Proof-of-Friendship Consensus Mechanism for Resilient Blockchain Technology
Abstract
1. Introduction
- Enhancing decentralisation and fair validator selection.
- Improving trust.
- Promoting sustainable and energy-efficient consensus.
- Strengthening resistance against 51% attacks and collusion.
2. Background Materials
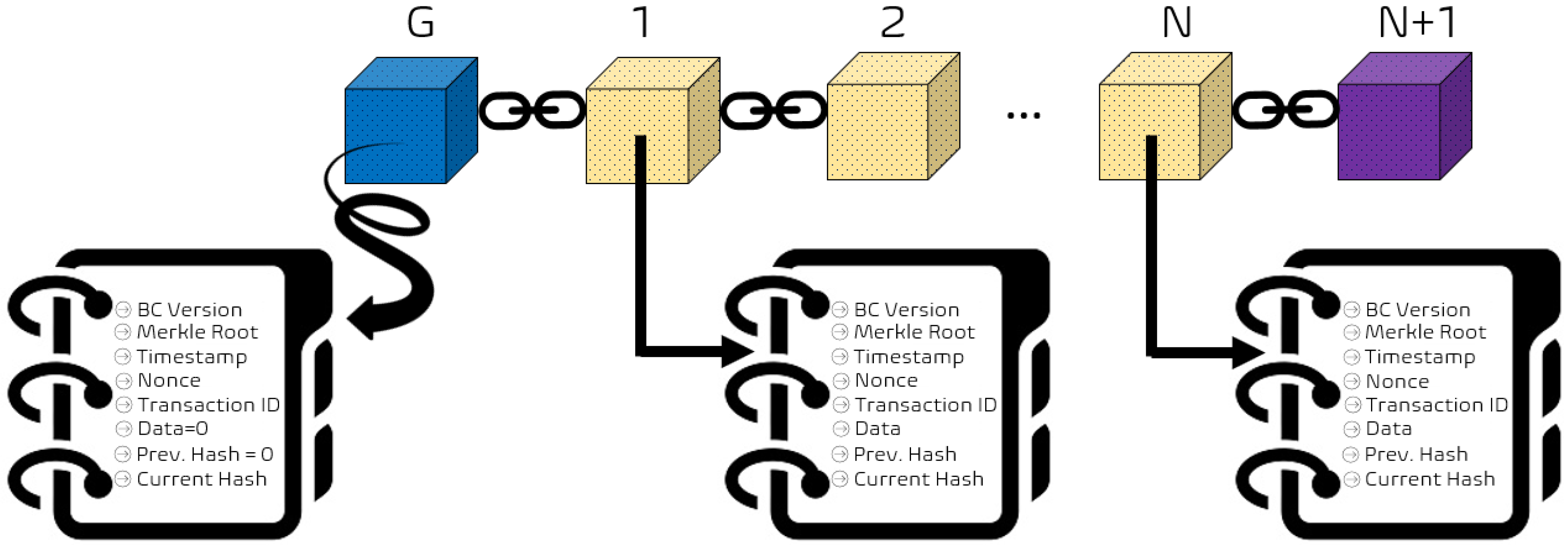
2.1. Blockchain Components
2.2. Blockchain Efficiency and Scalability (PoW vs. PoS)
2.3. Blockchain Security (PoW vs. PoS)
- Implementing stricter revenue distribution systems.
- Modifying mining protocols to exclude recognition of partial proof of work.
- Establishing credit-verification systems to evaluate miner trustworthiness.
- Adopting dynamic algorithms to determine network difficulty, factoring in past transactions.
2.4. Background Study of the Next Generation of Blockchain Consensus Mechanisms
3. Proposed Consensus Method
- Geo-location (Gi): Incorporating geo-location as a factor in selecting validators can help address socio-political challenges and avoid monopoly and control by certain influential validators of a particular region. On a global scale, validators from different regions as the transactors often carry a higher level of perceived trustworthiness, fostering greater confidence in the network when the same agreement is reached across the network.
- Trust based on the success rate of transactions (Si): Transaction failure leads to a waste of network gas fees. It means that even if the transaction is not successful, the gas fee is taken by the network validators. So, failure to complete the transaction is expensive and the network is not trustable. Thus, the higher a validator’s success rate, the higher should be the chance of being nominated by the consensus mechanism. Therefore, the transaction success rate is key to maintaining the validator’s trust. So, in this proposed system, Si is directly proportional to the selection of the validators for the consensus mechanism.
- Verified eco-energy source (Ei): Selecting the right network validators to improve efficiency is one thing, but it is also critical to promote clean validators because of the challenges faced by net-carbon zero, so the use and promotion of clean re-renewable energy during the mining and validation process is vital to make the blockchain solution scalable and sustainable. So, in this proposed system, a novel idea of encouraging the network to use renewable energy is taken into account in the process of selecting the validators. Thus, validators who have a verified renewable power source will be rewarded with a higher chance of selection in the consensus process to make the network scalable and sustainable. This is one of the ways to promote clean mining and validation processes and to make blockchains eco-friendly.
- Trusted Validator: This will be a validator who has once validated one of the user’s transactions already and meets the criteria in terms of geo-location, transaction success rate, and energy sources; they will be included in the ‘friend list’. Depending on the diversity of geographical location, transaction success rates and use of green energy the trust factor of the same node varies over time. Regardless, its trust value is higher than that of a New Validator.
- New Validator: A New Validator meeting a validator’s prerequisites regarding system resources, network requirements, and bandwidth can take part as an initial factor of selection.
Proposed Choosing Validators
- Trust factor;
- Geo-location;
- Energy source.
| Algorithm 1 The pseudo code for the validator selection in PoF |
| Initialised: MIN_GEO_DIVERSITY = 51, MIN_SUCCESS_RATE = 90, GREEN_ENERGY_WEIGHT = 1.0, NUCLEAR_ENERGY_WEIGHT = 0.75, BIOFUEL_ENERGY_WEIGHT = 0.5 //Function: Screening Potential Validator Based on Success Rate function add_validator(validator_address, country, success_rate, energy_source): if success_rate >= MIN_SUCCESS_RATE: new_validator = Validator(validator_address, country, success_rate, energy_source) candidate_validators.append(new_validator) Output: “Validator Added”, validator_address, country else: “Validator does not meet minimum success rate” //Assign validators based on energy source selected_validators = [] for validator in trusted_validators: if validator.energy_source == “green”: chance = GREEN_ENERGY_WEIGHT elif validator.energy_source == “nuclear”: chance = NUCLEAR_ENERGY_WEIGHT elif validator.energy_source == “biofuel”: chance = BIOFUEL_ENERGY_WEIGHT else: chance = 0 # Exclude validators with other energy sources calculate Pi: Probability of selecting the ith validator by using Equation (1). //Step 4: Calculate geo-location diversity function calculate_geo_diversity(): unique_countries = count_unique_keys_in_dictionary(country_count) return (unique_countries * 100)/total_validators //Function: Select validators function select_validators(): selected_validators.clear() country_count.clear() total_validators = 0 //Iterate through candidate validators for each candidate in candidate_validators: Calculate (Trust Factor: Ti) by using Equation (2). current_geo_diversity = calculate_geo_diversity() if current_geo_diversity >= MIN_GEO_DIVERSITY or country_count[candidate.country] == 0: selected_validators.append(candidate) country_count[candidate.country] += 1 total_validators += 1 Output: “Validator Selected”, candidate.validator_address, candidate.country if total_validators >= MAX_VALIDATORS: break elif calculate_geo_diversity() < MIN_GEO_DIVERSITY: continue return selected_validators (friend[list]) |
- n: Total number of validators;
- Wi: Weight of the ith validator based on the energy source;
- Pi: Probability of selecting the ith validator.
- The following values are assigned:
4. Analysis and Discussion
4.1. Harvesting the Benefit of Proof-of-Friendship Mechanism
- (a)
- Increased Decentralisation: Selecting validators from diverse regions reduces the risk of centralisation, as no single country or region can dominate the network. Decentralisation enhances security by making it harder for attackers to coordinate attacks across geographically dispersed nodes.
- (b)
- Enhanced Resilience: Geographic diversity improves network reliability and fault tolerance. Regional validators ensure the network continues to function even if one region experiences downtime due to natural disasters, technical failures, or regulatory actions.
- (c)
- Cultural and Socio-Political Trust: Validators from diverse regions may gain the trust of local transactors who are more comfortable interacting with representatives from their area. This inclusion reduces scepticism or resistance in regions with less familiarity or trust in foreign governance. It is also interesting to note that if two rival countries agree on the same transaction, it is more trustable than two partnering allies agreeing on the same transaction validity.
- (d)
- Global Economic Participation: Spreading validator roles across regions allows stakeholders worldwide to benefit economically from participating in the blockchain network. It fosters inclusivity, allowing smaller or developing economies to engage in and profit from blockchain technology.
- (e)
- Regulatory Compliance and Adaptability: Distributed validators can better navigate region-specific regulations and compliance requirements. Local validators are familiar with their jurisdiction’s legal frameworks, reducing the risk of unintentional violations.
- (a)
- Network Reliability and Efficiency: Validators with a high transaction success rate contribute to the smooth operation of the network by consistently processing and validating transactions without errors or delays. A low success rate could lead to failed or delayed transactions, undermining user trust and the network’s reliability.
- (b)
- Maintaining Consensus Integrity: Validators are responsible for ensuring that only valid transactions are added to the blockchain. A low success rate could indicate poor validation practices, risking the inclusion of invalid or fraudulent transactions, wasting of network computation energy, and loss of gas fees. High success rates ensure that the network reaches consensus efficiently and securely.
- (c)
- User Trust and Confidence: Users expect their transactions to be processed promptly and correctly. Validators with a high success rate build confidence in the network’s ability to handle transactions reliably. Repeated transaction failures can drive users away and damage the network’s reputation.
- (d)
- Resource Optimisation: Each failed transaction consumes network resources like bandwidth, computation, and storage without contributing to meaningful progress. High success rates reduce resource wastage, ensuring the blockchain network operates cost-effectively. This will allow validators with higher success rates to be given equal opportunity across different regions to earn rewards consistently, aligning their interests with the network’s overall health.
- (e)
- Fairness in Validator Selection: Networks that consider transaction success rates when selecting validators can ensure that only competent and reliable validators participate. This reduces the risk of disruptions caused by underperforming or malicious validators.
- (f)
- Protection Against Malicious Activity: Validators with low success rates might be engaging in malicious activities, such as double-spending or spamming the network. Monitoring and prioritising high success rates help safeguard the network against such threats.
- (g)
- Scalability and Growth: As blockchain networks grow and handle more transactions, maintaining high success rates becomes critical for scalability. Validators with consistent performance ensure that the network can manage increased traffic without compromising transaction finality or speed.
- (a)
- Environmental Benefits: Validation using renewable energy sources like solar, wind, and hydropower significantly reduces greenhouse gas emissions compared to fossil fuels. This aligns blockchain operations with global efforts to combat climate change. Renewable energy is inexhaustible compared to finite resources like coal and oil, ensuring a long-term energy supply for blockchain networks.
- (b)
- Cost Savings: Renewable energy sources, especially solar and wind, have decreasing costs over time due to advancements in technology and economies of scale. Once the infrastructure is established, the ongoing energy costs are significantly lower than those relating to fossil fuels. Moreover, renewable energy is less susceptible to price volatility than fossil fuels, providing predictable costs for blockchain operations.
- (c)
- Regulatory and Social Acceptance: Many governments are introducing stricter environmental policies. Using renewable energy helps blockchain miners comply with these regulations and avoid penalties. As blockchains often face criticism for their high energy consumption, adopting renewable energy demonstrates a commitment to sustainability, thus enhancing trust and reputation.
- (d)
- Decentralisation and Accessibility: Renewable energy enables mining and validation in remote or underdeveloped areas with abundant natural resources (e.g., solar energy in deserts, wind in coastal areas). This promotes decentralisation, a core principle of blockchain technology. By relying on locally available renewable energy, miners reduce the dependency on centralised power grids and external energy providers.
- (e)
- Enhanced Network Resilience: Using renewables reduces the reliance on traditional power grids, which may be subject to outages or geopolitical risks. A distributed network of renewable-powered nodes increases the robustness of blockchain operations. Renewable energy systems can be integrated with microgrids, ensuring a continuous energy supply even during larger grid failures.
- (f)
- Long-Term Viability: As blockchain adoption grows, energy demands will increase. Renewable energy ensures that this growth does not come at the expense of environmental degradation. Companies and organisations utilising blockchain can meet Environmental, Social, and Governance (ESG) goals by adopting renewable energy, making their solutions more attractive to investors and customers.
- (g)
- Technological and Economic Innovation: The demand for renewable energy from blockchain miners can drive investment in renewable energy infrastructure and innovation. Blockchain networks powered by renewables appeal to environmentally aware users, developers, and investors. Moving to renewable energy mitigates risks associated with the future scarcity of fossil fuels and potential regulatory crackdowns on energy-intensive operations.
4.2. Addressing Security Issues Using Proof of Friendship
- (a)
- Node spoofing: Malicious nodes, on the lower end of the scale, can target transactors and purposefully fail transactions. They enable Sybil and Eclipse attacks. Since Proof of Friendship requires a background check with its users—at least to verify their location, transaction success rate and energy source—there is a higher chance that the nodes are genuine. The mechanism removes validators that have lower trust values. Even if the IP of the node is spoofed, it will be very challenging to spoof the location using VPN, and attempt to meet the required minimum transaction success rate using VPN.
- (b)
- Pool hopping/Block withholding/FAW: These are attacks limited to the Proof-of-Work mechanism. Proof of Friendship does not utilise mining pools, or even miners. So, such an attack will not be possible in the PoF consensus mechanism.
- (c)
- Frontrunning: Since Proof-of-Friendship blockchains will not use mempools, and transactions are processed much more rapidly than in an average Proof-of-Work network, there is no current potential for insider information. Removing the primary component for a frontrunning operation leaves no room for the operation to take place. Keeping this mechanism open-source will facilitate community improvements to further prevent frontrunning.
- (d)
- Politically charged transaction manipulation: Proof of Friendship takes into account geo-location and allows users to select validators from the different regions. If a transaction has any reason to suspect that their transaction might be targeted, they have an option to choose a trusted validator from their personalised list of validators, who have previously validated one of their transactions. This will not allow validators from one region to dominate or monopolise the process.
- (e)
- Attack minimisation: The level of decentralisation is very high, due to the consideration of geo-location as one of the key factors to select validators, so it will be very challenging to coordinate among nodes to perform attack and network manipulation. If any manipulation-related actions are visible, then the trust value of the node will be affected due to the consideration of the transaction success rate as one of the factors for validator selection, so a coordinated attack is highly unlikely. Moreover, the reliability of the transaction validation is higher when nodes from different regions agree and maintain the network integrity and security.
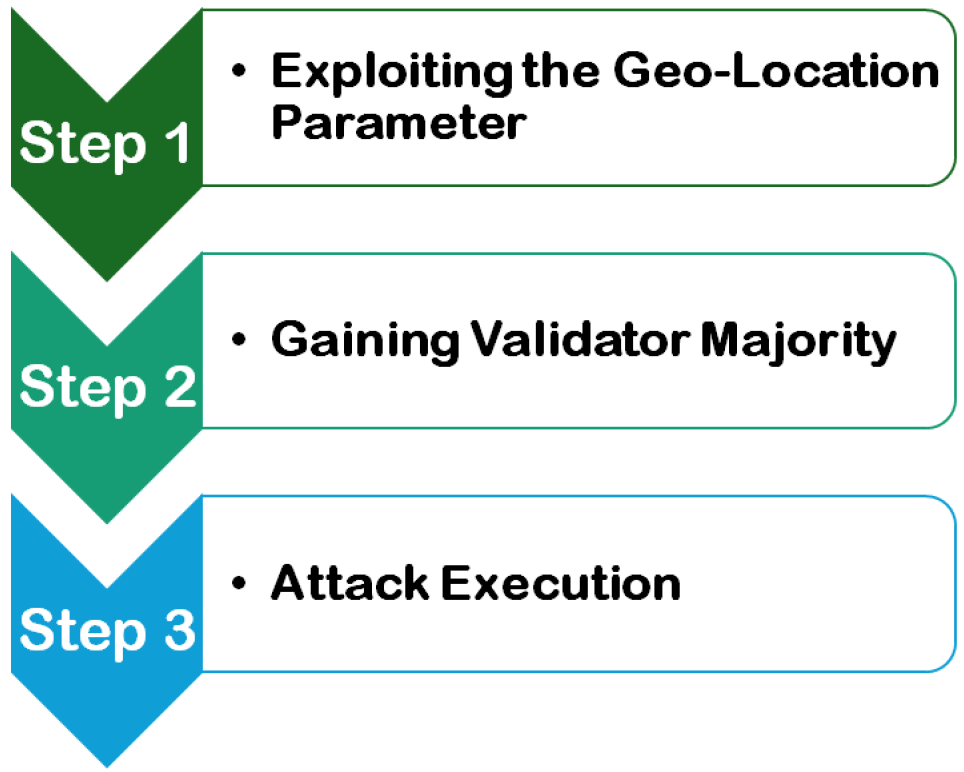
4.3. Possible Attack Scenario of PoF: Geo-Location Spoofing and Validator Control
- (a)
- VPNs and Proxies: The attacker configures their nodes to appear as if they originate from different countries by using VPNs or proxy services.
- (b)
- Satellite Internet Providers: The attacker registers nodes under different ISPs that provide global coverage, making their location seem diverse.
- (c)
- Fake Regional Registrations: The attacker leases cloud servers in various countries and registers validators from those regions.
- (a)
- High Transaction Success Rates: The node can execute low-risk transactions (e.g., sender and receiver belonging to the same entity, smart contract interactions that do not require external validation, etc.), and they can attempt to artificially boost their success rate to meet the 90% success rate requirement. In the future, this aspect will be further mitigated to avoid such scenarios. In the PoF mechanism, it is assumed that any successful transactions are part of the commutative successful transaction rates irrespective of being low-risk transactions or not.
- (b)
- Green Energy Certification Spoofing: If the blockchain uses weakly verified energy sources from a third party, the attacker can falsely claim to use green energy to maximise selection probability. In the PoF mechanism, we assume that a trusted third party has verified the energy sources, and their reports are considered accurate. However, in reality, globally secure energy-source-verifying agents are required to correctly identify and verify the energy sources, but that challenge is not addressed in this paper.
4.4. Example Discussion with Simulation Results
4.5. Comparison of Proof of Friendship (PoF) with PoW and PoS
5. Limitations and Future Directions
- Trust Manipulation: Malicious actors could attempt to forge relationships or create fake trust connections to manipulate the system by IP spoofing using, e.g., a VPN.
- Network Bootstrapping and Adoption Hurdles: PoF requires an established trust graph to function effectively, making initial adoption difficult in new or small networks. A mechanism for verifying new participants without excessive centralisation needs further refinement.
- Scalability of Trust-Based Consensus: PoF introduces additional computational overhead in validating trust relationships, which may become computationally expensive in large-scale networks. Efficient algorithms for real-time trust verification need further development.
- Privacy Concerns: To verify friendships, regional information, transaction success rates, and energy sources are needed, leading to privacy risks unless the node’s data are filtered appropriately to avoid any revelation of personal information. Ensuring zero-knowledge proofs (ZKPs) to verify trust without revealing the node’s identity remains an open challenge.
- Need for Verification of Renewable Energy Sources: Since verifying renewable energy usage in blockchain networks often depends on external certifiers, ensuring long-term trustworthiness requires a dynamic, automated, and tamper-resistant verification mechanism. So, the PoF system can continuously verify and update renewable energy certifications for validators in real-world conditions by integration with Decentralised Energy Tracking Systems: To avoid relying solely on third-party certifiers, PoF can integrate with blockchain-based energy tracking systems, e.g., Energy Attribute Certificates (EACs), referred to as Guarantees of Origin (GO) in Europe [80]. Such a system can allow validators to register their energy source with an on-chain energy registry. It can also be linked with smart contracts to verify and store certificates or real-time energy consumption data, and then conduct periodic re-verification to check if validators are continuing to use renewable energy.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Pilkington, M. Blockchain technology: Principles and applications. In Research Handbook on Digital Transformations; Edward Elgar Publishing: Cheltenham, UK, 2016; pp. 225–253. [Google Scholar]
- Yaga, D.; Mell, P.; Roby, N.; Scarfone, K. Blockchain technology overview. arXiv 2019, arXiv:1906.11078. [Google Scholar]
- Efanov, D.; Roschin, P. The all-pervasiveness of blockchain technology. Procedia Comput. Sci. 2018, 123, 116–121. [Google Scholar] [CrossRef]
- Lashkari, B.; Musilek, P. A comprehensive review of blockchain consensus mechanisms. IEEE Access 2021, 9, 43620–43652. [Google Scholar] [CrossRef]
- Xie, M.; Liu, J.; Chen, S.; Lin, M. A survey on blockchain consensus mechanism: Research overview, current advances and future directions. Int. J. Intell. Comput. Cybern. 2023, 16, 314–340. [Google Scholar] [CrossRef]
- Zhang, C.; Wu, C.; Wang, X. Overview of blockchain consensus mechanism. In Proceedings of the 2020 2nd International Conference on Big Data Engineering, Shanghai China, 29–31 May 2020; pp. 7–12. [Google Scholar]
- Nguyen, G.T.; Kim, K. A survey about consensus algorithms used in blockchain. J. Inf. Process. Syst. 2018, 14, 101–128. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 10 January 2025).
- Buterin, V. Ethereum white paper. GitHub Repos. 2013, 1, 22–23. [Google Scholar]
- Rajavat, A.; Bhardwaj, V.; Kaur, N.; Rawat, R.; Rawat, A.; Jadon, G.S. Sustainable Futures: Navigating Blockchain’s Energy Dilemma. In Online Social Networks in Business Frameworks; John Wiley & Sons: Hoboken, NJ, USA, 2024; pp. 85–112. [Google Scholar]
- Taherdoost, H. Blockchain Integration and Its Impact on Renewable Energy. Computers 2024, 13, 107. [Google Scholar] [CrossRef]
- Khosravi, A.; Säämäki, F. Beyond Bitcoin: Evaluating Energy Consumption and Environmental Impact across Cryptocurrency Projects. Energies 2023, 16, 6610. [Google Scholar] [CrossRef]
- Kohli, V.; Chakravarty, S.; Chamola, V.; Sangwan, K.S.; Zeadally, S. An analysis of energy consumption and carbon footprints of cryptocurrencies and possible solutions. Digit. Commun. Netw. 2023, 9, 79–89. [Google Scholar] [CrossRef]
- Udeh, E.O.; Amajuoyi, P.; Adeusi, K.B.; Scott, A.O. Blockchain-driven communication in banking: Enhancing transparency and trust with distributed ledger technology. Financ. Account. Res. J. 2024, 6, 851–867. [Google Scholar]
- Lal, R.; Chhabra, A.; Singla, S.; Sharma, D. Blockchain Technology: Revolutionizing Trust, Transparency, and Transaction Efficiency. In Proceedings of the 2024 International Conference on Knowledge Engineering and Communication Systems (ICKECS), Chikkaballapur, India, 23–24 April 2024; Volume 1, pp. 1–5. [Google Scholar]
- Udeh, E.O.; Amajuoyi, P.; Adeusi, K.B.; Scott, A.O. The role of Blockchain technology in enhancing transparency and trust in green finance markets. Financ. Account. Res. J. 2024, 6, 825–850. [Google Scholar]
- Ali, V.; Norman, A.A.; Azzuhri, S.R.B. Characteristics of blockchain and its relationship with trust. IEEE Access 2023, 11, 15364–15374. [Google Scholar] [CrossRef]
- Rijal, S.; Saranani, F. The Role of Blockchain Technology in Increasing Economic Transparency and Public Trust. Technol. Soc. Perspect. (TACIT) 2023, 1, 56–67. [Google Scholar] [CrossRef]
- Cambridge Blockchain Network Sustainability Index. Bitcoin Power Consumption. Available online: https://ccaf.io/cbnsi/cbeci (accessed on 31 December 2024).
- Cambridge Blockchain Network Sustainability Index. Ethereum Power Consumption. Available online: https://ccaf.io/cbnsi/ethereum (accessed on 31 December 2024).
- Ethereum. Proof-of-Stake (PoS). 2022. Available online: https://ethereum.org/en/developers/docs/consensus-mechanisms/pos/ (accessed on 23 August 2024).
- Aponte-Novoa, F.A.; Orozco, A.L.S.; Villanueva-Polanco, R.; Wightman, P. The 51% attack on blockchains: A mining behavior study. IEEE Access 2021, 9, 140549–140564. [Google Scholar] [CrossRef]
- Vashchuk, O.; Shuwar, R. Pros and cons of consensus algorithm proof of stake. Difference in the network safety in proof of work and proof of stake. Electron. Inf. Technol. 2018, 9, 106–112. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Boston, MA, USA, 11–14 December 2017; pp. 557–564. [Google Scholar]
- Chainspect. What Is Block Time? [Definition & Real Metrics]. Chainspect. 2024. Available online: https://chainspect.app/blog/block-time (accessed on 19 February 2025).
- Crypto.com. ConfirmationTime. Crypto.com. Available online: https://crypto.com/glossary/confirmation-time (accessed on 19 February 2025).
- Gorenflo, C.; Lee, S.; Golab, L.; Keshav, S. FastFabric: Scaling hyperledger fabric to 20 000 transactions per second. Int. J. Netw. Manag. 2020, 30, e2099. [Google Scholar] [CrossRef]
- Bitstamp. What Is Block Size? 2024. Available online: https://www.bitstamp.net/en-gb/learn/crypto-101/what-is-block-size/ (accessed on 19 February 2025).
- Tardi, C.; Mansa, J.; Jackson, A. Gwei. 2022. Available online: https://www.investopedia.com/terms/g/gwei-ethereum.asp (accessed on 14 August 2024).
- Coinbase. What Is Hash Rate? Available online: https://www.coinbase.com/en-gb/learn/crypto-glossary/what-is-hash-rate (accessed on 19 February 2025).
- Centieiro, H. Bitcoin Proof of Work—The Only Article You Will Ever Have to Read. 2021. Available online: https://levelup.gitconnected.com/bitcoin-proof-of-work-the-only-article-you-will-ever-have-to-read-4a1fcd76a294 (accessed on 23 July 2024).
- Aggelos Kiayias, G.P. Speed-Security Tradeouts in Blockchain Protocols. Cryptol. ePrint Arch. 2015. Available online: https://eprint.iacr.org/2015/1019 (accessed on 10 January 2025).
- Bączkowski, A. Fundamentals: TPS vs. Latency vs. Finality. 2022. Available online: https://alephzero.org/blog/tps-latency-finality/ (accessed on 20 July 2024).
- Catt, M. Blockchain Fundamentals: Latency & Capacity—Featuring the Ark Ecosystem. 2018. Available online: https://medium.com/ku-blockchain-institute/blockchain-fundamentals-featuring-the-ark-ecosystem-part-1-af1f9052e579 (accessed on 20 July 2022).
- Edwood, F. Block Size and Scalability, Explained. 2020. Available online: https://cointelegraph.com/explained/block-size-and-scalability-explained (accessed on 20 July 2024).
- Alameda, T. Zero Knowledge Proof: How to Maintain Privacy in a Data-Based World. 2020. Available online: https://www.bbva.com/en/zero-knowledge-proof-how-to-maintain-privacy-in-a-data-based-world/ (accessed on 2 August 2022).
- Chainlink. What Is a Blockchain Oracle? 2021. Available online: https://chain.link/education/blockchain-oracles (accessed on 11 August 2024).
- Sharma, T.K. Blockchain Oracle: A Deep Dive. 2022. Available online: https://www.blockchain-council.org/blockchain/blockchain-oracle-a-deep-dive/ (accessed on 12 June 2024).
- Chen, Y.; Chen, H.; Zhang, Y.; Han, M.; Siddula, M.; Cai, Z. A survey on blockchain systems: Attacks, defenses, and privacy preservation. High-Confid. Comput. 2022, 2, 100048. [Google Scholar] [CrossRef]
- Ethereum. Smart Contract Security. 2021. Available online: https://ethereum.org/en/developers/docs/smart-contracts/security/#attacks-and-vulnerabilities (accessed on 2 August 2024).
- Marshall, B. Beginner’s Guide to an MEV Bot: Creating an Arbitrage Bot on Ethereum Mainnet. 2022. Available online: https://www.blocknative.com/blog/mev-and-creating-a-basic-arbitrage-bot-on-ethereum-mainnet (accessed on 12 August 2024).
- Craig, T. MEV and Proof-of-Stake with Eden Network’s Caleb Sheridan. 2021. Available online: https://cryptobriefing.com/mev-and-proof-of-stake-with-eden-networks-caleb-sheridan/ (accessed on 12 August 2024).
- Radix DLT. What are Proof of Work and Proof of Stake? 2021. Available online: https://learn.radixdlt.com/article/what-are-proof-of-work-and-proof-of-stake (accessed on 12 August 2024).
- Cryptopedia. Eclipse Attacks: Explanations and Preventions. 2022. Available online: https://www.gemini.com/cryptopedia/eclipse-attacks-defense-bitcoin (accessed on 12 August 2022).
- Frankenfield, J. Selfish Mining. 2022. Available online: https://www.investopedia.com/terms/s/selfish-mining.asp (accessed on 1 July 2024).
- Sriman, B.; Ganesh Kumar, S.; Shamili, P. Blockchain technology: Consensus protocol proof of work and proof of stake. In Intelligent Computing and Applications: Proceedings of ICICA 2019; Springer: Singapore, 2021; pp. 395–406. [Google Scholar]
- Raikwar, M.; Gligoroski, D. Dos attacks on blockchain ecosystem. In Proceedings of the European Conference on Parallel Processing, Lisbon, Portugal, 1–3 September 2021; Springer International Publishing: Cham, Switzerland, 2021; pp. 230–242. [Google Scholar]
- Singh, N.; Singh, H.P.; Mishra, A.; Khare, A.; Swarnkar, M.; Almas, S.K. Blockchain Cloud Computing: Comparative study on DDoS, MITM and SQL Injection Attack. In Proceedings of the 2024 IEEE International Conference on Big Data & Machine Learning (ICBDML), Bhopal, India, 24–25 February 2024; pp. 73–78. [Google Scholar]
- Kumar, A.; Sah, B.K.; Mehrotra, T.; Rajput, G.K. A review on double spending problem in blockchain. In Proceedings of the 2023 International Conference on Computational Intelligence and Sustainable Engineering Solutions (CISES), Noida, India, 28–30 April 2023; pp. 881–889. [Google Scholar]
- Caldarelli, G.; Ellul, J. The blockchain oracle problem in decentralized finance—A multivocal approach. Appl. Sci. 2021, 11, 7572. [Google Scholar] [CrossRef]
- Rodler, M.; Li, W.; Karame, G.O.; Davi, L. Sereum: Protecting existing smart contracts against re-entrancy attacks. arXiv 2018, arXiv:1812.05934. [Google Scholar]
- Aggarwal, S.; Kumar, N. Attacks on blockchain. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2021; Volume 121, pp. 399–410. [Google Scholar]
- Rehman, Z.; Gregory, M.A.; Gondal, I.; DOng, H.; Ge, M. Eclipse Attacks in Blockchain Networks: Detection, Prevention, and Future Directions. IEEE Access 2025, 13, 25918–25933. [Google Scholar] [CrossRef]
- Alangot, B.; Reijsbergen, D.; Venugopalan, S.; Szalachowski, P.; Yeo, K.S. Decentralized and lightweight approach to detect eclipse attacks on proof of work blockchains. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1659–1672. [Google Scholar] [CrossRef]
- Crypto News. Hope, C. Solana Network Faces High Failure Rate in Transactions Amid Memecoin Mania. 2024. Available online: https://coinmarketcap.com/academy/article/solana-network-faces-high-failure-rate-in-transactions-amid-memecoin-mania (accessed on 19 February 2025).
- Singh, S.K.; Salim, M.M.; Cho, M.; Cha, J.; Pan, Y.; Park, J.H. Smart contract-based pool hopping attack prevention for blockchain networks. Symmetry 2019, 11, 941. [Google Scholar] [CrossRef]
- Chen, H.; Chen, Y.; Xiong, Z.; Han, M.; He, Z.; Liu, B.; Wang, Z.; Ma, Z. Prevention method of block withholding attack based on miners’ mining behavior in blockchain. Appl. Intell. 2023, 53, 9878–9896. [Google Scholar] [CrossRef]
- Eskandari, S.; Moosavi, S.; Clark, J. Sok: Transparent dishonesty: Front-running attacks on blockchain. In Financial Cryptography and Data Security: FC 2019 International Workshops, VOTING and WTSC, St. Kitts, St. Kitts and Nevis, February 18–22, 2019, Revised Selected Papers 23; Springer International Publishing: Berlin/Heidelberg, Germany, 2020; pp. 170–189. [Google Scholar]
- Manolache, M.A.; Manolache, S.; Tapus, N. Decision making using the blockchain proof of authority consensus. Procedia Comput. Sci. 2022, 199, 580–588. [Google Scholar] [CrossRef]
- Wang, Q.; Xu, M.; Li, X.; Qian, H. Revisiting the Fairness and Randomness of Delegated Proof of Stake Consensus Algorithm. In Proceedings of the 2020 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), Exeter, UK, 17–19 December 2020; pp. 305–312. [Google Scholar] [CrossRef]
- Andrey, A.; Petr, C. Review of existing consensus algorithms blockchain. In Proceedings of the 2019 International Conference Quality Management, Transport and Information Security, Information Technologies (IT&QM&IS), 23–27 September 2019; pp. 124–127. [Google Scholar]
- Karantias, K.; Kiayias, A.; Zindros, D. Proof-of-Burn. In Financial Cryptography and Data Security. FC 2020; Lecture Notes in Computer Science; Bonneau, J., Heninger, N., Eds.; Springer: Cham, Switzerland, 2020; Volume 12059. [Google Scholar] [CrossRef]
- Cedricwalter/Blockchain-Consensus. Available online: https://github.com/cedricwalter/blockchain-consensus/blob/master/chain-based-proof-of-capacity-space/proof-of-capacity-poc.md (accessed on 24 December 2024).
- Chen, L.; Xu, L.; Shah, N.; Gao, Z.; Lu, Y.; Shi, W. On security analysis of proof-of-elapsed-time (PoET). In Stabilization, Safety, and Security of Distributed Systems; Spirakis, P., Tsigas, P., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 282–297. [Google Scholar] [CrossRef]
- Frankenfield, J. Proof of Elapsed Time (PoET). 2022. Available online: https://www.investopedia.com/terms/p/proof-elapsed-time-cryptocurrency.asp (accessed on 22 June 2024).
- Moran, T.; Orlov, I. Simple Proofs of Space-Time and Rational Proofs of Storage. In Advances in Cryptology—CRYPTO 2019. CRYPTO 2019; Lecture Notes in Computer Science; Boldyreva, A., Micciancio, D., Eds.; Springer: Cham, Switzerland, 2019; Volume 11692. [Google Scholar] [CrossRef]
- Xiao, B.; Jin, C.; Li, Z.; Zhu, B.; Li, X.; Wang, D. Proof of Importance: A Consensus Algorithm for Importance Based on Dynamic Authorization. In Proceedings of the IEEE/WIC/ACM International Conference on Web Intelligence and Intelligent Agent Technology (WI-IAT ’21), Melbourne, VIC, Australia, 14–17 December 2021; Association for Computing Machinery: New York, NY, USA, 2022; pp. 510–513. [Google Scholar] [CrossRef]
- Zilberman, A.; Offer, A.; Pincu, B.; Glickshtein, Y.; Kant, R.; Brodt, O.; Otung, A.; Puzis, R.; Shabtai, A.; Elovici, Y. A Survey on Geolocation on the Internet. IEEE Commun. Surv. Tutor. 2024. [Google Scholar] [CrossRef]
- Hu, Z.; Heidemann, J.; Pradkin, Y. Towards geolocation of millions of IP addresses. In Proceedings of the 2012 Internet Measurement Conference, Boston, MA, USA, 14–16 November 2012; pp. 123–130. [Google Scholar]
- Dan, O.; Parikh, V.; Davison, B.D. IP geolocation using traceroute location propagation and ip range location interpolation. In Companion Proceedings of the Web Conference 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 332–338. [Google Scholar]
- Dan, O.; Parikh, V.; Davison, B.D. IP geolocation through reverse DNS. ACM Trans. Internet Technol. (TOIT) 2021, 22, 1–29. [Google Scholar] [CrossRef]
- Gawusu, S.; Zhang, X.; Ahmed, A.; Jamatutu, S.A.; Miensah, E.D.; Amadu, A.A.; Osei, F.A.J. Renewable energy sources from the perspective of blockchain integration: From theory to application. Sustain. Energy Technol. Assess. 2022, 52, 102108. [Google Scholar] [CrossRef]
- Zhang, D.; Chen, X.H.; Lau, C.K.M.; Xu, B. Implications of cryptocurrency energy usage on climate change. Technol. Forecast. Soc. Chang. 2023, 187, 122219. [Google Scholar] [CrossRef]
- Siddique, I.; Smith, E.; Siddique, A. Assessing the sustainability of bitcoin mining: Comparative review of renewable energy sources. J. Altern. Renew. Energy Sources 2023, 10, 10–46610. [Google Scholar] [CrossRef]
- De Vries, A. Renewable energy will not solve bitcoin’s sustainability problem. Joule 2019, 3, 893–898. [Google Scholar] [CrossRef]
- Koemtzopoulos, D.; Zournatzidou, G.; Ragazou, K.; Sariannidis, N. Cryptocurrencies Transit to a Carbon Neutral Environment: From Fintech to Greentech Through Clean Energy and Eco-Efficiency Policies. Energies 2025, 18, 291. [Google Scholar] [CrossRef]
- Vijayamohan Mankayarkarasi, B.; Ramalakshmi Murugan, A. Energy Transition Through Voluntary Carbon Credit System. In Energy Sustainability; American Society of Mechanical Engineers: New York, NY, USA, 2024; Volume 87899, p. V001T04A006. [Google Scholar]
- Suryanarayana, A.; Rao, V. Embracing Blockchain Technologies for Sustainable Finance Through Carbon Credits and Renewable Energy Trading. Educ. Adm. Theory Pract. 2024, 30, 1151–1155. [Google Scholar] [CrossRef]
- Richard, M.O. Carbon Credit Concept and Africa’s Sustainable Development—An Empirical Review. 2024. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4823877 (accessed on 9 January 2025).
- Holzapfel, P.K.; Bánk, J.; Bach, V.; Finkbeiner, M. Relevance of guarantees of origin for Europe’s renewable energy targets. Renew. Sustain. Energy Rev. 2024, 205, 114850. [Google Scholar] [CrossRef]


| Year | Bitcoin | Ethereum 1.0 | Ethereum 2.0 |
|---|---|---|---|
| 2011 | 0.14 TWh | - | - |
| 2012 | 0.10 TWh | - | - |
| 2013 | 1.06 TWh | - | - |
| 2014 | 4.73 TWh | - | - |
| 2015 | 3.62 TWh | 0.10 TWh | - |
| 2016 | 5.73 TWh | 0.20 TWh | - |
| 2017 | 12.93 TWh | 2.65 TWh | - |
| 2018 | 43.32 TWh | 8.98 TWh | - |
| 2019 | 54.63 TWh | 5.75 TWh | - |
| 2020 | 67.14 TWh | 6.69 TWh | - |
| 2021 | 89.00 TWh | 16.40 TWh | 0.01 GWh |
| 2022 | 95.53 TWh | 17.58 TWh | 2.33 GWh |
| 2023 | 121.13 TWh | - | 5.85 GWh |
| 2024 | 183.62 TWh | - | 5.72 GWh |
| Attack Type | PoW | PoS | Description |
|---|---|---|---|
| 51% attacks | These attacks target blockchain networks regardless of mechanism type. A 51% attack in blockchain refers to a situation where a single entity or group gains control of more than 50% of a blockchain network’s mining or computational power [22]. | ||
| DoS attacks | A Denial of Service (DoS) attack is a malicious attempt to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of traffic or sending data in a way that the system cannot handle [47]. | ||
| Injection attacks | Injection attacks are a type of cyberattack where an attacker injects malicious code or commands into a vulnerable program, query, or system [48]. | ||
| Double-spending | Double-spending in blockchain refers to a scenario where the same cryptocurrency or digital asset is spent more than once [49]. | ||
| Oracle exploits | These kinds of attacks exploit vulnerabilities in smart contracts. An oracle is one of the parts of a smart contract that interacts with the external Internet, and naturally, it offers a trove of vulnerabilities [50]. | ||
| Re-entrancy attacks | It is a vulnerability in smart contracts, particularly in Ethereum and other blockchain platforms that support programmable contracts [51] | ||
| Sybil and Eclipse attacks | Sybil and Eclipse attacks target inter-node communications and spoof nodes [52,53,54] | ||
| Transaction failure | The most common security flaw is that a user’s transaction fee is taken even if a transaction fails [50,55] | ||
| Pool-hopping | Pool-hopping is a strategy used by miners in blockchain-based mining pools to maximise their rewards by switching between different mining pools based on their payout schemes and block discovery patterns [56]. It primarily affects PoW and less on PoS. | ||
| Fork After Withdrawing attacks | Fork After Withdrawing (FAW) attacks are a type of blockchain attack that exploits the possibility of creating a forked version of the blockchain after completing a transaction, typically withdrawing assets, to revert the transaction’s effects on the original chain [39]. | ||
| Block Withholding | Block withholding (BWH) is an attack in blockchain mining where a miner deliberately withholds valid blocks they discover instead of broadcasting them to the network [57]. | ||
| Frontrunning | Frontrunning in a blockchain network refers to malicious or opportunistic behaviour where an entity (usually a miner, validator, or bot) exploits knowledge of pending transactions to gain a financial advantage by placing their transaction ahead of others in the blockchain transaction queue [58]. |
| Consensus Algorithm | Security | Decentralisation | Energy Consumption | Fairness | Scalability | Resilience |
|---|---|---|---|---|---|---|
| Proof of Work [46] | High (strong against attacks, costly to compromise) | High | Very High | Low | Low | High |
| Proof of Stake [46] | High (with risk of stake centralisation) | Medium to Low | Low | Medium to Low | High | Medium to High |
| Proof of Authority [59] | Medium (validator trust required) | Low | Low | Low | Very High | Medium |
| Delegated Proof of Stake [60] | Medium to high (dependent on delegate integrity and voter participation) | Low | Low | Medium | Very High | Medium |
| Leased Proof of Stake [61] | Medium to high (pooled stakes enhance security but risk centralisation) | Medium | Low | Medium | High | Medium |
| Proof of Burn [62] | Medium to high (economic disincentives for attacks; risks from wealth concentration) | Medium | Low | Medium | High | Medium to High |
| Poof of Capacity [63] | Medium to high (dependent on storage distribution and diversity) | Medium | Low | Medium | High | Medium to High |
| Proof of Elapsed time [64,65] | Medium to high (relies on trusted hardware) | Medium | Low | High | High | Medium to High |
| Proof of Space and Time [66] | Medium to high (combines storage and time for robust defence mechanisms) | Low | Medium | Medium to High | High | High |
| Proof of Importance [67] | High (ensures secure participation) | High | Low | Medium | High | Medium to High |
| Validator | Geo-Location (Gi) | Success Rate (Si) | Energy Source (Ei) |
|---|---|---|---|
| 1 | 1 (Unique) | 0.99 | 1.0 (Green) |
| 2 | 1 (Unique) | 0.95 | 0.5 (Biofuel) |
| 3 | 0 (Common) | 0.98 | 0.5 (Biofuel) |
| 4 | 1 (Unique) | 0.97 | 0.0 (Non-renewable) |
| 5 | 0 (Common) | 0.96 | 1.0 (Green) |
| 6 | 1 (Unique) | 0.99 | 1.0 (Green) |
| 7 | 1 (Unique) | 0.94 | 0.0 (Non-renewable) |
| 8 | 0 (Common) | 0.93 | 0.5 (Biofuel) |
| 9 | 1 (Unique) | 0.98 | 1.0 (Green) |
| 10 | 0 (Common) | 0.92 | 0.75 (Nuclear) |
| Validator | Gi | Si | Ei | Ti | Rank |
|---|---|---|---|---|---|
| 1 | 1 | 0.99 | 1.0 | 0.996 | 1st |
| 2 | 1 | 0.95 | 0.5 | 0.88 | 3rd |
| 3 | 0 | 0.98 | 0.5 | 0.492 | - |
| 4 | 1 | 0.97 | 0.0 | 0.788 | 4th |
| 5 | 0 | 0.96 | 1.0 | 0.584 | - |
| 6 | 1 | 0.99 | 1.0 | 0.996 | 1st |
| 7 | 1 | 0.94 | 0.0 | 0.776 | 5th |
| 8 | 0 | 0.93 | 0.5 | 0.472 | - |
| 9 | 1 | 0.98 | 1.0 | 0.992 | 2nd |
| 10 | 0 | 0.92 | 0.75 | 0.518 | - |
| Metrics | Values |
|---|---|
| Processing latency (PL) | 85 ms |
| Network latency (NL) [transaction size/network speed] | 172 ms |
| Synchronisation delays (SDs) | 1802 ms |
| Cumulative delay per transaction [PL + NL + SD] | 2059 ms |
| Criteria | Proof of Work (PoW) | Proof of Stake (PoS) | Proof of Friendship (PoF) |
|---|---|---|---|
| Selection Basis | Computational power | Cryptocurrency stake | Geo-location, transaction success rate, and energy source |
| Decentralisation | High initially, but centralisation occurs due to mining pools | Tends to favour wealthy participants, leading to validator monopoly | Promotes decentralisation by selecting validators from diverse locations |
| Energy Efficiency | Very low (high energy consumption) | Moderate (no mining, but requires computational power for staking mechanisms) | Moderate (energy consumption by relying on green energy and trust) |
| Security | High (resistant to attacks due to computational difficulty) | Moderate (51% stake attack possible, leading to network control) | High (Sybil-resistant via social trust validation through multifactor association and reducing fake identities) |
| Scalability | Low (slow transaction processing due to mining complexity) | High (faster than PoW, but can face congestion in high-demand networks) | High (trust-based validation allows efficient and fast transaction processing) |
| Trust Factor | No inherent trust factor relies purely on computational power | Trust is based on financial investment, not actual reliability | Trust is based on network diversity, past transaction success, and sustainability efforts |
| Attack Resistance | Vulnerable to 51% hash power attacks | Vulnerable to 51% stake attacks and centralisation risks | Resists Sybil |
| Environmental Impact | High carbon footprint due to mining | Moderate (energy consumption varies based on staking mechanisms) | Low (rewards validators using renewable energy sources) |
| Fairness | Favours miners with expensive hardware | Favours wealthy individuals with large crypto holdings | Promotes fairness by selecting validators based on the node’s location, success rates, and sustainability |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Marchang, J.; Srikanth, R.; Keishing, S.; Kashyap, I. Proof-of-Friendship Consensus Mechanism for Resilient Blockchain Technology. Electronics 2025, 14, 1153. https://doi.org/10.3390/electronics14061153
Marchang J, Srikanth R, Keishing S, Kashyap I. Proof-of-Friendship Consensus Mechanism for Resilient Blockchain Technology. Electronics. 2025; 14(6):1153. https://doi.org/10.3390/electronics14061153
Chicago/Turabian StyleMarchang, Jims, Rengaprasad Srikanth, Solan Keishing, and Indranee Kashyap. 2025. "Proof-of-Friendship Consensus Mechanism for Resilient Blockchain Technology" Electronics 14, no. 6: 1153. https://doi.org/10.3390/electronics14061153
APA StyleMarchang, J., Srikanth, R., Keishing, S., & Kashyap, I. (2025). Proof-of-Friendship Consensus Mechanism for Resilient Blockchain Technology. Electronics, 14(6), 1153. https://doi.org/10.3390/electronics14061153








