A Seamless Authentication Scheme for Edge-Assisted Internet of Vehicles Environments Using Chaotic Maps
Abstract
1. Introduction
- We propose a chaotic map-based [10] initial authentication scheme for V2I communications. The Chebyshev chaotic map has a lower computational cost than elliptic curve-based authentication. Thus, it can ensure efficient authentication for IoV environments.
- We propose re-authentication and handover authentication schemes to ensure seamless communication in IoV environments. After the initial authentication, the ES stores the pseudo identity of the authenticated vehicle and sets the expiration time. It can lead to authenticating the vehicle quickly during the re-authentication process. In a handover situation, the ES transmits information about the vehicle in advance to the other ES and enables the performance of a quick handover authentication.
- We analyzed the security of our scheme using the Scyther tool and RoR model to show that our scheme can guarantee mutual authentication and session key security. We also compared the proposed scheme with previous schemes in terms of computational costs, communication cost, and security features. We show that the proposed scheme has better security and has lower computational cost than other schemes.
Paper Organization
2. Related Work
3. Preliminary
3.1. Chaotic Map
3.1.1. Definition
3.1.2. Hardness Assumptions
- 1.
- ECMDL problem: When a big integer is given, there is no efficient algorithm to find s which satisfies ≡ y in polynomial time.
- 2.
- ECMCDH problem: When p and p for big integers y and z are given, there is no efficient algorithm to calculate p in polynomial time.
- 3.
- ECMDDH problem: When p, p, and for big integers y, z, and r are given, it is hard to determine whether .
3.2. Threat Model
- The adversary has complete control over the wireless communication channels, and can eavesdrop, modify, and delete the messages transmitted in wireless channels.
- The adversary can act as a middleman between communication entities, performing replay attacks and man-in-the-middle attacks.
- The adversary can try to trace an identity or location of a vehicle using obtained messages from wireless channels.
- The adversary can obtain long-term or short-term keys of the network and try to reveal the session key.
3.3. Design Goal
- 1.
- Mutual authentication: A vehicle and an edge server must verify each other’s legitimacy before agreeing to a session key. The communication should be rejected if the other party cannot be authenticated during the authentication phase.
- 2.
- Vehicle privacy: A vehicle’s identity, location, and transmitted data must be hidden in wireless channels. If traceable messages are continuously sent from a vehicle, an adversary may be able to guess the vehicle’s location or personal information.
- 3.
- Perfect forward secrecy: Even if the network is compromised and long-term keys are leaked, previously agreed-upon session keys must not be calculated. This includes session keys in all situations of initial authentication, handover authentication, and re-authentication.
- 4.
- Resistance to ephemeral secret leakage attack: Even if random numbers generated in a session are leaked to an adversary, the adversary cannot calculate the session key.
- 5.
- Seamless authentication: Considering the characteristics of IoV environments, it is necessary to lower the computational cost in repeated authentication situations. Furthermore, security must be guaranteed during the re-authentication and handover authentication processes.
3.4. System Model
- CS: CS is a fully trusted entity that initializes the network, distributes secret keys for edge servers, and registers vehicles.
- ES: ESs communicate with vehicles in real-time and provide services. The transmitted data between an ES and a vehicle may contain sensitive and private data of the vehicle, and the transmission should be carried out after being mutually authenticated. In addition, when vehicles’ handover or re-authentication occurs, ESs should be able to verify vehicles quickly to ensure real-time communication.
- Vehicle: A vehicle with a user registers with CS and participates in the network. Vehicles initially authenticate with a nearby ES, and perform re-authentication and handover authentication with ESs frequently. An adversary may attempt to masquerade as a legitimate vehicle and steal private information.
4. Proposed Scheme
4.1. System Initialization
4.2. Vehicle Registration
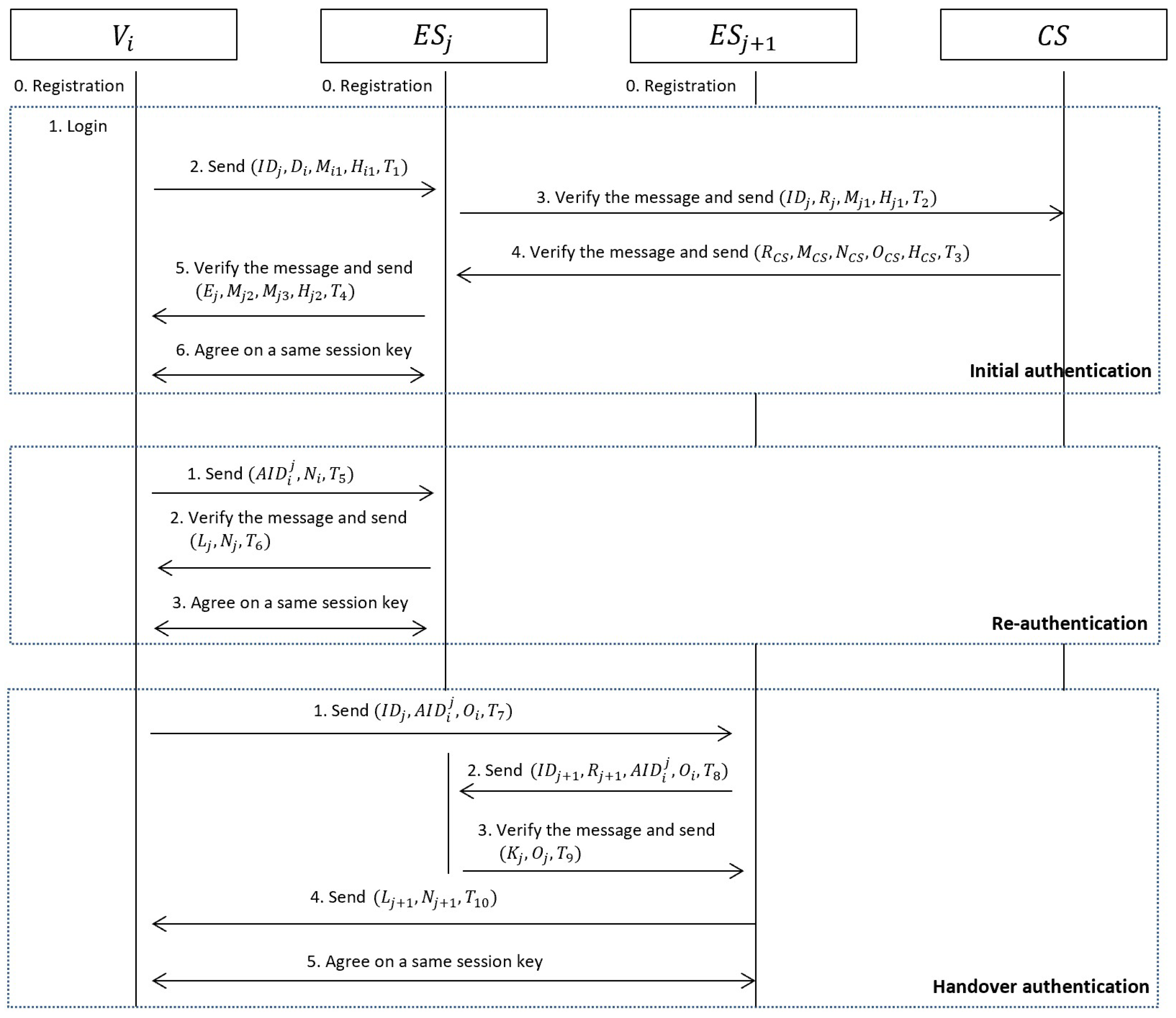
4.3. Login and Initial Authentication
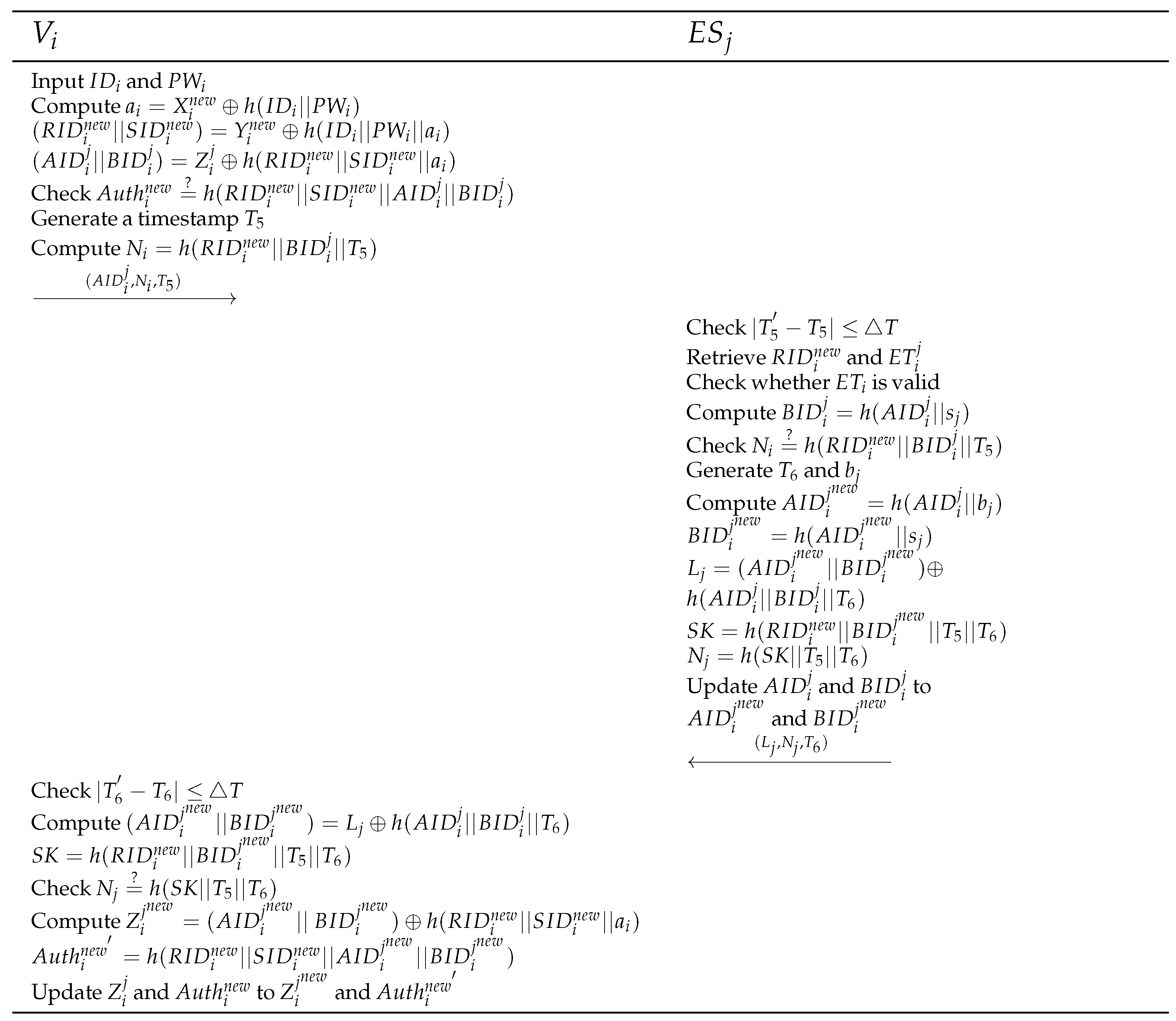
4.4. Re-Authentication
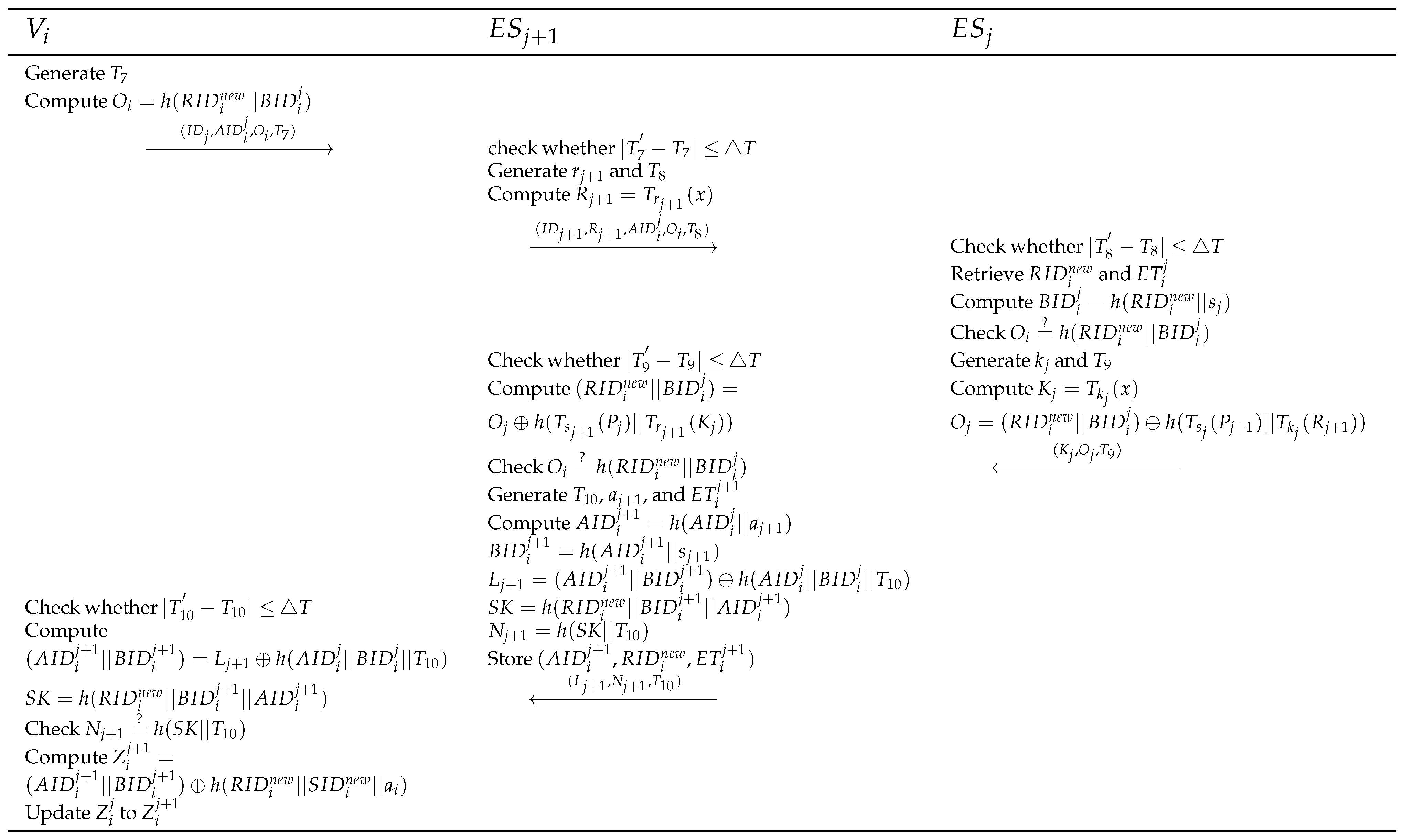
4.5. Handover Authentication
5. Security Analysis
5.1. Informal Analysis
5.1.1. Resistance to Replay Attacks
5.1.2. Resistance to Privileged Insider Attacks
5.1.3. Resistance to Impersonation Attacks
5.1.4. Support Perfect Forward Secrecy
5.1.5. Resistance to Ephemeral Session Random Number Leakage Attacks
5.1.6. Support Vehicle Anonymity and Untraceability
5.2. Formal Security Under RoR Model
- : In , we assume that A has no information about the session key and performs no queries. When denotes the probability of A succeeding in guessing the correct bit c after ends, we can induce the following equation by the definition of the semantic security:
- : A performs and queries in the first game. In our scheme, A cannot obtain any values to calculate through a public channel. In the proposed scheme, the session key is calculated by . A cannot obtain any of the values to calculate through a public channel. Therefore, A has no advantage by executing query for guessing successfully, and we can induce the following equation at the end of :
- : A performs and queries to calculate in this game. Each message transmitted through a public channel includes a timestamp and message hash value, and A cannot arbitrarily modify the message. Therefore, A must find a hash collision to compromise of our scheme. Then, the advantage function of A after the end of can be induced as follows:
- : A can perform query and can obtain the stored values of such as , , and . If A succeeds to log in and sends an authentication request a message to , then A can agree on a session key with disguising as . However, for this attack to succeed, A must successfully guess the correct and , which is mathematically impossible. Assuming that A has and , the probability of successful guessing is
5.3. Scyther Tool
6. Performance Analysis
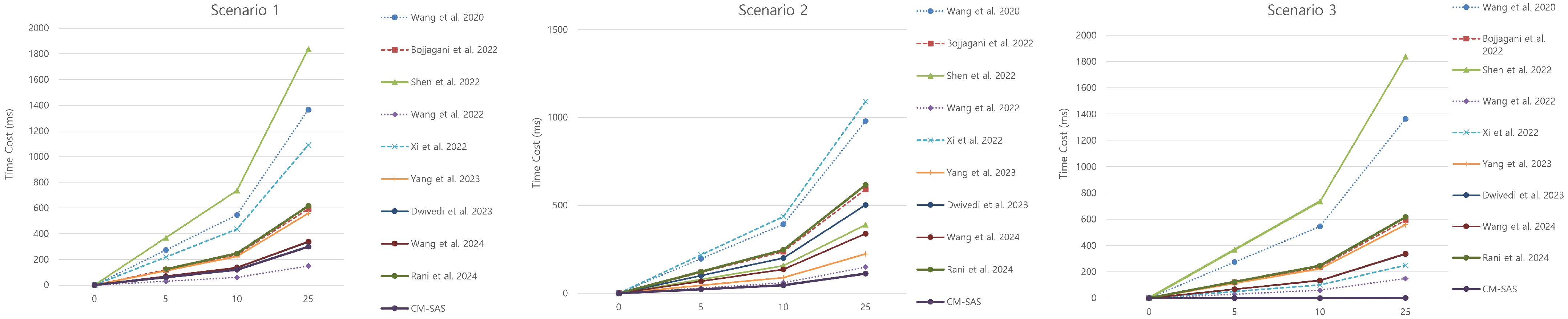
6.1. Computational Cost
6.2. Communication Cost
6.3. Security Features
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ji, B.; Zhang, X.; Mumtaz, S.; Han, C.; Li, C.; Wen, H.; Wang, D. Survey on the internet of vehicles: Network architectures and applications. IEEE Commun. Stand. Mag. 2020, 4, 34–41. [Google Scholar] [CrossRef]
- Contreras-Castillo, J.; Zeadally, S.; Guerrero-Ibañez, J.A. Internet of vehicles: Architecture, protocols, and security. IEEE Internet Things J. 2018, 5, 3701–3709. [Google Scholar] [CrossRef]
- Girdhar, M.; Hong, J.; Moore, J. Cybersecurity of autonomous vehicles: A systematic literature review of adversarial attacks and defense models. IEEE Open J. Veh. Technol. 2023, 4, 417–437. [Google Scholar] [CrossRef]
- Yan, C.; Wang, C.; Shen, J.; Dev, K.; Guizani, M.; Wang, W. Edge-assisted hierarchical batch authentication scheme for VANETs. IEEE Trans. Veh. Technol. 2024, 73, 1253–1262. [Google Scholar] [CrossRef]
- Tian, J.F.; Ni, R. An identity authentication and key agreement protocol for the Internet of Vehicles based on trusted cloud-edge-terminal architecture. Veh. Commun. 2024, 49, 100825. [Google Scholar] [CrossRef]
- Mazhar, S.; Rakib, A.; Pan, L.; Jiang, F.; Anwar, A.; Doss, R.; Bryans, J. State-of-the-art authentication and verification schemes in VANETs: A survey. Veh. Commun. 2024, 49, 100804. [Google Scholar] [CrossRef]
- Rawat, P.; Singh, K.D.; Chaouchi, H.; Bonnin, J.M. Wireless sensor networks: A survey on recent developments and potential synergies. J. Supercomput. 2014, 68, 1–48. [Google Scholar] [CrossRef]
- Manivannan, D.; Moni, S.S.; Zeadally, S. Secure authentication and privacy-preserving techniques in Vehicular Ad-hoc NETworks (VANETs). Veh. Commun. 2020, 25, 100247. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Zhang, L. Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos Solitons Fractals 2008, 37, 669–674. [Google Scholar] [CrossRef]
- Wang, C.; Shen, J.; Lai, J.F.; Liu, J. B-TSCA: Blockchain assisted trustworthiness scalable computation for V2I authentication in VANETs. IEEE Trans. Emerg. Top. Comput. 2020, 9, 1386–1396. [Google Scholar] [CrossRef]
- Bojjagani, S.; Reddy, Y.C.A.P.; Anuradha, T.; Rao, P.V.V.; Reddy, B.R.; Khan, M.K. Secure authentication and key management protocol for deployment of Internet of Vehicles (IoV) concerning intelligent transport systems. IEEE Trans. Intell. Transp. Syst. 2022, 23, 24698–24713. [Google Scholar] [CrossRef]
- Shen, M.; Lu, H.; Wang, F.; Liu, H.; Zhu, L. Secure and efficient blockchain-assisted authentication for edge-integrated internet-of-vehicles. IEEE Trans. Veh. Technol. 2022, 71, 12250–12263. [Google Scholar] [CrossRef]
- Wang, W.; Han, Z.; Alazab, M.; Gadekallu, T.R.; Zhou, X.; Su, C. Ultra super fast authentication protocol for electric vehicle charging using extended chaotic maps. IEEE Trans. Ind. Appl. 2022, 58, 5616–5623. [Google Scholar] [CrossRef]
- Xi, N.; Li, W.; Jing, L.; Ma, J. ZAMA: A ZKP-based anonymous mutual authentication scheme for the IoV. IEEE Internet Things J. 2022, 9, 22903–22913. [Google Scholar] [CrossRef]
- Yang, Q.; Zhu, X.; Wang, X.; Fu, J.; Zheng, J.; Liu, Y. A novel authentication and key agreement scheme for Internet of Vehicles. Future Gener. Comput. Syst. 2023, 145, 415–428. [Google Scholar] [CrossRef]
- Dwivedi, S.K.; Amin, R.; Vollala, S.; Khan, M.K. B-HAS: Blockchain-assisted efficient handover authentication and secure communication protocol in VANETs. IEEE Trans. Netw. Sci. Eng. 2023, 10, 3491–3504. [Google Scholar] [CrossRef]
- Wang, S.; Fan, Z.; Su, Y.; Zheng, B.; Liu, Z.; Dai, Y. A Lightweight, Efficient, and Physically Secure Key Agreement Authentication Protocol for Vehicular Networks. Electronics 2024, 13, 1418. [Google Scholar] [CrossRef]
- Rani, D.; Sachin, T. BTTAS: Blockchain-based Two-Level Transferable Authentication Scheme for V2I communication in VANET. Comput. Electr. Eng. 2024, 120, 109767. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C.-C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–207. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Analysis of key-exchange protocols and their use for building secure channels. In International Conference on the Theory and Applications of Cryptographic Techniques, Proceedings of the EUROCRYPT 2001: Advances in Cryptology— EUROCRYPT 2001, Innsbruck, Austria, 6–10 May 2001; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2045, pp. 453–474. [Google Scholar]
- Sutrala, A.K.; Obaidat, M.S.; Saha, S.; Das, A.K.; Alazab, M.; Park, Y. Authenticated key agreement scheme with user anonymity and untraceability for 5G-enabled softwarized industrial cyber-physical systems. IEEE Trans. Intell. Transp. Syst. 2021, 23, 2316–2330. [Google Scholar] [CrossRef]
- Yu, S.; Park, Y. A robust authentication protocol for wireless medical sensor networks using blockchain and physically unclonable functions. IEEE Internet Things J. 2022, 9, 20214–20228. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the International Workshop on Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 65–84. [Google Scholar]
- Ryu, J.; Son, S.; Lee, J.; Park, Y.; Park, Y. Design of secure mutual authentication scheme for metaverse environments using blockchain. IEEE Access 2022, 10, 98944–98958. [Google Scholar] [CrossRef]
- Prajapat, S.; Gautam, D.; Kumar, P.; Jangirala, S.; Das, A.K.; Park, Y.; Lorenz, P. Secure lattice-based aggregate signature scheme for vehicular Ad Hoc networks. IEEE Trans. Veh. Technol. 2024, 73, 12370–12384. [Google Scholar] [CrossRef]
- Scyther Tool. Available online: https://people.cispa.io/cas.cremers/scyther/ (accessed on 6 December 2024).
- Kilinc, H.H.; Yanik, T. A survey of SIP authentication and key agreement schemes. IEEE Commun. Surv. Tutor. 2013, 16, 1005–1023. [Google Scholar] [CrossRef]
- Abbasinezhad-Mood, D.; Ostad-Sharif, A.; Mazinani, S.M.; Nikooghadam, M. Provably secure escrow-less Chebyshev chaotic map-based key agreement protocol for vehicle to grid connections with privacy protection. IEEE Trans. Ind. Inform. 2020, 16, 7287–7294. [Google Scholar] [CrossRef]



| Ref. | Year | Technique | Strengths | Limitations |
|---|---|---|---|---|
| Wang et al. [11] | 2021 | ECC, bilinear pairing | Consider both initial and handover authentications | High computational cost because of using bilinear pairing |
| Bojjagani et al. [12] | 2022 | ECC | Consider various situations including V2V, V2I, and V2R | Lack of considerations about repeated authentications, high computational cost because of using ECC |
| Shen et al. [13] | 2022 | ECC, blockchain | Store vehicle’s identity on blockchain for handover situation | High storage cost because of using blockchain |
| Wang et al. [14] | 2022 | Chaotic map | Design fast and efficient authentication and re-authentication protocols | Do not consider repeated authentications; RSU cannot retrieve vehicle’s pseudo identity |
| Xi et al. [15] | 2022 | ECC, ZKP | Propose a ZKP-based authentication scheme considering a fast reconnection | High computational cost because of using ECC |
| Yang et al. [16] | 2023 | ECC | Consider subsequent authentication situations for IoV | High computational cost beacuse of using ECC |
| Dwivedi et al. [17] | 2023 | ECC, blockchain | Design blockchain-based IoV system model and propose various authentication schemes | Generate computational load when a vehicle moves to the other region |
| Wang et al. [18] | 2024 | ECC, PUF | Utilize various cryptosystems to guarantee privacy of vehicles | Do not consider handover and re-authentication situations |
| Rani and Tripathi [19] | 2024 | ECC, blockchain | Integrate a blockchain storage for reducing the computational cost in re-authentication | Additional costs arise due to the use of blockchain |
| Notation | Meaning |
|---|---|
| i-th vehicle | |
| j-th edge server | |
| s | secret key of |
| (k = 1, 2, …) | timestamps |
| expiration time of | |
| pseudo identity of | |
| secret identity of | |
| authentication value for login | |
| random nonce | |
| one-way hash function | |
| message digest | |
| message from , , and | |
| pseudo identity of agreed upon between and | |
| secret identity of agreed upon between and |
| Query | Description |
|---|---|
| It represents an eavesdropping attack carried out by A. A can obtain the messages between and transmitted through a wireless channel. | |
| It indicates that A succeeded in corrupting . A can extract stored values in using power analysis attack. | |
| It represents A sending a message to a network participant and that A can receive the response. | |
| It indicates that A performs a one-way hash operation using the obtained values. | |
| It is performed to verify the semantic security of the session key. We assume that there is an unbiased coin c, which of the head represents 1 and the tail represents 0, and the results are veiled from A. When A performs query, c is flipped, and a random number is given to A if , and the session key is given if . At this time, A must be able to determine whether the value is a session key or a random number. |
| Notation | Meaning | Time Cost |
|---|---|---|
| signature generation | 3.85 ms | |
| signature verification | 0.1925 ms | |
| ECC scalar multiplication | 2.226 ms | |
| ECC point addition | 0.0288 ms | |
| modular exponentiation | 3.85 ms | |
| Chebyshev chaotic map | 0.742 ms | |
| bilinear pairing | 5.811 ms | |
| one-way hash | 0.0023 ms |
| Initial Authentication | Handover Authentication | Re-Authentication | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Total | Total | Total | |||||||||
| Wang et al. [11] | ms | ms | - | 54.5786 ms | ms | ms | ms | ms | - | - | - |
| Bojjagani et al. [12] | ms | ms | - | ms | - | - | - | - | - | - | - |
| Shen et al. [13] | ms | ms | ms | ms | ms | - | ms | ms | - | - | - |
| Wang et al. [14] | ms | ms | - | ms | - | - | - | - | - | - | - |
| Xi et al. [15] | ms | ms | - | ms | - | - | - | - | ms | ms | ms |
| Yang et al. [16] | ms | ms | - | ms | ms | - | ms | ms | - | - | - |
| Dwivedi et al. [17] | ms | ms | - | ms | ms | ms | - | ms | - | - | - |
| Wang et al. [18] | ms | ms | - | ms | - | - | - | - | - | - | - |
| Rani and Tripathi [19] | ms | ms | ms | ms | - | - | - | - | - | - | |
| CM-SAS | ms | ms | ms | ms | ms | ms | ms | ms | ms | ms | ms |
| Initial Authentication | Handover Authentication | Re-Authentication | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Total | Total | Total | |||||||||
| Wang et al. [11] | 1056 bits | - | - | 1056 bits | - | 2048 bits | 160 bits | 2208 bits | - | - | – |
| Bojjagani et al. [12] | 2752 bits | 1408 bits | - | 4160 bits | - | - | - | - | - | - | - |
| Shen et al. [13] | 1016 bits | 3808 bits | 960 bits | 5784 bits | 896 bits | - | 1312 bits | 2208 bits | - | - | - |
| Wang et al. [14] | 1056 bits | 768 bits | - | 1824 bits | - | - | - | - | - | - | - |
| Xi et al. [15] | 2240 bits | 256 bits | - | 2496 bits | - | - | - | - | 1728 bits | 256 bits | 1984 bits |
| Yang et al. [16] | 1696 bits | 800 bits | - | 2496 bits | 1696 bits | 800 bits | - | 2496 bits | - | - | - |
| Dwivedi et al. [17] | 1376 bits | 864 bits | - | 2240 bits | 1376 bits | 864 bits | 1472 bits | 3712 bits | - | - | - |
| Wang et al. [18] | 3584 bits | 3872 bits | 128 bits | 7584 bits | - | - | - | - | - | - | - |
| Rani and Tripathi [19] | 576 bits | 1216 bits | 288 bits | 2080 bits | - | - | - | - | - | - | - |
| CM-SAS | 960 bits | 2016 bits | 1312 bits | 4288 bits | 704 bits | 1054 bits | 544 bits | 2752 bits | 544 bits | 544 bits | 1088 bits |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Son, S.; Kwon, D.; Park, Y. A Seamless Authentication Scheme for Edge-Assisted Internet of Vehicles Environments Using Chaotic Maps. Electronics 2025, 14, 672. https://doi.org/10.3390/electronics14040672
Son S, Kwon D, Park Y. A Seamless Authentication Scheme for Edge-Assisted Internet of Vehicles Environments Using Chaotic Maps. Electronics. 2025; 14(4):672. https://doi.org/10.3390/electronics14040672
Chicago/Turabian StyleSon, Seunghwan, DeokKyu Kwon, and Youngho Park. 2025. "A Seamless Authentication Scheme for Edge-Assisted Internet of Vehicles Environments Using Chaotic Maps" Electronics 14, no. 4: 672. https://doi.org/10.3390/electronics14040672
APA StyleSon, S., Kwon, D., & Park, Y. (2025). A Seamless Authentication Scheme for Edge-Assisted Internet of Vehicles Environments Using Chaotic Maps. Electronics, 14(4), 672. https://doi.org/10.3390/electronics14040672






