A Methodology for Online Situational Awareness Provision in a Business Entity
Abstract
1. Introduction
- A comprehensive, methodological approach to online situational awareness management at a company level.
- A methodology for conducting in-depth threat analysis and dynamic risk assessment and propagation in a network of dependent services, business processes, and information infrastructure assets.
- An architecture of a Situational Awareness Management System, its implementation, and its pilot deployment in a critical infrastructure entity.
2. Related Work
3. Impact of Hazard Events
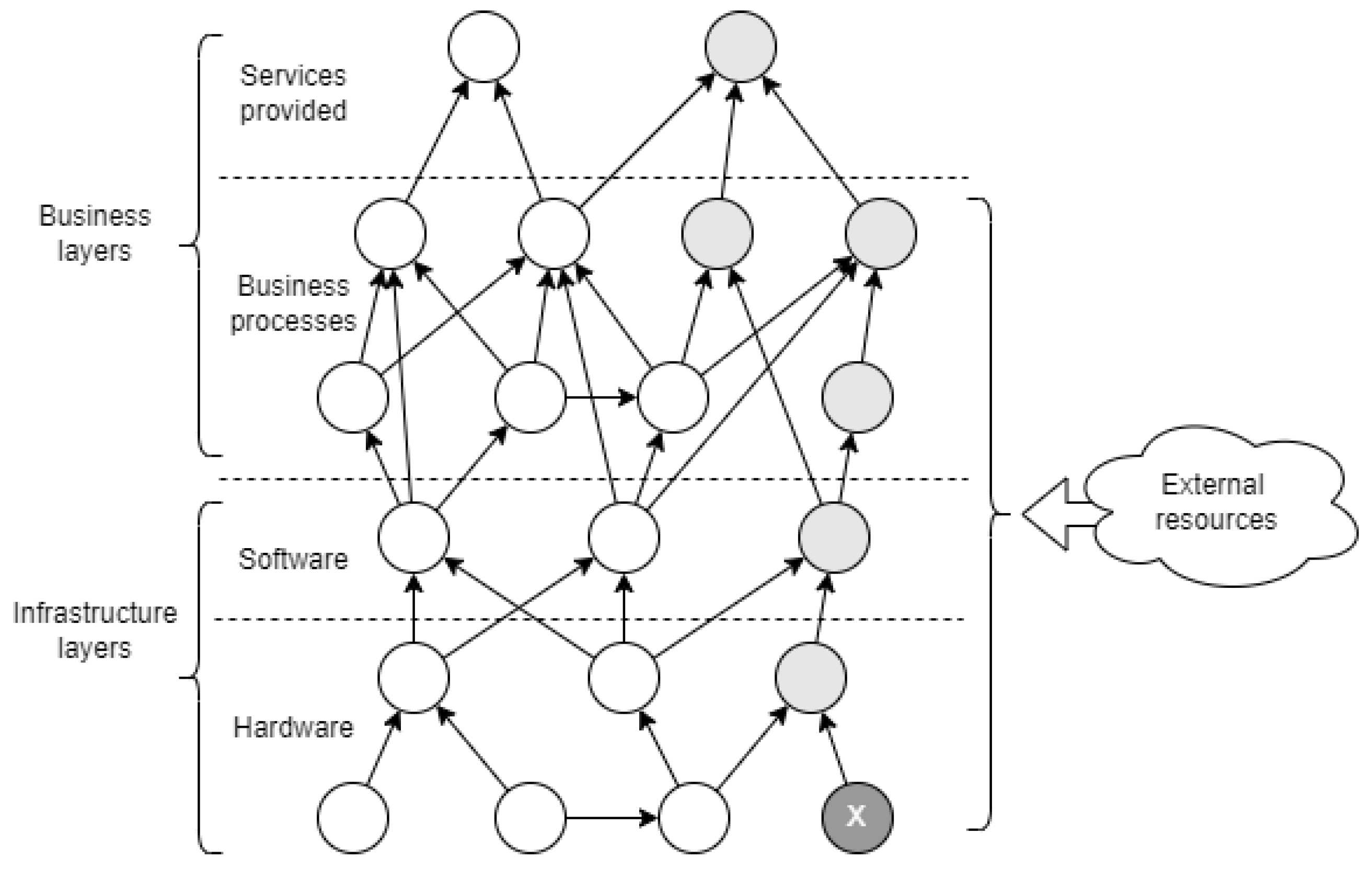
3.1. Model of Cyberspace
- Relative criticality, , characterizing the significance of the object ’s impact on a dependent one, ;
- Business criticality, , describing the importance of the object in accomplishing business objectives.
- Impact time, , determining the time after which the degradation of the security attribute of object will affect the values of the security attributes of the related object ;
- Impact scale, , defining the level of degradation of the security attribute of object as a result of the security degradation of impacting object .
- Exposure to degradation , representing the likelihood of object degradation associated with identified vulnerabilities and hazard events at time t;
- Security risk , representing the impact of the security degradation of the object occurring at time t on accomplishing business objectives.
3.2. Dynamic Risk Assessment
- Intrinsic risk resulting from identified weaknesses associated with the object;
- External risk (contributed) resulting from the propagation of risk in cyberspace;
- Overall risk , which is a composite of intrinsic and external risks.
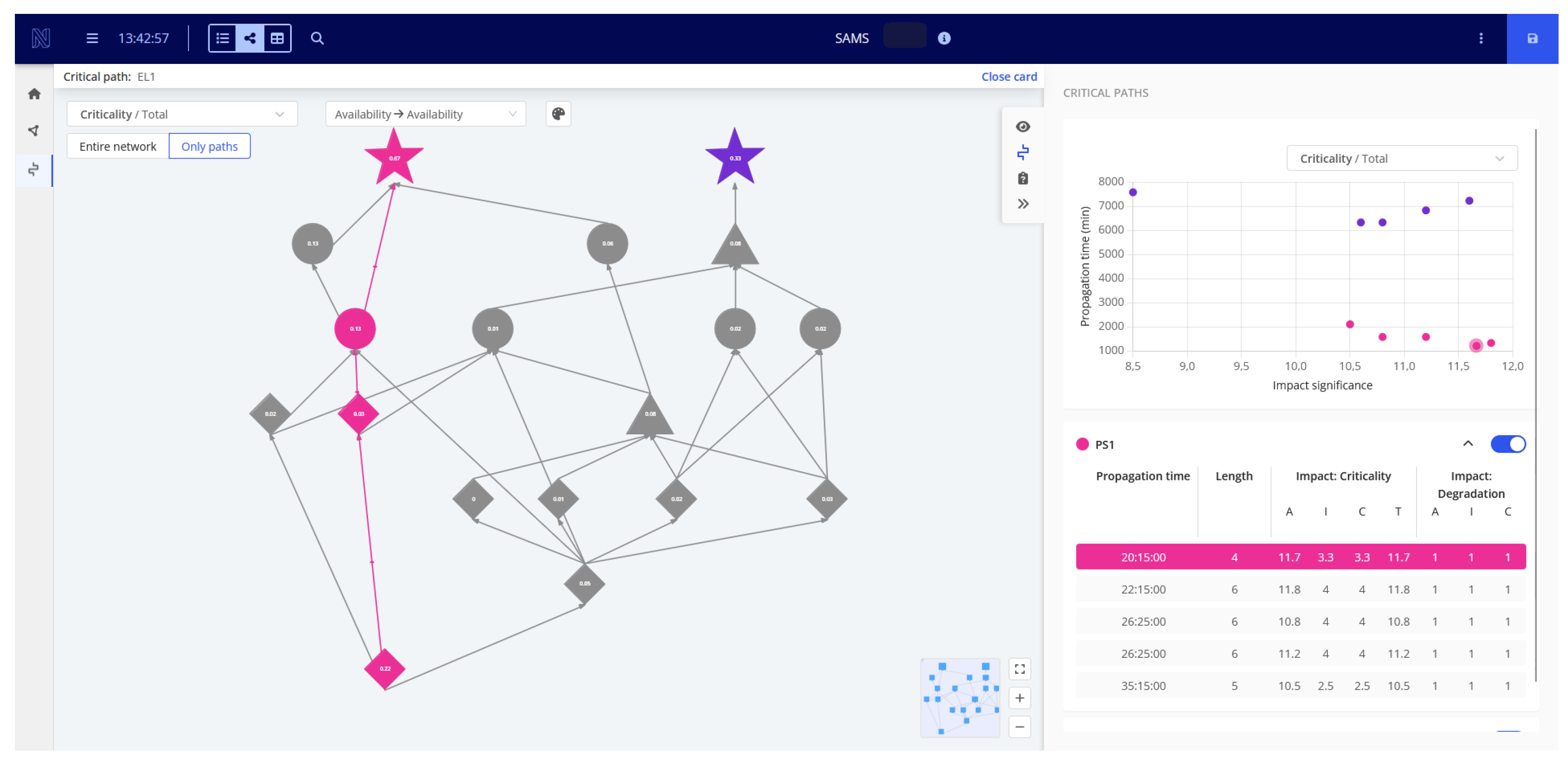
3.3. Threat Propagation Paths
- Threat propagation time ;
- Significance of the impact .
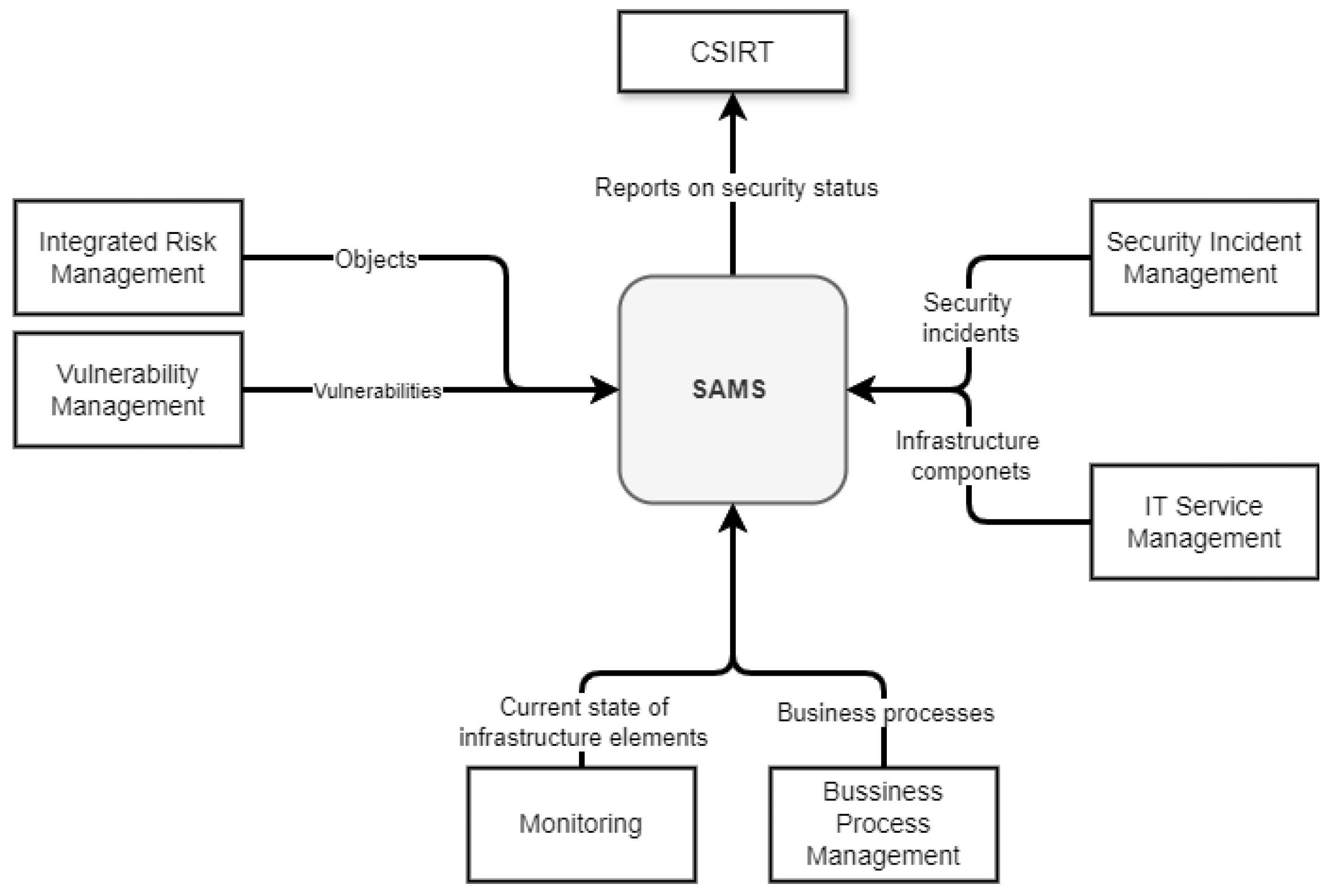
4. Situational Awareness System
4.1. Goals and Objectives
- Assessment of occurring or potential security hazard events, their magnitude, and their significance for business continuity;
- Ensuring an understanding of the impact of a security breach, including threat propagation and associated risks and the impact on achieving business objectives;
- Delivering the details on hazard event propagation, enabling the undertaking of preemptive action to reduce the consequences of identified or potential risks;
- Dynamic assessment of cybersecurity risk for all cyberspace objects following the occurred or identified potential hazard events;
- Predicting the impact on security and business continuity of planned changes in infrastructure and business layers.
- Supporting the process of building a company’s cyberspace representation, composed of the following elements:
- –
- Key services provided or overarching business processes;
- –
- Internal business processes and services;
- –
- Services or resources provided by external organizations;
- –
- Information and operational technology systems used and their components;
- –
- Supporting technical systems and their components.
- Ongoing updating of the knowledge of cyberspace and its status;
- Visualization of the following:
- –
- The current and predicted security status of all cyberspace elements;
- –
- The results of the dynamic assessment of risk and its propagation.
- Predicting the impact of security hazard events on the state of cyberspace and its elements;
- Supporting the carrying out of in-depth analysis, including the “what-if” type.
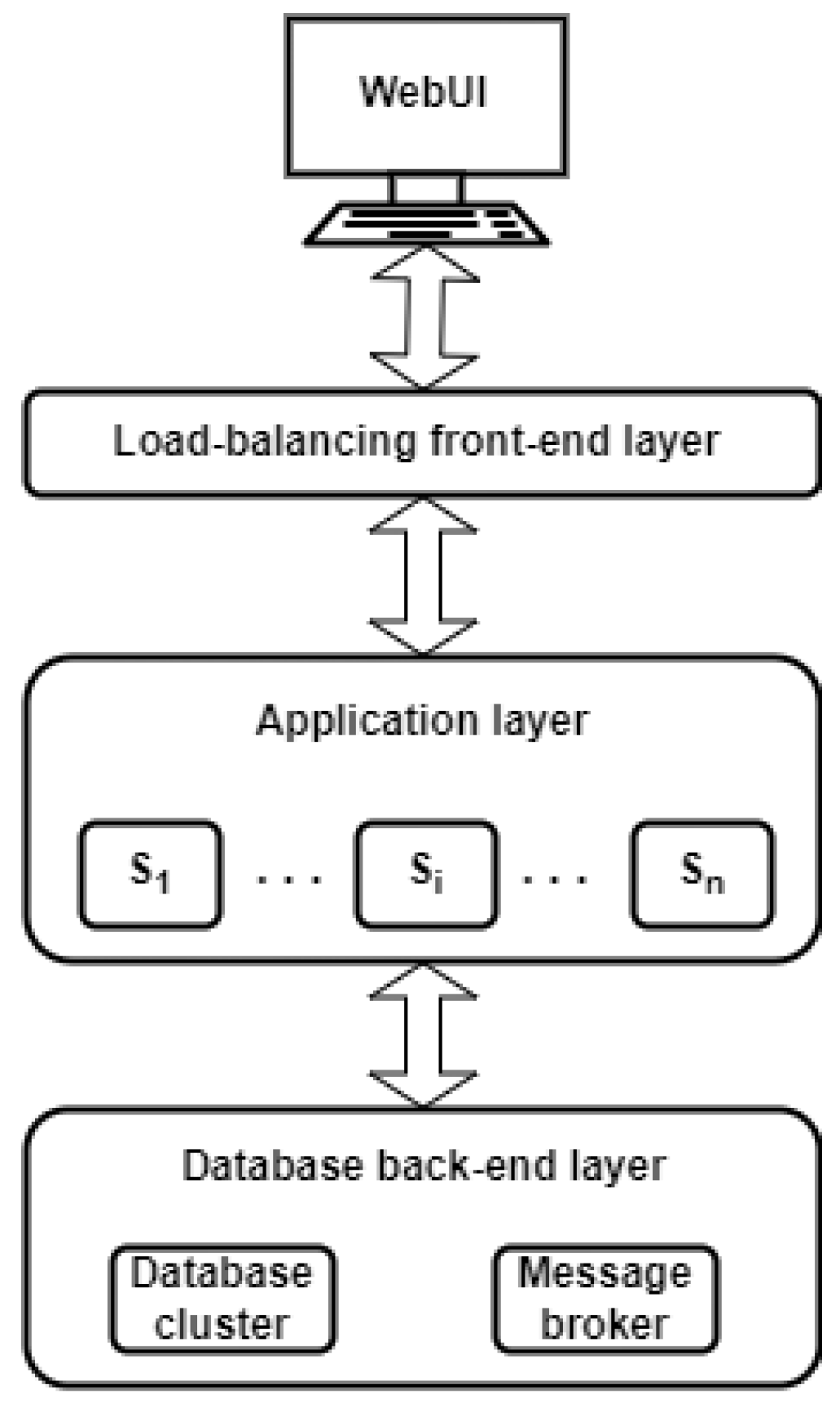
4.2. System Description
- A web user interface (WebUI) enabling user interaction with the system;
- A front-end load-balancing layer, designed to provide the users with an interface for highly available applications;
- An application layer containing specific, interconnected microservices performing the system business logic that communicates with database back-ends and serves data to the front-end application for user interactions, including the following:
- –
- Cyberspace model generation and management;
- –
- Hazard events processing;
- –
- Dynamic risk assessment;
- –
- Critical path selection and analysis;
- –
- Vulnerability data integration and processing;
- –
- Identity management;
- –
- Execution of computationally demanding tasks to conduct simulations and predictions of the state of cyberspace;
- –
- Gathering data on security events and visualization of global statistics on cyberspace security;
- –
- Acquisition and processing of data from external management systems.
- The database back-end layer contains a database cluster that stores operational data and a message broker to synchronize notifications between WebSockets.
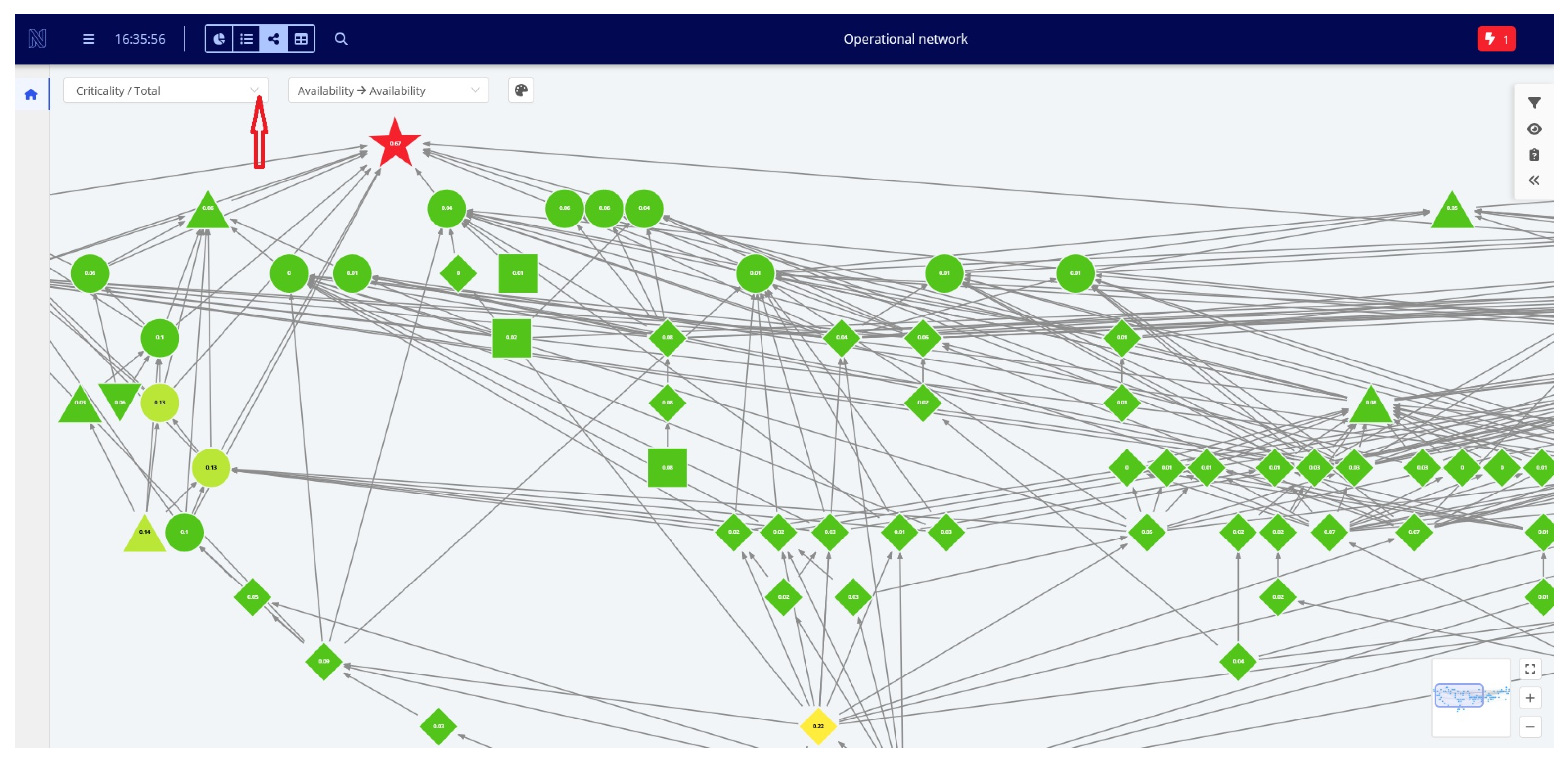
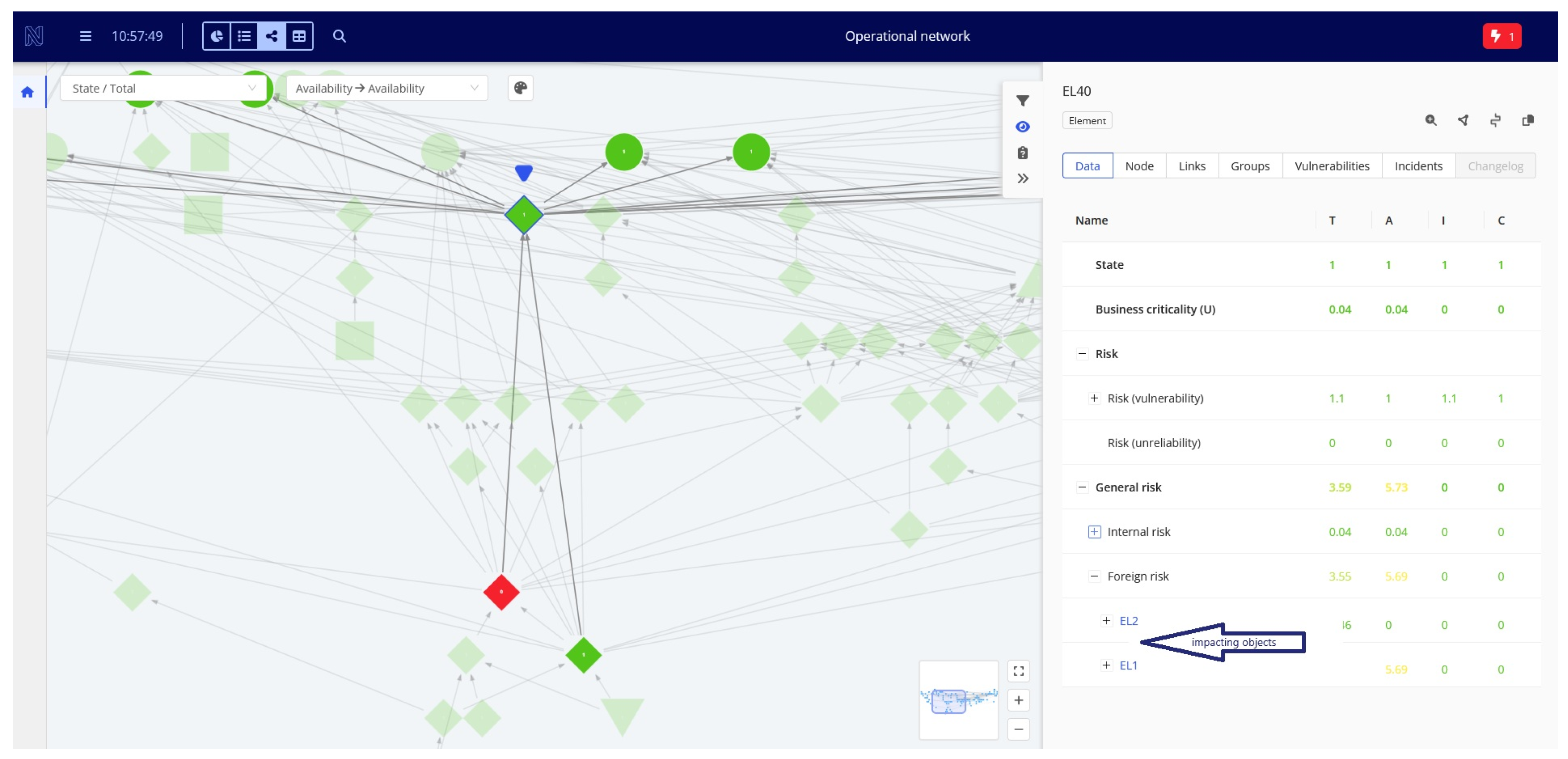
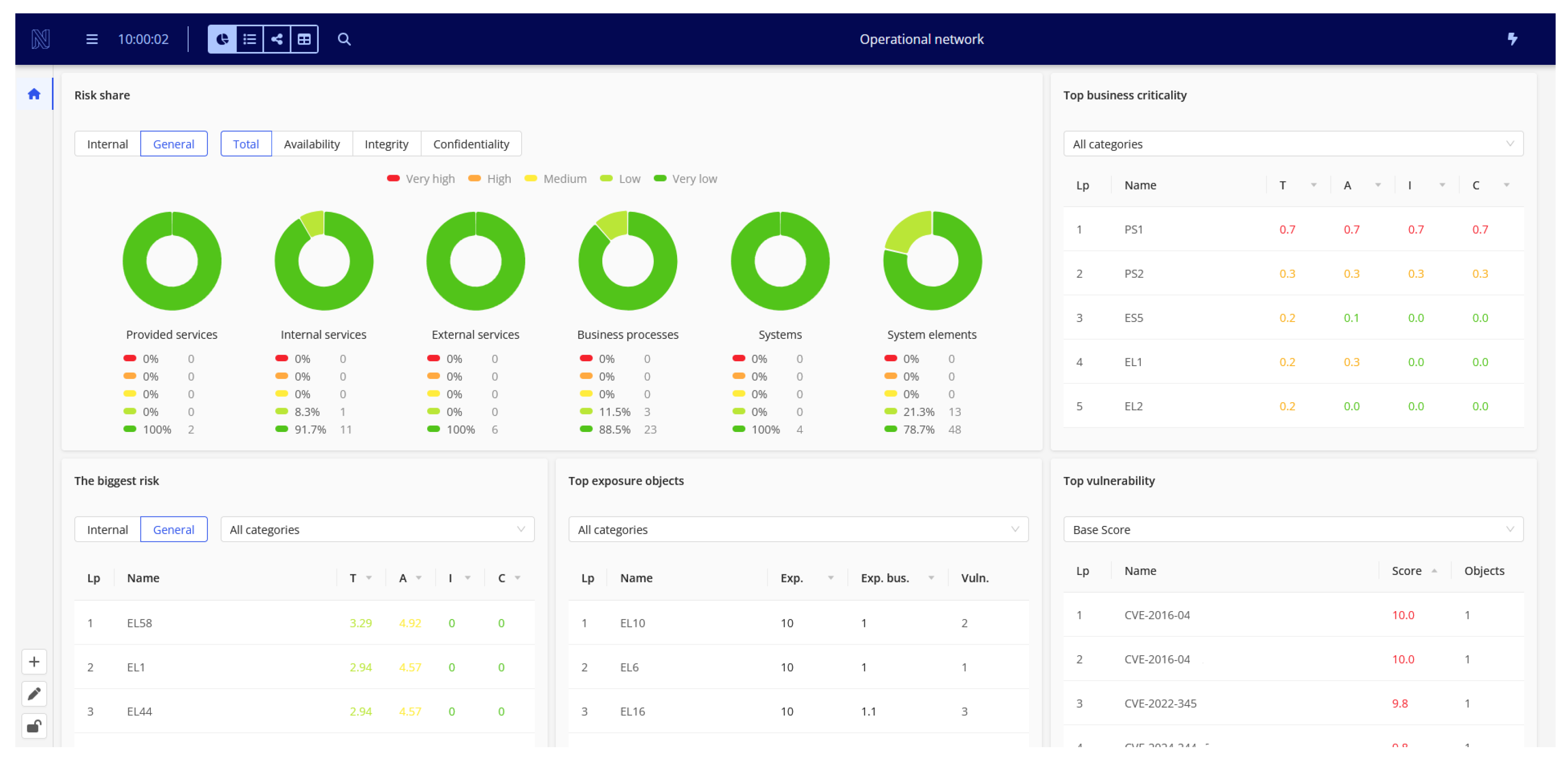
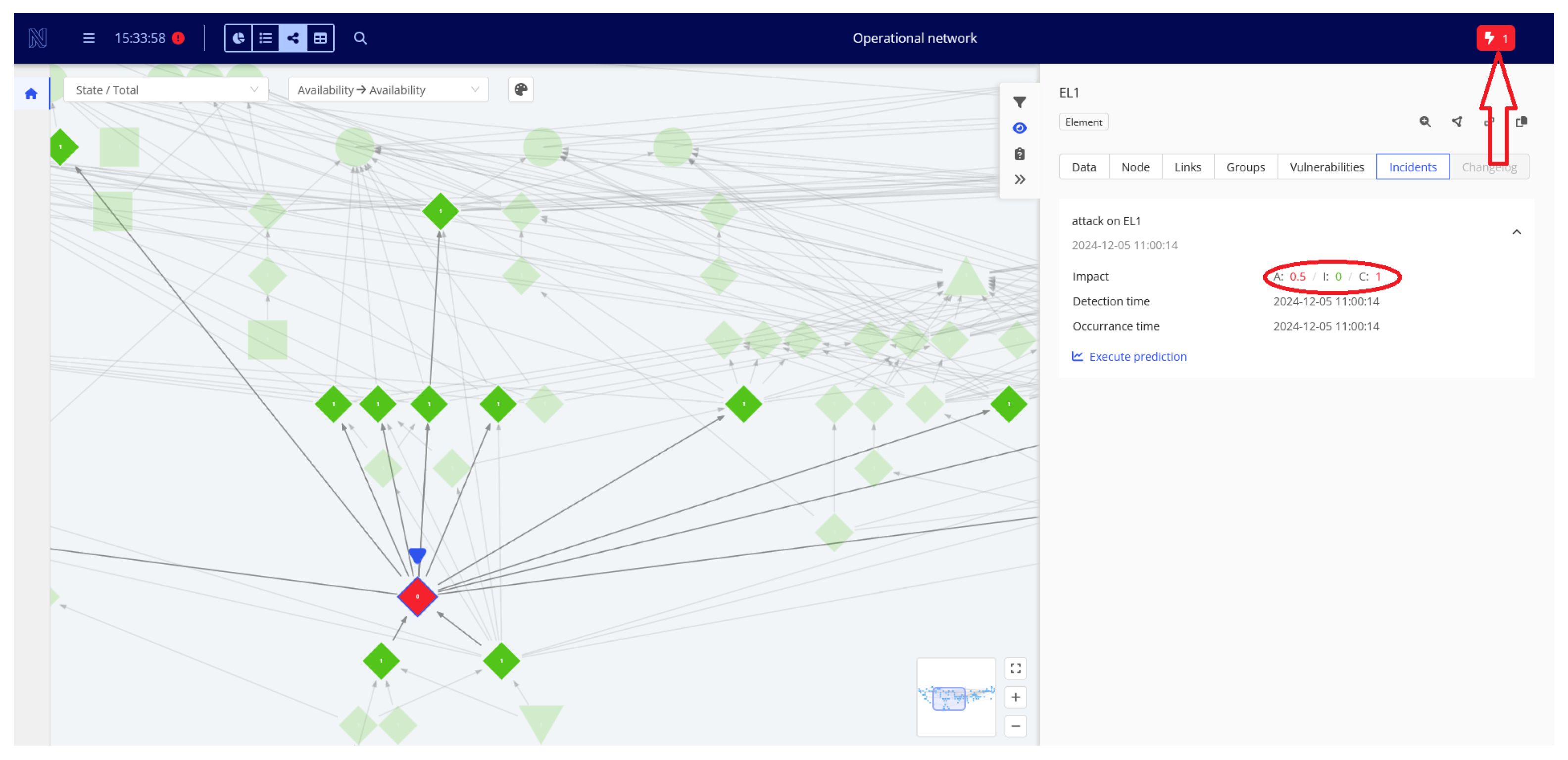
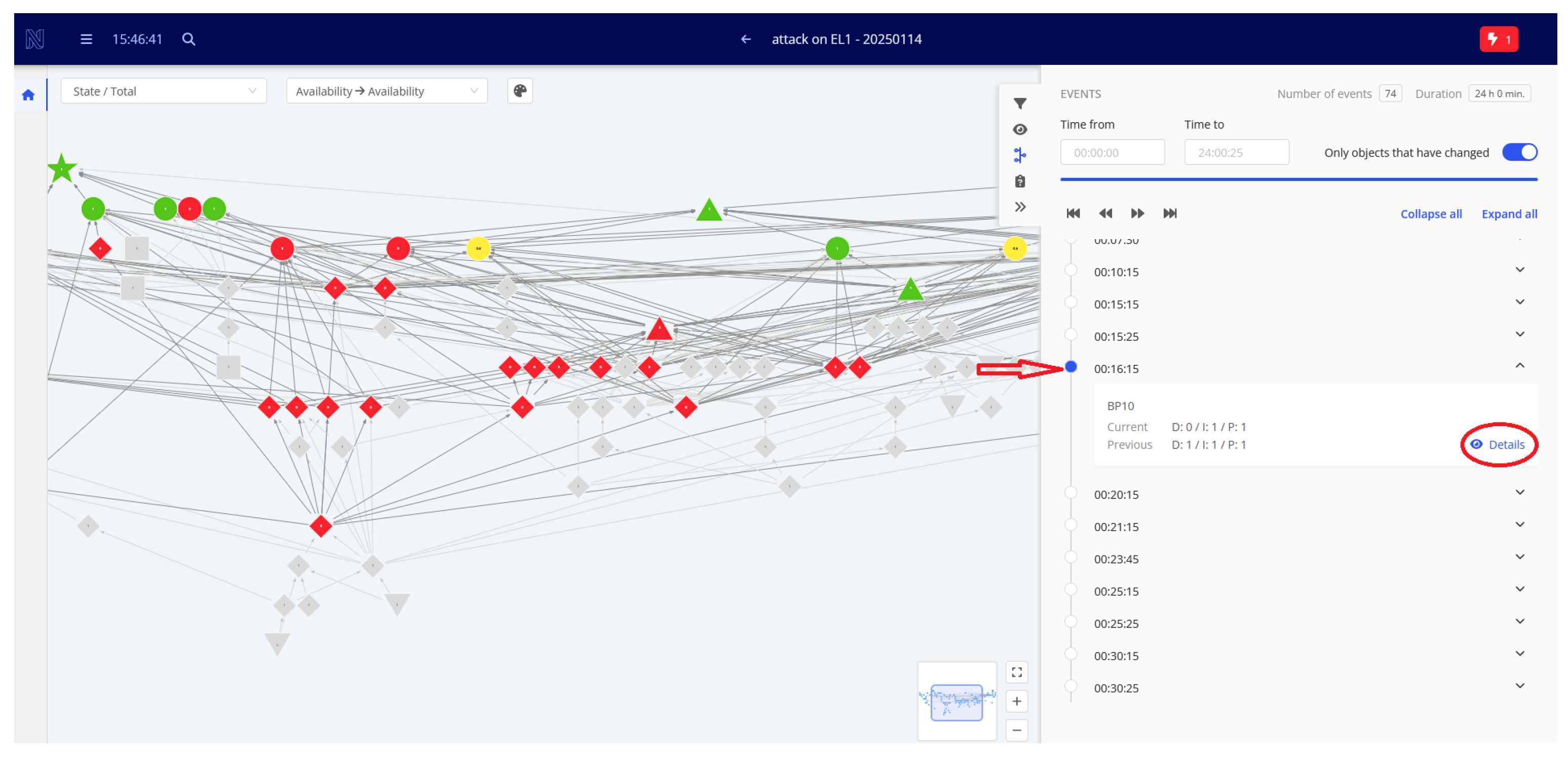
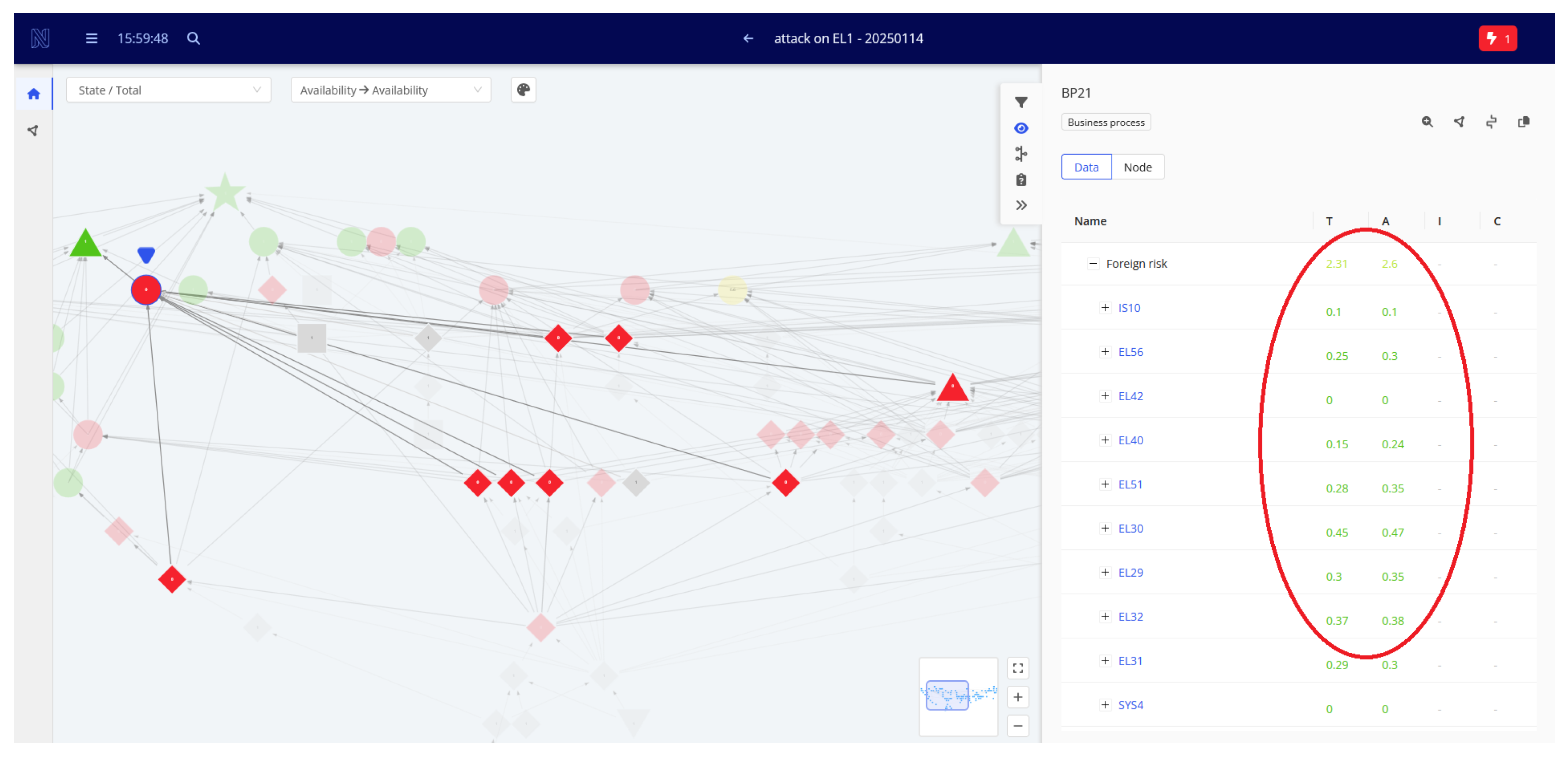
5. Example of SAMS Usage
- Identify the part of the organization that may be affected by the event and the time and scale of its impact;
- Alert relevant management staff of potential incident impacts on objects they are responsible for, enabling them to take preemptive actions to mitigate the threat and reduce its propagation.
6. Discussion
- Simplifying user interaction with the system;
- Customizing user interfaces;
- Automated report generation of daily reports;
- Integration of the SAMS with Business Intelligence platforms;
- Developing a simplified version of the system that could be offered to a broader community for examination;
- Examination of the impact of the configuration attributes of the dynamic risk assessment method on the evaluation results and determining their reference values;
- Objects attribute specification, supported by machine learning techniques;
- Inclusion of complex models of redundant groups, allowing their dynamic reconfiguration.
7. Conclusions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Zimmerman, R. Decision-making and the vulnerability of interdependent critical infrastructure. In Proceedings of the 2004 IEEE International Conference on Systems, Man and Cybernetics (IEEE Cat. No. 04CH37583), The Hague, The Netherlands, 10–13 October 2004; IEEE: Piscataway, NJ, USA, 2004; Volume 5, pp. 4059–4063. [Google Scholar]
- Banerjee, J.; Zhou, C.; Das, A.; Sen, A. On Robustness in Multilayer Interdependent Networks. In Proceedings of the Critical Information Infrastructures Security, Berlin, Germany, 5–7 October 2015; Lecture Notes in Computer Science. Springer: Cham, Switzerland, 2016; Volume 9578, pp. 247–250. [Google Scholar] [CrossRef]
- Granat, J.; Batalla, J.M.; Mavromoustakis, C.X.; Mastorakis, G. Big Data Analytics for Event Detection in the IoT-Multicriteria Approach. IEEE Internet Things J. 2020, 7, 4418–4430. [Google Scholar] [CrossRef]
- Amanowicz, M.; Kamola, M. Building Security Awareness of Interdependent Services, Business Processes, and Systems in Cyberspace. Electronics 2022, 11, 3835. [Google Scholar] [CrossRef]
- Amanowicz, M. Cybersecurity Awareness Provision: Case Study. In Proceedings of the ESREL2024: Advances in Reliability, Safety and Security, Cracow, Poland, 23–27 June 2024; Kołowrocki, K., Ed.; Polish Safety and Reliability Association: Cracow, Poland, 2024; Volume 4, pp. 9–18. [Google Scholar]
- Wang, F.; Magoua, J.J.; Li, N. Modeling cascading failure of interdependent critical infrastructure systems using HLA-based co-simulation. Autom. Constr. 2022, 133, 104008. [Google Scholar] [CrossRef]
- Szpyrka, M.; Jasiul, B. Evaluation of Cyber Security and Modelling of Risk Propagation with Petri Nets. Symmetry 2017, 9, 32. [Google Scholar] [CrossRef]
- Stergiopoulos, G.; Kotzanikolaou, P.; Theocharidou, M.; Lykou, G.; Gritzalis, D. Time-based critical infrastructure dependency analysis for large-scale and cross-sectoral failures. Int. J. Crit. Infrastruct. Prot. 2016, 12, 46–60. [Google Scholar] [CrossRef]
- Puuska, S.; Rummukainen, L.; Timonen, J.; Lääperi, L.; Klemetti, M.; Oksama, L.; Vankka, J. Nationwide critical infrastructure monitoring using a common operating picture framework. Int. J. Crit. Infrastruct. Prot. 2018, 20, 28–47. [Google Scholar] [CrossRef]
- Giacobe, N.A. Application of the JDL data fusion process model for cyber security. In Proceedings of the Multisensor, Multisource Information Fusion: Architectures, Algorithms, and Applications, Orlando, FL, USA, 5–9 April 2010; Braun, J.J., Ed.; SPIE: Bellingham, WA USA, 2010; Volume 7710, p. 77100R. [Google Scholar] [CrossRef]
- Endsley, M.R.; Selcon, S.J.; Hardiman, T.D.; Croft, D.G. A Comparative Analysis of Sagat and Sart for Evaluations of Situation Awareness. Proc. Hum. Factors Ergon. Soc. Annu. Meet. 1998, 42, 82–86. [Google Scholar] [CrossRef]
- Lewis, J.R. The System Usability Scale: Past, Present, and Future. Int. J. Human–Computer Interact. 2018, 34, 577–590. [Google Scholar] [CrossRef]
- Amanowicz, M. A Shared Cybersecurity Awareness Platform. J. Telecommun. Inf. Technol. 2021, 3, 32–41. [Google Scholar] [CrossRef]
- Luidold, C.; Schaberreiter, T.; Wieser, C.; Koumpis, A.; Cappiello, C.; Citro, T.; Andriessen, J.; Röning, J. Increasing Cybersecurity Awareness and Collaboration in Organisations and Local/Regional Networks: The CS-AWARE-NEXT Project. In Proceedings of the S3C’23: Sustainable, Secure, and Smart Collaboration Workshop, CEUR, Turin, Italy, 20 September 2023. [Google Scholar]
- ISO/IEC 33020:2019; Information Technology—Process Assessment—Process Measurement Framework for Assessment of Process Capability. ISO/IEC: Geneva, Switzerland, 2019.
- Kim, A.; Kang, M.H.; Luo, J.Z.; Velasquez, A. A Framework for Event Prioritization in Cyber Network Defense; Technical Report; US Deperment of the Navy: Monterey, CA, USA, 2014. [CrossRef]
- Yen, J.Y. Finding the k Shortest Loopless Paths in a Network. Manag. Sci. 1971, 17, 712–716. [Google Scholar] [CrossRef]
- Dreyfus, S. An appraisal of some shortest path algorithm. Oper. Res. 1969, 17, 395–412. [Google Scholar] [CrossRef]
- Aggarwal, A.; Schieber, B.; Tokuyama, T. Finding a minimum weight K-link path in graphs with Monge property and applications. In Proceedings of the 9th Symposium Computational Geometry, San Diego, CA, USA, 18–21 May 1993; Association for Computing Machinery: New York, NY, USA, 1993; pp. 189–197. [Google Scholar]
- Eppstein, D. Finding the k Shortest Paths. SIAM J. Comput. 1998, 28, 652–673. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Amanowicz, M. A Methodology for Online Situational Awareness Provision in a Business Entity. Electronics 2025, 14, 470. https://doi.org/10.3390/electronics14030470
Amanowicz M. A Methodology for Online Situational Awareness Provision in a Business Entity. Electronics. 2025; 14(3):470. https://doi.org/10.3390/electronics14030470
Chicago/Turabian StyleAmanowicz, Marek. 2025. "A Methodology for Online Situational Awareness Provision in a Business Entity" Electronics 14, no. 3: 470. https://doi.org/10.3390/electronics14030470
APA StyleAmanowicz, M. (2025). A Methodology for Online Situational Awareness Provision in a Business Entity. Electronics, 14(3), 470. https://doi.org/10.3390/electronics14030470





