1. Introduction
The Internet of Things (IoT) has emerged rapidly, also giving rise to the Internet of Medical Things (IoMT), which is an extension of IoT for the medical community. In recent years, an increasing number of daily operational processes have turned to IoT devices to automate and collect data for decision-making processes. Recent studies [
1] expect the IoT landscape globally to exceed 40 billion connected devices by the end of 2034, with approximately 40% of those belonging to IoMT devices. The global Internet of Medical Things (IoMT) market is expected to reach approximately USD 852.88 billion by 2030, and its widespread adoption is projected to generate up to USD 500 billion in cost savings for the healthcare sector [
2].
The Internet of Medical Things (IoMT) is a complex interconnected “ecosystem” comprising medical sensors, diagnostic devices, clinical information systems, and wearable health monitors. This digital health system enables a wide variety of smart health services, such as remote patient monitoring, smart hospitals, Ambient Assisted Living (AAL), fitness tracking, and elderly care, to facilitate improvements in diagnostic precision and timely intervention and minimize operational costs [
3]. Despite these benefits, these advantages must be weighed against the greater challenge in addressing and maintaining the security and privacy of IoMT systems [
4].
Due to the sensitive nature of medical data, strong protection mechanisms are required throughout the complete data life cycle, including acquisition, transmission, processing, and storage of data. The Research and Global Threat Report shows that approximately 50% of IoMT devices deployed have serious security vulnerabilities [
5,
6,
7]. IoMT infrastructures are different from conventional networks because they have a direct impact on patient safety and well-being. Thus, a breach of data confidentiality or integrity could result in ethical and clinical ramifications. Healthcare record data is believed to be 50 times more valuable than financial data on the dark web [
8]. Thus, it is a valuable target for attackers.
Though IoMT-based connected devices offer significant development, they also contribute to newly discovered risks by being connected to public networks and managing life-critical information [
9]. Cyber attacks on IoMT systems can produce horrific outcomes that can result in physical harm and even lead to death. For example, compromising a connected insulin pump or pacemaker could endanger a patient by administering a fatal overdose via an unauthorized user. Many studies have shown there are risks of various cyber attacks and threats against IoMT systems, including false data injection, Denial of Service (doS), and eavesdropping. These advanced persistent threats (APTs) pose threats to patient privacy and clinical safety, threaten the availability of systems, and can be a precursor to failure of healthcare infrastructure [
10,
11,
12,
13].
Addressing such challenges requires deploying strong, intelligent security mechanisms that sustain the core principles of information assurance, namely, authentication, integrity, non-repudiation, and data confidentiality, as well as availability [
14]. Although classical security mechanisms (e.g., cryptographic protocols, access control schemes) provide essential protection of information, they lack the rigor necessary for use in resource-limited IoMT environments. These contexts are often particularly characterized by devices that furnish limited computational power, limited energy resources, and limited options for integrated security modules, thus limiting the scalability of classical security mechanisms [
15]. Moreover, most commercial and open-source medical devices were never designed with embedded security as a fundamental aspect of their design. Consequently, researchers have only looked at trust management, authentication schemes, and lightweight encryption schemes to promote resilience in wearable and implantable devices.
Despite these initiatives, the currently available security mechanisms are still computationally heavy with limited support for real-time intrusion detection in low-power medical IoT nodes [
16]. Additionally, a large proportion of the literature cited addresses isolated issues and does not contribute toward a unified, scalable defense. Yaacoub et al. [
17] developed a classification of IoMT security strategies that cover a variety of dimensions, including intrusion detection, awareness, availability, and authorization, that also utilizes cryptographic techniques as well as non-cryptographic techniques in Wireless Body Area Networks (WBANs) and IoMT models.
In a related investigation, the researchers determined that the IoMT security landscape presented multiple recurrent challenges, including a single point of failure, limited adaptability of the systems, and a lack of protocols for emergency scenarios [
18]. In cognizance of this, the authors [
19] presented cloud-based protective mechanisms that are intended to ensure medical data collected through wearable devices is secured. While these protective mechanisms utilize nonlocal cloud-based computation and protection components, they may incur latencies associated with the offloading of data from the cloud, and they do pose privacy risks.
Recent advances in physical layer (PL) security have emerged as potential complements to conventional cryptographic solutions by utilizing the inherent properties of wireless communication channels to improve both security and robustness within the context of networked communication systems [
20,
21,
22,
23]. These methods leverage physical characteristics rooted in the Signal-to-Noise Ratio (SNR), propagation randomness, and Channel State Information (CSI) to enable secure communication without the need for recursive encryption schemes. However, the practical realization of signal-perturbation-based security for IoMT applications, in light of the aforementioned assumptions concerning weak-type adversaries and the wholly time-varying nature of wireless channels, will have to undergo some transformation before being deployable for widespread implementation in real-world scenarios.
To mitigate these challenges, more recent studies have begun to use Machine Learning (ML)-based security frameworks in Smart Healthcare Systems (SHSs) to defend against more advanced cyber attacks. ML-based models possess a learning capability that is dynamic in nature and can improve by learning new attack signatures. These models have been shown to significantly improve network resilience by mitigating attacks like Denial of Service (DoS) and single-point failures while decreasing physical layer authentication errors by 64% compared to previous methods [
24].
The current study is positioned within the context of an attempt to incorporate Internet of Things/Internet of Medical Things (IoT/IoMT) infrastructures into a federated learning (FL) paradigm, allowing for decentralized, privacy-preserving collaborative learning approaches for intrusion detection. The main purpose is to allow secure and intelligent monitoring of medical data while keeping patient-sensitive information at the point of care and confidential. To achieve this purpose, we propose a novel security framework, PriFed-IDS, which is a privacy-preserving, FL-enabled intrusion detection system (IDS), to be used in a distributed IoMT environment. To the best of our knowledge, this is the first framework in the healthcare discipline to combine federated learning and reinforcement learning (RL) in order to autonomously detect and learn complicated latent patterns in medical data that signify cyber attacks. The motivating factor for the PriFed-IDS framework is to provide a secure, adaptive, and scalable cybersecurity solution that can respond to the fundamental issues surrounding data privacy, computational efficacy, and communication constraints that must be addressed for IoMT deployments. The PriFed-IDS framework allows for multiple Sharp Health Systems (SHS) nodes to independently develop and train local IDS models, in situ, without transmitting raw data to a data repository, which preserves patient privacy and complies with health data protection. Within the PriFed-IDS framework, a dynamic fusion and aggregation approach is used at the central server to aggregate updates for only certain high-performing local models to update the global model. The updating of the global model not only optimizes the accuracy of the global model but also reduces communication costs. Additionally, a reinforcement learning agent is used to evaluate client contributions and system states to update the client participation policies dynamically and to efficiently allocate resources to improve convergence.
This research makes the following contributions:
Development of a cooperative and distributed IDS framework specific to intrusion detection in Internet of Medical Things (IoMT) networks. The system is proven capable and reliable in identifying different types of cyber attacks, including DDoS, password brute-force, backdoor, injection, and scanning attacks, consequently strengthening the resilience of the SHSs.
The design of tailored intrusion detection models that carry out computing and anomaly detection on the edge devices of each SHS to reduce data transfer and improve data privacy by design.
The incorporation of reinforcement learning for intelligent detection, allowing the model to capture latent patterns and interdependencies in healthcare multivariate time-series, leading to better classification of advanced persistent threats (APTs) and zero-day attacks.
The establishment of a dynamic fusion/aggregation policy, which only uses certain selected local models based on accuracy and speed, leads to reduced communication demands and improved convergence times across rounds within the training process.
Empirical results using real-world datasets, including ToN-IoT and UCI heart disease empirical data, illustrate that the proposed PriFed-IDS model surpasses the performance of the best-in-class method in detection accuracy, robustness, and communication efficiency.
The structure of the article is as follows:
Section 2 and
Section 3 present a literature review and a detailed overview of IoMT security, federated learning, and reinforcement learning-based IDS architectures, respectively.
Section 4 proposes a methodology, including the architectural design, mathematical formulation, and training pipeline of the PriFed-IDS framework.
Section 5 reviews the experimental setup and reports the quantitative results alongside a comparative analysis. Lastly,
Section 6 summarizes this paper with the key findings and future research directions.
3. Overview of the Proposed FL-Based IDS Architecture
The Internet of Medical Things (IoMT) is a revolutionary healthcare development that allows medical devices, wearable devices, and cloud-based solutions to work together for real-time monitoring and patient diagnosis. However, this type of connected framework has high-level security risks because there is usually a lot of sensitive patient information transmitted through IoMT networks, especially Electronic Health Records (EHRs) and real-time vital signs. The heterogeneous security is complicated because IoMT devices are wide-ranging from implantable to hospital-grade, have different communication standards, resource limitations, and exposure to advanced cyber threats, such as data spoofing the device, interception, and Denial of Service (DoS).
In order to overcome these issues, IDSs play an important role in detecting and stopping malicious acts associated with IoMT settings. Conventional IDS methods that use predetermined signatures or statistical anomaly detection are ineffective in defending IoMT networks, as they are not flexible in terms of changing real-time attack vectors. Deep Neural Networks (DNNs), on the other hand, provide a reliable option as they are capable of learning complex patterns in network traffic data of high dimensions on their own. Since DNNs can identify zero-day attacks, as well as more subtle anomalies, in an unformulated way, this characteristic of theirs makes them especially well-suited to the intricate and adaptive nature of IoMT security threats.
When applied in IoMT intrusion detection, DNNs apply multiple architectures, e.g., Convolutional Neural Networks (CNNs), to extract spatial features and Recurrent Neural Networks (RNNs) or Long Short-Term Memory (LSTM) networks to model the temporal nature of traffic. These models can work within edge device computational constraints and be effective at processing both multimodal IoMT data, such as encrypted communications and irregular devices, and at working with mixed-modality data. This study will contribute to the aspect of making healthcare systems more secure against new cyber threats by implementing DNN-based IDS functionality into IoMT architecture, with a focus on a low level of latency and high scalability of the designed solution to facilitate its future deployment in a real-world environment.
4. Proposed Methodology
4.1. Overview
The IoMT and SHSs can be defined as an extremely interconnected ecosystem made up of an extensive range of medical sensors, diagnostic devices, wearable gadgets, and clinical management tools. Due to the nature of this infrastructure, which necessitates complexity, and the fact that this is critical infrastructure, such networks are extremely susceptible to a wide range of cyber attacks. In turn, it is crucial to apply a precise, scalable, and robust IDS to curb emerging security risks in real-time.
To address this challenge, this study proposes a unique intrusion detection system called PriFed-IDS, which specializes in protecting the IoT security and protection of IoMTs. The advanced model makes use of components of FL together with reinforcement learning (RL) to properly detect malicious behaviors among healthcare nodes that are distributed. It conducts this by using smart aggregation and fusion of gray-box models, which are trained locally by different nodes of SHS, into a global model residing at the central server, thereby realizing collaborative learning without risking sensitive patient data.
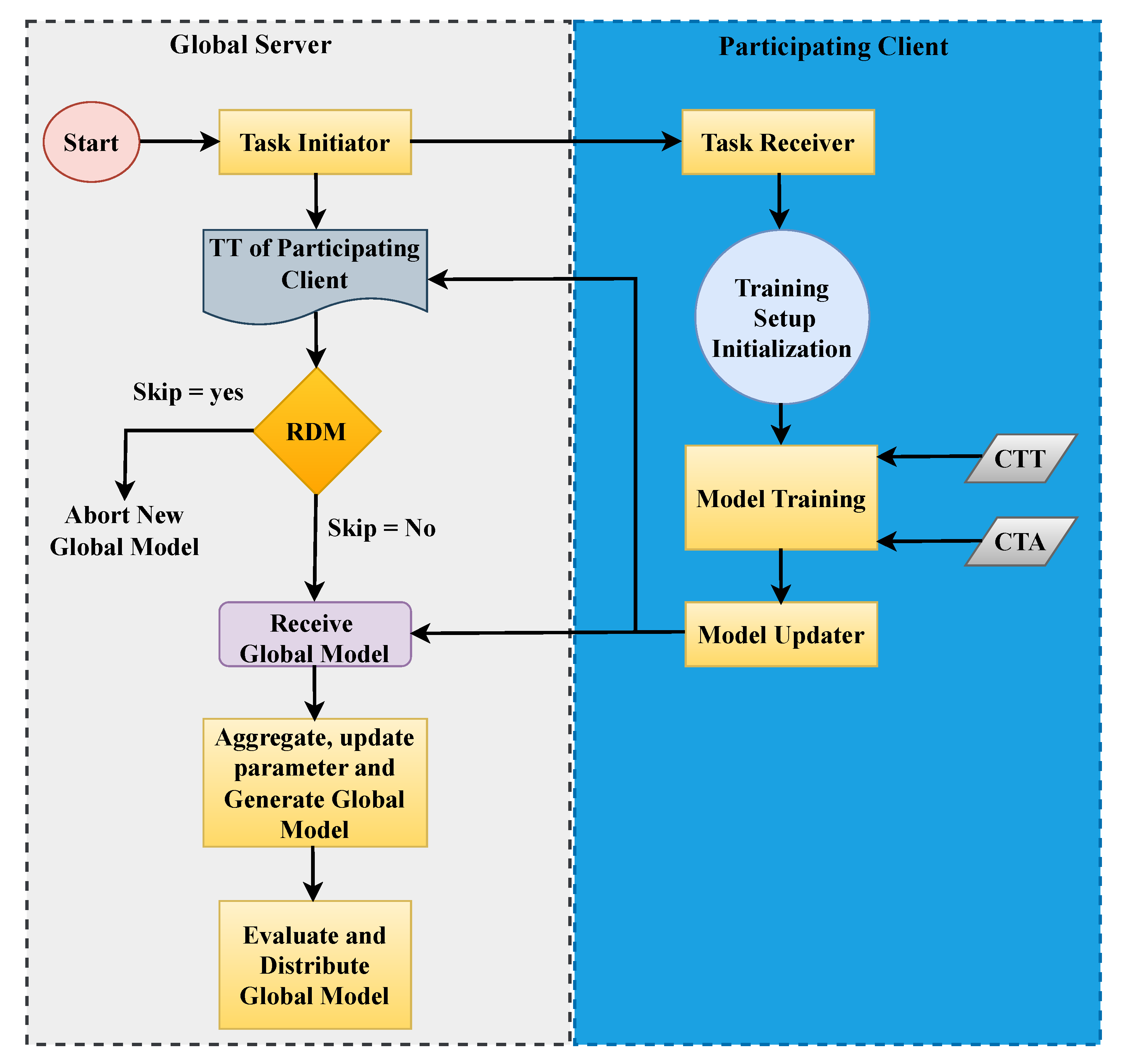
Figure 1 demonstrates a high-level architectural overview of the PriFed-IDS framework that shows how each of the key system components, i.e., local IoMT nodes, a central coordinating server, and a reinforcement learning agent in charge of progressive client selection and the optimization of the policy, works. Remarkably, the offered framework is modular and extensible per se, thus allowing the attachment of new hardware to a device or subsystem at any stage of the deployment process without interfering with the operations in progress.
4.2. Federated Learning (FL)
FL works in a similar way to distributed and collaborative machine learning because it allows multiple devices to train a model together without sharing their data [
56,
57]. In FL, the architecture is primarily composed of two integral components: a centralized coordination server and a set of participating clients that are distributed. The centralized server is tasked with orchestrating and initializing the global training process, while each client is responsible for locally training its model using computational resources and data available on-site. In PriFed-IDS, deep neural networks are employed to learn and train both central and client-side models. These networks facilitate end-to-end feature extraction and classification by directly processing the raw input data from users.
Within an IoMT environment, each client typically associated with SHS collects, stores, and preprocesses data generated by connected medical devices. The centralized server initiates the training cycle by transmitting a configuration package to all selected clients. This package includes key parameters such as global model initialization, fusion aggregation criteria, and predefined time constraints for participation.
Following the acquisition of these configurations, each client commences a local training phase by optimizing a local model based solely on its private dataset. After a specified number of epochs is completed, the client uploads its model parameters to a central server. At this point, the server’s aggregator takes these updates and coalesces them into a single global model.
Significantly, each training round is concluded by comparing the performance of the updated local model with the performance from the previous round. Updates to the model from a client are incorporated into the global model only if the new performance exceeds the performance from the previous round. Furthermore, any client that did not meet the required training epochs in the specified time period is not included in this round of fusion. Once updates are received from all clients who completed their designated training epochs in the requisite time period, the central server aggregates the results, and the newly updated global model is transmitted back to all clients. This decentralized training process, followed by aggregation and redistribution of the global model, is illustrated in
Figure 2 for the reader’s convenience.
In order to improve communication efficiency and accelerate the training, the proposed fusion mechanism follows two main criteria: client selection and client participation. The client selection phase depends on the time taken by each client to finish its training task. If a client exceeds the maximum allowed training time, it will not be allowed to participate until the next training round. This policy ensures speed, minimizes straggler effects, and facilitates faster overall convergence in federated learning.
4.3. Reinforcement Learning (RL)
Reinforcement Learning (RL) is a specific machine learning paradigm in which an agent interacts with an environment to learn the optimal decision-making process through receiving rewards and penalties. The main concept is to encourage actions we want to take through positive rewards and discourage actions we do not want to take through negative rewards. The agent finds to maximize these rewards through exploration and exploitation with some trial-and-error [
58]. In a general RL framework, the system is made up of two main components: the
agent and the
environment. At each discrete time step
t, the agent observes the state
, takes an action
, and receives a reward
from the environment. The reward
is supposed to be a metric in some way quantifying the value of the action taken after the observable state. The agent then adjusts its policy using the feedback from the previous step so it can increase the total reward it expects to earn in the future. Based on this setup, an agent can perform decision-making through available actions to maximize its positive reward through a sufficiently controlled trial-and-error process.
The proposed PriFed-IDS framework employs Q-learning, a model-free Reinforcement Learning (RL) algorithm, to determine agent policies and actions. It can be applied without prior knowledge of the dynamics of the environment where it is being applied. Instead, Q-learning seeks to estimate the optimal action-value function
, which estimates the expected utility of an action
a, when the agent is in state
s and follows the optimal policy after action
a is taken. The Q-learning process relies on iterative updates to the Q-table, a two-dimensional matrix where each row corresponds to a state
, and each column corresponds to an action
. The Q-value for a given state–action pair is updated using the Bellman equation, as defined in (
1) and (
2):
where
is the value function at iteration
f for state
.
represents the action taken.
denotes the next state.
is the transition probability from state
to
.
is the reward function.
is the discount factor (
).
To make the learning process even easier, we use a value iteration method, which tries its best to correct the Q-values at each step until we obtain the optimal policy. In this way, the agent can know which actions are the most rewarding in different states at different time points. To ensure conceptual clarity, the reinforcement learning cycle of the observation of the environment, based on which a policy is executed, thus obtaining a reward and updating the policy, is graphically presented in
Figure 3. The agent stands for the local IDS model present at each client node, while the environment reflects the distributed IoMT network, which gives appropriate feedback in terms of a reward function, which indicates the detection rate and efficiency of communication. The states and actions of this RL process are also shown, which indicates the way this RL process can dynamically optimize the intrusion detection and model aggregation. Q-learning is used in this study because it is a self-adaptive learning model, meaning that it cannot make use of pre-determined models or an expert. It is computationally simple and experimentally convergent, and hence, it is suitable to be deployed in resource-limited scenarios like those of an IoMT node, where the requirements of policy learning are speed and efficiency.
4.4. Dataset Acquisition and Preprocessing
In order to evaluate the effectiveness of the proposed PriFed-IDS framework, extensive experimentation with the real-world dataset aimed at evaluating the proposed model and other existing benchmark models was performed using a real-world dataset generated at the Cyber IoT Lab, the University of New South Wales (UNSW), the Australian Defence Force Academy (ADFA) [
59]. The data portfolio encompasses a broad range of cyber attacks applicable to both IoT and IoMT settings, such as password attacks, injection attacks, Distributed DOS (DDoS) attacks, backdoor attacks, scanning attacks, and Ransomware. The attacks were planned and tracked in a well-planned manner so as to guarantee variation between good and bad network traffic instances in an effort to model realistic threat scenarios in medical cyber–physical systems.
In
Table 1 we display the record distribution and volume in our dataset, which offers a wholesome diversity of both labeled attack and non-attack examples. This dataset was chosen due to its real-world application and specific focus on networked medical devices that often transmit sensitive patient health information using communication channels such as Wi-Fi, Bluetooth, and 4G/5G. For experimental training and validation, each of the various IoMT datasets was divided into training, validation, and testing datasets in a ratio of 70:15:15, maintaining the original distribution of the types of intrusions across all datasets. To mitigate the impact of the imbalance between the number of samples of a specific type of intrusion, as is common in cybersecurity datasets, stratified sampling and targeted oversampling of the minority classes were also implemented.
To guarantee high-quality data for the training phase, the PriFed-IDS framework employs various data preprocessing methods, including labeling the attack and benign classes, feature normalization in order to render the input attributes in a consistent scale, and dimensionality reduction techniques such as Principal Component Analysis (PCA), used as the dimensionality reduction technique before model training. The PCA technique converts the original feature space, which is correlated, into a smaller number of independent orthogonal components that retain maximum variability in the data. This helps in eliminating multicollinearity, reduces computational complexity, and, at the same time, retains the most informative features of the data. These preprocessing methods are necessary for filtering noise, addressing data imbalance, and standardizing inputs in order to prepare robust intrusion detection models. In addition to the IoMT cyber attack dataset, the evaluation of the proposed framework was performed on the common Heart Disease Dataset from the UCI Machine Learning Repository [
60]. The Heart Disease Dataset contains 303 instances with 13 clinical features that are used to predict the probability of heart disease in patients. This dataset serves as a second benchmark to demonstrate how well PriFed-IDS generalizes across healthcare data domains, specifically in a supervised classification context related to medical diagnoses.
5. Results and Evaluation
The PriFed-IDS framework was implemented using Python 3.10 on Ubuntu, utilizing an Intel Xeon Gold 5218 processor, an NVIDIA A100 GPU, and 64 GB of RAM. The framework was set up with a learning rate of 0.001, which provided sufficient computational resources to perform all required deep learning operations and to carry out near-federated training simulations.
To evaluate the proposed intrusion detection model, we used standard classification metrics, with a focus on accuracy and detection rate. These metrics are defined as follows: A collaborative and federated intrusion detection system (IDS) framework is designed for intrusion detection in IoMT networks. The designed framework enables an effective detection of various types of cyber attacks, including injection attacks, DDoS, password brute-force, backdoor, and scanning attacks, improving the resiliency of SHSs.
Accuracy (): Accuracy is an important performance measure, which measures the number of correct predictions (for both attack class and benign class) against the total number of observations (i.e., the total number of samples or instances). It is a measure of how successful the classifier is at recognizing patterns or structures within the data. Accuracy is calculated as:
Precision (): Precision is an important assessment criterion in intrusion detection, measuring how many samples that were classified as attacks are true attacks. It indicates how well the classifier manages false positives and, therefore, quantifies the accuracy of the positive (i.e., attack) classifications. Hence, high precision indicates a low false positive rate, which is particularly important for security applications that do not want to misclassify traffic as benign traffic. Precision is calculated by using the following equation:
Detection Rate (): This term refers to the percentage of correctly classified samples out of the total observations, also referred to as recall or sensitivity, which refers to the fraction of true positive intrusions that the detection system correctly identified. It is expressed as:
True Positives () refer to a correctly classified attack sample, and True Negatives () refer to a correctly classified benign sample. False Positives () are benign samples reported as an attack, and False Negatives () are reports of an attack that is not recognized.
F1-score (F1): The F1-score is calculated using the harmonic mean of precision and recall (detection rate), providing an overall measure of the two types of errors (false positives and false negatives). The F1-score is especially important for imbalanced datasets and when both false positives and false negatives are critical, as is the case in intrusion detection. It indicates whether the classifier is able to balance between capturing as many intrusions as possible and limiting the number of false alarms. It is defined as:
High values of , , , and indicate that the model performs well in both general classification and correctly identifying malicious behaviors, which are essential for an effective intrusion detection system in IoMT contexts.
5.1. Performance Evaluation and Results
The performance of the proposed PriFed-IDS is empirically evaluated via exhaustive quantitative experiments that rely on a real-world IoMT dataset, as discussed in the Dataset Acquisition section. The experiment was performed in a CS node and three client nodes, which are distributed and configured with different amounts of computational resources to simulate the heterogeneity that is characteristic of SHSs.
In order to assess the performance of detection, the model was trained on a balanced representation of normal (benign) data and abnormal (malicious) data, where the data contained samples from different attack patterns, as detailed in
Table 1. The results of the evaluation considered the classification accuracy achieved at each client node compared to the accuracy of the centralized global model results.
Table 2 provides a summary of the accuracy results for the individual localized models and the fused global model. The results clearly demonstrate that the federated fusion-based learning method substantially outperformed the independent client models and traditional centralized learning. The proposed model consistently achieved vastly higher accuracy, demonstrating its capacity to generalize across distributed data in order to learn intricate patterns and relationships related to modern cyber attack vectors.
Furthermore, the model demonstrated good convergence behavior during communication rounds. The evaluation of
,
, and loss is shown in
Figure 4,
Figure 5 and
Figure 6. The plots demonstrate that PriFed-IDS keeps a steady and stable
over time, confirming its reliability and robustness in realistic IoMT security situations. The high detection rate implies that the model minimizes FN while keeping FP low, which is vital for healthcare applications.
In addition, the attack-specific detection capability of the model is demonstrated in
Figure 5, showing accuracy scores across the different classes of cyber attacks (e.g., DDoS, injection, scanning, ransomware). These results confirm that the framework can achieve high accuracy, precision, recall, and F1-score across the different types of attacks, demonstrating adaptability and generalizability in neuro-linguistic processing and machine learning classification of heterogeneous and changing situations in cyber threats to IoMT.
Overall, the experiment results can confirm that PriFed-IDS can bring high accuracy and detection efficacy compared to baseline models, stable convergence, and low communication complexity, representing a strong option to be implemented in next-generation IoMT cybersecurity.
5.2. Comparative Analysis
To evaluate the performance of the PriFed-IDS framework, five state-of-the-art approaches were selected for comparison based on their relevance to distributed and privacy-preserving machine learning and deep learning in healthcare and IoMT security. Xu et al. [
61] transform structured data into a 2D image format for Convolutional Neural Networks to secure IOT devices from intruders, using normalization and data augmentation to prepare the data for deep learning. Fan et al. [
62] apply FL to train a shared sleep-monitoring model across hospitals, with a central server aggregating updates without transferring patient data safely. Hossen et al. [
63] combine a custom CNN with FL to classify skin diseases, training across distributed clients while preserving medical image privacy. Chen et al. [
64] integrate FL with Transfer Learning to personalize wearable healthcare models, keeping all user data secure on the device while improving accuracy. Nguyen et al. [
65] detect compromised IoT devices by modeling network traffic as symbol sequences and using FL to identify attacks without sharing raw data. These models provide relevant benchmarks for evaluating PriFed-IDS in distributed, privacy-sensitive IoMT environments.
The comparative analysis of PriFed-IDS with state-of-the-art approaches is presented in
Table 3, which demonstrates that the PriFed-IDS framework significantly outperforms state-of-the-art approaches in terms of both accuracy and detection rates. Specifically, the PriFed-IDS system achieved an accuracy (
) of 99.42% and a detection rate (
) of 99.37%, outperforming all evaluated baseline methods. The results confirm the framework’s robustness and generalizability in identifying a broad spectrum of cyber attacks in sprawling IoMT systems. Existing models usually deal with only accuracy optimization and false alarm reduction in such systems. Our model embraces performance parameters holistically, that is, the true positive rate, false alarm reduction, and efficiency of communication. The learning dynamics of the proposed model are visualized in
Figure 4a, which illustrates the consistent increase in accuracy across communication rounds, eventually stabilizing at approximately 99.42%.
Figure 4b presents the convergence of the loss function, showing a sharp decline in training loss over successive rounds and eventual stabilization at a low value. This indicates efficient learning behavior and confirms the suitability of the selected loss function.
Due to the non-linear and complex nature of medical data, where the clear hierarchy of features is not always associated with it, the network architecture was developed in detail based on the TensorFlow deep learning framework. The model consists of one layer of linear transformations, followed by two convolutional layers to perform hierarchical feature extraction, and two fully connected layers to make the last classification. As an optimization algorithm, Stochastic Gradient Descent (SGD) was used since it is computationally efficient and has a stable convergence record in distributed learning systems.
Figure 6 shows the evolution of the detection rate over training rounds, in which we can observe that, over further communication iterations, the model is consistently able to enhance its detection rate. This increase shows that the model sequentially discovers hidden relations in the training data, thus improving its capability to distinguish normal and malicious behaviors. Also, the trade-off between sensitivity and specificity is depicted by the Receiver Operating Characteristic (ROC) curve expressed in
Figure 7. The AUC supports the high predictive capacity of the offered model and substantiates its overall practicability in a real-life medical cybersecurity context.
The communication efficiency of the proposed models is evaluated here, in addition to their classification performance. The communication efficiency is assessed by checking the number of parameter uploads in the federated training process and the total upload time taken. In this regard, the proposed framework, due to its dynamic selection of clients and an appropriate fusion strategy in the model, reduces the communication overhead significantly, on average by 59%. Thus, the proposed methodology, based on established techniques, demonstrates superior performance over the baseline models by effectively addressing the communication efficiency problem.This proposed solution is also suitable for deployment in medical environments, where bandwidth availability and latency are critical communication factors. PriFed-IDS, while shown to have very marginal improvements in classification () values as compared to most benchmarks, has shown significant improvement in the value of and also in general communication efficiency, which are factors that are very important for real-time requirements for high-performance and scalable intrusion detection in the IoMT ecosystem.
Besides accuracy in detection, the proposed PriFed-IDS framework was also evaluated in terms of resource consumption, communication latency, and scalability to obtain a more comprehensive analysis of performance. The experimental results show that PriFed-IDS reduces the average latency in training by around 18% compared to conventional federated IDS models, mainly due to the adaptive selection of clients and its dynamic aggregation strategy. Also, it shows a 15% reduction in computational overhead, since reinforcement learning effectively optimizes training cycles and reduces redundant updates. The detection performance of PriFed-IDS remains stable, while the number of clients participating in the system is increased, thus confirming the scalability of the framework and its appropriateness for large IoMT environments. These results show that the proposed framework ensures high detection accuracy and, at the same time, obtains operational efficiency and scalability, which are fundamental for real-world healthcare applications.
To assess the efficacy of the proposed PriFed-IDS framework, we conducted experiments, comparing it to a centralized IDS using the same model architectures, hyperparameters, and input features. In the centralized comparison, all the IoMT client data was centralized in a single setting for the purpose of training, eliminating the communication and privacy restrictions of real-life distributed deployments. The centralized model achieves a marginally improved detection accuracy at 99.56% due to the use of the complete set of datasets. However, PriFed-IDS achieves slightly lower performance at 99.42% while preserving privacy in distributed operation and producing lower communication costs, both important for operational IoMT networks. The results of this comparison show the promise of federated learning as a reasonable and safe alternative to centralized training without significant sacrifice in detection performance.
We performed an ablation study to investigate the effect of the client selection and fusion mechanisms. For this we used three configurations: the full PriFed-IDS framework, a configuration without the client selection mechanism, and no fusion. Each of the configurations was trained on the same communication rounds and parameters to ensure a fair comparison. The removal of the client selection mechanism resulted in an increased communication overhead of 27% and a small drop in detection accuracy at 98.76%. The removal of the fusion mechanism resulted in a communication overhead of a further 17% and a drop in accuracy to 98.36%. Conversely, the full PriFed-IDS framework achieved an accuracy of 99.42% with the lowest possible communication costs. The results clearly show that both mechanisms outlined are essential for efficient privacy-preserving training and that they substantially improve overall performance within the environment of distributed IoMT systems.
5.3. Practical Implications
The proposed study presents various significant practical implications for strengthening security architecture and enhancing the scalability of healthcare systems based on IoMT technologies. The PriFed-IDS framework proposed offers a flexible means to modernize medical cybersecurity infrastructures through federated learning. In particular, this permits integration with already existing healthcare systems with almost no changes to architecture and allows for compatibility with existing healthcare system topologies. The framework can greatly enhance the privacy of data and allows continued compliance with data protection laws such as the General Data Protection Regulation (GDPR) act and the Health Insurance Portability and Accountability Act (HIPAA) through the provision of avenues for local learning in the individual SHS, while still being capable of transmitting only limited information (parameterized models only). Moreover, the framework can offer a scalable means of designing novel, advanced, privacy-aware, and intrusion-aware architectures to enable current normal centralized architectures to migrate to decentralized security systems.
The system also boasts a large amount of available resource efficiency and lower communication overhead rates during its dynamic fusion process, whereby the model often sends only high-quality model updates on request, thus improving the training convergence rate and saving bandwidth and making it capable of operating in settings of low-resource medical levels. This real-time threat detection is vital for healthcare facilities, as it enables them to contain cascading security threats in high stakes environments such as smart hospitals and emergency departments. Also, the lightweight architecture of the PriFed-IDS model gives it extra flexibility, in that it can be easily installed on cheap edge devices, for instance, Raspberry Pi, Arduino, or disabled Internet of Things devices, and can also be easily installed in various environments in the various health-related industries. In general, the system presents massive possibilities, being powerful yet very light in terms of resource requirements, and privacy-law-compliant, even for small clinics and large smart hospital installations.
When used in actual IoMT settings, PriFed-IDS must be implemented effectively by taking operational sensitivities into consideration. The federated training process introduces communication latency. We estimate this to be about 50–120 ms per training round, depending on how many clients are participating and the quality of the transmission medium. Bandwidth consumption is kept low through application of adaptive client selection and selective model aggregation, which we estimate gives an approximate decrease of 18% against presently existing federated IDS approaches. The practicality of the framework is enhanced by the fact that it has a small computational overhead, such that it is suited for use on resource-limited IoMT devices, since training has an average CPU load of less than 22%, all while ensuring that privacy and security issues can be properly handled. The considerations that result from this show the practical utility as well as the potential problems that would be faced when implementing PriFed-IDS in real healthcare networks.
6. Conclusions
Critical infrastructures, like SHSs and IoMT networks, require robust, scalable, and adaptable security mechanisms to effectively combat increasingly sophisticated cyber attacks. To meet this need, in this work, we propose PriFed-IDS. PriFed-IDS is a novel intrusion detection framework based on federated learning and Q-learning-based reinforcement learning, allowing for privacy-preserving, communication-efficient, and highly accurate cyber attack detection in distributed IoMT environments.
The federated learning module of the proposed model guarantees the local retention of sensitive patient data and fulfills strict privacy constraints. The dynamic federated aggregation scheme significantly improves communication efficiency by aggregating higher-quality model updates. The reinforcement learning agent aligns client sharing and optimizes its own learning based on performance parameters, enhancing global model convergence and attack detection accuracy. Extended experimental evaluations have verified that the PriFed-IDS approach significantly outperforms existing state-of-the-art benchmarks, with results of 99.42% and 99.37% , underscoring its validity in the detection of advanced threat vectors and zero-day attacks in real-world IoMT networks.
In order to further improve the performance and scalability of the PriFed-IDS framework, future work will focus on two strategies. First, the use of asynchronous FL will be investigated to eliminate synchronizing bottlenecks between client nodes and the central server. This is expected to reduce communication overhead and improve training throughput, particularly for heterogeneous and latency-sensitive clients. Second, the integration of incremental or continual learning techniques will be investigated in order to allow for real-time model updates with the inflow of new data. This is expected to allow the framework to automatically adapt to evolving intrusion patterns without needing full retraining frequently. The enhancements above are expected to greatly strengthen PriFed-IDS as a real-time, adaptive, and scalable security framework for next-generation IoMT applications.