Abstract
The extensive interconnection and intelligent collaboration of multi-source heterogeneous devices in the industrial Internet environment have significantly improved the efficiency of industrial production and resource utilization. However, at the same time, the deployment characteristics of open-network architecture and the promotion of the concept of deep integration of OT/IT have led to an exponential growth of attacks on the industrial Internet. At present, most of the detection methods for industrial internet attacks use deep learning. However, due to the black-box characteristics caused by the complex structure of deep learning models, the explainability of industrial internet detection results generated based on deep learning is low. Therefore, we proposed an industrial internet intrusion response method xIIRS based on explainable deep learning. Firstly, an explanation method was improved to enhance the explanation by approximating and sampling the historical input and calculating the dynamic weighting for the sparse group lasso based on the evaluation criteria for the importance of features between and within feature groups. Then, we determined the defense rule scope based on the obtained explanation results and generated more fine-grained defense rules to implement intrusion response in combination with security constraints. The proposed method was experimented on two public datasets, TON_IoT and Gas Pipeline. The experimental results show that the explanation effect of xIIRS is better than the baseline method while achieving an average malicious traffic blocking rate of about 95% and an average normal traffic passing rate of about 99%.
1. Introduction
1.1. Research Background
With the degree of industrial informatization deepening, the industrial Internet security problem is becoming increasingly serious [1]. At present, the protection of the industrial Internet mainly focuses on the detection and identification of attacks, namely the industrial intrusion detection system (IDS), but it is also necessary to respond to the attacks, namely the industrial intrusion response system (IRS). Among them, as an important line of defense in the industrial Internet, intrusion detection systems maintain the security of the industrial Internet by monitoring the entire network to detect attacks [2,3]. Current deep learning-based industrial internet intrusion detection systems (DL-IIDS) [4,5,6] show excellent detection performance due to their strong ability to detect and capture complex patterns and small deviations, but at the same time, their black-box characteristics due to their complex structure make it difficult to explain the model-detection results, which leads to low explainability [7,8,9,10]. Therefore, the decisions made based on the deep learning model lack trustworthiness and are difficult to use as the basis for a series of subsequent complex operations. The emergence of Explainable Artificial Intelligence (XAI) provides ideas to solve the above problems [11,12,13], and offers the possibility of implementing industrial intrusion response based on XAI.
In recent years, many methods have been focused on explaining security-related decisions. For example, the Natural Language Generation (NLG)-based security decision explanation method [14] can help users understand the security threats in automated rules by generating easy-to-understand natural language security risk explanations, thereby improving users’ decision-making trust. However, the explanation of deep learning models, especially in the context of time-series and interdependent network traffic, the existing explanation methods for deep learning models [15,16,17,18,19] provide local explanations for specific input samples and their decisions by highlighting important features. However, none of these methods can explain DL-IIDS well. Specifically, the input to industrial internet intrusion detection is a time series and interdependent, and the majority of the existing explanation methods do not take into account the complex dependencies between historical input samples and features. Although xNIDS [20] proposed a solution for the above problem, this method did not fully consider the differences in features between and within feature groups when capturing feature dependencies of industrial traffic data, which weakened the explanation effect and further reduced the effect of industrial intrusion response.
1.2. Contribution and Organization
To address the problems of the existing explanation method xNIDS, we noted that the study in [21] improved the effectiveness of obtaining genes related to cancer diagnosis by introducing between and within gene groups importance-evaluation metrics in the traditional sparse group lasso. With this inspiration, in this study, we improved an explanation method by approximating and sampling the historical input and calculating the sparse group lasso dynamic weighting according to the between and within feature groups importance-evaluation criteria, which improves the ability of sparse group lasso to capture key features and implements fine-grained explanation. Finally, we determined the defense rule scope based on the obtained explanation results and generated more fine-grained defense rules to implement intrusion response in combination with security constraints. The main contributions of this paper are as follows:
- We improved an explanation method by approximating and sampling the historical input and calculating the sparse group lasso dynamic weighting according to the between and within feature groups importance-evaluation criteria, which improves the ability of sparse group lasso to capture key features and implements fine-grained explanation. When calculating the weights between feature groups, the symmetric uncertainty was calculated to determine the contribution of different feature groups to the classification, and the importance weights of different features within a feature group were calculated by considering the group-affiliation trustworthiness and comprehensive evaluation criteria.
- We proposed an industrial internet intrusion defense rule generation method that determines the defense rule scope based on explanation results and generates fine-grained defense rules combined with security constraints to effectively respond to industrial internet intrusions.
The rest of this paper is organized as follows: In Section 2, we review the research studies related to this paper. In Section 3, we present the detailed design of the xIIRS. In Section 4, we evaluate and analyze the proposed xIIRS in this paper through experiments. In Section 5, we describe the advantages and practical implications of xIIRS. Finally, in Section 6, we conclude this work and provide a vision for future work.
2. Related Work
In this section, we review existing methods for explaining deep learning and related research on active intrusion response methods, as explanation methods are needed to implement industrial intrusion response.
2.1. Explanation Methods
In industrial scenarios, XAI can help humans make trusted decisions for critical applications that require information fusion. XAI is essential to explain the decisions made by AI, support trustworthiness, and guarantee compliance. XAI articulates the clear reasoning behind the decisions made, helping to understand the AI recommendations that are critical to making safety decisions. Feature importance is one of the most popular types of explanations returned by local explanation methods. For feature importance-based explanation methods, the explainer assigns an importance value to each feature, which indicates the importance of that particular feature for the analyzed prediction [22]. The methods considered in this paper for explaining the results of deep learning are mainly by calculating feature importance, and the specific explanation methods are described as follows: IG [15] calculates the importance score of feature Xi by accumulating the path gradient of feature Xi from the benchmark input to the actual input. This method maintains the sensitivity of feature importance to input changes so that the importance score of each feature can accurately reflect its influence on model prediction. LRP [16] calculates the importance score of feature Xi by tracing its contribution to detection layer by layer. Specifically, LRP starts from the output layer of the model and gradually propagates to the input layer along the hierarchical structure of the model to calculate the contribution of each layer’s features to the final prediction result. In this process, each layer of the model passes a correlation to the previous layer features based on how much it contributes to the final prediction, which allows LRP to visually show how each input feature affects the final classification or regression result. LIME [17] and SHAP [18] both compute feature-importance scores by lasso regression and assume that the selection of features is independent. However, LIME uses cosine similarity to measure the relationship between features and prediction results, while SHAP is based on Shapely values and assigns a fair importance score to each feature through cooperative game theory. LEMNA [19] calculates feature-importance scores by constructing a unique hybrid regression model, which first generates a set of artificial data samples in the local region of the input sample and fits a hybrid regression model consisting of K linear regression models through these samples. In the process of model fitting, LEMNA introduces fused lasso as a regularization term to force adjacent features to have similar importance scores so as to effectively capture the dependencies between features, which can approximate the local nonlinear decision boundary of the deep learning model and extract the explanation of key features from the hybrid regression model. xNIDS [20] focuses on the time-series characteristics of traffic by approximating and sampling historical input traffic and uses the sparse group lasso method to capture the dependencies between features. This method allows predefined groups of features to be either all selected or all excluded, ensuring that all features in the same group are either all included or completely excluded. This approach has desirable group-level and feature-level sparsity effects, helping to identify the key features that are most explanatory to the prediction results. However, when performing sparsity interpretation, the importance of different feature groups and the importance of the features within the group may differ. Treating them as the same may lead to a reduction in the explanatory effect.
2.2. Active Intrusion Responses
For the protection of the industrial Internet, it is not enough to use IDS alone. IDS must be combined with IRS to dynamically deploy appropriate defense rules to mitigate the detected attacks and restore to the normal state [23]. Many scholars have tried to use feature-based or specification-based NIDS [24,25] to implement active intrusion response. For example, the study in [26] proposed a network-control framework based on the open-source Bro [24] network security monitor, which enables passive network monitoring systems to actively control network components (such as switches, firewalls, etc.), and finally used OpenFlow [27] for the evaluation of functionality and performance. The study in [28] proposed SnortFlow, an intrusion prevention system based on OpenFlow and Snort, which enables cloud-network environments to detect intrusions and deploy defenses through real-time reconfiguration of the cloud-network environment. In short, the proposed defense system utilizes Snort to analyze the network traffic and deploys defense rules on OpenFlow to defense. The study in [29] proposed Poseidon, a high-performance, low-cost, and agile DDoS defense system, which uses a modular policy abstraction to represent defense policies, divides them into programmable switches to run according to the attributes of the defense primitives, maps the high-level policies to defense resources through an optimized orchestration mechanism, and finally a runtime-management mechanism is designed to achieve dynamic defense without blocking legitimate traffic. The study in [30] proposed a method, FIRMA, to detect and respond to network intrusions using network characteristics and blacklists; however, the method is too strict and leads to excessive intrusion response, which not only blocks malicious traffic but also normal traffic, and fails to achieve fine-grained management of traffic. The study in [20] proposed xNIDS, an intrusion response framework based on the explanation method, which focuses on the time-series characteristics of the traffic by approximating and sampling the historical input traffic and then uses the sparse group lasso method to capture the dependencies between the characteristics. This method allows predefined groups of features to be either all selected or all excluded, ensuring that all features in the same group are either all included or completely excluded. This approach has desirable group-level and feature-level sparsity effects, helping to identify the key features that are most explanatory to the prediction results. However, when performing a sparsity explanation, the importance of different feature groups and the importance of the features within the group may differ. Treating them as the same may lead to a reduction in the explanatory effect.
In summary, the existing explanation methods and active intrusion response methods still have the following problems: Firstly, IIDS needs to make a decision based on the current sample and several historical inputs when making predictions, and it needs to consider the complex dependencies between features. However, the explanation methods LEMNA, LIME, and SHAP only consider the current sample and ignore the historical input samples. Second, explanation methods cannot capture the complex dependencies between features. For example, IG, LIME, and SHAP assume that features in the input sample are independent, and LEMNA assumes that adjacent features have the same contribution, which cannot capture the dependencies between features. Although there have been related studies such as xNIDS to solve the above problems, they do not fully consider the differences between feature groups and features within feature groups, resulting in poor explanation effects. Finally, most of the existing intrusion response methods, such as SnortFlow, Poseidon, and FIRMA, mainly rely on predefined feature matching or rule specification to respond, which lack dynamic adaptability and cannot achieve fine-grained management of network traffic. However, in actual industrial scenarios, defense rules often need to be dynamically adjusted and deployed according to real-time industrial network traffic to adapt to the complex and changing network environment, and defense rules also need to implement fine-grained management of industrial network traffic. Considering the problems existing in current research, this paper proposes an intrusion response method for the industrial Internet based on explainable deep learning to realize active protection for the industrial Internet.
3. System Design
In this section, we introduce two important parts of this work: explaining industrial intrusion detection results and generating industrial intrusion defense rules, where the part of explaining industrial intrusion detection results describes the improved explanation method in detail, and the part of generating defense rules describes the method of determining the scope of the defense rules based on the explanation results and generating the industrial intrusion defense rules in combination with the security constraints.
The industrial internet intrusion response system considered in this paper is shown in Figure 1, which includes two important parts: the explanation of industrial intrusion detection results and the generation of industrial intrusion response rules. Specifically, first of all, the traffic in the industrial Internet is collected and uploaded to the industrial intrusion detection model based on deep learning, and the results will be output when the detection is finished. The trained industrial intrusion detection model based on deep learning, the traffic to be explained, and the detection results will be uploaded to the improved explanation method of this paper. After the explanation, the output is the feature-importance score. Based on the explanation results to determine the defense rule scope and combined with the security constraints to generate unified defense rules, in order to verify the effectiveness of the defense rules, the unified defense rules will be specific and then deployed to different defense tools to achieve a more fine-grained blocking and passing of industrial traffic.
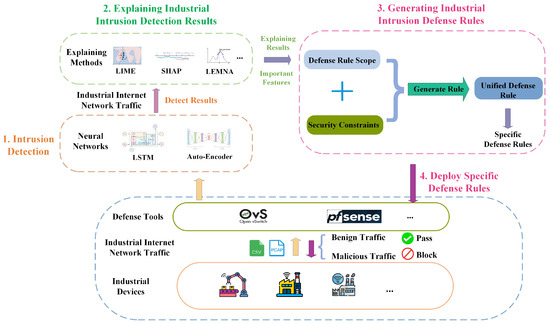
Figure 1.
xIIRS system framework.
3.1. Explaining Industrial Intrusion Detection Results
The explanation of industrial intrusion detection results consists of two key steps: approximating historical inputs and sampling and capturing feature dependencies. Firstly, in order to fully consider the influence of historical inputs of industrial internet traffic, we approximate the historical inputs and synthesize the samples using Weighted Random Sampling (WRS) [31]. We then take into account the importance of features between and within feature groups and use a dynamically weighted sparse group lasso to obtain a more fine-grained explanation of the results.
3.1.1. Approximating History Inputs and Sampling
Due to the strong time-series characteristics of industrial internet traffic, although the existing explanation methods LEMNA, LIME, and SHAP can highlight the features that have important contributions to the detection results to explain the detection results, they are not sufficient to explain the detection results about historical inputs. Aiming at this problem, some studies have begun to consider historical inputs to obtain a better explanation. However, in industrial internet intrusion detection, the explanation results obtained only from the current input or a fixed number of historical inputs are insufficient, which will lead to low explanation fidelity. In addition, it is also unreasonable to consider all historical inputs, which will produce redundancy, so it is necessary to effectively find a small number of inputs to approximate the relevant historical inputs [20]. This involves approximating the historical input and synthesizing samples by weighted random sampling around the historical input.
When approximating the historical input, we first need to find a length L, such that the approximate historical input of length L and the approximation result containing K actual historical inputs meet a specific accuracy, if not, we will double L, otherwise we will cut L in half, until the approximate accuracy is satisfied or the maximum number of updates is reached. Secondly, some weakly correlated historical inputs were deleted from the obtained historical inputs of length L to ensure that the detection results still meet the requirements of approximate accuracy, and then the most relevant inputs were selected.
When sampling the historical input, considering that the latest input may have more influence on the result than the old input when DL-IIDS make decisions, the sampling is not uniform near the historical input. Firstly, we assign weights according to the arrival order of historical inputs and assign greater weights to the latest historical inputs. Then, we synthesize samples closer to the latest historical inputs by Weighted Random Sampling (WRS). Specifically, the probability of each sample being selected at WRS is determined by its relative weight. Weights are assigned to each historical input according to its arrival order, and features of the latest historical input have a higher probability to be selected, while features of the same input have the same probability to be selected.
3.1.2. Capturing Feature Dependencies
To achieve sparse explanation, the most relevant features from the input are selected as the result of the explanation, while ignoring those features that have less contribution to the detection result. The traditional sparse group lasso (SGL) is a regression method that supports selection on the basis of feature groups, which allows predefined groups of features to be included in the model as a whole or excluded as a whole. This method has shown desirable results in terms of sparsity of both feature groups and individual features [32]. However, the traditional sparse group lasso does not consider the differences between and within groups. To address this problem, we integrate the importance-evaluation criteria of features between and within feature groups on the basis of the traditional sparse group lasso, which is used to measure the importance of different features between and within feature groups, so as to implement the dynamically weighted sparse group lasso to further enhance the explanation effect. The specific calculation formulas are as follows:
The evaluation of the importance of feature groups requires measuring the relationship between the module feature vector and the classification label Y, specifically calculating the contribution of the g-th feature group to the classification, as shown in Equation (1):
where is the number of features in group g, which reduces the impact of the number of features on the detection results, and meg denotes the representative features of feature group g obtained by Principal Component Analysis (PCA), Equation (2) measures the degree of correlation between the representative feature meg and the categorical label Y through an information theoretic perspective:
According to the feature group importance evaluation shown in Equation (1), we construct the g-th feature group weight, as shown in Equation (3):
The symbol denotes the group-affiliation trustworthiness of the t-th feature of the g-th group, and the group-affiliation trustworthiness indicates the degree of trustworthiness that the feature belongs to the feature group, specifically calculating the similarity between the current feature and the representative features of the group, as shown in Equation (4):
The symbol denotes the comprehensive evaluation criterion for the t-th feature in the g-th feature group, and the definitions of each parameter and other representations are described in detail in [21], as shown in Equation (5):
The within-group feature importance of the t-th feature of the g-th feature group is the product of the group-affiliation trustworthiness of the feature and the comprehensive evaluation criterion, as shown in Equation (6):
Based on the within-group feature-importance shown in Equation (6), we construct the weight matrix of the features within the g-th feature group, as shown in Equation (7):
We proposed an improved dynamic weighted sparse group lasso. Compared with the fixed coefficient of the traditional sparse group lasso, we refine the penalty strength for the feature group and the features within the group. Through the importance calculation Equations (3) and (7), the calculated weighted coefficient is introduced for dynamic weighting, such as Equation (8):
3.2. Generating Industrial Intrusion Defense Rules
After extracting the important features used by DL-IIDS for decision making, xIIRS generates defense rules based on these features. Figure 2 gives a detailed example of how xIIRS generates defense rules. It comprises the following three steps: (1) determine the defense rule scope according to the explanation results. (2) create a unified defense rule entity by filling the important feature matching values into the corresponding fields according to the defense rule scope and security constraints. (3) specify the unified defense rules in different defense tools to generate their own defense rules.
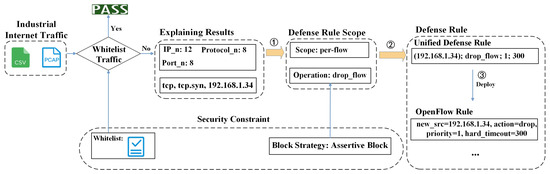
Figure 2.
Defense rule generation process.
3.2.1. Defense Rule Scope
In order to balance accuracy and generalization, we use the defense rule scopes defined in the study in [20] to determine the scope of application of the rules, where the per-flow scope can only affect network traffic for a specific flow, the per-host scope blocks multiple flows from the same host, and the multi-host scope blocks multiple flows from multiple hosts.
Specifically, the defense rule scope is determined by analyzing the corresponding explanations. As shown in Table 1, the statistics are defined as S and contain the following five fields: IP_pool, IP_n, MAC_n, Port_n, and Protocol_n. We determine the defense rule scope (scope of action) by examining the values of the fields in the statistics. For example, a large value of Protocol_n or Port_n indicates that the abnormal traffic shares the same protocol or port, and there is a high probability that multiple hosts are sending traffic together, focusing on a certain protocol or port, which indicates that multiple hosts may be involved in the attack. Therefore, the scope of the defense rule should be multi-host. Otherwise, if the abnormal traffic comes from the same host, the corresponding defense rule scope should be set to per-host scope or per-flow scope. In this case, if multiple protocols or ports are included in the important features, which means that the host uses multiple protocols to launch the attack, the defense rule scope is per-host scope; otherwise, it is per-flow scope.

Table 1.
Details of statistical information.
3.2.2. Security Constraints
The industrial network environment is complex and dynamic, which needs to be flexibly adjusted according to different network environments and possible changes. To this end, security constraints that can be dynamically configured by industrial network managers are introduced. These constraints include whitelisting and blocking strategies to ensure the availability of industrial networks and maintain an appropriate blocking rate. Among them, the whitelist ensures that the industrial network traffic of critical services is not affected by the defense rules, and the blocking strategy chooses the assertive block strategy with better malicious traffic blocking effect and normal traffic passing effect in [20], specifically, the industrial network managers are more inclined to trust the rules automatically generated by the corresponding DL-IIDS and xIIRS.
3.2.3. Generating Unified Defense Rules
To support defense tools that use different rule syntaxes, we adopt the unified defense rule representation in [20], where each unified defense rule consists of 4 tuples: ⟨Entity, Action, Priority, Timeout⟩. Entity is the target of application defense actions (network flow, connection, IP address, etc.). Action is the specific defense action to be performed for all network flows of the entity. Priority is the order of operations to resolve potential conflicts by applying the rule with the highest priority when a single instance of network traffic matches multiple unified defense rules. Timeout indicates the effective time of the defense rule.
To generate defense rules, we create defense rule entities by filling the corresponding fields with values matching important features related to the scope and security constraints of the defense rule. Two basic operations, drop_flow and drop_host, are defined, and for per-flow, the drop_flow operation is used to block malicious traffic. For per-host, the drop_host operation is used to block malicious hosts. For multi-host, the drop_flow operation is used to recursively block malicious flows.
4. Experimental Evaluation
This section verifies the proposed xIIRS scheme from three aspects: experimental settings, explanation method evaluation experiment, and industrial intrusion response evaluation experiment. Firstly, Section 4.1 mainly introduces the experimental environment, comprising three parts: the dataset description, the evaluation metrics, and the target system performance. Secondly, Section 4.2 systematically evaluates the explanation effect of the improved explanation method from four aspects of fidelity, sparsity, completeness, and stability. Finally, Section 4.3 implements the evaluation of industrial intrusion response through response latency evaluation experiment and response effectiveness evaluation experiment.
4.1. Experiment Settings
Method Implementation. The experiment is carried out on the Ubuntu 22.04.3 LTS platform with Intel Xeon Gold 5118 CPU (128 G) and two 10 G network cards. The Python package asgl [33] was used to implement xIIRS and grid search was used to adjust parameters to improve performance. Finally, OpenFlow was selected from multiple defense tools to verify the effectiveness of the generated defense rules.
Target DL-IIDS. We use widely used deep learning models as the target DL-IIDS, specifically employing the AutoEncoder and the commonly used LSTM model in RNNs for the DL-IIDS.
Comparison Baselines. The baseline methods we compare are LIME, SHAP, LEMNA, IG, LRP, and xNIDS.
4.1.1. Dataset Description
The experiments were conducted on two datasets: TON_IoT dataset [34] and natural gas pipeline dataset [35].
The TON_IoT dataset contains nine types of labeled IoT network traffic data aggregated from heterogeneous data sources, including Normal, Scanning attacks, Denial of Service (DoS) attacks, and distributed DoS (DDoS) attacks, Ransomware attacks, Backdoor attacks, Injection attacks, Cross-Site Scripting (XSS) attacks, Password Cracking attacks (PWA) and Man-In-The-Middle attacks (MITM). The data contains about 22 M log entries with 46 features and 9 devices. A sample of these data is used in this study, and the data are divided into two subsets: 80% of the data are used for training, and 20% are used for testing.
Another dataset used in this paper is the natural gas pipeline dataset, which was established by the Mississippi State University’s critical Infrastructure protection center, and the data source is the network layer data of the natural gas pipeline SCADA control system. Compared with traditional enterprise networks, SCADA network topology and services are relatively fixed. There are two categories of features in the dataset: network traffic features and payload content features. Network traffic features are used to describe normal traffic patterns to detect malicious activities, including device address, function code, length of packet, packet error checking information, and time intervals between packets. Payload content features describe the current state of the SCADA system, including sensor measurements, supervisory control inputs, and distributed control states, which are used to detect attacks that cause abnormal behavior of the device. This dataset collects network data of normal natural gas pipeline operation and network data of 7 types of network attacks. Each network data includes 26 features and 1 label. A total of 80% of the data are used for model training and 20% for testing.
4.1.2. Evaluation Metrics
In order to evaluate the explanation performance of the proposed xIIRS, this study used four common indicators in study [20] to evaluate the explanation effect of the detection method: Average Descriptive Accuracy (ADA), Mass Around Zero (MAZ), the proportion of abnormal samples that generate non-degenerate explanations (Anomaly) and the Average Stability Score (Stability). To measure the effectiveness of the defense rules, we used indicators such as latency and block rate.
- 1.
- ADA: We use the evaluation metric below to evaluate the fidelity of the explanation methods.where D is the dataset, x is a sample in D, the size of the dataset D is n, is the prediction function, denotes the k-th feature of the i-th sample, and denotes the class of the i-th sample is c. A steep decline in ADA indicates better fidelity of the explanation method.
- 2.
- MAZ: We use the evaluation metric below to evaluate the sparsity of the explanation methods.where is the importance score scaled to a range of [0,1]. The larger the slope of MAZ near 0 and the smaller the slope near 1, the better the sparsity of the explanation method.
- 3.
- Anomaly: We use the evaluation metric below to evaluate the completeness of the explanation methods, measuring the completeness of the historical inputs by calculating the percentage of anomaly samples able to generate non-degenerate explanations.where is the number of abnormal samples for generating non-degenerate explanations and is the total number of abnormal samples, and the larger the result of Anomaly indicates the better the completeness of the explanation method.
- 4.
- Stability: We use the evaluation metric below to evaluate the stability of the explanation methods. To check the stability of the explanation, we calculated the size of the first K feature intersections of the explanation results concerning the same inputs from different tests.where denotes the set of the first K important features obtained from the n-th explanation, and the closer the result of Stability is to 1 indicates the better the stability of the explanation method.
4.1.3. Target System Performance
Table 2 is the target system where we need to conduct explanation method evaluation experiments and industrial intrusion response evaluation experiments. It shows the intrusion detection performance of different models under the two selected datasets.

Table 2.
Target system intrusion detection model performance.
4.2. Explanation Methods Evaluation Experiments
We conducted experiments on two widely used industrial network traffic datasets to perform an explanation evaluation of xIIRS, and the results are as follows.
4.2.1. Fidelity Evaluation Experiment
This experiment evaluates the degree of trustworthiness of the explanation method in capturing important features that contribute to a particular detection result. This fidelity evaluation experiment focuses on the effect on the ADA of the dataset after modifying the first k relevant features for normal and abnormal samples. There are two ways of modifying the k relevant features as described in [20]. For abnormal samples it is to set the k important features to 0, and for normal samples, it is to replace the first k relevant features of the benign samples with the corresponding features of the nearest abnormal samples.
For the abnormal traffic samples, as shown in Figure 3 and Table 3, xIIRS has the largest decrease in ADA and the smallest area under the curve compared with the baseline method on both datasets, which shows that the features selected by xIIRS are highly correlated with the detection results. Similarly, to validate the fidelity of the explanation method in the case of the normal samples, as shown in Table 4, we observe that the replacement of normal features by abnormal features significantly increases the anomaly rate by at least 3 times on all datasets, which shows that the features selected by our explanation method still have a good fidelity effect in the case of the normal traffic samples.
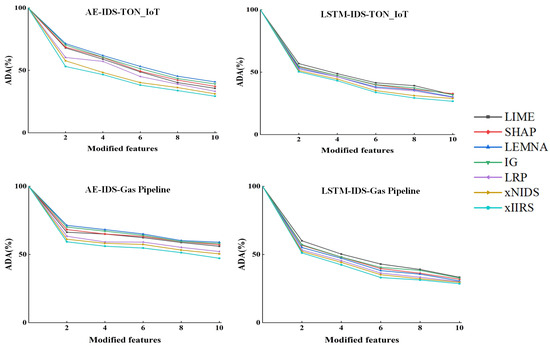
Figure 3.
Explanation method fidelity comparison experiment.

Table 3.
Area under the ADA curve.

Table 4.
Comparison of setting benign features to zero and replacing abnormal features.
4.2.2. Sparsity Evaluation Experiment
This experiment evaluates the sparsity of the explanation method. An ideal explanation method should select a limited number of features as the explanation result. We follow the experimental evaluation method in [20]. We first scale the feature-importance scores to the range [0,1], then fit to a semi-canonical histogram h, and then compute the MAZ. If the explanation method can be assigned to most of the features near 0 and achieve a sparse explanation, then the MAZ curve will have a steeper slope close to 0 and a larger area under the curve.
As shown in Figure 4 and Table 5, xIIRS has the steepest slope and the largest area under the curve, which means that most of the feature-importance scores assigned by xIIRS are close to zero, and xIIRS is better than the baseline method in the sparsity criterion. Among them, LEMNA performs poorly in the sparsity criterion, which is due to the fact that LEMNA assumes that neighboring features contribute similarly to the detection results. In contrast, xIIRS takes into account the differences between the between- and within-group features and could achieve more accurate feature-level sparsity while guaranteeing group-level sparsity. Compared with the xNIDS method with traditional sparse group lasso, xIIRS reflects stronger sparsity.
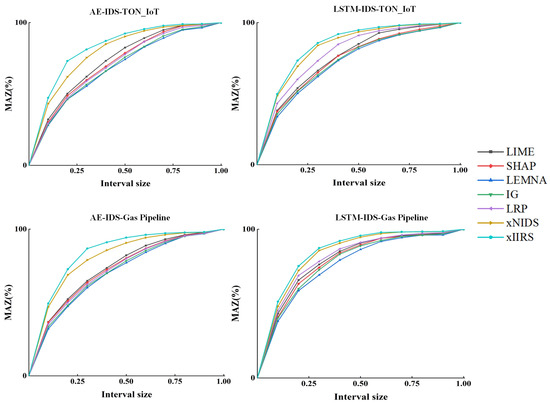
Figure 4.
Explanation method sparsity comparison experiment.

Table 5.
Area under the MAZ curve.
4.2.3. Completeness Evaluation Experiment
This experiment evaluates the completeness of the explanation method, an ideal explanation method that creates suitable results for all possible input samples. We follow the experimental evaluation method in [20] and measure the completeness of the historical inputs by calculating the percentage of abnormal samples that are able to generate non-degenerate explanations.
As shown in Table 6, at least about 22% of the anomaly samples of LIME, SHAP, LEMNA, IG, and LRP do not contain enough information to generate non-degenerate explanations because they ignore historical inputs. In contrast, only about 3% of the anomaly samples of our proposed xIIRS and xNIDS generate degenerate explanations due to considering the impact of historical inputs on the explanations and because our methods consider the differences between and within feature groups and optimize the selection of key features within groups, generating a higher proportion of non-degenerate explanations compared to xNIDS.

Table 6.
Proportion of anomaly samples generating non-degenerate explanations.
4.2.4. Stability Evaluation Experiment
This experiment evaluates the stability of the explanation method. An ideal explanation method should produce similar results for the same samples across many tests. We follow the experimental evaluation method in [20] and calculate the intersection size of the first K features in the explanation results for the same inputs under different test conditions. Since the explanation results of IG and LRP are deterministic, we focus on the stability of the perturbation-based methods LIME, SHAP, LEMNA, xNIDS, and xIIRS.
As shown in Table 7, the average stability scores of xIIRS are all higher than those of LEMNA, SHAP, LIME, and xNIDS, which is due to the fact that xIIRS takes into account the differences in features between and within feature groups, and the dynamic adjustment of the feature weights enables the model to keep the key features more stably and reduce the fluctuation of the unimportant or redundant features in different testing conditions and thus improves the stability of the intersection size of the top K features in the explanation results.

Table 7.
Average stability score for explanation methods.
4.3. Industrial Intrusion Response Evaluation Experiment
In order to verify the effectiveness of the generated defense rules, we deploy them on the widely used defense tool OpenFlow and carry out experiments on industrial internet intrusion response latency and response-effect evaluation.
4.3.1. Response Latency Evaluation Experiment
This experiment evaluates the explanation method latency and the generation of defense rule latency. As shown in Figure 5, more than 90% of the explanation delays of our method on the TON_IoT dataset and Gas Pipeline dataset are less than 900 ms and 800 ms, respectively. As shown in Figure 6, the maximum delay of generating the defense rules on the TON_IoT dataset is 51 ms against the MITM attack, and the average delay is about 39 ms. The maximum delay for generating the defense rules on the Gas Pipeline dataset is 40 ms for the MFCI attack, and the average delay is about 32 ms.
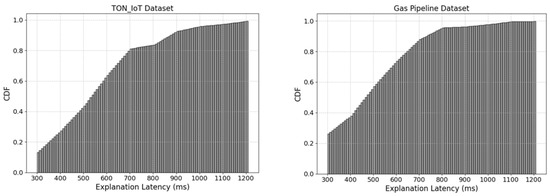
Figure 5.
Explanation method latency on TON_IoT, Gas Pipeline datasets.

Figure 6.
Defense rule generation latency on TON_IoT, Gas Pipeline datasets.
4.3.2. Response Effectiveness Evaluation Experiment
In order to verify the defense effectiveness of the generated defense rules, we compare them with the baseline method xNIDS based on the blocking rate, we replay the traffic of the relevant dataset and verify the change in traffic blocking rate before and after deploying the defense rules on the defense tool OpenFlow to quantitatively analyze the effectiveness of the generated defense rules.
As shown in Figure 7, before the deployment of the defense rule, the direct blocking of the relevant hosts is used, and it could be seen that the blocking rate of the malicious traffic and the normal traffic are both high, which leads to many normal industrial traffic being blocked by mistake. As shown in Figure 8 and Figure 9, after the deployment of defense rules, the blocking rate of malicious traffic on the TON_IoT dataset decreases by about 1.08% and rises by about 0.37% on average compared with that of xNIDS and xIIRS before the deployment of the defense rules, respectively, and at the same time reduces the blocking rate of normal traffic by about 12.39% and 12.81% on average, respectively. The blocking rate of malicious traffic on the Gas Pipeline dataset has increased by about 1.99% and 2.24% on average compared to xNIDS and xIIRS before the deployment of defense rules, while the blocking rate of normal traffic has decreased by about 15.7% and 16.1% on average. Finally, our proposed method achieves an average blocking rate of 93.17% for malicious traffic and 1.34% for normal traffic in the TON_IoT dataset and an average blocking rate of 96.01% for malicious traffic and 1.36% for normal traffic in the Gas Pipeline dataset. The above experimental results demonstrate that our generated defense rules can achieve better blocking for malicious traffic and better passing for normal traffic.
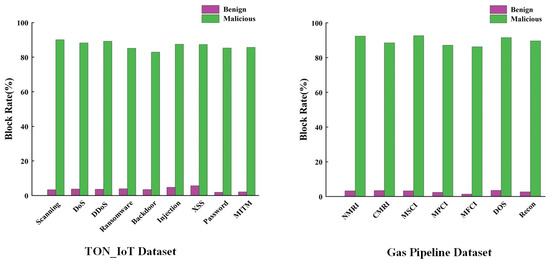
Figure 7.
Traffic blocking rate before deploying defense rules on TON_IoT, Gas Pipeline dataset.
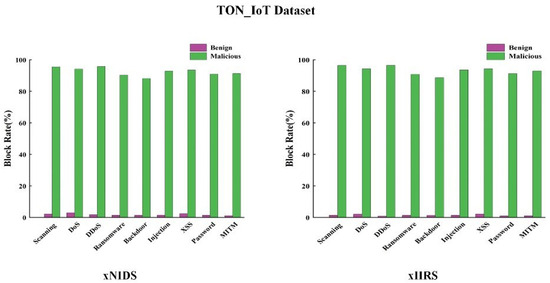
Figure 8.
Traffic blocking rate for different methods after deploying defense rules on TON_IoT dataset.

Figure 9.
Traffic blocking rate for different methods after deploying defense rules on Gas Pipeline dataset.
5. Discussion
We consider the impact of feature differences between feature groups and feature differences within feature groups on the traditional sparse group lasso in capturing feature dependencies and introduce the calculated dynamic weights according to the proposed evaluation criteria to obtain a more fine-grained explanation. The experimental results show that the improved explanation method is superior to the existing baseline methods in fidelity, sparsity, completeness, and stability, which also strongly demonstrates the effectiveness of feature group and within-group feature differentiation consideration. The industrial intrusion response method implemented based on the above explanation method has a 90% explanation delay of less than 900 ms on the two datasets, and the maximum delay time of defense rule generation is less than 40 ms, which is acceptable in most industrial scenarios. In terms of response effect, the average blocking rates of malicious traffic in TON_IoT and Gas Pipeline datasets reached 93.17% and 96.01%, and the average blocking rates of normal traffic were 1.34% and 1.36%, respectively. The experimental results show that the defense rules generated by us can achieve better blocking for malicious traffic and better passing for normal traffic.
In the face of increasingly complex industrial internet attacks, our proposed intrusion response scheme xIIRS for industrial Internet based on explainable deep learning can block malicious traffic and release normal traffic in a relatively short time, which realizes fine-grained management of industrial internet traffic. When the industrial internet traffic environment changes, our method can also dynamically adjust the defense rules for response disposal.
6. Conclusions and Future Work
In this paper, we proposed an industrial internet intrusion response method xIIRS based on explainable deep learning. Firstly, we improved an explanation method by approximating and sampling the historical input and calculating the sparse group lasso dynamic weighting according to the between and within feature group importance-evaluation criteria, which improves the ability of sparse group lasso to capture key features and implements fine-grained explanation. Then, we determined the defense rule scope based on the obtained explanation results and generated more fine-grained defense rules to implement intrusion response in combination with security constraints. Finally, we conducted a large number of experiments on TON_IoT, natural gas pipeline dataset, and the experimental results show the effectiveness of xIIRS. In future work, we will consider further improving the generation of defense rules and the generalizability for new attacks, and at the same time, to carry out a large number of tests and verifications in actual industrial scenarios to adapt to the more complex and changing real industrial network environment.
Author Contributions
Conceptualization, Q.X. and Z.Z.; methodology, Q.X.; validation, Q.X., K.F. and M.W.; investigation, Z.Z.; writing—original draft preparation, Q.X.; writing—review and editing, Q.X.; supervision, Z.Z., K.F. and M.W.; project administration, Q.X.; funding acquisition, Z.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by Project of Leading Talents in Science and Technology Innovation in Henan Province under Grant 204200510021, Program for Henan Province Key Science and Technology under Grant 222102210177, and Grant 232102211060, the Joint Fund Project of Science and Technology Research and Development Plan of Henan Province under Grant 232103810042, Henan Province University Key Scientific Research Project under Grant 23A5200086 as well as Henan Province Key Research and Development Project under Grant 241111211400.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Kikissagbe, B.R.; Adda, M. Machine Learning-Based Intrusion Detection Methods in IoT Systems: A Comprehensive Review. Electronics 2024, 13, 3601. [Google Scholar] [CrossRef]
- Zainudin, A.; Akter, R.; Kim, D.S.; Lee, J.M. Federated learning inspired low-complexity intrusion detection and classification technique for sdn-based industrial cps. IEEE Trans. Netw. Serv. Manag. 2023, 20, 2442–2459. [Google Scholar] [CrossRef]
- Lopes, I.O.; Zou, D.; Abdulqadder, I.H.; Akbar, S.; Li, Z.; Ruambo, F.; Pereira, W. Network intrusion detection based on the temporal convolutional model. Comput. Secur. 2023, 135, 103465. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Chang, V.; Hawash, H.; Chakrabortty, R.K.; Ryan, M. Deep-IFS: Intrusion detection approach for industrial internet of things traffic in fog environment. IEEE Trans. Ind. Inform. 2020, 17, 7704–7715. [Google Scholar] [CrossRef]
- Zhou, X.; Liang, W.; Shimizu, S.; Ma, J.; Jin, Q. Siamese neural network based few-shot learning for anomaly detection in industrial cyber-physical systems. IEEE Trans. Ind. Inform. 2020, 17, 5790–5798. [Google Scholar] [CrossRef]
- Yin, C.; Zhang, S.; Wang, J.; Xiong, N.N. Anomaly detection based on convolutional recurrent autoencoder for IoT time series. IEEE Trans. Syst. Man Cybern. Syst. 2020, 52, 112–122. [Google Scholar] [CrossRef]
- Javeed, D.; Gao, T.; Kumar, P.; Jolfaei, A. An explainable and resilient intrusion detection system for industry 5.0. IEEE Trans. Consum. Electron. 2023, 70, 1342–1350. [Google Scholar] [CrossRef]
- Keshk, M.; Koroniotis, N.; Pham, N.; Moustafa, N.; Turnbull, B.; Zomaya, A.Y. An explainable deep learning-enabled intrusion detection framework in IoT networks. Inf. Sci. 2023, 639, 119000. [Google Scholar] [CrossRef]
- Dwivedi, R.; Dave, D.; Naik, H.; Singhal, S.; Omer, R.; Patel, P.; Qian, B.; Wen, Z.; Shah, T.; Morgan, G.; et al. Explainable AI (XAI): Core ideas, techniques, and solutions. ACM Comput. Surv. 2023, 55, 1–33. [Google Scholar] [CrossRef]
- Patil, S.; Varadarajan, V.; Mazhar, S.M.; Sahibzada, A.; Ahmed, N.; Sinha, O.; Kumar, S.; Shaw, K.; Kotecha, K. Explainable artificial intelligence for intrusion detection system. Electronics 2022, 11, 3079. [Google Scholar] [CrossRef]
- Moustafa, N.; Koroniotis, N.; Keshk, M.; Zomaya, A.Y.; Tari, Z. Explainable intrusion detection for cyber defences in the internet of things: Opportunities and solutions. IEEE Commun. Surv. Tutor. 2023, 25, 1775–1807. [Google Scholar] [CrossRef]
- Shoukat, S.; Gao, T.; Javeed, D.; Saeed, M.S.; Adil, M. Trust my IDS: An explainable AI integrated deep learning-based transparent threat detection system for industrial networks. Comput. Secur. 2025, 149, 104191. [Google Scholar] [CrossRef]
- Kummerow, A.; Abrha, E.; Eisenbach, M.; Rösch, D. Unsupervised Anomaly Detection and Explanation in Network Traffic with Transformers. Electronics 2024, 13, 4570. [Google Scholar] [CrossRef]
- Breve, B.; Cimino, G.; Deufemia, V. Hybrid Prompt Learning for Generating Justifications of Security Risks in Automation Rules. ACM Trans. Intell. Syst. Technol. 2024, 15, 1–26. [Google Scholar] [CrossRef]
- Sundararajan, M.; Taly, A.; Yan, Q. Axiomatic attribution for deep networks. In Proceedings of the 34th International Conference on Machine Learning, Sydney, Australia, 6–11 August 2017; pp. 3319–3328. Available online: https://proceedings.mlr.press/v70/sundararajan17a.html (accessed on 1 August 2017).
- Bach, S.; Binder, A.; Montavon, G.; Klauschen, F.; Müller, K.R.; Samek, W. On pixel-wise explanations for non-linear classifier decisions by layer-wise relevance propagation. PLoS ONE 2015, 10, e0130140. [Google Scholar] [CrossRef]
- Ribeiro, M.T.; Singh, S.; Guestrin, C. “Why should I trust you?” Explaining the predictions of any classifier. In Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, San Francisco, CA, USA, 13–17 August 2016; pp. 1135–1144. [Google Scholar] [CrossRef]
- Lundberg, S.M.; Lee, S.I. A Unified Approach to Interpreting Model Predictions. In Proceedings of the Advances in Neural Information Processing Systems, Long Beach, CA, USA, 4–9 December 2017; Guyon, I., Luxburg, U.V., Bengio, S., Wallach, H., Fergus, R., Vishwanathan, S., Garnett, R., Eds.; Curran Associates, Inc.: Red Hook, NY, USA, 2017; Volume 30. Available online: https://proceedings.neurips.cc/paper/2017/hash/8a20a8621978632d76c43dfd28b67767-Abstract.html (accessed on 1 December 2017).
- Guo, W.; Mu, D.; Xu, J.; Su, P.; Wang, G.; Xing, X. Lemna: Explaining deep learning based security applications. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 364–379. [Google Scholar] [CrossRef]
- Wei, F.; Li, H.; Zhao, Z.; Hu, H. {xNIDS}: Explaining Deep Learning-based Network Intrusion Detection Systems for Active Intrusion Responses. In Proceedings of the 32nd USENIX Security Symposium (USENIX Security 23), Anaheim, CA, USA, 9–11 August 2023; pp. 4337–4354. Available online: https://www.usenix.org/conference/usenixsecurity23/presentation/wei-feng (accessed on 1 August 2023).
- Song, X.; Liang, K.; Li, J. WGRLR: A weighted group regularized logistic regression for cancer diagnosis and gene selection. IEEE/ACM Trans. Comput. Biol. Bioinform. 2022, 20, 1563–1573. [Google Scholar] [CrossRef] [PubMed]
- Bodria, F.; Giannotti, F.; Guidotti, R.; Naretto, F.; Pedreschi, D.; Rinzivillo, S. Benchmarking and survey of explanation methods for black box models. Data Min. Knowl. Discov. 2023, 37, 1719–1778. [Google Scholar] [CrossRef]
- Bashendy, M.; Tantawy, A.; Erradi, A. Intrusion response systems for cyber-physical systems: A comprehensive survey. Comput. Secur. 2023, 124, 102984. [Google Scholar] [CrossRef]
- Paxson, V. Bro: A system for detecting network intruders in real-time. Comput. Netw. 1999, 31, 2435–2463. [Google Scholar] [CrossRef]
- Snort. 2020. Available online: https://www.snort.org/ (accessed on 19 January 2025).
- Amann, J.; Sommer, R. Providing dynamic control to passive network security monitoring. In Proceedings of the International Symposium on Recent Advances in Intrusion Detection, Kyoto, Japan, 2–4 November 2015; Springer: Cham, Switzerland, 2015; pp. 133–152. [Google Scholar] [CrossRef]
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow: Enabling innovation in campus networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 69–74. [Google Scholar] [CrossRef]
- Xing, T.; Huang, D.; Xu, L.; Chung, C.J.; Khatkar, P. Snortflow: A openflow-based intrusion prevention system in cloud environment. In Proceedings of the 2013 Second GENI Research and Educational Experiment Workshop, Salt Lake City, UT, USA, 20–22 March 2013; IEEE: New York, NY, USA, 2013; pp. 89–92. [Google Scholar] [CrossRef]
- Zhang, M.; Li, G.; Wang, S.; Liu, C.; Chen, A.; Hu, H.; Gu, G.; Li, Q.; Xu, M.; Wu, J. Poseidon: Mitigating volumetric ddos attacks with programmable switches. In Proceedings of the the 27th Network and Distributed System Security Symposium (NDSS 2020), San Diego, CA, USA, 23–26 February 2020. [Google Scholar] [CrossRef]
- Rafique, M.Z.; Caballero, J. Firma: Malware clustering and network signature generation with mixed network behaviors. In Proceedings of the Research in Attacks, Intrusions, and Defenses: 16th International Symposium, RAID 2013, Rodney Bay, St. Lucia, 23–25 October 2013; Proceedings 16. Springer: Berlin/Heidelberg, Germany, 2013; pp. 144–163. [Google Scholar] [CrossRef]
- Efraimidis, P.S.; Spirakis, P.G. Weighted random sampling with a reservoir. Inf. Process. Lett. 2006, 97, 181–185. [Google Scholar] [CrossRef]
- Simon, N.; Friedman, J.; Hastie, T.; Tibshirani, R. A sparse-group lasso. J. Comput. Graph. Stat. 2013, 22, 231–245. [Google Scholar] [CrossRef]
- Mendez-Civieta, A.; Aguilera-Morillo, M.C.; Lillo, R.E. Adaptive sparse group LASSO in quantile regression. Adv. Data Anal. Classif. 2021, 15, 547–573. [Google Scholar] [CrossRef]
- Alsaedi, A.; Moustafa, N.; Tari, Z.; Mahmood, A.; Anwar, A. TON_IoT telemetry dataset: A new generation dataset of IoT and IIoT for data-driven intrusion detection systems. IEEE Access 2020, 8, 165130–165150. [Google Scholar] [CrossRef]
- Morris, T.; Gao, W. Industrial control system traffic data sets for intrusion detection research. In Proceedings of the Critical Infrastructure Protection VIII: 8th IFIP WG 11.10 International Conference, ICCIP 2014, Arlington, VA, USA, 17–19 March 2014; Revised Selected Papers 8. Springer: Berlin/Heidelberg, Germany, 2014; pp. 65–78. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).