Abstract
In recent years, the growing importance of data ownership has attracted significant attention, reflecting not only its pivotal role in the evolving data-driven environment but also the complexity of addressing it across diverse contexts. The necessity of developing effective data ownership concepts for data platforms is indisputable; nevertheless, the process is inherently complex and demands a comprehensive examination of the requirements surrounding this multifaceted issue. This paper puts forward a novel approach to the development of data ownership concepts, which draws on principles from requirements engineering (RE). The efficacy of this approach is evaluated through in-depth case-studies focusing on three distinct contexts: the development of a data ownership concept within the realm of smart meters, smart livestock farming, and data spaces for energy. Through the application of RE principles, this work strives to provide a structured and effective approach for addressing the nuanced challenges associated with data ownership in the process of developing data ownership concepts for data-driven platforms and applications.
1. Introduction
Achieving an equitable balance between leveraging the advantages afforded by data and ensuring privacy protection is imperative. The establishment of transparent and robust frameworks for data ownership is not only instrumental in safeguarding data rights, but also fosters trust and facilitates the effective and secure utilization of data. In essence, effective management of data ownership is a fundamental element in realizing the full potential of data while upholding ethical and privacy standards. According to Abbas et al. (2024), “data ownership refers to the legal rights and control an individual or organization has over their data, including the ability to manage, share, and dispose of it”. In contrast, data sovereignty includes a broader framework that extends beyond ownership to integrate aspects, such as protection, provision, and participation. While data ownership primarily emphasizes individual or organizational rights, data sovereignty considers collective responsibilities and contextual factors that shape data management and sharing practices [1].
The development of effective data ownership concepts requires a comprehensive study and analysis of the general requirements of such concepts. The requirement engineering (RE) process plays a fundamental role in ensuring the effectiveness, ethicality, and user acceptance of data ownership concepts. This process entails the identification and analysis of relevant stakeholders, facilitating the understanding of their needs, expectations, and concerns. This alignment ensures that data ownership concepts are developed with a comprehensive view of the diverse interests involved, promoting inclusivity and stakeholder satisfaction. It also helps to map legal requirements, ethical guidelines, and industry standards, ensuring that the concept is fully in compliance. This not only ensures legal compliance, butalso fosters user trust. Additionally, conducting a thorough requirement elicitation helps identify security and privacy requirements and anticipate future changes, ensuring that the concept can accommodate emerging technologies and evolving user needs.
In the context of the conceptualization and design of a new data-based system, software, or platform, data ownership-related aspects are frequently overlooked or addressed in a limited manner as part of the overarching development requirements. This oversight can result in the failure to address critical elements necessary to ensure data ownership protection. For example, the absence of data ownership in the process of RE can create confusion over rights, obstruct sustainable innovation, and make legal compliance more complex, while also causing misalignment between requirements and artifacts [2]. This mismanagement creates ambiguity in the use, access, and control of data, particularly in heterogeneous project surroundings [3].
While the necessity of data ownership is widely acknowledged, there are currently limited approaches for its implementation within the RE process. This discrepancy highlights a gap between the conceptual understanding of data ownership and its practical integration into RE.Likewise, data ownership requirements are not universally consistent and can vary depending on the specific case. Therefore, to comprehensively address the necessary requirements in each instance, a structured approach is imperative. This approach should be predicated on predetermined steps and clearly defined data ownership characteristics and aspects. This study therefore explores the following research question: “How can the concept of data ownership be effectively incorporated into the RE process to ensure that the rights and interests of heterogeneous involved stakeholders are properly considered?”
The aim of this work is to provide a roadmap approach for the elicitation of data ownership-related requirements in any context. In order to evaluate the applicability of the approach in different cases, the evaluation will be conducted through three case-studies across three distinct domains. This work represents a continuation of a previously published study [4], in which the concept of data ownership was surveyed and a conceptual model depicting a new definition of data ownership was introduced. This present work will build upon the conclusions of the previous study, utilizing the aforementioned conceptual model of data ownership in conjunction with the principles of RE to elicit requirements for the development of data ownership concepts. The principles of RE provide the necessary guidance throughout the process, and the conceptual model of data ownership provides the characteristics and aspects of data ownership that need to be addressed.
The initial section of the work provides a comprehensive overview of the principles of RE and data ownership. Subsequent sections then apply the principles of RE to address the issue of data ownership. The approach is demonstrated through three case-studies, which highlight its application in the development of data ownership concepts. The work concludes with a discussion of the approach and its applicability.
2. Materials and Methods
2.1. Requirements Engineering
Typical RE involves comprehending and analyzing three dimensions: WHAT problem should be solved, WHY the problem needs to be solved, and WHO the relevant actors are in the problem-solving process [5]. Addressing and analyzing the requirements for solving data ownership-related issues is analogous to this process, and the three dimensions of RE can serve as the foundation for solving such issues.
The “WHY” dimension of RE involves comprehending the prevailing circumstances of the issue and the rationale behind the necessity of a transformation. To address this, a range of actions must be undertaken in addition to grasping the problem itself. Initially, it is essential to acquire knowledge about the domain in which the problem world is situated. This encompasses understanding concepts, regulations, procedures, and terminologies, among other aspects. Subsequently, the evaluation of alternative possibilities in the problem world should be conducted in terms of their respective advantages and disadvantages, taking into account the potential implications and risks. Finally, it is essential to identify the objectives of the process and the stakeholders who will be involved in the RE process [5].
The “WHAT” dimension of RE delves into the necessary requirements to achieve the objectives identified in the WHY dimension, focusing on the identification of services, constraints, and assumptions of the desired solution. These requirements can be classified as either functional or non-functional. Functional requirements delineate the functional effects of the desired solution and address the question, “What should the solution do?”. Conversely, non-functional requirements define constraints on the manner in which the desired solution should satisfy the defined functional requirements, thereby answering the question, “How should the solution fulfill these requirements?”. Non-functional requirements also encompass quality requirements, which stipulate quality-related properties that the functional effects of the desired solution should possess, thus answering the question, “How well should the solution perform?” [5]. Such requirements are of paramount importance, particularly when addressing issues such as data ownership concepts. Privacy, for instance, is generally regarded as a non-functional quality requirement. While privacy used to be seen more as a social and legal issue, in recent years, it has increasingly found its way into software applications. Especially when a large number of data are collected or personal data are stored, user trust plays a major role [6]. Nevertheless, its assurance is profoundly related to the understanding of data ownership. As an example, a privacy requirement would determine whether the consent of the data owner is required to disclose private information in a particular context. A suitable privacy RE tool is P-SQUARE developed by the Software Engineering Institute (SEI) at Carnegie Mellon University that assists organizations in identifying privacy requirements for their software systems [7].
Finally, the “WHO” dimension delineates the allocation of responsibilities for achieving the objectives, services, constraints, and the identified requirements in general among the components and the actors of the desired solution. This includes, but is not limited to, the system-to-be, humans, departments, organizations, devices, or software. To conduct a requirements engineering process, a variety of activities involving various stakeholders must take place. While the specific activities may vary across different sources, the following activities are typically involved in the process: domain understanding, requirements elicitation and analysis, requirements specification, and finally, requirements verification and validation [5].
As mentioned earlier, domain understanding aims to illustrate a comprehensive picture of the current situation from different aspects. The aspects that need to be studied to understand the domain of the problem may vary according to the domain and the problem itself, and according to the desired outcome of the RE process. However, domain understanding generally includes the following aspects [5]:
- Understanding of the domain and the problem;
- Understanding of organizational context;
- Understanding the technical context;
- Understanding the legal aspect surrounding the problem;
- Defining the stakeholders involved in the process;
- Understanding the current state, including its strengths and weaknesses.
It is imperative to comprehend these aspects, particularly the organizational, technical, and legal dimensions, to be able to understand the necessary data ownership requirements. In the organizational context, for instance, comprehending the existing organizational structure, decision-making hierarchy, business processes, and workflow is necessary to develop a data ownership concept that takes into account what is required for that specific organization and how the concept would affect the organization.
Similarly, in the legal context, understanding internal legal aspects such as organizational rules and restrictions, intellectual property and copyrights, and binding agreements, in addition to understanding external legal aspects such as country laws, industry and manufacturer laws and regulations, and general laws such as the European General Data Protection Regulation (GDPR) is inevitable when addressing the requirements of a legal-related topic such as data ownership.
Finally, it is also critical to understand the technical context, including the general technical infrastructure, the systems and tools available, the communications between these systems, and the security and privacy measures currently in place to identify requirements for the development of a data ownership approach that would enhance or replace current functionality or systems.
Requirements elicitation is commonly referred to in the literature as one of the most important and critical activities in the RE process. Capturing the right requirements is an essential but also a difficult step that can affect the success of RE and the development process as a whole [8,9,10,11,12].
Requirements elicitation is mainly concerned with the identification of candidate requirements based on the information gathered through domain understanding. It revolves around discovering, extracting, and acquiring the necessary knowledge from the problem domain, where it can be translated into useful requirements. The elicitation process therefore aims to understand the desired expectations, needs, demands, and constraints of the various stakeholders and transform them into explicit, understandable, and verifiable requirements [8,9,10,11,13,14].
The elicitation process is a complex process that involves various activities that can be carried out through the use of various available techniques [8]. The process of choosing an appropriate technique depends on the resources available, in addition to the type of information that needs to be elicited [15].
There are a variety of techniques that can be used to elicit requirements. The various studies that review or address these techniques agree to some extent on categorizing them into a set of categories that summarize the methods that can be used (Figure 1). Of course, the methods listed in these categories may vary from domain to domain, and new methods may emerge that prove useful for the elicitation process.
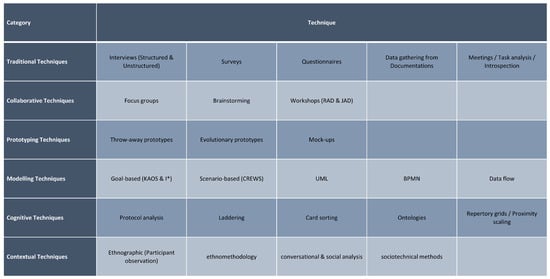
Figure 1.
Examples of requirements elicitation techniques (own representation).
- Traditional techniques:As the name suggests, this category includes basic and traditional techniques that collect generic data. Generally, this category includes techniques such as interviews in both structured and unstructured forms, surveys, questionnaires, and data collection from existing documentation [11,15,16]. Some of the literature also includes other methods such as meetings, task analysis, and introspection. Introspection can be useful when there is a lack of answers and feedback; the requirements analyst may then need to imagine what kind of requirements are needed [9].
- Collaborative or group elicitation techniques:These techniques aim to achieve a better understanding of the requirements by gaining the agreement of the stakeholders, users, and the team involved in the process. They also help to prioritize the necessary requirements. This category includes techniques such as focus groups, brainstorming, and workshops such as Rapid Application Development (RAD) and Joint Application Development (JAD) [9,11,15,16].
- Prototyping techniques:A prototype can be used in the elicitation process when there is uncertainty about the requirements and feedback is needed. It can also serve as a basis for discussion or a further elicitation process [15,16]. There are two types of prototypes: throw-away prototypes, which can be used for better understanding of the requirements, and evolutionary prototypes, which represent a simplified working version of the outcome that can later be part of the final outcome [11].
- Model-driven or modeling techniques:This category revolves around the use of a specific model to illustrate the information that needs to be collected to be used later in the elicitation process. This includes goal-based approaches such as KAOS and I*, and scenario-based approaches such as CREWS [15]. It also includes business process modeling approaches such as UML, Business Process Modeling Notation (BPMN), and data flow diagrams [11,16].
- Cognitive techniques:These techniques prioritize the elicitation of knowledge and thus encompass a range of multidisciplinary approaches from various fields where knowledge elicitation is requisite [9,15]. These techniques encompass a range of approaches, including protocol analysis, laddering, card sorting, repertory grids, ontologies, and proximity scaling techniques [9,11,15,16].
- Contextual techniques:These techniques aim to elicit requirements directly from the context to better understand social and organizational behavior. They collect rich data about stakeholders and everything related to their work, including environment, processes, models, and workflows [16]. These techniques include ethnographic approaches such as participant observation, in addition to ethnomethodology, conversational and social analysis, and sociotechnical methods [9,11,15,16].
In addition to the aforementioned categories, Sharma and Pandey added an additional category called Innovative Techniques, where new techniques for requirements elicitation can be listed [9].
After the elicitation process, the elicited requirements need to be evaluated and validated. There are a number of techniques that can be used for evaluation and validation, but they are not discussed in this paper as they are outside the scope of this paper. In the subsequent chapter, the notion of data ownership will be explored, along with its various characteristics and aspects. This exploration aims to demonstrate the necessity of employing RE techniques in the development of data ownership concepts.
2.2. Data Ownership
In the ever-evolving landscape of data management, the concept of data ownership remains elusive and ambiguous. The increasing volume and complexity of data, coupled with advances in technology, have made data ownership a critical issue in the digital age. Data ownership refers to the legal and ethical rights that an individual or entity has over data that are generated, collected, or processed. In the context of personal data, data ownership typically implies control and authority over how those data are used, shared, and stored. It includes the right of individuals to determine who can access their information and for what purposes. In a business or organizational context, data ownership may include the rights and responsibilities associated with the data generated or acquired in the course of operations. While individuals may own their personal data, organizations often claim ownership of data generated within their systems. The evolving landscape of data ownership is influenced by legal frameworks, industry regulations, and ongoing discussions about digital rights and privacy.
While commonly perceived as the complete control over data rights, a unified definition proves challenging. A recent study from an initiative of the European Commission stated that a precise meaning of data ownership remains undefined in EU-level legislation, and that the scope of potential data ownership rights is similarly ambiguous [17]. In a considerable number of instances, data ownership is intertwined with other topics such as data sovereignty. Data sovereignty can be considered analogous to data ownership, as it pertains to the legal rights, regulations, and controls over data. On the other hand, data ownership goes beyond the legal ramification of data possession and also addresses the data rights and responsibilities in relation to the data owner. The intricacies of data ownership extend beyond a simplistic view, demanding a nuanced understanding of multiple perspectives, legal implications, and other ramifications.
In a previously published study [4], a state-of-the-art study was conducted regarding the issue of data ownership. The study analyzes the various aspects surrounding the issue of data ownership and its complications. It also provides an overview of the legal aspect of data ownership in Europe and in Germany as a special case, and it surveys the state-of-the-art regarding data ownership in five major sectors. The study shows that the concept of data ownership is far from simple, unlike the ownership of tangible assets or property, and introduces various complexities and complications. The study also reveals an inherent ambiguity surrounding the issue. On the one hand, there is currently no universally accepted definition of the term. On the other hand, the fundamental question of data ownership—“Who owns the data?”—lacks a straightforward answer, exacerbated by the lack of comprehensive rules covering the trivial variations of the issue. Moreover, even when an owner is identified or agreed upon, the requirements for preserving data ownership remain unclear.
The study concludes that any aspect of data that meet the objectives and requirements of a particular case is relevant to formulating a data ownership concept tailored to that specific scenario. This means that the different requirements of the considered case need to be elicited. To summarize these findings, the study provides a definition of data ownership and presents it as a conceptual model (Figure 2) that will serve as a basis for categorizing the needed requirements. The conceptual model defines the fundamental elements of data ownership and the features that must be addressed in the development of a data ownership concept. The conceptual model is composed of two main parts. The initial part includes the characteristics that define the essence of data ownership and it includes the following: data possession, rights over data, control possession, granting rights, and responsibilities for data. The second part describes the foundation of data ownership and includes the aspects that need to be considered when developing data ownership concepts and includes the following: legal aspects, ethical aspects, type of data, technical requirements, and case requirements. Further explanation of the conceptual model of data ownership can be found in a previous work by Asswad and Gómez [4].
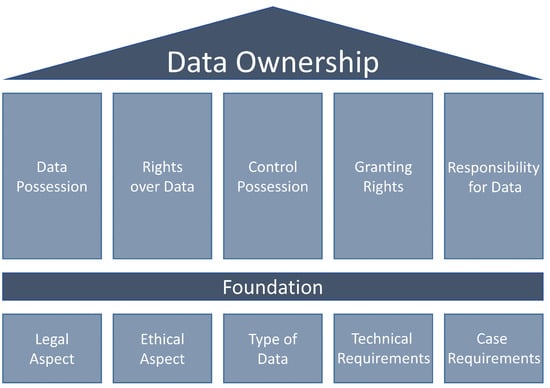
Figure 2.
Data ownership conceptual model [4].
From the standpoint of our previous study, data ownership is “the possession of data and the control of data including the ability to grant rights over data to others, taking into account the type of data, the legal and ethical aspects, the responsibility for data, and the needed requirements to preserve and achieve this possession” [4].
3. Requirements Engineering Approach for Data Ownership Concepts
The complexity and ambiguity of addressing data ownership requires a clearer approach when it comes to developing a data ownership concept for a specific case. This part of the work presents a novel approach that applies the principles of RE for eliciting requirements for developing data ownership concepts in any given case (Figure 3).
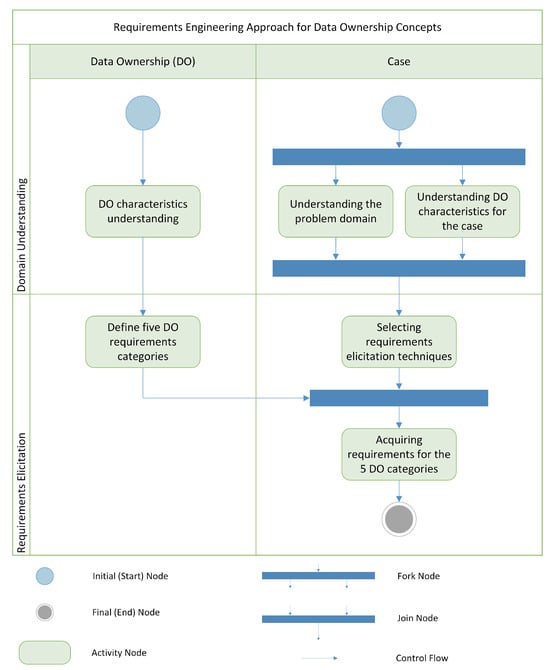
Figure 3.
UML activity diagram for the RE approach for data ownership (DO) concepts.
The approach focuses on only two steps of the RE process, namely, domain understanding and requirements elicitation. The subsequent steps of the RE process are not part of this approach, as they will be addressed in a subsequent work in which the elicited data ownership requirements based on the presented approach in this work will be analyzed and validated in order to integrate them into a data ownership reference model for the realization of data ownership concepts.
In this approach, the domain understanding would not only study the domain of the case, but also analyze the relevant aspects related to data ownership in the considered case. For the elicitation process, the requirements would be explored according to predefined data ownership requirement categories. In the following Section 3.1 and Section 3.2, both steps of the approach are further clarified.
3.1. Domain Understanding
As mentioned earlier in this work, understanding the domain in which the problem world is rooted is the very first crucial step in RE. Therefore, the presented approach starts with the general domain understanding of the case, which includes two main parts. The first part is the understanding of the domain the case is based on. Meanwhile, the second part is the understanding of the data ownership domain, in which the characteristics of the data ownership for this specific case need are analyzed and understood.
Our previous work [4] studied the issue of data ownership from different perspectives and in different sectors. It also proposed a definition of data ownership depicted in a conceptual model (Figure 2) that summarizes the results of the study and the state of the art. This conceptual model can be used to cover part of the domain understanding and to serve as a basis for requirements elicitation for the development of data ownership concepts.
The conceptual model argues that addressing data ownership in any context requires consideration and incorporation of a comprehensive set of aspects and characteristics. Within the scope of a viable data ownership concept, it is essential to maintain possession and control of the data. This concept should encompass the ownership of various rights over the data, including the ability to grant certain rights to third parties. In addition, data ownership involves taking responsibility for the data that are owned.
These five characteristics define the basic understanding of data ownership. Therefore, when analyzing the domain of the case, these five aspects need to be explored and understood. This means that the following five questions must be answered for the specific case:
- Who owns/possesses the data?
- Who posses rights over the data?
- Who controls the possession of the data?
- Who can grant rights over the data?
- Who is responsible for the data?
In addition to these five characteristics, it is necessary to identify the stakeholders that may be involved in the process. The stakeholders involved in data ownership concepts may vary from case to case, but in most cases a set of stakeholders are available in data ownership related concepts, such as the following:
- Data owner
- Data provider
- Data user/consumer
- Data repository
The data owner is basically the one who has the rights over the data, including the right to grant these rights to third parties. The data user/consumer is the one who wants to access and use the data. The data provider is the one who provides the data to the data user/consumer or stores the data in a suitable persistence medium. Finally, the data repository is where the data are stored and maintained.
However, the roles or the complexity of these stakeholders may be different or intertwined depending on the case. In some cases, the data provider may be the same person/entity as the data owner. In other cases, the data user may be another data provider to other users. In addition, the data repository is more complex than just a place where the data are stored. In most cases, it is part of a data platform, a data management system, or some other type of system, and that adds another layer of complexity. On the other hand, if other stakeholders are also part of the concept, the roles as well as the dynamic relationships and interactions between the defined stakeholders may differ to include more or less rights with or over the data. The absence of legal confirmation regarding data ownership and the rights of the data owner necessitates the identification of all data stakeholders and the comprehension of their relationships and interactions in each particular case. This understanding is critical to understanding data ownership in this case and assigning responsibilities to the right stakeholder.
To illustrate this interaction, let us take an example of a person who has an electricity contract with an energy provider: although the data of this person’s consumption should be their own, in many cases, these data belong to the energy provider. According to the General Data Protection Regulation (GDPR), this individual possesses certain rights regarding his personal data, including the right to access and download his information and the right to have it forgotten. It is imperative to recognize that the individual’s electricity contract with an energy provider does not inherently transfer ownership of his personal consumption data to the provider. Despite this, the General Data Protection Regulation (GDPR) recognizes the individual’s rights to access, download, and erase their data. However, the contractual agreements or binding arrangements between the individual and the energy provider may grant the provider additional rights over the data, such as the right to process and analyze the data, the right to transfer the data to third parties, or even the right to use the data for commercial purposes. In this particular example, the person who entered into the contract is not the data owner, but the data provider, and the energy provider is the data owner. In the event that the data are to be transferred to a third party, said third party is thereby the data user or data consumer. The portal of the energy provider, inclusive of its backend storage, is designated as the data repository. To define the necessary functional or non-functional requirements for asserting data ownership rights in this case, it is essential to comprehensively understand the various possible interactions between these stakeholders and the rights of each.
3.2. Requirements Elicitation
After the domain understanding, the approach continues with the requirements elicitation process. To capture the relevant requirements for data ownership concepts, the elicitation process is guided and grouped into specific categories according to the foundation of the data ownership conceptual model.
While the five characteristics introduced in the previous paragraph define the essence of data ownership, to design and conceptualize a robust data ownership concept, it must be based on a strong foundation. This foundation determines the extent and manner in which the characteristics of the concept should be considered. First, the foundation includes an understanding of the legal aspect of the case, including but not limited to country laws, organizational regulations, binding agreements, and manufacturer restrictions. It also considers the ethical dimension of the case, particularly when it involves medical, personal, or sensitive data. Understanding the nature of the data at issue is a critical element in establishing a sound foundation. The type of data may influence the characteristics of the approach or the complexity required to address that particular type of data. In addition, the foundation of a data ownership approach should be built on a thorough understanding of the case itself. For example, decisions must be made about the scale at which the concept will be implemented: whether within a platform, a system, an organization, a city, or a country. The foundation must also consider the extent to which the concept should be applied to preserve data ownership in the particular case. Finally, the foundation should incorporate a full understanding of the technical requirements of the case. This includes considerations such as whether the concept will be implemented on top of a legacy or existing system, or whether it will be built from scratch. Other technological requirements may include consideration of using a specific technology or set of technologies for implementation.
In summary, the conceptual model of data ownership introduces five aspects and characteristics that define the understanding of data ownership. In addition, it presents a foundation of five categories that can serve as the basis for starting the requirements elicitation process. The five characteristics and the five basic categories of the conceptual model of data ownership were defined as mentioned in Section 2.2 based on the results of the in-depth state of the art research we conducted, reviewing general and legal aspects of data ownership and surveying data ownership considerations in five major sectors, namely, energy, transportation, health, industry, and smart cities [4].
As mentioned earlier, there are a variety of techniques that can be used to elicit requirements. However, in order to structure and maximize the information obtained, the requirements needed to develop data ownership concepts would be categorized according to the foundation of the data ownership conceptual model presented earlier in Figure 2. This means that the elicitation process will gather information for the following categories:
- Requirements for the legal aspect;
- Requirements for the ethical aspect;
- Data requirements;
- Technical requirements;
- Case requirements.
The collection of information for these categories can be carried out using any appropriate elicitation technique, depending on the case and the background study required.
The entire approach, including domain understanding and the elicitation process, is shown as a Unified Modeling Language (UML) activity diagram in Figure 3.
In the next section, the introduced approach will be illustrated in three case-studies that deal with data ownership in different contexts. In these case-studies, the case domain is explored and different elicitation techniques are used to gather the necessary requirements for the development of an appropriate data ownership concept for the case.
4. Case-Studies
In this part of the paper, the introduced approach is applied and evaluated in three different case-studies. The aim of presenting the approach via three case-studies is to highlight the applicability of the approach in different domains and with different data ownership requirements. Each case-study will be structured as follows: It will start with an overview of the case and the problem at hand. This part will also include a basic understanding of the domain of the case. Next, a methodology will be presented, including the different requirements elicitation techniques used. In the next step, the preliminary results of the elicitation process will be presented. These results are presented in two tables according to the conceptual model of data ownership. One table presents the data ownership characteristics of the case, representing the domain understanding part of the approach, and the second table presents the necessary requirements for the intended implementation of a data ownership concept for the case, representing the requirements elicitation part of the approach.
Section 4.1 presents a case-study that addresses the need to develop a data ownership concept in smart-meter-based implementations. Subsequently, the case-study in Section 4.2 deals with precision livestock farming and addresses the issue of data ownership throughout the pig production value chain. The final case-study is presented in Section 4.3 and addresses the issue of data ownership for data exchange between stakeholders in the context of energy data spaces.
4.1. Case-Study: Smart Meters
This case-study explores the question of data ownership for smart meters in Germany, with the objective of identifying the necessary requirements for the development of a data ownership concept for smart meters within the German context.
Smart meters are poised to play a pivotal role in the imminent energy grid, as they provide valuable insights into energy consumption patterns among consumers and producers. However, the implementation of smart meters in Germany has experienced significant delays in recent years, particularly due to the involvement of heterogeneous stakeholders with varying requirements for the development process [18]. While leveraging meter data offers a substantial opportunity to enhance the grid efficiency [19], the question of data ownership arises in the context of smart meter implementation.
Germany is currently implementing a nationwide rollout of the intelligent measuring system (iMSys), also known as smart meters, with the objective of enhancing grid monitoring and efficiency. The iMSys consists of two primary components: a modern measuring system and a smart meter gateway. The smart meter gateway serves as a communication unit that processes and transmits data, while the modern measuring system is a digital electricity meter that reflects the actual energy consumption and the actual time of use [20].
The provision of new data by smart meters will provide distribution system operators (DSOs) with substantial assistance in optimizing the grid network. This will empower DSOs to make data-driven decisions and enhance grid management. By employing smart meters, DSOs can obtain insights into energy consumption patterns, identify areas of inefficiency, and implement the necessary adjustments to reduce energy waste and improve the overall sustainability of the grid [19].
In the current German context, the metering point operator (MSB) bears the responsibility for the measurement, collection, and distribution of energy data derived from smart meters. The operations of the MSB are governed by the Measuring Point Operation Act (MsbG) [21]. The MSB is responsible for equipping end consumers with smart meters and for the distribution of measured values directly to all authorized external market participants, including the DSO. In the majority of grid areas, the DSO assumes the role of the MSB, having taken on the responsibilities of the MSB.
In this context, there are four main stakeholders interacting with smart meter data:
- End consumer: a natural or legal person who purchases electrical energy or produces it by means of a local, decentralized generator.
- Metering point operator (MSB): the entity responsible for the installation, operation, reading, and maintenance of electricity meters as well as for the actual metering process.
- Distribution System Operator (DSO): a company that operates electricity and gas networks for distribution to end consumers (private households and small consumers).
- Third party: a natural or legal person, public authority, agency, or other body that processes data on behalf of the DSO.
In Germany, a contractual agreement between the end consumer and a DSO (e.g., a public utility) allows the DSO to collect and process the consumer’s energy consumption data for the purpose of providing energy services. The data collected by the meter are transmitted to and stored by the MSB, which then forwards the data to the DSO. The DSO can subsequently process the meter data to support its operations or transfer them to a third party service provider, as illustrated in Figure 4.
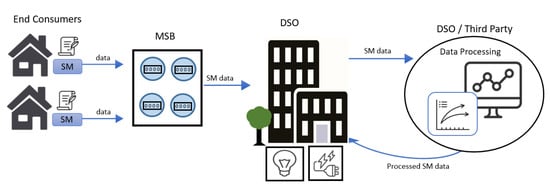
Figure 4.
Flow of smart meter data between stakeholders.
As previously stated in Section 3.1, there are typically four key stakeholders involved in the data ownership domain. However, in the context of smart meters, these stakeholders are closely intertwined. The data owner is situated between the end consumer and the DSO, as both entities possess data rights. The data user/consumer, the data provider, and the data repository are the DSO, although the DSO may authorize a third party to assume these roles.
4.1.1. Methodology: Smart Meters
In carrying out the requirement elicitation process, we followed a structured methodology as described in Section 3. This approach enables a comprehensive elicitation of requirements for smart meters. To gain a deeper understanding of the case, we first conducted a thorough analysis, which is detailed in Section 4.1. This analysis provided valuable insights that guided the selection of appropriate elicitation techniques. We chose traditional methods, including data gathering from existing and relevant studies from the literature, laws and regulations, unstructured interviews to collect qualitative data, and a questionnaire to gather structured data. These methods allowed us to gain different perspectives and gain a comprehensive understanding of the requirements.
Background Study and Literature Review
The increasing demand for smart meter infrastructure has given rise to new challenges concerning data ownership, leaving the question of data ownership unresolved [22]. The German legal system does not recognize data ownership of personal data [23]. However, according to the definition of personal data in the European General Data Protection Regulation (GDPR), smart meter data are considered as such and are therefore protected by the GDPR, which sets out some guidelines for data privacy and protection [24]. Nevertheless, laws and regulations that determine which data belong to the customers and which data must be protected by utilities are still lacking [25].
The predominant concerns associated with the implementation of smart meters pertain to privacy, given that these devices collect high-frequency consumption data, thereby providing detailed insights into consumer behavior. This information can be utilized to create accurate profiles and to monitor users for various purposes [26,27,28]. Additional concerns regarding privacy include the potential use of consumer data by utilities and third parties for targeted advertising and the differentiation of treatment of users based on observed behavior [19]. The efficiency of an energy system should not be achieved at the expense of consumer privacy. Smart meters have the potential to enable utilities to effectively manage energy demand and supply; however, their implementation must be carried out in a manner that is both trustworthy and transparent [19].
In an effort to address the challenge of data privacy in the context of smart meters, a number of concepts have emerged. An illustrative example is the concept proposed by Cavoukian et al. [19], which gives consumers control of their data and ensures that consumers are the focal point of any system while guaranteeing the functionality of the energy grid. Alternatively, Wang et al. [28] present a different approach, promoting data sharing behaviors among actors in the energy grid while still ensuring data privacy.
A variety of data protection methods have been proposed to safeguard consumer privacy when utilizing smart meter data, including data anonymization [29], data encryption [30], and blockchain technology [28]. While anonymization is a relatively straightforward process, it does not necessarily guarantee comprehensive privacy, as there is a possibility of re-identification [29,31]. Encryption techniques offer the advantage of preserving the original data; however, they can be computationally complex and expensive [31]. The application of blockchain technology has been put forward as a potential remedy for the ownership and privacy concerns that plague current data exchange processes. This technology is reputed for its ability to ensure data security; nevertheless, it remains to be seen whether it can effectively address the challenges related to its technological maturity and its capacity to support large-scale operations [32].
Unstructured Interview and Questionnaire
In light of the complex nature of the subject matter, a series of pertinent questions concerning the process of data ownership requirement elicitation emerged. To address these inquiries, an unstructured interview was conducted with a data ownership expert, who offered invaluable insights into the RE process for data ownership. The interview included questions regarding the general understanding of data ownership, including the legal and ethical aspects surrounding the issue. Furthermore, the expert was asked about the state-of-the-art and the known requirements in addressing data ownership. The expert outlined the basics of data ownership and explained the complexity and uncertainty in addressing data ownership, especially when addressing it in different contexts in different cases. The expert further confirmed that a requirements engineering-based approach for defining specific data ownership requirements would facilitate comprehension of the necessary aspects for ensuring data ownership in a given case. During the expert interview, the smart meters case-study was presented, and the expert confirmed that numerous aspects necessitate direct review with the DSOs, as they possess the necessary expertise to manage the smart meter data and to answer open questions. Consequently, a questionnaire was developed together with the expert for the DSOs to collect their input and further refine the understanding of the requirements necessary for the data ownership concept. The questionnaire, which was meticulously designed, incorporated both multiple-choice and open-ended inquiries, encompassing the following subjects:
- The intended use and rights of smart meter data and information derived from it.
- Responsibility and control over the data.
- Government and company regulations regarding the utilization of smart meter data.
- Access control.
- Data security and privacy.
A structured interview was conducted with the DSO partners in the case-study to respond to the questionnaire and ascertain the requisite conditions for data ownership. Two German public utilities participated in the case-study and were interviewed separately to ensure that each utility provided its unique perspective and insights without potential influence by the other. Notably, one utility offered responses based purely on the knowledge and the experience of the interviewees, while the second utility sought legal advice to answer some of the questions. Finally, a qualitative analysis of the interviews was conducted, which provided valuable insights into the experience and comprehension of both utilities regarding the utilization of smart meter data. The qualitative analysis examined the completeness of the provided answers. Each response from the questionnaire underwent in-depth analysis and discussion, and in cases of ambiguity, further elaboration and explanation was obtained from the DSOs.
4.1.2. Preliminary Results: Smart Meters
A comprehensive analysis of the findings from the literature review and interviews was conducted, and these findings were then mapped to the data ownership conceptual model (Figure 2). This analysis yielded several key findings on data ownership aspects (Table 1) and illuminated the necessary requirements for data ownership categories (Table 2). This analysis provided valuable insights regarding the complexity of the needed data ownership concept. The results of this study, including the requirements for a data ownership concept in smart meters and findings related to data ownership aspects, are presented in the following tables.

Table 1.
Smart meters: data ownership characteristics.

Table 2.
Smart meters: data ownership requirements.
4.1.3. Case-Study Summary: Smart Meter
The requirements for data ownership in smart meters are intricate and multifaceted, necessitating meticulous consideration to guarantee adherence to legal and ethical standards. In order to gain a comprehensive understanding of these requirements, we employed a series of techniques designed to elicit requirements related to data ownership. This process permitted the collection of diverse perspectives and the development of a comprehensive framework for the concept of data ownership in the context of smart meters. These requirements are crucial for ensuring the responsible handling of smart meter data, respecting individuals’ privacy and security. Our findings contribute to the establishment of a robust framework necessary for implementing the DO concept in smart meter management. Adherence to these requirements enables organizations to efficiently implement the data ownership concept when handling smart meters.
4.2. Case-Study: Precision Livestock Farming
In this chapter, we examine a use case in the field of Precision Livestock Farming (PLF) in Germany. As with smart cities, the term smart farming is becoming increasingly common. In this context, data ownership plays a critical role in ensuring that farmers retain control over their operational and sensitive data. The pig production value chain generates significant amounts of data, including animal health records, veterinarian inputs, climatic data from barns, and mortality rates. Many management solutions available today are offered as Software as a Service (SaaS), meaning that data are often controlled by external providers rather than the farmers themselves.
The objective of establishing clear data ownership in this context is to safeguard farmers’ data sovereignty, prevent dependency on third-party platforms, and enable secure and transparent data sharing. This not only supports compliance with documentation and transparency regulations but also reinforces trust in animal welfare practices and the supply chain.
Consumers are increasingly concerned with questions such as ”Where does my meat originate?” and “How was the pig raised?” [33]. This trend underscores the importance of having a system of documentation that is transparent, secure against tampering, and traceable. Such a system ensures that consumers can easily access reliable information about the origins and conditions of their food, reinforcing trust in food safety and ethical practices.
Due to numerous national and international factors, the structures of pig farming in Germany and its associated economic sectors have significantly evolved over the past decades. From 2010 to 2019, the number of pig farms in Germany decreased by about a third, while the pig population only slightly declined, indicating a shift towards larger operations [34,35]. By 2019, German farms were raising a third more pigs per farm than at the decade’s start, raising concerns about transparency and traceability in pig production among stakeholders [36].
In Lower Saxony, structural changes led to an increase in farm specialization and a concentration of pig production in specific regions, introducing new technical, logistical, social, and economic challenges at all levels of the supply chain [37]. These challenges include issues related to animal welfare, management, advisory services, extensive documentation requirements, sustainability, environmental impacts, labor and income conditions in meat production, disease and consumer protection (One-Health approach), and data exchange including data sovereignty and security among all participants in the chain. Recent events in Germany, such as the COVID-19 pandemic and the outbreak of African Swine Fever, have revealed significant weaknesses in information and data exchange, highlighting the absence of suitable interfaces and procedures between stakeholders [38]. Moreover, there are increasing demands from society, trade, and regulatory bodies for greater transparency and faster traceability throughout the entire pig supply chain for food safety and animal and consumer protection purposes (From Farm to Fork), suggesting significant potential for improvements through targeted digitalization advancements [39].
4.2.1. Methodology: Precision Livestock Farming
In the initial phase of our research, it was crucial to obtain a visual representation of the intricate journey a pig undergoes from fertilization to becoming a consumer product (From Farm to Fork) (https://food.ec.europa.eu/horizontal-topics/farm-fork-strategy_en) (accessed on 21 March 2025). To achieve this, we developed a model using BPMN, a graphical modeling standard for depicting business processes. This model was meticulously refined through consultations with a diverse range of partners within the pig farming sector. The foundation for this model was a pilot barn, already equipped with a comprehensive array of Internet of Things (IoT) sensors, providing a rich dataset for analysis. In addition to laying the groundwork for the BPMN, our preliminary research shed light on the legal documentation requirements pertinent to the industry. This exploration was instrumental in mapping the entire flow of data across the pig production value chain, offering insights into both the operational and regulatory landscapes of pig farming.
A use case diagram was developed to represent various stakeholders and their roles and define ownership rights across fundamental processes. This diagram encompasses a spectrum of protocols, from straightforward guidelines like the erasure of all user data and the stipulated retention period for time series data to more intricate allocations of roles among the diverse stakeholders involved. This structured approach facilitates a clear understanding of responsibilities and rights, ensuring that all parties are aware of their duties and privileges within the system, thus enhancing the governance and operational clarity of the data management process.
Requirements were elicited through workshops and interviews with stakeholders from the pig farming sector, including farmers, veterinarians, and technology providers. These sessions were used to refine the BPMN process model and to identify realistic goals that aligned with customer expectations, regulatory requirements, and the case-study’s framework. The varied expertise within the case-study group was instrumental in not only outlining the study’s aims but also in establishing concrete milestones that reflect a balanced consideration of the study’s scope, customer needs, and regulatory requirements, thereby charting a clear path forward for the study’s progression.
4.2.2. Preliminary Results: Precision Livestock Farming
The results from the BPMN, literature review, and use case diagram were examined and linked to the data ownership (DO) conceptual model (see Figure 2), uncovering significant insights into the facets of data ownership and highlighting the essential criteria for different categories of data ownership. By applying the mentioned techniques, it was possible to find out that numerous third-party vendors currently present comprehensive solutions for the centralized management of these data volumes, which inherently binds users to their proprietary ecosystems. Consequently, the data are exclusively stored within the cloud infrastructure of these providers. Additionally, many sensors on the market are pre-configured solutions from third-party entities, which typically provide only proprietary interfaces. These vendors frequently impose fees for enabling data access, such as through MQTT protocols, further entrenching the dependency on their systems and limiting flexibility in data management and integration.
To address data ownership challenges, a Distributed Ledger Technology (DLT), a decentralized and tamper-resistant ledger system, is proposed, using blockchain to ensure transparency and control. In this approach, individual pigs are assigned Decentralized Identifiers (DIDs), which are globally unique digital identifiers that create secure links to their data records. Sensitive data, such as health records or mortality rates, are stored off-chain, while the blockchain records access permissions and transactions. This setup allows farmers to control who can access their data through verifiable credentials and consent management, following the principles of Self-Sovereign Identity (SSI) systems, where users manage their own digital identities without relying on centralized authorities. The system is operated by trusted entities, such as cooperatives or government bodies, ensuring neutrality and preserving data sovereignty. By using blockchain, data sharing becomes traceable and tamper-proof, supporting both transparency and privacy in the supply chain. In this solution, individual pigs are assigned DIDs (https://www.w3.org/TR/did-core/) (accessed on 21 March 2025), which facilitate the creation of secure links to their data on a blockchain. By entrusting the operation of this blockchain to trusted entities such as cooperatives or governmental bodies, it can be ensured that data sovereignty is maintained with the users. This approach not only enhances data security and privacy but also empowers stakeholders by returning control of the data to its rightful owners.
Blockchain technology is proposed as a means to enhance data transparency and traceability in the livestock sector due to its decentralized and secure nature, as highlighted by [40,41]. However, challenges such as low awareness among stakeholders, sector-wide coordination issues, and limited capabilities of primary suppliers have been identified by [42] as obstacles to its widespread adoption. Despite being in the early stages of adoption, efforts are underway to utilize blockchain for better traceability in the pig supply chain, as demonstrated by [43]. Current strategies aim to engage all stakeholders in the pig production value chain, introducing innovative approaches like Self Sovereign Identity (SSI) and new systems to improve privacy and data ownership during data exchange and certification.
The ensuing criteria for data ownership implementation aspects in Precision Livestock Farming (PLF) are outlined in the subsequent Table 3 and Table 4, accompanied by insights regarding requirement aspects of data ownership.

Table 3.
PLF: data ownership characteristics.

Table 4.
PLF: data ownership requirements.
In this PLF use case, the data include not only livestock data but also veterinarian records, farmer-related data, climatic data from barns, and sensitive operational data such as mortality rates (e.g., dead pig count). Even if not personal data in a legal sense, this information is critical for farmers’ competitiveness, transparency, and compliance. Clear data ownership ensures farmers maintain control over their data, prevents dependency on third-party providers, and supports trust and traceability in the supply chain. These factors informed the requirements listed in Table 4.
4.2.3. Case-Study Summary: Precision Livestock Farming
This case-study examines Precision Livestock Farming in Germany, highlighting the growing importance of data ownership and smart farming practices. The pig production sector generates substantial data, managed primarily through cloud-based services, which raises concerns about data sovereignty and the need for systems that ensure transparency and traceability for consumers.
To address these issues, this study utilized BPMN to map the pig’s journey from fertilization to the consumer, integrating IoT sensor data from a pilot barn. By employing BPMN to systematically model each stage of the pig’s journey, from fertilization to consumer, this approach provided a structured visualization of data exchanges and regulatory checkpoints. This detailed mapping enabled the identification of critical legal requirements and gaps in data governance, ultimately improving transparency and regulatory compliance.
Workshops were conducted to align the study’s goals with regulatory and customer expectations, leading to the exploration of Distributed Ledger Technology (DLT) and DIDs as solutions to reclaim data sovereignty. The study advocates for blockchain technology to improve data transparency and traceability, despite challenges in adoption and coordination across the sector.
4.3. Case-Study: Data Spaces for Energy
The objective of this case-study is to conduct risk forecasts empowered by methods of artificial intelligence (AI). The combination of AI and data should be used to estimate the risks of energy supply availability or reliability in various economic sectors of Germany. The case-study requires the utilization of various datasets obtained from different sources. For instance, one of the datasets that must be used to mitigate the risks of a power outage or bigger events, such as blackouts, is a dataset on outages. This dataset is primarily provided by a Distribution System Operator (DSO). The use of these datasets raises several concerns that need to be addressed. Among these concerns are the transparency of data exchange between involved parties and the preservation of ownership of the used and exchanged data.
In this particular case-study, it is imperative that communication and data exchange between participating DSOs, Transmission System Operators (TSOs), authorities, and consumers be facilitated through open source software, namely, GridFailureInformation (German: Störungsinformationstool) provided through openKONSEQUENZ [44,45]. Furthermore, the software in question should be endowed with a dedicated data connector, the purpose of which is to facilitate data exchange within a designated data space. This connector must adhere to the standards set forth by the International Data Spaces Association (IDSA) [46]. The objective of data spaces is to empower stakeholders to securely share data while retaining control over its access and utilization. Furthermore, data sharing should be facilitated across various industries [47]. Moreover, the data foundation should be complemented by power grid topologies, weather data, and other datasets (e.g., historical events related to power outages, power consumption, and demand from particular industries) to identify crisis scenarios originating in the energy sector. The tools within the case should enable the implementation of countermeasures, which could be designed in advance in the form of a catalog of countermeasures.
4.3.1. Methodology: Data Spaces for Energy
Given the generic nature of requirements, it is essential to address the specific requirements necessary to address an issue within a particular domain. Requirements can be elicited through various methods and approaches. Consequently, in the context of the energy domain, there is a range of methods and approaches that can be adapted to elicit such requirements. For instance, brainstorming and prototyping are two techniques that could be applied to the energy domain to elicit requirements, with a focus on data, data privacy, energy, and sustainability. The current case-study will demonstrate how various methods have been applied to produce requirements that are relevant for data spaces in the energy domain.
In order to obtain a high-quality set of requirements from the elicitation process, it is possible to combine different methods. Throughout the process, a variety of RE methods were utilized. During the first stage, a brainstorming session was conducted to understand the scope of the case-study and its applicability within the context of data spaces for energy. After the brainstorming session, a shortlist of potential useful use cases was identified. These use cases were parts of the initial case-study. Subsequent to the identification of these use cases, a specialized method was employed for their analysis. The design approach of the requirement identification process, which was utilized for the design of the use cases and their filtration, is delineated in [48]. Thereafter, the defined use cases were consolidated into a unified case-study. This case-study comprises the gathered data and incorporates critical elements such as stakeholders, problem definition, goals, data sources, data interfaces, involved parties, and other components. Following the merging process, the requirements and core goals were finalized. Subsequent to initial requirements being settled and finalized, the data scope was analyzed.
The smart grid architecture model approach (UCMR) is utilized to illustrate the subsequent steps of the case-study. UCMR is a framework that helps structure and visualize the complexities of smart grid systems, focusing on interoperability. It can be used an auxiliary tool to organize and structure a use case [49].
4.3.2. Preliminary Results: Data Spaces for Energy
The preliminary results of the case-study data analysis and the use of artificial intelligence methods can be found in [50]. Harnessing the power of data and artificial intelligence (AI) methods, the cited work explores their potential to approach crisis management in a proactive, adaptive, and scalable way. It aims to transform reactive responses into proactive, data-driven strategies that build resilience through intelligent crisis management services. Although the work does not implement a data space for data integration, it serves as a proof of concept demonstrating the benefits of integrating such data.
The next steps are to move to proactive data analysis and active data sharing. Otherwise, data silos will be built to address only a subset of issues and will lack the flexibility to integrate other potentially useful case-studies. Although breaking such data silos can be challenging, storing data in such a form may introduce major risk [51].
The description provided in Table 5 shows the relevance of the five categories of the conceptual model of data ownership Figure 2 to the case-study of energy data spaces.

Table 5.
Data spaces for energy: data ownership characteristics.
The description provided in Table 6 shows the application of the five foundation categories of the conceptual model given in Figure 2 to the case-study of energy data spaces focusing on requirement elicitation. Requirements were elicited through workshops and interviews with stakeholders from the energy sector as well as experts from non-energy fields. An initial use case scenario draft was created using a process of requirement identification described in [52]. This particular requirement identification process consists of a structured way to define use case scenarios and relevant requirements. The process makes use of workshops and interviews. Later sessions with stakeholders were used to create and refine a more precise use case scenario. This time, a UCMR template was used in order to structure the use case scenario, as well as to capture and refine requirements.

Table 6.
Data spaces for energy: data ownership requirements.
4.3.3. Case-Study Summary: Data Spaces for Energy
The preliminary results of the case-study show that a valuable result could be achieved based on the integrated data. However, the drawbacks of the integrated data silos in terms of data ownership requirements should be further investigated. For example, it should be mentioned that the maturity of the software used (e.g., data space connectors [46]) must be significantly improved and achieve much wider adaptation in the energy domain. Otherwise, despite applying well-planned approaches with data ownership in mind, such as the RAM IDS Reference Architecture Model, it is going to be technically challenging to implement the aforementioned concepts. This will lead to additional challenges and problems that must be solved during the integration of data ownership concepts in real-world scenarios [53].
5. Discussion
In the contemporary digital age, data have become the fundamental element upon which numerous applications and systems operate. However, numerous barriers exist that impede the optimal utilization of data within various contexts. A prominent and pervasive challenge pertains to the issue of data ownership. In addition to the imperative to safeguard the substantial volume of data being generated and accumulated, a significant proportion of these data encompasses personal information, necessitating protection. Securing data ownership, therefore, entails more than just protecting data and privacy as commonly assumed; it is also essential for ensuring sustainable data management throughout its lifecycle. A viable approach to data ownership involves preserving the ownership of data and its associated rights, including the ability to grant or revoke those rights. The presented approach encompasses a comprehensive consideration of various issues, including the legal and ethical ramifications of the data under use, the nature of the data themselves, the technical prerequisites for the intended implementation, and the supplementary requirements that may emerge in each distinct case.
Therefore, in order to develop a viable data ownership concept, it is necessary to understand and analyze the requirements surrounding the case and the implementation of the concept. The RE approach provides a suitable outlet to achieve this objective. Although it was originally used as part of systems and software engineering developments, the RE process provides a perfect way to address data ownership concepts and their complexity. On the one hand, it starts with an initial understanding of the domain of the case under consideration. Conversely, it offers a range of requirements elicitation techniques that can be employed to extract pertinent data ownership requirements.
The three case-studies presented offer a compelling illustration of the approach’s applicability. The application of the approach in three distinct cases resulted in the generation of pertinent requirements, tailored for the development of data ownership concepts. The presented approach offers a structured method that facilitates the utilization of the requirements engineering toolset for the elicitation of data ownership requirements relevant to the following five categories: legal, ethical, data, technical, and case requirements. A common thread among the three case-studies is the utilization of a structured approach, beginning with the identification of the problem and its domain. This approach involves the application of diverse requirements elicitation techniques, leading to the generation of relevant requirements for the five data ownership categories.
As previously stated, the issue of data ownership is intricate and cannot be addressed with a universally applicable solution. However, by implementing a guideline approach, it is possible to first comprehend the necessity of the data ownership concept in specific cases. Consequently, it provides a methodical and organized process for identifying the necessary requirements for particular cases.
6. Conclusions
This work introduced a novel approach for analyzing and discovering requirements for the development of data ownership concepts in any given context. The first part of the work introduces the groundwork of the approach, beginning with an overview of the well-established RE process. It highlights the importance of RE as a systematic process for understanding the problem at hand, as well as for defining, specifying, and analyzing the needed requirements for solving the problem. The paper then provides an overview of the different requirements elicitation techniques mentioned in the literature. The paper continues by providing an overview of the concept of data ownership and its complexity. It highlights the need to preserve ownership over increasing amounts of data and underlines the fact that data ownership extends beyond its common definition of possessing control over data and rights thereover, mandating a solemn consideration of diverse perspectives.
Therefore, this paper adopts the definition and the conceptual model of data ownership from our previous work [4] as the base for the approach. The model presents five characteristics that define data ownership: the possession of data, the possession of rights over data, control over possession, the ability to grant rights over data, and taking responsibility for given data. The model underscores the necessity of a robust foundation to develop a data ownership concept that encompasses these five characteristics for a particular case. This foundation, according to the model, should encompass five distinct aspects: legal aspects, ethical aspects, data type, technical requirements, and case requirements.
The presented approach in this work prioritizes domain understanding and requirements elicitation from the RE process. For domain understanding, it is suggested that, in addition to the fundamental understanding of the problem’s domain, the data ownership concept and its five characteristics must be determined and comprehended. For the elicitation process, the approach proposes the utilization of requirements elicitation techniques for exploring and defining requirements for the establishment of the data ownership concept by fostering requirements specifically for the five categories of the aforementioned foundational aspects. The rest of the paper evaluates the approach and its applicability through three different case-studies from different domains.
Author Contributions
Conceptualization, J.A.; methodology, J.A.; investigation, V.D., M.E.E.G. and C.T.; Writing—original draft preparation, J.A., V.D., M.E.E.G., C.T. and J.K.; writing—review and editing, J.A., V.D., M.E.E.G., C.T. and J.K.; supervision, J.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
No new data were created or analyzed in this study.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Abbas, A.E.; van Velzen, T.; Ofe, H.; van de Kaa, G.; Zuiderwijk, A.; de Reuver, M. Beyond control over data: Conceptualizing data sovereignty from a social contract perspective. Electron. Mark. 2024, 34, 20. [Google Scholar] [CrossRef]
- Panis, M.C. An Analysis of Requirements-Related Problems that Occurred in an organization Using a Mature Requirements Engineering Process. In Proceedings of the 2020 IEEE 28th International Conference on Requirements Engineering, Zurich, Switzerland, 31 August–4 September 2020. [Google Scholar] [CrossRef]
- Ragnostad, O.A. ‘Data ownership’ ambiguity. In Promoting Sustainable Innovation and the Circular Economy; Routeledge: London, UK, 2020; pp. 114–133. [Google Scholar]
- Asswad, J.; Marx Gómez, J. Data Ownership: A Survey. Information 2021, 12, 465. [Google Scholar] [CrossRef]
- Van Lamsweerde, A. Requirements Engineering: From System Goals to UML Models to Software; John Wiley & Sons: Chichester, UK, 2009; Volume 10. [Google Scholar]
- Kalloniatis, C.; Kavakli, E.; Gritzalis, S. Addressing privacy requirements in system design: The PriS method. Requir. Eng. 2008, 13, 241–255. [Google Scholar] [CrossRef]
- Institute, S.E. CERT SQUARE for Privacy (P-SQUARE); Carnegie Mellon University: Pittsburgh, PA, USA, 2012. [Google Scholar]
- Zowghi, D.; Coulin, C. Requirements Elicitation: A Survey of Techniques, Approaches, and Tools. In Engineering and Managing Software Requirements; Aurum, A., Wohlin, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 19–46. [Google Scholar] [CrossRef]
- Sharma, S.; Pandey, S.K. Revisiting Requirements Elicitation Techniques. Int. J. Comput. Appl. 2013, 75. [Google Scholar] [CrossRef]
- Lim, S.; Henriksson, A.; Zdravkovic, J. Data-Driven Requirements Elicitation: A Systematic Literature Review. SN Comput. Sci. 2021, 2, 16. [Google Scholar] [CrossRef]
- Tiwari, S.; Rathore, S.S. A Methodology for the Selection of Requirement Elicitation Techniques. arXiv 2017, arXiv:1709.08481. [Google Scholar]
- Wong, L.R.; Mauricio, D.S.; Rodriguez, G.D. A Systematic Literature Review about Software Requirements Elicitation. J. Eng. Sci. Technol. 2017, 12, 296–317. [Google Scholar]
- Sutcliffe, A.; Sawyer, P. Requirements Elicitation: Towards the Unknown Unknowns. In Proceedings of the 2013 21st IEEE International Requirements Engineering Conference (RE), Rio de Janeiro, Brazil, 15–19 July 2013; pp. 92–104. [Google Scholar]
- Bühne, S.; Herrmann, A. Handbook Requirements Management. IREB International Requirements Engineering Board e.V. 2022. Available online: https://cpre.ireb.org/en/downloads-and-resources/downloads/category:handbooks (accessed on 27 October 2023).
- Nuseibeh, B.; Easterbrook, S. Requirements Engineering: A Roadmap. In Proceedings of the Conference on the Future of Software Engineering-ICSE’00, Limerick, Ireland, 4–11 June 2000; pp. 35–46. [Google Scholar] [CrossRef]
- Pacheco, C.; García, I.; Reyes, M. Requirements Elicitation Techniques: A Systematic Literature Review Based on the Maturity of the Techniques. IET Softw. 2018, 12, 365–378. [Google Scholar] [CrossRef]
- Publications Office of the European Union. What Is Data Ownership, and Does It Still Matter under EU Data Law?: An Exploration of Traditional Concepts of Data Ownership, and of the Expected Impact of the Data Act; Publications Office: Luxembourg, 2024. [Google Scholar]
- Paustian, S.; Köhlke, J.; Mattes, J.; Lehnhoff, S. Ready, Set, … Rollout?—The Role of Heterogeneous Actors and Proximities in the Delayed Smart Meter Rollout in Germany. Clean. Eng. Prod. 2025, 26, 100930. [Google Scholar] [CrossRef]
- Cavoukian, A.; Polonetsky, J.; Wolf, C. SmartPrivacy for the Smart Grid: Embedding Privacy into the Design of Electricity Conservation. Identity Inf. Soc. 2010, 3, 275–294. [Google Scholar] [CrossRef]
- Bundesnetzagentur. Intelligentes Messsystem. Available online: https://www.bundesnetzagentur.de/DE/Vportal/Energie/Metering/start.html (accessed on 6 November 2023).
- Bundesministerium der Justiz. Messstellenbetriebsgesetz-MsbG Official Legal Text. Available online: https://www.gesetze-im-internet.de/messbg/ (accessed on 6 November 2023).
- Cavanillas, J.M.; Curry, E.; Wahlster, W. The Big Data Value Opportunity. In New Horizons for a Data-Driven Economy; Springer: Cham, Switerland, 2016; pp. 3–11. [Google Scholar]
- Froese, J.; Straub, S. Wem gehören die Daten?–Rechtliche Aspekte der digitalen Souveränität in der Wirtschaft. In Digitalisierung Souverän Gestalten; Hartmann, E.A., Ed.; Springer: Berlin/Heidelberg, Germany, 2021; pp. 86–97. [Google Scholar] [CrossRef]
- GDPR. General Data Protection Regulation (GDPR)—Official Legal Text. 2016. Available online: https://gdpr-info.eu/ (accessed on 6 November 2023).
- McHenry, M.P. Technical and Governance Considerations for Advanced Metering Infrastructure/Smart Meters: Technology, Security, Uncertainty, Costs, Benefits, and Risks. Energy Policy 2013, 59, 834–842. [Google Scholar] [CrossRef]
- Molina-Markham, A.; Shenoy, P.; Fu, K.; Cecchet, E.; Irwin, D. Private Memoirs of a Smart Meter. In Proceedings of the 2nd ACM Workshop on Embedded Sensing Systems for Energy-Efficiency in Building-BuildSys ’10, Zurich, Switzerland, 2 November 2010; p. 61. [Google Scholar] [CrossRef]
- Ács, G.; Castelluccia, C. I Have a DREAM! (DiffeRentially privatE smArt Metering). In Information Hiding; Filler, T., Pevný, T., Craver, S., Ker, A., Eds.; Springer Berlin Heidelberg: Berlin, Heidelberg, 2011; Volume 6958, pp. 118–132. [Google Scholar] [CrossRef]
- Wang, J.; Gao, F.; Zhou, Y.; Guo, Q.; Tan, C.W.; Song, J.; Wang, Y. Data Sharing in Energy Systems. Adv. Appl. Energy 2023, 10, 100132. [Google Scholar] [CrossRef]
- Efthymiou, C.; Kalogridis, G. Smart Grid Privacy via Anonymization of Smart Metering Data. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 238–243. [Google Scholar] [CrossRef]
- Chhachhi, S.; Teng, F. Market Value of Differentially-Private Smart Meter Data. In Proceedings of the 2021 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 16–18 February 2021; pp. 1–5. [Google Scholar]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Differential Privacy Techniques for Cyber Physical Systems: A Survey. IEEE Commun. Surv. Tutor. 2019, 22, 746–789. [Google Scholar] [CrossRef]
- Aitzhan, N.Z.; Svetinovic, D. Security and Privacy in Decentralized Energy Trading Through Multi-Signatures, Blockchain and Anonymous Messaging Streams. IEEE Trans. Dependable Secur. Comput. 2018, 15, 840–852. [Google Scholar] [CrossRef]
- Winkel, C.; Schukat, S.; Heise, H. Importance and Feasibility of Animal Welfare Measures from a Consumer Perspective in Germany. Food Ethics 2020, 5, 21. [Google Scholar] [CrossRef]
- Rohlmann, C.; Verhaagh, M.; Efken, J. Steckbriefe zur Tierhaltung in Deutschland: Ferkelerzeugung und Schweinemast; Johann Heinrich von Thünen-Institute: Braunschweig, Germany, 2021. [Google Scholar]
- Weible, D.; Christoph-Schulz, I.; Salamon, P.; Zander, K. Citizens’ perception of modern pig production in Germany: A mixed-method research approach. Br. Food J. 2016, 118, 2014–2032. [Google Scholar] [CrossRef]
- Bundesamt, S. Trend zu Großbetrieben in der Landwirtschaft-Schweinehaltung besonders betroffen. Pressemitteilung Nr. N 001. Available online: https://www.destatis.de/DE/Presse/Pressemitteilungen/2020/01/PD20_N001_413.html (accessed on 21 March 2025).
- Bäurle, H.; Tamásy, C. Regionale Konzentrationen der Nutztierhaltung in Deutschland; Institut für Strukturforschung und Planung in agrarischen Intensivgebieten (ISPA): Vechta, Germany, 2012; Volume 79. [Google Scholar]
- Federal Ministry of Food and Agriculture. African Swine Fever (ASF): Information on cases in Germany. Available online: https://www.bmel.de/EN/topics/animals/animal-health/african-swine-fever.html#:~:text=and%20awareness%20building-,Current%20situation%3A,boar%20population%20in%20the%20region (accessed on 21 March 2025).
- Patel, D.; Brahmbhatt, M.; Bariya, A.; Nayak, J.; Singh, V. Blockchain technology in food safety and traceability concern to livestock products. Heliyon 2023, 9, e16526. [Google Scholar] [CrossRef]
- Krampe, C.; Serratosa, J.; Niemi, J.K.; Ingenbleek, P.T.M. Consumer Perceptions of Precision Livestock Farming-A Qualitative Study in Three European Countries. Animals 2021, 11, 1221. [Google Scholar] [CrossRef]
- Xu, X.; Weber, I.; Staples, M. Architecture for Blockchain Applications; Springer: Cham, Switerland, 2019. [Google Scholar]
- Kampan, K.; Tsusaka, T.W.; Anal, A.K. Adoption of Blockchain Technology for Enhanced Traceability of Livestock-Based Products. Sustainability 2022, 14, 13148. [Google Scholar] [CrossRef]
- Yuan, Y.; Liu, X.; Hong, K.; Song, S.; Gao, W. Trustworthy Traceability of Quality and Safety for Pig Supply Chain Based on Blockchain. In Cognitive Internet of Things: Frameworks, Tools and Applications; Lu, H., Ed.; Springer International Publishing: Cham, Switerland, 2020; pp. 343–355. [Google Scholar] [CrossRef]
- Meister, J.; Lehnhoff, S.; Göring, A.; Altherr, T. Digitization of Measures Cascading for the System Safety of Power Grids by openKONSEQUENZ. In Proceedings of the 16th Symposium Energieinnovation, Graz, Austria, 12–14 February 2020. [Google Scholar]
- Goering, A.; Meister, J.; Lehnhoff, S.; Herdt, P.; Jung, M.; Rohr, M. Reference architecture for open, maintainable and secure software for the operation of energy networks. CIRED-Open Access Proc. J. 2017, 2017, 1410–1413. [Google Scholar] [CrossRef]
- Dam, T.; Klausner, L.D.; Neumaier, S.; Priebe, T. A Survey of Dataspace Connector Implementations. arXiv 2024, arXiv:2309.11282. [Google Scholar]
- Solmaz, G.; Cirillo, F.; Fürst, J.; Jacobs, T.; Bauer, M.; Kovacs, E.; Santana, J.R.; Sánchez, L. Enabling data spaces: Existing developments and challenges. In Proceedings of the 1st International Workshop on Data Economy, Rome, Italy, 9 December 2022; pp. 42–48. [Google Scholar]
- Leachu, S.; Janßen, J.; Gdanitz, N.; Kirchhöfer, M.; Janzen, S.; Stich, V. Cascading Scenario Technique Enabling Automated And Situation-based Crisis Management. In Proceedings of the 2023 Conference on Production Systems and Logistics: CPSL, Querétaro, Mexico, 28 February–2 March 2023; Herberger, D., Hübner, M., Stich, V., Eds.; publish-Ing.: Hannover, Germany, 2023; pp. 321–331. [Google Scholar] [CrossRef]
- Gottschalk, M.; Uslar, M.; Delfs, C. The Use Case and Smart Grid Architecture Model Approach: The IEC 62559-2 Use Case Template and the SGAM Applied in Various Domains; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Janzen, S.; Gdanitz, N.; Abdel Khaliq, L.; Munir, T.; Franzius, C.; Maass, W. Anticipating Energy-driven Crises in Process Industry by AI-based Scenario Planning. In Proceedings of the 56th Hawaii International Conference on System Sciences, Maui, HI, USA, 3–6 January 2023. [Google Scholar]
- Putrama, I.M.; Martinek, P. Heterogeneous data integration: Challenges and opportunities. Data Brief 2024, 56, 110853. [Google Scholar] [CrossRef] [PubMed]
- Leachu, S.; Berninger, S.; Janßen, J. AI-Based Crisis Management Utilizing Scenarios. In Proceedings of the 23rd Working Conference on Virtual Enterprises: PRO-VE 2022, Lisbon, Portugal, 19–21 September 2022; Springer International Publishing: Cham, Switzerland, 2022. [Google Scholar]
- Otto, B. The evolution of data spaces. In Designing Data Spaces: The Ecosystem Approach to Competitive Advantage; Springer International Publishing: Cham, Switzerland, 2022; pp. 3–15. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).