Workload-Dependent Vulnerability of SDRAM Multi-Bit Upsets in a LEON3 Soft-Core Processor
Abstract
1. Introduction
2. Related Work
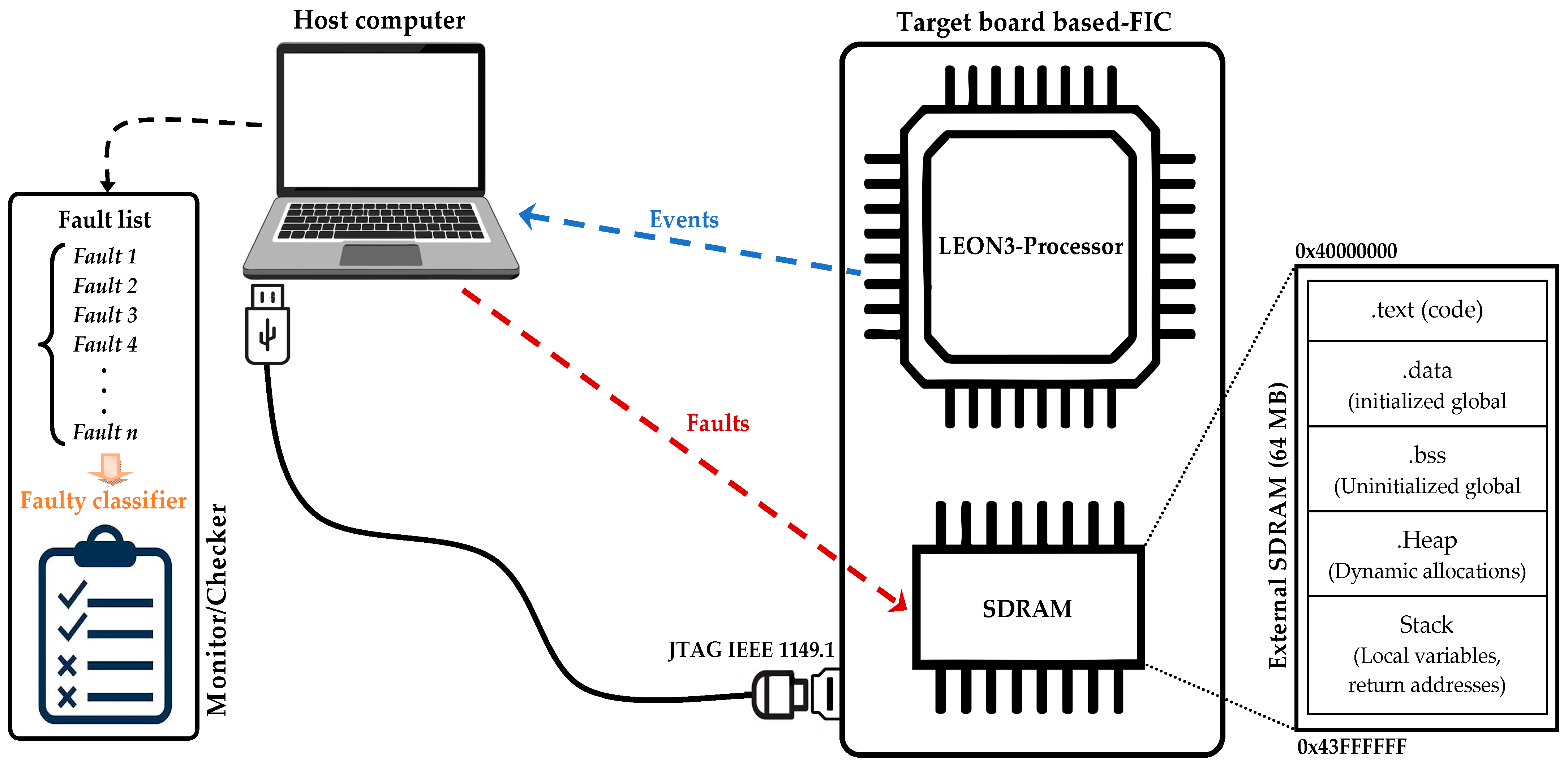
3. Methodology
3.1. Experimental Setup
- −
- masked faults,
- −
- silent data corruptions,
- −
- crashes, and
- −
- stopped-mode events.
3.2. Fault Model and Injection Mechanism
- 1.
- Memory mapping phase: The benchmark is executed in a dry-run mode to dynamically identify the base address and size of its data segment in SDRAM. This yields a runtime memory map that defines the injection target region.
- 2.
- Injection phase: Using the precomputed map, the FIC iteratively selects each word in the allocated region and flips two bits at configurable offsets (e.g., adjacent or spaced positions). After each injection, the benchmark resumes execution, and the Monitor/Checker records the system response.
3.3. Benchmark Suite
- Fast Fourier Transform (FFT): A memory-intensive signal processing kernel with strided and butterfly access patterns. Its numerical output enables precise detection of silent data error through comparison against a golden reference within a tolerance threshold.
- Matrix Multiplication (MulMatrix): A compute- and memory-bound linear algebra workload operating on two 30 × 30 dense matrices of 32-bit signed integers. It stresses accumulation logic and loop control, making it sensitive to both silent data corruption and catastrophic failures (e.g., illegal memory accesses or arithmetic exceptions).
- AES-128 encryption: A security-critical algorithm with deterministic control flow and structured memory accesses (e.g., substitution-box (S-box) lookups). Due to its strict correctness requirements, even minor corruptions in key or state data produce detectable output deviations, making it ideal for evaluating fault masking versus error exposure in cryptographic contexts. In the AES implementation, the 128-bit state buffer and 256-byte S-box lookup table are allocated in the heap. The state is updated in-place during each round, while S-box accesses follow a fixed, word-aligned pattern. This localized and repetitive memory behavior contributes to the algorithm’s high fault masking, as corrupted values are often overwritten before affecting the final ciphertext.
3.4. Experimental Protocol
- The LEON3 system is initialized by loading the synthesized bitstream onto the FPGA.
- To start the fault injection campaign, the benchmark is cross-compiled for the SPARC V8 architecture and loaded onto the LEON3 processor.
- The GRMON debug monitor executes script 1 to run the benchmark in profiling mode and generate a dynamic memory map of the data segment.
- Script 2 drives the injection loop over multiple independent execution runs, referred to as series. Each series to a distinct heap allocation layout in SDRAM, resulting from the dynamic nature of memory allocation in C (e.g., via malloc). For every word in the mapped region of a given series, the FIC applies a dual-bit MBU to SDRAM, and the benchmark resumes execution.
- The Monitor/Checker classifies each outcome into one of four mutually exclusive categories:
- Masked faults: No observable effect on execution or output (e.g., data never read or overwritten before use).
- Silent data corruption: Incorrect output with normal program termination and no exception raised.
- Crash: Abnormal termination due to a hardware exception (e.g., illegal instruction, memory alignment fault, or AHB error).
- Stopped mode: Implicit termination without output (e.g., due to watchdog timeout or unrecoverable stall), without a standard exception.
- Upon a stopped mode, the host computer reloads the FPGA bitstream, and resumes injection from the last untested address within the current series. This ensures continuity and full coverage without re-executing the benchmark. The memory layout (established during script 1) is preserved, so the execution context remains consistent across injections. Upon crash mode, the system reloads an updated script 2 and resumes injection from the next address, preserving the memory layout and ensuring full coverage.
- Results, including fault location, outcome class, and execution context, are logged in raw form to structured text files for statistical analysis.
4. Experimental Results
4.1. Classification and Analysis of MBU Effects During FFT Execution
4.2. Classification and Analysis of MBU Effects During Matrix Multiplication Execution
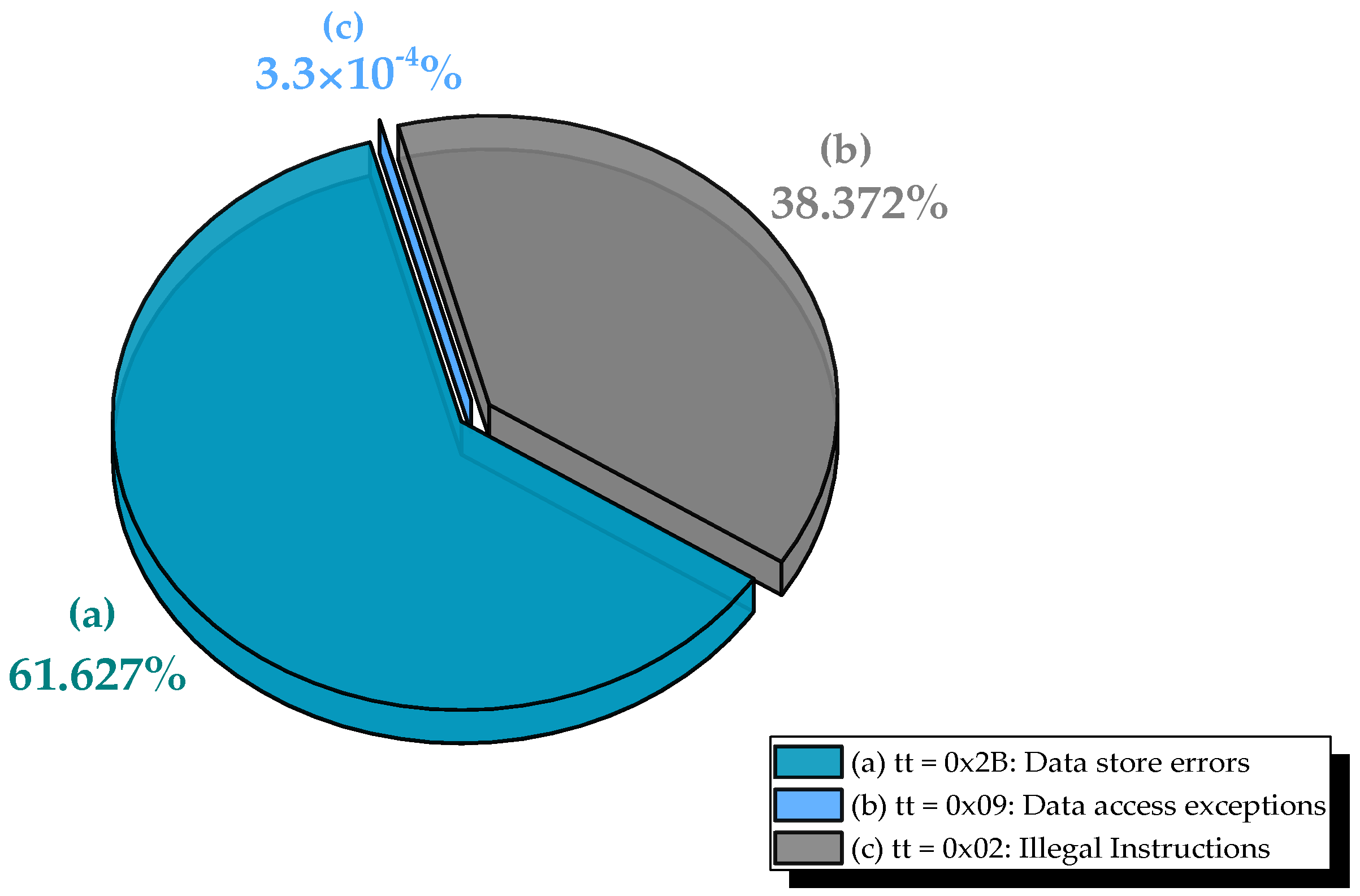
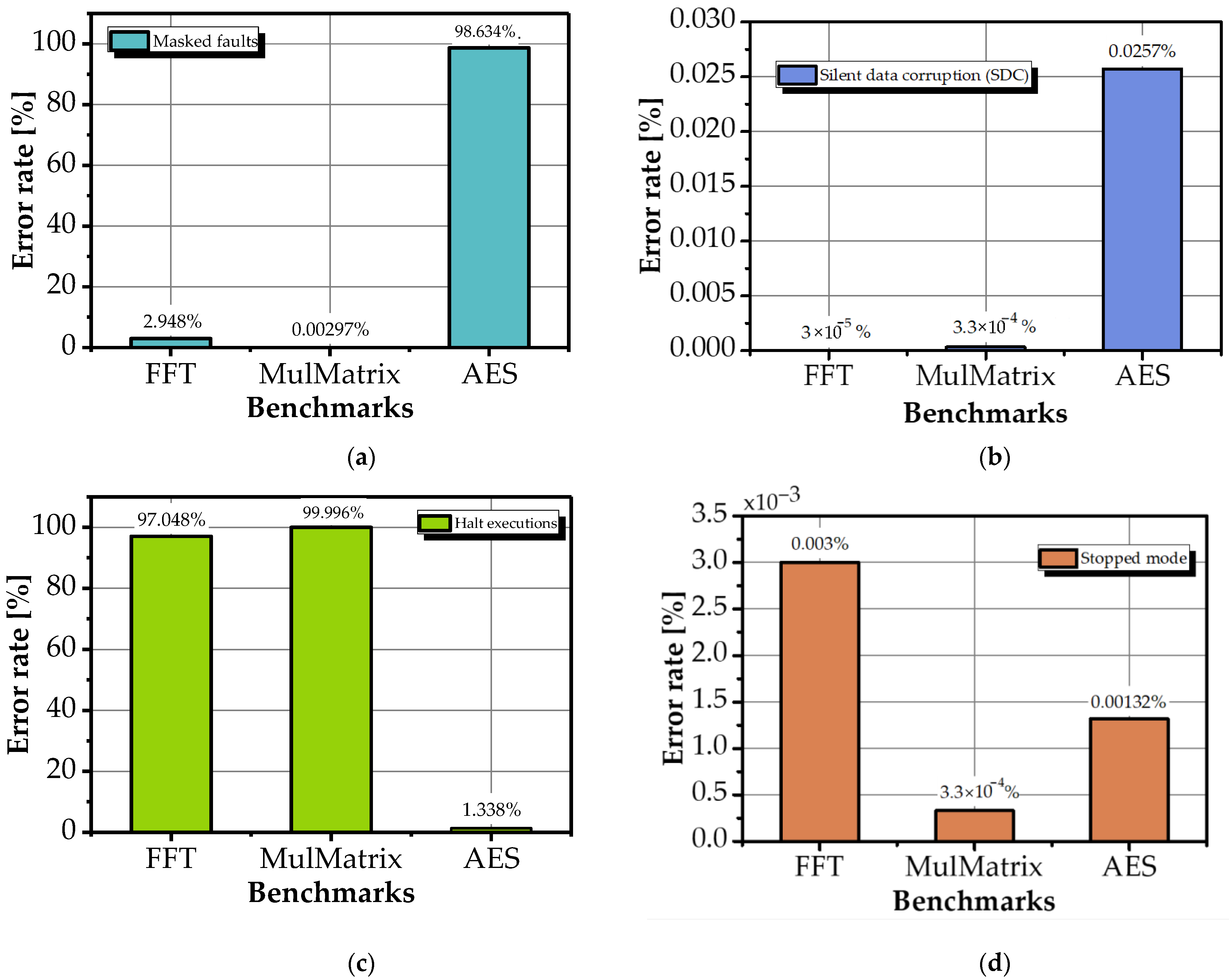
- In Series 1, illegal instruction faults (tt = 0x02) dominated, accounting for 116,264 events (38.37% of total injections). These occur when MBUs corrupt instructions in memory, causing the processor to fetch undefined or unimplemented opcodes. The high incidence confirms that the injection region included executable code or data aliased with the instruction stream.
- In Series 2, no illegal instruction faults were observed, as injections were confined to data-only regions. Instead, data store errors (tt = 0x2B) prevailed, with 186,495 occurrences (61.625% of total injections), reflecting corruption during write-back of computed matrix elements to SDRAM.
- Data access exceptions (tt = 0x09) occurred only once (in Series 1), consistent with MulMatrix’s regular, contiguous memory access pattern, which rarely generates invalid addresses.
- Memory alignment faults (tt = 0x07) were not observed, as the benchmark exclusively uses aligned data structures.
- Stopped mode occurred once in Series 1, triggering FPGA reinitialization and resumption of the campaign from the last untested address, a robust recovery mechanism that ensured full coverage.
4.3. Classification and Analysis of MBU Effects During AES Execution
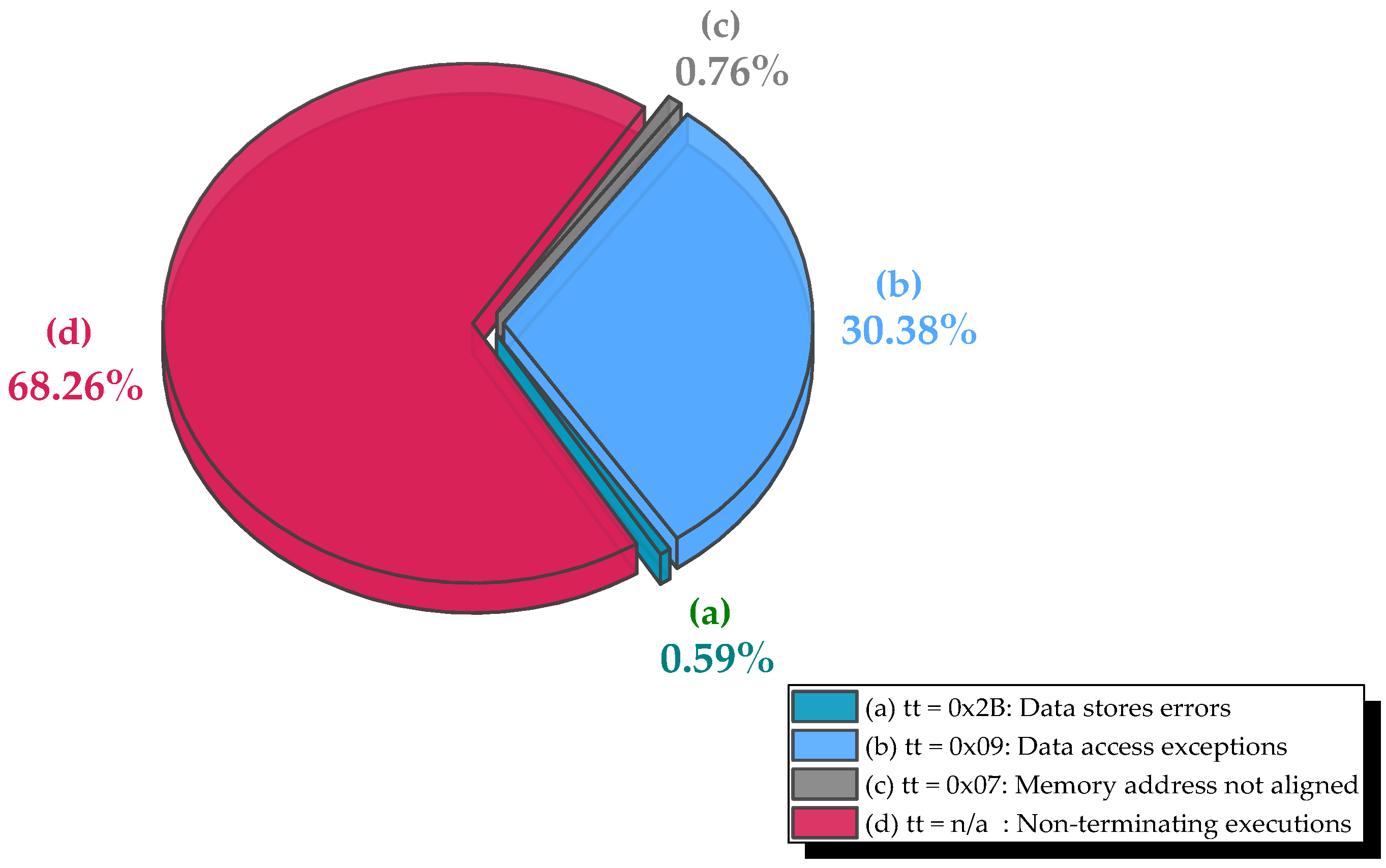
- Non-terminating executions (requiring watchdog timeout) occurred in 2770 cases (0.913% of total injections), representing 68.26% of all observed exceptions. These were concentrated in Series 1 and 2, suggesting heightened sensitivity to faults during early key-scheduling phases.
- Data access exceptions (tt = 0x09) totaled 1233 cases (0.406%), arising when MBUs corrupted pointers or indices used in S-box or state array accesses (30.38% of exceptions).
- Data store errors (tt = 0x2B) were minimal (24 cases, 0.007%), consistent with AES’s limited number of store operations relative to its compute-intensive rounds (0.76% of exceptions).
- Unaligned memory accesses (tt = 0x07) occurred in 31 cases (0.010%), likely due to bit flips in address LSBs during table lookups (0.59% of exceptions).
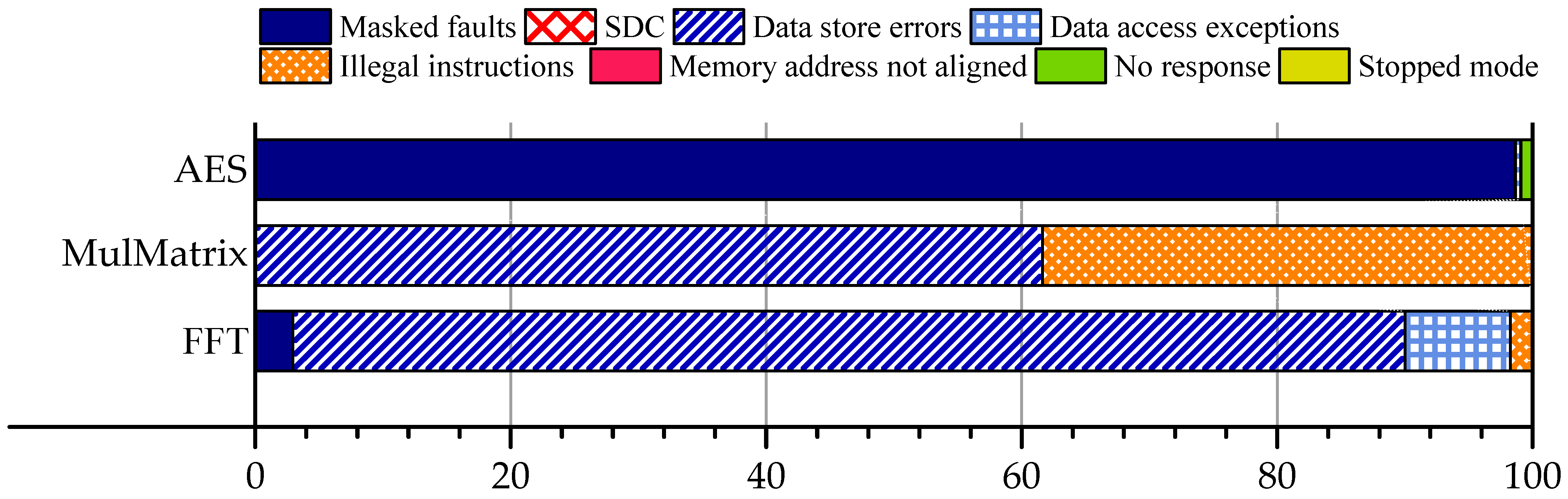
4.4. Comparative Fault Outcome Summary
5. Cross-Benchmark Comparison
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AES | Advanced Encryption Standard |
| AHB | Advanced High-Performance Bus |
| AMBA | Advanced Microcontroller Bus Architecture |
| ARM | Advanced RISC Machine |
| AVF | Architectural Vulnerability Factors |
| BRAM | Block Random-Access Memory |
| CAN | Controller Area Network |
| CMOS | Complementary Metal-Oxide-Semiconductor |
| CPU | Central Processing Unit |
| D-Cache | Data Cache |
| DEC | Double Error Correction |
| DFA | Differential Fault Analysis |
| DPSR | Double Parity Single Redundancy |
| DSU | Debug Support Unit |
| ECC | Error Correction Code |
| ESA | European Space Agency |
| FFT | Fast Fourier Transform |
| FI | Fault Injection |
| FIC | Fault Injection Controller |
| FinFET | Fin Field Effect Transistor |
| FIT | Failure-in-Time |
| FPGA | Field-Programmable Gate Array |
| FPU | Floating-Point Unit |
| GCC | GNU Compiler Collection |
| HW | Hardware |
| I-Cache | Instruction Cache |
| I/O | Input/Output |
| IEEE | Institute of Electrical and Electronics Engineers |
| JTAG | Joint Test Access Group |
| KB | Kilobyte |
| LET | Linear Energy Transfer |
| LSB | Least-Significant Bit |
| LSTM | Long Short-Term Memory |
| LUT | Look-Up-Table |
| MAC | Message Authentication Code |
| MB | Megabyte |
| MBU | Multiple-Bit Upset |
| MMU | Memory Management Unit |
| OS | Operating System |
| PCI | Peripheral Component Interconnect |
| PROBA | Project for On-Board Autonomy |
| PROM | Programmable Read-Only Memory |
| RFID | Radio Frequency Identification |
| RISC | Reduced Instruction Set Computing |
| SDC | Silent Data Corruption |
| SDRAM | Synchronous Dynamic Random-Access Memory |
| SEC | Single Error Correction |
| SET | Single-Event Transient |
| SEU | Single-Event Upset |
| SPARC | Scalable Processor Architecture |
| SRAM | Synchronous Random-Access Memory |
| STT-RAM | Spin-Transfer Torque Random-Access Memory |
| TCL | Tool Command Language |
| TID | Total Ionizing Dose |
| UART | Universal Asynchronous Receiver/Transmitter |
| UE | Uncorrectable Error |
| VHDL | VHSIC Hardware Description Language |
| VHSIC | Very High Speed Integrated Circuits |
References
- Papadimitriou, G.; Gizopoulos, D. Silent data corruptions: Microarchitectural perspectives. IEEE Trans. Comput. 2023, 72, 3072–3085. [Google Scholar] [CrossRef]
- Bittel, B.; Shamsa, M.; Inkley, B.; Gur, A.; Lerner, D.; Adams, M. Data center silent data errors: Implications to artificial intelligence workloads & mitigations. In Proceedings of the IEEE International Reliability Physics Symposium (IRPS), Grapevine, TX, USA, 14–18 April 2024; pp. 1–5. [Google Scholar]
- Wang, H.; Li, H.; Rahman, F.; Tehranipoor, M.M.; Farahmandi, F. Sofi: Security property-driven vulnerability assessments of ics against fault-injection attacks. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2021, 41, 452–465. [Google Scholar] [CrossRef]
- Safari, S.; Ansari, M.; Khdr, H.; Gohari-Nazari, P.; Yari-Karin, S.; Yeganeh-Khaksar, A.; Hessabi, S.; Ejlali, A.; Henkel, J. A survey of fault-tolerance techniques for embedded systems from the perspective of power, energy, and thermal issues. IEEE Access 2022, 10, 12229–12251. [Google Scholar] [CrossRef]
- Azimi, S.; De Sio, C.; Portaluri, A.; Rizzieri, D.; Vacca, E.; Sterpone, L.; Merodio Codinachs, D. Exploring the impact of soft errors on the reliability of real-time embedded operating systems. Electronics 2022, 12, 169. [Google Scholar] [CrossRef]
- Gangolli, A.; Mahmoud, Q.H.; Azim, A. A systematic review of fault injection attacks on iot systems. Electronics 2023, 11, 2023. [Google Scholar] [CrossRef]
- Ren, Y.; Zhu, M.; Xu, D.; Liu, M.; Dai, X.; Wang, S.; Li, L. Overview on radiation damage effects and protection techniques in microelectronic devices. Sci. Technol. Nucl. Install. 2024, 1, 3616902. [Google Scholar] [CrossRef]
- Oldham, T.R.; McLean, F.B. Total ionizing dose effects in MOS oxides and devices. IEEE Trans. Nucl. Sci. 2003, 50, 483–499. [Google Scholar] [CrossRef]
- Titze, M.; Belianinov, A.; Tonigan, A.; Su, S.S.; Vizkelethy, G.; Wampler, W.; Hehr, B.; Wang, M.; Zhou, H.; Narayanan, V.; et al. Displacement damage, total ionizing dose, and transient ionization effects in gate-all-around field effect transistors. ACS Appl. Electron. Mater. 2024, 6, 5759–5765. [Google Scholar] [CrossRef]
- Pereira, E.; Garibotti, R.; Ost, L.C.; Calazans, N.; Moraes, F.G. A Complementary Survey of Radiation-Induced Soft Error Research: Facilities, Particles, Devices and Trends. J. Integr. Circuits Syst. 2024, 19, 1–18. [Google Scholar] [CrossRef]
- Ibe, E.; Taniguchi, H.; Yahagi, Y.; Shimbo, K.I.; Toba, T. Impact of scaling on neutron-induced soft error in SRAMs from a 250 nm to a 22 nm design rule. IEEE Trans. Electron. Devices 2010, 57, 1527–1538. [Google Scholar] [CrossRef]
- Chabot, A.; Alouani, I.; Niar, S.; Nouacer, R. A new memory reliability technique for multiple bit upsets mitigation. In Proceedings of the 16th ACM International Conference on Computing Frontiers, Alghero, Italy, 30 April–2 May 2019; pp. 145–152. [Google Scholar]
- Jun, H.Y.; Lee, Y.S. Single error correction, double error detection and double adjacent error correction with no mis-correction code. IEICE Electron. Express 2013, 10, 20130743. [Google Scholar] [CrossRef]
- Neale, A.; Sachdev, M. A new SEC-DED error correction code subclass for adjacent MBU tolerance in embedded memory. IEEE Trans. Device Mater. Reliab. 2012, 13, 223–230. [Google Scholar] [CrossRef]
- Neale, A.; Jonkman, M.; Sachdev, M. Adjacent-MBU-tolerant SEC-DED-TAEC-yAED codes for embedded SRAMs. IEEE Trans. Circuits Syst. II Express Briefs 2014, 62, 387–391. [Google Scholar] [CrossRef]
- Deepanjali, S.; Sk, N.M. Fault tolerant micro-programmed control unit for SEU and MBU mitigation in space based digital systems. Microelectron. Reliab. 2024, 155, 115360. [Google Scholar] [CrossRef]
- Thunig, R.; Borchert, C.; Kober, U.; Schirmeier, H. Hybrid Hardware/Software Detection of Multi-Bit Upsets in Memory. In Proceedings of the 54th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshops (DSN-W), Brisbane, Australia, 24–27 June 2024; pp. 94–97. [Google Scholar]
- Maniatakos, M.; Michael, M.K.; Makris, Y. Vulnerability-based interleaving for multi-bit upset (MBU) protection in modern microprocessors. In Proceedings of the IEEE International Test Conference (ITC), Anaheim, CA, USA, 5–8 November 2012; pp. 1–8. [Google Scholar]
- Maniatakos, M.; Michael, M.K.; Makris, Y. Multiple-bit upset protection in microprocessor memory arrays using vulnerability-based parity optimization and interleaving. IEEE Trans. Very Large Scale Integr. Syst. 2015, 23, 2447–2460. [Google Scholar] [CrossRef]
- Gil-Tomas, D.; Saiz-Adalid, L.J.; Gracia-Moran, J.; Baraza-Calvo, J.C.; Gil-Vicente, P.J. A Hybrid Technique Based on ECC and Hardened Cells for Tolerating Random Multiple-Bit Upsets in SRAM Arrays. IEEE Access 2024, 12, 70662–70675. [Google Scholar] [CrossRef]
- Ziade, H.; Ayoubi, R.A.; Velazco, R. A survey on fault injection techniques. Int. Arab. J. Inf. Technol. 2004, 1, 171–186. [Google Scholar]
- Gunneflo, U.; Karlsson, J.; Torin, J. Evaluation of error detection schemes using fault injection by heavy-ion radiation. In Proceedings of the Nineteenth International Symposium on Fault-Tolerant Computing, Chicago, IL, USA, 21–23 June 1989; pp. 340–341. [Google Scholar]
- Ito, K.; Zhang, Y.; Itsuji, H.; Uezono, T.; Toba, T.; Hashimoto, M. Analyzing due errors on gpus with neutron irradiation test and fault injection to control flow. IEEE Trans. Nucl. Sci. 2021, 68, 1668–1674. [Google Scholar] [CrossRef]
- Ebrahimi, M.; Evans, A.; Tahoori, M.B.; Costenaro, E.; Alexandrescu, D.; Chandra, V.; Seyyedi, R. Comprehensive analysis of sequential and combinational soft errors in an embedded processor. IEEE Trans. Comput.-Aided Des. Integr. 2015, 34, 1586–1599. [Google Scholar] [CrossRef]
- Natella, R.; Cotroneo, D.; Madeira, H.S. Assessing dependability with software fault injection: A survey. ACM Comput. Surv. 2016, 48, 1–55. [Google Scholar] [CrossRef]
- Ruano, Ó.; García-Herrero, F.; Aranda, L.A.; Sánchez-Macián, A.; Rodriguez, L.; Maestro, J.A. Fault injection emulation for systems in fpgas: Tools, techniques and methodology, a tutorial. Sensors 2021, 21, 1392. [Google Scholar] [CrossRef]
- Abbasitabar, H.; Zarandi, H.R.; Salamat, R. Susceptibility analysis of LEON3 embedded processor against multiple event transients and upsets. In Proceedings of the 15th IEEE International Conference on Computational Science and Engineering (CSE), Paphos, Cyprus, 5–7 December 2011; pp. 548–553. [Google Scholar]
- Bonnoit, T.; Coelho, A.; Zergainoh, N.E.; Velazco, R. SEU impact in processor’s control-unit: Preliminary results obtained for LEON3 soft-core. In Proceedings of the 18th IEEE Latin American Test Symposium (LATS), Bogota, Columbia, 13–15 March 2017; pp. 1–4. [Google Scholar]
- Kchaou, A.; Saad, S.; Garrab, H.; Machhout, M. Reliability of LEON3 Processor’s Program Counter Against SEU, MBU, and SET Fault Injection. Cryptography 2025, 9, 54. [Google Scholar] [CrossRef]
- Quinn, H.; Graham, P.; Krone, J.; Caffrey, M.; Rezgui, S. Radiation-induced multi-bit upsets in SRAM-based FPGAs. IEEE Trans. Nucl. Sci. 2006, 52, 2455–2461. [Google Scholar] [CrossRef]
- Mukherjee, S.S.; Weaver, C.; Emer, J.; Reinhardt, S.K.; Austin, T. A systematic methodology to compute the architectural vulnerability factors for a high-performance microprocessor. In Proceedings of the 36th Annual IEEE/ACM International Symposium on Microarchitecture (MICRO-36), San Diego, CA, USA, 5 December 2003; pp. 29–40. [Google Scholar]
- Mukherjee, S.S.; Weaver, C.T.; Emer, J.; Reinhardt, S.K.; Austin, T. Measuring architectural vulnerability factors. IEEE Micro 2004, 23, 70–75. [Google Scholar] [CrossRef]
- Duan, L.; Li, B.; Peng, L. Versatile prediction and fast estimation of architectural vulnerability factor from processor performance metrics. In Proceedings of the 15th IEEE International Symposium on High Performance Computer Architecture (HPCA), Raleigh, NC, USA, 18 February 2009; pp. 129–140. [Google Scholar]
- Maniatakos, M.; Michael, M.K.; Makris, Y. Investigating the limits of AVF analysis in the presence of multiple bit errors. In Proceedings of the IEEE 19th International On-Line Testing Symposium (IOLTS), Chania, Greece, 8–10 July 2013; pp. 49–54. [Google Scholar]
- Ebrahimi, M.; Mohammadi, A.; Ejlali, A.; Miremadi, S.G. A fast, flexible, and easy-to-develop FPGA-based fault injection technique. Microelectron. Reliab. 2014, 54, 1000–1008. [Google Scholar] [CrossRef]
- Pournaghdali, F.; Rajabzadeh, A.; Ahmadi, M. VHDLSFI: A simulation-based multi-bit fault injection for dependability analysis. In Proceedings of the 3rd International eConference on Computer and Knowledge Engineering (ICCKE), Mashhad, Iran, 31 October–1 November 2013; pp. 354–360. [Google Scholar]
- Chatzidimitriou, A.; Papadimitriou, G.; Gavanas, C.; Katsoridas, G.; Gizopoulos, D. Multi-bit upsets vulnerability analysis of modern microprocessors. In Proceedings of the IEEE International Symposium on Workload Characterization (IISWC), Orlando, FL, USA, 3–5 November 2019; pp. 119–130. [Google Scholar]
- Chabot, A.; Alouani, I.; Niar, S.; Nouacer, R. A comprehensive fault injection strategy for embedded systems reliability assessment. In Proceedings of the International Symposium on Rapid System Prototyping (RSP), Turin, Italy, 4–5 October 2018; pp. 22–28. [Google Scholar]
- Souari, A.; Thibeault, C.; Blaquière, Y.; Velazco, R. An automated fault injection for evaluation of LUTs robustness in SRAM-based FPGAs. In Proceedings of the IEEE East-West Design & Test Symposium (EWDTS), Batumi, Georgia, 26–29 September 2025; pp. 1–4. [Google Scholar]
- Ullah, A.; Reviriego, P.; Sánchez-Macián, A.; Maestro, J.A. Multiple cell upset injection in BRAMs for Xilinx FPGAs. IEEE Trans. Device Mater. Reliab. 2018, 18, 636–638. [Google Scholar] [CrossRef]
- Tarrillo, J.; Tonfat, J.; Tambara, L.; Kastensmidt, F.L.; Reis, R. Multiple fault injection platform for SRAM-based FPGA based on ground-level radiation experiments. In Proceedings of the 16th Latin-American Test Symposium (LATS), Puerto Vallarta, Mexico, 25–27 March 2015; pp. 1–6. [Google Scholar]
- Mezzah, I.; Kermia, O.; Chemali, H. Extensive fault emulation on RFID tags for fault tolerance and security evaluation. Microelectron. Reliab. 2021, 124, 114263. [Google Scholar] [CrossRef]
- Chen, X.; Huo, L.; Xie, Y.; Shen, Z.; Xiang, Z.; Gao, C.; Zhang, Y. Fpga-based cross-hardware mbu emulation platform for layout-level digital vlsi. In Proceedings of the IEEE 32nd Asian Test Symposium (ATS), Beijing, China, 14–17 October 2023; pp. 1–6. [Google Scholar]
- Rajkumar, T.; Öberg, J. On Predictive Modeling of Multi-Bit Upsets for Emulated Fault Injection. In Proceedings of the 55th Annual IEEE/IFIP International Conference on Dependable Systems and Networks-Supplemental Volume (DSN-S), Naples, Italy, 23–26 June 2025; pp. 236–238. [Google Scholar]
- Rajkumar, T.; Öberg, J. Exploring the Potential of LSTM On Emulating Multiple-bit Fault Injection in SRAM-FPGA. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Stockholm, Sweden, 9–12 September 2025; Springer Nature: Cham, Switzerland, 2025; pp. 226–239. [Google Scholar]
- Sharma, J.; Rao, N.; Ait Mohamed, O. Fault Injection Controller Based Framework to Characterize Multiple Bit Upsets for FPGA Designs. In Proceedings of the IEEE International Symposium on the Physical and Failure Analysis of Integrated Circuits (IPFA), Singapore, 20–23 July 2020; pp. 1–5. [Google Scholar]
- Sharma, J.; Rao, N. The characterization of errors in an FPGA-based RISC-V processor due to single event transients. Microelectron. J. 2022, 123, 105392. [Google Scholar] [CrossRef]
- Magliano, E.; Savino, A.; Di Carlo, S. Real-time Embedded System Fault Injector Framework for Micro-architectural State Based Reliability Assessment. J. Electron. Test. 2025, 41, 193–208. [Google Scholar] [CrossRef]
- Khoshavi, N.; Samiei, A. The Study of Transient Faults Propagation in Multithread Applications. arXiv 2016, arXiv:1607.08523. [Google Scholar] [CrossRef]
- Abideen, Z.U.; Rashid, M. EFIC-ME: A fast emulation based fault injection control and monitoring enhancement. IEEE Access 2020, 8, 207705–207716. [Google Scholar] [CrossRef]
- Georgakos, G.; Huber, P.; Ostermayr, M.; Amirante, E.; Ruckerbauer, F. Investigation of increased multi-bit failure rate due to neutron induced SEU in advanced embedded SRAMs. In Proceedings of the IEEE symposium on VLSI circuits, Kyoto, Japan, 14–16 June 2007; pp. 80–81. [Google Scholar]
- Dixit, A.; Wood, A. The impact of new technology on soft error rates. In Proceedings of the International Reliability Physics Symposium, Monterey, CA, USA, 10–14 April 2011; pp. 5B.4.1–5B.4.7. [Google Scholar]
- Benevenuti, F.; Kastensmidt, F.L. Comparing exhaustive and random fault injection methods for configuration memory on SRAM-based FPGAs. In Proceedings of the IEEE Latin American Test Symposium (LATS), Santiago, Chile, 11–13 March 2019; pp. 1–6. [Google Scholar]
- Kchaou, A.; Saad, S.; Garrab, H. Emulation-Based Analysis of Multiple Cell Upsets in LEON3 SDRAM: A Workload-Dependent Vulnerability Study. Electronics 2025, 14, 4582. [Google Scholar] [CrossRef]
- IEEE 1149.1-2013; IEEE Standard for Test Access Port and Boundary-Scan Architecture. IEEE: Piscataway, NJ, USA, 2013. [CrossRef]
- Piret, G.; Quisquater, J.J. A differential fault attack technique against SPN structures, with application to the AES and KHAZAD. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Cologne, Germany, 8–10 September 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 77–88. [Google Scholar]
- Tunstall, M.; Mukhopadhyay, D.; Ali, S. Differential fault analysis of the advanced encryption standard using a single fault. In Proceedings of the 5th IFIP International Workshop on Information Security Theory and Practices, Heraklion Crete, Greece, 1–3 June 2011; Springer: Berlin/Heidelberg, Germany, 2025; pp. 224–233. [Google Scholar]
- Wu, C.; Chen, J.; Fang, Q.; He, K.; Zhao, Z.; Ren, H.; Xu, G.; Liu, Y.; Xiang, Y. Rethinking Membership Inference Attacks against Transfer Learning. IEEE Trans. Inf. Forensics Secur. 2024, 19, 6441–6454. [Google Scholar] [CrossRef]
- Liang, R.; Chen, J.; Wu, C.; He, K.; Wu, Y.; Cao, R.; Du, R.; Zhao, Z.; Liu, Y. VULSEYE: Detect Smart Contract Vulnerabilities via Stateful Directed Graybox Fuzzing. IEEE Trans. Inf. Forensics Secur. 2025, 20, 2157–2170. [Google Scholar] [CrossRef]


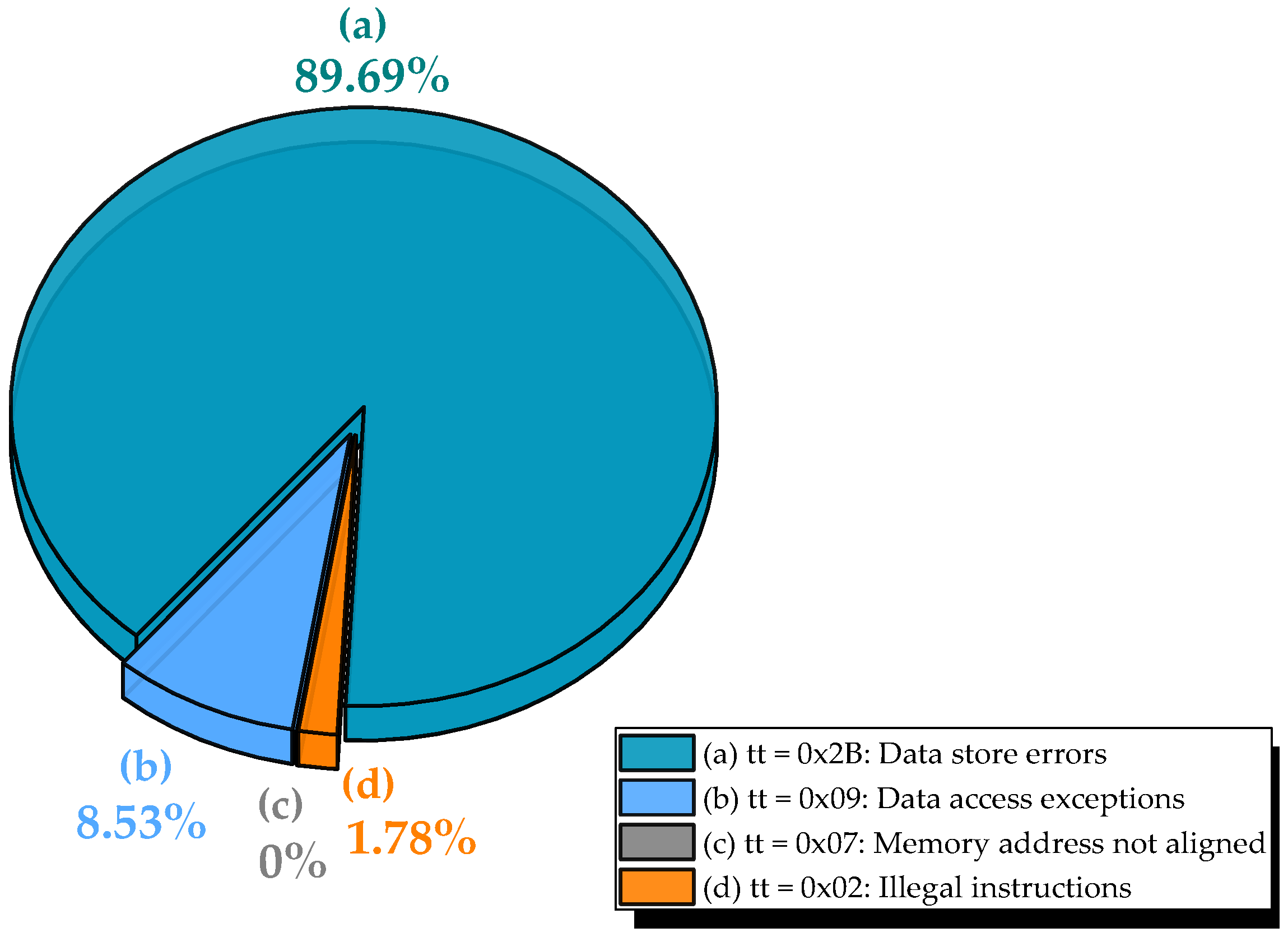
| FI Campaign (Total FI = 311,310) | Masked Faults | SDC | Halt Executions | Stopped Mode | |||
|---|---|---|---|---|---|---|---|
| Data Store Errors | Data Access Exceptions | Mem. Address Not Aligned | Illegal Instructions | ||||
| 5489 (Series 1) | 113 | 1 | 4 | 0 | 3 | 5367 | 1 |
| 31,474 (Series 2) | 830 | 0 | 4908 | 25,733 | 2 | 0 | 1 |
| 16,018 (Series 3) | 830 | 0 | 15,187 | 0 | 0 | 0 | 1 |
| 6654 (Series 4) | 830 | 0 | 5823 | 0 | 0 | 0 | 1 |
| 8738 (Series 5) | 830 | 0 | 7907 | 0 | 0 | 0 | 1 |
| 46,598 (Series 6) | 830 | 0 | 45,767 | 0 | 0 | 0 | 1 |
| 24,863 (Series 7) | 830 | 0 | 24,032 | 0 | 0 | 0 | 1 |
| 46,145 (Series 8) | 1595 | 0 | 44,549 | 0 | 0 | 0 | 1 |
| 62,497 (Series 9) | 830 | 0 | 61,666 | 0 | 0 | 0 | 1 |
| 40,434 (Series 10) | 830 | 0 | 39,603 | 0 | 0 | 0 | 1 |
| 22,400 (Series 11) | 830 | 0 | 21,570 | 0 | 0 | 0 | 0 |
| FI Campaign (Total FI = 303,000) | Masked Faults | SDC | Halt Executions | Stopped Mode | ||
|---|---|---|---|---|---|---|
| Data Store Errors | Data Access Exceptions | Illegal Instructions | ||||
| 116,501 (Series 1) | 8 | 1 | 226 | 1 | 116,264 | 1 |
| 186,499 (Series 2) | 1 | 0 | 186,498 | 0 | 0 | 0 |
| FI Campaign (Total FI = 303,161) | Masked Faults | SDC | Halt Executions | Stopped Mode | |||
|---|---|---|---|---|---|---|---|
| Data Store Errors | Data Access Exceptions | Mem. Address Not Aligned | No Responses | ||||
| 7960 (Series 1) | 7872 | 10 | 0 | 7 | 0 | 70 | 1 |
| 7057 (Series 2) | 3504 | 68 | 0 | 757 | 27 | 2700 | 1 |
| 4145 (Series 3) | 3673 | 0 | 0 | 469 | 2 | 0 | 1 |
| 3755 (Series 4) | 3752 | 0 | 0 | 0 | 2 | 0 | 1 |
| 280,244 (Series 5) | 280,220 | 0 | 24 | 0 | 0 | 0 | 0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kchaou, A.; Saad, S.; Garrab, H. Workload-Dependent Vulnerability of SDRAM Multi-Bit Upsets in a LEON3 Soft-Core Processor. Electronics 2025, 14, 4852. https://doi.org/10.3390/electronics14244852
Kchaou A, Saad S, Garrab H. Workload-Dependent Vulnerability of SDRAM Multi-Bit Upsets in a LEON3 Soft-Core Processor. Electronics. 2025; 14(24):4852. https://doi.org/10.3390/electronics14244852
Chicago/Turabian StyleKchaou, Afef, Sehmi Saad, and Hatem Garrab. 2025. "Workload-Dependent Vulnerability of SDRAM Multi-Bit Upsets in a LEON3 Soft-Core Processor" Electronics 14, no. 24: 4852. https://doi.org/10.3390/electronics14244852
APA StyleKchaou, A., Saad, S., & Garrab, H. (2025). Workload-Dependent Vulnerability of SDRAM Multi-Bit Upsets in a LEON3 Soft-Core Processor. Electronics, 14(24), 4852. https://doi.org/10.3390/electronics14244852







