Abstract
Scarcity of data is one of the major challenges in developing automatic computer-aided diagnosis systems, training radiologists and supporting medical research. One solution toward this is community cloud storage, which can be utilized by organizations with a common interest as a shared data repository for joint projects and collaboration. In this large database, relevant images are often searched by an image retrieval system, for which the computation and storage capabilities of a cloud server can bring the benefits of high scalability and availability. However, the main limitation in availing third party-provided services comes from the associated privacy concerns during data transmission, storage and computation. To ensure privacy, this study implements a content-based image retrieval application for finding different types of brain tumors in the encrypted domain. In this framework, we propose a perceptual encryption technique to protect images in such a way that the features necessary for high-dimensional representation can still be extracted from the cipher images. Also, it allows data protection on the client side; therefore, the server stores and receives images in an encrypted form and has no access to the secret key information. Experimental results show that compared with conventional secure techniques, our proposed system reduced the difference in non-secure and secure retrieval performance by up to 3%.
1. Introduction
In the healthcare sector, scarcity of data is one of the major challenges in developing automatic computer-aided diagnosis (CAD) systems, training radiologists and supporting medical research. In individual hospitals, image data are produced to support day-to-day clinical decisions. Therefore, combining these individual data repositories into one could be of great interest and benefit [1,2]. One solution toward this is a community cloud, where organizations with a common goal can benefit from shared services [3]. For example, cloud storage resources can be utilized as a shared data repository among the organizations for joint projects and collaboration. Also, cloud computation-resources can be used to implement several computer vision applications, such as a medical image retrieval algorithms to find and retrieve images relevant to a query from images stored on a cloud-server [1]. Such a retrieval system can support doctors and practitioners in disease diagnosis, training radiologists and medical research and can even aid in developing automatic CAD systems [4,5,6]. Though these capabilities of cloud servers bring the benefits of high scalability and availability to an image retrieval application, their main limitation comes from the privacy concerns associated with sharing data [7,8]. For example, like all communication systems, when images are outsourced to the avail of cloud services, they are at the risk of being stolen. Also, to be aligned with privacy regulation acts, it is not desirable to disclose any privacy-sensitive information during computation and storage to the cloud service providers.
To solve these privacy issues, secure content-based image retrieval (CBIR) techniques are proposed. In general, these techniques can be categorized as the ones that extract features on the client side and then encrypt both features and images before the cloud server receives them. They are often referred to as two-stage secure CBIR techniques. Secure CBIR was proposed in [9,10,11,12,13,14], which show examples in this category. Since feature extraction is in the plain image domain, strong data protection techniques can be exploited. For example, chaos theory-based algorithms were implemented in [9,14]. However, implementing a feature extractor on the client side is computationally inefficient, especially in resource-constrained environments. On the other hand, one-stage secure CBIR techniques are encryption-based, as they encrypt images on the client side prior to the cloud server storing them or receiving them as a query [15]. The images are protected in such a way that their features can be extracted directly from the cipher images, thereby eliminating any preprocessing on the client side, aside from encryption. Examples of secure CBIR in this category were proposed in [16,17,18]. Cryptographic techniques such as homomorphic encryption, which can enable computation directly on the encrypted data, can be used. However, their computational complexity and compatibility should be considered [10]. Alternatively, lightweight perceptual encryption (PE) was proposed, which hides only perceivable information in images while leaving their intrinsic characteristics intact to enable privacy-preserving computations. Its applications can be extended to secure CBIR applications. For example, for secure color image retrieval applications, the authors of [19] proposed a pixel-based PE technique that randomly substitutes and inverts pixel values to hide identifiable information in images. Similarly, the authors of [20] proposed a block-based PE technique that performs block-level transformations, and its security was improved in [21] by adopting sub-block processing. These PE-based CBIR techniques were proposed for natural image retrieval applications, but natural image contents significantly differ from those of medical images, which makes their retrieval more challenging [16]. Furthermore, in one-stage CBIR systems, there is a trade-off relationship between retrieval performance and privacy preservation.
To address the aforementioned challenges, this paper implements an image retrieval system for brain tumor images in the encrypted domain to find a better trade-off in a cost-effective manner. For this purpose, we propose a pixel-based PE technique that protects the image contents in a way that it can still allow the computation of an image retrieval algorithm over encrypted data. In the proposed framework, we implement the region-of-interest (ROI)-based medical image retrieval algorithm proposed in [3], which combines adaptive spatial pooling [22] and Fisher vector representation [23]. In this method, similar images are retrieved by comparing their feature vectors using a closed-form metric learning method. One of the main advantages of the proposed secure CBIR system is that data are protected on the client side. Therefore, the server receives template and query images in an encrypted form and has no access to the secret key information.
2. Related Works
The widespread adaptability of outsourced computation and storage resources in the healthcare domain raises several privacy concerns. Regarding this, numerous privacy-preserving solutions have been proposed to protect data during data transmission, storage and usage. For a comprehensive overview, we refer to [7], which summarizes the existing privacy-preserving techniques in outsourced medical image analysis applications. Nonetheless, in this section, we mainly focus on techniques that are applicable for privacy-preserving medical image retrieval applications.
In the domain of secure content-based medical image retrieval, Zhang et al. [9] proposed a medical image retrieval algorithm that uses encrypted images. This scheme performs logistic chaos-based encryption in the frequency domain on the images prior to extracting their features. The normalized correlation coefficient is used to evaluate the similarity between a query image and stored images. Zhu et al. [10] proposed TAMMIE, a secure image retrieval algorithm where medical images and features are protected using symmetric and matrix encryption techniques. To evaluate cipher-image similarity, a privacy-preserving Mahalanobis distance comparison method is proposed. Also, for better retrieval accuracy, a pretrained convolutional neural network (CNN) is used to extract features from the plain images. Li et al. [11] proposed PMIR, which modifies TAMMIE by replacing the Mahalanobis distance with the Euclidean distance for feature vector comparison. Later, Li et al. [12] proposed AVPMIR, which allows users to validate the correctness of the retrieval results. For faster retrieval speeds, clustering and index merging techniques are employed on the cloud server. In addition, an improved logistic chaotic mapping algorithm is proposed to protect images during transmission and storage. In another work, Duan et al. [13] implemented a CNN for medical image feature extraction and the Euclidean distance to measure image similarity. In this scheme, first, features are extracted from the plain images on the client side, and then the images are encrypted using a symmetric key algorithm before uploading them to the cloud server. Also, a lightweight access control mechanism is implemented to protect data from unauthorized users. Similarly, Rajan et al. [14] leveraged the ConvNeXt model for feature extraction in the plain domain. Then, they proposed an image protection algorithm based on multiple chaotic maps and DNA encoding to protect the images prior to uploading them to the server. In general, scarcity of data in medical imaging makes it difficult to train a deep learning-based feature extractor for medical image retrieval applications. Therefore, federated learning can be leveraged to collaboratively train the feature extractor module, as proposed in [2].
The works mentioned thus far can be categorized as two-stage secure CBIR techniques that extract features from the client side to leverage strong encryption algorithms for image protection. However, implementing a feature extractor on the client side is computationally inefficient. Therefore, we next consider works that are in one-stage secure CBIR techniques category. For example, Guo et al. [16] proposed a privacy-preserving CNN employing homomorphic encryption to extract features from medical images in the encryption domain for classification and retrieval applications. Similarly, Cai et al. [17] proposed a privacy-preserving CNN feature extraction method for medical image retrieval applications that implements a set of secure two-party computation protocols. Aside from this, blockchain-based approaches have also been proposed to address the privacy concerns in multi-party image retrieval applications. For example, Shen et al. [18] proposed a blockchain-based scheme for secure medical image retrieval, where the image features are encrypted using a secure multiparty computation protocol and the Euclidean distance is used for images similarity.
Secure CBIR techniques [16,17] address the limitations of two-stage secure CBIR techniques, but their computational and communication costs are still among their challenges [10]. On the contrary, we propose a one-stage secure CBIR scheme for medical imaging applications that implements a lightweight PE algorithm to find a better trade-off between privacy and retrieval performance in a cost effective manner.
3. Methods
3.1. Preliminaries
- Squared Sine Logistic Map. The squared sine logistic map (SSLM) proposed in [24] is defined as a combination of two simple dynamic chaotic maps, namely the logistic chaotic map and sine chaotic map. The logistic map parameterized by the control variable is as follows:
The sine map parameterized by the control variable is given by
For a positive initial value , the square operation ensures that the map’s iterations are in the interval . To control the dynamical behavior of SSLM, the parameters r and are chosen in the intervals and , respectively. In general, the r value varies while the value remains fixed, such as , as recommended in [24]. The SSLM exhibits better chaotic behavior than the logistic map, and its main advantage comes from its simple calculations. Also, SSLM has favorable properties for image encryption, as demonstrated in [19]. Therefore, we utilized SSLM to generate random sequences for the secret key generation in our proposed PE algorithm.
3.2. Proposed Secure Medical Image Retrieval System
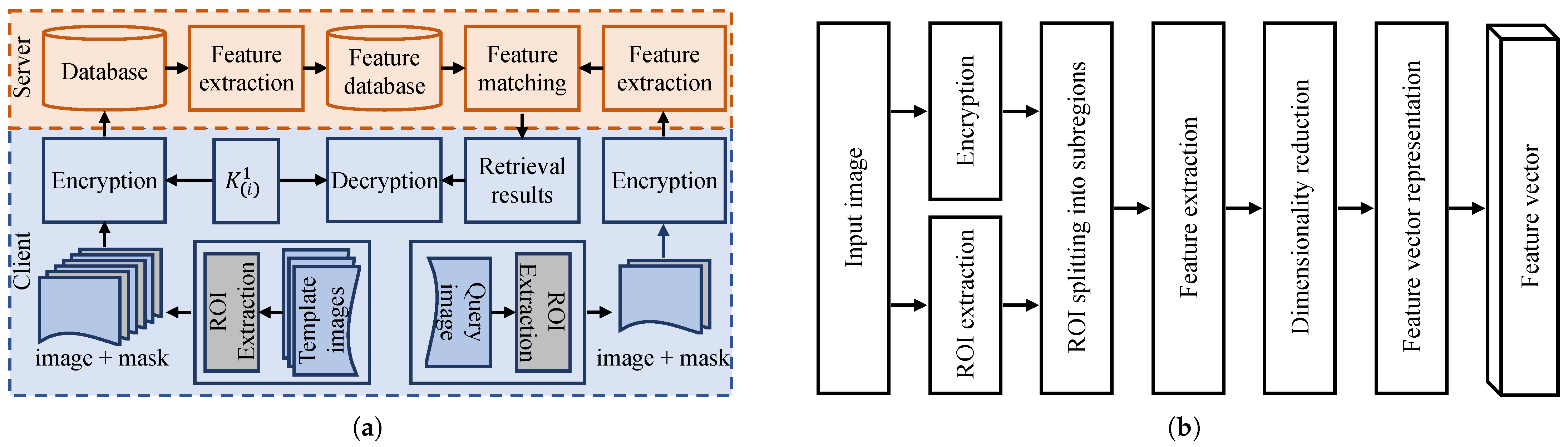
Figure 1a shows the framework of our proposed secure brain tumor image retrieval system, which mainly consists of two modules: an image encryption algorithm and an image retrieval method. Below, we describe them in detail.
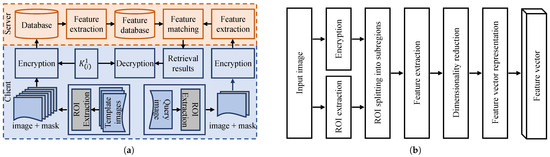
Figure 1.
An illustration of the proposed secure image retrieval scheme. (a) The overall framework adopted from [1]. (b) The secure feature extraction module.
3.2.1. Proposed Perceptual Encryption Algorithm
The proposed algorithm makes an image perceptually unrecognizable by hiding only part of the information in it. This data protection is achieved by a piece-wise encryption function that selectively substitutes pixel values based on a random key. Also, each pixel substitution is dependent on previously encrypted pixel values to exhibit favorable encryption properties. This procedure is described below in detail.
- Key generation. To generate a secret key , we iterate the SSLM in Equation (3) times to obtain three random sequences , and , each of a size N. The first M iterations are discarded to eliminate the transient effect, and N is the number of pixels in an image. The control parameter of the SSLM is set to for sequence , for sequence and for sequence . The initial value of the first sequence is set at random to , while it is set to for the second sequence and for the third sequence. These three sequences are preprocessed as and in Equation (4) to generate the secret key in Equation (5):
This key is used to substitute the pixel values in an image as described below.
- Encryption. A cipher image vector of a plain image vector can be obtained as follows:where is the number of intensity levels and is the previously encrypted pixel value. When encrypting the first pixel value , the value is set as the last pixel value of the plain image.
- Decryption. The proposed encryption method is a symmetric key algorithm, and its corresponding decryption process to recover the original image is the inverse of Equation (6), given by
3.2.2. Image Retrieval System
Following [3], our image retrieval system consists of three main steps—feature extraction, feature vector representation and feature matching—as illustrated in Figure 1b. In the first step, an image is divided into tumor (ROI) and background regions, where local features are extracted by dividing the ROI into subregions. Next, feature vector representation using the Fisher kernel technique is applied to concatenate the local features into a single vector to obtain the image’s global features. Finally, a closed-form metric learning method is applied to find similar images in the database to the query image by matching their feature vectors. These steps are explained in detail below.
- Feature extraction. The first step is to segment images by differentiating the ROI (such as the tumor region) from the background. This segmentation aids the feature extraction function in representing an image in a high-dimensional feature space by taking the disease characteristics into account. Also, we use an augmented tumor region as the ROI to identify the tumor-surrounding tissues because they can provide important information for the identification of brain tumor types, as highlighted in [3]. Second, we implement the method proposed in [22] that considers the intensity distribution and spatial information to further divide the ROI into subregions. To define the image’s local features, we extract raw image patches from each subregion and apply principal component analysis (PCA) to reduce their dimensions. To give these feature vectors a single vector representation, we apply a Fisher kernel in the next step.
- Feature vector representation. For feature vector representation, we apply a Fisher kernel [23], which is defined as follows:where is the Fisher information matrix of , expressed as
Given that is symmetric and positive definite, it thus has a Cholesky decomposition (). Therefore, the Fisher kernel can be written as , a dot-product between normalized vectors, as shown in Equation (10):
Here, is the vector representation of a set that contains T features extracted from an image, as proposed in [23]:
The gradient of the log-likelihood describes the direction in which the model parameters should be changed to better fit X. Following [23], we assume that X is modeled by a generative model such as a Gaussian mixture model (GMM) using a probability density function with a set of parameters: the mixture weight (), mean vector () and diagonal covariance matrix (), denoted as .
- Feature matching. Let be the feature vector for a query image q. The goal of a feature matching function is to return the template image , wherewith being a distance metric. This can be posed as an optimization problem where the objective is to minimize the distance between similar images while maximizing it between dissimilar images. This objective can be defined as follows [3]:where
The S and D are two sets containing image pairs () and their corresponding labels () (that is, ) contain pairs of similar images, and contains pairs of dissimilar images. Also, is the trace operation, L is a linear transformation matrix that projects the image features to a new feature space, and is a positive semi-definite matrix.
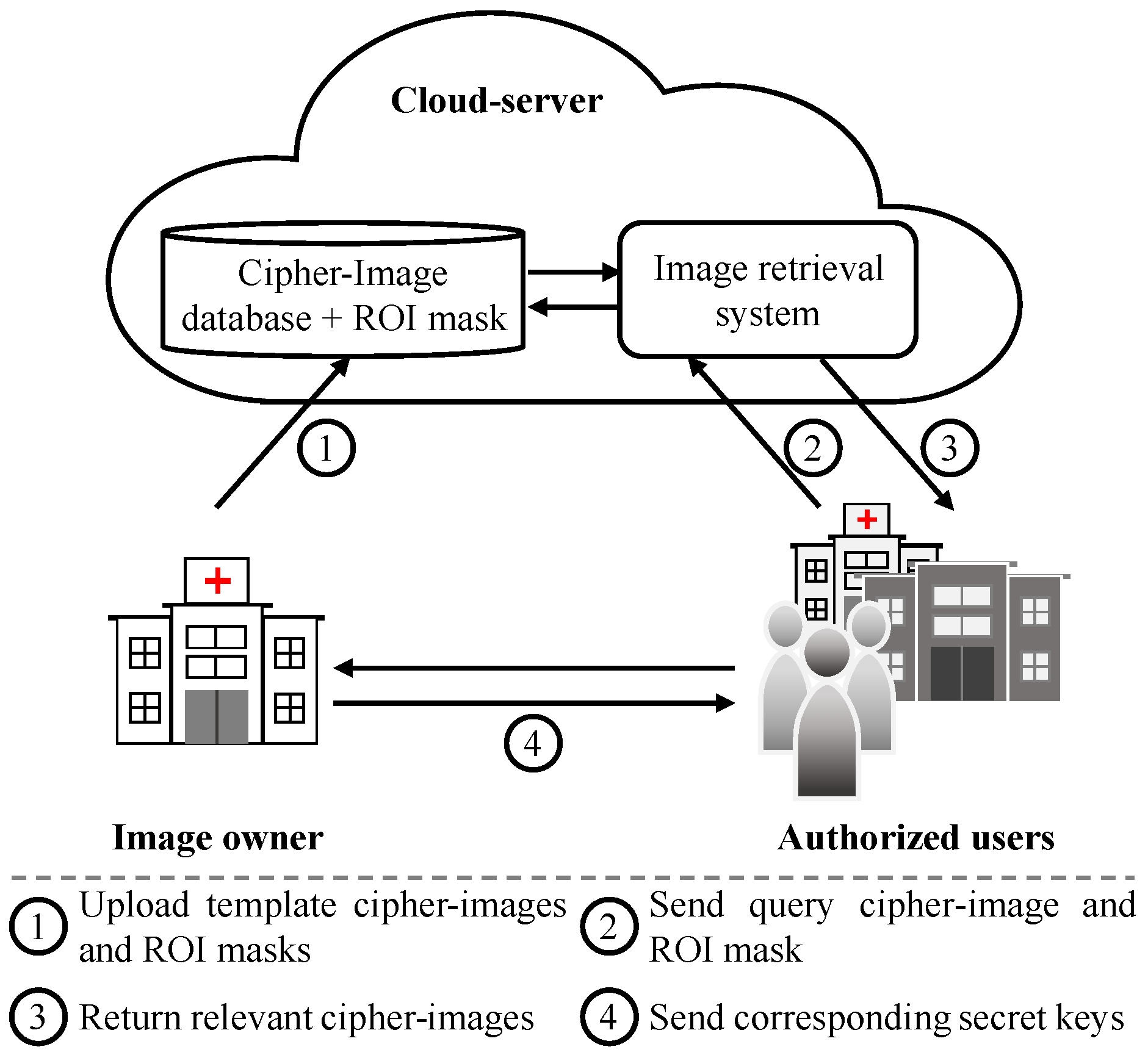
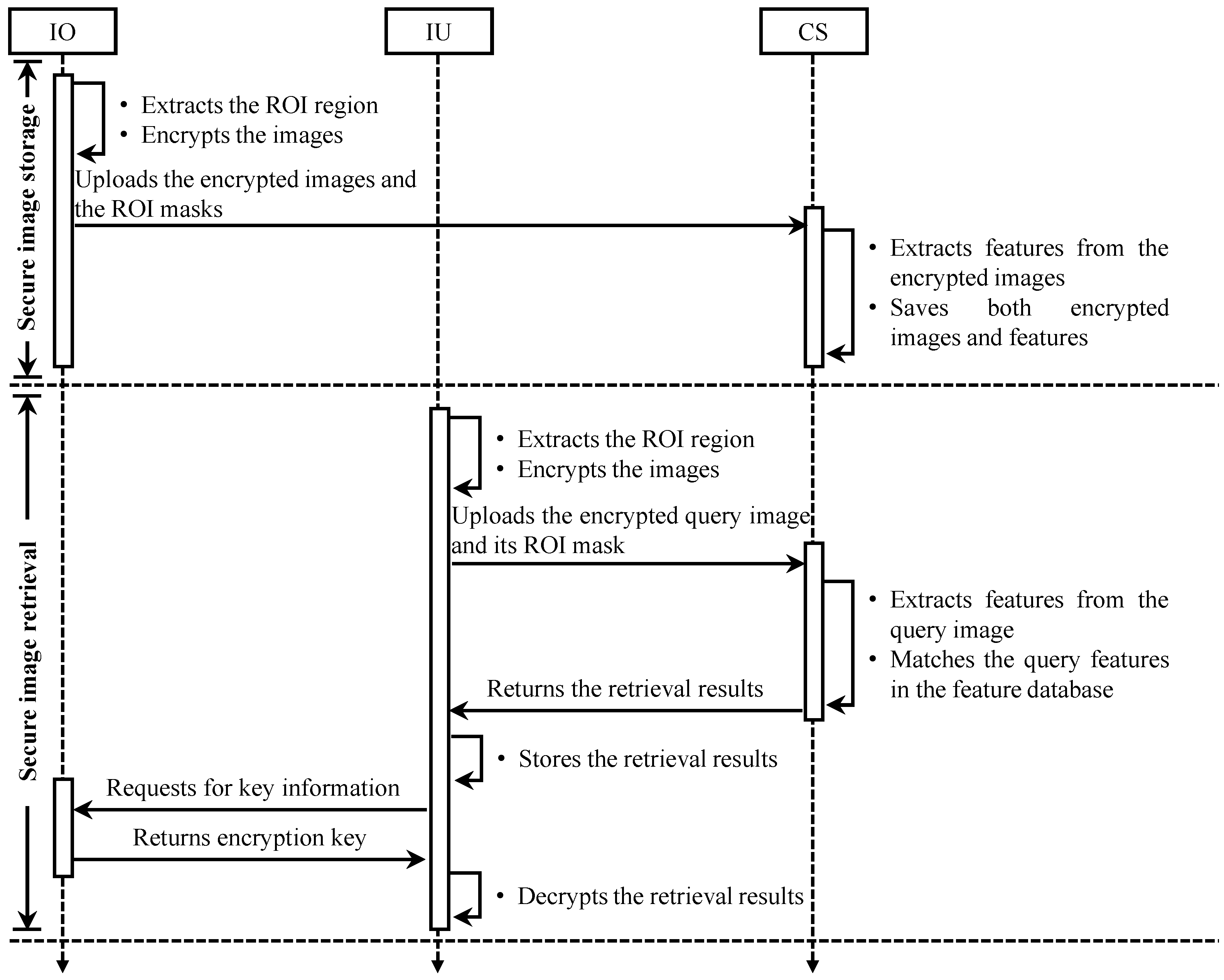
3.3. System Model
Figure 2 shows our system model for a secure brain tumor image retrieval application based on image encryption, while Figure 3 shows the end-to-end information flow in our proposed secure medical image retrieval application. This system has three main entities: image owner (IO), cloud server (CS), and image user (IU).
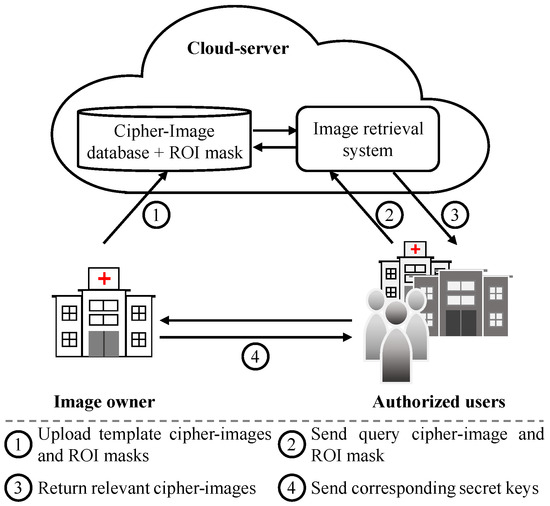
Figure 2.
System model for a secure image retrieval application, adopted from [1].
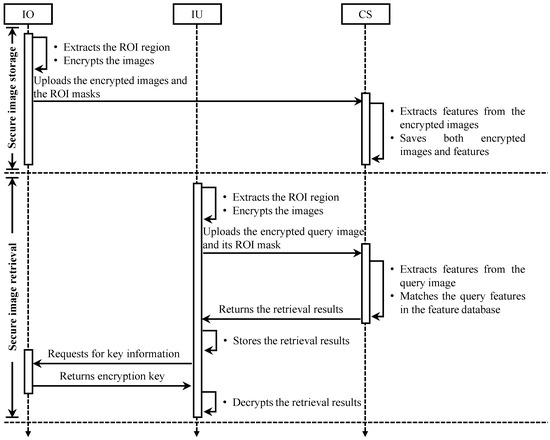
Figure 3.
End-to-end information flow in proposed secure medical image retrieval application (IO = image owner, IU = image user, CS = cloud server).
The image owner owns a collection of n images and wants to store it on the cloud server in the encrypted form to facilitate a secure medical image retrieval application. The encrypted images are obtained as , where is a collection of secret keys and h is a searchable encryption function. The image owner first generates a mask for by extracting the ROI regions in each image. Then, the tuple that consists of the cipher image collection and the ROI masks are uploaded to the cloud server.
Image users are the authorized entities that can request and retrieve images relevant to their query q from the cloud server. To request a search, the image user processes the query image using the same steps as the image owner. The user first generates a mask and for q and then uploads both and as a tuple to the cloud server. After the relevant images are returned, the user can decrypt them by requesting the corresponding secret key from the image owner.
The cloud server implements a feature extractor to extract features from the image owner’s data collection . Both the features and encrypted images are stored on the cloud server. Also, when a user submits a request with , the cloud server first extracts features from the user query. Then, to search similar images in the database, the cloud server implements a retrieval model that matches the extracted features from the query image with the stored features . Finally, the retrieval results are returned to the origin of query.
In this system model, the retrieval application’s computation and storage are carried out directly on the cipher images. Therefore, the secret key information is kept from the cloud-server. It is noteworthy that a secure image retrieval system should allow the encryption of template and query images using different keys when the image owner and user are two different entities. The three modules of this system—image encryption, feature extraction, and image retrieval—are based on the methods outlined in Section 3.
3.4. Threat Model
For security in the proposed secure CBIR scheme, we considered a data recovery attack in which an adversary tries to recover the dataset contents from by devising a function to minimize the dissimilarity metric .
4. Simulation Results
4.1. Retrieval Performance Analysis
- Dataset. Although different medical image modalities, such as Positron Emission Tomography (PET), Computed Tomography (CT), and Magnetic Resonance Imaging (MRI) scans can be used to create images of the brain, MRI remains the primary diagnostic modality for brain tumors because it is highly sensitive in visualizing soft tissues within the brain compared with other modalities. Therefore, we used an MRI dataset in our experiments. It is worth mentioning that our proposed secure retrieval scheme can be readily implemented for other types of image modalities. In simulations, we evaluated the performance of different brain tumor retrieval schemes on a public brain tumor MRI dataset available from [3]. This dataset contains 3064 T1-weighted, contrast-enhanced images in size from 233 patients with three kinds of brain tumors: meningioma (708 slices), glioma (1426 slices), and pituitary (930 slices). The images in the dataset were split into five subsets for fivefold cross-validation. Among these subsets, one was used as query images, while the rest of them were used as template images. Also, it was ensured that slices from the same patient did not appear simultaneously in the template and query images. Figure 4 shows an example image from the dataset for each brain tumor type in plain and encrypted form. The cipher images were obtained by encrypting the plain images using our proposed PE algorithm. In the cipher images, pixel values which were substituted during encryption appear as white noise for the key value in Equation (6).
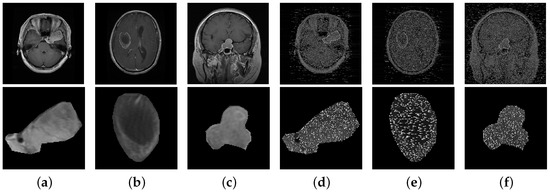 Figure 4. Example images from the dataset for each brain tumor type. (a–c) Plain-images and (d–f) their corresponding cipher images obtained from our proposed encryption technique. The tumor region (ROI) in each image is enlarged and shown below it. This information is visually unrecognizable in the cipher images.Figure 4. Example images from the dataset for each brain tumor type. (a–c) Plain-images and (d–f) their corresponding cipher images obtained from our proposed encryption technique. The tumor region (ROI) in each image is enlarged and shown below it. This information is visually unrecognizable in the cipher images.
Figure 4. Example images from the dataset for each brain tumor type. (a–c) Plain-images and (d–f) their corresponding cipher images obtained from our proposed encryption technique. The tumor region (ROI) in each image is enlarged and shown below it. This information is visually unrecognizable in the cipher images.Figure 4. Example images from the dataset for each brain tumor type. (a–c) Plain-images and (d–f) their corresponding cipher images obtained from our proposed encryption technique. The tumor region (ROI) in each image is enlarged and shown below it. This information is visually unrecognizable in the cipher images.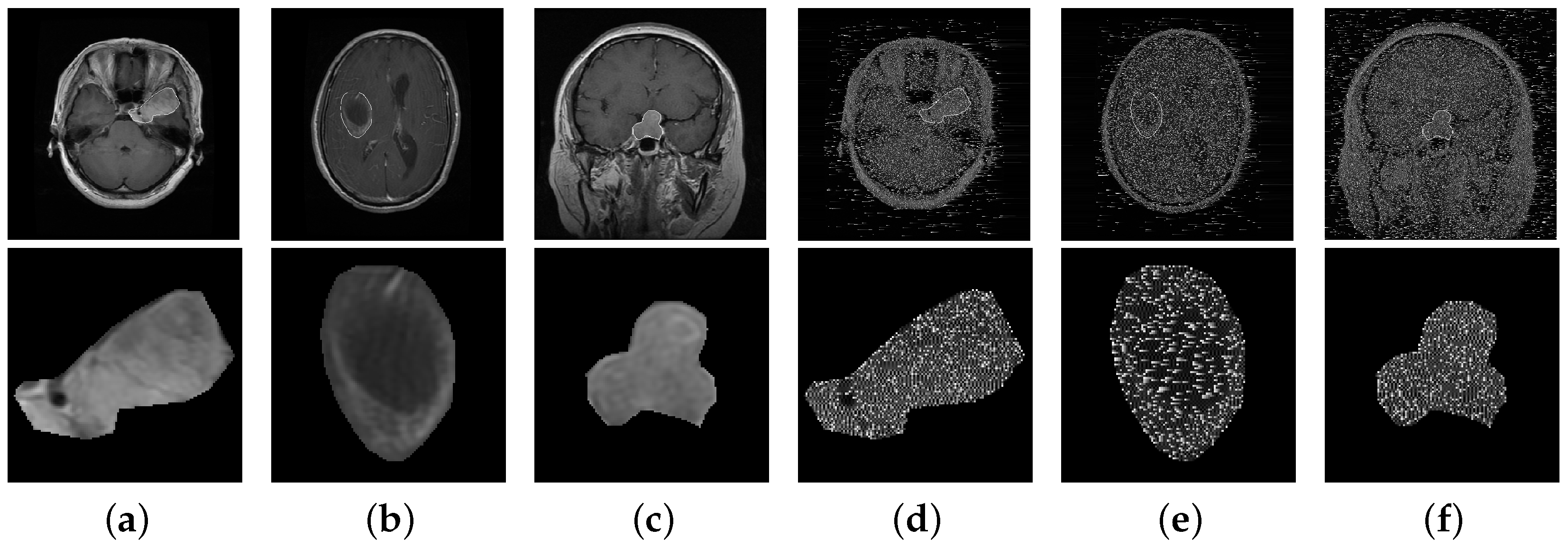
- Retrieval performance evaluation metric. The precision metric is one of the most commonly used metrics to evaluate an image retrieval system’s performance. It measures the retrieval performance in terms of how many retrieved images are relevant. Let and denote the sets of similar and retrieved images, respectively. The precision (P) is defined as follows:
Aside from the precision metric, we also evaluated the retrieval performance using the average precision (AP) metric, which measures the retrieval performance in terms of how well relevant images are ranked within the list of retrieved images for a single query. The AP score for a query image (q) is calculated as follows:
Here, means at position k within the list of retrieved images, and is a binary variable that takes a value of one if the retrieved result is relevant; otherwise, it takes a value of zero. The AP is a single-query evaluation metric, and therefore we extended its concept to calculate the mean AP (mAP) across all of the query images. The mAP score of a retrieval system that consists of Q total query images is defined by
These metric values lie in the range , where one indicates the best performance of an image retrieval system.
- Retrieval results. To analyze the efficiency of proposed technique, we implemented the different PE techniques proposed in [25,26,27] and analyzed their impact on the image retrieval system. For all techniques, analyses were carried out on the same dataset with fivefold cross-validation. Following [3], throughout our experiments, image dilation with a disk-shaped structuring element with a radius of 24 was used to augment the ROI region, and the size of the raw image patches was set to be nine for the local features. Also, for all encryption techniques, we considered encrypting all images with the same and different keys.
Table 1 compares all retrieval techniques in terms of their mAP and precision scores by varying the feature dictionary size between 16, 32, and 64. Also, the precision score was computed for different numbers of retrieved images. The metric scores are reported as the mean across the whole dataset. It can be observed that the retrieval performance of all of the techniques improved as the feature dictionary size increased in both the same keys and different keys scenarios. For a given dictionary size, the proposed scheme delivered a better performance difference between plain image and cipher image retrieval compared with the existing techniques. This difference was especially prominent when different keys were used in the cryptosystem. Furthermore, it can be observed that varying the number of retrieved images had no significant impact on the precision scores of any techniques.

Table 1.
Impact of different perceptual encryption schemes on brain tumor image retrieval performance in comparison with that of plain images. The metric scores are reported as mean and standard deviation values (i.e., mean ± std %). D is the feature dictionary size.
As mentioned earlier, the metric scores reported thus far are the mean values across different tumor types. Therefore, Table 2 evaluates the retrieval performance of the proposed method for different types of brain tumors and compares it with that of the non-secure and best-performing conventional encryption techniques [26]. It can be observed that the performance trend across all tumor types remained the same (i.e., it improved as the dictionary size increased for all techniques). In addition, the variance in retrieval performance of the proposed method across different tumor types was smaller compared with that in [26].

Table 2.
Retrieval performance of proposed method for different brain tumor types in comparison with non-secure technique and best-performing existing secure technique [26]. The metric scores are reported as () for secure techniques, and is the standard deviation. D is the feature dictionary size. T1, T2 and T3 correspond to meningioma, glioma and pituitary brain tumors, respectively.
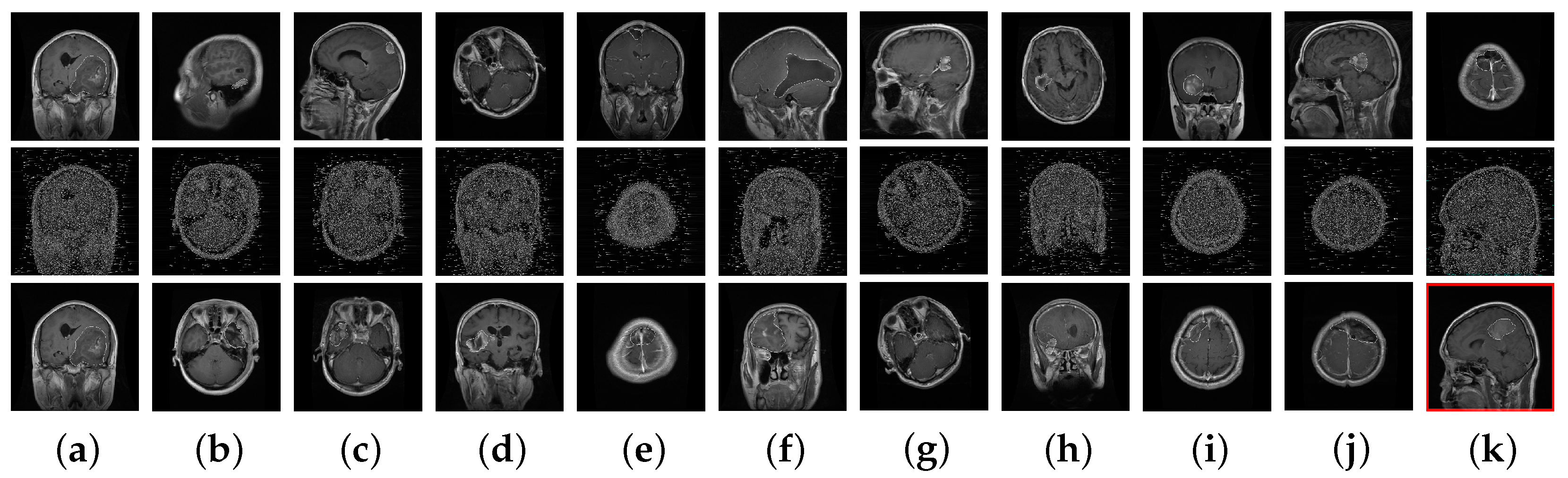
Finally, for visual analysis, Figure 5 shows an example query image and its corresponding retrieval results for both the non-secure and proposed secure retrieval techniques (where ). Though, most of the images retrieved using a cipher image query were different from those retrieved using plain image retrieval, inter-class discrimination was still preserved in the encrypted domain, as shown by the correct retrieval results.
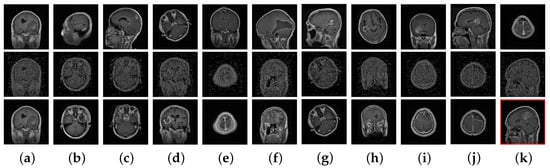
Figure 5.
Examples of non-secure and secure retrieval of images similar to a query image from the database. (a) Query images and (b–k) retrieved images. The non-secure retrieval results are in the first row, and the secure retrieval results are in the second row, with their decrypted images in the third row. The images were encrypted using the proposed encryption method with different keys. Incorrect retrieval results are in red boxes.
4.2. Encryption Efficiency Analysis
- Key space analysis. In general, the key space of an encryption algorithm should be larger than to resist brute-force attacks. The secret key of our proposed scheme is generated using three random sequences by varying the control parameter of the SSLM. Considering a precision of , the key space size can be determined to be , which is larger than the recommended value to resist a brute-force attack.
- Comparison with existing PE techniques. Similar to the proposed technique, the conventional PE techniques proposed in [25,26] modify only half of the pixel values. Their encryption function is an identity map for , while a cipher pixel value was computed to be in [25] and in [26] for . Consequently, each pixel is independently encrypted in them, which may make them vulnerable to select plaintext attacks. On the other hand, a PE technique was proposed in [27] where each pixel substitution is dependent on all previously encrypted pixels. Their encryption function is closely related to ours, given in Equation (6), with a difference in that the term computes as , as opposed to our identity map. This can achieve better security efficiency but at the cost of the downstream application performance, as given in Table 1.
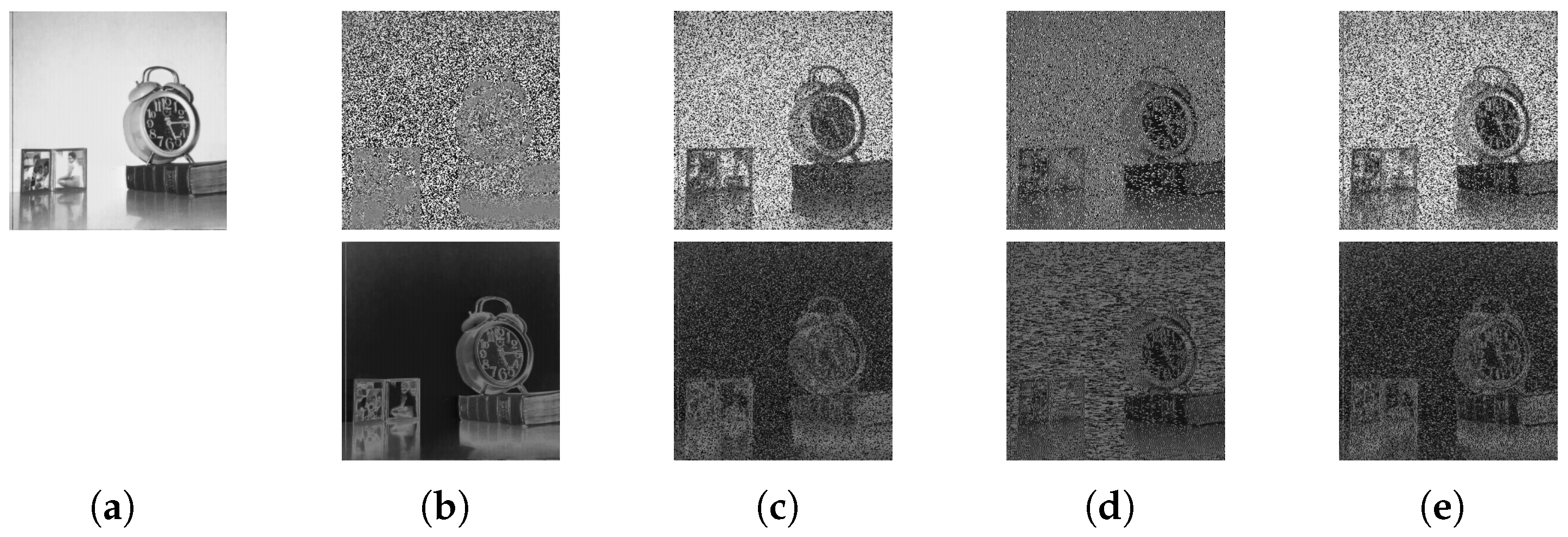
- Robustness against ciphertext-only attacks. For this analysis, we considered a threat model where an adversary (for example, a semi-honest cloud service owner) performed a ciphertext-only attack (COA) to decrypt a cipher image without access to the secret key. A popular example of such COAs against PE was proposed in [28], where the goal was to recover partial information from a cipher image to identify its contents. This attack works by guessing the leading bit of each pixel value with respect to the neighboring pixels, and hence it is also named the “leading bit attack”. Figure 6 shows an example image (https://sipi.usc.edu/database/, accessed on 30 October 2024) recovered by performing a leading bit attack on the cipher images of different PE techniques. Here, the example is of a natural image, as it is easy to understand visually meaningful information in such images. It can be observed that the image recovered from the proposed cipher image did not reveal any information. On the contrary, a PE technique that simply inverts pixel values in an image is more susceptible to such an attack; that is, its contents can be recovered with high visibility, as shown in Figure 6b.
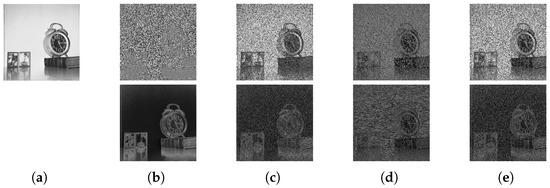 Figure 6. A ciphertext-only attack on perceptual encryption techniques. (a) Plain image and (b–e) cipher images produced by the methods in [25,26,27] and the proposed method. The recovered images are below each cipher image.
Figure 6. A ciphertext-only attack on perceptual encryption techniques. (a) Plain image and (b–e) cipher images produced by the methods in [25,26,27] and the proposed method. The recovered images are below each cipher image. - Time complexity analysis. To analyze the computational overhead of the proposed PE scheme on the client side, Table 3 compares its execution time with those of the schemes proposed in [25,26,27]. For this analysis, we chose 2124 images from our dataset, which were uniformly distributed among the three tumor types and each image was 512 × 512 in size. The time was reported in seconds as a mean across all of the images. It can be observed from Table 3 that a PE technique such as the one proposed in [25,26], which processes each pixel independently, had a shorter encryption time, as it is highly parallelizable. However, this can also lead to certain security vulnerabilities, such as data reconstruction attacks. On the other hand, in proposed method, only half of the current pixel processing is dependent on the previously encrypted pixel values to deliver a desirable level of security in an acceptable execution time.
 Table 3. Comparison of encryption and decryption times in seconds of proposed scheme with existing techniques.
Table 3. Comparison of encryption and decryption times in seconds of proposed scheme with existing techniques.
4.3. Discussions
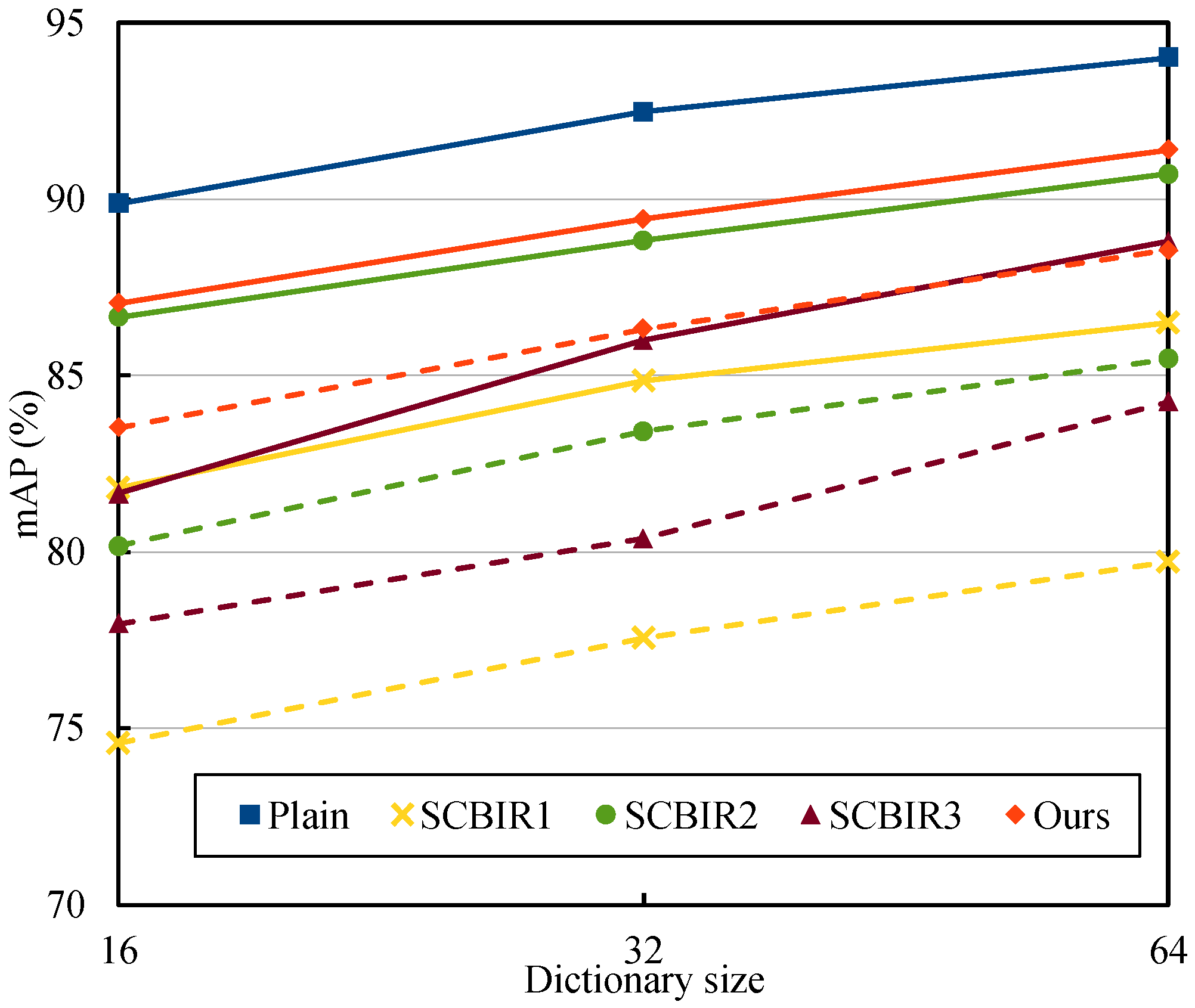
Figure 7 shows the mAP performance as a function of the dictionary size. It can be observed that the retrieval performance for the non-secure and secure methods improved similarly as the dictionary size increased. Compared with the existing techniques, our proposed scheme delivered a better performance difference between plain and cipher image retrieval in the same and different key scenarios. Though there was a difference in plain and cipher image retrieval performance, the proposed scheme outperformed the existing techniques. For example, when considering the dictionary size to be 64, the difference in the non-secure and proposed secure techniques’ mAP scores was 2.61% when (best case) and 5.46% when (worst case). The errors were 0.69% (best case) and 3.08% (worst case), which was less than that of the conventional best technique [26]. Therefore, the efficiency of the proposed secure system was more significant when using different keys, which is important for enabling applications where the image owner and users are not the same.
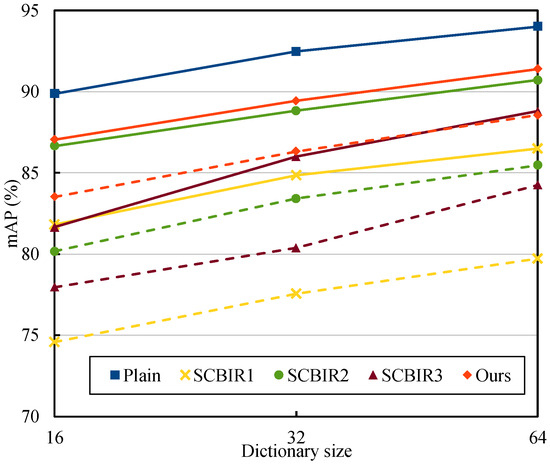
Figure 7.
Comparison of proposed secure retrieval system with existing methods in terms of mAP score. Plain is a non-secure CBIR technique proposed in [3], while SCBIR1, SCBIR2, and SCBIR3, are the secure CBIR techniques proposed in [25,26,27], respectively. For the secure techniques, the solid-line and dashed-line curves indicate use of the same and different encryption keys, respectively.
Despite achieving a better trade-off between security and retrieval performance, the limitation of the proposed secure image retrieval system comes with the extraction of an ROI and its correctness. First, the ROI needs to be extracted in the plain domain, thus necessitating computation on the client side, which could be challenging, especially in resource-constrained environments. Second, although it is not necessary to precisely segment the tumor region, as we used an augmented ROI, mislabeled tumor areas could still lead to inaccurate retrieval results.
5. Conclusions
In this work, we proposed a one-stage secure CBIR system for retrieving different types of brain tumor images in an outsourced database. In this system, the image protection algorithm belongs to perceptual encryption that preserves an image’s intrinsic characteristics while hiding only perceivable information in them. Simulation analysis demonstrated that our proposed system reduced the difference in non-secure and secure retrieval performance (both mAP and precision scores) on the same dataset using the same retrieval algorithm compared with its other secure counterparts.
In this work, similar images to a query image were retrieved by matching features extracted only from the ROI. Therefore, future research will be focused on two aspects. First, considering the selective image encryption principle in our proposed secure image retrieval scheme can further reduce the encryption time. Second, proposing a computationally efficient segmentation technique will ease the burden on the client side.
Author Contributions
Conceptualization, I.A.; methodology, I.A.; software, I.A. and M.S.U.; validation, S.S.; formal analysis, I.A. and M.S.U.; investigation, I.A. and M.S.U.; resources, S.S.; data curation, I.A. and M.S.U.; writing—original draft preparation, I.A.; writing—review and editing, I.A., M.S.U. and S.S.; visualization, I.A.; supervision, S.S.; project administration, S.S.; funding acquisition, S.S. All authors have read and agreed to the published version of the manuscript.
Funding
This study was supported by a research fund from Chosun University in 2023.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
All of the datasets used in this study are publicly available. The USC-SIPI Miscellaneous dataset is accessible at https://sipi.usc.edu/database/database.php?volume=misc (accessed on 30 October 2024). The brain tumor MRI dataset is available at https://figshare.com/articles/dataset/brain_tumor_dataset/1512427 (accessed on 16 September 2024).
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Ahmad, I.; Uzzal, M.S.; Shin, S. Secure Retrieval of Brain Tumor Images using Perceptual Encryption. In Proceedings of the 2025 IEEE International Conference on Big Data and Smart Computing (BigComp), Kota Kinabalu, Malaysia, 9–12 February 2025; pp. 73–74. [Google Scholar] [CrossRef]
- Tabatabaei, Z.; Wang, Y.; Colomer, A.; Oliver Moll, J.; Zhao, Z.; Naranjo, V. WWFedCBMIR: World-Wide Federated Content-Based Medical Image Retrieval. Bioengineering 2023, 10, 1144. [Google Scholar] [CrossRef] [PubMed]
- Cheng, J.; Yang, W.; Huang, M.; Huang, W.; Jiang, J.; Zhou, Y.; Yang, R.; Zhao, J.; Feng, Y.; Feng, Q.; et al. Retrieval of Brain Tumors by Adaptive Spatial Pooling and Fisher Vector Representation. PLoS ONE 2016, 11, e0157112. [Google Scholar] [CrossRef] [PubMed]
- Silva, W.; Gonçalves, T.; Härmä, K.; Schröder, E.; Obmann, V.C.; Barroso, M.C.; Poellinger, A.; Reyes, M.; Cardoso, J.S. Computer-Aided Diagnosis Through Medical Image Retrieval in Radiology. Sci. Rep. 2022, 12, 20732. [Google Scholar] [CrossRef]
- Owais, M.; Arsalan, M.; Choi, J.; Park, K.R. Effective Diagnosis and Treatment through Content-Based Medical Image Retrieval (CBMIR) by Using Artificial Intelligence. J. Clin. Med. 2019, 8, 462. [Google Scholar] [CrossRef] [PubMed]
- Sharma, S.; Aggarwal, A. A New Approach for Effective Retrieval of Medical Images: A Step towards Computer-Assisted Diagnosis. J. Imaging 2024, 10, 210. [Google Scholar] [CrossRef] [PubMed]
- Zhu, Y.; Yin, X.; Liew, A.W.C.; Tian, H. Privacy-Preserving in Medical Image Analysis: A Review of Methods and Applications. arXiv 2024, arXiv:2412.03924. [Google Scholar]
- Bellafqira, R.; Coatrieux, G.; Bouslimi, D.; Quellec, G. Secure Content Based Image Retrieval in Medical Databases. In Proceedings of the Journées RITS, Dourdan, France, 25–27 March 2015. [Google Scholar]
- Zhang, C.; Li, J.; Wang, S.; Wang, Z. An Encrypted Medical Image Retrieval Algorithm Based on DWT-DCT Frequency Domain. In Proceedings of the 2017 IEEE 15th International Conference on Software Engineering Research, Management and Applications (SERA), London, UK, 7–9 June 2017; pp. 135–141. [Google Scholar] [CrossRef]
- Zhu, D.; Zhu, H.; Wang, X.; Lu, R.; Feng, D. An Accurate and Privacy-Preserving Retrieval Scheme Over Outsourced Medical Images. IEEE Trans. Serv. Comput. 2023, 16, 913–926. [Google Scholar] [CrossRef]
- Li, D.; Wu, Y.; Lü, Q.; Zhang, K.; Wang, Z.; Wu, J. PMIR: An Efficient Privacy-Preserving Medical Images Search in Cloud-Assisted Scenario. Springer Neural Comput. Appl. 2024, 36, 1477–1493. [Google Scholar] [CrossRef]
- Li, D.; Lü, Q.; Liao, X.; Xiang, T.; Wu, J.; Le, J. AVPMIR: Adaptive Verifiable Privacy-Preserving Medical Image Retrieval. IEEE Trans. Dependable Secur. Comput. 2024, 21, 4637–4651. [Google Scholar] [CrossRef]
- Duan, Y.; Li, Y.; Lu, L.; Ding, Y. A Faster Outsourced Medical Image Retrieval Scheme with Privacy Preservation. J. Syst. Archit. 2022, 122, 102356. [Google Scholar] [CrossRef]
- Rajan, A.A.; V, V.; Raikwar, M.; Balaraman, R. SMedIR: Secure Medical Image Retrieval Framework with ConvNeXt-based Indexing and Searchable Encryption in the Cloud. Springer J. Cloud Comput. 2024, 13, 139. [Google Scholar] [CrossRef]
- Feng, Q.; Li, P.; Lu, Z.; Zhou, Z.; Wu, Y.; Weng, J.; Huang, F. DHAN: Encrypted JPEG Image Retrieval via DCT Histograms-Based Attention Networks. Appl. Soft Comput. 2023, 133, 109935. [Google Scholar] [CrossRef]
- Guo, C.; Jia, J.; Choo, K.K.R.; Jie, Y. Privacy-Preserving Image Search (PPIS): Secure Classification and Searching Using Convolutional Neural Network Over Large-Scale Encrypted Medical Images. Comput. Secur. 2020, 99, 102021. [Google Scholar] [CrossRef]
- Cai, G.; Wei, X.; Li, Y. Privacy-Preserving CNN Feature Extraction and Retrieval Over Medical Images. Int. J. Intell. Syst. 2022, 37, 9267–9289. [Google Scholar] [CrossRef]
- Shen, M.; Deng, Y.; Zhu, L.; Du, X.; Guizani, N. Privacy-Preserving Image Retrieval for Medical IoT Systems: A Blockchain-Based Approach. IEEE Netw. 2019, 33, 27–33. [Google Scholar] [CrossRef]
- Ahmad, I.; Kim, J.; Shin, S. A Searchable Encryption Technique for Secure Color Image Retrieval. In Proceedings of the 2024 15th International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 16–18 October 2024; pp. 36–41. [Google Scholar] [CrossRef]
- Iida, K.; Kiya, H. Privacy-Preserving Content-Based Image Retrieval Using Compressible Encrypted Images. IEEE Access 2020, 8, 200038–200050. [Google Scholar] [CrossRef]
- Uzzal, S.M.; Ahmad, I.; Shin, S. Perceptual Encryption-Based Privacy-Preserving Image Retrieval Application. In Proceedings of the 10th International Conference on Next Generation Computing (ICNGC), Angeles City, Philippines, 17–18 December 2024. (in press). [Google Scholar]
- Fan, B.; Wu, F.; Hu, Z. Aggregating Gradient Distributions into Intensity Orders: A Novel Local Image Descriptor. In Proceedings of the CVPR 2011, Colorado Springs, CO, USA, 20–25 June 2011; pp. 2377–2384. [Google Scholar] [CrossRef]
- Perronnin, F.; Liu, Y.; Sánchez, J.; Poirier, H. Large-Scale Image Retrieval with Compressed Fisher Vectors. In Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition, San Francisco, CA, USA, 13–18 June 2010; pp. 3384–3391. [Google Scholar] [CrossRef]
- de Carvalho, R.E.; Leonel, E.D. Squared Sine Logistic Map. Phys. A Stat. Mech. Its Appl. 2016, 463, 37–44. [Google Scholar] [CrossRef]
- Sirichotedumrong, W.; Kinoshita, Y.; Kiya, H. Pixel-Based Image Encryption without Key Management for Privacy-Preserving Deep Neural Networks. IEEE Access 2019, 7, 177844–177855. [Google Scholar] [CrossRef]
- Ahmad, I.; Shin, S. A Pixel-Based Encryption Method for Privacy-Preserving Deep Learning Models. arXiv 2022, arXiv:2203.16780. [Google Scholar]
- Ahmad, I.; Shin, S. Learnable Pixel-Based Encryption for Privacy-Preserving Image Classification. In Proceedings of the Symposium of the Korean Institute of communications and Information Sciences (KICS), Gyeongju, Republic of Korea, 20–22 November 2024; pp. 252–253. [Google Scholar]
- Chang, A.H.; Case, B.M. Attacks on Image Encryption Schemes for Privacy-Preserving Deep Neural Networks. arXiv 2020, arXiv:2004.13263. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).