Requirements Engineering Approach for Data Ownership Concepts
Abstract
:1. Introduction
2. Materials and Methods
2.1. Requirements Engineering
- Understanding of the domain and the problem;
- Understanding of organizational context;
- Understanding the technical context;
- Understanding the legal aspect surrounding the problem;
- Defining the stakeholders involved in the process;
- Understanding the current state, including its strengths and weaknesses.
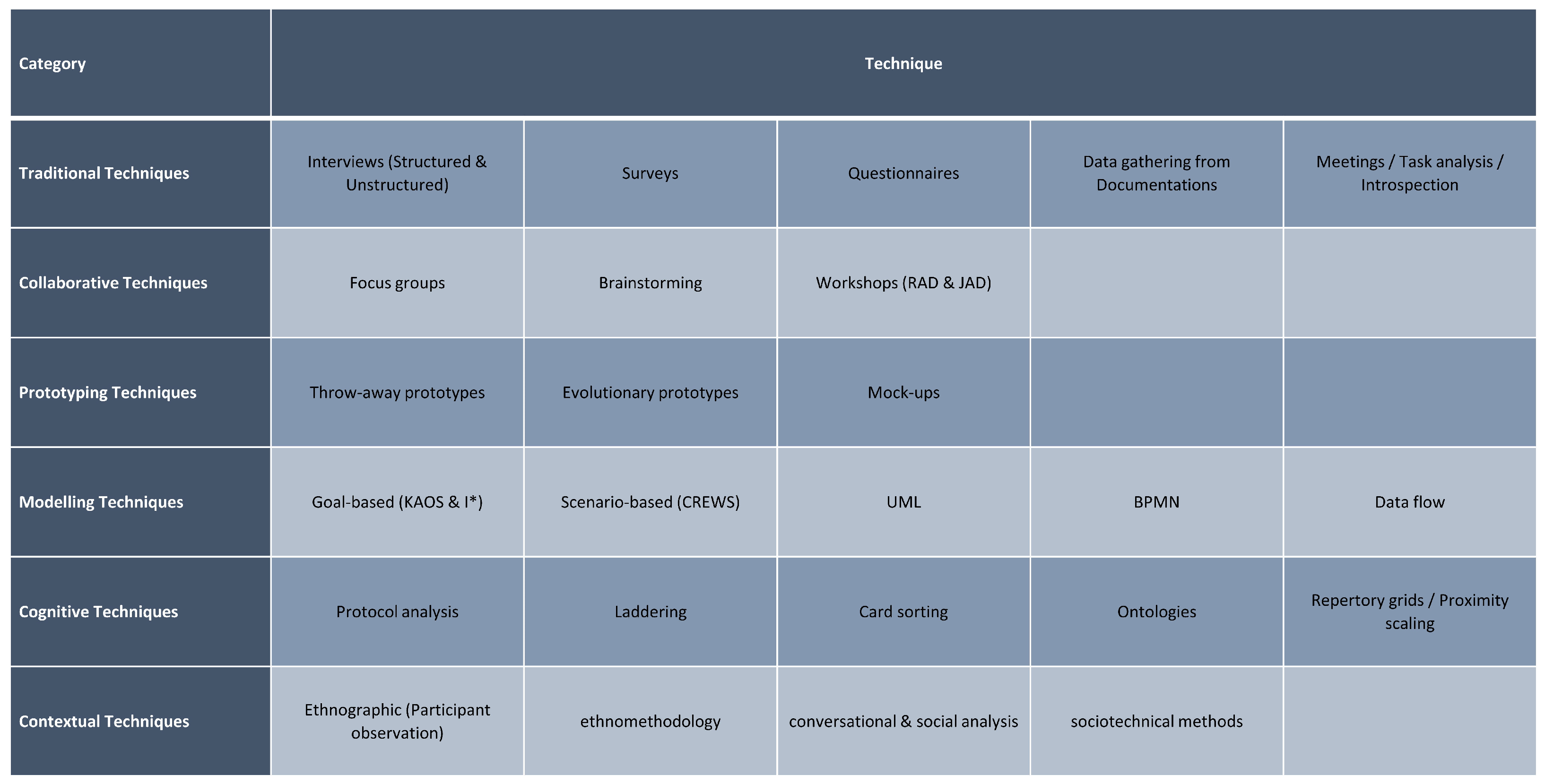
- Traditional techniques:As the name suggests, this category includes basic and traditional techniques that collect generic data. Generally, this category includes techniques such as interviews in both structured and unstructured forms, surveys, questionnaires, and data collection from existing documentation [11,15,16]. Some of the literature also includes other methods such as meetings, task analysis, and introspection. Introspection can be useful when there is a lack of answers and feedback; the requirements analyst may then need to imagine what kind of requirements are needed [9].
- Collaborative or group elicitation techniques:These techniques aim to achieve a better understanding of the requirements by gaining the agreement of the stakeholders, users, and the team involved in the process. They also help to prioritize the necessary requirements. This category includes techniques such as focus groups, brainstorming, and workshops such as Rapid Application Development (RAD) and Joint Application Development (JAD) [9,11,15,16].
- Prototyping techniques:A prototype can be used in the elicitation process when there is uncertainty about the requirements and feedback is needed. It can also serve as a basis for discussion or a further elicitation process [15,16]. There are two types of prototypes: throw-away prototypes, which can be used for better understanding of the requirements, and evolutionary prototypes, which represent a simplified working version of the outcome that can later be part of the final outcome [11].
- Model-driven or modeling techniques:This category revolves around the use of a specific model to illustrate the information that needs to be collected to be used later in the elicitation process. This includes goal-based approaches such as KAOS and I*, and scenario-based approaches such as CREWS [15]. It also includes business process modeling approaches such as UML, Business Process Modeling Notation (BPMN), and data flow diagrams [11,16].
- Cognitive techniques:These techniques prioritize the elicitation of knowledge and thus encompass a range of multidisciplinary approaches from various fields where knowledge elicitation is requisite [9,15]. These techniques encompass a range of approaches, including protocol analysis, laddering, card sorting, repertory grids, ontologies, and proximity scaling techniques [9,11,15,16].
- Contextual techniques:These techniques aim to elicit requirements directly from the context to better understand social and organizational behavior. They collect rich data about stakeholders and everything related to their work, including environment, processes, models, and workflows [16]. These techniques include ethnographic approaches such as participant observation, in addition to ethnomethodology, conversational and social analysis, and sociotechnical methods [9,11,15,16].
2.2. Data Ownership
3. Requirements Engineering Approach for Data Ownership Concepts
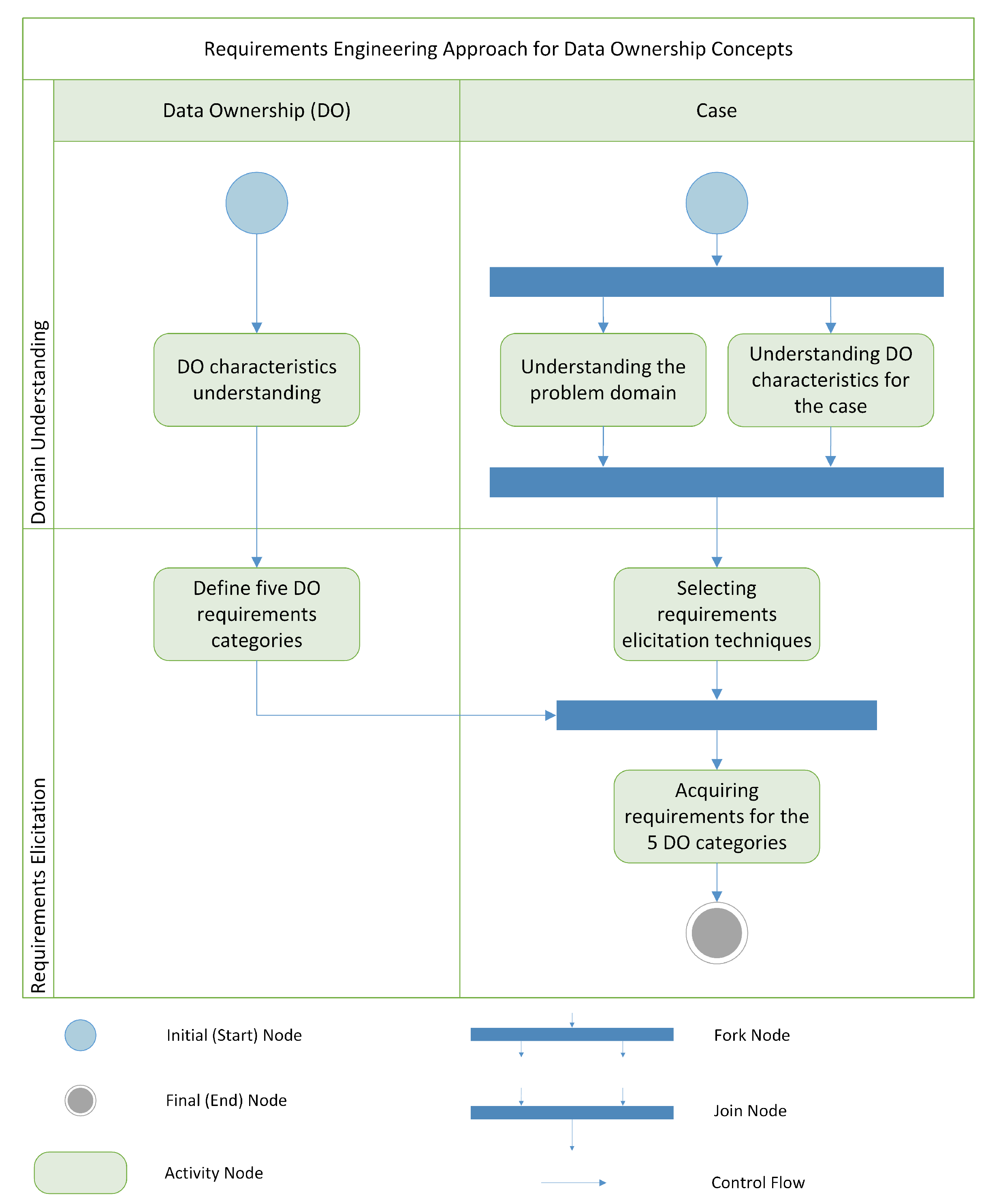
3.1. Domain Understanding
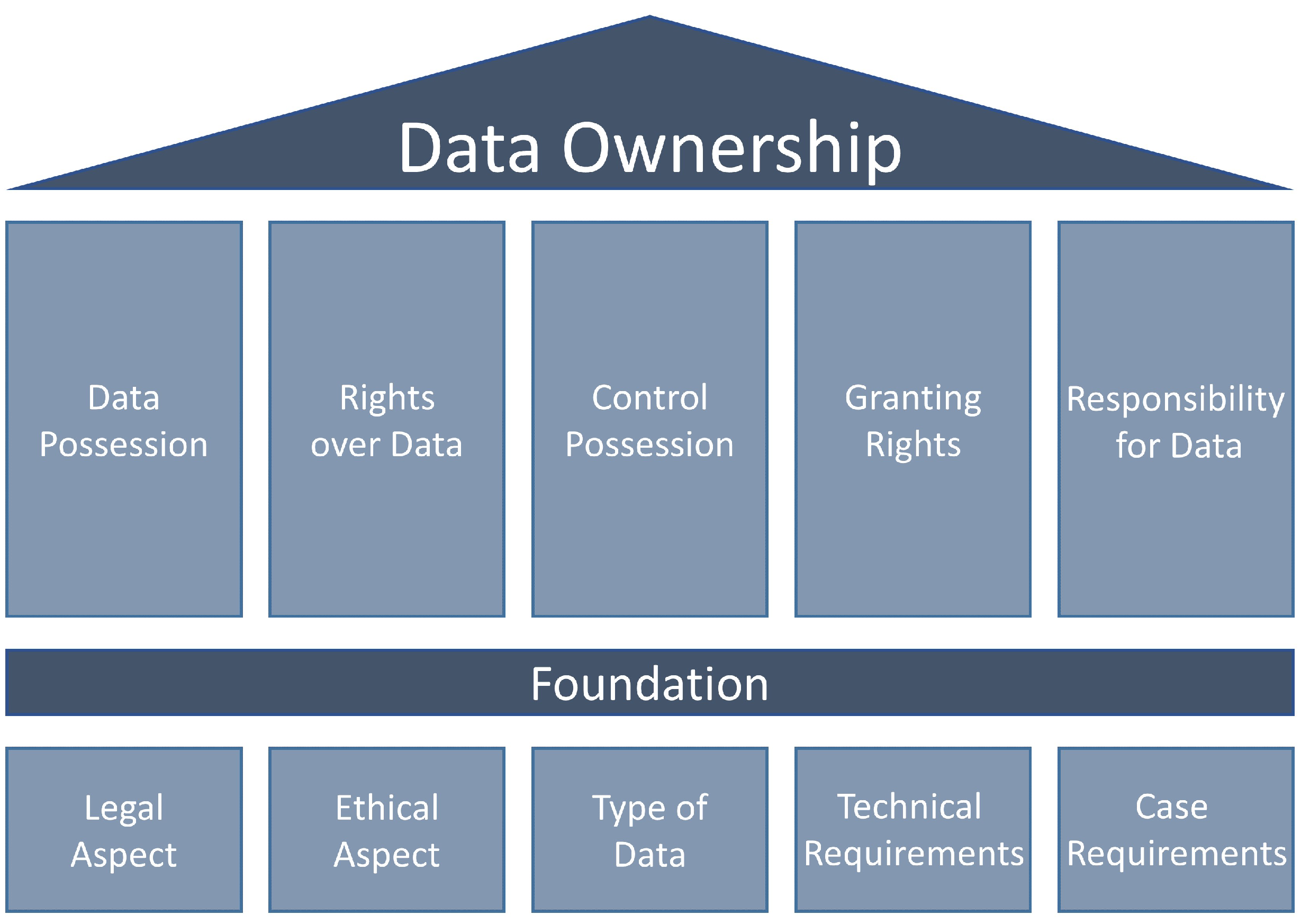
- Who owns/possesses the data?
- Who posses rights over the data?
- Who controls the possession of the data?
- Who can grant rights over the data?
- Who is responsible for the data?
- Data owner
- Data provider
- Data user/consumer
- Data repository
3.2. Requirements Elicitation
- Requirements for the legal aspect;
- Requirements for the ethical aspect;
- Data requirements;
- Technical requirements;
- Case requirements.
4. Case-Studies
4.1. Case-Study: Smart Meters
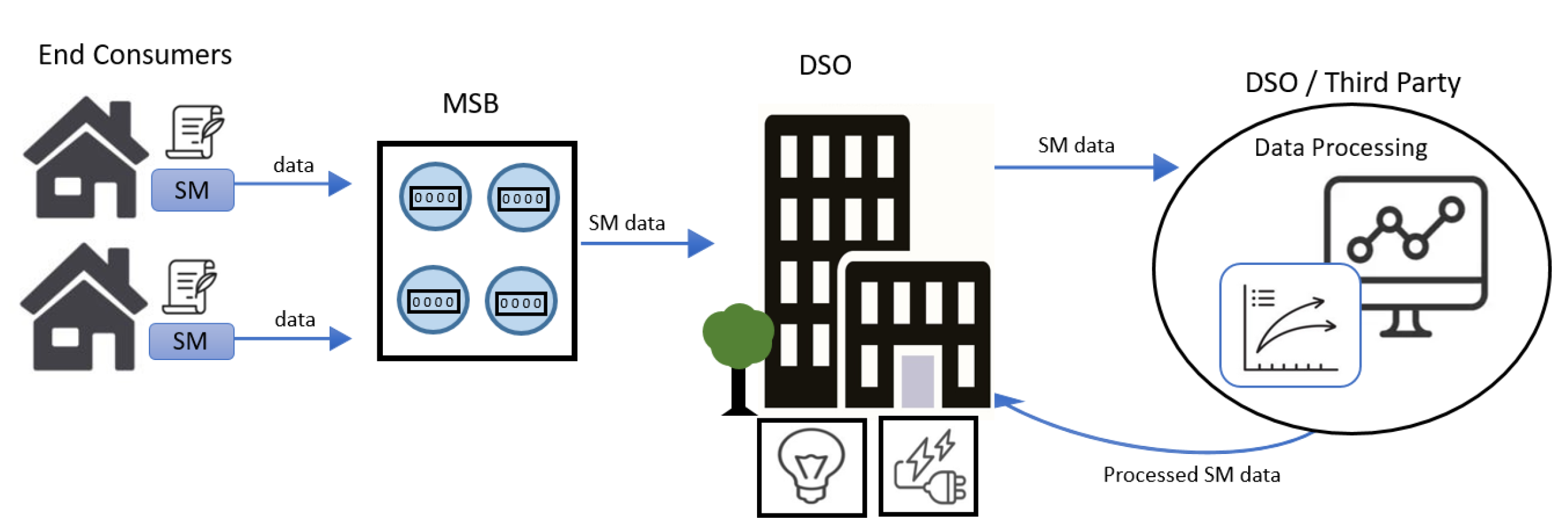
- End consumer: a natural or legal person who purchases electrical energy or produces it by means of a local, decentralized generator.
- Metering point operator (MSB): the entity responsible for the installation, operation, reading, and maintenance of electricity meters as well as for the actual metering process.
- Distribution System Operator (DSO): a company that operates electricity and gas networks for distribution to end consumers (private households and small consumers).
- Third party: a natural or legal person, public authority, agency, or other body that processes data on behalf of the DSO.
4.1.1. Methodology: Smart Meters
Background Study and Literature Review
Unstructured Interview and Questionnaire
- The intended use and rights of smart meter data and information derived from it.
- Responsibility and control over the data.
- Government and company regulations regarding the utilization of smart meter data.
- Access control.
- Data security and privacy.
4.1.2. Preliminary Results: Smart Meters
4.1.3. Case-Study Summary: Smart Meter
4.2. Case-Study: Precision Livestock Farming
4.2.1. Methodology: Precision Livestock Farming
4.2.2. Preliminary Results: Precision Livestock Farming
4.2.3. Case-Study Summary: Precision Livestock Farming
4.3. Case-Study: Data Spaces for Energy
4.3.1. Methodology: Data Spaces for Energy
4.3.2. Preliminary Results: Data Spaces for Energy
4.3.3. Case-Study Summary: Data Spaces for Energy
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Abbas, A.E.; van Velzen, T.; Ofe, H.; van de Kaa, G.; Zuiderwijk, A.; de Reuver, M. Beyond control over data: Conceptualizing data sovereignty from a social contract perspective. Electron. Mark. 2024, 34, 20. [Google Scholar] [CrossRef]
- Panis, M.C. An Analysis of Requirements-Related Problems that Occurred in an organization Using a Mature Requirements Engineering Process. In Proceedings of the 2020 IEEE 28th International Conference on Requirements Engineering, Zurich, Switzerland, 31 August–4 September 2020. [Google Scholar] [CrossRef]
- Ragnostad, O.A. ‘Data ownership’ ambiguity. In Promoting Sustainable Innovation and the Circular Economy; Routeledge: London, UK, 2020; pp. 114–133. [Google Scholar]
- Asswad, J.; Marx Gómez, J. Data Ownership: A Survey. Information 2021, 12, 465. [Google Scholar] [CrossRef]
- Van Lamsweerde, A. Requirements Engineering: From System Goals to UML Models to Software; John Wiley & Sons: Chichester, UK, 2009; Volume 10. [Google Scholar]
- Kalloniatis, C.; Kavakli, E.; Gritzalis, S. Addressing privacy requirements in system design: The PriS method. Requir. Eng. 2008, 13, 241–255. [Google Scholar] [CrossRef]
- Institute, S.E. CERT SQUARE for Privacy (P-SQUARE); Carnegie Mellon University: Pittsburgh, PA, USA, 2012. [Google Scholar]
- Zowghi, D.; Coulin, C. Requirements Elicitation: A Survey of Techniques, Approaches, and Tools. In Engineering and Managing Software Requirements; Aurum, A., Wohlin, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 19–46. [Google Scholar] [CrossRef]
- Sharma, S.; Pandey, S.K. Revisiting Requirements Elicitation Techniques. Int. J. Comput. Appl. 2013, 75. [Google Scholar] [CrossRef]
- Lim, S.; Henriksson, A.; Zdravkovic, J. Data-Driven Requirements Elicitation: A Systematic Literature Review. SN Comput. Sci. 2021, 2, 16. [Google Scholar] [CrossRef]
- Tiwari, S.; Rathore, S.S. A Methodology for the Selection of Requirement Elicitation Techniques. arXiv 2017, arXiv:1709.08481. [Google Scholar]
- Wong, L.R.; Mauricio, D.S.; Rodriguez, G.D. A Systematic Literature Review about Software Requirements Elicitation. J. Eng. Sci. Technol. 2017, 12, 296–317. [Google Scholar]
- Sutcliffe, A.; Sawyer, P. Requirements Elicitation: Towards the Unknown Unknowns. In Proceedings of the 2013 21st IEEE International Requirements Engineering Conference (RE), Rio de Janeiro, Brazil, 15–19 July 2013; pp. 92–104. [Google Scholar]
- Bühne, S.; Herrmann, A. Handbook Requirements Management. IREB International Requirements Engineering Board e.V. 2022. Available online: https://cpre.ireb.org/en/downloads-and-resources/downloads/category:handbooks (accessed on 27 October 2023).
- Nuseibeh, B.; Easterbrook, S. Requirements Engineering: A Roadmap. In Proceedings of the Conference on the Future of Software Engineering-ICSE’00, Limerick, Ireland, 4–11 June 2000; pp. 35–46. [Google Scholar] [CrossRef]
- Pacheco, C.; García, I.; Reyes, M. Requirements Elicitation Techniques: A Systematic Literature Review Based on the Maturity of the Techniques. IET Softw. 2018, 12, 365–378. [Google Scholar] [CrossRef]
- Publications Office of the European Union. What Is Data Ownership, and Does It Still Matter under EU Data Law?: An Exploration of Traditional Concepts of Data Ownership, and of the Expected Impact of the Data Act; Publications Office: Luxembourg, 2024. [Google Scholar]
- Paustian, S.; Köhlke, J.; Mattes, J.; Lehnhoff, S. Ready, Set, … Rollout?—The Role of Heterogeneous Actors and Proximities in the Delayed Smart Meter Rollout in Germany. Clean. Eng. Prod. 2025, 26, 100930. [Google Scholar] [CrossRef]
- Cavoukian, A.; Polonetsky, J.; Wolf, C. SmartPrivacy for the Smart Grid: Embedding Privacy into the Design of Electricity Conservation. Identity Inf. Soc. 2010, 3, 275–294. [Google Scholar] [CrossRef]
- Bundesnetzagentur. Intelligentes Messsystem. Available online: https://www.bundesnetzagentur.de/DE/Vportal/Energie/Metering/start.html (accessed on 6 November 2023).
- Bundesministerium der Justiz. Messstellenbetriebsgesetz-MsbG Official Legal Text. Available online: https://www.gesetze-im-internet.de/messbg/ (accessed on 6 November 2023).
- Cavanillas, J.M.; Curry, E.; Wahlster, W. The Big Data Value Opportunity. In New Horizons for a Data-Driven Economy; Springer: Cham, Switerland, 2016; pp. 3–11. [Google Scholar]
- Froese, J.; Straub, S. Wem gehören die Daten?–Rechtliche Aspekte der digitalen Souveränität in der Wirtschaft. In Digitalisierung Souverän Gestalten; Hartmann, E.A., Ed.; Springer: Berlin/Heidelberg, Germany, 2021; pp. 86–97. [Google Scholar] [CrossRef]
- GDPR. General Data Protection Regulation (GDPR)—Official Legal Text. 2016. Available online: https://gdpr-info.eu/ (accessed on 6 November 2023).
- McHenry, M.P. Technical and Governance Considerations for Advanced Metering Infrastructure/Smart Meters: Technology, Security, Uncertainty, Costs, Benefits, and Risks. Energy Policy 2013, 59, 834–842. [Google Scholar] [CrossRef]
- Molina-Markham, A.; Shenoy, P.; Fu, K.; Cecchet, E.; Irwin, D. Private Memoirs of a Smart Meter. In Proceedings of the 2nd ACM Workshop on Embedded Sensing Systems for Energy-Efficiency in Building-BuildSys ’10, Zurich, Switzerland, 2 November 2010; p. 61. [Google Scholar] [CrossRef]
- Ács, G.; Castelluccia, C. I Have a DREAM! (DiffeRentially privatE smArt Metering). In Information Hiding; Filler, T., Pevný, T., Craver, S., Ker, A., Eds.; Springer Berlin Heidelberg: Berlin, Heidelberg, 2011; Volume 6958, pp. 118–132. [Google Scholar] [CrossRef]
- Wang, J.; Gao, F.; Zhou, Y.; Guo, Q.; Tan, C.W.; Song, J.; Wang, Y. Data Sharing in Energy Systems. Adv. Appl. Energy 2023, 10, 100132. [Google Scholar] [CrossRef]
- Efthymiou, C.; Kalogridis, G. Smart Grid Privacy via Anonymization of Smart Metering Data. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 238–243. [Google Scholar] [CrossRef]
- Chhachhi, S.; Teng, F. Market Value of Differentially-Private Smart Meter Data. In Proceedings of the 2021 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 16–18 February 2021; pp. 1–5. [Google Scholar]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Differential Privacy Techniques for Cyber Physical Systems: A Survey. IEEE Commun. Surv. Tutor. 2019, 22, 746–789. [Google Scholar] [CrossRef]
- Aitzhan, N.Z.; Svetinovic, D. Security and Privacy in Decentralized Energy Trading Through Multi-Signatures, Blockchain and Anonymous Messaging Streams. IEEE Trans. Dependable Secur. Comput. 2018, 15, 840–852. [Google Scholar] [CrossRef]
- Winkel, C.; Schukat, S.; Heise, H. Importance and Feasibility of Animal Welfare Measures from a Consumer Perspective in Germany. Food Ethics 2020, 5, 21. [Google Scholar] [CrossRef]
- Rohlmann, C.; Verhaagh, M.; Efken, J. Steckbriefe zur Tierhaltung in Deutschland: Ferkelerzeugung und Schweinemast; Johann Heinrich von Thünen-Institute: Braunschweig, Germany, 2021. [Google Scholar]
- Weible, D.; Christoph-Schulz, I.; Salamon, P.; Zander, K. Citizens’ perception of modern pig production in Germany: A mixed-method research approach. Br. Food J. 2016, 118, 2014–2032. [Google Scholar] [CrossRef]
- Bundesamt, S. Trend zu Großbetrieben in der Landwirtschaft-Schweinehaltung besonders betroffen. Pressemitteilung Nr. N 001. Available online: https://www.destatis.de/DE/Presse/Pressemitteilungen/2020/01/PD20_N001_413.html (accessed on 21 March 2025).
- Bäurle, H.; Tamásy, C. Regionale Konzentrationen der Nutztierhaltung in Deutschland; Institut für Strukturforschung und Planung in agrarischen Intensivgebieten (ISPA): Vechta, Germany, 2012; Volume 79. [Google Scholar]
- Federal Ministry of Food and Agriculture. African Swine Fever (ASF): Information on cases in Germany. Available online: https://www.bmel.de/EN/topics/animals/animal-health/african-swine-fever.html#:~:text=and%20awareness%20building-,Current%20situation%3A,boar%20population%20in%20the%20region (accessed on 21 March 2025).
- Patel, D.; Brahmbhatt, M.; Bariya, A.; Nayak, J.; Singh, V. Blockchain technology in food safety and traceability concern to livestock products. Heliyon 2023, 9, e16526. [Google Scholar] [CrossRef]
- Krampe, C.; Serratosa, J.; Niemi, J.K.; Ingenbleek, P.T.M. Consumer Perceptions of Precision Livestock Farming-A Qualitative Study in Three European Countries. Animals 2021, 11, 1221. [Google Scholar] [CrossRef]
- Xu, X.; Weber, I.; Staples, M. Architecture for Blockchain Applications; Springer: Cham, Switerland, 2019. [Google Scholar]
- Kampan, K.; Tsusaka, T.W.; Anal, A.K. Adoption of Blockchain Technology for Enhanced Traceability of Livestock-Based Products. Sustainability 2022, 14, 13148. [Google Scholar] [CrossRef]
- Yuan, Y.; Liu, X.; Hong, K.; Song, S.; Gao, W. Trustworthy Traceability of Quality and Safety for Pig Supply Chain Based on Blockchain. In Cognitive Internet of Things: Frameworks, Tools and Applications; Lu, H., Ed.; Springer International Publishing: Cham, Switerland, 2020; pp. 343–355. [Google Scholar] [CrossRef]
- Meister, J.; Lehnhoff, S.; Göring, A.; Altherr, T. Digitization of Measures Cascading for the System Safety of Power Grids by openKONSEQUENZ. In Proceedings of the 16th Symposium Energieinnovation, Graz, Austria, 12–14 February 2020. [Google Scholar]
- Goering, A.; Meister, J.; Lehnhoff, S.; Herdt, P.; Jung, M.; Rohr, M. Reference architecture for open, maintainable and secure software for the operation of energy networks. CIRED-Open Access Proc. J. 2017, 2017, 1410–1413. [Google Scholar] [CrossRef]
- Dam, T.; Klausner, L.D.; Neumaier, S.; Priebe, T. A Survey of Dataspace Connector Implementations. arXiv 2024, arXiv:2309.11282. [Google Scholar]
- Solmaz, G.; Cirillo, F.; Fürst, J.; Jacobs, T.; Bauer, M.; Kovacs, E.; Santana, J.R.; Sánchez, L. Enabling data spaces: Existing developments and challenges. In Proceedings of the 1st International Workshop on Data Economy, Rome, Italy, 9 December 2022; pp. 42–48. [Google Scholar]
- Leachu, S.; Janßen, J.; Gdanitz, N.; Kirchhöfer, M.; Janzen, S.; Stich, V. Cascading Scenario Technique Enabling Automated And Situation-based Crisis Management. In Proceedings of the 2023 Conference on Production Systems and Logistics: CPSL, Querétaro, Mexico, 28 February–2 March 2023; Herberger, D., Hübner, M., Stich, V., Eds.; publish-Ing.: Hannover, Germany, 2023; pp. 321–331. [Google Scholar] [CrossRef]
- Gottschalk, M.; Uslar, M.; Delfs, C. The Use Case and Smart Grid Architecture Model Approach: The IEC 62559-2 Use Case Template and the SGAM Applied in Various Domains; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Janzen, S.; Gdanitz, N.; Abdel Khaliq, L.; Munir, T.; Franzius, C.; Maass, W. Anticipating Energy-driven Crises in Process Industry by AI-based Scenario Planning. In Proceedings of the 56th Hawaii International Conference on System Sciences, Maui, HI, USA, 3–6 January 2023. [Google Scholar]
- Putrama, I.M.; Martinek, P. Heterogeneous data integration: Challenges and opportunities. Data Brief 2024, 56, 110853. [Google Scholar] [CrossRef] [PubMed]
- Leachu, S.; Berninger, S.; Janßen, J. AI-Based Crisis Management Utilizing Scenarios. In Proceedings of the 23rd Working Conference on Virtual Enterprises: PRO-VE 2022, Lisbon, Portugal, 19–21 September 2022; Springer International Publishing: Cham, Switzerland, 2022. [Google Scholar]
- Otto, B. The evolution of data spaces. In Designing Data Spaces: The Ecosystem Approach to Competitive Advantage; Springer International Publishing: Cham, Switzerland, 2022; pp. 3–15. [Google Scholar]
| Name | Description |
|---|---|
| Data Rights | The GDPR grants end consumers several rights regarding their smart meter data. These include the right of access, the right of rectification, the right to be forgotten, and the right to stop data processing. Additionally, the GDPR grants certain rights to the controller, such as the DSOs in our case. These encompass the ability to collect, read, write, process, analyze, and delete the data. |
| Data Possession and Control | The possession and control of smart meter data resides with the DSO, who has the authority to transfer said possession and control to third parties through the formation of contractual or legal agreements. |
| Responsibility for Data | The DSO bears responsibility for smart meter data. This entails the ethical and legal obligation to oversee the collection, storage, processing, and usage of smart meter data in a manner that ensures its accuracy, security, privacy, and compliance with pertinent regulations and standards. |
| Granting Rights | The end consumers are the ones who grant smart meter data rights to the DSO. However, through the service contract, they provide the utilities with the authority to grant rights to third parties. |
| Name | Description |
|---|---|
| Legal Aspects | Smart meter data should be handled in accordance with the GDPR (https://gdpr-info.eu/issues/personal-data/) (accessed on 3 February 2025) and the MsbG (https://www.gesetze-im-internet.de/messbg/) (accessed on 3 February 2025). The DSO must obtain explicit consent from the end consumer through a contractual agreement prior to collecting, processing, or analyzing their data. The DSO should establish a contractual agreement with third party prior to sharing smart meter data. Smart meter data that can be linked to an individual should be deleted or anonymized in accordance to legal requirements as soon as they are no longer required for the intended purpose. |
| Ethical Aspects | The DSO should ensure that smart meter data are used exclusively to support the operations of the electric grid, in strict adherence to applicable data protection regulations and implementing necessary safeguards for data privacy and security. Access to smart meter data should be limited to the minimum amount of information necessary to provide the service. |
| Data Requirements | Smart meter data should conform to the specifications and guidelines outlined in the MsbG, including but not limited to the format, structure, and content of the data, as well as the protocols and standards for data transmission. |
| Case Requirements | When requesting consent from the end consumer, detailed information about what data will be collected and for what purpose should be provided, in an easily understandable language and in a comprehensible manner. End consumers should have access to their smart meter data, and it should be easy and clear how to access it. Smart meter data that can be linked to an individual should be anonymized or pseudonymized. |
| Technical Requirements | Smart meter data should be protected from unauthorized access, which includes implementing appropriate technical measures to protect the data, such as encryption, access control, and secure communication protocols. Data protection measures should be implemented by design and default. Specifically, data protection measures should be embedded in the data processing workflow, with default settings that prioritize security and privacy, unless explicitly overridden by an authorized party with legitimate justification. |
| Name | Description |
|---|---|
| Data Rights | Stakeholders in the SSI system can assign various rights, such as the length of the retention time of time series, restriction of data release without personal data, and deletion of off-chain data. On-chain data cannot be subsequently deleted or changed, but are useless without assignment. |
| Data Possession and Control | Due to the decentralized solution of a blockchain, the data are under the control of all participants in the network. The network participants themselves are in possession of the data. A decentralized storage solution would ensure that the data are stored redundantly by each participant, but only the owner has actual access to their data. |
| Responsibility for Data | Data responsibility is not yet relevant at the present time. |
| Granting Rights | Farmers can use decentralized identities to decide for themselves which data they want to release. There is no superordinate instance with extended rights that would have to grant rights on its own. |
| Name | Description |
|---|---|
| Legal Aspects | The system must ensure compliance with the General Data Protection Regulation (GDPR) requirements applicable to the processing of personal data. This includes, but is not limited to, ensuring data privacy and protection from the point of collection through processing to deletion, providing data subjects with the ability to access, rectify, erase, or port their data, implementing data protection principles by design and by default, and maintaining a record of processing activities. |
| Ethical Aspects | The data generated must adhere to ethical standards concerning data handling, participant privacy, and transparency. This involves obtaining informed consent from all participants, ensuring anonymity and data protection. Measures should be in place to anonymize participant data and safeguard personal information. |
| Data Requirements | The software must support the management of time series data, as well as various accompanying documents including veterinary documentation, qualifications, and certificates. This entails the ability to store, retrieve, update, and delete such data and documents as per user requests or system requirements. |
| Case Requirements | Documentation of the legal basis for data collection and the specific steps taken to protect personal data is maintained. Mechanisms for integrating legally obtained non-personalized data with personalized data are defined, prioritizing data security and consumer privacy. |
| Technical Requirements | PLF data must be stored off-chain to ensure scalability and efficiency of data access. Additionally, data traffic, including but not limited to MQTT communications, must be secured to safeguard data integrity and confidentiality during transmission. |
| Name | Description |
|---|---|
| Data Rights | Data rights should take into consideration, as follows: legal aspects of data needed to handle crisis situations, GDPR, and shared ownership of data between DSO, TSO, and customers. |
| Data Possession and Control | Some parts of the data are under the possession and control of the Distribution System Operator (DSO) and Transmission System operator (TSO). Data on outages are publicly shared by the TSO, where outages are gathered, processed, and later on communicated to the TSO by the DSO. |
| Responsibility for Data | The DSO holds the responsibility to gather data on outages and publicly communicate these data to the TSO (e.g., annually) and also to customers (e.g., on demand). |
| Granting Rights | The data should have a share ownership between the DSO, TSO, and consumer. However, it is not clear how exactly the consumer could influence the necessaty to data collection, because parts of the data are required to stabilize power grids and mitigate further risks of outages. |
| Name | Description |
|---|---|
| Legal Aspects | There is still a limited understanding of how a combination of utility data (e.g., personal and non-personal) for the analysts should be technically implemented in a way that does not violate the General Data Protection Regulation (GDPR). |
| Ethical Aspects | Multiple ethical considerations should be considered. During outages, access to essential data may be disrupted on both sides of the service, providers and consumers. Additionally, user privacy requires careful handling and secure storage to prevent unauthorized access or misuse. |
| Data Requirements | As long as multiple parties are exchanging the data, the data requirements should conform with the DO concept. |
| Case Requirements | In most cases, consent from the consumer to provide their data is provided by legal regulations; however, these data are not personalized. Thus, special steps should be included in order to make use of both types of data, whether data collected by law enforcement (e.g., for billing purposes) and personalized data (e.g., outages having happened at particular locations). |
| Technical Requirements | Data exchange between involved services (e.g., service providers, data consumers, etc.) should be carried out in a secure way and ensure protection against unauthorized access. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Asswad, J.; Dmitriyev, V.; Elizondo Guerrero, M.E.; Theesen, C.; Köhlke, J. Requirements Engineering Approach for Data Ownership Concepts. Electronics 2025, 14, 1288. https://doi.org/10.3390/electronics14071288
Asswad J, Dmitriyev V, Elizondo Guerrero ME, Theesen C, Köhlke J. Requirements Engineering Approach for Data Ownership Concepts. Electronics. 2025; 14(7):1288. https://doi.org/10.3390/electronics14071288
Chicago/Turabian StyleAsswad, Jad, Viktor Dmitriyev, Maria Edith Elizondo Guerrero, Cedrik Theesen, and Julia Köhlke. 2025. "Requirements Engineering Approach for Data Ownership Concepts" Electronics 14, no. 7: 1288. https://doi.org/10.3390/electronics14071288
APA StyleAsswad, J., Dmitriyev, V., Elizondo Guerrero, M. E., Theesen, C., & Köhlke, J. (2025). Requirements Engineering Approach for Data Ownership Concepts. Electronics, 14(7), 1288. https://doi.org/10.3390/electronics14071288






