IoT–Cloud Integration Security: A Survey of Challenges, Solutions, and Directions
Abstract
1. Introduction
2. Background
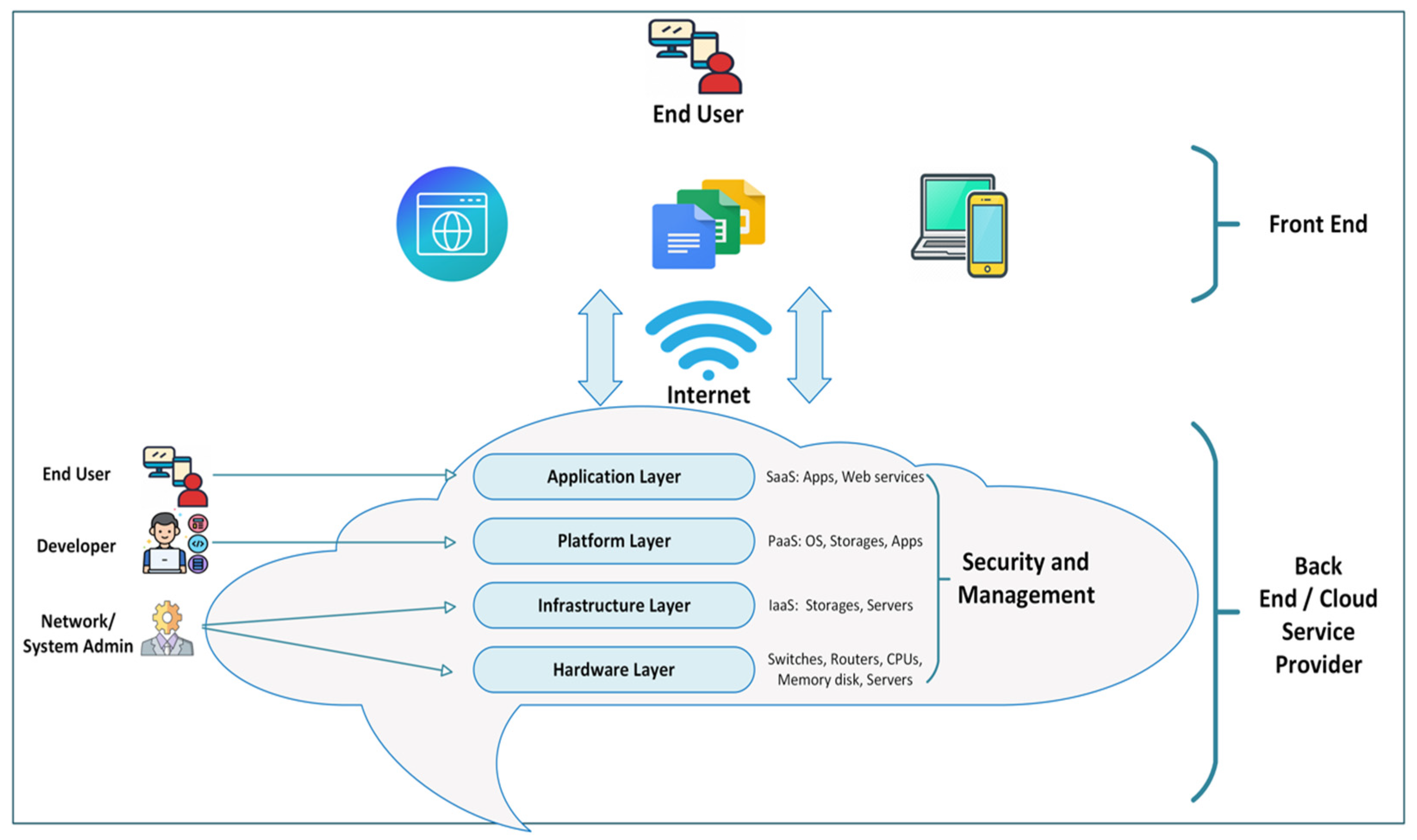
2.1. Cloud Computing Architecture
2.1.1. Cloud Service Models
- (a)
- Infrastructure as a Service (IaaS): Provides virtualized computing resources over the internet and has virtual machines, storage, and networking. Also, it is used for scalable computing resources, data storage, and networking capabilities. IaaS provides virtualized computing resources such as servers and storage that enable utility-like services for users [4].
- (b)
- Platform as a Service (PaaS): Offers hardware and software tools over the internet, which are usually used for application development, including development frameworks, databases, middleware, and development tools. Often, developers use it to build, deploy, and manage applications without dealing with the underlying infrastructure. PaaS offers development environments with APIs and middleware for custom application creation without the need for local configuration [4].
- (c)
- Software as a Service (SaaS): Provides software applications over the internet on a subscription basis. Moreover, it has fully functional software applications and user interfaces. Users can access SaaS applications via a web browser, which includes email services, CRM systems, and collaboration tools. Also, SaaS allows users to access cloud-based software on a subscription or pay-per-use basis [4].
2.1.2. Cloud Deployment Models
- (a)
- A public cloud is a cloud infrastructure that is owned and operated by a third-party cloud service provider that delivers computing resources like servers and storage over the internet. These resources are shared among multiple organizations (tenants).
- (b)
- A private cloud is a cloud infrastructure that is exclusively used by a single organization. It can be hosted on-premises within the organization’s data center or by a third-party provider.
- (c)
- A hybrid cloud is a combination of public and private clouds that allow data and applications to be shared between them. This model offers the benefits of both environments.
- (d)
- A community cloud is shared among several organizations with similar interests or requirements such as compliance and security. It is managed by one or more organizations in the community or by a third-party provider.
2.1.3. Cloud Computing Components
Compute Resources
- Virtualized servers that run on physical hardware, but they are managed independently. Examples include AWS EC2 instances and Azure Virtual Machines;
- Containers that offer lightweight virtualization at the operating system level, providing agility and efficiency compared to traditional virtual machines (VMs) [8];
- Serverless computing, or Function as a Service (FaaS), which enables cost-efficient, rapidly scalable applications without configuration and management overheads [9].
Storage
Networking
- Virtual private clouds (VPCs) are integral components of cloud network architectures that provide isolated virtual network environments within a public cloud infrastructure [15].
- Load balancers distribute incoming traffic across multiple instances to ensure high availability and reliability.
- A content delivery network (CDN) is responsible for distributing content to edge locations around the world to improve performance and reduce latency.
Management and Monitoring
Cloud Security
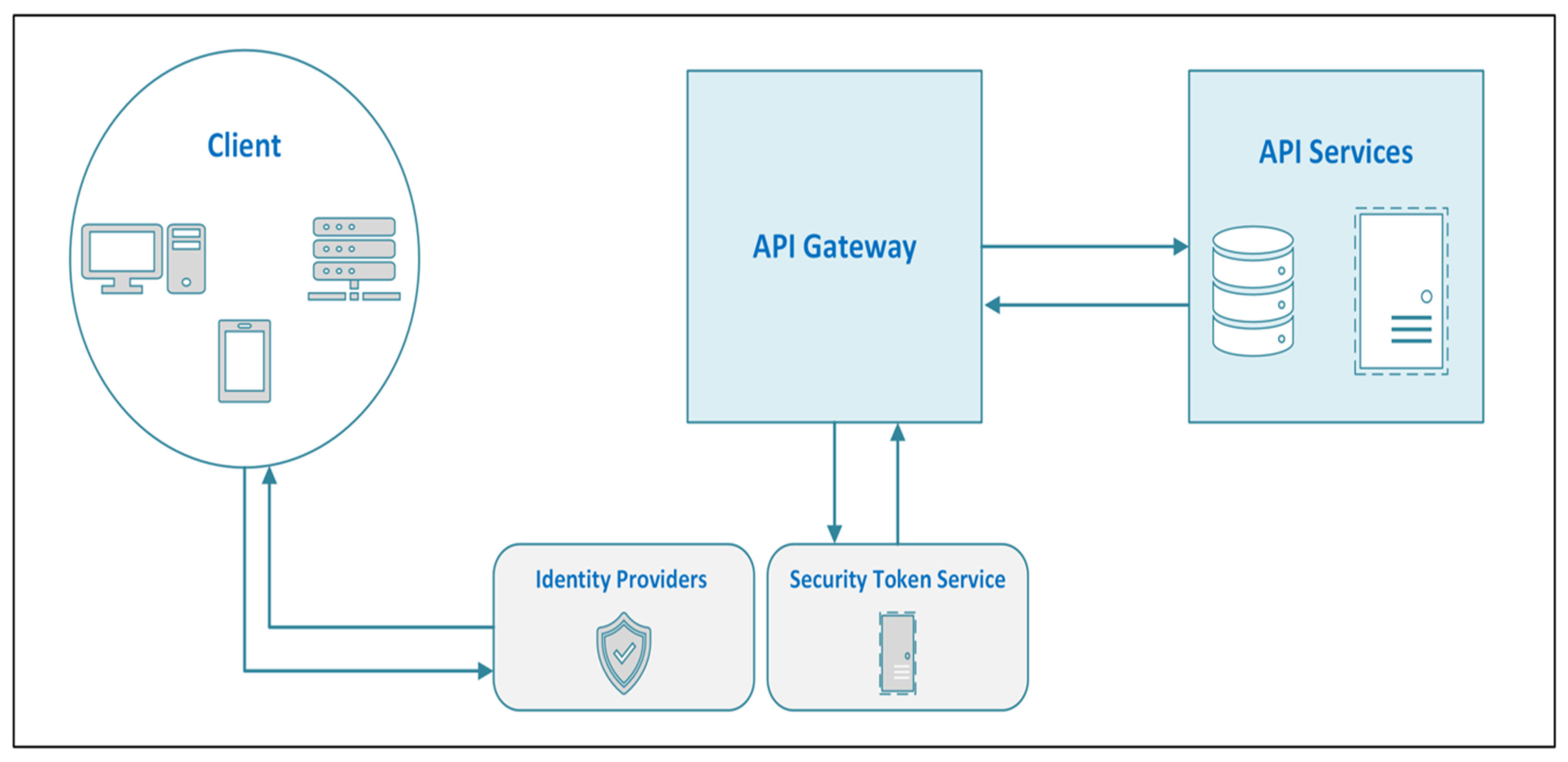
APIs and Interfaces
- In the request phase, the application sends a request to a cloud service through an API. This request can include commands like “get data”, “store data”, or “delete data”.
- In the processing phase, the cloud service receives the request and processes it, and this might involve interacting with databases, computing resources, or other services.
- In the response phase, after processing the request, the cloud service sends a response back to the application via the API, as shown in Figure 2. This response typically includes the requested data or a confirmation of an action taken (like a successful upload).
- In the user interaction phase, the application uses the data or confirmation from the response to update what the user sees, completing the interaction.
2.1.4. Key Cloud Considerations
- (a)
- Scalability
- (b)
- Reliability
- (c)
- Compliance and security
- (d)
- Performance optimization
- (e)
- Integration and interoperability
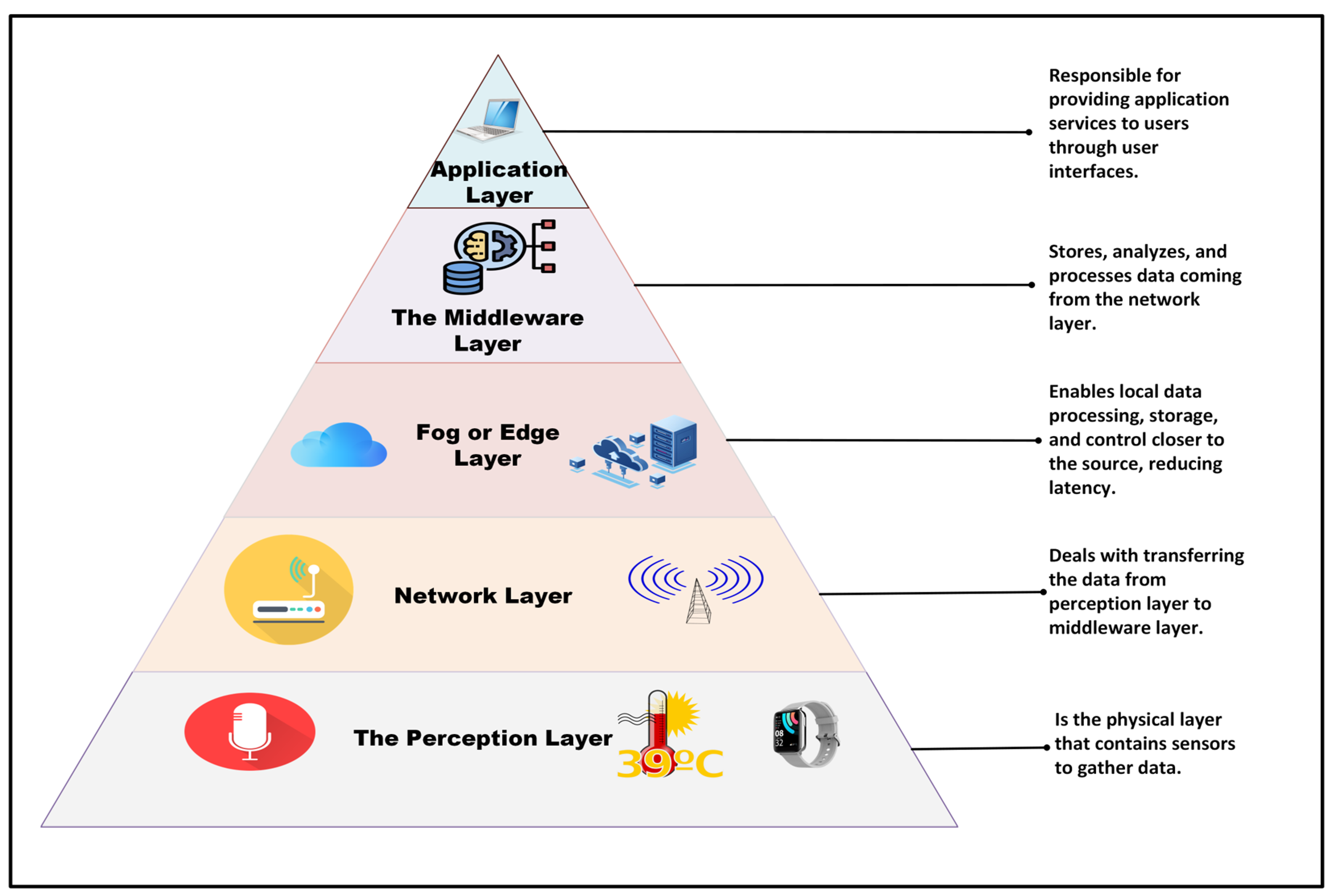
2.2. IoT Architectures
2.2.1. Perception Layer
2.2.2. Network Layer
2.2.3. Edge or Fog Layer
2.2.4. Middleware Layer
2.2.5. Application Layer
- Constrained Application Protocol (CoAP)
- 2.
- Message Queuing Telemetry Transport (MQTT)
- 3.
- Extensible Messaging and Presence Protocol (XMPP)
- 4.
- Data Distribution Service (DDS)
- 5.
- Advanced Message Queuing Protocol (AMQP)
- 6.
- Representational State Transfer (REST)
- 7.
- WebSocket
- 8.
- Java Message Service (JMS)
- Data breaches: Hackers can intercept data being transmitted between devices;
- DoS attacks: Malicious actors overflow the network, which makes services unavailable;
- Unauthorized access: Poor authentication mechanisms can lead to unauthorized users accessing sensitive systems, such as surveillance feeds in a smart city.
3. Related Work
3.1. IoT Security Studies
3.2. Cloud Security Studies
3.3. IoT and Cloud Integration Security Studies
4. Security Threats and Challenges in IoT–Cloud Integration
4.1. Device-Level Challenges
4.2. Network-Level Challenges
4.3. Cloud-Level Challenges
4.4. API and Interface Challenges
4.5. AI and Advanced Threats
- Types of Adversarial AI Attacks
- Evasion Attacks
- 2.
- Poisoning Attacks
- 3.
- Model Inversion Attacks
5. Security Solutions and Mitigation Strategies
5.1. Lightweight Cryptography and Post-Quantum Cryptography for IoT Security
5.1.1. Lightweight Cryptographic Solutions
- Elliptic curve cryptography (ECC), which offers strong security with shorter key sizes, reducing computational overhead while maintaining high levels of protection.
- Lightweight block ciphers
- PRESENT is an ultra-lightweight cipher designed for embedded systems, offering strong encryption with minimal power consumption.
- SIMON and SPECK are a pair of flexible lightweight ciphers optimized for IoT applications, balancing security and performance.
- Lightweight hash functions are cryptographic hash functions optimized for efficiency in IoT devices, ensuring secure data integrity with minimal resource usage.
5.1.2. Post-Quantum Cryptography and the IoT
- NTRU (lattice-based cryptography) is known for its efficiency in resource-constrained environments. NTRU offers a balance between security and computational complexity, making it a possible option for IoT applications [73].
- Crystals–Kyber (NIST-recommended PQC algorithm) is a strong candidate for post-quantum secure IoT networks. It provides efficient key exchange mechanisms while maintaining high security standards [74].
5.2. Blockchain-Based Security Frameworks
5.3. Mitigating Adversarial AI Threats in IoT–Cloud Security
- Countermeasures and Defenses
5.4. Defending Against Replay Attacks in IoT–Cloud Security
- Mitigation Techniques for Replay Attacks
- Nonce-based authentication implements unique, randomly generated values (nonces) for each authentication session, preventing attackers from reusing stopped credentials.
- Timestamp validation enforces strict timestamp-based request validation to ensure that old or replayed messages are automatically rejected [80].
- Secure session codes that use cryptographic session codes that expire after a single use can prevent attackers from exploiting previously valid authentication data [81].
5.5. API Security in IoT–Cloud Integration
- Secure APIs with OAuth 2.0 token-based authentication rather than relying on static API keys;
- Implement API gateways to act as intermediaries, filter out malicious traffic, and enforce security policies;
- Restrict the number of API requests per second to prevent abuse and DoS attacks;
- Use strict input validation to prevent injection attacks and ensure that all API requests use HTTPS encryption.
6. Case Study: IoT–Cloud Security Challenges in Smart Healthcare
6.1. Security Risks in Smart Healthcare
- Data breaches: Unauthorized access to EHRs due to insecure APIs or weak authentication mechanisms can expose sensitive patient information. A comprehensive analysis of healthcare data breaches from 2010 to 2019 revealed that hacking and IT incidents were the most prevalent causes, with a significant increase in recent years [83].
- Replay attacks: Medical IoT devices, such as smart insulin pumps and pacemakers, rely on wireless communication for remote configuration and monitoring. In a replay attack, an attacker intercepts and resends previous commands to manipulate drug dosages or disable life-saving equipment, potentially leading to fatal consequences. Studies have highlighted vulnerabilities in wireless infusion pumps, which could be exploited for malicious purposes [84].
- Adversarial AI attacks: Many smart healthcare systems use AI-driven diagnostic models to detect health conditions based on sensor data. Attackers can manipulate input data (e.g., ECG readings, blood glucose levels) to trick AI models into misdiagnosing conditions, leading to incorrect treatments. Research has shown that adversarial attacks on medical image classification systems can lead to misdiagnoses, posing significant risks to patient safety [85].
6.2. Applied Security Solutions
- Lightweight cryptography: Given the resource constraints of medical IoT devices, lightweight encryption algorithms such as ECC and PRESENT are used to ensure data confidentiality while maintaining low power consumption. Research has identified that IoT healthcare vulnerabilities in both devices and software pose risks to patient safety and system integrity, making lightweight cryptographic solutions critical [84].
- API security measures: Healthcare APIs are secured using OAuth 2.0 authentication, API gateways, and rate limiting to prevent unauthorized data access and DoS attacks. A study emphasizes the need for robust API security measures in healthcare IoT systems to prevent unauthorized access and data breaches [86].
- AI-based IDS: Machine learning models monitor IoT device activity and detect anomalies in data transmission that may indicate an attack, such as replay attempts or adversarial AI manipulations. Therefore, deep learning techniques would be effective in identifying attack patterns and securing IoT healthcare networks.
6.3. Key Findings and Future Directions
7. Discussion and Open Research Challenges
7.1. Evaluation of Current Security Solutions
7.2. IoT–Cloud Integration and Emerging Trends
7.3. Research Gaps and Future Directions
Final Considerations and Future Impact
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| IoT | Internet of Things | AWS | Amazon Web Services |
| GDPR | General data protection regulation | POSIX | Portable operating system interface |
| CI | Critical infrastructure | VPC | Virtual private cloud |
| IaaS | Infrastructure as a service | CDN | Content delivery network |
| PaaS | Platform as a service | SLA | Service level agreement |
| SaaS | Software as a service | MAC | Message authentication code |
| CRM | customer relationship management | SSL | Secure sockets layer |
| VM | Virtual machine | API | Application programming interface |
| FaaS | Function as a service | CLI | Command–line interface |
| QoS | Quality of service | LAN | Local area network |
| RFID | Radio frequency identification | WAN | Wide area network |
| BEDT | Blockchain-enabled distributed trust | 6LoWPAN | IPv6 over low-power wireless Personal area network |
| DoS | Denial of service | FPGA | Field programmable gate array |
| TCP | Transmission control protocol | DNN | Deep neural network |
| UDP | User datagram protocol | IIoT | Industrial Internet of Things |
| IAM | Identity and access management | AI | Artificial intelligence |
| SOC | Security operations center | MSTP | Master–slave/token-passing |
| RPM | Remote patient monitoring | EHR | Electronic health record |
| ECC | Elliptic curve cryptography | PQC | Post-quantum cryptography |
| IDS | Intrusion detection system | XAI | Explainable AI |
| MFA | Multi-factor authentication | XSS | Cross-site scripting |
| D2D | Device-to-device | RCE | Remote code execution |
| AMLS | Multi-layer security | SDN | Software-defined networking |
| DDoS | Distributed DoS |
References
- Sutikno, T.; Thalmann, D. Insights on the internet of things: Past, present, and future directions. TELKOMNIKA (Telecommun. Comput. Electron. Control) 2022, 20, 1399–1420. [Google Scholar] [CrossRef]
- Tawalbeh, L.A.; Muheidat, F.; Tawalbeh, M.; Quwaider, M. IoT Privacy and Security: Challenges and Solutions. Appl. Sci. 2020, 10, 4102. [Google Scholar] [CrossRef]
- Marco, G.D. Privacy Risk in the IoT Environment: The Need for a Multiple Approach According to the GDPR Principles. In Proceedings of the INTERNET 2019: The Eleventh International Conference on Evolving Internet, Rome, Italy, 30 June–4 July 2019. [Google Scholar]
- Gibson, J.; Rondeau, R.; Eveleigh, D.; Tan, Q. Benefits and challenges of three cloud computing service models. In Proceedings of the 2012 Fourth International Conference on Computational Aspects of Social Networks (CASoN), Sao Carlos, Brazil, 21–23 November 2012; pp. 198–205. [Google Scholar]
- Patel, H.B.; Kansara, N. Cloud Computing Deployment Models: A Comparative Study. Int. J. Innov. Res. Comput. Sci. Technol. 2021, 9, 45–47. [Google Scholar] [CrossRef]
- Tanque, M. Cloud-Based Platforms and Infrastructures. In Cloud Security: Concepts, Methodologies, Tools, and Applications; Information Resources Management Association, Ed.; IGI Global: Hershey, PA, USA, 2019; pp. 84–126. [Google Scholar] [CrossRef]
- Parsi, K. A Comparative Study of Different Deployment Models in a Cloud. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2013, 3, 512–515. [Google Scholar]
- Mavridis, I.; Karatza, H.D. Orchestrated sandboxed containers, unikernels, and virtual machines for isolation-enhanced multitenant workloads and serverless computing in cloud. Concurr. Comput. Pract. Exp. 2021, 35, e6365. [Google Scholar] [CrossRef]
- Lynn, T.; Rosati, P.; Lejeune, A.; Emeakaroha, V. A Preliminary Review of Enterprise Serverless Cloud Computing (Function-as-a-Service) Platforms. In Proceedings of the 2017 IEEE International Conference on Cloud Computing Technology and Science (CloudCom), Hong Kong, China, 11–14 December 2017; pp. 162–169. [Google Scholar]
- Jain, P.; Munjal, Y.; Gera, J.; Gupta, P. Performance Analysis of Various Server Hosting Techniques. Procedia Comput. Sci. 2020, 173, 70–77. [Google Scholar] [CrossRef]
- Eyk, E.; Iosup, A.; Grohmann, J.; Eismann, S.; Bauer, A.; Versluis, L.; Toader, L.; Schmitt, N.; Herbst, N.; Abad, C. The SPEC-RG Reference Architecture for FaaS: From Microservices and Containers to Serverless Platforms. IEEE Internet Comput. 2019, 23, 7–18. [Google Scholar]
- Bala, R.; Chandrasekaran, A.; McArthur, J. Magic Quadrant for Public Cloud Storage Services, Worldwide. 2017. Available online: https://winpro.com.sg/wp-content/uploads/2017/01/Magic-Quadrant-for-Public-Cloud-Storage-Services-Worldwide-24-July-2017.pdf (accessed on 25 March 2025).
- Armoogum, S.; Khonje, P. Healthcare Data Storage Options Using Cloud. In Internet of Things; Springer: Cham, Switzerland, 2021. [Google Scholar]
- Chung, L.; Lee, C.; Chou, J.C. Dynamic Block Partitioning Strategy for Cloud-Backed File Systems. In Proceedings of the 2016 IEEE International Conference on Cloud Computing Technology and Science (CloudCom), Luxembourg, 12–15 December 2016; pp. 253–260. [Google Scholar]
- Hu, Z.; Zhang, H.; Sun, S.; Gao, C.; Li, Y.; Li, X. FDRA: Fully Distributed Routing Architecture for Private Virtual Network in Public Cloud. In Proceedings of the International Symposium on Parallel Architectures, Algorithms and Programming, Shenzhen, China, 28–30 December 2020. [Google Scholar]
- Moharana, S. Analysis of load balancers in cloud computing. Int. J. Comput. Sci. Eng. 2013, 2, 101–108. [Google Scholar]
- Um, T.W.; Lee, H.; Ryu, W.; Choi, J. Dynamic Resource Allocation and Scheduling for Cloud-Based Virtual Content Delivery Networks. ETRI J. 2014, 36, 197–205. [Google Scholar]
- Zahariadis, T.; Papadakis, A.; Alvarez, F.; Gonzalez, J.; Lopez, F.; Facca, F.; Al-Hazmi, Y. FIWARE Lab: Managing Resources and Services in a Cloud Federation Supporting Future Internet Applications. In Proceedings of the 2014 IEEE/ACM 7th International Conference on Utility and Cloud Computing, London, UK, 8–11 December 2014; pp. 792–799. [Google Scholar]
- Zhang, X.; Du, H.; Chen, J.; Lin, Y.; Zeng, L. Ensure Data Security in Cloud Storage. In Proceedings of the 2011 International Conference on Network Computing and Information Security, Guilin, China, 14–15 May 2011; Volume 1, pp. 284–287. [Google Scholar]
- Sood, S.K. A combined approach to ensure data security in cloud computing. J. Netw. Comput. Appl. 2012, 35, 1831–1838. [Google Scholar]
- Waghchaude, K.G. A Review on Cloud Computing Security Issues, Applicable Solutions and Implementation. Int. J. Sci. Res. Eng. Manag. 2024, 8, 1–3. [Google Scholar] [CrossRef]
- Pal, S.; Khatua, S.; Chaki, N.; Sanyal, S. A New Trusted and Collaborative Agent Based Approach for Ensuring Cloud Security. arXiv 2011, arXiv:1108.4100. [Google Scholar]
- Gunjan, K.; Tiwari, R.; Sahoo, G. Towards Securing APIs in Cloud Computing. arXiv 2013, arXiv:1307.6649. [Google Scholar]
- Odun-Ayo, I.; Okereke, C.; Evwieroghene, O. Cloud and Application Programming Interface—Issues and Developments. In Proceedings of the World Congress on Engineering, London, UK, 4–6 July 2018. [Google Scholar]
- Katsaros, G.; Cucinotta, T. Programming Interfaces for Realtime and Cloud-Based Computing. In Achieving Real-Time in Distributed Computing; IGI Global Scientific Publishing: Hershey, PA, USA, 2012. [Google Scholar]
- Sill, A. When to Use Standards-Based APIs (Part 2). IEEE Cloud Comput. 2015, 2, 80–84. [Google Scholar] [CrossRef]
- Coleman, C.; Griswold, W.; Mitchell, N. Do Cloud Developers Prefer CLIs or Web Consoles? CLIs Mostly, Though It Varies by Task. arXiv 2022, arXiv:2209.07365. [Google Scholar]
- Taher, H. Harnessing the Power of Distributed Systems for Scalable Cloud Computing A Review of Advances and Challenges. Indones. J. Comput. Sci. 2024, 13, 1750–1769. [Google Scholar] [CrossRef]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A Survey of IoT Security Based on a Layered Architecture of Sensing and Data Analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef]
- Wang, H.; Sun, Z.; Chen, S. A novel real-time method for moving vehicle detection. J. Internet Technol. 2016, 17, 1501–1509. [Google Scholar]
- Wu, C.K. IoT Perception Layer Security. In Internet of Things Security. Advances in Computer Science and Technology; Springer: Singapore, 2021. [Google Scholar] [CrossRef]
- Bello, O.; Zeadally, S.; Badra, M. Network layer inter-operation of Device-to-Device communication technologies in Internet of Things (IoT). Ad Hoc Netw. 2017, 57, 52–62. [Google Scholar] [CrossRef]
- Khan, J.Y.; Yuce, M.R. (Eds.) Internet of Things (IoT): Systems and Applications, 1st ed.; Jenny Stanford Publishing: New York, NY, USA, 2019. [Google Scholar] [CrossRef]
- Hussain, B.; Elmedany, W.; Sharif, S. The Internet of Things Security Issues and Countermeasures in Network Layer: A Systematic Literature Review. In Proceedings of the 2022 International Conference on Data Analytics for Business and Industry (ICDABI), Virtual, 25–26 October 2022; pp. 787–793. [Google Scholar]
- Zaib, M.; Reegu, F.; Dar, A.; Bhat, W. Recent Privacy and Security Issues in Internet of Things Network Layer: A Systematic Review. In Proceedings of the 2022 International Conference on Sustainable Computing and Data Communication Systems (ICSCDS), Erode, India, 7–9 April 2022; pp. 1025–1031. [Google Scholar]
- Chiang, M.; Zhang, T. Fog and IoT: An Overview of Research Opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Trivedi, U.; Sanghavi, F.; Nguyen, S.; Salcic, Z. Predicting Parking Occupancy in Real-time Using Fog Layer Hosted DNN Implemented in FPGA. In Proceedings of the 2021 IEEE International Conference on Artificial Intelligence and Computer Applications (ICAICA), Dalian, China, 28–30 June 2021; pp. 345–352. [Google Scholar]
- Fersi, G. Middleware for Internet of Things: A Study. In Proceedings of the 2015 International Conference on Distributed Computing in Sensor Systems, Fortaleza, Brazil, 10–12 June 2015; pp. 230–235. [Google Scholar]
- Chaqfeh, M.; Mohamed, N. Challenges in middleware solutions for the internet of things. In Proceedings of the 2012 International Conference on Collaboration Technologies and Systems (CTS), Denver, CO, USA, 21–25 May 2012; pp. 21–26. [Google Scholar]
- Amaral, L.A.; Matos, E.D.; Tiburski, R.T.; Hessel, F.; Lunardi, W.T.; Marczak, S. Middleware Technology for IoT Systems: Challenges and Perspectives Toward 5G. In Internet of Things (IoT) in 5G Mobile Technologies; Springer: Cham, Switzerland, 2016. [Google Scholar]
- Bani Yassein, M.; Shatnawi, M.; Al-Zoubi, D. Application layer protocols for the Internet of Things: A survey. In Proceedings of the 2016 International Conference on Engineering & MIS (ICEMIS), Agadir, Morocco, 22–24 September 2016; pp. 1–4. [Google Scholar]
- Tayur, V.M.; Suchithra, R. Review of interoperability approaches in application layer of Internet of Things. In Proceedings of the 2017 International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), Bengaluru, India, 21–23 February 2017; pp. 322–326. [Google Scholar]
- Ferdows, J.; Mehedi, S.; Hossain, A.; Shamim, A.; Rasiq, G.M.; Rasiqul, I. A Comprehensive Study of IoT Application Layer Security Management. In Proceedings of the 2020 IEEE International Conference for Innovation in Technology (INOCON), Bangaluru, India, 6–8 November 2020; pp. 1–7. [Google Scholar]
- Imran, S.M.A.; Alam, M.M.; Su’ud, M. A Survey of IoT Security Issues—From Past to Future Trends. J. Comput. Sci. 2021, 17, 1031–1045. [Google Scholar] [CrossRef]
- Tan, S.F.; Samsudin, A. Recent Technologies, Security Countermeasure and Ongoing Challenges of Industrial Internet of Things (IIoT): A Survey. Sensors 2021, 21, 6647. [Google Scholar] [CrossRef] [PubMed]
- Hossain, M.M.; Kayas, G.; Hasan, R.; Skjellum, A.; Noor, S.A.; Islam, S.M. A Holistic Analysis of Internet of Things (IoT) Security: Principles, Practices, and New Perspectives. Future Internet 2024, 16, 40. [Google Scholar] [CrossRef]
- Pannayagol, B.B.; Deshpande, S. Security in Internet of Things: An Overview. In Proceedings of the 2023 International Conference on Device Intelligence, Computing and Communication Technologies, (DICCT), Dehradun, India, 17–18 March 2023; pp. 243–248. [Google Scholar]
- Şen, E.; Dash, E.A. Unveiling the Shadows: Exploring the Security Challenges of the Internet of Things (IoT). Int. J. Sci. Res. Eng. Manag. 2023, 7, 1–12. [Google Scholar]
- Kabir, M.; Elmedany, W.; Sharif, S. Securing IoT Devices Against Emerging Security Threats: Challenges and Mitigation Techniques. J. Cyber Secur. Technol. 2023, 7, 199–223. [Google Scholar] [CrossRef]
- Dritsas, E.; Trigka, M. A Survey on Cybersecurity in IoT. Future Internet 2025, 17, 30. [Google Scholar] [CrossRef]
- Tiwari, A.R. Securing the Cloud: Overcoming Challenges and Implementing Solutions for Effective Cloud Computing Security. Int. J. Res. Appl. Sci. Eng. Technol. 2024, 12, 5100–5110. [Google Scholar] [CrossRef]
- Aijaz, U.; Abubakar, M.; Reddy, A.; Pujari, A.C. An Analysis on Security Issues and Research Challenges in Cloud Computing. J. Secur. Comput. Netw. Distrib. Syst. 2024, 1, 37–44. [Google Scholar] [CrossRef]
- Surya, K.; Nivedithaa, M.; Uma, S.; Valliyammai, C. Security issues and challenges in cloud. In Proceedings of the 2013 International Conference on Green Computing, Communication and Conservation of Energy (ICGCE), Chennai, India, 12–14 December 2013; pp. 889–893. [Google Scholar]
- Mallisetty, S.B.; Devineni, P.; Tripuramallu, G.A.; Kavitha, D.S.; Kamada, K.; Venkata, D.A.; Krishna, P. A Review on Cloud Security and Its Challenges. In Proceedings of the 2023 International Conference on Intelligent Data Communication Technologies and Internet of Things (IDCIoT), Bengaluru, India, 5–7 January 2023; pp. 798–804. [Google Scholar]
- Chaudhari, A.R.; Gohil, B.N.; Rao, U.P. A review on cloud security issues and solutions. J. Comput. Secur. 2022, 31, 365–391. [Google Scholar] [CrossRef]
- Alghofaili, Y.; Albattah, A.; Alrajeh, N.; Rassam, M.A.; Al-rimy, B.A. Secure Cloud Infrastructure: A Survey on Issues, Current Solutions, and Open Challenges. Appl. Sci. 2021, 11, 9005. [Google Scholar] [CrossRef]
- Alenizi, B.A.; Humayun, M.; Jhanjhi, N.Z. Security and Privacy Issues in Cloud Computing. J. Phys. Conf. Ser. 2021, 1979, 012038. [Google Scholar]
- Singh, N. Cloud Computing Security Issues. Int. J. Res. Appl. Sci. Eng. Technol. 2024, 12, 2295–2298. [Google Scholar]
- Kulsoom, U.; Nasim, S.F.; Qaiser, A.; Aziz, S.; Fatima, S.A. A Review about Internet of Things (IoT) integration with Cloud Computing with a Limelight on Security. Pak. J. Eng. Technol. 2024, 6, 1–6. [Google Scholar] [CrossRef]
- Surianarayanan, C.; Chelliah, P.R. Integration of the Internet of Things and Cloud: Security Challenges and Solutions—A Review. Int. J. Cloud Appl. Comput. 2023, 13, 1–30. [Google Scholar]
- Bazgir, E.; Haque, E.; Sharif, N.B.; Ahmed, M.F. Security aspects in IoT based cloud computing. World J. Adv. Res. Rev. 2023, 20, 540–551. [Google Scholar]
- Ferencz, K.; Domokos, J.; Kovács, L. Cloud Integration of Industrial IoT Systems. Architecture, Security Aspects and Sample Implementations. Acta Polytech. Hung. 2024, 21, 7–28. [Google Scholar] [CrossRef]
- Shaukat, K.; Alam, T.M.; Hameed, I.A.; Khan, W.A.; Abbas, N.; Luo, S. A Review on Security Challenges in Internet of Things (IoT). IEEE Access 2021, 9, 168475–168496. Available online: https://ieeexplore.ieee.org/abstract/document/9594183 (accessed on 16 March 2025).
- Abdur Razzaq, M.; Habib, S.; Ali, M.; Ullah, S. Security Issues in the Internet of Things (IoT): A Comprehensive Study. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 383–388. [Google Scholar] [CrossRef]
- Alotaibi, B. Utilizing Blockchain to Overcome Cyber Security Concerns in the Internet of Things: A Review. IEEE Sens. J. 2019, 19, 10953–10971. [Google Scholar] [CrossRef]
- Kamucheka, T.; Fahr, M.; Teague, T.; Nelson, A.; Andrews, D.; Huang, M. Power-based Side Channel Attack Analysis on PQC Algorithms. IACR Cryptol. ePrint Arch. 2021, 2021, 1021. [Google Scholar]
- Lazzaro, S.; Angelis, V.D.; Mandalari, A.M.; Buccafurri, F. Is Your Kettle Smarter Than a Hacker? A Scalable Tool for Assessing Replay Attack Vulnerabilities on Consumer IoT Devices. In Proceedings of the 2024 IEEE International Conference on Pervasive Computing and Communications (PerCom), Biarritz, France, 11–15 March 2024; pp. 114–124. [Google Scholar]
- Kamruzzaman, A.; Thakur, K.; Ali, M.L. Cybersecurity Threats using Application Programming Interface (API). In Proceedings of the 2024 International Conference on Computing, Internet of Things and Microwave Systems (ICCIMS), Gatineau, QC, Canada, 29–31 July 2024; pp. 1–6. [Google Scholar]
- Hussain, F.; Noye, B.; Sharieh, S. Current state of API security and machine learning. IEEE Technol. Policy Ethics 2019, 4, 1–5. [Google Scholar] [CrossRef]
- Altayaran, S.A.; Elmedany, W.M. Security threats of application programming interface (API’s) in internet of things (IoT) communications. In Proceedings of the 4th Smart Cities Symposium (SCS 2021), Online, 21–23 November 2021. [Google Scholar]
- Pauling, C.; Gimson, M.; Qaid, M.; Kida, A.; Halak, B. A Tutorial on Adversarial Learning Attacks and Countermeasures. arXiv 2022, arXiv:2202.10377. [Google Scholar]
- Karthik, S.; Rengarajan, A. Advancing IoT Security: A Comprehensive Survey of Lightweight Cryptography Solutions. IJARCCE 2024, 13, 91–94. [Google Scholar] [CrossRef]
- Kumari, S.; Singh, M.P.; Singh, R.; Tewari, H. Post-quantum cryptography techniques for secure communication in resource-constrained Internet of Things devices: A comprehensive survey. Softw. Pract. Exp. 2022, 52, 2047–2076. [Google Scholar] [CrossRef]
- Liao, Q.; He, L. Lightweight key generation circuits for CRYSTALS-Kyber. In Proceedings of the 2024 3rd International Conference on Electronics and Information Technology (EIT), Chengdu, China, 20–22 September 2024; pp. 209–213. [Google Scholar]
- Jadhav, S.B. Blockchain in IOT Security. Int. J. Res. Appl. Sci. Eng. Technol. 2024, 12, 1074–1077. [Google Scholar] [CrossRef]
- Srinivas, C. Innovative Security Frameworks for IOT and Cloud Computing Integration: Challenges and Solutions. Int. J. Innov. Res. Sci. Eng. Technol. 2015, 4, 9535–9543. [Google Scholar] [CrossRef]
- Medhane, D.V.; Sangaiah, A.K.; Hossain, M.S.; Muhammad, G.; Wang, J. Blockchain-Enabled Distributed Security Framework for Next-Generation IoT: An Edge Cloud and Software-Defined Network-Integrated Approach. IEEE Internet Things J. 2020, 7, 6143–6149. [Google Scholar] [CrossRef]
- Albshaier, L.; Budokhi, A.; Aljughaiman, A. A Review of Security Issues When Integrating IoT With Cloud Computing and Blockchain. IEEE Access 2024, 12, 109560–109595. [Google Scholar] [CrossRef]
- Thalpage, N. Unlocking the Black Box: Explainable Artificial Intelligence (XAI) for Trust and Transparency in AI Systems. J. Digit. Art Humanit. 2023, 4, 31–36. [Google Scholar] [CrossRef]
- Farha, F.; Ning, H.; Yang, S.; Xu, J.; Zhang, W.; Choo, K.R. Timestamp Scheme to Mitigate Replay Attacks in Secure ZigBee Networks. IEEE Trans. Mob. Comput. 2022, 21, 342–351. [Google Scholar] [CrossRef]
- Arora, S.; Hussain, M. Secure Session Key Sharing Using Symmetric Key Cryptography. In Proceedings of the 2018 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Bangalore, India, 19–22 September 2018; pp. 850–855. [Google Scholar]
- Kumar, N.A.A.; Tl, N.D. Security measures implemented in RESTful API Development. Open Access Res. J. Eng. Technol. 2024, 7, 105–112. [Google Scholar] [CrossRef]
- Seh, A.H.; Zarour, M.; Alenezi, M.; Sarkar, A.K.; Agrawal, A.; Kumar, R.; Khan, R.A. Healthcare Data Breaches: Insights and Implications. Healthcare 2020, 8, 133. [Google Scholar] [CrossRef] [PubMed]
- Mejía-Granda, C.M.; Fernández-Alemán, J.L.; Carrillo-de-Gea, J.M.; García-Berná, J.A. Security vulnerabilities in healthcare: An analysis of medical devices and software. Med. Biol. Eng. Comput. 2024, 62, 257–273. [Google Scholar] [CrossRef]
- Tsai, M.J.; Lin, P.Y.; Lee, M.E. Adversarial Attacks on Medical Image Classification. Cancers 2023, 15, 4228. [Google Scholar] [CrossRef]
- Al-Rumaim, A.; Pawar, J.D. Exploring the Evolving Landscape of API Security Challenges in the Healthcare Industry: A Comprehensive Review. In Proceedings of the 2023 16th International Conference on Security of Information and Networks (SIN), Jaipur, India, 20–21 November 2023; pp. 1–8. [Google Scholar]
- Burke, W.; Stranieri, A.; Oseni, T.; Gondal, I. The need for cybersecurity self-evaluation in healthcare. BMC Med. Inform. Decis. Mak. 2024, 24, 133. [Google Scholar] [CrossRef]
- Li, S.; Chen, Y.; Chen, L.; Liao, J.; Kuang, C.; Li, K.; Liang, W.; Xiong, N. Post-Quantum Security: Opportunities and Challenges. Sensors 2023, 23, 8744. [Google Scholar] [CrossRef] [PubMed]
- Sarkar, S.; Choudhary, G.; Shandilya, S.K.; Hussain, A.; Kim, H. Security of Zero Trust Networks in Cloud Computing: A Comparative Review. Sustainability 2022, 14, 11213. [Google Scholar] [CrossRef]
- Pais, M.S.; FayizAhamed, K.; Raghavendra, G.; GowthamiK, M.; Suvarna, J.N. Adoption of Blockchain in IoT: Challenges and Solutions. Int. J. Adv. Res. Sci. Commun. Technol. 2022, 2, 294–302. [Google Scholar] [CrossRef]
- Murugan, G.; Chinnadurai, M. ESHA-256_GBGO: A high-performance and optimized security framework for internet of medical thing. Sci. Rep. 2025, 15, 9576. [Google Scholar] [CrossRef]
| Protocol | Transport | QoS | Architecture | Security |
|---|---|---|---|---|
| CoAP | UDP | Yes | Request/response | DTLS |
| MQTT | TCP | Yes | Publish/subscribe | TLS/SSL |
| XMPP | TCP | No | Request/response Publish/subscribe | TLS/SSL |
| DDS | TCP/ UDP | Yes | Publish/subscribe | TLS/SSL |
| AMQP | TCP | Yes | Publish/subscribe | TLS/SSL |
| REST | HTTP | No | Request/response | HTTPS |
| WebSocket | TCP | No | Publish/subscribe Client/server | TLS/SSL |
| JMS | MSTP | Yes | Client/server Request/response | SSL |
| Authors | Focus Area | Key Contributions | Limitations/Gaps | How Our Paper Improves |
|---|---|---|---|---|
| Tawalbeh et al. (2020) [2] | IoT risk security | Discusses data breaches, insecure APIs | Lacks coverage on IoT–cloud security integration | Analyzes IoT–cloud security holistically, including API security and replay attacks |
| Marco (2019) [3] | IoT privacy concerns | Covers GDPR compliance issues | Lacks discussion of post-quantum cryptography (PQC) risks | Explores PQC challenges and integration with IoT–cloud systems |
| Gibson et al. (2012) [4] | Cloud security risks | Covers IAM and insider threats | Ignores IoT-specific vulnerabilities | Discusses the integration of IAM with IoT–cloud-specific security threats |
| Sood (2012) [20] | Cloud data security | Discusses SSL, MAC-based integrity checks | Lacks zero-trust security and homomorphic encryption | Introduces lightweight cryptography for constrained IoT devices |
| Hussain et al. (2022) [34] | IoT network security | Analyzes DDoS, routing issues | Lacks discussion of API security concerns | Proposes API security best practices and lightweight cryptography |
| Alotaibi (2019) [65] | Blockchain in IoT | Focuses on decentralized trust | Lacks API security and multi-tenancy discussions | Explores blockchain-enhanced authentication tailored for IoT–cloud integration |
| Singh (2024) [58] | Cloud multi-tenancy risks | Covers virtualization security | Lacks discussion of adversarial AI and replay attacks | Analyzes adversarial AI threats in IoT–cloud systems and proposes mitigation strategies based on AI resilience techniques |
| Wang et al. (2016) [30] | IoT data processing | Discusses edge computing and secure APIs | Ignores API rate limiting and secure gateways | Analyzes API security gaps and proposes enhanced API gateway protections |
| Bello et al. (2017) [32] | IoT communication security | Covers authentication protocols | Lacks IoT–cloud-specific threats | Integrates device-to-cloud security mechanisms |
| Chiang and Zhang (2016) [36] | Fog computing security | Discusses latency and encryption | Lacks discussion of adversarial AI risks | Analyzes adversarial AI threats in IoT–cloud systems and proposes mitigation strategies based on AI resilience techniques |
| Alam et al. (2022) [35] | IoT data privacy | Covers encryption and privacy techniques | Lacks a focus on PQC and emerging cryptographic risks | Explores PQC integration for IoT–cloud privacy |
| Dritsas and Trigka (2025) [50] | Cybersecurity in IoT | Detailed survey on IoT cybersecurity and emerging threats | Lacks dedicated IoT–cloud integration and PQC discussions | Integrates IoT–cloud security, including PQC, API security, and adversarial AI threats |
| Tawalbeh et al. (2020) [2] | IoT privacy and security | Comprehensive IoT security and privacy overview | Cloud security integration gaps and emerging threats not covered clearly | Explores cloud integration and emerging threats |
| Shaukat et al. (2021) [63] | Security challenges in the IoT | Detailed analysis of IoT-specific threats | Limited discussion on IoT–cloud integration and adversarial AI | Provides detailed coverage of IoT–cloud security and adversarial AI |
| Abdur et al. (2021) [64] | Comprehensive IoT security | Broad IoT security survey | Lacks adequate discussion of PQC and API security | Provides integration of comprehensive API and PQC solutions |
| Risks | Existing Solutions | Future Research Directions |
|---|---|---|
| Data privacy and confidentiality in multi-tenant cloud environments | IAM, MFA, blockchain-based identity management | Developing adaptive IAM systems with AI-based anomaly detection, enhancing cross-tenant data isolation |
| Weak authentication and API security Vulnerabilities | OAuth 2.0, API gateways, rate limiting, secure session management | Strengthening API authentication with AI-driven anomaly detection, enhancing zero-trust API security models |
| Scalability challenges in lightweight cryptography | ECC and lightweight block ciphers (PRESENT, SIMON and SPECK) | Hybrid cryptographic models for large-scale IoT |
| Adversarial AI threats in IoT–Cloud security | Adversarial training, XAI, robust AI models (ensemble learning, defensive distillation) | Integrating robust adversarial AI models with blockchain for secure and tamper-proof AI-driven security |
| Replay attacks on IoT communication channels | Nonce-based authentication, timestamp validation, cryptographic session tokens | Improving real-time secure session management and adaptive authentication for IoT–cloud systems |
| Blockchain scalability for real-time IoT applications | Optimized blockchain consensus mechanisms (proof-of-authority, DAG-based blockchain) | Developing scalable blockchain solutions with low-latency transaction validation for time-sensitive IoT applications |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almutairi, M.; Sheldon, F.T. IoT–Cloud Integration Security: A Survey of Challenges, Solutions, and Directions. Electronics 2025, 14, 1394. https://doi.org/10.3390/electronics14071394
Almutairi M, Sheldon FT. IoT–Cloud Integration Security: A Survey of Challenges, Solutions, and Directions. Electronics. 2025; 14(7):1394. https://doi.org/10.3390/electronics14071394
Chicago/Turabian StyleAlmutairi, Mohammed, and Frederick T. Sheldon. 2025. "IoT–Cloud Integration Security: A Survey of Challenges, Solutions, and Directions" Electronics 14, no. 7: 1394. https://doi.org/10.3390/electronics14071394
APA StyleAlmutairi, M., & Sheldon, F. T. (2025). IoT–Cloud Integration Security: A Survey of Challenges, Solutions, and Directions. Electronics, 14(7), 1394. https://doi.org/10.3390/electronics14071394







