection (CFS) algorithm in routing phase to support the intermediate nodes to select dynamically a channel for sending a route request packet which can avoid the affected region of a primary user. A CRD protocol is then proposed to establish a good route from a source to a destination which utilizes the CDS based clustering and CFS algorithms to improve the network performances.
We finally implement the proposed CRD protocol in environmental conditions close to reality (OMNET++ platform) to show its superiority over the conventional AODV protocol in terms of PDR, control overhead, delay and energy consumption.
The rest of paper is organized as follows—
Section 2 describes system model, energy model and channel model.
Section 3 presents the proposed CRD protocol consisting of four subsections, such as basic concepts of the system model, necessary function and definitions, packet structures, underlying technology and the proposed CRD protocol. In the underlying technology subsection, we present necessary algorithms such as the proposed CDS selection, the proposed CDS size reduction, the proposed CDS based clustering.
Section 4 evaluates the performances of the proposed protocol in the considered system setup. Finally,
Section 5 concludes the paper.
2. System Model
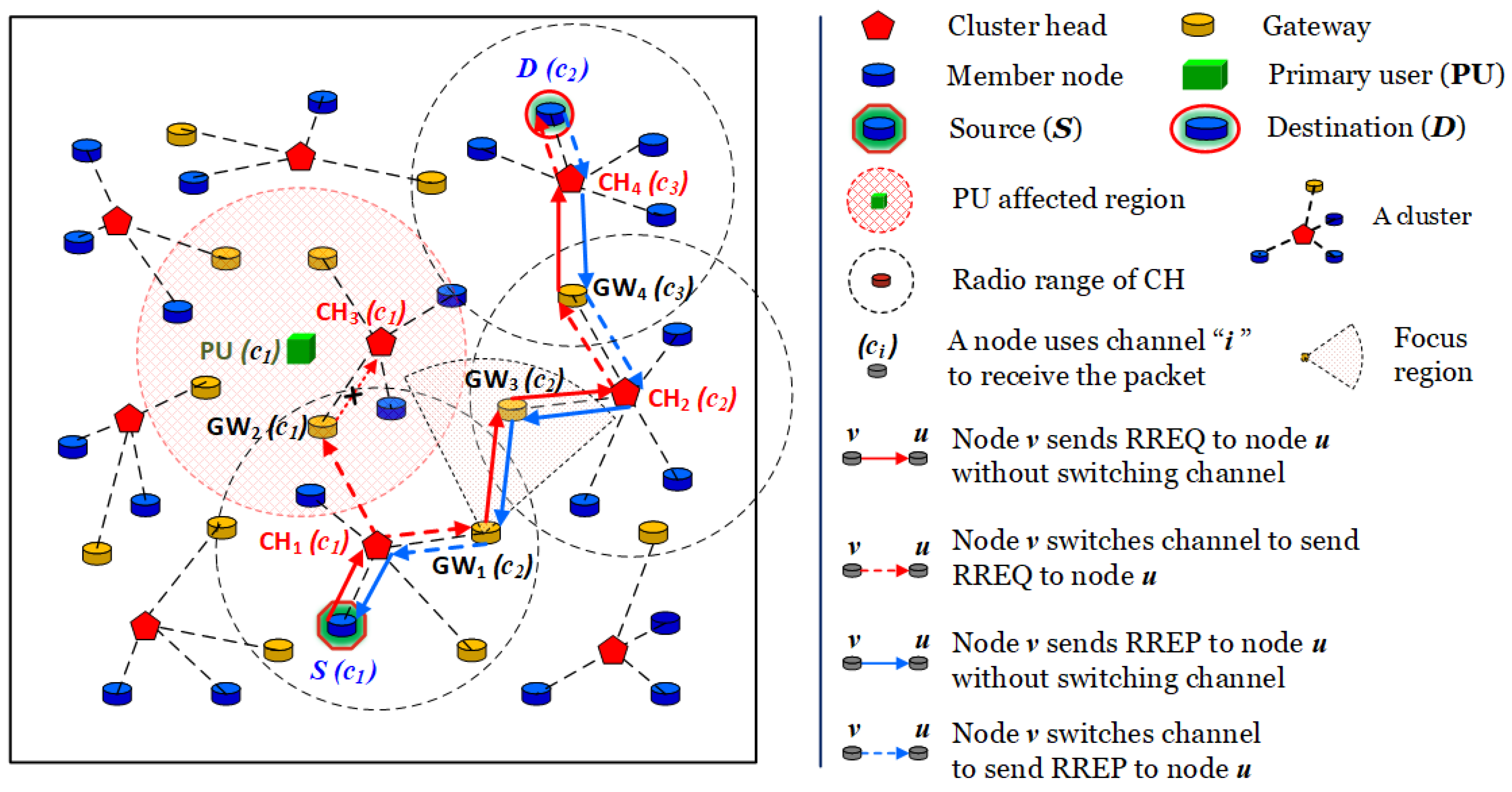
We consider an MCR-MANET consisting of multiple cognitive users (CUs) and a primary user (PU), as shown in
Figure 1. The PU operates on a licensed channel and switches randomly to ON mode or OFF mode. When the PU is in the ON mode, cognitive users can not transmit packets on the licensed channel in the affected region of PU. When the PU is in the OFF mode, cognitive users can use the licensed channel to transmit packets in the networks. This paper focuses on addressing the routing problems when the PU is in the ON mode to improve the spectrum utilization in cognitive environment. Moreover, the PU’s mobility follows the random waypoint (RWP) model. In the secondary network, each user can be seen as a mobile node and its properties can be listed as follows:
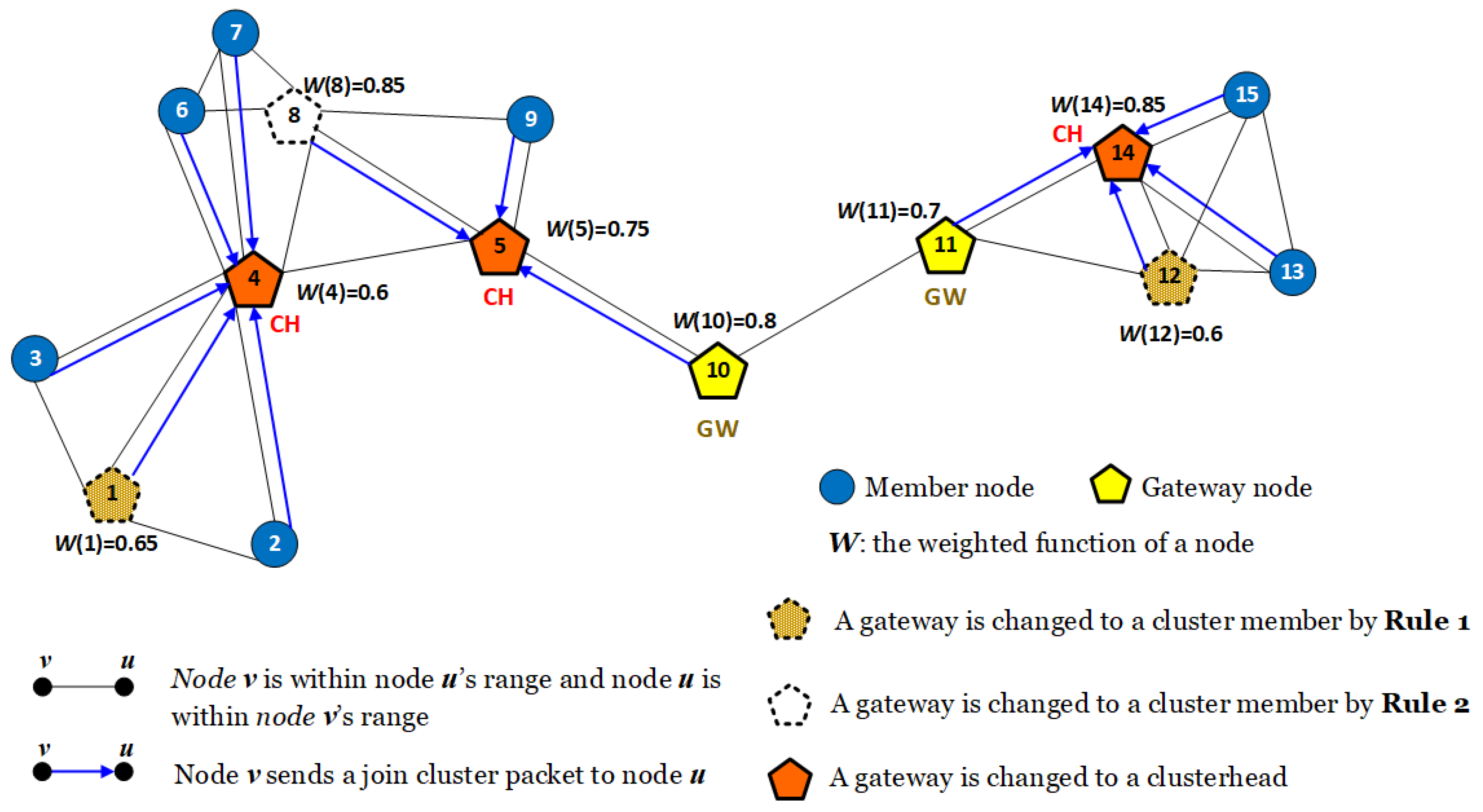
Moreover, mobile nodes in the secondary network can be classified into groups/clusters. Each cluster has three types of nodes including cluster head, gateway and cluster member, respectively [
37]. Firstly, a cluster head (CH) is a representation of a cluster and its tasks are aggregating packets of all cluster members and transmitting the aggregated packet within a single hop. Moreover, CH can directly communicate with a gateway or other CHs. Secondly, a gateway (GW) is an intermediate node which can directly communicate with its CH or CHs/GWs of other clusters within a single hop. Finally, a node in a cluster is a member (CM) if it is neither a cluster head nor a gateway. It only communicates with its CH within a single hop.
Figure 1 describes the operation of cluster head and gateway and cluster member in MCR-MANETs. As can be seen in
Figure 1, source
S generates a RREQ packet and sends it to
without switching channel.
chooses a focus region with sending channel 2 to forward the RREQ to
and
Because
is in the radio range of PU and PU uses channel 1 as licensed channel,
can not forward the RREQ packet on channel 1 to
while
can choose a focus region to forward the RREQ packet to
without switching channel.
continues to forward the RREQ packet to
without switching channel.
chooses a focus region with sending channel 3 to forward the RREQ packet to
continues to forward the RREQ to
without switching channel.
switches to channel 2 and forwards the RREQ packet to destination
When destination
D receives the RREQ packet from
, it generates a RREP packet and switches to channel 3 in order to send the RREP packet to
continues to forward the RREP packet to
without switching channel.
switches to channel 2 and forwards the RREP packet to
continues to forward the RREP packet to
without switching channel.
continues to forward the RREP packet to
without switching channel.
switches to channel 1 and forwards the RREP packet to
continues to forward the RREP packet to source
S without switching channel. When source
S receives an RREP packet, it sends data to the destination. We note that each node in routing process records the next hop and a sending channel into its routing table, which is used to send data from the source to destination
D.
In this paper, we mainly focus on the network layer to establish a route in MANET, where mobile nodes have to exchange their information together by using control packets. The energy consumption is primarily affected by transmitting and receiving control packets. Moreover, the energy consumption of data transmission from a source to a destination mainly depends on transmission energy of sender end reception energy of receiver. Thus, we only consider the transmission energy and reception energy issues that affect clearly on the network layer and considering other energy issues in physical and data link layer is indeed out of the scope of the paper. We apply the energy model in physical layer taken from References [
38,
39] to evaluate the energy efficiency of the proposed routing protocol. The energy consumption varies from 230 mA in receiving mode to 330 mA in transmitting mode, using a 3.3 V or 5.0 V energy supply. These values correspond to a 2400 MHz WaveLAN implementation of IEEE 802.11. The transmission energy and reception energy (in Joules), denoted by
and
, respectively, depend on packet size (in bits) and they can be expressed as
In MANETs, multiple channels are usually supported by the modern wireless MAC protocols [
40]. For example, it is known that the IEEE 802.11 b/g standard provides 14 channels and each node can use multiple channels to communicate with other nodes. Each node has two transceivers, one is always on common channel 0 for controlling packets while the other one can change its channel number from 1 to
for transmitting data packets, where
denotes the total number of channels.