1. Introduction
In recent years, modern wireless communication systems such as 6G networks have paved ways for ubiquitously connecting future generations of smart and intelligent systems [
1,
2,
3,
4]. However, in modern automation for smart industries, the large number of Internet of Things (IoT) and wireless devices running diverse applications poses severe data rate and multiple access challenges to the underlying wireless infrastructure. In addition, 6G and future high-frequency wireless networks lack robust coverage in Non-Line-of-Sight situations where signal blockage can occur.
Non-Orthogonal Multiple Access (NOMA) has emerged as a promising multiple access technique for next-generation wireless networks, enabling higher spectral efficiency and massive connectivity in automation systems and general smart industries [
5,
6]. NOMA improves the overall system capacity by allowing multiple users to share the same frequency and time resources through multiplexing in the power domain. However, users located farther from the base station often experience lower data rates due to increased path loss and weaker signal strength. Nearby users can serve as relays by decoding and forwarding data on behalf of distant users, improving data rates and overall quality of experience (PQoE). Nevertheless, motivating short-distance users to act as relays is challenging, as many traditional incentive mechanisms do not adequately reward them for sharing resources such as power and bandwidth.
Blockchain technology offers a decentralized, secure framework that can facilitate trustworthy interactions among network participants. Smart contracts, defined as self-executing agreements with terms written in code, allow automated, transparent, and tamper-proof transactions without the need for intermediaries. By integrating smart contracts into NOMA networks, it becomes possible to establish incentive mechanisms that encourage relay participation and ensure honesty via verifiable proofs.
In this paper, we propose a novel system that leverages smart contracts on the Ethereum blockchain to incentivize and verify the performance of relays in NOMA wireless networks. We introduce a Service Verification Contract that employs a Proof of Quality of Experience (PQoE) consensus mechanism to validate services provided by relays. Trust scores and dynamic verification requirements are incorporated to promote honest behavior and discourage malicious activities.
The main contributions of this research can be summarized as follows: First, we design a smart contract framework that integrates with NOMA wireless networks to incentivize short-distance users to serve as relays for users farther from the base station. Next, we develop a verification mechanism that compares data transmission rates to ensure relays deliver the expected PQoE. We also introduce trust scores and dynamic verification adjustments to strengthen network integrity and foster honest participation. Finally, to ensure practical feasibility, we adopt an incentive structure based on StableCoins, enabling secure and stable transactions in this decentralized environment.
2. Review of Related Work
Prior research has explored diverse incentive mechanisms and performance metrics for enhancing wireless communication networks. For instance, the Helium network [
7] introduced an approach to incentivize participation in decentralized wireless infrastructures by using a blockchain with a native protocol token. This framework, designed for low-power, long-range connectivity in IoT devices, introduced the concept of Proof-of-Coverage to verify that hotspots provide reliable connectivity. Another study by Ramamoorthy et al. [
8] proposed the Proof-of-QoE NOMA Token, which leverages the Ethereum blockchain and a QoE-based consensus mechanism to reward local relays for participating in data transmission. Their work also employs Vickrey–Clarke–Groves auctions to balance system-wide QoE gains against individual relay profits, thereby mitigating opportunistic behavior.
Choi et al. [
9] developed a Proof-of-Traffic (PoT) consensus model suitable for automatic traffic usage. Wang et al. [
10] introduced a connectivity-aware contract model that addresses moral hazard and adverse selection challenges, with the goal of optimizing blockchain utility in complex wireless environments. Liu et al. [
11] presented a blockchain-based distributed operation and incentive solution for P-RAN, emphasizing reliability. Liu et al. [
12] proposed an optimal incentive strategy in blockchain-enabled mobile crowdsensing through game-theoretic analysis, while Cai et al. [
13] employed a Bayesian game-driven incentive mechanism for secure federated learning in 6G. Yuan et al. [
14] designed an adaptive incentive and resource allocation scheme for blockchain-supported edge video streaming systems. Tang et al. [
15] proposed a game-based blockchain consensus and incentive framework for mobile crowdsensing, and Jain et al. [
16] developed a blockchain-based smart contract technique for cooperative spectrum sensing in cognitive radio networks.
Although consensus mechanisms such as Proof-of-Stake (PoS) and Proof-of-Traffic (PoT) are widely used in blockchain-based wireless architectures, they do not directly address the operational nuances of NOMA relay environments or the intricacies of verifying user experience quality. Many of these solutions also lack the dynamic trust adjustments and stable token-based incentives essential for mitigating dishonest activities and reward volatility in high-frequency networks. Consequently, the neighbors-help-neighbors paradigm in NOMA wireless networks remains underexplored from a blockchain perspective. These shortcomings motivate our proposed approach, which combines PQoE, trust management, and stable rewards within a single decentralized framework.
3. Smart Contracting Framework for NOMA Wireless Relay Networks
In this section, we present our novel smart contracting mechanism that extends standard NOMA architectures by integrating decentralized verification, trust scores, and incentive-based interactions on the Ethereum blockchain. By embedding a Proof of Quality of Experience (PQoE) consensus model, the framework aims to create a secure, auditable environment that motivates short-distance users to act as relays for users farther from the base station.
3.1. System Overview and Architectural Innovation
Traditional NOMA networks allow the base station to transmit a superimposed signal containing data for multiple users, with each user decoding the relevant signal. While short-distance users can help distant users by retransmitting data, standard approaches often fail to incentivize or verify the honesty of these relays.
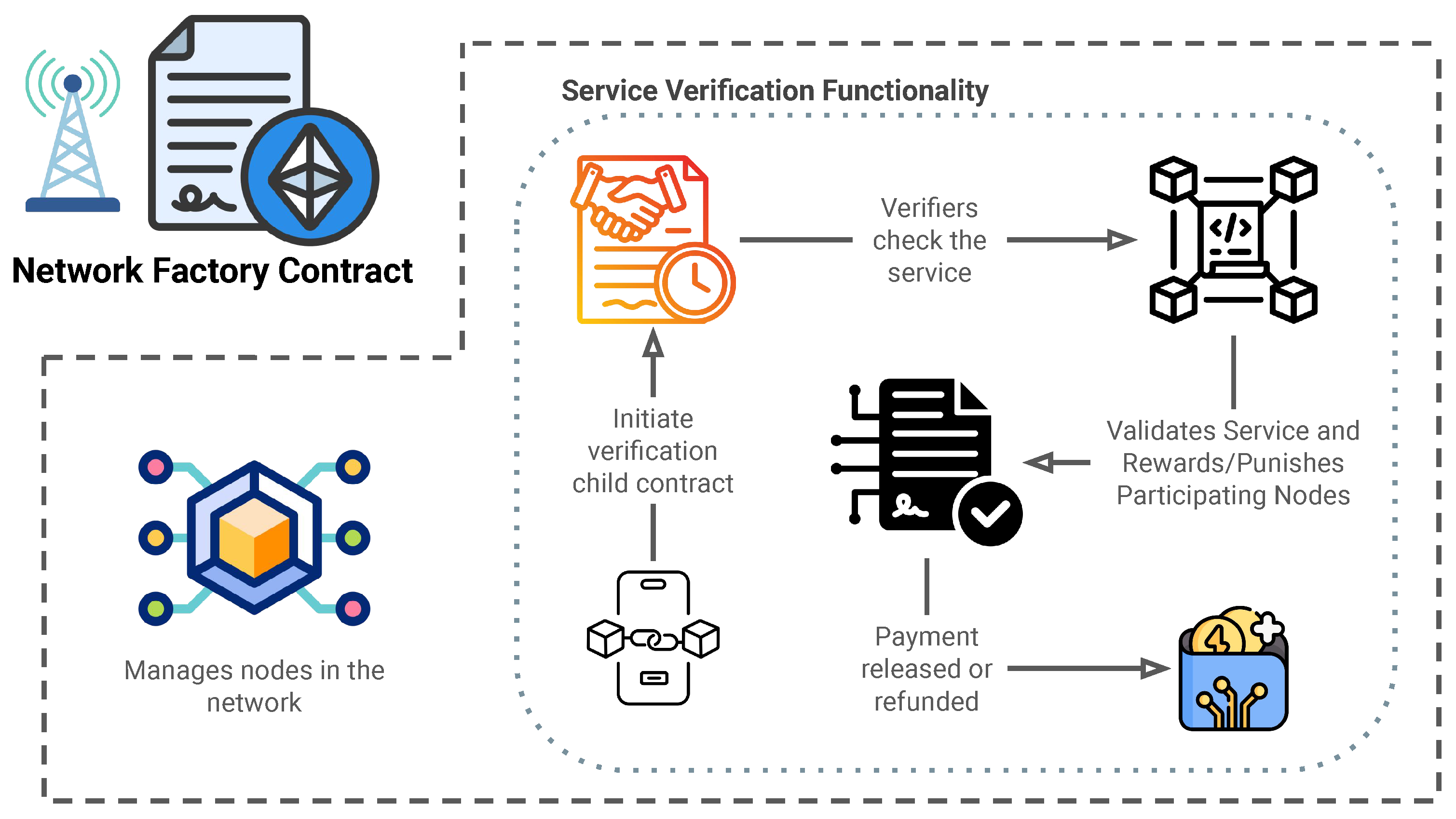
Our proposed framework addresses these gaps by introducing a Service Verification Contract on the Ethereum blockchain, augmented with a PQoE consensus mechanism. As illustrated in
Figure 1, the receiver (farther user) initiates a smart contract specifying payment to the relay (closer user). This contract ensures that the relay offers accurate and timely retransmissions, thereby improving the receiver’s data rate. Verifiers are strategically placed between the relay and the receiver to monitor transmission rates, helping confirm whether the service provided meets the contracted performance levels.
3.1.1. Technical Parameters for PQoE
The core of the PQoE mechanism relies on periodically sampling the relay’s transmission rate, comparing it to expected quality thresholds derived from the Shannon–Hartley theorem and distance-based attenuation models. These comparisons are encapsulated in on-chain smart contract functions that store relevant metrics, such as received power and estimated signal-to-noise ratios. We define a minimal acceptable rate that the receiver should observe, and verifiers collectively validate if the relay’s performance meets or exceeds this threshold. This process acts as an on-chain checkpoint, ensuring the data rate is verifiably tracked over multiple intervals before the system finalizes a decision.
3.1.2. The Network Contract
The Network Contract serves as the foundational smart contract that manages all nodes participating in the system. It handles initialization, storage, and dynamic management of nodes, ensuring efficient operation and scalability. Crucially, the Network Contract encompasses the functionality of the Service Verification Contract within itself, allowing receivers to initiate service requests and verifications without deploying additional smart contracts. This integration avoids excessive gas fees and enhances cost-effectiveness.
All nodes on the network are initialized and stored using a mapping data structure (e.g., a hash table) that associates unique node identifiers with their corresponding data, including trust scores, roles, and status. Each node is assigned an initial neutral trust score. Trust scores are pivotal for determining a node’s eligibility to participate in verification and influence the weight of their votes during PQoE checks.
3.1.3. The Service Verification Process
The Service Verification Process, embedded within the Network Contract, ensures that services provided by relays meet required quality standards:
Roles and Parameters: The process defines the roles of receiver, relay, and verifier, along with the agreed-upon fee.
Escrow Mechanism: The service fee is deposited in escrow. If verification succeeds, the relay is compensated; otherwise, funds revert to the receiver.
Adaptive Verification: Multiple verification rounds can occur until the system has sufficient confidence. This effectively serves as a multi-level mechanism, as dishonest behaviors across several rounds are more likely to be detected, thereby strengthening overall security.
Data Rate Assessment: Verifiers compare the relay-to-receiver data rate to expected values and check consistency with the relay-to-verifier measurements.
Payment Release and Penalties: Verified services trigger payment releases, while failure or insufficient verifications cause refunds. Trust scores are updated in either case.
3.1.4. System Dynamics
The system integrates trust scores and incentive mechanisms to promote honest behavior. Verification requirements adapt based on trust, ensuring high-trust relays require fewer confirmations while low-trust relays undergo intensified scrutiny.
Trust Evaluation Mechanism: Each verifier’s vote is weighted by its trust score, and the relay’s trust score shapes how many verifiers are required. In practice, misreports or discrepancies identified by other honest nodes lower trust values for potential attackers.
Rewards and Penalties: Honest participants see incremental boosts in their trust scores and direct financial rewards, while malicious actions reduce trust levels and can lead to exclusion from the network.
Progressive Security: Since multiple rounds of verification can be imposed when trust is low, malicious nodes face increasing difficulty in colluding or forging unanimous votes across multiple checks. This approach inherently raises the barrier against more advanced attack scenarios.
4. Proposed Verification Logic for NOMA Wireless Relay and Neighbors
In this section, we present the core verification logic and discuss the simulation-based algorithms used to evaluate a relay’s service.
Figure 1 introduced the overall framework, and here we focus on how trust scores and verification requirements evolve during the process. The step-by-step procedure is outlined in Algorithm 1, which describes how verifiers assess relay-receiver transmissions, provide weighted votes, and determine whether a relay’s service is verified.
| Algorithm 1 Service Verification Algorithm |
- 1:
Input: Relay R, Receiver , set of Verifiers V (with trust scores), base verification requirement , channel parameters, and maximum time . - 2:
Initialize: . - 3:
Monitor the transmission from R to . - 4:
for each verifier with do - 5:
; - 6:
- 7:
if and then - 8:
v marks the service as trustworthy. - 9:
else - 10:
v marks the service as untrustworthy. - 11:
end if - 12:
end for - 13:
Compute , , . - 14:
if
and
then - 15:
Verified: increase , adjust verifiers’ trust scores, release payment, reward verifiers. - 16:
else if and then - 17:
Not verified: decrease , refund , adjust verifiers’ trust scores. - 18:
else - 19:
Insufficient verifications: return funds to , no trust penalties. - 20:
end if
|
4.1. Proposed Verification Logic
4.1.1. Verification Criteria
The core verification criterion for PQoE relies on comparing data transmission rates between the relay–receiver link and the relay–verifier link. We use the Shannon–Hartley theorem to compute:
We also introduce a Relay–Receiver Distance Factor (RRDF):
A service is considered verified if:
Verifiers positioned between the relay and the receiver conduct these checks, and each verifier must have a trust score above
to minimize malicious influence.
4.1.2. Weighted Verification Count
Each verifier’s influence on the total verification depends on its trust score:
where
is the weight from verifier
i, and
is its trust score. The total weighted count sums all verifiers’ weights:
4.1.3. Adjusted Required Verifications
The required number of verifications,
, depends on the relay’s trust score
:
Relays with higher trust scores need fewer confirmations, while low-trust relays must pass multiple verifications before the service is approved.
4.1.4. Verification Outcome Determination
To finalize a service as verified, two conditions must be met:
If the result is positive, trust scores increase and the relay is compensated. Otherwise, the receiver is refunded. If
by the deadline
, funds are returned without penalties.
Algorithm 1 summarizes these steps, illustrating how multiple checks may be necessary when trust is low.
5. Results and Discussion
In this section, we evaluate the performance of the proposed verification framework through simulation studies designed to illustrate how trust and verification requirements adapt when both honest and malicious verifiers are present. We also provide a comparative discussion to situate our solution within the broader literature and examine how advanced attack scenarios could be mitigated through multi-round checks.
5.1. Simulation Results
We consider a network that includes one base station, one receiver, one honest relay, and twenty-four verifiers (twenty honest and four malicious), for a total of twenty-seven nodes. The verification system is tested over 40 discrete rounds. The smart contracts are compiled using Truffle and deployed to a local Ethereum blockchain simulated by Ganache. We rely on Truffle’s testing suite, enhanced with OpenZeppelin’s test-helpers, to replicate on-chain transactions and measure how verifiers respond to different transmission outcomes. During each round, the honest relay consistently provides accurate data, and malicious verifiers misreport outcomes in roughly 70–80% of the rounds. Each verifier’s trust score evolves as correct or incorrect decisions are identified through consensus. The system tracks both the total weighted verification count and the required number of verifiers per round, highlighting how dynamically adjusting trust-based thresholds influences the verification process.
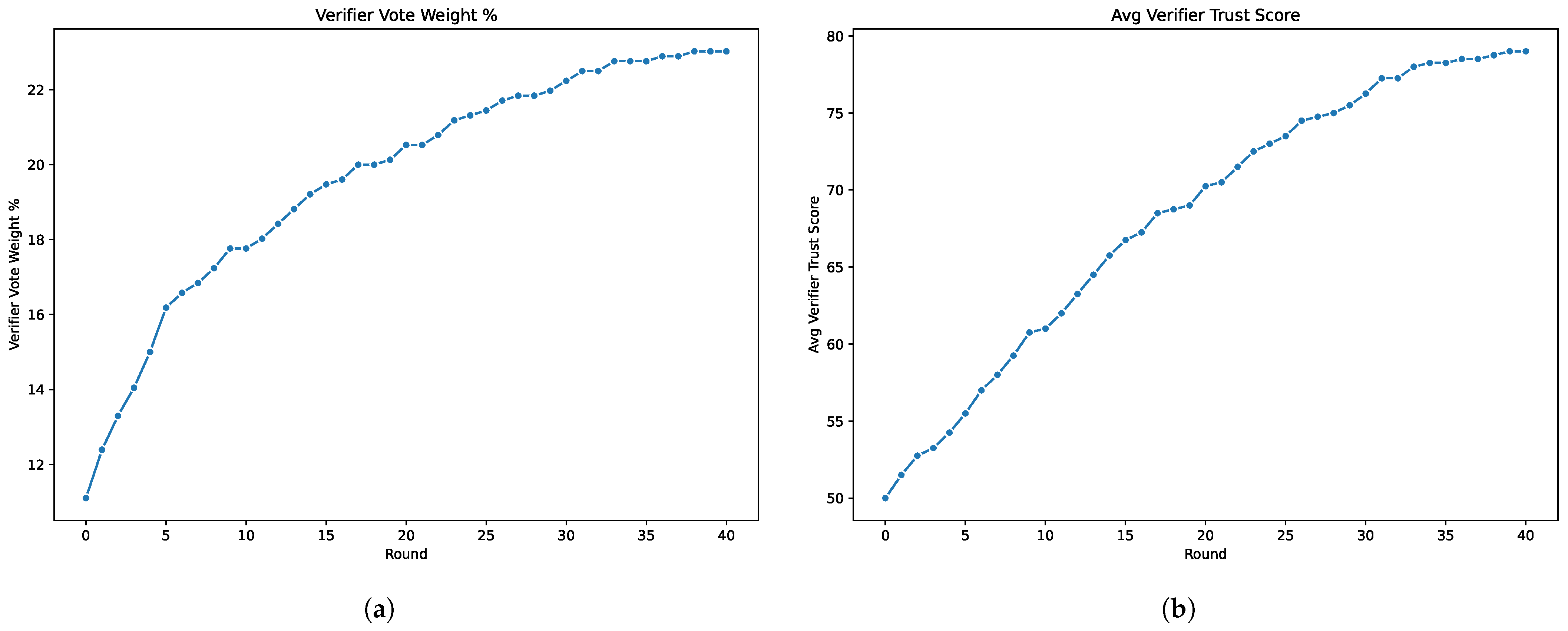
Figure 2a illustrates the evolution of the average percentage of vote weight of the verifiers. Initially, trust scores are neutral, so the vote weight is low. As verifiers demonstrate reliable behavior, their trust scores climb, leading to greater weighted impact in subsequent rounds.
Figure 2b shows the average trust score among all verifiers, indicating that honest verifiers see their scores rise consistently, while malicious verifiers incur penalties.
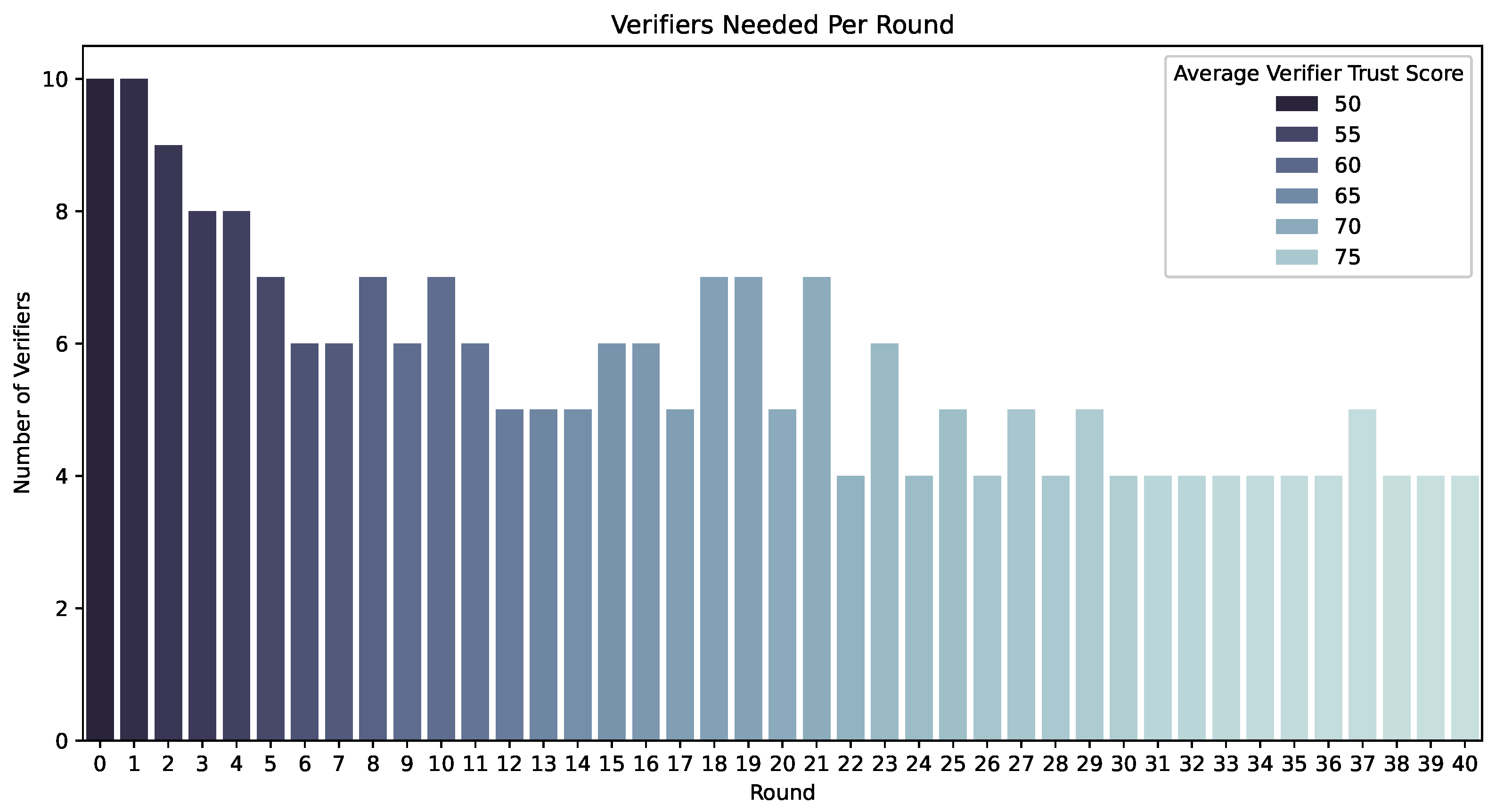
Figure 3 presents the required number of verifiers each round (vertical bars) alongside the average verifier trust score (color scale). Early in the simulation, more verifiers are required because the network lacks historical data on node reliability. As trust builds for honest nodes, fewer verifiers are needed in subsequent rounds. The gradually lighter bar colors illustrate how verifiers’ average trust scores improve over time, allowing the system to reduce overhead once nodes have proven their integrity.
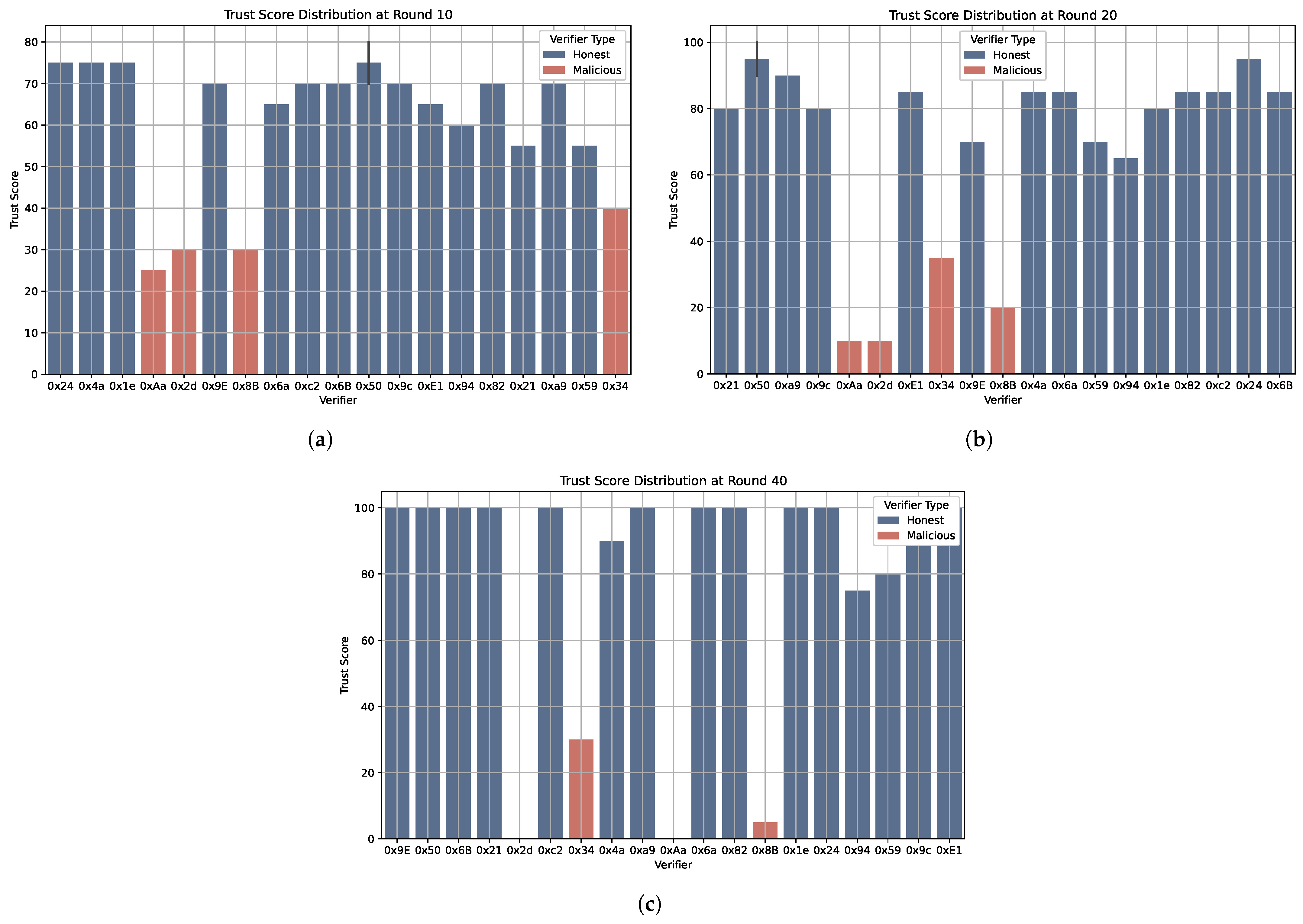
By Round 10 (
Figure 4a), honest verifiers begin to separate from malicious ones. At Round 20 (
Figure 4b), the gap widens further, and by Round 40 (
Figure 4c), honest verifiers approach the upper trust range while malicious verifiers cluster at the lower end. This divergence confirms that repeated honest contributions yield higher credibility over time.
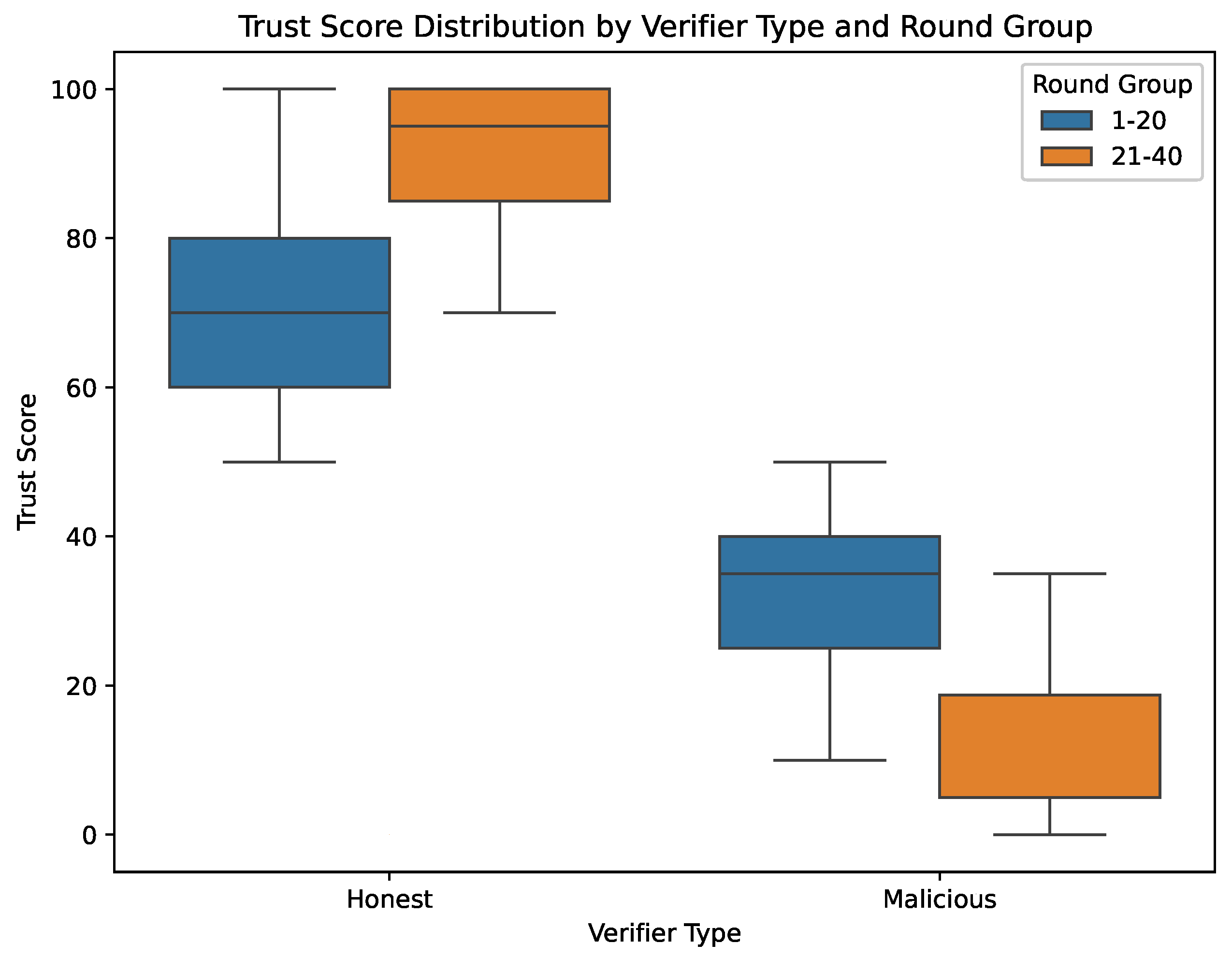
Figure 5 depicts trust score distributions for honest (left) and malicious (right) verifiers in early rounds (1–20) versus later rounds (21–40). Honest verifiers show a steady climb in median scores, while malicious verifiers undergo further penalization. The system thus naturally promotes honest participants and disenfranchises malicious ones.
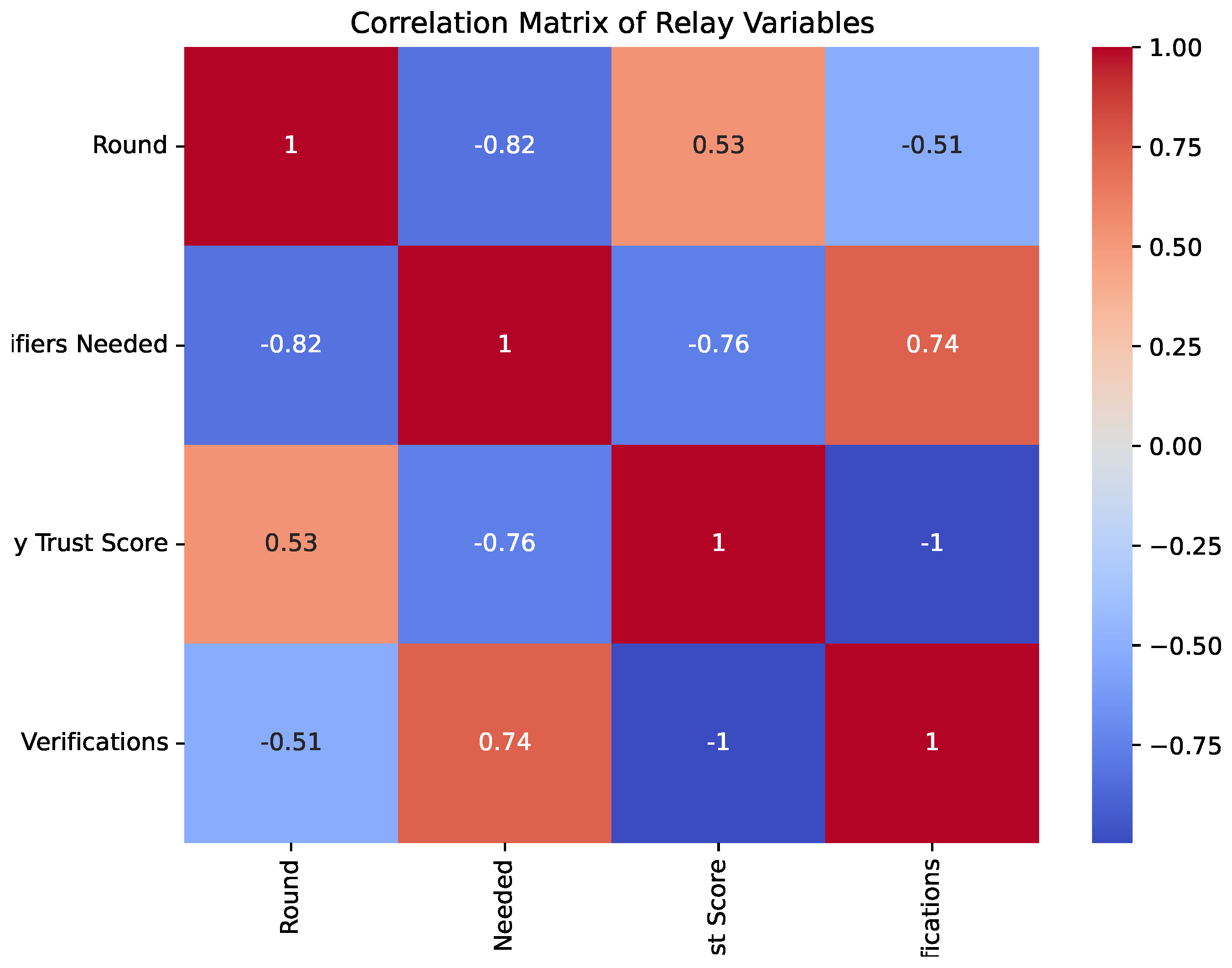
In
Figure 6, the negative correlation between Round and Verifiers Needed illustrates that fewer verifiers are required over time. Meanwhile, Relay Trust Score shows a moderate positive correlation with Round, reflecting that repeated verifications strengthen the relay’s credibility. Additionally, Relay Trust Score and Verifiers Needed exhibit a strong negative correlation, indicating that higher relay trust scores mitigate the necessity for further verification.
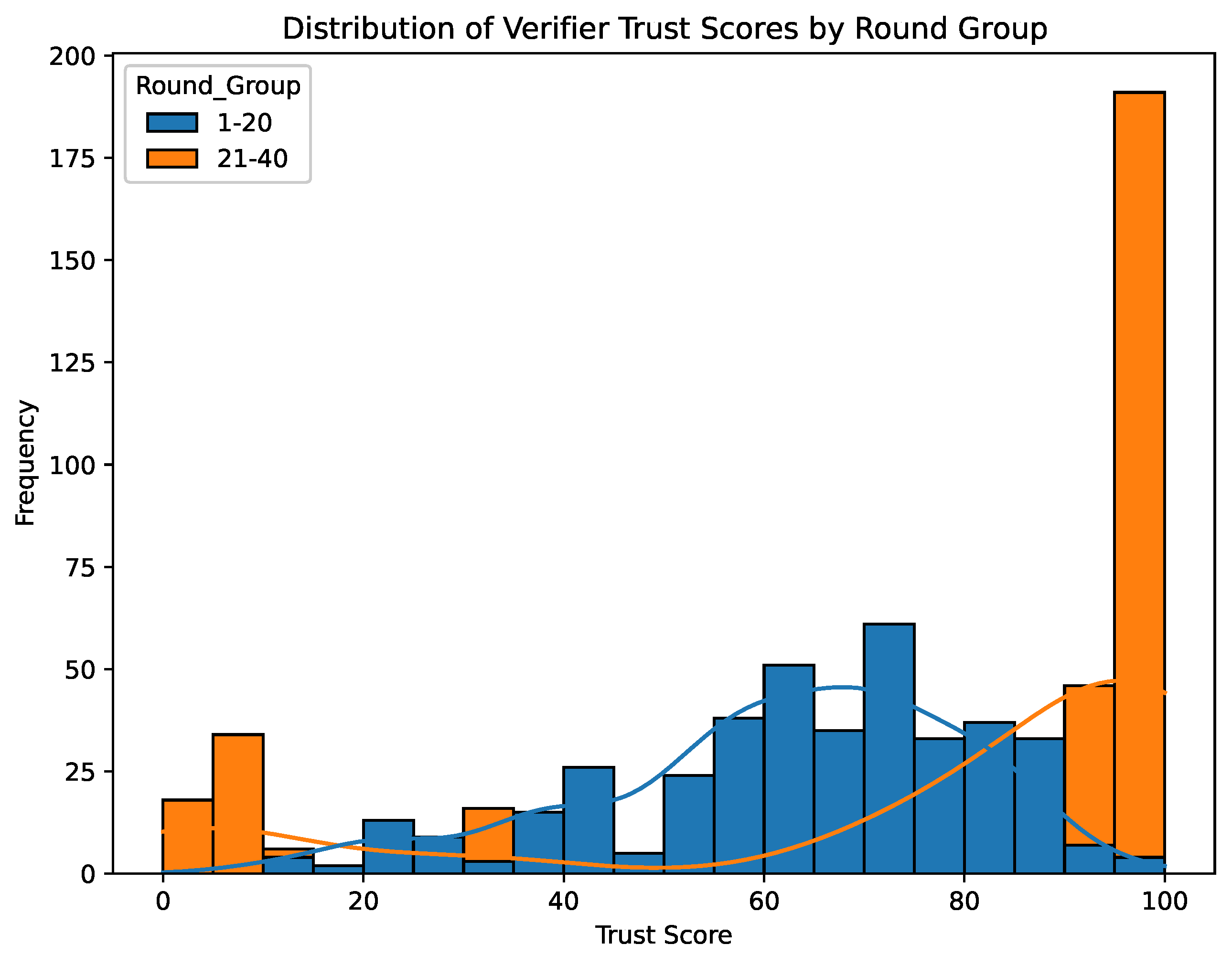
Figure 7 contrasts the distribution of verifier trust scores in Rounds 1–20 (blue) with Rounds 21–40 (orange). As the simulation proceeds, more verifiers cluster near the top of the trust scale, illustrating the network’s natural inclination toward rewarding repeated honest behavior.
5.2. Comparison with Existing Approaches
While our approach is novel in its use of a Proof of Quality of Experience (PQoE) mechanism within a NOMA relay setting, key parallels with other blockchain-enabled solutions can be identified. Helium [
7] leverages a Proof-of-Coverage model to verify hotspot reliability, but does not address dynamic trust-based incentives or repeated multi-round checks. Proof-of-Stake (PoS) is commonly used in public blockchains but does not evaluate data rate or user experience quality. Proof-of-Traffic (PoT) [
9] focuses on traffic metrics rather than distance-based or QoE-driven verifications. Moreover, the Proof-of-QoE NOMA Token proposed by Ramamoorthy et al. [
8] lacks refined trust score mechanisms and does not implement multi-round checks. Our system uniquely integrates trust scores, adjustable verification thresholds, and stable token rewards, making it well suited for NOMA relay deployments that prioritize verifiable quality and resistance to advanced attacks.
5.3. Additional Discussion: Security Enhancements and Implementation Challenges
Our multi-round verification strategy inherently increases resilience to advanced collusion or eclipse attacks by requiring malicious nodes to consistently deceive multiple verifiers across multiple checks. While this approach does not eliminate the possibility of sophisticated adversaries, it raises the cost of executing large-scale malicious activities. Incorporating further multi-level verification could include cross-validation by different sets of verifiers in separate intervals, though this would need to be balanced against potential increases in overhead.
We acknowledge that privacy is an important concern for many blockchain applications, but it falls outside the primary scope of this paper. Future work could investigate privacy-preserving methods for sharing channel metrics or trust data. Similarly, real-world deployment might encounter regulatory or technological barriers, including the availability of stable tokens in certain jurisdictions. Nonetheless, our results suggest that the proposed mechanism significantly enhances the security and reliability of NOMA relay systems while remaining cost-effective within the Ethereum framework.
6. Conclusions
Future generations of wireless networks, operating at higher frequencies, will face Non-Line-of-Sight signal blockage and massive access challenges while supporting smart industries and intelligent automation systems. In this paper, we proposed a framework that integrates blockchain technology and NOMA relay wireless access through smart contracts, providing a robust solution to incentivize cooperation and ensure service reliability. By leveraging trust scores and dynamic verification mechanisms, the system promotes honest behavior and deters malicious activities. The Proof of Quality of Experience consensus mechanism and use of StableCoins for payment ensure both transaction stability and practical deployment feasibility.
Our simulation results confirm that honest verifiers accumulate higher trust over repeated interactions, while malicious nodes lose their influence. This reinforces the viability of the proposed solution for next-generation wireless networks, paving the way for more efficient and secure communications in future smart and intelligent systems. In comparison to related solutions, the integration of a PQoE mechanism, stable rewards, and adaptive trust-based verifications sets our approach apart, offering an effective balance between decentralized security, cost-effectiveness, and practical usability.
Author Contributions
Conceptualization, V.S. and W.W.; methodology, V.S.; software, V.S.; validation, V.S. and W.W.; formal analysis, V.S. and W.W.; investigation, V.S.; resources, W.W.; data curation, V.S.; writing—original draft preparation, V.S.; writing—review and editing, W.W.; visualization, V.S.; supervision, W.W.; project administration, W.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The data, models, or codes that support the findings of this study are available from the corresponding author upon request.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
| PQoE | Proof of Quality of Experience |
| NOMA | Non-Orthogonal Multiple Access |
| RVD | Relay–Verifier Data Rate |
| RRD | Relay–Receiver Data Rate |
| RRDF | Relay–Receiver Distance Factor |
References
- Akyildiz, I.F.; Kak, A.; Nie, S. 6G and Beyond: The Future of Wireless Communications Systems. IEEE Access 2020, 8, 133995–134030. [Google Scholar] [CrossRef]
- Jha, A.V.; Appasani, B.; Khan, M.S.; Zeadally, S.; Katib, I. 6G for Intelligent Transportation Systems: Standards, Technologies, and Challenges. Telecommun. Syst. 2024, 86, 241–268. [Google Scholar] [CrossRef]
- Tataria, H.; Shafi, M.; Molisch, A.F.; Dohler, M.; Sjöland, H.; Tufvesson, F. 6G Wireless Systems: Vision, Requirements, Challenges, Insights, and Opportunities. Proc. IEEE 2021, 109, 1166–1199. [Google Scholar] [CrossRef]
- Khan, R.; Tsiga, N.; Asif, R. Interference Management with Reflective In-Band Full-Duplex NOMA for Secure 6G Wireless Communication Systems. Sensors 2022, 22, 2508. [Google Scholar] [CrossRef] [PubMed]
- Lyu, L.; Guan, X.; Cheng, N.; Shen, X.S. Advanced Wireless Technologies for Industrial Automation. In Advanced Wireless Technologies for Industrial Network Systems; Springer International Publishing: Cham, Switzerland, 2023; pp. 21–71. [Google Scholar] [CrossRef]
- Alla, K.R.; Thangarasu, G. Improved Data Transmission Using NOMA Technology for Office Automation Application. In Proceedings of the 2023 IEEE 13th Symposium on Computer Applications & Industrial Electronics (ISCAIE), Penang, Malaysia, 20–21 May 2023; pp. 186–191. [Google Scholar] [CrossRef]
- Haleem, A.; Allen, A.; Thompson, A.; Nijdam, M.; Garg, R. Helium: A Decentralized Machine Network. In Proceedings of the an Academic Conference. 2018. Available online: https://api.semanticscholar.org/CorpusID:51236036 (accessed on 10 January 2025).
- Ramamoorthy, K.K.; Wang, W.; Sohraby, K.; Zhao, Y. Proof-of-QoE NOMA Token: A Crypto Rewarding Concept to Incentivize Local Relay in Non-Orthogonal Multiple Access Wireless Networks. In Proceedings of the 2024 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 26–29 February 2024; pp. 311–315. [Google Scholar] [CrossRef]
- Choi, S.; Wu, Y.; Liu, G.; Xie, Z.; Zhang, S.; Wang, X. Proof of Traffic: An Incentive Mechanism for Traffic Sharing in Decentralized Wireless Networks. In Proceedings of the 2023 IEEE 9th World Forum on Internet of Things (WF-IoT), Aveiro, Portugal, 12–27 October 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, W.; Chen, J.; Jiao, Y.; Kang, J.; Dai, W.; Xu, Y. Connectivity-Aware Contract for Incentivizing IoT Devices in Complex Wireless Blockchain. IEEE Internet Things J. 2023, 10, 10413–10425. [Google Scholar] [CrossRef]
- Liu, X.; Chen, X.; Bi, Q.; Liang, W.; Li, J.; Zhang, Z. Blockchain-Based Distributed Operation and Incentive Solution for P-RAN. Comput. Commun. 2023, 198, 77–84. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, S.; Zhang, D.; Zhang, Q.; Wang, J. Optimal Incentive Strategy in Blockchain-Based Mobile Crowdsensing Using Game Theory. Comput. Netw. 2023, 237, 110053. [Google Scholar] [CrossRef]
- Cai, L.; Dai, Y.; Hu, Q.; Zhou, J.; Zhang, Y.; Jiang, T. Bayesian Game-Driven Incentive Mechanism for Blockchain-Enabled Secure Federated Learning in 6G Wireless Networks. IEEE Trans. Netw. Sci. Eng. 2024, 11, 4951–4964. [Google Scholar] [CrossRef]
- Yuan, S.; Zhou, Q.; Li, J.; Guo, S.; Chen, H.; Wu, C.; Yang, Y. Adaptive Incentive and Resource Allocation for Blockchain-Supported Edge Video Streaming Systems: A Cooperative Learning Approach. IEEE Trans. Mob. Comput. 2025, 24, 539–556. [Google Scholar] [CrossRef]
- Tang, C.; Bao, Z.; Cai, X.; Lin, F.; Zhang, Z.; Chen, G. A Game-Enabled Blockchain Consensus and Incentive Mechanism for Secure and Efficient Mobile Crowdsensing. IEEE Syst. J. 2024, 18, 210–221. [Google Scholar] [CrossRef]
- Jain, A.; Gupta, N.; Sreenu, M. Blockchain based smart contract for cooperative spectrum sensing in cognitive radio networks for sustainable beyond 5G wireless communication. Green Technol. Sustain. 2023, 1, 100019. [Google Scholar] [CrossRef]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).