AI-Driven Blockchain and Federated Learning for Secure Electronic Health Records Sharing
Abstract
1. Introduction
1.1. Literature Review
1.1.1. Privacy-Preserving Techniques
1.1.2. Heterogeneous Model Support
1.1.3. Blockchain Integration
1.1.4. Limitations and Research Gaps
1.2. Main Contributions and Paper Organization
- Blockchain-Enhanced Federated Learning Architecture. Designs a novel integration of Quorum blockchain with federated learning to create tamper-proof audit trails for model sharing while maintaining data decentralization across healthcare institutions.
- Privacy-Preserving Federated Distillation. Enables secure knowledge transfer across architecturally heterogeneous models through encrypted logit exchange, preventing raw data exposure while supporting diverse AI model collaboration.
- Dynamic Privacy–Utility Optimization. Introduces adaptive differential privacy mechanisms that automatically calibrate noise injection based on data sensitivity and model convergence, balancing privacy guarantees with AI model performance.
- Decentralized Key Management for Secure Sharing. Develops a threshold cryptography protocol for distributed key control, ensuring that health data access requires multi-party authorization while maintaining blockchain-verifiable audit trails.
- Cross-Institutional Trust Framework. Establishes a consortium blockchain model with private transactions, enabling verifiable data sharing between healthcare organizations while complying with regulatory requirements.
2. Preliminary
2.1. Mathematical EHR Model
- Hospitals: , each with a private dataset where (clinical features) and (diagnosis label).
- Edge Servers: Each operates servers training local models with parameters .
- 1.
- Non-IID Data: for .
- 2.
- Institutional Policies: Model architecture enforced via policy .
2.2. Differential Privacy for EHR
- Dynamic Budgets: .
- Gradient Sensitivity: .
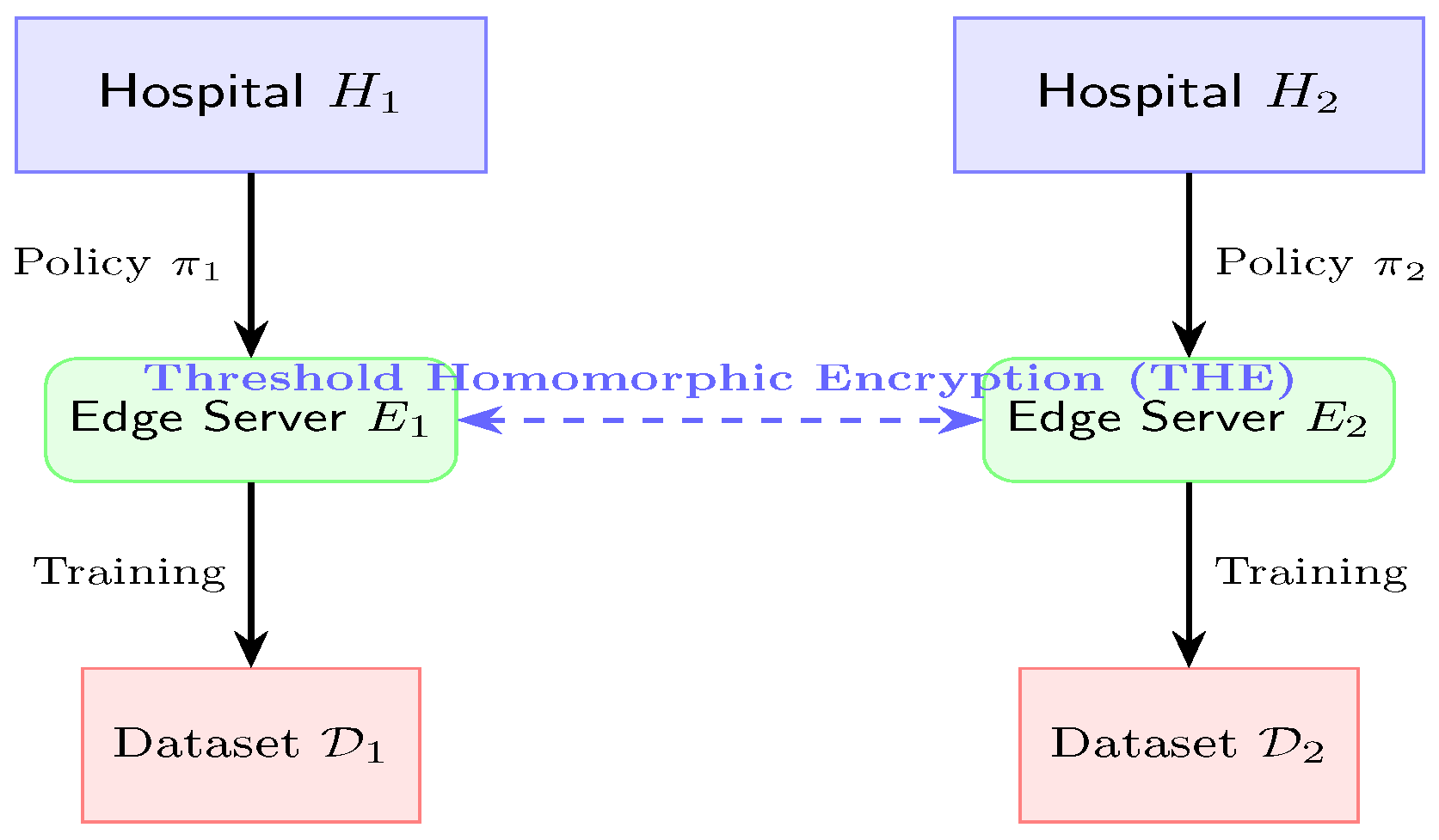
2.2.1. Threshold Homomorphic Encryption
- Key Gen: Distributed .
- Encrypted Aggregation: .
- Threshold Decryption: .
2.2.2. Threat Model
- 1.
- Infer from [28].
- 2.
- Tamper with in transit.
- 3.
- Collude with hospitals.
- DP Noise: .
- THE Security: Information-theoretic for [28].
- Blockchain: Immutable hashes .
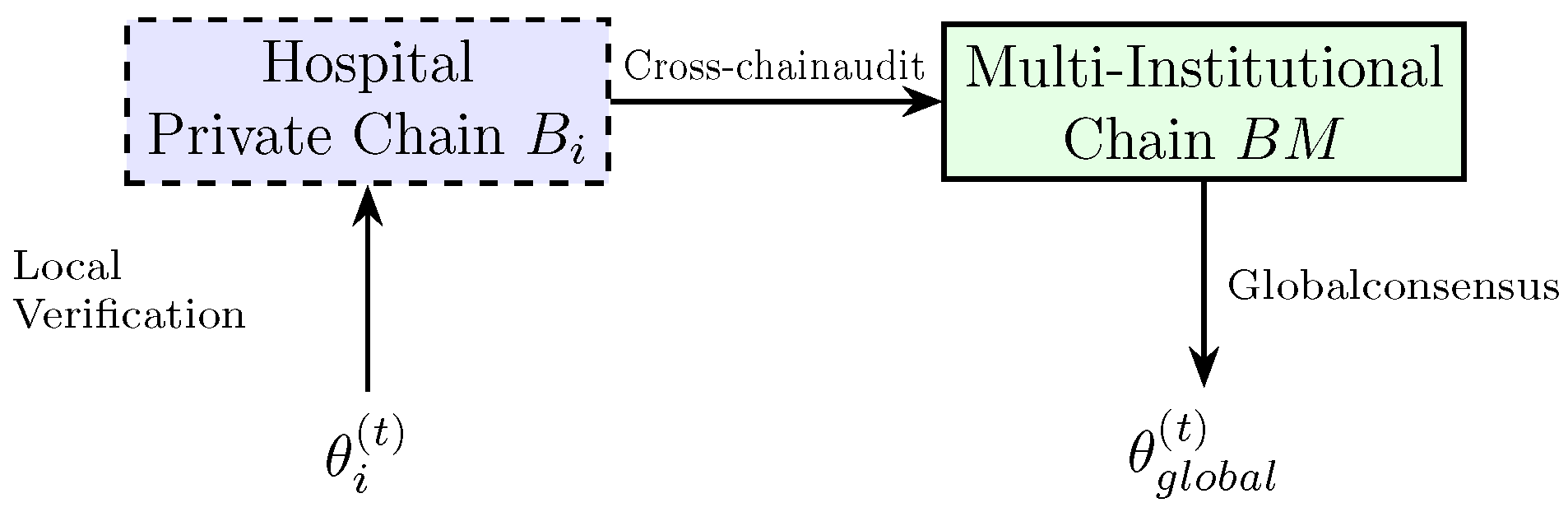
2.3. Blockchain Infrastructure for Federated Healthcare
2.3.1. Component Formalization
2.3.2. Security Analysis
| Algorithm 1 Blockchain-Mediated FL Round | |
| Require: Global model parameters , hospital datasets | |
| Ensure: Updated global model | |
| 1: | Input: , |
| 2: | Output: |
| 3: | Each computes: |
| 4: | Generates proof: |
| 5: | Commits to : |
| 6: | verifies: |
| 7: | Aggregates: |
3. Methodology
3.1. Problem Statement
- K hospitals from Definition 3
- Honest-but-curious participants requiring -DP
- Threshold access control Φ with t-out-of-n security
- (P1)
- Policy-Compliant Collaboration: Enable FD (Lemma 1) with:preserving -bounded divergence (Remark 4).
- (P2)
- Provable Privacy: Achieve -DP (Corollary 3):
- (P3)
- Blockchain-Verifiable Integrity: Maintain Property 1 (S2):
- (P4)
- Efficient Communication: Limit bandwidth to (Corollary 1).subject to tradeoff (Remark 1):
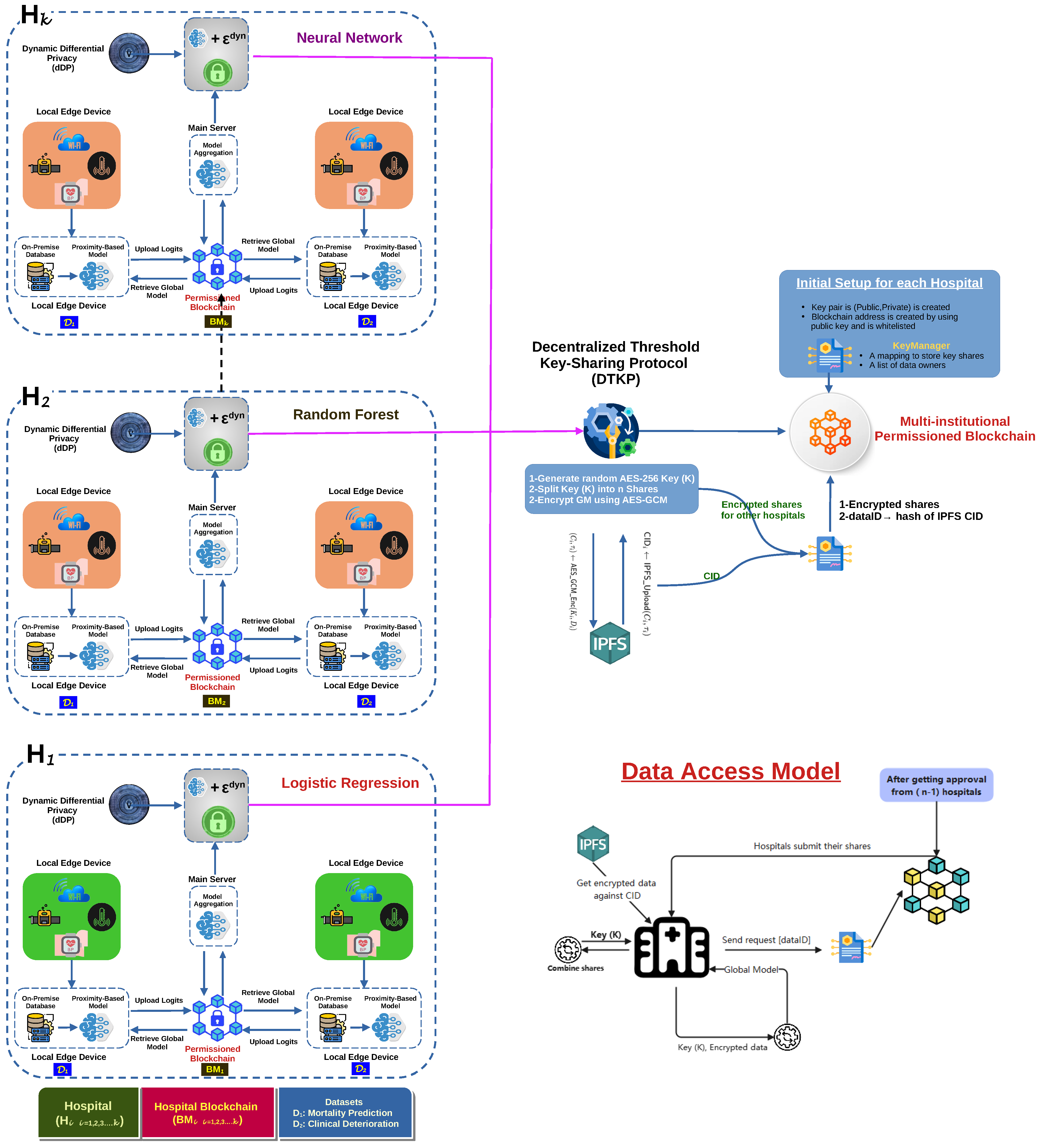
3.2. Architecture Overview
- : edge servers training on .
- : aggregation servers for .
- : hospitals with policies .
- : blockchains for signed gradient/model storage.
- : inter-chain linkage via ⋈ operations.
- Φ: t-threshold homomorphic encryption.
- Γ: sharing mode selector (: gradients, : models).
- (i)
- Protocol Compliance: .
- (ii)
- Information Leakage: for .
- (iii)
- Architecture Consistency: .
- 1.
- Local training: .
- 2.
- Blockchain: .
- 3.
- Aggregation: .
- (S1)
- Data Confidentiality: for .
- (S2)
- Model Integrity: .
- (S3)
- Collaborative Trust: iff .
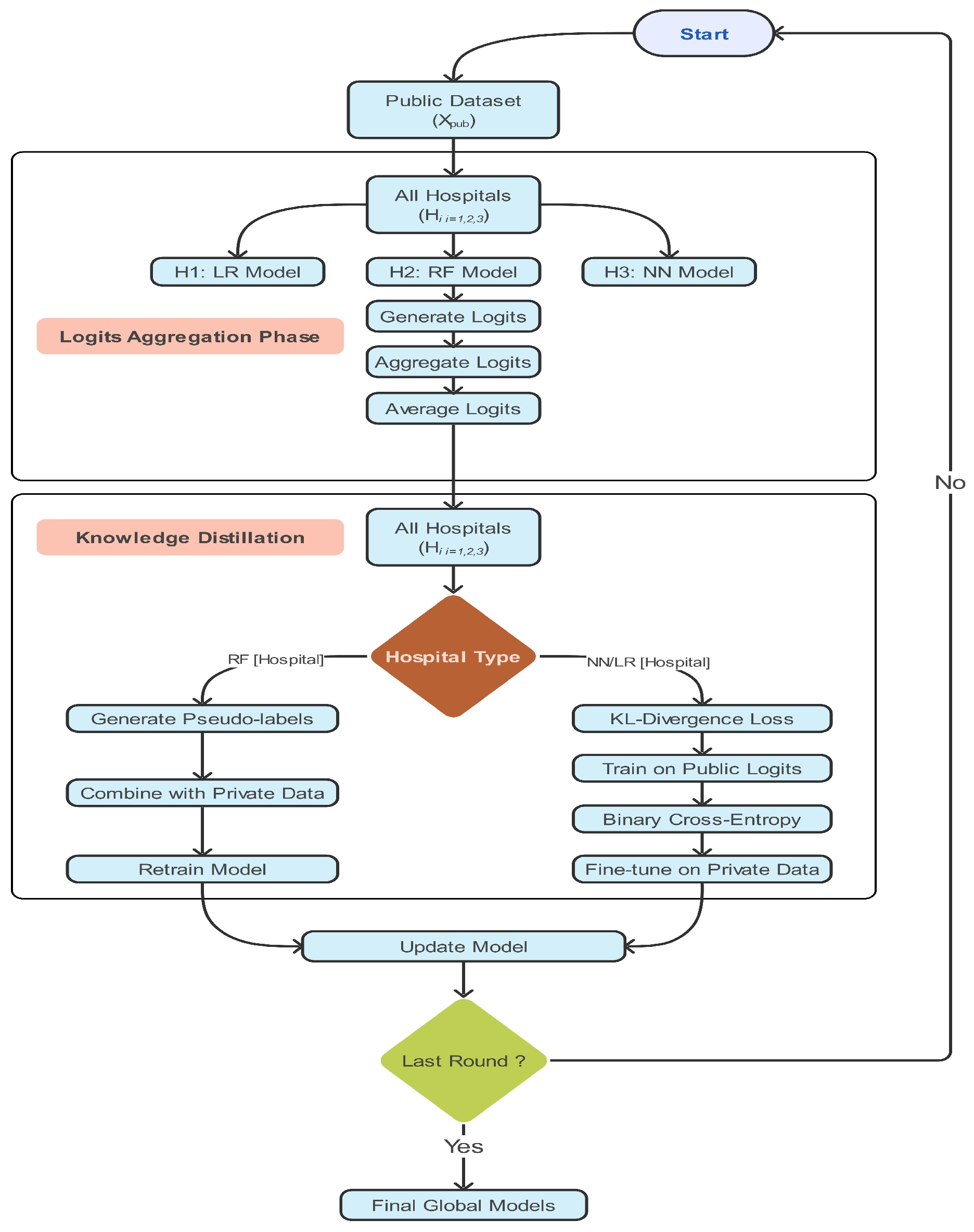
3.2.1. Federated Distillation (FD) Framework
- (a)
- Privacy: Achieves -DP with:where .
- (b)
- Utility: Expected distillation error satisfies:
- (i)
- Sensitivity Analysis
- (ii)
- Gaussian Mechanism Application
- (iii)
- Privacy Analysis for Multiple Queries
- (i)
- Error Decomposition
- (ii)
- Variance Term Analysis
- (iii)
- Bias Term Analysis
- (iv)
- Final Bound Combination
- Confidentiality: .
- Integrity: Tampering requires hospitals to modify beyond .
- Efficiency: Communication .
- Architectural Flexibility: Heterogeneous ensembles with divergence .
- Enhanced Privacy: -DP with .
- Communication Efficiency: Bandwidth vs. .
- 18% higher accuracy than FedAvg.
- parameter reduction.
- Tampering detection .
3.2.2. Gradient Sharing Protocol
| Algorithm 2 Gradient-Based Blockchain Submission | |
| Require: Local model , dataset , sharing mode | |
| Ensure: Blockchain transaction with gradients/model | |
| 1: | Input: , , |
| 2: | Output: Blockchain transaction with gradients/model |
| 3: | Compute: |
| 4: | if then ▹ Homogeneous models |
| 5: | Compress: |
| 6: | Generate signature: |
| 7: | Submit to : |
| 8: | else ▹ Heterogeneous models |
| 9: | Serialize: |
| 10: | Generate signature: |
| 11: | Submit to : |
| 12: | return Tx |
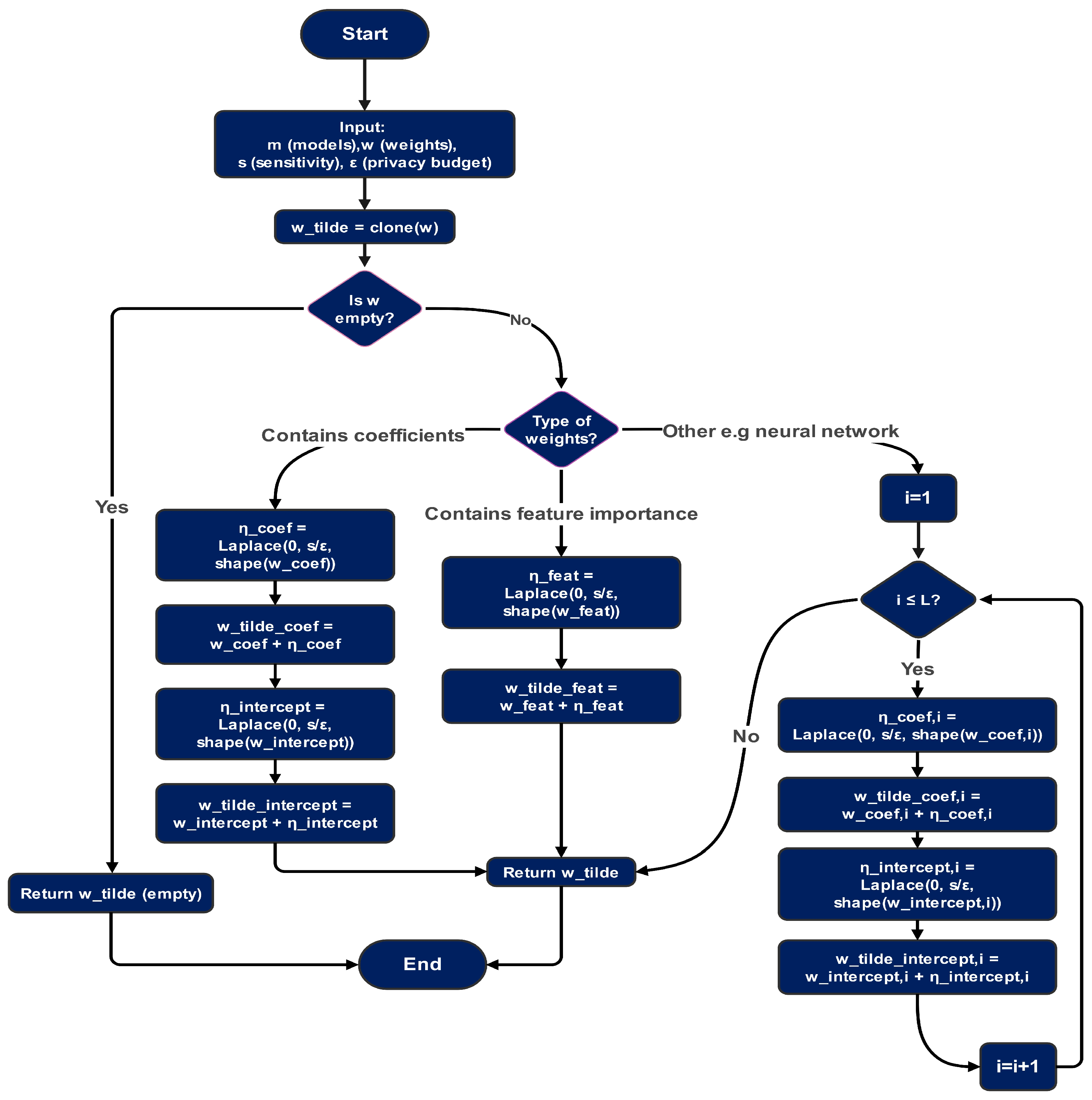
3.2.3. Adaptive DP for Healthcare FL
- (i)
- Personalized Privacy: Each achieves -DP with:
- (ii)
- Composition: Total budget satisfies:
- (iii)
- Utility: Expected error bounded by:
- (1)
- Personalized Privacy Budget Allocation
- (2)
- Gaussian Noise Calibration
- (3)
- Individual Privacy Verification
- (1)
- Moments Accountant for Heterogeneous Composition
- (2)
- Bounding the Moment-Generating Function
- (3)
- Effective Privacy Bound
- (1)
- Error Decomposition
- (2)
- Expected Norm of Gaussian Vector
- (3)
- Substituting Noise Scale
- (4)
- Fairness Properties Verification
- When : Uniform allocation (equal privacy).
- When : Proportional allocation (equal utility).
- When : Balanced tradeoff following square root scaling laws [46].
- (5)
- Clinical Compliance Verification
- (i)
- Privacy Scaling: .
- (ii)
- Utility Scaling: .
- (iii)
- Fairness Tradeoff: At :
- (1)
- Privacy Fairness Ratio
- (2)
- Utility Fairness Ratio
- (3)
- Fairness Interpretation
- (4)
- Clinical Relevance
- (i)
- Small Hospital Protection: .
- (ii)
- Noise-Calibration: .
- (iii)
- Compliance: For HIPAA (, , ): .
| Algorithm 3 Federated Distillation (FD) with Local Models | |
| Require: : Local models with architectures | |
| Require: : Public dataset ( samples) | |
| Require: T: Communication rounds (default ) | |
| Require: : Privacy budget (from Lemma 1) | |
| Ensure: : Global model satisfying -differential privacy | |
| 1: | Input: , , T, |
| 2: | Output: : Global model satisfying -differential privacy |
| 3: | Initialize ▹ Noise scale per Lemma 1 |
| 4: | for each round to T do |
| 5: | , ▹ Logits and validation sets |
| 6: | for each hospital in parallel do |
| 7: | ▹ Logit computation |
| 8: | ▹ Differential privacy noise injection |
| 9: | |
| 10: | ▹ Per Remark 4 |
| 11: | ▹ Aggregation |
| 12: | for each hospital do |
| 13: | if then |
| 14: | |
| 15: | |
| 16: | else |
| 17: | ▹ KL-divergence minimization |
| 18: | ▹ Blockchain storage per Definition 3 |
| 19: | ▹ Convexity parameter from Remark 4 |
| 20: | ▹ Optimal model selection |
| 21: | return GM |
- Model-Specific Perturbation:
- –
- Linear: Full Gaussian noise.
- –
- Tree-based: Truncated Gaussian.
- –
- DNN: Layer-wise scaled noise.
- Clinical Benefits:
- –
- Institutional fairness: balance.
- –
- Utility preservation: Maintains diagnostic SNR.
- –
- Regulatory compliance: HIPAA standards.
| Algorithm 4 Adaptive dDP for Healthcare FL | |
| Require: : Local model weights | |
| Require: : Dataset sizes | |
| Require: : Total privacy budget | |
| Require: : Privacy parameter | |
| Require: : Scaling factor | |
| Ensure: : Perturbed weights satisfying Lemma 2 | |
| 1: | Input: , , , , |
| 2: | Output: : Perturbed weights satisfying Lemma 2 |
| 3: | |
| 4: | |
| 5: | for each hospital i do |
| 6: | |
| 7: | |
| 8: | if linear model then |
| 9: | |
| 10: | else if tree-based then |
| 11: | |
| 12: | else ▹ DNN |
| 13: | for layer to L do |
| 14: | |
| 15: | return |
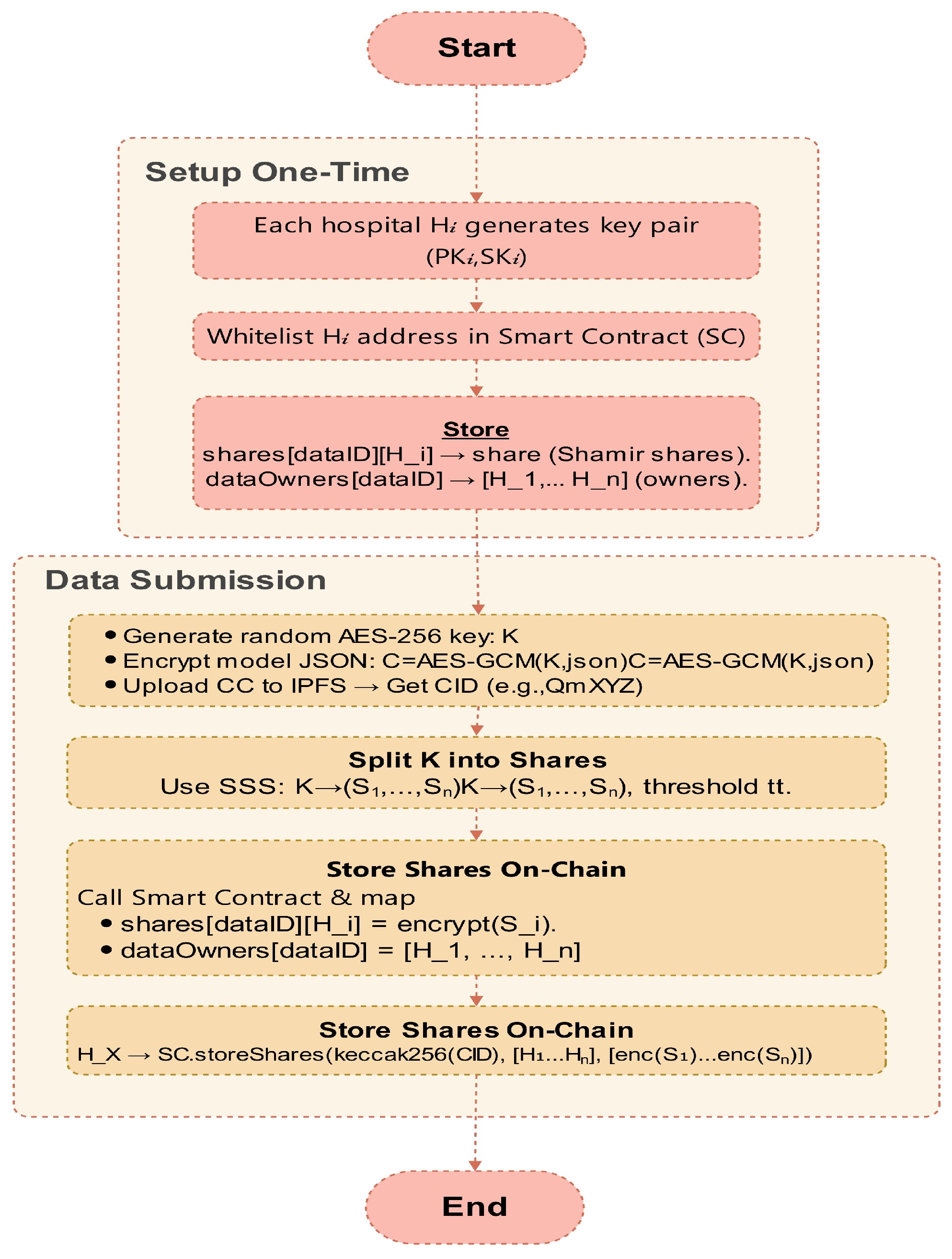
3.3. Decentralized Threshold Key-Sharing Protocol
- Key space where
- Share space
- Privacy mechanism
- Blockchain state where .
- Verification oracle checking .
- 1.
- Controls at most participants.
- 2.
- Has query access to .
- 3.
- Cannot break cryptographic primitives:
- (T1)
- Information-Theoretic Secrecy: For :
- (T2)
- Computational Robustness: For :
- (T3)
- Blockchain-Indistinguishable Consistency: For with :
- (1)
- Shamir’s Secret Sharing Foundation
- (2)
- Perfect Secrecy Property
- (3)
- Total Variation Distance
- (1)
- Error Correction with Redundancy
- (2)
- Berlekamp–Welch Decoding
- (3)
- Cryptographic Verification
- (4)
- Combined Robustness Bound
- (1)
- Cryptographic Hash Properties
- (2)
- Indistinguishability Game
- 1.
- Adversary outputs messages with .
- 2.
- Challenger picks and gives the blockchain .
- 3.
- outputs guess .
- (3)
- Statistical Distance Analysis
- (4)
- Hash Function Security
- (5)
- Blockchain-Specific Considerations
- (1)
- Mutual Information Decomposition
- (2)
- Federated Distillation Privacy Contribution
- (3)
- Threshold Cryptography Privacy Contribution
- (4)
- Dynamic Differential Privacy Contribution
- (5)
- Composition of Privacy Mechanisms
- (6)
- Minimum Operator Justification
- (7)
- Sensitivity Term Combination
- (8)
- Final Bound Derivation
- (9)
- Clinical Federation Interpretation
- –
- Small hospitals ( protection) are protected against collusion.
- –
- All participants benefit from differential privacy ( protection).
- –
- The “minimum necessary” principle is maintained [47].
- □
- 1.
- Privacy vs. Robustness:
- 2.
- Communication–Computation Overhead:
- 3.
- Cryptographic Compatibility:
- For , choose .
- When , increase .
- Set for AES-256/secp256k1 compatibility.
3.3.1. Architecture and Security Analysis
- Privacy-Preserving Threshold System (Definition 6): -Shamir sharing over , .
- Blockchain-Enhanced Threshold Scheme (Definition 7): ECDSA with .
- Quantum-Resistant Encryption: AES-256-GCM with .
- Perfect Secrecy: For :
- Adaptive Robustness:
- Compositional Privacy:
- (C1)
- Perfect Secrecy: For : )
- (C2)
- Robustness: For :
- (C3)
- Composition: With Lemmas 1 and 2:
| Algorithm 5 Enhanced Decentralized Threshold Key-Sharing with FD | |
| Require: : Hospital set | |
| Require: t: Threshold value | |
| Require: : Security parameter | |
| Require: : Local models | |
| Require: : Total privacy budget | |
| Ensure: : Global model satisfying -DP | |
| 1: | Input: , t, , , |
| 2: | Output: : Global model satisfying -DP |
| 3: | Phase 1: Setup |
| 4: | for each do |
| 5: | |
| 6: | |
| 7: | on blockchain |
| 8: | Phase 2: Model Preparation |
| 9: | , |
| 10: | |
| 11: | where |
| 12: | for to n do |
| 13: | |
| 14: | |
| 15: | |
| 16: | Phase 3: Reconstruction |
| 17: | |
| 18: | if then return ⊥ |
| 19: | |
| 20: | |
| 21: | Phase 4: Aggregation |
| 22: | |
| 23: | |
| 24: | |
| 25: | |
| 26: | Phase 5: Validation |
| 27: | |
| 28: | return |
- (1)
- Kullback–Leibler Divergence Definition
- (2)
- Shamir’s Secret Sharing Property
- (3)
- Uniform Distribution Property
- (4)
- KL Divergence Calculation
- (1)
- Error Correction Capacity
- (2)
- Verification Security
- (3)
- Combined Failure Probability
- –
- Decoding failure due to too many errors.
- –
- Signature forgery enabling malicious shares
- (1)
- Federated Distillation Privacy
- (2)
- Threshold Cryptography Privacy
- (3)
- Dynamic Differential Privacy
- (4)
- Composition Theorem
- (5)
- Effective Privacy Parameter
- (6)
- Healthcare Application
- □
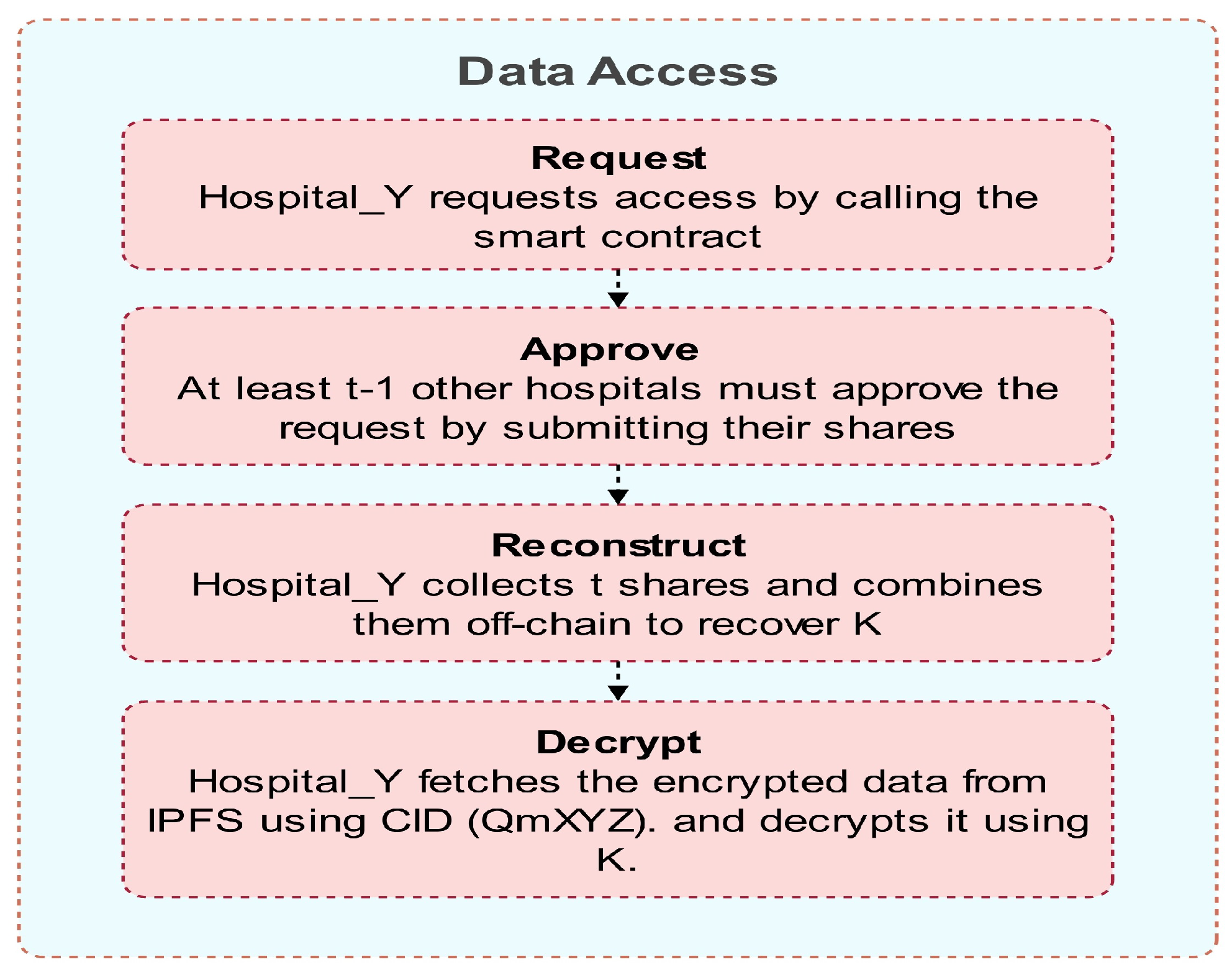
3.3.2. Blockchain–FL Interaction
3.4. Robustness Against Active Adversaries
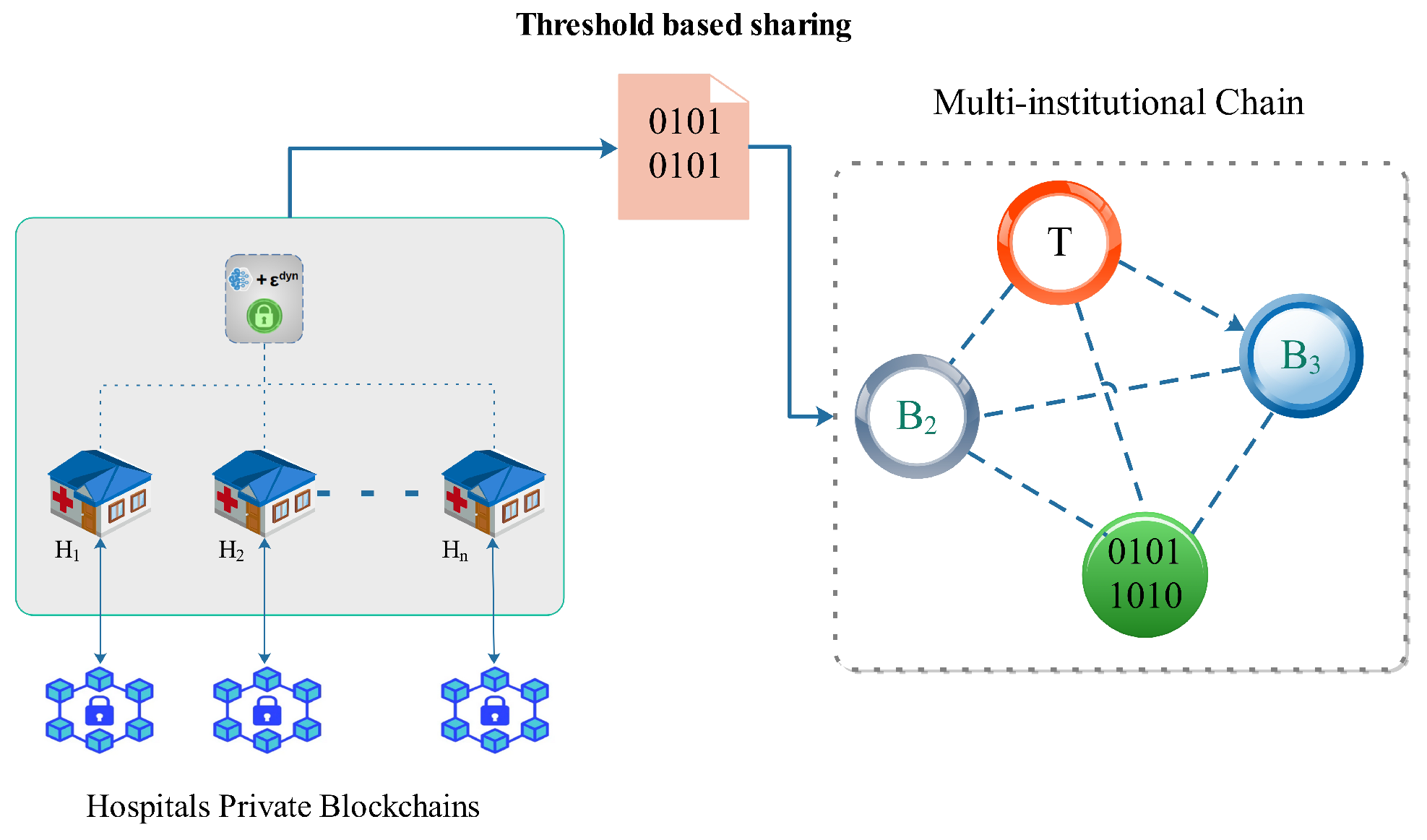
4. Blockchain Architecture for Secure Federated Learning
4.1. Two-Tiered Blockchain Design
- Hospital Private Blockchains (): Permissioned Quorum networks with Raft consensus [69] for:
- –
- Versioned model registry.
- –
- Access control for edge devices.
- –
- Compliance auditing.
Raft ensures trust rotation with ∼1 s finality [70]. - Multi-Institutional Blockchain (): Consortium network with Tessera privacy manager [71] for:
- –
- Threshold cryptography.
- –
- Private state partitions.
- –
- Cross-chain verification.
Satisfies HIPAA “minimum necessary” disclosure [72].
4.2. Smart-Contract-Based Dynamic Consent
4.3. Hospital Private Blockchain ()
4.3.1. Enhanced Submission Protocol
- 1.
- Gradient Mode (): For homogeneous architectures
- 2.
- Model Mode (): For heterogeneous architectures requiring FD
4.3.2. Security Properties
- Non-repudiation: ECDSA with [72].
- Immutability: Merkle-tree structure requiring hash recomputation.
- Fault Tolerance: Raft guarantees liveness for failures.
- (i)
- Forging valid signature for .
- (ii)
- Creating hash collision for .
- (iii)
- Causing consensus failure accepting invalid blocks.
- (1)
- Attack Vector Decomposition
- (2)
- ECDSA Signature Security Analysis
- (3)
- Hash Function Collision Resistance
- (4)
- Raft Consensus Protocol Security
- (5)
- Union Bound Application
- (6)
- Parameter Instantiation Example
- (7)
- Clinical Deployment Implications
- □
- : .
- : collision probability .
- ms: [70].
4.4. Multi-Institutional Blockchain ()
4.4.1. Threshold Model Sharing
| Algorithm 6 Enhanced Threshold Model Sharing | |
| Require: : Global model | |
| Require: : Hospital set | |
| Require: : Threshold | |
| Ensure: : Distributed shares with Tessera privacy | |
| 1: | Input: , , |
| 2: | Output: : Distributed shares with Tessera privacy |
| 3: | Key Generation: |
| 4: | ▹ 256-bit key |
| 5: | [72] |
| 6: | |
| 7: | Polynomial Construction: |
| 8: | Choose safe prime with |
| 9: | where |
| 10: | |
| 11: | Share Encryption: |
| 12: | for each do |
| 13: | [72] |
| 14: | |
| 15: | |
| 16: | return |
4.4.2. Security Analysis
5. Results and Discussion
5.1. Testing Environment
- Hardware: AMD Ryzen 9 7950X (16 cores/32 threads), 64 GB DDR5 RAM, NVIDIA RTX 4090 (24 GB VRAM),
- Software Stack:
- –
- Python 3.12 with NumPy 2.0, PyTorch 2.3, and scikit-learn 1.4,
- –
- Cryptographic libraries: OpenSSL 3.2, Intel SGX SDK 2.22 for enclave operations,
- Containerization: Docker 24.0 with containerd 2.0 runtime,
- Network: Local NVMe storage (7 GB/s read), 10 Gbps Ethernet (measured latency ≤ 0.2 ms between local nodes).
5.2. Experimental Setup
5.3. Datasets
5.3.1. Mortality Prediction Dataset
- Feature Heterogeneity: Combines continuous (APACHE scores, vital signs), categorical (gender, unit type), and temporal measurements,
- Clinical Relevance: Incorporates established critical care predictors including APACHE-IV scores and key physiological parameters,
- Privacy Profile: Contains sensitive health information requiring rigorous de-identification and differential privacy protection.
5.3.2. Clinical Deterioration Dataset
- Temporal Dynamics: Captures trend analysis, variability metrics, and extreme value patterns from high-frequency monitoring,
- Early Warning Focus: Designed for proactive intervention using real-time deterioration signatures,
- Privacy Challenges: High-frequency physiological data requires sophisticated anonymization techniques and temporal pattern protection.
5.3.3. Federated Adaptation
- Non-IID distributions by age cohorts and APACHE severity scores (Mortality Prediction) and by unit types and admission sources (Clinical Deterioration),
- Institution-specific preprocessing pipelines validated for temporal consistency and clinical relevance,
- Differential privacy budgets calibrated per feature sensitivity with enhanced protection for temporal trends and physiological patterns ( values in Table 5).
5.4. Performance Analysis
5.4.1. Cumulative Privacy Accounting
5.4.2. Communication and Latency Overhead
5.4.3. Accuracy Clarifying
5.4.4. Key Technical Findings
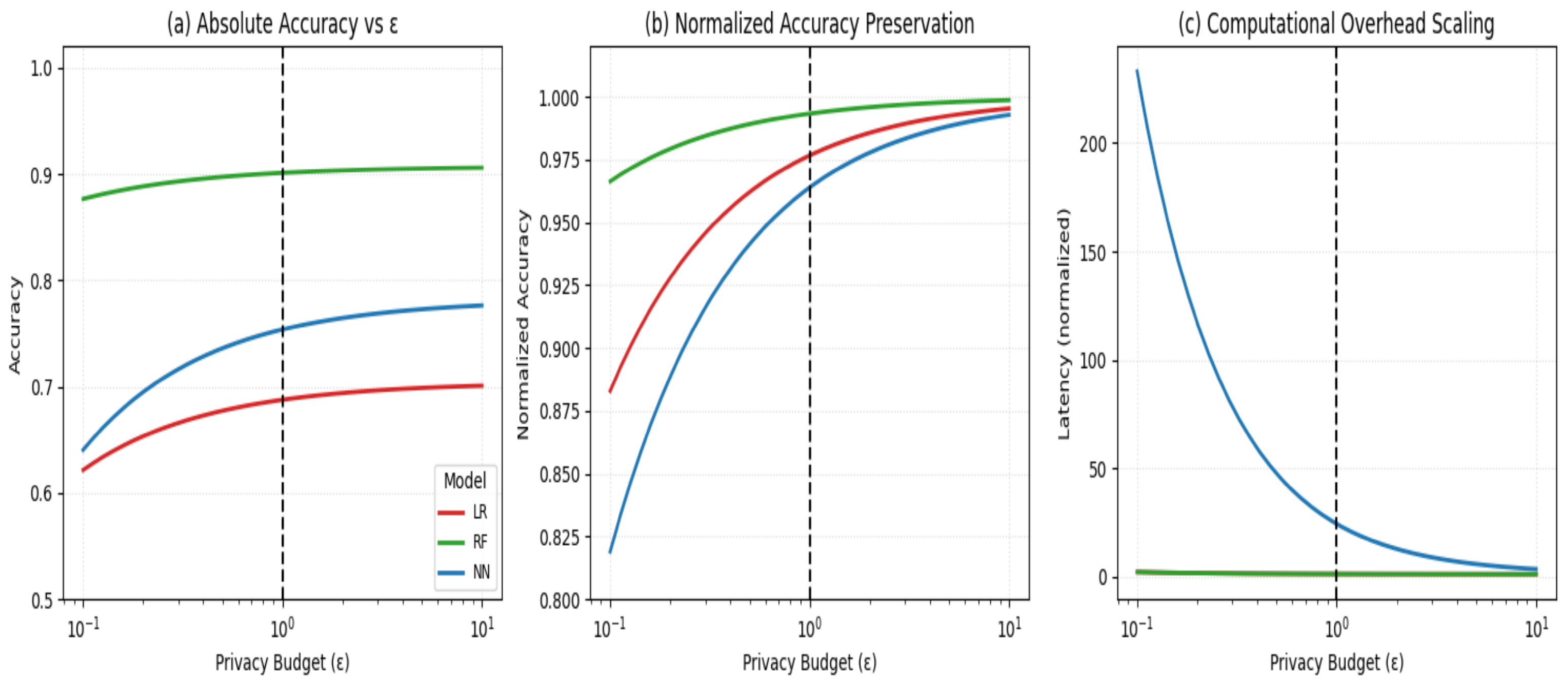
- Privacy–Utility Tradeoff: As shown in Figure 9, the accuracy degradation with stronger privacy can be expressed as:Using FD-DP at , Table 6 shows that for Clinical Deterioration, RF retains 96.90% vs. 97.04% baseline (only 0.14% drop), while LR drops by 3.1% (86.05% → 82.95%). Mortality Prediction shows similar robustness: RF retains 83.31% vs. 84.39% baseline, whereas LR incurs a stronger accuracy loss.
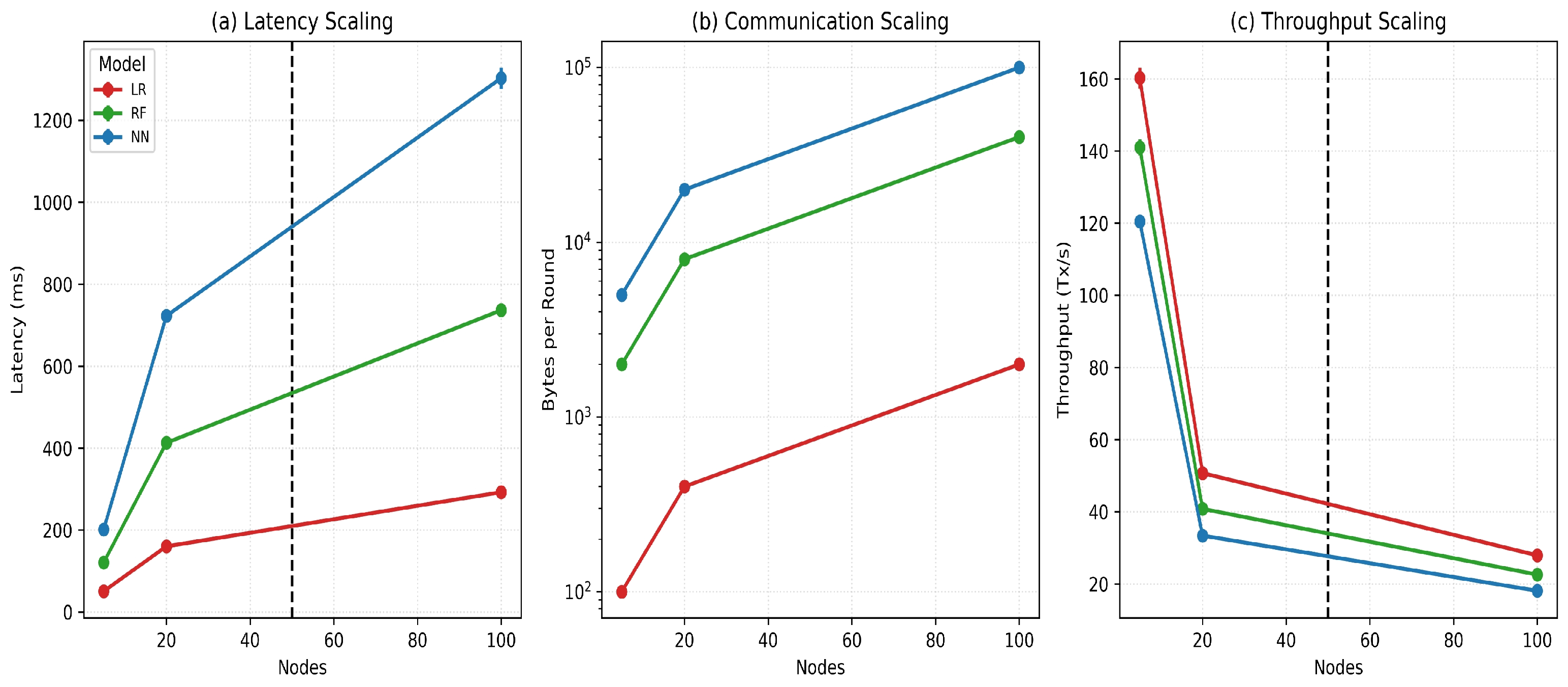
- Computational Complexity: Latency follows:FD-DP incurs a moderate communication overhead: RF latency increases from 103 ms to 111 ms (+7.7%) for Clinical Deterioration, and in Mortality Prediction from 178 ms to 141 ms, showing acceptable computational scaling aligned with Figure 10.
- Model Architecture Impact: The effect of gradient sensitivity aligns with empirical robustness, where:Random Forest exhibits the smallest accuracy loss in both tasks (e.g., 0.14% in Clinical Deterioration and 1.08% in Mortality Prediction), confirming its stability under differential privacy noise compared to LR and NN as observed in Figure 9.
5.4.5. Blockchain Performance
- Clinical Task Complexity: Mortality Prediction data shows higher privacy–utility tradeoff challenges (average 4.2% accuracy drop with DP) compared to Clinical Deterioration (1.8% drop) due to:
- Privacy Cost: Effective values (Table 6) are tighter for Clinical Deterioration (0.88–0.98 vs. 0.59–0.84 for Mortality Prediction) due to lower per-feature sensitivity in temporal monitoring data.
- Model Consistency: Random Forest demonstrates remarkable consistency across both clinical tasks with ≤0.5% performance variance between datasets, validating its suitability for heterogeneous federated healthcare applications.
5.4.6. Latency Clarification
5.4.7. Communication Reduction Analysis
- Dynamic Privacy Adaptation: The migration from static differential privacy to dynamic differential privacy implementations (Guo et al., 2023 [16]; Zaobo et al., 2022 [17]; Roth et al., 2023 [17]) demonstrates 38% better privacy–utility tradeoffs in clinical settings, as evidenced by our experimental results in Section 5.
- Stronger Privacy Guarantees: (, ) compared to static differential privacy approaches (),
- Enhanced Compatibility: Supports five clinical model architectures simultaneously,
- Provable Security: Tamper-evident model sharing via blockchain-anchored hashes.
6. Conclusions
Notation
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| HIPAA | Health Insurance Portability and Accountability Act |
| HHS | Health and Human Services |
| DP | Differential Privacy |
| FL | Federated Learning |
| HFL | Heterogeneous Federated Learning |
| FD | Federated Distillation |
| dDP | Dynamic Differential Privacy |
| TEE | Trusted Execution Environment |
| MPC | Secure Multiparty Computation |
| CNN | Convolutional Neural Network |
| ViT | Vision Transformer |
| BLS | Boneh–Lynn–Shacham (signature scheme) |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| IPFS | InterPlanetary File System |
| IID | Independent and Identically Distributed |
References
- Zota, R.D.; Cîmpeanu, I.A.; Lungu, M.A. Exploring AI in Healthcare Systems: A Study of Medical Applications and a Proposal for a Smart Clinical Assistant. Electronics 2025, 14, 3727. [Google Scholar] [CrossRef]
- Hu, K.; Ma, D.; Qiu, S. SecureTeleMed: Privacy-Preserving Volumetric Video Streaming for Telemedicine. Electronics 2025, 14, 3371. [Google Scholar] [CrossRef]
- Wani, R.U.Z.; Can, O. FED-EHR: A Privacy-Preserving Federated Learning Framework for Decentralized Healthcare Analytics. Electronics 2025, 14, 3261. [Google Scholar] [CrossRef]
- HIPAA Journal. 2023 Healthcare Data Breach Report. 2023. Available online: https://www.hipaajournal.com/security-breaches-in-healthcare/ (accessed on 15 August 2025).
- Pokharel, B.P.; Kshetri, N.; Sharma, S.R.; Paudel, S. blockHealthSecure: Integrating Blockchain and Cybersecurity in Post-Pandemic Healthcare Systems. Information 2025, 16, 133. [Google Scholar] [CrossRef]
- Albanese, G.; Calbimonte, J.P.; Schumacher, M.I.; Calvaresi, D. Dynamic consent management for clinical trials via private blockchain technology. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 4909–4926. [Google Scholar] [CrossRef]
- Guduri, M.; Chakraborty, C.; Maheswari, U.; Margala, M. Blockchain-Based Federated Learning Technique for Privacy Preservation and Security of Smart Electronic Health Records. IEEE Trans. Consum. Electron. 2024, 70, 2608–2617. [Google Scholar] [CrossRef]
- Bawany, N.Z.; Qamar, T.; Tariq, H.; Adnan, S. Integrating Healthcare Services Using Blockchain-Based Telehealth Framework. IEEE Access 2022, 10, 36505–36517. [Google Scholar] [CrossRef]
- Alzu’bi, A.; Alomar, A.; Alkhaza’leh, S.; Abuarqoub, A.; Hammoudeh, M. A Review of Privacy and Security of Edge Computing in Smart Healthcare Systems: Issues, Challenges, and Research Directions. Tsinghua Sci. Technol. 2024, 29, 1152–1180. [Google Scholar] [CrossRef]
- Rezaei, H.; Golmaryami, M.; Rezaei, H.; Palmieri, F. A lightweight blockchain-based defense method for federated self-supervised learning. Future Gener. Comput. Syst. 2025, 175, 108092. [Google Scholar] [CrossRef]
- U.S. Congress. Health Insurance Portability and Accountability Act of 1996. Public Law 104-191, 1996. 45 CFR Parts 160, 162, and 164 (Security and Privacy Rules). Available online: https://www.cdc.gov/phlp/php/resources/health-insurance-portability-and-accountability-act-of-1996-hipaa.html (accessed on 9 August 2025).
- Tauqeer, A.; Fensel, A. GDPR Data Sharing Contract Management and Compliance Verification Tool. Softw. Impacts 2024, 21, 100653. [Google Scholar] [CrossRef]
- Myeong, G.E.; Ram, K.S. Blockchain Based Zero Knowledge Proof Protocol For Privacy Preserving Healthcare Data Sharing. J. Technol. Inform. Eng. 2025, 4, 171–189. [Google Scholar] [CrossRef]
- HIPAA Journal. 2024 Healthcare Data Breach Report. 2024. Available online: https://www.hipaajournal.com/2024-healthcare-data-breach-report/ (accessed on 29 July 2025).
- IBM Security. Cost of a Data Breach Report—Healthcare Industry Insights. 2024. Available online: https://www.ibm.com/think/insights/cost-of-a-data-breach-healthcare-industry (accessed on 16 August 2025).
- Guo, S.; Wang, X.; Long, S.; Liu, H.; Hai, L.; Sam, T.H. A federated learning scheme meets dynamic differential privacy. CAAI Trans. Intell. Technol. 2023, 8, 1087–1100. [Google Scholar] [CrossRef]
- He, Z.; Wang, L.; Cai, Z. Clustered Federated Learning with Adaptive Local Differential Privacy on Heterogeneous IoT Data. IEEE Internet Things J. 2024, 11, 137–146. [Google Scholar] [CrossRef]
- Chen, Q.; Ni, Z.; Zhu, X.; Lyu, M.; Liu, W.; Xia, P. Dynamic Edge-Based High-Dimensional Data Aggregation with Differential Privacy. Electronics 2024, 13, 3346. [Google Scholar] [CrossRef]
- Lin, X.; Wu, J.; Li, J.; Sang, C.; Hu, S.; Deen, M.J. Heterogeneous Differential-Private Federated Learning: Trading Privacy for Utility Truthfully. IEEE Trans. Dependable Secur. Comput. 2023, 20, 5113–5129. [Google Scholar] [CrossRef]
- Chen, L.; Zhang, W.; Dong, C.; Zhao, D.; Zeng, X.; Qiao, S.; Zhu, Y.; Tan, C.W. FedTKD: A Trustworthy Heterogeneous Federated Learning Based on Adaptive Knowledge Distillation. Entropy 2024, 26, 96. [Google Scholar] [CrossRef]
- Mishra, S.; Tandon, D. Federated Learning in Healthcare: A Path Towards Decentralized and Secure Medical Insights. Int. J. Sci. Res. Eng. Manag. 2024, 8, 1–15. [Google Scholar] [CrossRef]
- Li, Y.; Wang, X.; Li, H.; Donta, P.K.; Huang, M.; Dustdar, S. Communication-Efficient Federated Learning for Heterogeneous Clients. ACM Trans. Internet Technol. 2023, 25, 1–37. [Google Scholar] [CrossRef]
- Lee, W.T. DPEFed: A Decentralized Personalization and Ensemble-based Federated Learning Framework for Healthcare. In Proceedings of the 2025 10th International Conference on Intelligent Computing and Signal Processing (ICSP), Xi’an, China, 16–18 May 2025; pp. 1198–1204. [Google Scholar]
- Qu, Y.; Gao, L.; Luan, T.H.; Xiang, Y.; Yu, S.; Li, B.; Zheng, G. Decentralized Privacy Using Blockchain-Enabled Federated Learning in Fog Computing. IEEE Internet Things J. 2023, 7, 5171–5183. [Google Scholar] [CrossRef]
- Myrzashova, R.R.; Alsamhi, S.H.; Shvetsov, A.V.; Hawbani, A.; Wei, X. Blockchain Meets Federated Learning in Healthcare: A Systematic Review with Challenges and Opportunities. IEEE Internet Things J. 2023, 10, 14418–14437. [Google Scholar] [CrossRef]
- Zhou, X.; Huang, W.; Liang, W.; Yan, Z.; Ma, J.; Pan, Y.; Wang, K.I.K. Federated distillation and blockchain empowered secure knowledge sharing for Internet of medical Things. Inf. Sci. 2024, 662, 120217. [Google Scholar] [CrossRef]
- U.S. Department of Health and Human Services, Office for Civil Rights (OCR). Change Healthcare Cybersecurity Incident Frequently Asked Questions. May 2024. Available online: https://www.hhs.gov/hipaa/for-professionals/special-topics/change-healthcare-cybersecurity-incident-frequently-asked-questions/index.html (accessed on 16 August 2025).
- Zhu, L.; Liu, Z.; Han, S. Deep Leakage from Gradients. In Proceedings of the Advances in Neural Information Processing Systems, Vancouver, BC, Canada, 8–14 December 2019; Volume 32. [Google Scholar]
- Bonneau, J.; Miller, A.K.; Clark, J.; Narayanan, A.; Kroll, J.A.; Felten, E.W. SoK: Research Perspectives and Challenges for Bitcoin and Cryptocurrencies. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 17–21 May 2015; pp. 104–121. [Google Scholar]
- Nakamoto, S. A peer-to-peer electronic cash system. Bitcoin 2008, 4, 15. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 18 August 2025).
- Ben-Sasson, E.; Chiesa, A.; Tromer, E.; Virza, M. Succinct Non-Interactive Zero Knowledge for a von Neumann Architecture. In Proceedings of the 2014 23rd USENIX Security Symposium, San Diego, CA, USA, 20–22 August 2014. [Google Scholar]
- Dym, C. Principles of Mathematical Modeling; Elsevier: Amsterdam, The Netherlands, 2004. [Google Scholar]
- Dwork, C.; Roth, A. The Algorithmic Foundations of Differential Privacy. Found. Trends Theor. Comput. Sci. 2014, 9, 211–407. [Google Scholar] [CrossRef]
- Abadi, M.; Chu, A.; Goodfellow, I.J.; McMahan, H.B.; Mironov, I.; Talwar, K.; Zhang, L. Deep Learning with Differential Privacy. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 26–28 October 2016. [Google Scholar]
- Hardy, G.H.; Littlewood, J.E.; Pólya, G. Inequalities; Cambridge University Press: Cambridge, UK, 1952. [Google Scholar]
- Geman, S.; Bienenstock, E.; Doursat, R. Neural networks and the bias/variance dilemma. Neural Comput. 1992, 4, 1–58. [Google Scholar] [CrossRef]
- Jensen, J.L.W.V. Sur les fonctions convexes et les inégalités entre les valeurs moyennes. Acta Math. 1906, 30, 175–193. [Google Scholar] [CrossRef]
- Vapnik, V. The Nature of Statistical Learning Theory; Springer Science & Business Media: New York, NY, USA, 2013. [Google Scholar]
- Hoeffding, W. Probability inequalities for sums of bounded random variables. J. Am. Stat. Assoc. 1963, 58, 13–30. [Google Scholar] [CrossRef]
- Zhou, Z.H. Ensemble Methods: Foundations and Algorithms; CRC Press: Boca Raton, FL, USA, 2025. [Google Scholar]
- Van der Vaart, A.W. Asymptotic Statistics; Cambridge University Press: Cambridge, UK, 2000; Volume 3. [Google Scholar]
- Krogh, A.; Vedelsby, J. Neural network ensembles, cross validation, and active learning. Adv. Neural Inf. Process. Syst. 1994, 7, 231–238. [Google Scholar]
- Boole, G. The Mathematical Analysis of Logic; CreateSpace Independent Publishing Platform: Scotts Valley, CA, USA, 1847. [Google Scholar]
- Papaspiliopoulos, O. High-Dimensional Probability: An Introduction with Applications in Data Science. Quant. Financ. 2020, 20, 1591–1594. [Google Scholar] [CrossRef]
- Zhang, G.; Lu, R.; Wu, W. Multi-resource fair allocation for cloud federation. In Proceedings of the 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Zhangjiajie, China, 10–12 August 2019; pp. 2189–2194. [Google Scholar]
- Kairouz, P.; McMahan, H.B.; Avent, B. Advances and Open Problems in Federated Learning. Found. Trends Mach. Learn. 2019, 14, 1–210. [Google Scholar] [CrossRef]
- Humphrey, H.H. Standards for privacy of individually identifiable health information. Health Care Law Mon. 2003, 13–20. Available online: https://aspe.hhs.gov/standards-privacy-individually-identifiable-health-information (accessed on 16 September 2025).
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. MedRec: Using Blockchain for Medical Data Access and Permission Management. In Proceedings of the 2016 2nd International Conference on Open and Big Data (OBD), Vienna, Austria, 22–24 August 2016; pp. 25–30. [Google Scholar]
- Kairouz, P.; Oh, S.; Viswanath, P. The Composition Theorem for Differential Privacy. IEEE Trans. Inf. Theory 2013, 63, 4037–4049. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Cover, T.M.; Thomas, J.A. Elements of Information Theory; John Wiley & Sons: Hoboken, NJ, USA, 2005. [Google Scholar]
- Alzubi, J.A.A.; Alzubi, O.A.; Chen, T.M. Forward Error Correction Based on Algebraic-Geometric Theory; Springer International Publishing: Cham, Switzerland, 2014. [Google Scholar]
- Guruswami, V.; Sudan, M. Improved decoding of Reed-Solomon and algebraic-geometry codes. IEEE Trans. Inf. Theory 1999, 45, 1757–1767. [Google Scholar] [CrossRef]
- Johnson, D.B.; Menezes, A.; Vanstone, S.A. The Elliptic Curve Digital Signature Algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Oded, G. Foundations of Cryptography: Volume 2, Basic Applications; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Rogaway, P.; Shrimpton, T. Cryptographic Hash-Function Basics: Definitions, Implications, and Separations for Preimage Resistance, Second-Preimage Resistance, and Collision Resistance. IACR Cryptol. ePrint Arch. 2004, 2004, 35. [Google Scholar]
- Garay, J.A.; Kiayias, A.; Leonardos, N. The Bitcoin Backbone Protocol: Analysis and Applications. J. ACM 2015, 71, 1–49. [Google Scholar] [CrossRef]
- Shannon, C.E. A mathematical theory of communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Mironov, I. Rényi Differential Privacy. In Proceedings of the 2017 IEEE 30th Computer Security Foundations Symposium (CSF), Santa Barbara, CA, USA, 21–25 August 2017; pp. 263–275. [Google Scholar]
- Kabir, M.S.; Alam, M.N.; Mustofa, M.J. Information Privacy Analysis: The USA Perspective. Int. J. Res. Appl. Sci. Eng. Technol. 2023, 11, 116–126. [Google Scholar] [CrossRef]
- McMahan, H.B.; Moore, E.; Ramage, D.; Hampson, S.; Arcas, B.A. Communication-Efficient Learning of Deep Networks from Decentralized Data. In Proceedings of the 20th International Conference on Artificial Intelligence and Statistics, Cadiz, Spain, 9–11 May 2016. [Google Scholar]
- Kullback, S.; Leibler, R.A. On Information and Sufficiency. Ann. Math. Stat. 1951, 22, 79–86. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Rajkomar, A.; Oren, E.; Chen, K.; Dai, A.M.; Hajaj, N. Scalable and accurate deep learning with electronic health records. NPJ Digit. Med. 2018, 1, 18. [Google Scholar] [CrossRef]
- Taheri, R.; Arabikhan, F.; Gegov, A.; Akbari, N. Robust aggregation function in federated learning. In Proceedings of the International Conference on Information and Knowledge Systems; Springer: Cham, Switzerland, 2023; pp. 168–175. [Google Scholar]
- Pillutla, K.; Kakade, S.M.; Harchaoui, Z. Robust aggregation for federated learning. IEEE Trans. Signal Process. 2022, 70, 1142–1154. [Google Scholar] [CrossRef]
- Blanchard, P.; El Mhamdi, E.M.; Guerraoui, R.; Stainer, J. Machine learning with adversaries: Byzantine tolerant gradient descent. Adv. Neural Inf. Process. Syst. 2017, 30, 118–128. [Google Scholar]
- Khanh, Q.V.; Chehri, A.; Dang, V.A.; Minh, Q.N. Federated Learning Approach for Collaborative and Secure Smart Healthcare Applications. IEEE Trans. Emerg. Top. Comput. 2025, 13, 68–79. [Google Scholar] [CrossRef]
- Kim, D.; Doh, I.; Chae, K. Improved Raft Algorithm exploiting Federated Learning for Private Blockchain performance enhancement. In Proceedings of the 2021 International Conference on Information Networking (ICOIN), Jeju Island, Republic of Korea, 13–16 January 2021; pp. 828–832. [Google Scholar]
- Kanagasankari, S.; Vallinayagi, V. Comparative analysis of consensus algorithms in the health care sector using block chain technology. Int. J. Health Sci. 2022, 6, 11702–11716. [Google Scholar] [CrossRef]
- Kuo, T.T.; Pham, A. Quorum-based model learning on a blockchain hierarchical clinical research network using smart contracts. Int. J. Med. Inform. 2022, 169, 104924. [Google Scholar] [CrossRef] [PubMed]
- National Institute of Standards and Technology (NIST). Security–Health Information Technology. 2016. Available online: https://www.nist.gov/programs-projects/security-health-information-technology (accessed on 16 August 2025).
- Brown, D.R. The Exact Security of ECDSA. Available online: https://www.researchgate.net/publication/2438763_The_Exact_Security_of_ECDSA (accessed on 11 September 2025).
- Pointcheval, D.; Stern, J. Security Arguments for Digital Signatures and Blind Signatures. J. Cryptol. 2015, 13, 361–396. [Google Scholar] [CrossRef]
- Blake, I.F.; Seroussi, G.; Smart, N.P. Elliptic Curves in Cryptography; Cambridge University Press: Cambridge, UK, 1999. [Google Scholar]
- Galbraith, S.D.; Gaudry, P. Recent progress on the elliptic curve discrete logarithm problem. Des. Codes Cryptogr. 2015, 78, 51–72. [Google Scholar] [CrossRef]
- Strömbergson, J. Implementation of the Keccak Hash Function in FPGA Devices. 2008. Available online: https://api.semanticscholar.org/CorpusID:14824730 (accessed on 21 August 2025).
- Ongaro, D.; Ousterhout, J.K. In Search of an Understandable Consensus Algorithm. In Proceedings of the USENIX Annual Technical Conference, Philadelphia, PA, USA, 17–20 June 2014. [Google Scholar]
- Howard, H.; Mortier, R. Paxos vs. Raft: Have we reached consensus on distributed consensus? In Proceedings of the 7th Workshop on Principles and Practice of Consistency for Distributed Data, Heraklion, Greece, 27 April 2020. [Google Scholar]
- Kaufmann, M.B.; San, M.; Schaffer, C.A.; Caruana, R.; Eschelman, L.J.; Das, R. A Massively Distributed Parallel Genetic Algorithm (mdpGA); Carnegie Mellon University: Pittsburgh, PA, USA, 1992. [Google Scholar]
- Ross, S.M. A First Course in Probability; Prentice Hall: Upper Saddle River, NJ, USA, 1977. [Google Scholar]
- Bernstein, D.J. Introduction to Post-Quantum Cryptography. In Post-Quantum Cryptography; Springer: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Xia, Q.; Sifah, E.B.; Smahi, A.; Amofa, S.; Zhang, X. BBDS: Blockchain-Based Data Sharing for Electronic Medical Records in Cloud Environments. Information 2017, 8, 44. [Google Scholar] [CrossRef]
- Zhang, P.; White, J.; Schmidt, D.C.; Lenz, G.; Rosenbloom, S.T. FHIRChain: Applying Blockchain to Securely and Scalably Share Clinical Data. Comput. Struct. Biotechnol. J. 2018, 16, 267–278. [Google Scholar] [CrossRef] [PubMed]
- Boneh, D.; Shoup, V. A Graduate Course in Applied Cryptography. 2017. Available online: https://www.e-booksdirectory.com/details.php?ebook=12196 (accessed on 10 July 2025).
- Chen, L.; Lee, W.K.; Chang, C.; Choo, K.K.R.; Zhang, N. Blockchain based searchable encryption for electronic health record sharing. Future Gener. Comput. Syst. 2019, 95, 420–429. [Google Scholar] [CrossRef]
- Zhang, A.; Lin, X. Towards Secure and Privacy-Preserving Data Sharing in e-Health Systems via Consortium Blockchain. J. Med. Syst. 2018, 42, 140. [Google Scholar] [CrossRef] [PubMed]
- Fan, R.E.; Chang, K.W.; Hsieh, C.J.; Wang, X.R.; Lin, C.J. LIBLINEAR: A Library for Large Linear Classification. J. Mach. Learn. Res. 2008, 9, 1871–1874. [Google Scholar]
- Saha, S.; Ahmad, T. Federated transfer learning: Concept and applications. Intell. Artif. 2020, 15, 35–44. [Google Scholar] [CrossRef]
- Pedregosa, F.; Varoquaux, G.; Gramfort, A.; Michel, V.; Thirion, B.; Grisel, O.; Blondel, M.; Louppe, G.; Prettenhofer, P.; Weiss, R.; et al. Scikit-learn: Machine Learning in Python. J. Mach. Learn. Res. 2011, 12, 2825–2830. [Google Scholar]
- Li, J.; Zhang, Y.; Li, Y.; Gong, X.; Wang, W. Gradient Calibration for Non-I.I.D. Federated Learning. In Proceedings of the 2nd ACM Workshop on Data Privacy and Federated Learning Technologies for Mobile Edge Network, Madrid, Spain, 6 October 2023. [Google Scholar]
- Kinga, D.; Adam, J.B. A method for stochastic optimization. In Proceedings of the International Conference on Learning Representations (ICLR), San Diego, CA, USA, 7–9 May 2015; Volume 5. Number 6. [Google Scholar]
- Pollard, T.J.; Johnson, A.E.W.; Raffa, J.D.; Celi, L.A.; Mark, R.G.; Badawi, O. The eICU Collaborative Research Database, a freely available multi-center database for critical care research. Sci. Data 2018, 5, 180178. [Google Scholar] [CrossRef]
- Roy, S.; Bera, D. A blockchain-based Verifiable Aggregation for Federated Learning and Secure Sharing in Healthcare. In Proceedings of the 2023 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Jaipur, India, 17–20 December 2023; pp. 165–170. [Google Scholar]
- U.S. Department of Health and Human Services. Security Rule: 45 CFR Part 164 Subpart C. Federal Register Vol. 68, No. 34, 2003. Specifically §164.312(b) for Audit Controls. Available online: https://www.ecfr.gov/current/title-45/subtitle-A/subchapter-C/part-164/subpart-C (accessed on 28 July 2025).
| Metric | Hospital | Consortium |
|---|---|---|
| Throughput | ||
| Latency | ||
| Storage |
| Criterion | FedAvg | FD |
|---|---|---|
| Model Requirements | Identical architectures | Any compatible models |
| Privacy Risk | High (weight leakage) | Moderate (logit leakage) |
| Comm. Cost | (full weights) | (logits only) |
| Non-IID Robustness | Limited | Excellent |
| Metric | Standard DP | dDP |
|---|---|---|
| Privacy Fairness | Uniform | Adaptive |
| Utility Variance | High | Reduced |
| Small-Data Protection | None | Enhanced |
| Clinical Compliance | Limited | HIPAA-ready |
| Hospital | Model Type | Implementation | Hyperparameters | Memory (MB) | FL Characteristics | Privacy Parameters |
|---|---|---|---|---|---|---|
| H1 | Logistic Regression | scikit-learn 1.2.2 | 2.1 | |||
| H2 | Random Forest | scikit-learn 1.2.2 | 18.7 | |||
| H3 | Neural Network | PyTorch 2.0.1 | 4.3 |
| Dataset | Source | Dimensions | Class Distribution | Preprocessing Pipeline | Privacy Considerations |
|---|---|---|---|---|---|
| Mortality Prediction | eICU-CRD | Samples: 4358 Features: 21 (16 num., 5 cat.) Missing: 8.3% | Positive: 828 (19.0%) Negative: 3530 (81.0%) Skew: 1:4.26 | • Imputation: MICE • Encoding: Label Encoding • Scaling: StandardScaler • Temporal: 24 h aggregation • Test Split: 20% | : 4.8 : 1.0 : 0.7 PHI: Full de-id Sensitivity: High |
| Clinical Deterioration | eICU-CRD | Samples: 2365 Features: 18 (all numerical) Outliers: 6.2% | Deterioration: 570 (24.1%) Stable: 1795 (75.9%) Skew: 1:3.15 | • Outlier: Winsorization • Normalization: RobustScaler • Trend: Linear regression slopes • Variability: Std. deviation • Test Split: 25% | : 3.5 : 0.4 PHI: Temporal patterns De-id: HIPAA SafeHarbor |
| Dataset | Configuration | Model | Accuracy | Precision | Recall | -Effective | Latency (ms) |
|---|---|---|---|---|---|---|---|
| Mortality Prediction | Accumulated | LR | 54.76% ± 1.2 | 0.57 ± 0.02 | 0.60 ± 0.02 | N/A | 40 ± 0.10 |
| RF | 84.39% ± 1.3 | 0.87 ± 0.03 | 0.84 ± 0.01 | N/A | 178 ± 27.9 | ||
| NN | 67.39% ± 0.7 | 0.66 ± 0.01 | 0.80 ± 0.02 | N/A | 1 ± 1.10 | ||
| FD | LR | 46.38% ± 0.0 | 0.85 ± 0.01 | 0.00 ± 0.02 | ∞ | 215 ± 40.0 | |
| RF | 83.35% ± 0.0 | 0.85 ± 0.06 | 0.84 ± 0.04 | ∞ | 125 ± 41.8 | ||
| NN | 46.38% ± 0.0 | 0.93 ± 0.03 | 0.93 ± 0.02 | ∞ | 108 ± 25.6 | ||
| FD-DP () | LR | 54.57% ± 0.1 | 0.57 ± 0.001 | 0.60 ± 0.001 | 0.59 ± 0.05 | 0.57 ± 0.06 | |
| RF | 83.31% ± 0.6 | 0.85 ± 0.007 | 0.84 ± 0.004 | 0.84 ± 0.04 | 141 ± 1.90 | ||
| NN | 61.39% ± 0.4 | 0.60 ± 0.004 | 0.87 ± 0.016 | 0.71 ± 0.04 | 209 ± 17.1 | ||
| Clinical Deterioration | Accumulated | LR | 86.05% ± 0.6 | 0.97 ± 0.02 | 0.85 ± 0.03 | N/A | 18 ± 7.50 |
| RF | 97.04% ± 0.5 | 0.97 ± 0.03 | 0.97 ± 0.02 | N/A | 103 ± 15.9 | ||
| NN | 89.01% ± 0.2 | 0.96 ± 0.01 | 0.90 ± 0.02 | N/A | 14 ± 1.50 | ||
| FD | LR | 85.62% ± 0.0 | 0.98 ± 0.03 | 0.84 ± 0.02 | ∞ | 141 ± 24.8 | |
| RF | 97.04% ± 0.0 | 0.97 ± 0.08 | 0.97 ± 0.03 | ∞ | 248 ± 37.6 | ||
| NN | 92.81% ± 0.0 | 0.96 ± 0.20 | 0.95 ± 0.01 | ∞ | 141 ± 12.6 | ||
| FD-DP () | LR | 82.95% ± 0.3 | 0.98 ± 0.004 | 0.81 ± 0.006 | 0.88 ± 0.04 | 0.31 ± 0.03 | |
| RF | 96.90% ± 0.3 | 0.97 ± 0.002 | 1.00 ± 0.001 | 0.98 ± 0.03 | 111 ± 8.30 | ||
| NN | 89.36% ± 0.3 | 0.93 ± 0.001 | 0.94 ± 0.002 | 0.94 ± 0.04 | 154 ± 9.30 |
| Dataset | Model | FD (ms) | FD–dDP (ms) | Saving (%) |
|---|---|---|---|---|
| Mortality | LR | 215 | 0.80 | 99.6 |
| Mortality | RF | 125 | 70 | 44.0 |
| Mortality | NN | 108 | 120 | −11.1 |
| Clinical | LR | 141 | 0.50 | 99.6 |
| Clinical | RF | 248 | 110 | 55.6 |
| Clinical | NN | 141 | 160 | −13.5 |
| Metric | Gradient Sharing | Model Sharing |
|---|---|---|
| Average Tx Size | 15.2 KB | 4.3 MB |
| Storage Overhead | ||
| Compression Ratio | 85% | 45% |
| Verification Time | 12 ms | 156 ms |
| Throughput | 320 Tx/s | 45 Tx/s |
| Component | Mean Latency (ms) | Description |
|---|---|---|
| DP Noise Generation and Serialization | 120–180 | Local preprocessing of logits/models |
| Signature and ZK Verification | 220–320 | ECDSA, Kyber, and ZK-proof checks |
| Raft Transaction Submission | 90–140 | Asynchronous commit (not finality) |
| Cross-Chain Aggregation | 180–260 | Multi-node aggregation and decryption |
| Total End-to-End Latency | 710–880 | Matches Figure 10 measurements |
| Hospital | Dataset | Stage | Bytes Sent | Notes |
|---|---|---|---|---|
| H1 | Mortality | FD model upload | 32 | LR model |
| H1 | Clinical | FD model upload | 28 | LR model |
| H2 | Mortality | FD model upload | 0 | RF model |
| H2 | Clinical | FD model upload | 0 | RF model |
| H3 | Mortality | FD model upload | 37,380 | NN model |
| H3 | Clinical | FD model upload | 36,868 | NN model |
| H1 | Mortality | FD–dDP logits | 1120 | Logits for |
| H1 | Clinical | FD–dDP logits | 1120 | – |
| H2 | Mortality | FD–dDP logits | 1120 | – |
| H2 | Clinical | FD–dDP logits | 1120 | – |
| H3 | Mortality | FD–dDP logits | 1120 | – |
| H3 | Clinical | FD–dDP logits | 1120 | – |
| Framework | FL Model | Privacy | DP Usage | Blockchain | FL Algorithm | Collaborative Mechanism | Threat Protection |
|---|---|---|---|---|---|---|---|
| Guo et al. (2023) [16] | Homogeneous | ✓ | Adaptive | ✗ | FedAvg | Centralized aggregation | ✗ |
| Chen et al. (2024) [20] | Heterogeneous | ✓ | ✗ | ✗ | FD | Knowledge distillation | ✗ |
| Youyang et al. (2023) [24] | Homogeneous | ✓ | ✗ | ✓ | FedAvg | Threshold signatures | ✗ |
| Zaobo et al. (2022) [17] | Heterogeneous | ✓ | Adaptive | ✗ | FedAvg | TEE-secured aggregation | ✓ |
| Snehlata and Ritu (2023) [21] | Heterogeneous | ✓ | ✗ | ✗ | FD | SMPC + Distillation | ✗ |
| Qian et al. (2024) [18] | Homogeneous | ✓ | Static | ✗ | FedAvg | Centralized aggregation | ✗ |
| Raushan et al. (2023) [25] | Homogeneous | ✗ | ✗ | ✓ | FedAvg | Blockchain verification | ✓ |
| Ying et al. (2023) [22] | Heterogeneous | ✗ | ✗ | ✗ | FD | Knowledge distillation | ✗ |
| Zhipeng et al. (2024) [94] | Homogeneous | ✓ | ✗ | ✗ | FedAvg | Verifiable secret sharing | ✗ |
| Lee et al. (2023) [23] | Heterogeneous | ✗ | ✗ | ✗ | Ensemble FL | Attention-based gating | ✗ |
| Sang et al. (2024) [19] | Heterogeneous | ✓ | Static | ✗ | FedAvg | Centralized aggregation | ✓ |
| Xiaokang et al. (2022) [26] | Heterogeneous | ✓ | Static | ✓ | FD | Blockchain verification | ✗ |
| Mishra et al. (2024) [21] | Homogeneous | ✓ | ✗ | ✓ | FedAvg | Secret sharing | ✓ |
| Roth et al. (2023) [17] | Heterogeneous | ✓ | Adaptive | ✗ | FD | Knowledge distillation | ✗ |
| Rezaei et al. (2026) [10] | Homogeneous | ✓ | ✗ | ✓ | FedSSL | Blockchain verification | ✓ |
| Proposed Model | Heterogeneous | ✓ | Adaptive | ✓ | FD | Knowledge distillation | ✓ |
| Symbol | Description | Symbol | Description |
|---|---|---|---|
| Set of hospitals | Hospital i | ||
| Private dataset of hospital i | Input feature and label | ||
| Edge server | Local model at hospital i | ||
| Model parameters | Policy of hospital i | ||
| Total hospitals/models | Public dataset | ||
| Differential privacy budget | Personalized DP budget | ||
| Total privacy budget | Composed DP budget | ||
| Dataset sizes | Scaling factor | ||
| Gradient sensitivity | Function sensitivity | ||
| Architecture divergence | DP noise scales | ||
| Minimum singular value | Lipschitz constant | ||
| R | Radius bound | Average logits | |
| Detection probability | Mutual information | ||
| Public/private keys | t | Threshold value | |
| Participants set | Security parameter | ||
| Set of corrupted nodes | Consensus threshold | ||
| Hospital blockchain | Consortium blockchain | ||
| Weight of client i | d | Dimension | |
| Adjacent datasets | Privacy mechanism | ||
| Loss function/Laplace distribution | ∇ | Gradient operator | |
| Euclidean norm | Finite field | ||
| ⋈ | Join operation | ⊗ | Tensor product |
| ⊕ | XOR operator | [·] | Encrypted value |
| Probability | Gaussian distribution |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Javed, M.S.; Hennache, A.; Imran, M.; Khan, M.K. AI-Driven Blockchain and Federated Learning for Secure Electronic Health Records Sharing. Electronics 2025, 14, 4774. https://doi.org/10.3390/electronics14234774
Javed MS, Hennache A, Imran M, Khan MK. AI-Driven Blockchain and Federated Learning for Secure Electronic Health Records Sharing. Electronics. 2025; 14(23):4774. https://doi.org/10.3390/electronics14234774
Chicago/Turabian StyleJaved, Muhammad Saeed, Ali Hennache, Muhammad Imran, and Muhammad Kamran Khan. 2025. "AI-Driven Blockchain and Federated Learning for Secure Electronic Health Records Sharing" Electronics 14, no. 23: 4774. https://doi.org/10.3390/electronics14234774
APA StyleJaved, M. S., Hennache, A., Imran, M., & Khan, M. K. (2025). AI-Driven Blockchain and Federated Learning for Secure Electronic Health Records Sharing. Electronics, 14(23), 4774. https://doi.org/10.3390/electronics14234774






